Industrial devices and protocols differ from the modern protocols we see in enterprise, service provider or datacenter environments. Traditional spanning tree protocol variants are also not good enough for an industrial environment requiring fast convergence. There are though specific protocols designed for OT environments, which we will address below. Let's jump into the first one.
Media Redundancy Protocol
A ring topology is built, with a ring master and clients, all having a pair of ports participating in the ring. The master is responsible for managing the ring by sending control frames in both directions. One of the master ports is in blocked status, allowing only control frames to arrive. Whenever there is a failure in the circuit, the blocked port will transition to forwarding state, allowing communication in both directions towards the break point. Convergence time is deterministic from 10ms to 500. All ports that belong to the ring need to have Spanning-Tree disabled, however it's recommended to enable it on non-ring ports to prevent loops.
%3CmxGraphModel%3E%3Croot%3E%3CmxCell%20id%3D%220%22%2F%3E%3CmxCell%20id%3D%221%22%20parent%3D%220%22%2F%3E%3CmxCell%20id%3D%222%22%20value%3D%22%26lt%3Bb%26gt%3B%26lt%3Bfont%20color%3D%26quot%3B%2300cc66%26quot%3B%20style%3D%26quot%3Bfont-size%3A%2020px%3B%26quot%3B%26gt%3BMRP%20Ring%26lt%3B%2Ffont%26gt%3B%26lt%3B%2Fb%26gt%3B%22%20style%3D%22rounded%3D0%3BwhiteSpace%3Dwrap%3Bhtml%3D1%3Bdashed%3D1%3BdashPattern%3D8%208%3BfillColor%3D%23CCFFE6%3Balign%3Dcenter%3BstrokeColor%3Dnone%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%2291%22%20y%3D%2250%22%20width%3D%22539%22%20height%3D%22200%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%223%22%3E%3CmxCell%20style%3D%22vsdxID%3D1%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%2C%5B0.87%2C0.96%2C0%5D%2C%5B0%2C0.24%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22118.91%22%20y%3D%2279%22%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%224%22%20style%3D%22vsdxID%3D2%3BfillColor%3Dnone%3BgradientColor%3Dnone%3Bimage%3Baspect%3Dfixed%3BstrokeWidth%3D102%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D0%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%3Bimage%3Ddata%3Aimage%2Fjpg%2C%2F9j%2F4AAQSkZJRgABAQAAAQABAAD%2F4gHYSUNDX1BST0ZJTEUAAQEAAAHIAAAAAAQwAABtbnRyUkdCIFhZWiAH4AABAAEAAAAAAABhY3NwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAA9tYAAQAAAADTLQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAlkZXNjAAAA8AAAACRyWFlaAAABFAAAABRnWFlaAAABKAAAABRiWFlaAAABPAAAABR3dHB0AAABUAAAABRyVFJDAAABZAAAAChnVFJDAAABZAAAAChiVFJDAAABZAAAAChjcHJ0AAABjAAAADxtbHVjAAAAAAAAAAEAAAAMZW5VUwAAAAgAAAAcAHMAUgBHAEJYWVogAAAAAAAAb6IAADj1AAADkFhZWiAAAAAAAABimQAAt4UAABjaWFlaIAAAAAAAACSgAAAPhAAAts9YWVogAAAAAAAA9tYAAQAAAADTLXBhcmEAAAAAAAQAAAACZmYAAPKnAAANWQAAE9AAAApbAAAAAAAAAABtbHVjAAAAAAAAAAEAAAAMZW5VUwAAACAAAAAcAEcAbwBvAGcAbABlACAASQBuAGMALgAgADIAMAAxADb%2F2wBDAAMCAgICAgMCAgIDAwMDBAYEBAQEBAgGBgUGCQgKCgkICQkKDA8MCgsOCwkJDRENDg8QEBEQCgwSExIQEw8QEBD%2F2wBDAQMDAwQDBAgEBAgQCwkLEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBD%2FwAARCAGPCigDASIAAhEBAxEB%2F8QAHgABAAAHAQEBAAAAAAAAAAAAAAECAwUGBwgECQr%2FxABwEAABAgQEAgQGCQoNDgwGAQUBAgMABAURBgcSIQgxEyJBUQkUMmFxkRUWI0KBkqHR0hcYGTNSVZOUscEkJVNWYnKChKKywuHiNDU2Q0VUV2NzdIOVo7MmN0RGZGV1haS00%2FAnKDh2w%2FFHZneltYb%2FxAAbAQEAAgMBAQAAAAAAAAAAAAAAAQIDBAUGB%2F%2FEAFERAQABAQQDCQkMBwgCAgMAAAABAgMEBREGMdESFBYhQVKRkqEVUVNUYXGBsdIHEzIzNDVCRKKyweEiIyVDYnLwJEVVY3OCwuIXJjbxs8PT%2F9oADAMBAAIRAxEAPwD6pwhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQhCAQiFx3wuO%2BAjCIXHfC474CMIhcd8LjvgIwiFx3wuO%2BAjCIXHfC474CMIhcd8RgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgPn%2FwAcXH7WstcXTGUmUEy3LVWkrR7LVdQCw08QFeLtoIIUQD1j2HbmDbk%2F7I5xNadQzTYJHMeJsgj%2BDGmOIidmZ7OHH85MvLcfcxTVFFxStyfG3OcagW5AdkN%2BEZ4mXFgfVYl0g77ybFhbsPVjxOeEs4ni%2BsN5jICbqSkmSZA9Pkxx%2Bs3HPsMUzc8zf0wHZbvhG%2BKltagxmEXm%2FerVTmk3HxYk%2ByO8V1%2F7PyfRT2j%2FACY5dlMf4kkJNuUbWw40wlKE9Iwk2SBa0T%2FVOxP9xJ%2Fi6YDqH7JFxUjnjtX%2Br2voQ%2ByQcVLilFvHq7dwp7Rt%2FBjl05m4mPNuTPpl0xIcy8T9ipVPdaWTtAdR%2FZG%2BK7l7fnt%2F%2BrWvow%2ByOcVp5Y8f3%2F6uZ%2BjHLf1TcW8hMsfgEiIjM3F3Pxtnf%2FEJP5oDqT7I3xXjnjp%2F%2FVzX0IiPCNcVqv8An0%2F%2FAKua%2BjHLiszcXKH9VtfgE%2FNFM5l4wB2m0fAyn5oDqoeEX4rzyxvMH%2Fu5n6MF%2BEU4sleTjabT%2FwB2NfRjlM5lYvKtXjuk2t1WUD80ROZmMjznyf8ARJEB1QfCK8WoP9ms3%2Fqxr6MPsi%2FFnbfGk5%2Fqxr6McsfVKxiP%2BWK%2FBj5oiMzcZjlO%2FwCzT80B1UnwjfFfaycWzSz2%2FpY19CJh4R3isHVOK5jV3exzX0Y5QVmXjFZt48UnvCAIgrMjGVrGpK9IbT80B1j9kb4sSdsTTX%2BrWvoxMPCLcWZ%2F50TP%2BrWvoxyV9UbGPL2Vc%2BKPmiYZh4vP92HR%2B5T80B1sPCK8WR%2F5zTP%2BrmvoxOjwi%2FFc41pRiN8qvfUJBrl8WORxmHjMDq1l4ehKfmiX6oWNL3NYfJ77iA63%2ByKcWn65Jj%2FV7X0Yn%2ByJ8W3ZiF8%2BintfRjkX6oWNfvvMesfNEpx9jJXOrTHrEB1yrwinFseWIZlP%2Fd7X0Yk%2ByK8W%2B%2F8AwkmNuf6XtfRjktOYGMk8qq98JBiX294x%2B%2FD8B1unwinFwd%2FbHMEf9ntfRiqjwjXFi4rSmuTIPnpzdv4scgnHGMFG5rMzt57RFWOsZOJ0mtTdvMoQHX48IvxaFRT7OPG3aZFofyYfZE%2BLf7%2BPfiDX0Y499vOMOXs5OfGiBxvi8neuTh%2FdfzQHYn2RTi0%2B%2Fr%2F%2Br2vow%2ByJ8Wv38mP9Xt%2FRjj3284u5ezc36x80PbzjG4V7Pzlxy60B2EfCJ8WoF%2FZyY%2F1e39GJD4RPi5G%2Fs4%2Fb%2Fs9v6MchJx7jJI0muzah5zeIJx7jFAKU1qbAPPrC0B16PCKcXANjXXx5zT2gP4sTq8InxbAbVx%2F4ZBr6Mcg%2B33GNrezcxbu2ib2%2F4z%2B%2Fkwdrb2MB119kX4thzrT34g39GKqfCKcXKvJqzh9Mi39GOQRmDjJKAg1p8pTaw22tyin9UDGQ%2FuzN%2FGEB2L9kR4uvvo5%2BJNfRiC%2FCJ8XTZsupug%2F5i39GOO%2FqgYyOwrM38YROMeYzCVIRWplKVcwDAdgfZFeLn76Ogf5k39GA8Ipxbk7VZ0%2FvBv6MceDG%2BMB%2Fdyb9Yib294x%2B%2Fk38C7QHYX2RPi3%2B%2Bzv4i39GIr8Ihxct%2BXWHB6JFs%2FyY469vOL%2Fv1OfHiQ46xhe%2Fs3M%2FGgOyD4Q%2Fi7Tzqzv4g39GH2RLi5vY1N%2F0%2BIN7%2FwAGOOvb9jP79zXwKh7fcZ%2Ffqd%2BNAdkDwiHF0n%2B6Ewf3g39GCPCI8XIPWn3j%2B8m%2Foxx0MfYwCTrrU4Se0r5xTGPcYaj%2Bm81buCoDs%2F7IdxbaCPHn9d9j4i3a3xYpq8Ihxb9k88P3k39GONRj7F45VWZH7uJvb%2FjH3tZmx6FwHY58IdxdgA%2BPrN%2BwSbZP8WJU%2BET4uFf3QcHpkm%2FoxxwMfYxSrUmuTST5lRA46xernWJr48B2R9kS4ufvgv8AE2%2FowHhEuLhR0ioLJ7vE2voxxuvHWMF3vWZsX3Nlw9veMd%2F08m99z1oDso%2BEP4vQbePOekybf0YDwiHF52zyxbvlG%2FoxxqceYuG3sxMkdoKolOPcYn%2B68z697QHZn2RTi1%2Fv938Sb%2BjA%2BER4uveTjq%2FRJN%2FRjjMZgYzv%2FXmZ9cVvqj41%2B%2FkyPRtAdkHwjPFskpu6sXPLxJH0YmPhHOLH9WX%2BJI%2BjHGIzFxohWtutzST3gxA5iY1PKuTg%2FdwHZ32R3iw%2FV1fiSPoxA%2BEZ4sU9ZU24Ae6SR9GOMRmHjUW%2FTyaNuVyDEfqhYyJBVWZq45dflAdlp8JDxVrNkziif8yR9GKn2Rniy%2FV1%2FiaPoxxp9UTF5Gg1ycCfMqKf1QsZ%2Ffyb%2BNAdn%2FZGeLL9XX%2BJo%2BjEyvCK8WabfohR1ctMmg%2FyY4vGYOMRyrk2OzZcR%2BqFjE6R7OTY07CyrWgOzUeEZ4s1Lt4w5b%2FM2%2FoxUX4RLi1R5T6vxNH0Y4s9veLbW9nJq3O2qBx5i379zXx4DtFvwi3Fm6Pc3lHz%2BKI%2BjFY%2BEW4sD22va36FRvf9zHEwx1i0cq5OAeZZtE6cdYxT5Nbm7ft4DtY%2BEW4sE81H8VR9GJD4RrivSqxUfxRFv4scWHHOMCdRrM1f9vD284w%2B%2FM18eA7VHhGeLDzH96o%2BjEfsjHFh3f8AhUfRjioY5xf21uc%2BPE3t5xf9%2B5z48B2n9kY4suwH8VR9GH2Rfix7L%2FiqPoxxUcc4wvtWpz8LEBjjF3ZWpz8LAdrHwi3FoeQV%2BKo%2BjER4RHi1O41H0Srd%2FwCLHFXt3xb21uc%2FCQ9u%2BLfv3OfhIDtX7IpxbA7tq%2BGVR9GJvsi%2FFiB9q%2F8ADo%2BjHE5xvjD7%2BTtv8pEvt1xZfatTv4SA7a%2ByNcWX6h%2F4ZH0YfZGuLH9RH4uj6McUe3jF%2FwB%2B5348BjfF6fJrU6P3cB2v9ka4sf1EfiyPow%2ByMcWJ5hI%2FeyPoxxV7d8Y%2Ffqa%2FCQTjbGCeVbnPwkB2sfCM8VwOnoyT5pVH0YiPCL8WKfKYV8MqgfyY4q9vGMfv5N%2FhIgccYxP93Jv8JAdq%2FZGeLDn0Qt%2Fm6PowPhGuK4f2q%2FolkH%2BTHFHt0xcRb2am7d3SRMnGuLU7prc6P9JAdp%2FZHOK79SV%2BKp%2BjFYeEX4r2%2FLZB21by6B%2FJjij2940G3s%2FO%2FhYgcc4yULKrk2e3dyA7YT4SDirUgWlGtzYEsJ5%2FFiJ8I3xXAX8VQfRLpP8AJjiM4yxYVa1ViaKu8uROnHGMECyazNDz694Dtk%2BEc4q%2B2XA%2FeyfowHhH%2BKdStHQNg%2F5un6McTKxzjJaQhVdnNI7OkiPt2xbo0ezs5bu1wHbCvCOcViPKkfVLp%2BjAeEf4qFbeJWPnlk%2FRjib274vHk12dHociJx3jQkk16cJIsTrHr9MB2wPCN8U55sAfvVP0YJ8I5xVLbLiZQaRzJl0j5NMcTqxzjBSdJrc5b%2FKxKMcYyCir2cm7lOm5cubd0B219kb4q7X8Vb%2FAJv8AxYl%2ByPcVRWUIk0qI52lk%2FRjiz6oON739npy%2FfrESLx5jZwELxBOkHs6SA7cX4SLimR5VKH4uPoxKPCT8UZOn2KRf%2FNx9GOIxjfGP36m%2FjxOcdYyKdBrU5bu6SA7cPhIOKUC5prY83Qpv%2FFiZHhHeKZfk0tP4uPoxxCMd4ySbitTYPmXEBjrGg5V2d2%2FxsB2%2BrwjnFQnnSwP3uPoxA%2BEe4p0jUqmNgXAJ6AbX%2FcxxEceY2JJNenLnn7pD29407a5N%2FhIDuBXhHeKhCgg0pq5FwAwPoxI54SDikaQlaqYnSvkRLg%2FyY4jGPMZBvoxXJ0J7g5tEfb%2Fjbrfp5Odc3V7pzPfAdtDwkPFGf7mpHplx9GA8JDxRjyqcg%2FvcfRjiT2%2B41%2B%2Fk5%2BEh7fca%2Ffyc%2FCQHcDfhIOKBQ%2FrWyfS0B%2FJgjwkXE6olJpTSSO9kfRjh4Y6xjaxrU4R3Fy8VDj%2FGSk6DW5y37eA7cR4STidW4W00hJI%2F6MLfxIj9ki4nidIo6L%2F5EfRjiNeYOM1psuuTah3FcUhjvGqU6EV6cCeVg5Adwr8JBxQI50hs%2BhgH%2BTEPskvE596EG3cwPoxw8jHWM2zdFbmwfMuJjj3Gyr667OKvzuuA7e%2ByS8TYFzSR6PFxf%2BLA%2BEm4m7f1rQnt6zA5fFjiQ5hY3WQXK5NEgWB1comOYWNSB%2Bn02LdxEB2yPCS8TihqFLaI7%2BgH0YgfCS8Tn3uaH%2BgH0Y4nVmHjddtWIJvbsuAIm%2BqDjW39fpo2%2FZQHa7nhJeJtleh2mtJI72B9GK%2F2SfiWtf2IY9HRD6McPfVBxl1v05mzqNzdd7xN9UbG17%2BzU1fvuIDtw%2BEp4mNdhRWyP8j%2FAEYj9ko4mrH9JEfgP6McRnMTGxTr9nJq%2FwC2ES%2FVGxte3s5NfGgO3vsk%2FEyE6vYZs%2BboR9GH2SviY%2B8KPwP9GOIfqiY3H92pr1iJvqj44%2B%2FMz8nzQHbKvCW8TKTc0NFv8h%2FRic%2BEs4mUnSqgpH%2Bh%2FoxxEMx8cjlW5sfuoiMx8cjlWpr1wHbg8JZxLq3TRW%2FR0P8ARiceEp4meSqI1c8vcf6McQN5l44QvUa1M%2Bg2MRVmRjdarqrM1v5xtAdsr8JbxLJsk0du997MX%2FkxVa8JbxJK%2FuGwfS2B%2FJjiNOY2NwNq5NesQRmNjVH92Hz%2B2AP5oDuFHhKuJNzVpw8x1efuf9GKTnhNeI1lQSrDzO%2Fb0X9GOI1ZjY1UoKVWZi45WsLRBvMXGjaOjTWpnT3XgO4VeEs4kyjWjDrNvM3f%2BTHm%2Byb8SH63mvwJ%2BjHFKcycbN7irun0pEU1Zk41JuazMX%2BD5oDtweE04kSNQw8z8LW%2F8WJvsmnEh%2Bt1r8EfoxxCczMddTTV306OVgPliJzNxud11Z8%2FAIDt77JnxHDnh9sX%2FwAT%2FRiU%2BE04jxzoDIA%2FxP8ARjiQZoY27KivfvSIiMz8a7H2TcuOd0CA7ZHhOuIkp1CiMEd%2FRf0Yk%2Bye8RINjRGPwX9GOLDmjjNXOof7MRJ9U3GV7%2ByJPmLYMB24nwoXECryaBKH9x%2FRgvwoPEC2pSV4flwU%2BV7ny%2FgxxGvMzGKwEmfsAbizSfmidGaWNGx1Z8fC0IDtc%2BFFz%2B97QpX4UH6MB4UbP4%2F3Blfgb%2BdMcUHNbHBVq8dSPQ0n5oKzSxo4bmokeYNJA%2FJAdsK8KHn8gXVQpX4u%2FwDFiB8KLn6kG9DlR%2Fo%2BX8GOKPqn4w028cTb%2FJJ%2BaAzSxgm9phG%2FP3JO8B2p9lLz6B0ihSxN7WDf9GKifCk5%2BG%2BrDsuLc7t%2F0Y4pOa%2BMyNJmUEf5FPzRTOaeMf75T%2BCTAdtfZSM%2BT5NClT6EX%2FkwHhRs%2FVAgUCWNufuf9GOJ0Zq4wQm3jjZ85YSYmRmxjBHKaaPpYTAdro8KLn4bfpBLqtz9z5%2FwYifCi5%2Fav7HpcDu0H6McSuZrYwc%2F5Q0nfV1WUjeBzWxf%2FfLf4IQHbSvCk59JAUrDcsABckpO4%2BLEFeFHz8TZasPSgSeV0%2F0Y4l%2BqtjC1umbI7i0DEDmni1XlOsfgBAdtL8KTn0jdeH5ZP7g%2FRiVfhTM%2BEf8AN%2BX5X%2B1H6McUfVUxdaxfZItaxZSdoirNXFxBAmGQD2BlO0B2qnwpufC%2FJoMof3B%2BjEVeFMz5QrSqhSQNuRSfoxxU3mxjJvyZiX%2BGWT80SrzUxes36eXv3mXSfywHa7nhS8%2Bk3KaHKlIJBIbPr8mKQ8Khn1r0%2BwcqR39GR%2FJjir6qWNP7%2Bb%2FAJiUZn4uSNn2%2Bd%2FtKYDtoeFOz4UnUmhypBNh1Dz%2BLFT7KnnqDpOGpQnb3p%2BjHEQzaxglSlB5gFWxswn5og5mxjB0nVNtgHmkMptAdujwquefk%2B1uTvcdhv%2FFiYeFTz1uAcLywJNgClQufixxA3mxi9sjTMsm3fLIN9rd0TO5tYudSEdMyhKQLBLCRy5QHbqfCpZ6qcUhOG5TUjmkIVcfwYgnwqmeSz7lhyTXvudJFvWmOH%2FqqYs0geMNWSefQJv64HNXFZbKFTDFlHceLpveA7hPhUc99%2FwDgpLbc7pP0YkV4VTPVv7dhqTb298lQ3%2BLHESc1sVJAKVy1wbg%2BLpB%2BSILzYxc4NPSsAWtswmA7eHhVM9SSoYakynsslX0YqJ8Kbny6SW8NyQFu0H6McOJzYxfbQJtvYWHuI2ioc18VHyjLKPYVS6djAdvHwp2e4KknDkrdPOyFG38GIjwq2eCEdKrDckUJNiSFfRjh5Ga%2BLUnUp1hR5X6Id1vyQVmvixQIVMskEWIVLpO3qgO40%2BFbzr1afavJk93W%2BjEyfCrZ3qtpwpKnVe3VV9GOGfqp4qUQovyxIWHASwm4I%2BCJvqr4wuCmfbFhawZTAdzq8Knnc35WF5Ej0qH8mCfCn56WI9qsmT6FbfwY4aGbuLbBC32FJFwAWEw%2Bq7iu50vsIBFiEsJHw%2BmA7mR4U%2FPRfkYRlVegK%2BjEPsp%2BeO98Kym%2FmV9GOG1Zt4qWVKVMs3Xz9ySIic3sWnnNMHe%2B7KYDuE%2BFRzuvcYZlD5gk%2FRgfCn56ghPtRlrncdRW%2FwDBjh45w4tPlPyv4skxKc3sWk7zjRHK3QptzvAdvr8KxnaFafaxI37gSf5MTI8Knngs3ThWTI7rK%2BjHEH1W8VaQkGU25foVMTLzdxavYGVT5kyyQPVaA7gc8Krnc2Sn2oyKiOekqNv4MD4VjOr3uEpM3F9wvYfFjh4Zr4wvq6VjcWPuIiIzYxYm4C5cX2PuCd4DuEeFWzsV5OEZI3Nh5X0Yirwqed6eeEJIfG%2BjHD31V8Xbf1MQE6RdgHaH1VsXdH0epi3%2BQEB3IjwqWdizb2oygNtgAo%2FyYpr8KxnYwAXMISIueSioX%2Fgxw99VHFR2LjF7fqAuYiM08VEAWYUezUwDAdwJ8KznYOeEZE%2FCr6MTL8KznOhoFWF6eFX71X%2FixxAnNrGKPJVLj97piT6qeLP%2BjcrfaB80B299lbzpsP8AgxIfwvowHhXM6ykhOEZEnnfr%2FQjiQZs4sTqIRLXPI%2BLp2%2BSIfVexdtq8XNuX6HFvVAdwN%2BFbznSPdMJU86uV1KH8mJl%2BFdzhbIDuEqek2vYqV9GOGjm3ispCC3KkA33YG8TqzdxcvYoktzfeWST8sB3Cnwr2caz1cIU%2B37ZX0YiPCv5xi59pcir0KV9COG%2FqrYsuCUSZsnSB4snlEPqs4vunryvV7PFk2MB3InwredKhcYKk7ecK%2BhAeFczlUQlvCVPUs80gquPT1I4fGbWLrqUUy118yGAIk%2Bqti4%2BV4sr9swLwHcivCvZxNKKXcIU4G3IqULfwIHwrucitITg%2BQFxzure%2FL3kcOpzZxgL6vFlXFifF03iBzXxcoglMubG%2F2kQHcq%2FCs5yNoSV4RkATfmVj%2BRFMeFfzfPk4Tp6vQtX0Y4e%2BqxjHrBS2VBXYphJ%2FNEPqrYpHksSI%2FeqYDulHhWc5EuJUvBEkpINykqULj06YifCtZxK02wVIJvfkpZv%2FAAY4XVm1ipaytTUmbggjoBax5xInNfFyffy3wMJEB3YrwrGcaEhS8F09IPIqWsX%2FAIMSHwr2bwSkjB9NNz2OK%2BjHDKc2cWW6xZJ87SVD1GDebOKUC3RyZ8%2FiyQYDuRXhYM3UFKV4PpoKjYArXufiRMPCt5xqOlOC6eT%2B2X9COHBm1ijUVaZbcWI6BPzQObOLNICQ0mxvcNDf07QHca%2FCuZxoNvaXTie7WsfyYl%2Byw5u9X%2FgjSbnmnpV3H8COHDmzik80Sx3vuwmJvqt4k%2FvOQPplk39cB3H9lfzfNtOC6arVys4vf%2BBA%2BFgzdb2dwdTUEdhcXc%2BjqRws9mrilzTZuURbc2lxv80RVmxidVtbUsq3fLpMB3R9lizaSCo4Spm3YpxY%2FkxFHhZM2XBdGDKZbzOLP8iOFjm7idzZTMooctJlk%2FNE4zdxT5CWpNKRttLp%2BaA7n%2Byx5tG%2BnBVOOnn11%2FQiH2WTNpR9zwdTFW%2FZr%2BhHDJzfxe0LNGU%2BGXSYpqzYxYsXWmWR50y4FoDutXhZc2QL%2B0qm2HMlaxb%2BBD7LHm2BqOC6YB2EOKN%2F4McJfVUxWOoHUWVz1S6CPyRTOaOJgbamVhPkgsi3qtAd4jwsObhIKcFU2w71rF%2F4ERX4WPNq5IwVSwO4OrP8iOD0ZrYqTfrMEE3IMukiJ%2FqrYnuVFMmb9niqNoDuv7LHm5a%2FtKptv26%2FoRE%2BFizbQpOrBVMAHO7i7H%2BBHCIzZxOlroQiW0A3A8XTFP6q%2BJbWV4uR3GXTAd5HwsWbnZgyknq6vtyuXxYnR4WTNdSUlODKSdQvs8sn1aI4IVmtiZdisyxPYPFU8oivNXEobAIlwAdtMukEwHfH2WXNYHSMCUxxX7F5ZI%2FgwPhZs1Ujr4IpQNiopLy7jzHqRwMM28Sg30yxPf4ukH1gRIvNbEzhupaL3uSGUb%2FJAd%2B%2FZY82Q2FnAFNIJsCl1Zv%2FAAIfZY8176V4Dp6Sdx13PoRwKM2sUgbOgHbkym23LaKic28Vba1tKsb%2FAGlIvAd8K8LDmshAUcC0sE8wt5aSn1oiVPhZM1SnWrAtMTvy6Zf0I4JOa2JVEqU3LG5vYsJNvkiP1W8VEgqdaJG1ywncd3LlAd6%2FZYs11bowPTD%2FAKZf0IgjwsuayloSMCU33Tl7qv6EcFDNbEo8lUuPTLpMQXmziorCkPtI0gdVMugDlbugO%2BT4WLNW1xgalWva%2FTr%2BhEUeFhzWKjqwNSRYbgzC%2FoR8%2FwBGaWJ0JCA42UjkCwm35IqrzSxKtNlrYtbT%2FUyNh6oDv5XhY81G129oVLUm1wenc3Pd5ER%2ByxZpKJIwFS0gHl0yz%2FIj5%2BHNLFBQWzMJKDbboU9nLsiZGaWKUm4f7b26FNvyQHf58LHmnrA9olKCe33Zzn8SJleFizSASoYDpVibbvL22%2FaRwIM2sVX1FbBP%2BboB%2FJETm1i1SNBLGi97eLpJ%2FJAd8nwseaXMYDpNv8uv6ESfZZc0%2BzAdJ%2FDufQjgpGbWJ0CwalyLWsZZJ29UTDN%2FFiftbUmB55UfNAd7jwsGaWnWcD0fY2ID7hI8%2FkcoK8LDminTqwJSxq5Xec%2BhHAqc3cXp8kyqd77S6REpzaxarmZY%2FvdMB36fCv5pDV%2FwGpHVFz7uv6ESp8LDmmpJKcBUo25APr3%2FAIEcBDNXFKVlY8XBPMeLpsYnVmzixxJT%2BhwTvdLCRb5LQHf7fhYc0m0hT%2BXlM0nYFT6x6upEB4WbM0pv9T2ki9rEzLnb%2B4jgQZrYt0JTql7JFh7iPmiP1VcTptql5TY3F5dJ39UB3x9lpzNKtIy9pV%2F84c%2BhFZPhX8zlC6cvqWSAbjp3Ba37iOAlZsYrUPJkxtbaWT6%2BUSnNjFx8tbJP%2BQTAd%2Br8LHmghxKPqdUkBQvczDgI83kQV4WXMoGwwDSCdVv6oc9fkRwGc2cXKGkqZI7PcE7RS%2Bqfie5Opq6tz7gjf5ID6BnwsmZYuTgCk87f1Q59CIHws2ZIJvgGji3%2FAElzn8SOARmxipNtSJZYHYphNj8kSqzXxATfxGRBNr2Z52gO%2FwBPhZMzDzwDR09u8w59CCvCyZmJ%2FwCYNGPbtMufQjgA5tYiVsqTkz6WYgM0q6rlTpMf6KA%2BgQ8LFmeSAMBUQEnTYzbnP4kTDwtOZGkkZfUS4NrGbc%2BhHz8VmdXl%2BVISp%2F0cU%2Fqi1tKT%2BgpUav8AFwH0IX4WnMhGv%2F4e0Q9GAVKE45Yg93U3gnwtGY5sPqe0QHzzjgt5vIj55HMSskbyrB%2F0cSfVEq%2F96y%2F4OA%2Bh58LVmOpCVt5e0U6rkAzbl%2FVoiZPhacw9IUrL%2BjbkA2mnNtv2kfOpWPqqo3LTWxuPcolOPqt%2Bos%2FEMB9GFeFnzCHk4CoarGxtOObdx8iJU%2BFqzBUrSvAFFR5zNuW%2FiR85HMa1JaFIUw11gEk6NyBHlXiefX5Vz%2B5gPpMfC05gJSVHAtCNhewnF39HkRH7LTj3pA2cDUHcX1eOrtyv9x8EfNNdfnVDdPn5R5zVJhe60k%2FAYD6YjwtmPrAnAlBBsSQZ1fq8iJ0%2BFux0k9bAdAUm1951y%2F8AEj5l%2BPvHkFj0RAzrx%2B7gPpuPC443UpAGAsP2WO2dc29PUiYeFuxzdQ9oOHtr7%2BPOb%2FwI%2BYhqE0k7KVEPZGZ88B9PR4WzHClBCMA4eJP%2FAE5z6ETI8LXjVaygYGw7e5FvHnPoR8v%2FAGSmzYb7dwiInJlRNtdwLn0QH0%2BPha8dAA%2B0PDt72I8fc2%2FgROPC0Y4Jt7RcO37T4%2B5YfwI%2BXrlRdKQkBW294mRPvqIJCtQ3gPp8rwtGOktdL7Q8OEXtYT7l%2FwCJEV%2BFoxuAFIwPhw3NrePr2%2FgR8wfZB79l6onE%2B%2BTYBV%2FRAfT1vws2N16bYIw2m%2FMmfc27veQHhZ8c6t8CYdAvb%2Br1%2BvyY%2BYZnZgbLaWPgiAnXDySuA%2BoP2WfG%2BtSfaDhrqgG%2Fsi5Y%2FwACJvss%2BM0uaF4Cw4fOmouEfxI%2BXwnnu5UPHZjs1QH0%2FV4WfGgb1%2B0DDpUVWCfZBzYd56kR%2ByzYz6%2F%2FAADw11Bf%2BuLnW9HUj5emamCbkLPoh46%2F3LgPqEnws2M1I1e0PDQ6oVY1Fy%2Fo8jnEPstOMdGr2g4dvq029kHL27%2FIj5fePPdyoePPD7qA%2BoSvCzYy1qCcBYc0otuag51u%2B3Uh9lmxncf8A8N2UCR%2BmDu1uw9SPmAKi92X9cPH5nzwH0%2FX4WfGaE6vaJhogkf3Qc7f3ETfZZcXjpL4Dw6ejAItUHOvfu6nZHy8NRf7dXqh7JPef1QH1D%2ByyYx1JT7RsNXI5%2ByDtge7yInHhZ8WG3%2FALDQuSN6k52fuI%2BXaajMdiVH4ImVUHtO6FeqA%2BoI8LPi33UnAOG%2BoLp%2FTF26vMOpEfss2LC4lv2iYaSFIC9Sqi5YE%2B98jnHy59kXfuVeqJxUXP1MwH1DR4WfFa0gnAWHATzBqDv0IDws%2BLDf%2FAIB4ZBSSFA1Jy4I7upvHy79k5keQCIgapMDykXgPqMvwseL0rWlGAsNL0i4Psk4Ar0dSI%2FZYsY6UkYCwwbnSbVNw2PxI%2BW%2Fsq9%2BpQ9lXv1L5ID6lHwruNbXRl%2Fhhd06haqObnu8iII8K9jhV%2FwD4fYX2Ntqq5t5z1I%2BW3slMHcN2iYVR%2FwC4MB9SD4VvHJbccby7wwrQogD2Vcufg0RP9lbxwQ4oZb4X9ySFKHsw4Nj3e57x8thVHjzQfXA1N7uI%2BGA%2BpDfhX8YuKAOXmFUA9prDm3%2BzgPCvY4UhS05aYZOm%2B3sw5fbzdHHy0NRfJuW9Q88RFRWP7X8IHKA%2BpX2V%2FHBcS0nLTDCipOoWrLlv93E48Kvj8oLv1MsKhsL0E%2Bzi7%2Bm3R8o%2BWnsmoe9v6RAVJZOyD8AgPqT9lbx5vbLHC5sbD9OnBf8A2cRR4VnHyjpOWGFUm9t64v8A9OPlyKg9bYKimqoPX99AfUw%2BFYx6laknLHC%2FV%2F67X%2F6cB4VfMEgH6luGdxfetrBt8SPlomoudqAfyxOKi52NQH1JHhWMf21fUsw3uQAPZte9%2FwBxEFeFYzDCVH6lGHB0Yuv9O1bfwN4%2BXPsi79yYmFXdQO0QH1H%2Byq5g3t9SjDn%2BvFfQgnwq%2BYBtfKXD5v8A9dqH5UR8uk1uY96tXqBiunEL4OyR8WA%2BnE%2F4WfGFNlfGJrKeigh7olJTV1KI6t7%2BRy88eFrwvWLXW1FvKajKVcaf01Xy8%2FucfNOdqszPtNpUBpbJIskDePESsHUbD0iA%2BoafC2Y0KNf1JKLbz1dQ%2FkRsrIrwndAzCx1TMC5iYMbw4qsTCJSVqMtOiYl0vrIDaXLgFIUSBq3AJF7DePjshSDz0n4Iv%2BEph2Xrci7LLLbiJhtSFI2IUFAg%2BuA%2FSnCEIBCEIBCEIBCEIBCEID87ufn%2FABq43%2F8AuSpq5%2F8AS3Y1O7G1c%2FNs08cD7nEdT%2F8ANuxqpyA9lCpjlVmEy4cQ0krGt1wbIRzKvkG3beMk9gae3sOmcGryzZJI9HZ3x5sNdeQ6TtT1PVF1gPGmh0fktD537Fj5oj7XqKftbEwpX%2BUHzR6%2BUQK%2F3MB4va%2FT%2BXRL9YiBw3TCv7U7b9uPyx7ddu28OkMB4va7TEpulpwG%2FPWDEfYGQBtZZ9BEe4bmx9MSnvA9UB4FYdp55h34VCIpoMgk7a%2FWI9iye8xBLmnYq%2BCA8jlAkVdiz6CIkGHpBHldJ8KhFw1jzw1jz%2BuA8QoUpa1ln4RA4blXeSHEk%2FsxtHtB7ifSDDXfyTfuJ7IDwnDkqjq2VcdusRP7XpPtStXoUI9l1kbAfB%2BWABF76jvble57BYdu8Bb14blT5PSJ%2FdCIDDcqOes%2FuhG8cYcLub2A8uH8zsW0mRpdNlmWX35N6bT4%2B0l5wIbCmRyJKgbXuBzjT%2FbAeE4blQm4ZXbv1CJBhuUJ31ju6wi5AnsJBgpVjyv54DwjDEueSnPWIm9rMq3q1lZ7usI9gcX3RdsP0Kt4prEnhzDlMfqVVqLoZlJNhOpx1Z%2FIANyTsBzgMbVhqXO4U56xEvtclx75frEbTzlyexDknieQwniKtUqoz07TGaktNOe6TxbWSOic7QoFJseRFiIwJQUhtxR1KCdyB5t4C1pw7LfdqUe0ahyiZeG5UJuFlP7oRuHHXD5jPAuAMN5o%2BMyNZw3iKRYm1z1OWXESC3RdLT3cezVy1XHOLdk%2Fla5mxiWaw17aaRQly0kZpt2oOaRMK6RKAy0Oal9a9u4GA1UcNyhP2xfyRVbwxKkXK1n4RG48Q8P%2BN6PnP9QymCXrNed6ByXcllENKZcaDnSLKraEoTfVflaMkzH4T8b5d4Qn8bS2IaFiSSoq9FZZpMx0r1PTyK1p7Ug8%2B0c4Dno4Zkvul%2FGESHDElf7c78kbcn8kcTyWSlJz1StEzRKnPqk3ZZhKlvyqOkLTb67C2haxpFt7kd8M2sjcYZNSOGJjGDsmJjE8k7NplWF3ckloKdTLvZqAWnlte47IDUXtYkv1d35ImOF5EbF50eqNqYHytl8aO4PpTmLqXQJ3FAqk87M1Zzo5WUkJVQbbVfmpx1wPBKe5Ai55o5BYpy5zFpWWqHmcQVWuyrEzTfEb%2B79KopSmx3B2ufNvAaZGFqf2zD59UQVhWQPKZeHpAMdL4n4MMxsOYUqVcartAq1UorPjVSotPmelmZVm1ySPfEC%2B3mNoxLKLh3xdm7SJ7FUnVqTQMNU93xddXqr%2FAEbTr%2B122x74i4ueQvaA0ucJ0ocn5hXwAREYUpffMfGEbbx5kXjfLvMOkZcVpuWXMYgelkUmoNuXlJ1t50NhxK%2BzSo2UDuNu8RkExwvY%2Bl8%2BmsifGZVbzzPj6aykK8TFPCevMk2vZKgUaeeqw7YDQvtUpY5uvnzXETe1ajW5P%2FHHzRnFQwLUJHNP6l7y0uzaMRN0BbrZ6pKnw2pweYJJV8EbEwJwt4qzWpdexXl9XqMqiSNWqUjT2p%2BdSmcfallEJWpCRtrABB5bwGgfarRz%2FbH%2FAIw%2BaHtUo%2F6o%2FwDGHzRsvKvJrH%2BctVfpmB6Sl1EkkKnZyYcDUtKA9jizsCewDcxdc4MgcXZKsUmaxJV6HPNVhbrTPsdOB5SFtgE6080gg7HkYDUSMJ0hJuVPkH9mPmgrCtJPJT4%2FdAxsrJ7KusZx43awPSZ%2BWkHlyUzPKmZkKLaEMpBIOne5uAI8%2BbWWdYyhx%2FPYBq09Lzz8mxLzAmZe%2FRrQ82Fp2O4IuQRAa7OGKONit%2F1iJDhikar3mLfthFxPOF77K2EBbxhij32Ex8cRMcLUu909OB3FYMe33IHyiI99BpEziCt06gybjaJipzTMmwp1QSgOOLCU6lHZKd7k9ggLAcMUvvf9YiYYbpQ5pdP7oR0y3wL50Ozpp8rWcGTT5WpCEMVpCyuxtsB8Hrjnmaacl335Z2wcln3JdwJNxrbWUKsRzF0neAtZw5SyonS%2BCeVljb5IlOGKaeSnh8Ij3wue%2BA8PtYpv3T3rEPaxTU9b3Y3%2FAGQi4WiF99zAeD2r008lvfGHzRD2pyJ5OO%2FGEXHaFoC3%2B1enHqgvkjt1CJThWSH6t8cRcrQ274C1jCkgvktxPpUIj7U6enmt0%2BhQi5A3icb9sBavapIdi3fhWIHCkj%2BqrH7oRdbX74ha3IwFrGEJPyi%2B5b0iIjCVOTupx5XwiLsk25qiOsfdQFpVhKmHyVvD92PmiX2o0%2F8AVXfjCNw5W5B5hZt0uoV7DbVOlKRS3OhmanVJtMtKpcNuoFq2KtxsO%2BLHmXlfjXKTEhwtjaleKTqmUzLSkLC2n2VbBxtY2ULi0BrwYQp1t3XvjCIDCdKuQp2Yv2WUNou61H7qKY5wFtThGmHyn3x%2B7ER9qFK%2FviY%2BOIuoidKSSTsAkXJJsAIC0e0%2Bl8%2BmmPjCI%2B1Gl%2Fqj%2FwAcfNG33MhcfS%2BS0xnlU2JSn0JE1LsSsvNu9HNzjTq9AeabPNOr4SLkC0a37bdsBaPajTP1eY%2BMmI%2B1Gmfqz%2FxkxtvLTIjG%2BbeF8UYmwUZGbcwr0PjFLL1pyZCwVXZR74BIPdc7C5jAGZR12bZlFgMqefbl7u9QNrUsI69%2FJAJ3vyAMBYhhGljk6%2F8AGER9qNM%2FVX%2FjJjemcXDZirJXDEjjGvYjw%2FVaXP1FVMS7TJguhDiWlOFRNrFPVULjti%2F4V4Ls28T4ala%2BXqJTJmpS%2FjNOpk7OBubmWyLpIR2XBB374Dmz2o0w83Zj4wh7TqR2vTXxkxt%2FLXIfHmZ%2BKcT4MosuxJ1jCco9MT8rPKLay6hzowwkdril7AGw88eei5KY1xBlbirNyWl2pejYTdLMy3Mq0PPrQ4lD6Wk9paKhqG29xAap9qFJGwdmvjJh7UKX%2BqTXx0xldFpUtO07FNZqE0qWksNUJ2p60t6unm1Otsyst%2Bx6Rx3n3IMbUzH4Xca5Y5bjMqrYhw7UpFqYlWJpulznTqYEwBoUTaxsogGx2vAaB9p9M%2B7mvjJiYYPpA8pc18dMdB5dcJWaWY%2BEpTGUlMUekSdU1Glt1Oa6J2dSDbWhP3JPI9sYXScm8x65mQ%2FlFJ4adGK5NxxE3JurCUsIQApTql8uj0qSQrkbi0BrD2oUXscmvjpiPtPo1vt05f8Abpt%2BSN6ZpcMGYWUtBGK6w9TKtQkzCJSYn6VMB5Eo8s6UpeHNIKurq5X5xYMQZM4ww9lFhvOl5huaoGI3TLpEsSt6VcU4pDPSptsHFIUlJHvrDtgNU%2B1Cj9rs38dPzRN7UKL%2BqTnx0%2FNGz828lcbZLzdAkcbtSrT%2BIaaak03LvdIqWAWErYd7nE3Fx549WAckMTZmVTDmG8ITkp7N1vDExi2aZqDol2pWTEypuXShR3cU42npLW2uIDU3tQop5OTvx0%2FNERhCijdS5z8In5o2Ni7KjGuCsyhlLU6YJrEbplhLS8krphNCYRraLZHMEA%2BixvGb4q4Q87MF4LqmOcRU6lSkjRpNU%2FOsqqDZfbYTbVZIO6hcdUQGgvanQfu5z8In5oe1Og%2Fdzn4RPzRdpdlx99plAF3nUNAk2AKlBIv5rmNt558NWM8hqNSq3ieqUqcl6rPO05PiTqlKaeQ30nWuBsU39UBo72qUH7uc%2FCJ%2BaIe1Ch7G855%2FdU7%2FACR7nOpuOtAOQHh9qtAHNU7y%2FVE8%2FVEParQvu5346fmj2qVeL7grB2J8e4glcK4OoszVqtOEhqVl0alaQLqWexKRtdR2FxAYr7VKEeS5346fmgnB9E7VTh%2F0ifmjZOaOUuO8nJul07H1KZkpmsSypuUbbfQ6VNpd6M30k2OrsjPU8FvEOtYQnCtO1FHSaTV2Eq06dV7FV%2BXy7QHPftRov3U5%2BET80PajRfupz8In5ouDnXcF%2BpzSrVsdjYg%2FCDEuswHgOE6ICd5z8In5ok9qtDHNU5%2BET80XBS7xA6idgN4DxHCtEtfVOAf5RPzRFGFqFySucV%2FpE%2FNHrPniLagPJFoDyHCNFve87a%2FLpE8vVEvtSo3fOfhE%2FNFxCz3xEk%2B9SDt2iAtntVoyTznd%2BzpE7fJEThSjK5Gc25e6J%2BaLhqWdlDftI7ohpWO30b84DwHCNESnUTOD%2FSp%2BaIJwpSQCD42T2HpEi3yR70r8yh6YibH33ywFuGFaODsqbJ%2FyiYm9qVJP99%2FhExcOyJiW229bjiUi3OAtRwhTT5K5kelYiJwhTNtK5kWG%2FXG5jctZ4ac4sNZcTOauJMMKpdElGmX3W5t0NzQadWlCF9CetYlQ59m8ezAHC%2Fm7mbg6UxzhOSpTtKnlzDbHT1Ftp0qZcLa7oJuBqFhfnAaPGEaerql1%2FwCFQgrCNPTsHHvjCNk5rZQY4ybrNPw%2FjySl5adqUiajL%2BLvpeSWQ4WybjkdSTtGD63OVoC2e1CRO4mHfWIJwnIjnNOn4RFzus8zbTERv8MBbRhOR%2FV3PWIlOEpUjqzDnyRuHJnIPGud7tXXhkyMjTKFLuOztVqbpZlG3Uo1BnXbdZAJ8w52jWsu4X5dp9PUS4m%2Bk84C1JwpKdq3CP20VE4UkyLB5Y%2BGNl5QZX1vOPHcpl5Q6tTafPTstMTTL1Qc0NKDKdSkC25UbgADz90Y%2FinC1fwRiao4UxRSn6dV6U8WZmWdHqWk8lIUNwobGAxT2oyJFzMO%2BsRL7UpL9Xd9Yjf8pwwYtnsmpjOeSxNhyZkZSkGtPU9maKpptgXuhQtZLoAPUJ7I82UPDRjnOHD8xi6nTtKolBamvEmqjVXuiamX9robHNViQCeV9ucBov2pU%2B1ukev36h80BhGR%2FVXvWI3LUshsdUHN%2BiZJ1yUl5Ou1%2BYabkX1OXlnmV6rPpWOaLIVftFrWi54a4Xcz8TZu1vJ2Ubkpap0FszU3OTLpTKeKq2YeSsDdLxKQn4b2sYDQ7mE5Aiwde%2BMIlThGSt9ud%2BMIzPCGHJjFGNaNg1wmWeqVUTT3lmx6BKVqD6%2FPoQhxVu3TGz8veF3F%2BZ2WbmaOGMVYeVT3ZeoTsnIPTVp1UvLLWE9Kgfa1rSgkA9474DQHtRp%2F6o98YQ9qtO%2FVH%2FjCNy5NcP8AjnOySnazhxyRp1Gp6ktzFTqj3Qy4dUm4bCu1e4uByuI8OZeSOYeVeNZLAmIqU2%2FP1fQaQ5JOdK1UgtYQCyrtsshJHMQGplYTkOx94eqIjCkgP7c6fVHS%2BIOCnOWg4WncQNijVKepsqZ2coklOJcn22gkqVZHJRCQTYG5ttGA4AyVxhmTl1jDMrDKZd6Qwc2HJmXKj4xM2aDy0sot1ilm6yO4HtgNTDCsiOa3j%2B7HzRA4SkVcnHh%2B6BjbNUyYxZSMlKNnpOrlW6JXKmJCVl1KImVNq1dHMabfa1lCrG%2FKx7YtGGcCTeLpGnN0t8ms13EzGGaNKKIQ3MOqZ6R5xbqtkJb1ND935oDXntOk%2B2YX8YRH2nyA5vO%2FHEbdzmyJx5kVM0hnG6KetNaD6ZV2Rmg%2BguMqSlbZI991gR3gxmeFOCnPzFlJlKsmg06lJnwFyzFTnkMPKQRcFST5N9ucBzh7UKb92%2F8AHESe06T%2FAFd0fCIyOYZelJp2SfRpdl3nGHQCCAtCilQBGxF0ncc42zUOGjG8lkSzn0qpUpVKcpjNZVJdKrxlMo670aVWtbVcgkX5QGg%2FafIDnMOesRMnCNMT9sdfI8yhF4cBHMaYolfwwFtVhSnEWS68P3QiVGDpJR%2B3u%2BsRc9yE6%2BV49tIpk9WKlJ0WkyD89UKhMIlZSVlkFbj7qjslIHP5oCxe02TG%2FTPesRA4SkOWt71iN74z4T88sBYTnsZV7DksqRpLJmakzKziHpmRZAuVutpNwADc9wilgLhczozHwzJYvw5h2XRS6okrpzs9Nol1TyPumUqN1pPYYDRHtSkCftjvrETjB0lz6Vz4wjJcSYdr2E65PYbxJTH6dVKY8ZablXhZbLgsdJ%2BAggjYggiLXcjeAtqsKSINtbu3nESjCkiVW6Zwd%2B4i6BZO5X6IEotcn0wFsVhSR5B1z1iJfanI%2FqzvrEXIrHYdol35hRgLccJyXY656xA4RYN7OO%2BsRcApV%2BZir0qx78wFoOE5YeU64PhESHCcvyDq%2FRtF4Kyd73iGpQ5DbugLT7UmbfbVj1RD2po7HVfJF4u84sA7J9MZNl%2Fl7i%2FNHFUvgvBFMM9Vplp15DJdS2AhsXUoqUbAC%2FbAa%2FVhQDcOn1CIe1cj%2B2n1CMur1Hq%2BGqzUsMV%2BTXJ1OjzTsjPS67amX21FK0G2x3HPkYtth92qAsXtUCv7bY%2BgRKcKKTyfJi%2BqJG2o2iAJHIgwFi9q6%2F1UxH2rr%2FVY2XljlTj3OLEasJZfUcVKqpllzamS6lsJaRa6ipRAFypIHeTGKzLE1JzL0nNMrYmJZ1xh9pwaVtOoWULQodhCkkH0QGOnCiz%2FAG5MSnCjv6smL%2BbjmTEhcttc%2BqAsKsJPX%2B2p9URGEHVDqqBMXvpHL%2BWInC3LeWYCwe1GZBN3Ej0xIMHvlW7yfVGQgrJPXtDUsHyzAY%2F7TpgH7akj0QVg5Z5rTfnyi%2FnpL31kbd8CpdvLKtu%2BAx1WEXh5Oj1xTOFplPa364yPpHTttEQV9qRAY0MKzR9%2BiI%2B1Sa70xkvbuPUYivSOV%2FXeAxn2pzNt9IiReFZwXskHv3EZN0iRzJHpiYOIPJfoMBintVnv1JPriojCU4dykCMmUuw2cvcd%2FKIeMKTfSq94DGTg6aFzYc%2B6HtOnSmwQSfRGTpeWo6lKO3cYj0rhIKHV9vbAYgcHVIcmL%2Be8TJwZUVblpKfOTGYJceO%2BtYvE2tXviSfTAYccGzoO5R64nTgyc5go9cZYp%2B21hEocUr34EBjCcJTyOej1xcaXgSt1WYMrIyT8y8lOsty8ut5QTe17JBNrxd7L%2FVY3Jw1VjEFAfzfrWGqxMyFUp2VNVm5Wall6XWXETcqQpKuw2BF%2FPAaceygxrLAqew1WkpACifYeYtY8vexH6kONLJV7V63pUdIV7EP2v8WNo0%2FiC4gJlsOPZ5Y3JbPV01IC3p6m8ehWf3EFbSnPHG4Frf1xHL4kBqheT%2BNUah7WK1dCdah7Ev3A238nziJRlFjO2peGqy2LgXVSXxz5e9jbEjn5nW7iSnU%2BvcQuM6NSZiZYRPVFc%2BXBJsKPuj2gJurSm5sNzGw%2BJDGmbuT2N6FS8F8RmYdUpWIMLyOIZaYnpxLbumYUsAFASQBpSlQ7d7QHMZymxkm18O1kX%2F6qf2%2FgxJ9TLEpWpsUerlaL6k%2BxT4KfSNMbgTxCZ%2FrbS0c8MaKSlWoWqKQb%2BnReH1wXEEDf6tuNL2tfx5H0IDTqsssUNG0zRqq0dvKpj%2Fby97EzeVuLXk626DVlAjUCKY9uO8bR1Zw25hZlZtYneoOKM%2Fs13au%2FMSsvKU2gstzDiJNZCXqg%2B6tIQ2w0pSQoeV22jwZf51Z40jihwzl5UM%2Bq5iOiSmYMpSFzKXkGWqMq3NaCrTo2CgmxAPO8ByenCZI1GoIA%2FwAkYHCajsJ31skRuGv5MZ0zFerU21lRilCXqrPOgimOEWXMuKBG1rbxbBkbnaWi8MqcYFBTq1CmO2O1%2B6A1h7UEnnPb%2FwCRVEfagj%2B%2Fv9gqNny2R%2Bd7urRlHjCye32Ldufkic5JZ2gEqynxfsrSbUp0kHz7QGrvag398v8Aw6oDCKR5U%2F8A7BUbS%2BoZnYpJU3lNi9Vk6t6U6LjzbbxA5N5yLC1OZT4vAQguKKqU7ZCQLkk222gNYe1NPZPp%2FF1RXk8BVGqPCUpPTTkyUqcLMvKOOL0JF1K0pBJAG5i5MP6wlxCzZXKO8eArLlVEwfU80azh1yUxBUKl0FFqD6Slz2OSxoWpofcLcKgTbrWgPnojCJdShxqpMuNuAFK0NKKSD57RL7VVFZCZ1pSR2hpW8dKcY2WDOXeb85N4cwwqi4ZrsnKzdP8AF2VJlFTOg%2BNIbPIK12UUdmrYWjQxcXz7P%2Fe94C0oweo31zzIt%2FiVbxR9qqv78Y%2FBKi%2BLfdF0qUASoKNu6Ia%2FdF92n%2F2QYC0e1EFF%2FH2NXd0Kok9qRsoKnWEgdvRKi%2BIKyEm51AEjfnBa1rX5avVAWf2nt2%2Frijlv%2Bhl7Hs7N4j7TgP7os%2FgV%2FNF2T0p5rMVQ44VBOswFoawU%2FMOIYlptDrriglDaJdalrPcEgEmLq9lDi5lK1OUKsJ6KwcCqNMjTfce8jcvCW5MN8RWD3WVKC2hUXEqAHUUmQfIVvyIIuD2GL%2BnGWfkxw%2B0HPLC3ELjGekWHF0nFUhOTSWnpGe6TS24wog9O2QU3A6wvfvtmsrObSM4nv8mer0tW3vMWNUUTEceWuctc5RyTyubp3LeuyEqienpOal5VxQQl9%2BnvNtlR5DUpIG%2FZFt9qK%2FvhLau7Qr5o6VwXmvmRmNlPnhI43zArOIpKn4OlJlpmdeStLLvskyEuIASLKAvv540cVL%2B7itdnEUxXTOcT5Ml7C2rrqqorjKY7057GNHCM2NkzEspPaSCPzRFODpk7%2BNyxPdv80ZChLqjuoq9EAXEKPVV6bxjZ2PnBs7y6WWT6%2FmiCMGzST1piWPr%2BaMg6aYJ3dJiKnXkjZRiMxj6sKvJVcuy3pufmgcMrG63Je3fqPzRkImHNN1OEmKbzqim%2FSA%2Ba8SLF7W3CnUlyWuOYKoirDq1%2BSiXuDvZXZGSSIRMod6VRBQgFPzGPQ1JtoSbuGxPO0BiftYfvrT4upO%2FvokOHSkBawwgH7pdoyeoNLlHGUBZUh1OoXFrb2Mbhylqslg%2FKKtY0TQsHzlRcxrRaAajieRM1KU2TmGXVLcKbjSAoJUo77JMWpomudzH9ZcbFb20WFnNcxnq4vPOX4udzQe7xU%2BhcRXhaaWjWhDBT5jHS2P8ANvMnLLFk1g7GOT%2BVQmEBMxLzTOHwuWqEm4CWpmWcCrLaWncHmOR3iwZx1ORxJl5ldmCMKUGhVivy1ZaqDdGlzLS7yJeaShlZbJNlhNwTfeMs2GWf6Udv4w17K%2BVWk0xVZzETxROcTHL3pnvNCJw1MI6ol2lg8jf5Yn9qU2q2plrfu7IyHprEkm1vPEDMjscUIwN1jisNuIXo8VQTqtf0xE4We7Zdv1RkTc311dfbv5RXE6QspWkLTYn5IDFUYafJKPF07AconGGn0dQyyL%2BmMhM2VkBIKSTY%2Be0emTl5%2BpzbUlTpOYnJt9WlqXl2i44s9wSNzAYwMMPf3s36xFROFnuxhsbX8oRlEnTazP4iZwlT6POzNemZhMm1TEMq8ZL6iAEFHMHfe%2FLtjdmHsveG%2FBmN5HCOdmcqpioMLU3WJaiy6lU2Te0byzs8LgLSeZQki%2B14DmU0GYHlSyE%2BmJU0N9RP6DbMZ5jFWFZbF9dlsEVV%2Bo4cZnnk0iZmAA87Kg9QqA7bdttxYxYxOgNB1JCgv3yTse4wFhcob6NNpZtI9I%2FLEww%2FNq%2F5GjnbdQ5xf0zhVqJUDtYXEVmZwLWlAUVAqN1C3dt8MBjowxOHfxNn4ViJThmdOq0oyNIF7KEZi1TXH2VPpcUW0kJUVCwSSPliVUiehcX0x9yaUtPV52I2PwQGGnD0wmwUw1sb7qETjD5IN22L25BfbF9U4o802sLjfticOJCQCg%2FAe2Ax72vL%2B5Z%2BOIh7X3f1Jv4wjIOkK%2Bw%2FNaI9MfuBAWD2AWQQGWSe3eCMOO9LpEu1a3O4i%2Brc3U4gEAbHeJFPJSCQSSRAWsYWeKtPRscr7rHqisnCLx5IlD%2FpUxkaqeOgS6h9QJANinkIry1JVMuJZbfXdS7XCd%2FRAYscKODmiUH%2BkETIws5%2F0ID%2FACojbmQ71ARjl5GJ8Ez2J5d%2BkzbLEtJyCp5UvMHQUTC2EqSVpSAsbKFisHeOnn3OGhfu8xwn46C99hhaZSD3%2FwBs794DgZeGU6dJVI6u%2FpPmiUYWT752WHmJ5x2rmCOHR7B9VmaDw74wpK5KkTwU89huaaLTi0e5TBfLmlsNLspRUCCnbbnGmeG7JZzO%2FHYw%2FPT65ak0yVE9WJpggO9CVaUtt32ClquLnlYmA0qMKAnSlcqD3a4e1M%2Fqsn8Yx9LcdcPXC7gXL%2Bbn8W4J9jKVKKQ14%2FLzbxqTj7pCGm2jc9K6pRGlISb79l44hzvyrqeSuZFQwJO1A1GWbZZnadPFvozMybydTSlp964OshY7FJPfAawcwkptlcyy3LTSWxqcDKtSkp5lVuZA7bcotSE0tStKktaezaMplpyblJlqal5godYWFtnuI%2FKPNG1qBwv4exZQ6fileMnZA1hkThlW5S6WCsklIN9xe9oiZnVEZyn9GKd1VOUOfyilg2ShHPuh0cgT5DfqjpRXBrSVXEvjx5Z06rmUsOV994la4N6W7YDMFSFEdsioi%2FdcGGVpzZRurPnQ5w6GQ%2B4b9UTBimdqUj0COj1cGLCVaPqgJ3tYiUNt%2B%2FePOng3U5YNY8bJN7gyh2t8PbExFfNlHvlnH0oc7LYpSb3QFbdgglqj2JKLbx0Q9wbuslVsfyxAF%2F6kVHhXwiOAqSjHbKiDa3iqonc182T32y50NDFijkBXUteI%2BLUhd9LaT6o3yjg8ccHWx%2BwlXcZRUVPrOpoX0ZgSw%2Feqonc182T32y50NAGSpSuen4YeIUfvb9UdBr4Nly8uqbnczqbKstgqWt5hSQkWv%2BYxiD%2BQOEwtSZbO6gLtaxU24Ar0G1oRRactMx6FffbLPKKozawMhR%2Bru3y7oeJ0QNAKcbG%2FdG2GOGSVn7GSzfws9dClo0PK66UgFRHovv3RSd4aqQxMCVmc8cItuEBQ1TBKbHtuIqu1c1LUIatXR7eaJOhoLqrJbRbvKbRt1XCqnxnxSXzgwzMvHdKZYuPFze3VCQb84lHC06uemJAZrYZRNSbpYel3i426hwc0qQRcEdogNTeKYfTsplo%2FAYgZPDx9416o23M8K8xKiz%2BbWFUE%2BSFPLF%2Fkignhem1KCRm3g2xNiTNmw%2BSA1emTw5zKGyjUbgc7WgZXDqyCQ3cpsfTGx5rhxFOKGpvN%2FBY1qIV0U0twpAHldVPKLQ5knJt9YZpYcWg8le7AH%2BBAYg3T8PKFgWrp3SABa3bEwk6CnZxDenv0iL3M5XUiSLSX80MOtl6%2BklL4Sq2xsdFjHmcy%2FpqEkN5jUR625DXTKNuzkjaA8Qk8Pa9Ohq24vYWuO2JfE8OlbWhTVle%2FA3SRbciK68ESl%2FccZ0o27w8P5MedeFZdJ0pxXJK7NmnbD09SArLlsPKWrpnApWo9Y8jEqafhvfSpobbbWsY8pw0Vbmvyhty6jn0YlGF5gnq1RgjncNO%2FRgLg5JYbU4kBTSLHZVve2%2BeKhkcKIQhwBLgNyrSnyTFqVh6YbF11FoebonPoxRNJUklKZ1Fx3NOfNAXkU3CQsWlMuNqTcK0nf5oGl4XUptx1LKWlKsopN9Jtte3LuizIpz7artTbZI2JUys3HwCJDTnhdSn735kNr%2BaAvppeFUmxU2vksAWspNjqF%2BxQNtombpmD0qQhzogvT1tQsLxYRSpjVpSHdW%2BwaX80ehOF8QqsjxGb23CjLr7fggLn7H4ULmpzo20k6SEC%2FLmYmcp2GC5oQltISrSmwuT5%2Fgi2HC2IUDeTmh6WF%2FJtEhw3X0DenTyVdl5dY%2FNAXlumYYDYKg05zKgO7zQ8RweqVW40hsqSFKCSmxsDy9MWNFErAG9Pmr%2FddAv5oqpoNUI3lngf2TSx6toC%2B%2BxeDQodVoEgFFxsb9hiHsfhLygGSgm6dO3pjH3aLV2zvKzI8ymFWPyRIKVUwT%2Bh3kkDl0Ku70QGSN0vB%2Br3VTaQsAhQHLzRM1S8IpC%2Bk6DUm4SNV72HOMZ8Qn0pCVIdTc8y2q1%2FVEyaROLJ9xUFW2BQoE%2BjaAvyqXhZdluBlAAOsWvoP5%2ByKvsTg93VdpkWItp7RGNuUSqpNzLPau7o1fNAUiqWv4u96OjV80Bk%2FsNg4kBroyRfUCORiDlOwYgAtdGTfStFrFPn9EYwJKfUNC2nR1uqeiVa%2Fqisim1BR1paN7gWKFXPyQGRqpGCndJYUhxHvhpIJ9ETiiYNa1AhnUFbAjsPKMXXSKtrulh8E72DarfkgKTW9JBl3ibA2U0q%2Bx9HZAZN7E4OXseg8nUmyfWInFCwevpNDrR0C42tqPcIxNVNqjiRqbdtcpCyhXb57ROmkVMdQrUB%2B1Vy9UBkopGC0JWtbrbak6bXHO%2FZ8EVjQMFqUtvWypSPJUORjFF0aohIvqJPMBB%2BaJ0UCuuqC25OcUnbdLCyPTygMnXh3BASpDbralEhTayiwULct%2BRvBNEwIXkthxAOlJSOQv2i%2FZGPHD1cI0mSnCO7xdfzRTGGq%2Bq%2BinTar9zCvmgMoTSMBEKs6kqUjUUkbpVqt8O0SJpGC1KUnomwVg6CNxz2%2FnjGfa9Whf8AS6c25%2B4K%2BaILo1eUbqkJr8AoQGW%2Bw%2BBkNtKslesK1HQLJUOW3ce%2BJfYzANlFwNEpbuAn3y%2B7zCMT9hq0OUjOg%2BZlUTCkVntps5zt9oPP1QGVIpeBQkuaGgAATffftEVE03AC2ipTiEqSQCgt9nbvGLt4cxC79qoU%2Bve3VYUfzRP7VMWadYw9UbWvfxZfL1QGSmk5eIUkKWyNV7dTfzRXTQcBddCSyslN0kJuL35eqMU9qmMli3tdqZTe%2FwDUyvmiqMFYxY8rDdRR%2FoFCAzpGE8vfFm3SGVBToQoJV10oPM6e8c7eaMIxphOg0%2Bn1R%2BXeQFS8v00mpK7peKXBcEcxdBJ9IjzDD2IgRenvoBNrLaUbnuhNiYo7jPs%2FTkzLLpIVKvFSQ6O7UNwYDCaQ2HArpOtvvF5wpvXJJP8A0lofwhFeoSVIlkmfoij4k6vo%2BhdcCnWFWvpNrXHcYoYLuvEUgm17zbIt%2B7EB%2BliEIQCEIQCEIQCEIQCEIQH53OIH%2FjXx1fmcS1P%2FAM47GpXT1SfMY23xDG%2BbeOlcgcT1Q%2F8AjHo1G99pv51flgMuwqgLpJcVz1Rc73G0WrDJPsVpB98IuRc0DSYATEhN4iTeJSTADy2iKdheAPVtA7JgBXaIpcikqCYCoveIIQIgE3iqEECAl0mGkxNY90LX7InKRKB2XiYNgxDo1ROEqHZDKRFIttqtt3ROha7JBXpUkpKTyIUCCD6bgRLoUd7RG1oZSOppXEWI8V8CWZNfxTX56tVGfxg2t2anHi44QXpbv5AHsFgLxyqfLV%2B2jLpPNDG8hltP5RSVSl28K1KdFQmZXxVJdcfC0Lv0vlWu2jq8toxPol84ZSIEX5KiBQeww6JwdkRBWOaIZSIi8dfcFs5hY4PxTT8ACmy%2BdDktM%2BJOVk%2B5LlbDoQxb3t9XSAbk6b9WOQ0b8xHvpVWqVCqklXKHPvyFSpzoflJphWlxlY7Qe0HkQdiNjDKRuOsO5XyWSeMGcy5Str4ghV3lzy5xCxMCYU8kNab9Qy3QavhIt2RktfqHBsc1Mu3qDTJ4YOl5KbXiZN3S2X%2BhSJRL1%2BsSHNfSadj1Y1Hm3m3ijOfEMhijFVMpctUJGnN01Tkizo8aSgk9I6TupZJPmAsBGEWX26k%2BiGUjtXh4nZaUxLmbPYb6FjhoQXVtpxAFFhLpbTrRK69ygrC9SeQ2I60cqT72Fl5oN1HBsvMsYdViSVdo6Jr7cxLmab0k%2Bje3ba0XTGWduOMdYMwxl5VVSknh3Csk3Jy8hIN9E3NKRyffHv17nzdvPeMFZmXZablp5jT00s%2B3MN6hca21habjtF0iGUjvyRSGvCO4mQtSemfwgtLKbb6zLIv8NheNOcJ7c9KU7iHXUjMFhrCz6J4zOoIM10j3laua9O1%2B60amxPnnj%2FFWbX1bROMUnFKVsKQ5IJKW0Bpvo9OlROpKk3CgeeoxkmY3FdmbmThabwdOU2g0SQqlvZVdKlejdqFrdVw9xsL9ttrwykb1ydzaoGT3CHlfX8aUSYqNFqU1PU2aQy2lxbTiVOvNL6NXljU2EnuuD2RhXHFiJ3FOF8o8YtSa23a9RJqpNtA6l6nS2oN%2Bc3IHpMaMqeamKaxlPRMmZtmQ9gqBUX6pKPJaPjKnXdV0qVyCBrVYDv8ANF0rWcWIMTyuXUliyjykzIZbtsMU9uWSUOTTbSkq90Ubi56NsG3YDDKRj2bbckjE8xhtCQuWwpISeHEAi4UZZoF1dvulPuPE%2BeOysXrl0cc2RjiylKZjDTCLK7VKl3Qg%2BmOEZx2ZqkxOTk6VeMVB96afUOfSOrUtRH7pRjP8e53Y6zCxjh%2FHdTVK02tYWkZOQpj9PQUdH4tuh3e91kkk9m9oZSN%2FcOMrUm%2BMTNB%2BZbm0raka77IuuBQSoFz3HWTsRYdXzXtGDVxDEx4O3CJbK3ZNnG9TM9puUuDp3tOvT2XKCPPaLfivjGzexbhSdwu7K0Klrq7Pi9TqlPlOjnJpuxBBV70kEi%2FZc2tGL5T8QWNcnqdPUCgylLqNEqDwmXaVUpYPS4eAA1oB8kkJF%2B8gGGUjdOa7jrWFuEt2odIZhtVPU4h4nplDpZc3VffnbnHQNUz3w5J8RyMjH8OTCcQzNVakWJ0pT0RkHGlTKjr8oEKSE9HyJ3jgXH2cuOczcbyGPsTTbAnKS5LLpsqwjTLyaWXQ4lCE9xUkXPbFwm8%2BsYTuektxBTFNpqsRSs21OCVCVCVuhotBAF76dJN9%2BcMpF5xJNCl565t42LiVKwt7NzkqFCwVOTBEpKpv2HXMEjzojJuAptMtmxUJBuZWGkYQqKOjKjZehCLEjlcC%2B8aWrmOJ2uy%2BKJmpsaqrjOtsVWpPNAIaDbPSOBlCeY92WFehAi7ZNZuV%2FJfFc1i2gU2Unn5mlTdLUxNXCLPpAC7je6SAbdvKGUjcGCZo0ngJrtSpc3UZZt%2FHTaMRvUwEzYppmG0OEW3BDVrb8ie%2BLJnzk7lRhPLvBmaGVOJq%2FUqNi595lt2or1uLZQjXqSFboWNLiSk7XjCcnM9MZ5JzM4mgS0nU6VVEBNQpM%2BkqlpggWC7b2Vba9jtFxzi4g6nm7Q6DhpeCqPh2m0B52YlpanFWjW4nSbAgBIAvsO%2BGUjfGGcLZGZU4Uw7xS4domZ0hTWpnQ026tsrVLuXbDsy2Ocu4raw5mxihjfB%2BQ2PMA1fihxFRMzJyTq0y4pxSFoDqGkjo0TCEHYS6VhKEk7c40lVOJbG9WyclskXaDS0UZmny9NXODWqZdZad6ROxOkG9hfuiMrxM44ksk15GIodINKVS10fx5wOGYEsp3pCLX06uwHshlI077r%2FbE9H%2Bx56RzAJ7xyiQkxWc6P7omKe3KGUiXRq664nQNfufZEdP7GI9GtaF890lOq9rdm0MpHTuTTKMhuGjFGfjiFtYnx4k4bwep1RKmWDqSuZRc7FRC13%2B5aT3xzAEIaabYSorDSdN1HdR7z3mM1xxm9jvMajYbw5iiclfYvCUr4rSpSUlwy22NCUayBzVoSBfznvMYT0Z7IjIQVaAItBTaogEEROUiJVEhPdE%2BmJtEMpFIHvicKibREukxGQhECSDEYgReAJ5xMVadjEQgp3tEFJKuQMTlIaj2QuYBB7jFQN37IZSJL7bmItkA7iCkAHaJwkgchEZGbpDBNdy5x7wkTmQ2PcYzmAkSNcdqTVcdkHXZGfBd6XoitA6yxqsUE3ulBjKOOlVIRh3KOSlZh151iivGWdmLh96Q6JhLa3Ad0lSgF2PaTGj8tOILMjKqjzeGaE9Tajh%2Bdf8ado9WkxMyoeNtTiUnko2F%2FQIx7MfMfGWamKX8XY4qvjtRdQllAQnQzLspvpaaSPJSLk%2BcmJykYyVDuEUybxPYnsiGi8MpEoJEbH4e28sn836Axm%2BSMNrWsXWrTLmdsPFhMHsZK9ldlym%2B14130ZiIbStCm1t6kqBSQrkQeYhlI7bzodkn%2BJKn0nipV4llQmmOuYNMk4tqnLmwEAGZU2Lh4I6QAWsOqE7HfS7Y4Y05X5qtmanTjBFSqPtGW64sOOyR0%2BIqSLaSPL6TXY2jGqhn7jisZMLyQxLLydZkETMu%2FT6lOhS5yQaaVqDaFdv3IWdwkkb7W1ovpDy3iMh1BTE4Jp2KcqX%2BCt%2BffzGnGwnELUw64qWVJJZbLwqAV1W7Pa90na1072jxcbUrlzLZoSXtZRLM4smJZTuLGJMgyiXTp6JRHIPHr6h2pCSQCTGt8ps9sZ5N0LFVHwZKU5EzihLSfZR5q8zIaE6T0R7Um5Ok7BQB3jXbzz777szMzLszMvuKdffdUVOOuKN1KUo7kk9phkN%2B43bQ34PrLYhohLWOZ0KSSTsXnr%2FAAG9oz%2FiTmKo1xt5aNSipxCAxQBTgy6pKAguHxjownYpIsFjujnaoZnVqq5NUPJKcp8oaLQ61M1lmaBJfdU7q9zUOQSkrUQRudu6Nl4X4zcycN4dp9InsN4fr1VocqJSkV6fY%2FRUq1o0gHY6jYC5BF7bxOUje%2BA51NK4yuJOfkGW3V0%2BhoqAbSvT0rjOhwp1dhJAF%2B%2BPNXc5MDZy8NWbb2AKFMU2nUejSz82l9kMap6dKJiYTpHMpXcKX74m4jlbAGeGNMvsRYzxex4pWazjilTNMqU1UAokKeVcvJCeZTuAk7Wt3RbMF5qV7AuX2OctaRLSj8hj1uUbnZh9KulluhABLYG3WSLG%2FLnDKR5VTBpOVb8sEpCsY4jCyo%2B%2FkaY3cgdw8amB%2BDjbVNQWPB24%2FZlEWKsbsJQNz1btm4vytaNJ4krbVUksO0yVlXGZahUkSgSu3uky66t6aeFuxbi07dgQIv0rmpiCTyYqWRqqbJqo1RrrVdXNnV06VthJ6EDloK0hRPPmIjIbt4sZqdaXw9GlrnZZj2vUwyCZVxbYS%2BXZa%2BjTsVlN%2FgJjfU2oK40s2X6apIn2spZNLBasXEvkkp8%2BoWT8kcrZe8XONcB4SpOEajg6g4raw0f0imqqgqfp21kgHe4SNgdjba8YbRc8syaLmu7nbL19DuK5tbnjbjjd2JhlxISZdaP1NKUpCfuSAYZDZfDo49NcKHEQiouTC5NEjIqKX1qUPGS3qcUnVyUV6Sq3bG4ME5u4Lyi4Tsop%2FMOhuz9ArUlNsPFpkP8Ai87Kqdm5clo7qCnUABQ8lVido55zQ4ncY5nYVVgdjDVBwnQZh%2FxqflKOjSag4DcB1VhtqGogczzjDsS5m1vE%2BUGDsmKhKSqKXgt6celZxpSunmQ%2FrAS5fYaEuKAtz2J5ROUjefHS9VMbVXKJ2VlyxPYpw2p5lpStRaenZhmySrtILgufMY0ViWuy8xnEahQ5p5mRo9akKHSXJdamlIkZN1qVbSkg30qDa1HsOs98ZFiHPisY0xVl3iHFNJkWxl1RVUyVblUqInHEIPQuuJVskhaWiQLjqnvjVki89IrlZlpQcmJV1h%2FUsXC3GnUuXPpUnf0mIyH0Pp9OkXPCO4rm5oMuTUrgBmYpyFIuW3NCUKKR3hBI9CjHO%2BGMvMLZ05KY3zNq%2BbeLJrMTDcpO1PFFFm3FeKykyhxwtMqbJALakNGxAsDYWFoxHHfEPirFHEEniIwtLow7WZdEqiXldReaCG2ujcac5a23AVXHnHdGc17jBka5g%2FFlClcmaDRatjSQXJVeoSD2gPlSSnWsWBUQFLsDyJicpFDh0yOykzowjVPZtGOvbHRGH5uoGmNpEqW9d5dmXUfKmFoFwnY3HmjbSJjKLjFdkMEpxHmZM%2B0SlrmJkTUohkOvj3LpX1EdaaXYtgDmQqOe8iuJHE2QUtW5WgUCnVditTUrOaZx5aegcYbKAU6eYIIv6PPHnyZ4isUZJV3FFdpVAp9XOK32JqaRNLWgNOtvOujRp7CXVA37AIZSMEzJl8GSeNqlI5eitigyqksMitMBmdS8kWeQ4gctK7gdu0YtF2xFV53EtfqmJJ9pDcxV5%2BYn3UI8lC3XFLKR5gVWEW0NKBiBJYxeMO40xhgFdUrmBq%2FMUepzVIm6YuZYtrMu8kdIgE%2BSToT1huLbRa7RFbaJhlyVU3cPJLa7GxsoW2hkOqOPWWfm8WZXIbW5MLmcJstoQ2NTjjhfaJCe9aybD9kYzVGIcmuKTiBGBcX5O40oNdmsPFpiqzNRXKTkmiXAsjxdJsEm67LVspVhaOXcz84MZ5wv4dmsZGUbfwxIexsg9INFhQbCkkLJBJ1goSQoWsReM8XxnZ0mm9FroCq6ZEU1zEyqeDU1sDkC537Xv372hkNM4rohwximuYX8eTOijVOap6ZhJuHktPKQFfCAL%2Be8WtfIRWfOt5ThWpxS1Fa1rN1KUTdRPnJJJikoEnlDIU%2B2IpuNonAvyiVQ80MhIqCe%2BJiIAHsETlIhqgF25XiFgYaRECYOq7InC1na0QSg87RWS2bcoZCioxKDFVbZ7okDZ7onKQio2ULc0PIC06grfblEmmJkIvDKR1vKY5xljvgdzUxNjTEk3Vqo%2FiaXlETD5F0y3SSgS2kAWCR3Rqzhby2m8186aThtydnGqDSgquVlDc0422ZZlQ0oNjYdI5pB8wVGJ07N3GdIyuq2TMsqQOGK5PJqE2hUtd%2FpUltQ0uX2F2k7W74q4BzhxnljhrFOHcIOScu3jGXMpUZpTF5pDPRlAS05cFAGpR5czeGUi68Rua4zjzbrmLZJ8qo8u4KXRkjZJk5clIWB%2BzXrX6FCNWL0KNybWiokJQhDLLYQ20kIbT3JA2EQ6O%2FZzhlIpfDHspK6f7JyZq3jAp4mWvHTLAF4S%2BsdKWwdivRqt54odFBsFtzlDKR3DxEmVpOWmX0pltoluHWanJZWKJzD91TipRb6CtTpHW0FN9SvKKwQq1gIwCXb4Km%2BICfXOTjqcuThhgyYQ6%2F4uqq9KpLwC7dJ9o0qT2Fy%2FojV%2BUXEDjTJmn1ihUWUkK1QK8w6zN0aqoLsolbiClTyE9hN%2BsnyVWBNiLxq8NdGhpgKUoNIDepRPZDKRvGlPcPbeSdWdoc3Xms428QzS8HmTLongvxxIp%2FRpSNKkeLjr33uVRt3ipYYfyJwpOZ6IpjOdQbbRJ%2BxgAcWz0g6UTA5dGGySockueTsSI5myjzNrOTeOJXHlCotLqs3KsPS6WKigltPSJ09IlQ3Q4nsUO8jti1YzxjiPHmJZ7FuLao5UKtUF63nl7JQn3raE8koSNgBDKRvHhsb08P3Emwx5SsOtOpN9iejc%2BW45xLnJMLe4CcmENLcVLPTs2ZksqUG3HbP9GVhPvtfK%2Fvh3xqnBuamI8DYMx1gaiMSqpLMOnN06ovOA9LLJQVXW12XUlakm%2FLYiMsyl4lsV5RYamMDtUCjYlwy7NGelqZVmdaZOZUQVKaO%2BylAK0kbKuQRcwykdDYw6QcQ%2FCM9UnV%2BNO0ZtM0XN3Cvo7da%2B%2FPVz7bxtLAGeuEsVZ4VDKZjDL8riumzNQk6tNaBoXJSKkmWcS6N16ulFmz5F1RwlUs%2Fse1rOKjZ4VtcpPVqgTrc1ISakFMoywjV%2BhkgbhB1qurnfeJsKZ84twfnRUM86bTabM1qqrnjMyr2oS4TNW1JTbe6ClBSfNvzhlIs%2BH%2Blpz%2BP8ZpcCXMPyU7JSrifKTP1KaVKMqSexSWzMq%2BCNu8DrDEpUs2lsNaCnAL1iORCS5z89u3zRoJVZbGEXcNpZcVOTuIPZ2dmFpsHNEupplu45gLeec35KULRkuVObuI8oXsTroEjJzaMWUJ6gTqZnUOiacv7q3b36dRtfbeGUjZ5UpHg3KAhmaW2y9jZ1M6WlKAcQpahpcI7BZPyRteTQ8%2FOcEktWHVPTinpha1TJKnClEoNAJVueSfhtHOGS2f%2BLslqVN4WpMjSq5hmfcS%2B%2FRKwx0suHgkJ6VBsdKjpTcWINo8eY%2BeOYGZ2MaRjWq1JmmTeGy37Bs05vo2qboWFAt9tyUi5PMC1rQykdHZFO1JHhD8cNTk1OlAbrPjIccXp8WsyWEkHq6Bc6e7fzx4OETG8jl1kTm%2Fj2fp7s5IUbFqZl9lkArXKqQGllIOyrIXe3aBbtjAsQ8beaFbolQkJXDuHaRW6pKiSnsQSMsEzbsvpKT6FEKVvc2vtGs8K5sV7B%2BVGM8oKZJSaqRjVUsuaeVq6aXLISkhvsIWlIBvytfthlI6a4k8wsNZlcJcrinCEkJHDjONG6PSkKaDP6FlS6hLhbH2sGxsjsFo5Rxw2mnUXB%2BFENKlJimUNVVnbLIV4%2FUXTMkm24UlhMqkHmBHtnczq3P5KSeQk2ww3hpnECq25NNIPjawtRK2QT1bDUsg87kA7CLJjPECsXYureJzK%2BLoqc2XGGdrtMJSltlBttdLTbaTbtBhlI6rxZLSVUPBVSa2pU1LzymHZozKi506khs9cq3USvTcmLlWsGUHPbiuzHy5zLzUxpRq5LVRlnDVIpqlstLpQlkqdeSbhJsom4PMX3jmvH2cdWx1hPLPCS5FFLXlnTlyUnUJd4l994uJU2%2BP1MoCE7dpBMbkw3x1ViWnKXiXG2VdEr2LaNLKlJbEDDni8w42RuFggkBRF1AEjc2teGUjX%2FD7ljl3mPj2o5ZY3msVisuTbsrSn6O0hUq2xLlxL8zMqV5ABSnzbiN%2FyzmTdcpUvwUe2bNBL8lVlSym3KeEOdA0NYlnXNNjJJv0urtBG9o5dylzhq%2BUOP5vMOm0iSqE3Pyk%2FKPSswtSGgmac6RRSU7gpI280XdniPxS1n5N8QnsHImrTso5JPU8uLEuplcqmXtcdbZKAfTDKR4uIrBuXWXWNG8E4FOJ%2FHKSHmK0mttJTrXqBYelynym1oKjfkbC0apjNs38zqxnLmFP5hVyny0jMzctKyaZaXUVNttsN6E2J3JO5PpjCym8MpCLzhGv4sw1ianV3A03NyuIJZ7o6c7JtByYDzgKNLaSD1lBRTy7Ys9j3RkuXeNKzlrjOlY9w8iWVU6K8qYlRNN9I1r0KTdSe22q435wykzdTTtWf4WMsMX17M3EUzXs2c3JVaHaa%2B%2BXWJFpTSm%2BkeI6o6NLiys7BSgEDYGNb8M1ZwzQ8fYGo2ec7mAuckp6RZy%2BQpTopjTamtBJRzUhSyjdN0hPPYx567xm5rYko1SodWouEH5arSL1OmiukBa1NONqQoBSiSLBZI32MePAfFvmfgbClDwquTw%2FiZOFZdMrQJ6syWubpjSU6UpbWOYAAG9tgBDKRZuK2XxfKZ%2F4waxzOSEzWOmYX0sgCJcyqmUmWSgK3GlvSkg73B7LRqTUSN4vGKcTV%2FGmIahirFFSXUKtVXjMTkyoW1L5AAdiUgBIHYBFpKD3GIyFKF4FJvyMLHuMTlIhEbxOlF%2BcSrTpMMpM0sSkm%2FOJolPOIAExNcaim4uOy8EW7Y6hzGygy5pnBBl5mhScPtNYpqM3IuTVUStXSTHjDkwh1pQvpKU9Gi21xY98BrPKnh6xhm1gPGOP8P1KnMS%2BDUFTkrMqUHZ1QYU%2BpDRGySEJJ61gTYRm%2FAW4ZjPxEwi%2FRu4WqawLdhDW%2FqMbF4NNDXDlnkvVsyp8lQOyR7ELIJ7t%2B2Nb%2BD%2FJTndJJI54RqI%2FgsQGE5606brXEjjqkySQubqeL3JNrUbAuuuNtpJPYLqFz3Rbs9MmMQZC44RgXEVUkam%2B7Tmai3NyV%2BiWhalpUmyhcFKm1DzixjLccFK%2BMaplRTY5ksAm%2B1vGmhGa%2BEWGnPKm38pvCrSiO0HxmYtfzEcoDlsEHlvGzsI5B4rxnk5i7Oumz9PZpWD1LD8m8oiYnEtpQp7orC10hxJANtW9o2dnzk9l7hDhmymx7huiGTrdZ8U8fnA6pRnhMSi3lFYPVulaBp08gSDGW5DMgcB2cLiVglSqqVeY%2BLy4A%2BGAtXg4xbOXEP7LDifknGvnjRU1hao5i57TuDqIWW5%2FEmLqhISqphdkIWucdsVHuABPwRvfwcadWddcACt8OIG3L%2BrGecapydWgcW2E3dVknMOaAKvPNzH%2F6gMYznylrWSuYM3l9XqhKz7zMtLT0vOypPRTEu%2BjUhQBsUnZQIPdGBOEcgb2joTj7U7LcQdamDspnC9IWgcyLS7hA%2BTaMi4z8m8tctcvco8QYAw2KZN19hxE8%2Bh5S0ziBIy74WvUbdJrcVumwsbQHKtzflEdRiOwiGodwgJoRBMTjlASqVyuDfsPmimdvfbdkVSDySr0RDQPe2%2FngKduR1EQGxUAu9uUVCOZ03imQeqLAW7oCa5iEIQEiyTukk357XiYI6mkJ%2BSIuIuvSE7DshcXuDuO0QEiFJO4Gx5RMpy22nfs9EUwhSjcbejvie5TssDzWgKiFI07fLEp06t1eqJQoX74nJH3EBMVpAAKjE8lJz9SnUSNOkpibmHblDDLSnHF6dzpCdzt3RSHM9S%2B0bl4Olvt8SOF35VxbTzFLxA804g2La0UiZUlQ9BAPwQGtVYLxukhK8C4jSTyBpbw%2FkxEYExypakDAWIipJ0qHsW9se7yYyOh8RXEW9LSglc88aAvtJXZdRvclPeoGLu5nZxLPIRqzvxkEo8kiqj8yd4DBG8G42TYowTiA8%2F7mvbW5%2B97I2Rk%2FRcQ0TD2eE5VcPVOnpeyoqLCXZmXWylX6NlLoClAbkdnmjwzGevEbIM65nOzFi0C6LeyIPP0DtjLMuM0s0cc5fZ6UrGeP63XpGXy1mX2ZefmelQ26Z%2BVTrAIuDa4vftgNHS06uWSBoCitWruiquvqvfxZOrkSDzjzStLmp1sLQUqHbdQH%2FsxXOHp4JS4pDdiLi6x8EB4KpMLqhcKk9Cp1kM7HkNJF42FnXm4rOKrYTrj9G9jXMOYTp2GFth3pOnVKBQL4I5BevZJ3FowuRw7WqrXJTDdIpUzUKxUHkS0nJSqOkdmHV%2BSlIHPz9w3i95hZUZjZUT0lTsxsJzlEeqLRdlFPWU0%2BEmywhxJKSpJ8pN7i8BYW67o0BcqT50m%2Fwx6Wq3LgrKmrqKSAD3xRGH59SAsNtkH9mIkcoNTb1Xl0nSkrNlDkBeA2Rktmvl%2Flu81NYoy6qlVq9NqzFZplao1ZVIzbQa0kyTw8lyWWpN1C1zyi55VYnXj7i7wVi%2BbpkjTncQY%2FlqkuUlUaWGCt1ThQgdgH5bmNXYTwjiXHdfksK4QoU1V61UFFMtJSqNTjlhc%2BgAbknaNh8M0s%2FJcUmV8jOMqQ7K4vZYfZWLFLjfSBSCO8KSQfRAYjU8wMbezdQdYzCxahs1GbDJRXJoXSJhzSlIC9u60SjG%2BbKhqTjbG5HZ%2BnE5b%2BPGY5B4apdbxTiSr1CVbmFUqbdMshxOpLS3H3jq85AG0bMruc2XmE6pMUKtThE9JlAeZalivoiQFAEgdoINo4l6xa0srzN2sLLdzGt9KwXQa5XvCLPF8TvcWNFpMxTxROqZjjmZjjnKeLvOf%2FAG45q30nGeOLjcAVicP8uDWL80GipTeMMcJKjqVprM6LnvPXjdx4jsm0J0uVd5tV72MmsfmiqniOyZukDEotuFHxR3YfFjD3TxHku3b%2BTdjQ7RaP71jop9ppA4yzWUgXxrjooSdQBrc3YH40RRjrNZtC7Y5xtof2cCq1NkOAdhGqxEbqTxD5Rq64rGmwIAEsvf5IrDiFygcBKa6nSOeuUWCfR1Yd1MQ5bv2%2FkcDdF51YtT9n2nOTklOzCFIVIvISsEdVojbzR0llFxXZgS9WpuGc0syZrDuFKZSnGJabkMPtzL6VstWl2VJtcpNrX77X53iT6veTzhSBiBtSe0iUXt%2FBisrOLKpbYmGquFpPJSJVSvyDaHdS%2FwDi09P5Ip0L0YnVi9PRT7TV2Ymf%2Bceb1Ck6Fj%2BreOyUtNmoy7LVNTLFDxQUBR03sdB3T5%2FNGuFy04s6HJR6%2Brqjoz2b3jpNGc%2BVGopFZOxv%2FUS%2Fox6F5w5YNCwq6V28oeKqunuvtDupf%2FFp7diY0L0ZmM%2B69PRT7TmTxKaQdLko6Bq5FBHywVKzQvpkZhVh2NqjpJWe2VjYWgTDikdpEoqw9O0RPEDlO2SRVEI65O8osdm1rJh3Uv8A4tPT%2BSJ0J0anVi9PRT7Tm4NPIICpV8kCws2dz6oriTm%2BkIclXUKTa92lXF%2FgjpjDPEZkxTMT0SpzdQQ9LyU8w%2B8kyKjZAV1jYpsduyN2r4yOG7pVhiaD6EkkOJpAsb%2FuI7eFTb36iqq3pizmJ1TOt8%2F0tulw0fvNFhh9vvmmqM5mnVE56uKZ8759rlJgH7W4r%2FRqv%2BSHikwOUs6bdzZMd%2BO8ZfDanV0jiE6ueukgX%2FgRFjjH4Yio2qEq2VDcmljf%2BBHWjD651VR0vITjER%2B6q7djkbh%2FxZRMDZvYfxJimadp9JaTOykzN9AtYl%2Bnk3mUrUALlIUtN7dhjL8OhFDk8FSp4n8EzMngNpwUamTNAm3JRLqtYU6630Wl1yyjZatxtHSSOLvhovduoyN%2B8UtP0IqDi74avfVKU%2BCkJP8AIjasblXZU64n0uZfb3F7qirKaeLLVn5p1cUxnLnfG%2BM6EcNZjVGp5m4VxLWMW4WlMNSEnhuiPSYDiKgiZDriS2lBAAXdXPkOyNALYevboFpPnB2%2BCPoP9d1w1oQA3VZIauaPYlI9Y0R518WfDEgdKqoU%2FV%2F2SL%2FxIW90qvGXHEZeVfD73TcLOaIpqn%2BvM4AWxNNaSWFgHfyTyiRaHz9raWod1j80d9ucX3DBfQ5OyZ7bGkAj%2BJEBxg8LjYOmo05JFyAKOkXIF%2FuI1pw2rnR0t%2FuzHg57djgItLHNoj4DEdKejvpV6jHfI4wOFd1Q1zVPuRzVRU7bftIl%2Bu94XCi6XaedrafYZA%2FkRMYbVzo6TuzHg57djgLQhKwFEb7lPK%2Foig6W294%2Bj83R8kuJPAk9KUuk09yXLTiJSdk5VDMzJP21IcQoAbg80m4IuDHzYrPSSL8xJOrClyrzkupQ5KUhakEj06YwXi6V3emKs84lu3O%2F03uZoiMqo5JVGqm1JKcKwTr2snsiKcSMpGhbKiRy88YJP1mZXMKDCylsHSD%2BUx41VObV5T6t%2B7aNRutkTuJG5xLCSlSSy2UXV27xtfK9M3ibJOvYbochSavUWseUStvUifnUS6JqSl2HdYUVkXQVEINt7KJjl8VKYHJ5fridU24tN1G%2FpjJZVxRXuqozjj7YyYLzZVW1nuaZyni7Jz8nrduuS2YlerlUxDmfkdhTF63NDVElvbY1KytFkUg2kpdtC%2FI1aTq53HKNa50tTmFcIZY4Lq7UtLVajyFccm6exNomUyiX58uMJ6RJIUOjIAJ36u8c1iZcHWBtaBqMyPJdUI2K7xTVTMRHHPLxeTY0rG4Wlna01TVG5p5IictUxy1TEa89XGzh2oXcsoEbX2iAnTsQ2r1X9UYMapPD%2FlCogKpPi1ppYty3jTdRm%2FsmluJ%2FZJpzmT6owX2Tnf74V6hExq0%2Bec0564DOPH1e85Rsrh%2BzweyLzHZx8ihIq7TUk%2FJvy5UG3UodAHSMrOyHAUix7iY589lJ7%2B%2BnfXFT2antOlU0sjzwHXtd44cZTePKjjbCmB8IUd2dOnp5imB6oON20kOTIINym4JTY2MZGxjxjNbCKK9krkzlecQSKCnEeD5ukJXN3G6Z2RWXE%2BMMqvZSPLQoHmN44e9lplX%2FAChXqidFWm0uIdbmltuNm6FoUUrSfMobj4IDt6vY4zW4c5zCuMMwMisqkN1fplyCZWlAPILbaSttR1qDagHU3Ckna4jm3F%2BL5fF2JajiRuh0ujGfdLxkaUwWZVpXI9Gi5CQbXsNr35RieIs1MwsX02QpGKsaVSrSdKuJJqbe6QMXSEnSSL3KUpBJJOwjHU1ObSrqzCvXAZp4%2BnlYx6G6kylSUpTukbAdpjBDVZ3%2B%2BVeoRKqpz55TK4DZ6cTtts%2BL9EsIJuTq29URGKpXoH5cpWFOsFsHs1Ej5LRq72Vnz1TMr2iIqk6P%2BUE%2BkQGyGplC21WOrqiIdIs8jGP4dqnjyVsPAB1sXKhyWn8xi%2FDblATXVC6hziS6u2FzeAmKtW2%2B8RShu%2BlajEgB8pKt4K1DcmAvzValkpQgNqKgkAg8riPTT6wxJPszDaFFSVDUDYXB5%2FDFiRJTZQFiWWUnuBibxadSrQZRwHu0GA27w4oxw7jeqpwJXqRTpv2BmhOJqMk5NJm5QuNBbSGmiHFL1FCroNwEKPK8dwikcaPWP1bMrz6KLMncD9v3x8%2BcnssKvm1iSbo9HrTFMmaZTXqoHVpdK1JQtCClsNdcq90BNvehRPKOhTwBZp%2Fa05p0dXompsen0wGw84JXillcI1d3FGZmAKkJfDlZmj4pSJtvVKBhKZpgOai2h1xtQCA4N7HTuDHPfCLmjg3LjG1Wo%2BPnRLYcxrRxQ5qaUpSEyq9RLZWpPWQhWtaCsbpJSYvWOeDDM3BOG6jXJzManzjdPpc7VXpdD030bzMshKltlZ9zC1JV1UrtqsbRobDeGMT42qyKBhHD07WJ95J0Sso0Vq09pVbYDznaA%2Bh%2BFspZ3DNep1bzCzclcT4EwMlTuB26g%2BguS6lg%2B7zrt9L7jKToaXv1d%2Bccc8VubFFzazdnq5h90TFIp0szSqfM2I8ZQ3cresd7KWpVvMBGtsXYYxVgSrvYHxjT5%2Blz1O0Kdpkw8opYK0hSSE3KRdJB2iwr5iAjfc2jrnLOxy8wvqUqyaUzbbmbnmfRHIaP7bsY7MytSy3lnhhSwCPYtu%2FrMWs5ytIjyT%2BClvH6ifPH4s7YkwmVYUkABSNNyB8ESlky7tmwUhIBCuxRHZFfD802%2FLISW9TWi6UrT1lHkdoqvkM%2B4rOlTt1eYW3A%2FwDfnjecmZmJyl4XHC2tJXbR5PnvbaKLziDPJU37kjSNPIX9NovMtQKhW2mZWWbQxOOLSGw44OjJPaVHlGJ428RwlV36bV8X0mZ8USyooknelDgcB1WIFlFJFlC%2B1xzvF6YmdUKzVGWcvbUpsJDmh1OpQCdtjYx51qlnG1qKx0mnqqB527Phi0oxBgCZk5ibRjqRS9KtBaZebbcaU%2BQkkpbJFib7AEi948%2BK5Kp4RnNE09JTctNstzUvOSMyl%2BWdbXewC07BQsbg%2Bbvhlx5StTxxnC9s1GXbaU7MpBCUHUb733F4x%2Bq46kqc2FIQU6lXSsCxta1x64xJ%2FETrhJcXtpBJBt%2F7O8YjOVt6Ylgw4oOdRWkkDl2GLfBZMs3szCxhMVaVcaamlqZ0gqSnfSmx%2FJ%2BeNW0apOstJCngS3yFuW%2FdGYT62%2FFXX3mV9C2ytTgSACs2Nrenb1RruWQphtAJ1Ha9opa1zMxMs13piIlg2YdRmG8Vz6JV9baXEJBCDpACgLgAcgSN%2B%2BPDWVNKYpuhCU3p7IVYWuRfeKWOHekxVOq7m0Qr6S37GpsQDT5cje%2FNN40J%2BFLoU%2FBh7KBP1WmzLb1Lq07JutkFtyXmFtrQRyKVA3HKI4pxBX56bXVZ2uVCYqEw4px%2BcdmVqedWbXUtZN1E95jz0pYumPPXvJHpiskrQudnphzU%2FPTLh71vKP54qJW8E2Ey%2BB5nVfPHiBsbxVDhiEPT0zqN0zLoPeHFX%2FLE4qc6OU7M27ulVb8seLpYgFEwGbVLMTFs5gSjYGqVXMxRKfVZmpyDS0guSz7iAl0Jc8rQrY6L2vvGTYVzDxdgmULuCscv00VFlsziWJdtWtSSSEq6RKvJN7Ed8atqc%2BqWoMkyiXZUpxx8dIsFSgLjyd7CPZKTR9j2HP8AFiA2pM8RmcoJJzNqNyq5tKSm5%2FBR5HOJLOZwFK8zKmQbcpWVHLlyajVr00lwm8UtY74DaP1xOcdrfVLq1vM2wP8A8cehHExng2epmvXU7WsnoRt3fa41J0h74h0vnEBt9zibzsfJU%2FmrXVk2vcMHzfqcUjxE5sEHVmVWusNJ6rHL8HGpel84h0nnEBt1jiLzPbBvmbW0352Swf8A8cVHOJHM9xOheaFcI7uhl%2F8A0o02VX5mGvzQG4VcRWZ6zdWZ9eJ5Xsx%2F6cRHERmmQkHNTEICeVy1t%2Fs41Br80NfmgNupz%2FzLW2GnM2K%2BEg6rXbO%2FxIl%2BrxmGUlCs18RKSTe2tv6Eal1GJ0C45QG1xnnj1wWXmdiIj%2FKNj%2BRA545gAaRmbiEJ%2FwAo0f5Eaq0nuMNJgNqLzxx%2B79szTxCr0rb%2BhEVZ4Y9WNK80a%2BR%2B2a%2BhGqTyikecBtpedWMHE6HMx8QKHO3SNfQiCs7cZLtqzFxGbCw90Z%2BhGphtFQLIgNsDO3GjvlZjYnNuV3Wjb%2BBE72c%2BNCSXcycRkjY3cauPT1I1Q1rU27ZZHuao7D4%2FaDh%2BlN5NzFJoUlTpmay4ppmlS0ulovKF%2BsvSBqV5zvAaR%2BrLidSQ05mXX1JG4Gtof%2FjiovOjEyrasxsSKty92a%2F9ONTQgNsuZyYictfMbFJtyu60f5EU3836%2FMqK38ycTqURYkuN3t3eTGqoQG1mc2600kIbzOxOhKfJGpsgfwYi9mhUn7l3NHEirkki6ALn9zGqIiEkm0Bs04%2Fv1VZm4jKf2yb%2FAMWIuZhFy6fqoYqsRY2dt%2BQRrQMExIttSTAbLGNJc315m4pOrn7uREpxTSleVmVifbYfog3tGsokgNoDEOGCgh%2FMfE9%2B7pVbjt3ERTV8DL0hzMrEgvzOpZt8F41fY84DnAbaFQwSUEpzXrmrsBW4PzRGWncHPoUXc3KvLqHIOPu7%2BoRqkbWioHOyA2ixU8OOLsjOGrtJ%2B7M28kfIIr%2BOYevoVnHV1Jva6ag8R6do1SHNoqNG6rwG0xM0BwWVnJWQO4zz20VZX2nreHsrmXWJpjkS1Pu3t8MawSkEbx7m0o6NPVgOll4L4W0Ybl6xReIDFkxOqCQ9IuyrqHGVEHcE3BAO1%2FPGma9MNCuNYXYrr2I6PVXkS7Tk01pfl3lnShQUN7hRG%2FaLxQoqUGmKsOtqi3tp14ww4gKAJqspuez3dEBZH5SZp0zP0ucRpmJJ9yWeT3ONrKFfKDEcCke2amj%2FAKax%2FvBGYYqpFKqOOsRSFIrEmqbmqvOqbbU8N1eMOHQSeVvljEsGSr8pjmnScw2EON1OXQtINwD0ggP0qwhCAQhCAQhCAQhCAQhCA%2FO%2FxIJtm9jtvuxPVPkm3o1C7vLI9JVG4eJQWzkx%2BTtbFFV%2BWcfjTzn9SJV51D8kBleGP62X84i5LTeLdhb%2BtHn1D88XMjtgKRMQJifRckRDRsSdoCQmCvJgeyB5bwEsRTEQREwIgIx0Nw5cNVJzQw%2B9jfHM%2FOsUhU0uVkZWSIS7MqbI6RalHyUAkAW3JBjnpJF4714fpgSfCVKVJN21ylOrLgKTY60hxQI897R4P3QsTvuGYZZ7xq3NVpaRRMxriMpmcvLxZeZ0sLsqLS2mq0jOKYmXi%2BtW4dLaennQq9lA1YXSfOLRFPCjw%2BFKk%2BNTh021H2VFxfl2RyNgNjDmJsL16dq9dZoCJqjSGHi7NMTEy89UdQmXZtsovpVpbCTfc6ztGTz9CwRVpmtopuYqEeyjtLWjoqTOLEqmURpIT3F09ZV%2B2OXVojikTlGI2s%2BXKZ738Xl7G13UqmndbijzZU5%2Bp0r9aXkKFlXTT%2Bo8h7KC48%2FKJvrTciQOdS09p9k9vyRytibBeE6xiOpVxebtWaXUZxyaLMnSZxDbWsk6EDsAvaLYxgLChfU4vO%2BsM6VdVl6Sm%2BsDtfc7RSdEcW4v2ja5%2FwAtX4VppxKqdVNn0Rsdeq4SciiSgsVMKA31VT%2BaIJ4TsgkarInTY2N6qDY9g5Ry7PYaoVaQzLzWes0CzTGKWgN0%2BaSVobOrXsrdw2sSecY3OY7WmfnKmMxa61NzVYVVFFulFPu5b6MHSF206fe8h2RXgdi0xlOJW3Vq9onEa4yzs7P7Ox2MnhMyHWdkTyinb%2BuosB6omHCVkSpVxLzyyq9rVX8m0cOs1unssGUZzIxQ2yqTXIqSZNZuytzpFJ8vtXvfn2XtE0xW5dxtx45h4neU4ppR%2FQriOs2NKCLL2sNtufbGSNC8TmOPErboq9o7pTyWdHZsdwjhNyHUQoS9RsnuqZt%2BSH1pmQgFuinyBzBqpHy2jlScwjhmWc6CU4iaw8lKha0nOIuDuokX23748ruE8EJfcQjPfELzZIHSJp831u82Kh27Rj4GYpq7pW3RV7SaMRrmeKiz7NjrZHCdkPYapecIT7%2F2SJsPVvFX61PI8XSJeeuoaripAbebblHIklQsISsu4j6ttcJK%2FJ9jpvcfH2iVzDWA1lXSZ2Ylm3L6WG0SM5dV%2BzyojgdilOvEbbq1e0tGI15%2FAs46NjrtPCfkh5Wmo2PIeyIUPyRBzhSyLTcLRUEn%2FtED80ciHBOGdaVDNnF0oBsSaXO7H40UXsI4UCSqZzkxKlalhJDlNnBcdpJKvki3A7E514lbdWr2yrEauZZ9mx1%2BOFPIj7mdPpqY%2BaJvrU8hAftc3%2FrMfNHI6cv8BLVdOd1bVYXKUyUyFkDc6QV7m3Id9o1%2FfD7rjyl45xa22l1YZQqWd1KRfqlXulgbcwImNDsUjXiVt1avbRViNcxutzZz0Z%2Bp32jhPyHvdTc%2BR3Cpp%2BaIjhSyEPNidH%2Fef80cDJbpCgCnMLFyRY7dC7e3x%2BUS6KWlAUnHWL3D2gocH8uE6G4rOrEbXoq9spxKuri3FHZsd%2BfWo5DLQG25Wd1A6rip7n03ETfWn5Fncs1E3FkkVTl8Fo5AVl%2FgNhanZbPfELnuadK002YSpSikXT5fYbi%2FbaJGMAYBcm22Hc9MUNtCwMwafMlKdrmw1357QnQ%2FFY4oxG16KvaTGIzMfAs%2BzY69%2BtJyL1agqp21cvZTYeblE44S8iDsE1In%2FtYfNHH3tGwAhs6M6MYDVzCqe%2BLkcibLio3hLLJps%2F8AxXxg4%2FezYZk37rWTtp68RwRxb%2FELWfRPtI39x5TTR%2FXodcO8KeQbR3E%2Fcbf13G3yQ%2BtWyAHWL036PZZPzRx%2FN5d4YQ44qax5jqWUTcodpT%2Bq%2FnGrzx43sAYIbPSO5k4wbR925S3U%2FlXFo0RxSYz7oWvRPtJm%2FwBcRqs%2BzY7NXwsZABPWTNgHt9luXyRSHCxw9DcmdPprH80cgy2BstnBZecWKloI3R4qtJJ7RuuMMUjBpmXUpxPjZKAs6UlA1aAe33S17WiOB%2BKT%2FeNt0Ve0nftVUarL7Ox3mnhV4ekr1LROfuqv%2FNEVcKvD6o3SueHmFY%2Fmjg4y%2BC1%2BXirHCf8ARg%2F%2FAJIlclcKNgdBijGbhCha4CRa%2B%2F8AbO6IjQ%2FFNfdG16KvbV35aRyWX2djvU8KeQKrAqnj%2FwB7%2FwA0PrT8gbFQE9Ycz7LfzRx8%2FgPLBqacQ1nJjB1tJslYk1hSh3213EQfwrlvLgy8pmhjlxpQu5%2Bh1BK%2FNYr2hGh%2BJxHzhbdFXtIi%2FVTq967PZdg%2FWpcPw%2Fv3%2FW%2F80Bwq8P8AYAOTqhe%2F9dgbesRxsnCeWi9l5g42t3dAb%2Fx49MthPLJ0Bo4oxqonZAQ0palnuAC4cEcVjji%2F23b7bLF8r5feuz2XYI4WeHobnxk2v%2FdYW9VokHCvw9fdTH%2BtR80cguZdYHaKhNV%2FMBgDmkySxb09baPK9gfLhlelzFWPGU%2FduSygn%2BPDgpifLf7bon2078q79l2ey7L%2BtV4fbgpM2O%2B1UTv8kPrWOH4C2qa35n2WTt6No47ksEZYzT7TSsxcYlZP2pKDqI5mx12vaMGc9rKnXVsVbGIb1q6NBmElSUX2uQu17c4mnRDE6tWIW3RPtsU3yqeOn3qej2Xfh4V8gCb9NOn%2FAL1SfzQPCpkC4U2fnkgcwKmnf5I4GDVA7KxjD8ZT9OJVS1Mseiq2LFHsKpxKf5UXjQ7Ff8RteifbV7o2lOuLPs2O%2B1cKXD9uBNTwJ76sj5ol%2BtP4etkLmJ5RUrVc1RNx6LDeOPl4QymZmFtv5hY7WQqxIl7KHft0l9opnCeVgQlaMa49U4OYLYFh6dcY%2BCWKZ5Tf7bon2mSb7VPguiPZdinhR4ee2cnB%2FwB6J%2BaJVcK3DnyXPzXw1ZI%2FII5A9r%2BUDexruNFjV5Sxc%2Bk9eKXtTyjWoqXifHKAewNjb%2BFFqdFMUj69bf1%2FvU37V%2Fl9Eey6%2FwDrYOGxlQK6pNptzCquiyvkiwY24OMCzeG5uo5bV2eRUGGFzEul90TDExpBPR3SLgq5AxyBmFgSh0fC9PxnhGdxBO0mZqj1GmXqj7mG5pDKHkoTZRvdtd7%2BaO6eBxl57ICQcmHFuLIqLiFLUTZKXgEgX7t452L3bFtGrGi%2BWV9rqndRGVUcXL35nvZelmsa6bzXNFpRTMRGecR5vJDhEkknUgpPIpPYRsR64zHKTLapZr46kcFU%2BZRKJmEuTE3NKSVCXlmxda7dp5ADtJEYpNEKn5kpG3jL1vwio6D4HWw5nJNpPL2vzZ%2BHUi0fQ9JL%2Fb4dhNtertxVxTxeSZ5fQ49ysabW8U0VccZtsI4S8gaQluVq1YqypgoTdcxUW2isjtCbbAxOnhZ4cFWSxW5zpEnUdFWQTf1RoXi6oRxvxMy%2BHpqsKpso1hxiZemwhbiJVltpxxayhO%2FMgbDtEazTlFg1CQ4jOlSnDa4Zp8xcgx4XDMBxbE7nZXyvELWJriJyiJnLPzTDo219qsrSaaaKIjyxGfqdmo4TOH5%2Frs1OfUPfD2VRufRaJxwhZDqXqE3UyO5NTT80cdS2XeA6cXUzOak1MLPk2kZpHyCKczgnCL8y0iSzsnJJtSSOtLzY63muY3OCOK1TlGIW3RPtKxf55Ys%2Bj%2Fq7K%2Bs%2FyM1aBMVNSj2CpJv%2BSIHg8yQbGtblVA71VJPzRx0zl3ROlB%2BuJnRbktTU1t8N4x%2FFNIp%2BHqu7SF5wYhnC0G1KeEtMltZUAq6Tr3ABEROh2MZ%2FOVr1Z9pWcSmmfgUdEbHc31oOSHLp6p%2FrJHzRH6z%2FACQVYB6qXAttUk%2BvlHAiFU1SrnNXER84l5q%2F8aKnTSbKitnNfEwNuYYmhf8AhwjQ%2FGI1Yla9WfaO6s%2BDo6I2O9hwg5FeT45Ub93skn5oing8ySCuq9VVgb2FQR80cY0HCMlWKRL1dzP%2BoyXTqcSZd1qb1o0qtc7nnzi5u4Hool2i5xLz%2BtYUVt9FO2Rblv23iJ0PxmOOMRteidpTiVcz8Cz7PZdd%2FWeZKK5P1gHzT6bfkiKeDzJU2%2FRVZT5%2FHUD80ccpwdSgk6uJGd1HyUhqcv6TvtFeXwxRZWyF8Q0%2B8Cd3Utzlkdw5%2FPEVaJY1lnGI2nRO1kjEauWiz7Njr5XB3kyqyUztabRzP6YN7%2FJD6zrJZFv0dWN%2BRNQRy9AEceTmHKHMPdK3n1VgSOsoSs8oHuIN4pnCtPbASOIGrNA8wqUnt%2FWYinRDGp14ladE7ScQ71NHZsdkjg8yVGxn6yRe9jUEfRiVXB5kmo2TO1dJ%2FwC0W%2FmjjtvBMg4f%2FqJqABTcFSJsb9x3jGsTSTFDrCqdI5z4mqLbLaQ5MMy8yEKc98EEq6yRtv2xbgjjOfzladE7UTiVUfu6OzY7qb4OMlbKSuerTnmFRbv%2BSB4N8lioETtZCe1Psgj5o4F8aJSEHNnFtkiwuxM8r3%2B7iCX7882MWfA1MfTi3BDGf8StOidqO6WeuijojY77PB3kqk7zdbSO8T6DcfCImPBvkopWozlc9HsigD8kcXUbB7VRo7FUcz3rMo46VWlphuZDiAFWuetaxG8VnsFU9JIXxD1S%2B4sluaNtufOJ4JYzH942nRO1HdH%2BCjs2OyxwcZMpIKahW9hYA1FB%2FkxBHBxkxqK11CtqJ5k1Bvf5I41bwfTeY4iqqNPk3amrennFzZwphZCOgmuIWpzKRycDM0oX7QBcH4YpVorjUf3hadWdrJTf4n6NHZsdc%2FWaZK21eP1m3%2FaDfzRD6zXJQc5%2Bsf6wR80cb1HDVEUvXL54V5tBHW0yc7pv5jePIMMU0glWfdfS3cJBclJy3ymLU6KY1MfOVp1Z2pnEIj6NHRHsu1E8HGSQAJnquUnkfZBFvXaJzwfZIK5v1g%2Fv9HzRxo1gCRes0viDqDY033TM6R5vKiw1yn0%2BhVNVMGdmJ3yykB15ErNFsr%2FYEK6ybdsTwTxjlxK06s7VJxKeSijs9l3OOD3I4EnxyspB%2FwCnoNvkiX6zzJIddM9WAOd%2FH2%2FXyjgkuSKuoc4cVGyT%2FwAkmrejyoh0Uhayc2MTJFrWEpM%2FSieCWMxqxK06s7VJxOqP3dHRHsu%2BU8HuSSSf0dWl3629RRy%2BAREcHmSSiLT9YJOwAnkb%2FJHFMhgpM1ISNTRnpVGROM6y26iaS4wQpSdKxf8AY32uLERV9qDcr0bo4gqmlSFdUNImlFJ7xvtEcE8ZiePErXonaTiVWqKKOiPZdnDg3yXAJRUK3a%2F9%2FoNvkiccHGSWkdJP1km5ufH0D80cWnCzCSplPEFVSknsbmwk%2BnrR6pbDOH0N6ZrO%2BpuKv1z0U2bk8yOvvETonjOvuja9Wdq9OI9%2Bijs2Ox0cHuSA8qo1hX7%2FAEfNEFcH2RtwDPVf4agj5o4umcL0N1YVKZz1dtlSQQoS05cnt99HmdwjT0nWrO2qDSOZYnNj3bmEaI4zV%2FeVp1Z9onEO9TR0R7Lto8IGQ6hZM5VAQD%2FdJO%2FyQRwe5FFshudqp33UKig%2Fmji1GX1MW0p5Oe86hSU3Nm5nUT2jyuXni0Ygo8hhmqzlGGdGIXDKJRdcvKzWhxakarDrcrEb9sTwOxf%2FABK06s%2B0d0auSijs2O6U8HeRqDdVUrB57GoI7fggeEHIspBTVartskCoN7%2BnaOAlMMO3K82cSOAqBJVLTO57%2BcRVJyACQvNetqCd0hcvM7b9l1bRkp0QxXlxK06s%2B0pOI18yz7NjvtXCDkOVDXU6wO79MW%2BfedomVwiZDhHXqdV6wsVGoo38%2FKOJJLAVOn6XL1E56TEsZllTipd5maS8yrURoWL2uQAoWuLERM7gKlaENu58uPJSnZK2prbzc4Toliv%2BI2vVn2le6NXMs%2BzY7S%2BtJ4ez%2FdieH7WqN%2FNEquEnh4Bv7Oz4199Ub%2BTaOMpXAWB5U9GvNMuq8pShLTIsfXHmmct8JPuLXL5uBpBtZIlpi35YinRTFJnKcQteifaWm%2FVZZ7mz6I2O0vrVuGsEpcxJNIUb9X2WbB257ERI9wf5HVWUdThzENX6Y6kofanW30tLA2Kkgb%2Bi4jh%2BvZUSkvhmtYnoeO0Vp2gMMTkzLIbeQ6Zd14MlxJPYlSk6vMoRvvwcyJteLMa2mXVMNS0k50ZcJSFqeKSqx7SLi8c7GMIxPBrjaX2jELSaqOPKfPEcsz3%2B8y3e23xa00V0U5T3o%2FJqLH2CarlzjSq4JrLrbszSnuiLzYIQ8ggKQ4kHsUkgxZpOTmqhOS9PkmS7MTbyJdlA984tQSkfCSI3LxkNpRxD4haQkAMy0g3cdtmSBf4LRgmVyG%2FqmYL6RN0e2Kn6h3%2B7Jj3t1xK3nBKL9ax%2Bs97iqe9utznPa5sWVM3r3vkzdTUPgwyxw%2FRWzmNiWpTFQshM281MolpVp3mW0XF1AHa552j0fWscMq%2BqnGs4m%2B%2F9eWvVFm8I7NPs5d0CRZ6RSpzEK09Ggn3RYlyUpsOfWUI5PqeSuF6TUXKfOZsyPjMqstTAEm%2F7m4B1k%2BkHY3j53o7ccY0huUX%2B2v1pE1TPFEcXFPk1eZ1b1a0WVrNFnRTER38tjtE8KXDi6rpEYonXArtRV27GA4R%2BHi4%2FTypKPb%2BmyN%2Fkji6Uy7wFJrAnczHn2ignSzITI0r7OX5YnmMG4Heb1SuY83Jrvq1uS80B3bnsjsVaMYrHwb%2Fa9H%2FZii9%2F6fR%2BTtJPCXw7C9qzP7i39dG%2FmgrhC4fFarVqpjfsqrY%2FNHFasssKaSUZzqWQLgCWmN%2BXn9MRreX2FaHS5KoO5vVWb8cmHG%2F0JJPuJZS2gElfWFlFSkhI7Rc9kVnRjF44%2B6Nr1Z2om%2BTzaOzY7S%2BtI4f0o1JrNUCgb2NTRt5uUVBwjZBLF01Wpkm6ikVRu437NuUcGIpGHFBYVmFXlaiD%2FULxuRyJ68QRRcOhQWMxMRIUAU3TJPg2PMeXyhToxi88fdG16s7Ub%2Bnloo6I2O9Bwi5BE9atVJSewJqrX5hA8IGQgNk1ep3%2FAO1EGOH6FgjCdUM4k5s1WnGWCCC%2FJPpDuo26pCuznvFz%2BpjhBpp113PCdC0pBaDcpMKDh7RcK2%2BGLcGMXq%2FvG16s7UxfJmPg2fZsdnp4QcidNjU6obHdXskj5og5wg5EK0%2Fp7VE276k1v6do4tVgPCKFLQjOytlCiL2k5gah5%2BtFeSwbl6w%2B8JnNmrTiU%2Fa0uyUyjVbtHW5xWdF8XjjjELXqztTF7mqctzZ9mx2WrhAyFbCWxWasrtJFSb%2BaH1oOQh51urcrb1Nvn6o47nMC4FnADSMw6%2BQj7YtmnTSgD9zfUR3R5k5c0FaRbMnFOq1yPYqb2HeetCNGcWnjnELWP9v5q1XnLko%2Fr0O0jwj5DBtbZrVUAVz%2FAEzb%2BaJfrRchVGyqrVFeiptj80cWuZf4OddUH84awOsEnpZGYSrlsSCuPNifBWEMOykk7J5n4lqT8666FliUdDbSEJFrqLm6iTy7BExoxi8%2F3ja9WdpF7nkps%2BzY7cXwhZCKSm9Rqw073FUbH5oHhEyHUkAVSq7doqbe%2FwAkcA%2Bx9HUnSrHOKz2by7n%2FAKkTIkqU0QEY1xUADcFLLif%2FAMkRVotjHJiNr1Z2oi%2BVZ%2FBs%2BzY78HCHkQUBIqdX9Psm3c%2FJEfrP8i9Yc9kqvYDTo9km9J%2BSOIMM4Zw3Xm5t6ezKxVT2pUtNtuOtLWHFrudAAXtYC%2FwxeF4FwU2kE5y4oI2I6OVdUbg7%2B%2FivBfG41YjadX8199564s%2BzY7HVwc5FqB%2FTast33umpoPr2iKeDnIldianWVC%2FP2Tb%2BaOL14QwOkJT9VjGK97m0o4Nvj7x7JPDGXqNfSZk4wUbdW7DgBPo1xSrRvG4%2Bv2s%2F7Z2pi8096z7NjsJfBxkPyNUq4%2F7yb%2BaI%2FWdZEJ3FUqoHmqbfzRyEMC4WqjOul4rx%2FMIasHVS0i6sAnsuFx5jltRk3S5iLMY3t1fEHb%2FD1oiNGsanXiFr1f8Asibz3qbPs2OyTwc5GLNjV6uD2WqTYP5N4h9Z1kWdhVa2f%2B8W%2FmjjBWD8BpWNWaGMG3EC1nWHEKSe7dcUMR4ewPRJCmTdNzCxxUVVAzALzAs2joiApBu5fXc37rRaNGcb5MQter%2F2TFvHLTZ9MbHa44PMjQLGfq5H3RqKL%2FkimODnI0narVn%2FAFg380cHBWGFjrYox8pPcXAPk6SItqwrpGvE2YKCT2PJ2H4SHBjG%2FwDELXq%2F9kzb96mz6Y2O7zwbZIKGkVetD9kJ9v5omRwZ5KGwRWayQDy8ebN%2FkjiSi0nB1Ulpp%2Bax7jqR6F1DbPSuXDoIJO4c2I22i5%2B17Arart5l47KbeUhw8%2FjxPBrHcs4xC06v%2FYi8Uxrps%2BzY7G%2BsxyW1X9mK0Re9hOt%2FNEw4Lslkm4qlaV2kKnm%2FmjjRVFwECSMxMwlb3A6Qg3%2BPFRmnYBQpXTY1zAcFuanzt%2FDhwbxzL5wtOrHtLb5o5tn0%2Fk7E%2BsvyTbRZ2q1q%2FeZ9sfmiCuDXI7tq9ZH%2FAHi380chnC%2BFaq2l2lVTMydZQsoU40slBPOw63OJG8D0p7SDP5m3JtbUom%2FxocGscnj7oWvVj2lN808kWf8AXodhng6yO6RRFQrIUo6gPZBFh8kQ%2Bs1yTKlH2YrVjyHj7e3yRxoMP4EQsInsfY7k1IBC0uuEFKrHqkarjs9cUcTUzBtClKOadinHc85UGX5h15NQCW0hLpQlCetcna5PLcCEaMY3%2FiFr1f8AsjfMc2z7NjtBXBbkxcI9lq2FD%2FprZJ%2BSIq4MMlli3srWwrvE63%2BS0cKInqUg3FZx4kgWumrJ3%2FhxKqo09CtTdbx3t2eywF%2Fh1RaNGsbzynELTo%2F7Kxe8%2FoUdmx3X9ZVk5pSr2crtk9vjje%2F8GIjgrydWnT7NV3c%2B9nm%2BXxY40wtJYdq0lNTVcxhj6UAdSiWDdS1hYA6xPW5g7RfG6DgEKTpx1mKUgXJTP2P8aJ4NY5H94WnVjan3%2BieSz6fydWnglybSbKrmIB2bz7f0YDgoyZO5rdfHpnW%2FoxymKXl8la1vYgzEmffAuVIXuefvokmKXl5N9ZFZzEZOm2n2VBuezfVFY0ax3POcQteiPaJtrOOSj%2Bv9rrE8F%2BR7SfdqxW%2BsLJJnWxa3dtFCZ4Lsln0FuVr1fDlrJCZtpdj32tvHMFDy6wpi2qM4Vw9ibHwq1QbmG6cp%2BoBTXjKWHHG0qSFX0lSAD6YpcEeK8TVfPOnUx%2BtTs1Iv0ycfm2H5hakgtt3SpNzsQr13MYL5gmL3K7Wl6nELXOiJnKYjjyjPv%2BRawtqbW0pspoo455Mtjx5yZVVbJ3GzmEanNJnWHpZM%2FT51CNImJZSlJF0%2B9WlSSlQ9B7YwWOo%2BP5pLWP8AA5TbU7hdTqj3kzMcuHtj2%2BjF9t8SwmwvV5%2BHVHH5cpmM%2FTk5d7s6bO2qpojihKDaLw%2FjHFc1hySwdNYjqL1Bprq35OmOPky0u4q%2BpSEcgTcnzXNrRZTzidPKO81l3pWKMTUOn1Ok0Wvz8jIVtnxepyrD5Q1Ot9iXUjZQtt6DGwOHDN6m5L5ryuOq3RZipU4U%2Bap8wxLKAeSl7RZaL7EgoAt3KMbQyF4SMNYry5ZzfzfxQ7R8PTjLk1KMNrSyTKg6UzDritkpUQdIG5HpjA%2BI7AmSGDqPhqtZIYy9nGagJ9NSSqdS%2FwBCpkI6M7AFF9Stj3bQGucc4oOMcb4gxolgyq63V5mqJaSvdguOFaQFDtSLbjujx4gxLiLFdQVXMU12frFTcabZXNzrxddU2gWQm57Ei9h5zG8s%2FwDh8wRlXlFl7j7DE7VXKjihbSKg3NuIU0Nch05LYAuDruN%2FexkuW%2FDbk%2FT8laZnXntiWpykjW0NPyzdPJDUqy6tSWukUlKlKUopUTYWAtAc0zmLMVVSiU3DVVxJUZ2kUUqNOkZh8rZlLix6NJ8nYkeYGElifElOos%2Fhmn4gqMrR6s4h2oU9mYUmXm1otpU4jkSLD1C94yTNGgYAazKcouR9UmsR4dqCJFFJccVqecmngErZJsNw5ty5GOmUcIuRuV%2BF5Wcz%2FwAw%2FFqpOKCCG5tMtLodA6zTWxU5pJspXK4gNKcLefNJ4e8wp%2FFtcoE9V5Go0rxAtSakh1t1L6HUK6xAKSUaT3XvGq5qqTEzWH6%2BwtyTmnqjMVNpUu4Url3XJhTyShY3CkFQse8RsPE%2BUVMqmfk3lHk3UxXqbO1BlmiTqnkuAyy2UOLdW4nYpbuu5H3NucdFv8IfDJhOap2EceZpzSMTzyQhoqqDMqp5xXIoZIOkH3uo7wHF%2BIa%2FiDFlVmK9iquTtZqk2Eh%2BdnXOkedCRZIUruA2A5RTrWLMV4jkaVR8Q4nqlUkaFLGUpTE3MFxEizsOjaB8kWAHabAC9hGz%2BI7h%2Fq2QWIpGQfqZqtCrSX10ipFro3Flop6Rh5HJLqAtJ22UDcdsacXAUzzMSgb3iK%2B2JkDbnAALRGEIATaAN4lVEUwExCvgiQkRPcna8S6RARHKJIn5RJAT2iQp80TxHbe8BR0LJ2NhELKHbcxUUkkc4plP3JO8BKjn6fV6YiXCjb333XZA3biHPr9sBOlw6Sb9kbo4Qin6uss6T1mcJYqdQf2Qo8wPyExpRHkxsfh6x7hjLPNaRxhjNqoOUVNKq9LmRT0BcwjxySclw4hJIB0ly9oDXeGXEtSdLcXuEy7ZPxBGTN1SX6qOmPkjrdnLn54zdmkcIckhtlrGWanRNtJbQfYWX6tk27HN%2BQjJcEZccLGOEYgk6VjTM5L%2BG8NT2J5p16kyzeqUlAkupbBX1lnWmwgNPVF1uYpTulY6VLzWlH3Sd9R%2BDaM5yT9zwTn24UE%2F%2FDJxHO3lVOV%2BaJkSPCg%2BhC3sW5tMuEHUPYSWJUOzcOWBjKMMYl4WMF0zGdFpmJ8zpxnG%2BHva3NuPUVgGWb8YamA8kBzrKCmtNttlmA0pSpthph0Pqsrmkg737LiPT7IS3W%2FRIPLkfPf8sZ0xIcJ6ylL%2BM8122yCoJFBlyW1m2%2BrpOsNuUSiR4T1IQn26ZqIUVWcKqBLmw7xZyAs%2BA2K1V83MOSODcatYVqs%2FNNy0tiBx8MIpyVNq6VzWeR6PWkDtKgO2Nx8ZEpL4Tw7l7lXhKckJ%2FAmGHp5VPn11hE9UalUXUhUxNTASollCgpWkHmonzRraaovCM8gI9vmZy0LFlMrw4yUp%2BHpLGL%2Fl%2FlVwv46rUzQaDmPj1qclKRPVh1buG20XlZNlTzwBC%2BelOw77QGpfZBH6v8sTiYF1lx0HU2oC57xGaIpvCi600pGZWY7WuxUtzDLZsD3AORVmJDhJSoiXzDzPUE263taa63o90gNucDWM8psB1KTeqONpeh5g4ixFLSDZnZNSmU0ZsdIuXbe8hpcwsBJWojSBbtjB8qEUZrjlwq3hmoon6acx5lyWmkpUhLiFKfWbBW9gVKSD26b8jGMCkcJrySHc1MxTsQEDC6SfN7%2FtjJsrsQcLeWeY%2BFMyJfMLHs69hSqt1JuSdw0EJf0IUnQVBe19XOAl4Y2mlT2N0rNm%2FGd%2FQFzBjS%2BLKNVMccRM%2FhSnNPOPVfEDUp0bC0pcLdk6ylSiEghCVG5Nu%2BNz8LxDisazaRs84h1KVe9DinlW9SrRrXDSFDjEbKAkkVudACuRtKr2jz11iO61vPLlH4PreNTNGgVwn%2BP%2FAPoyqVpmXWGJF2gU%2FA8tWWUz83MIqdVeUZt9lSgGW1BJ0JCEp97zKlb8o809I5dz05T5mdyykEIkJvxlTclPutJm0abFl3mQm9lAp3FiO3aM3294jMMDZUTeL8OT2NqtiygYUwzTplMi5Vq5N%2BLsLmSnUGW%2BZWvTuQBtcR38o5XyaJmeViZpWWjikg5WU8OOWtaov237LRkAyuoUlhmv1yayackfY%2BkTUwmYmDM6WHEgaHCFAA2JvYmxjLqdgDKyipdrqeIzLub9jWX5hKJedWp1biGllCUjTuoqCQPORHLNbzGxtL0xiVruNMTz0vNps5LzNWfeQQbEpWhSrK%2BEdkRlHeTnPfW6drss2lDTlFpjSiLlTLagT8BVFtmarJPvmYQ5Ny61c0y5CEeq8WeqVJufcQ7LBSRaxuOUeYqIHOJ4oV3UspRiyaS2ltqcf6vvilAV64z3KvF1XqWI5GnvSdJqTU7U5WXcbqEj0ylgqSjowpCgQFBVjbe5jRU2HCYyXC2K5WiUpUmpp4TDjxc1gbJG1rHsPnicoM5dS4lw5LUKYnJmq5Hv06UanVoWucEyhsaVkWKyAAO6%2FmjHumy4cUfGsr5NaCCkhqpuoO%2FaDY2I7IsWT2Nazi3G9EpOLs2anSKDVjMSc0%2FXKlMOyPRKaV9tC1KTpJAFyOdrWjcj3D3hlzo2qVxL5VzrrvUaSqqlrUo%2BSkFW1ydoncQtnPfavpn1O6TSpCmJy5bnnpNuzs9N1BwvTSytSipQT1UiykpAHYi%2FbFd93L5yqSFXbwKtpuWlHpWZpjM%2BpMvNLJu08VG6kqRc3A2VtyifHOB8T5b4pn8GYxpqpGrU4p6VsqCkrbWNTbqFDZaFDcKGxjJsvMk8U5hUCfxZJVCi0ei0%2BZTJLqNan0ScuuZI1dEhSj1lAWJA5XENxTJnPfY287lfOKbDuVy3nCqxHss6NV%2BwACPbP4SwSxhnElXlckKpJuUyluTKH52oPhhhWtCUqVYC%2FlEW7SRGZryOqGEWX8WvZrZcrZpEs%2FPWk8QsuzBW22pSA2j3y9QTpHfaOfcU54ZpVKkGh4zzIxLU6dOoStyTnJ1TjTwBChrTaxsew9sNxBnPfWV%2FEFDbfSg4cl5cA9ZKJ51QUL%2BcbR4ZmqIemnX5OdEpLrWFIYsXNI7RqPOMWqM4xOP3YUSnzx5tbiOUFc2bN1httCUrmOmI5qBKb%2FBaM7y3XgjE9QpeG69gWo1BdSqaG3p%2Bn1kszSWSN0NNKQUKVzNyeyNBTExMoVdDy0%2BgxneA8dKwkmlVqj1ZcpXKY8JqXeR5cu8knSsE7X%2BeIqk3TbPtLybLoZfexkSFlJPTMC47CPP5opVDLrKV%2BRmGqPWsVyE8tsmWfmm2XWUOjcBxKTcoPIkbi97HlGU5b5hZwZ%2BVxGXc1OUuut1STmnWJVdOk5Z1b7aQsOIfSlBSsEX52O4IjKXuFjiFbIbGV0%2B4smwSxMMO39GlW8RuYTq1NaSeWmS7snLePYpxezMlpsTAblWlNlzT19G99Oq9r9nOMWzFy8p%2BHKZUMU4KxZ4%2FR5BMvrlKjLqZnkqcdLZsBdC0i6FarjZVuyMlm5WoUqoTFKqsjMSM9JuqYmZWYbLbrLieaVpO4Me4qX7R8egC7RwpNh1B8lXuzGm%2FnCgCPOItuYhWc51uk%2FB5L15YoLn%2FACyrT7ih3FLRG3m2jhPEb3SVCfev5c5ML9byzHa%2Fg8Z9f1OEyzp6jE%2FPFPm1sn84jh%2BuAJdmEpJID74ue33RUdGqf2bRH8U%2Fi411ie6VtPkj1sJmFddQv2kfLFaRl5J0Ezrrx36rbABXa2532AjyuGy4Ic6NaVg7xznayXH%2FAIMjl7KepHzxTWuge8VUh6UI%2BeLvh6hyFWpEzMOu6XGFjplN3Lsq2dkvFH9savsq26efaIsVTpk5R51clOoAcSAoKSbocQfJWgjYpI3BgTCsj2CUqynKiL7bNp%2BeJqjJykksJYmlundLjbjehxpQ7FDluCCCItusREuFRKlEkqNySeZghEkRLc98QieAlue%2BIRMT2RIVGAjCJbnvhc98BVuO%2BFx3xJCAmuIah3xLCAqJN4qDlFJrrLCYuE4xJmSl5ynLcIPuEylZvZ4b3FvekWt6DAeIntiW9zELmJSTAZBhRYTOuJI8psgebeMwQ5GF4V3qQT90giMvRsN%2FP%2BWArhZKuW0Ek3tfmYkCrJ0kc4eVunsgKovexV6oqJULeTc%2BeKQvYC1u%2BBUCbk8oDMpeofodppxISpCN9zvbe9oryk4GZodI8nyFWPO9wYxvD7CqpW6PRC8tAqVQlZFTiU6lIS66lBIHaQFbDzCLtmVhIZf5lYswG3Ulz7OHK1NUxqaUjQp5DThSFlO9iRa47xAZFki7gFjFE09mLK1l%2BVRS3VSApYmbonCtCbumWBdDegr3G2rTfaOjm6xwMu%2B5OKzNbc3V7u7WAfOb2te1hHM%2BUObVbyexHP16iSUvOpqVNNNmWHplyXPR9Kh0Kbdb6yFBTab9igSDG%2Bk%2BEWzNKlqVl3hk6htaYeBT8kBQzHmeElvB1YOE5nHiFTNIm25czL1V0pqJCTJqKXE9EpskKC9ZAtbnGncjsc4wwTmNR2cHV56lKxFU6ZSqkqXSkrmJTxtC1NAnyQoje25G0bJx3xz49x1hqo4cn8CUVhNUp01Sn1tTj5bSzMJAcV0RGlawEjSVeTc2jnik1SeodQkqzTZpUtO06ZbmpZ9IBLTragpCrHY2IBtAbs47FBHFHi2USnSJdEm2BfkOgTtGiARbcxesfY%2BxPmVimcxrjKfTPVqo6DNTKWkthwpSEg6U7DqgRj9zAehBRfeO0suaW8%2FlrhhLCm9aaW1rC7jdQJ5xxT%2Fa1LjtPL%2BoNs4Ew20VrCxS5fYdp0xNjGdvHmn1wx3if1Mx5YZ9TpFcq610y3NTdnNx1UjzW7I2O5lZUMZNysvJB%2BWE3LreS4y0FLUpI9zKQfehZGo90Y7l6mXm67JMVKYYQydN1unq6SQB6dzyjrrLeqUqrJdqbZbQhoGUp6SALSyDbUPOtQ1H4I2Lau0pnKhqXezs7Sc63NuLsmH6bS%2F0yamZuZbl21PMtKIb0JHuigO225F%2Bccw5jUmn0fdpotNhaiyCkJKmyeqbdm0fRbPCt0qRozszMzaGW2kFtx29g2Vdt%2FNHAeOVyuK%2BlqNAn6XXGGtp5Em9rdp5APubrR6yLgXBtp32Mde6Wc1WMVVcrl3n9C2mKNSx5R5MfVUmpyemKiqXlZF0MupTusE7oIB7Oe8b3kuGTDVDZX7FJnUpWk9KxqHQO38rU3bSbkA3tcd8a6ygxlSsscA49x8pMuTTJFgyMk6%2F0bk88tVmwm%2FNCb9YgG0bPneJ1GLMjKhi%2FAdHdmXZMSsniTWpLc1QA6N3lNn7a0sBYQ4i%2Fn5GNSixtK7Wap1Z5R2bW7NrRFEUxryiZ6Z2OOs153DWFcWz9GoM5NLakJjoZtKxqYCSNi2u9%2BqbpIPmsYxQOLeGh5QJbbGk%2FtuXptG1eKDGOS2OHcP1DJnDL8lOPSyZapsFJAmHVEBKUg3Klk3BPbcRzzQavN0OeckZ1t1UqhxbQbeSQ40UqsUG%2B90qFiDyib1T73VHFlnx5d7z%2BVlsKN1RlHHlxZ99sjVLu0l%2Fxgou0yVHrbLsNhbt2jWbjgbbvGwZd%2BVnafOOIUFLclFK2T1QbHb02vGranOIYZ26x%2B5jXqnOIlms4ynJrzGCr4nnie1tB%2BSPTiuQmKcKKJhh1ozVHk5tHSJI6RCwqy096TbY%2BYxasSTBnK1MrUs7y7aLjnsCI2DnrmW7mOvL5p2Sk5f2o4Bo2GUKYTZTwYStWtf7L3S3wRpzrltxOUQw%2Bk3sk%2BaKVfJCEm%2FbFekEFA%2FaxQxCfckRUWAG0TRSBMTQExNomQYpxMkwHqxB%2FWGjo7lTSvWpPzR6pMj2ElldqkqHymPJiMFNJootspt8%2FwAP%2BaPTLm1Hk0D7jV%2BWA8q0q52EEpUryrxOEq5kRUbSpw6UmAkDO2wiRTduyOvuBfhZpGc%2BKqjiXMCRXMYLw42A%2B0lwt%2BPTixdDOsbgJSCtRHZaPHxxcK9IyKxhT6%2FgGTmW8G4qbUqTZdUXPEJ1ABelC4dyCmziCdykkb2gOSFdUwUraK8w1Y8o85EBLfeJogAbxHzwFQAnsioGxblGUZWZd4mzYx1Rsu8HMsO1qvTPisml90NtlekqOpR2Askx0a54NTifQlRTScLqUk20ivMA39F4Dk5DYMbMyVyEzGz3xKcMZc0JU8%2ByErm5hag3LSbZ9%2B64dkj5Y3MfBucT0qjWrD2HHvM3XZcn8sbtxpl9mHktkJlhwtZY0xclmJmlOTExiB2RdSlby0DUtpUwDs0hO5UDbSk25wGsEeDixDNOGkUnP3K6fxGBYURFSUl1S9%2BqF2teOaMzsqMdZR4unMDZh4bmaLWZIBa2Ht0uIN9LjSx1XEG2ykkiOjZzwd3EdJ1qnS9CpmHK43NzIQa1R6qlTci8Dcl9zZxsg%2B%2BHbGzncB5hcXXC9M4RrLUrW828mcWvYclKo7ONj2Qk7e6NLmD1XAE2IUTuUJPMm4fPBxu0UFIAMdVq8HPxVqG%2BCKV%2FruW%2BlBnwbPFZNL6FnBNLU6eSRW5bf%2BFAcpQi4VikztDqk3RqowpidkX3JaYaNrocQopUm%2FbZSSNo8BFoCsx5Dn%2BTVHZ%2FhDFlxrJRSvKOXNMJ%2BEK%2BaOMGPIc%2Fyao7H8IUu8zkyj7nLWk%2Fy4Djdw9aIX3iDh60QgJ4RneTmS2YWeuKXcH5bURFTqbMqudcaW%2BlpKWUEBSipRA5qHrjcivBzcVqbkZeSSrd1Xl%2FpQHMjbd427kdwyZrcQM4%2BxgGhpMjJKtO1WcWGJKW8ynFcz5hcxnx8HvxXMS6tGWLTjp6qQKrL8%2B%2Fyo6IzrwRmJNVHBfA%2FwAOzbtPp1AwszW8Rvh8yzZccT1pibeG%2BkkqFu0kQGoql4NnNgyc0rBeN8CYvqUm2VvUqmVYCaFuYSFgBR81xHKWIcN1jDdTnKJXqXM0%2Bfp7ypablZlotvMOp5oWk7g%2Fl5x1HKcEvF7gPEyqxheiop07S5RyryuJqZW20yx6Kytn9QClm27axYjnzjamd%2BT%2BNuNTKjK%2FiKy4wQzM44rVMcpuLZdt1uWS8uXUUImTrIBOpK09%2BlQHYID52lob7xT6Ox5iOn1%2BDv4sDe2VXLuqst9OLfWuAHirodGnq9PZVvJlKdLLnJhSKhLuKS0hJUohIVc2AOw3gOcDsIkKt7x6HG7cwY86k7wEQqJwqKY7IEmArBQMVW1WjypVvFTVbtgLg25cR72HAUWizsr3j3SrhKrQGa0D%2Btjh%2FZRb5YFWOMNoHbWJMcv8eiLhQjakOedREeKlXVmHhdA5qrUiB%2BHRAY9WnF%2FVKrK%2Fua5Oecf1Q58kXbD4BzOpw7VVSU5ft0RZ611MxK3p636cTn%2FmFxeMNJJzYpaOz2WlB%2FDRAfpGhCEAhCEAhCEAhCEAhCEB%2BefihRozszDR3Ypqo%2F8AFu%2FPGmlbyiP3XrvG6%2BK1GjPfMVH%2FAPVNV%2BWZdjSZv4mPNr9d4DLsMptSrd9vymL1T6fP1aoSlJpUm7Nz0%2FMNykrLNJ1OPvOKCUISO0kkARacMj9LPhT%2BSN%2B8HbmFhnM23iukUd9pmnTNQkqpVZ7xdmjTksOkZmALgOKK9KdJOwJI5QGN5b5J1%2FEuYeG8M4xp9Uw7RqtiRzDcxUZiRX0Yn2UKcckwf1QhBTq8kHc7Axdc98rML4FoOC8V4aouJsNpxSuqS79AxJpVUGFyrgtMFSOqGlpWhKRzuCfPG5qvJZuU%2FI%2FMpXE8uhYvn5VDdbwpT5msIZebW5raeqcr0RBU2kLQUJFyrSoRyJVqzWK3MJqFfrdQq890bbS5mdmFvOKShISkXUTYAAbCAoSNNdqMwJdhSQsi%2FWPZFy9plU%2FV2fWY8dHqDVPqTUy8FdGkK1aRvyjIzjGkDZKXiO%2FTvAY7V6BOUZCHZlba0LVp1IN7HziLXq7t4yPE2IJKqyLDEqF3S5qXqFuzaMaBHZAVL2juzJF5uX4MVPPFJbTS8QFWrlbS5%2BeOEQewx3Rk0kTXBe8ysAJVSq62PSA4R64%2Bbe6bOVxuv%2BtH3K3Wwj4yvzS47wG3bKp5tYV7niRk795kTv6bGMyy1lTiDHAw%2FMzlRbkU0iZmVMSUyWCt3WkIUoi9wkX2jFcBJ6TKWbmCNxiaXCh6ZAxdaLOT9Crrddo77ktOIl3Gg%2B0AVJbtqUADsb25GPolnxUuZXOeTb%2F1NGEAqNQrwt73x1RMYNm3QJHD%2BLaVRKU9NqRMspcU7MOanOu6BYq7e0%2BaLTP8TE0wG0P4oxQnpBqClU%2BWv8FjGOHNzLmp16XxBiqcxpVnWHG3C2lEu3qCFXCEknqgkb84ywo8tRzdGD6k81L5eYfmJhLL7LMy6p5S2tYW30gBVYqAJI7Ad41VN4hExNqcZleiSr3uvV6zHrxXVpas1Bc1KAhojqg3uLqUq2%2Fdqt8EY0tvQ5e8Fl%2FZrGw1MX%2BGPYKw242ptaCnWLXB3HnHnjHG1eaKod0wRLbrmcAxBMsyM3l7hpLs0420uZl%2FGG3ASAnWE6ykHtta1yYuUw2W3FotslWmNO0eotyFWkp95tbjUtMtOutoUEqWhKgVJB7CRcA98blnMzclXnXFSdIx0htTii2l5cqopQTsCQrcgdsVS8TnbFN1%2BakWDMyUy5LTDdi282bLbN7agew7xXcx3lKthZ9iMYgkEpOuW0g9l972EemapLXSOy0ypapVFy6W06llAGo2T32iykxm6RmcMOznROCXn9KmWybTTpTq0C6tz77mfOYxjM7B1OlsA1GYdlplEw280oOuTC1HSpQBGgm23O%2FONJfVooEoltPsrjFpDjYUB0qCNJ2BBC79kQbzhy%2Bmn2lVuoY0nZVDiVuS4U0jpAOy6lG3ptEZExm81TzZVhGoPSMtgyhPLYQpDM2tlanBfYOWKragOW1r9kaum8RsKmyqTadKVgKUXiL6%2B3lFXFFWardRcnZdOhDh6ovyFzGMuAomBCYzWhk8vXHVosWEpj1ipqW1pUm2oWBBjHWHLDePSl28MkNsKzhma4%2FLy85grDba3C1LrdlZdbKj5KdYsqwV28rXvF1mOo4tHZqKfUY05IzyJOdk5xbfSJYfQ6tANtaUqBKb9lwCL95jbc3mbk7MTb7rOHsaNsOOlTTRmpUqbR9zftPniUwObiLXVnpiUpz83KvOMutC6HG1FKkm43BHI7849ozCyscaUBQMXJXvpJmpew22v8Me8SCHnhJvhZlnFXWEgFXRgajYd9oIiXQq8I%2ByaJaYXJzZJlWUKWJlxRdOkdY9bnFix9hClM4AqzLtNdTNoW0tDzkwsqSnWAUhJNrRp2ZzvwBKJbZbw%2Fi9BLaFI1zzJGjs5HnaJPq45UTZQKnhbGTzaVIUtDdSaRr0m%2Bm5vYE84CyVjN6dwnUHqfIYMwusBlbbbr8kpa0BaSnVuqxUAdjbnvGr14hS5MKLLZCVfdK3iviqpS9bqz07JpKWlXKQTyBJNvg5RjYGh8WiJ4zPNlMvWVLG6IripLdQpO6R3jYj0RYG3NEV234kbcczjn8S1aXRUME4VS7OOMyzrsrIlhVjZBULKsFGwJNucVZhCG1rQPeqKfljWFDqjVNrVOqcywX2ZOcZmHWQrSXUIWCpF%2By4uL9l42tP5jZHTMzMuymCMbNNuPKcZaVVpZQbQSSEE6d7cr%2BaInjFvK97CIVl5yXoM0%2FLPuMzCQgtuNqKVJuoAkEbg2POKi8dZN2szg%2FGaFaLJUarLq63eRp%2BSPc%2FSQKqqlvKWuXQpQWQndSEpK7ActRA9cIjIdIzWFGq0qXqD8q2lZlWGlqRMFIc0NhIUoazdRA3PabxiGa%2BF6XTcup9sSDQnDMsuNP9OVOadSQpI6xFrG%2FK8aPmc3MESDiVrw%2FiRKlp6RNp5kjT2dkedvN3L5yZYXO0DFD7CHQ48ymeYb6YDcIKtJsL2vErTGaWfzer2Cas8zTMN4ZVoQ42y87TtbyErSUkhRVYqAJsq2x3jWDWIXtelCEjzG%2B0erFFVbrM%2B5ONI0JWbhP3PmjHGf6pVeCrKGq64R1kpisKylR6wI9EY%2BlXmiYKPdAbZObNXxTNt0uawrhdDk8tDLswxT9DxGw1JOqwUe0233iVwBtxaNSuqogee0a9w3VmaPXZCrTMv4wzKTCHXGdVukQD1k37Li4vGxpvH%2BU81NLel8K4nabUolLaqgydI7r6d4uPPr80TI5xA4yy3c6qcN4kSCdlePskjuuLb78%2FNHp8XW250S%2BspPV%2FPGPLNaYXrG4twxyZHbmUs%2F8A%2BMEdh8Cri3eHmQ1cmk1VtJ7x04P545Bx0ylPDFJbk6syV7d36WCOw%2BBg%2FwDy501OjTpTVRf7r3e9%2Flj517ovFcaI%2FwAyn1S7WE%2FCq%2Fln1w4OmE6Z14f494%2F7RUdB8DO2dM5f9b83%2FGRHPkyFJnXkrNyH3h%2FtFR0JwOWGdE7tf%2Fg9N283WRHa00n9gW8%2Fw7Gph3FeqfOnz79w4oMQoNk68tHyVA9imLfkFo03Jzc7IsqmJGdXKzC5uRaQ%2Bi2psKmEhRSTyNiReN0Z%2FNJPFLXgL%2B6ZXuk37%2BhPL1RpFxKOh0uglsKbeKb8yg6h8ojY0RjPBLtP8Eepr33itqvO31UsGzE1UX5hE3iFtsudRCptSikdwJTvGJ5r4YlaHgxudXOVOYmTMttlM490iRddwUCwKTbY98WB%2FNBUgCit5kYhlZloN9KlDAU0hSk6glKiq5sCN%2B%2BLFVseYTxKEM1rMqrzjaSF6FsItqHL33ZHpI42s8D9fw9hKmy71WwtK1Yuy7L7jr8w6lRLpX1QlsgAAJt384wPHeYdLxZW5iqy9OTKLmF6jLy6ChplISlKUICiTYBPMm5i9Zl1jCVTa6HC83MLlG5WTlW0TS0l5TjSVlbhCOqlJK9hckAC8akmkKYfBJ3PbFskTDIm6tJkC5WDHpE40sghaiIxhLpTa5uY9TT6ttRIEVS2vhTMTDlEw7L0Ss4KpdUek3nXG5t119t1TayFBtWhQBCTextexi7TU1KTvRVCTlxLNTjKZlDAUVBoK5JBO5G3bGmOkC21deN1UTEmUM5hmiCq1uvydVlKc1LTzbbDLjSnEEjU2SoHSU22O9wYTxpyhbnF78og2FLdbTfmoCL%2BioZObdPirEI7%2BjkWjf8Ahxaaj7FiZTPYcnnpqnTDZdYcmGg25sSkhQBI5jmDEZGTb2CJSu4jwJTZtzFFbQvxmbRZh1CWUtIWEtthIRsRYkm%2B9xF%2FYwbMvtPs1DF%2BKLCXcUyG5hGnpLbdIFJ3RzuBvGr6VmLL4CpJoTWMKvTnWXSp1tmVQpjpVpCyAVG%2FJQvHrXnnIVBlDFRzGrTzajZbaJRhAKe0X1X5QyMmDzeKKLhyQbequGJOfE0VBLrj7ySlW5I0o2taMJxfjuk4krz9Yk5FEiiYCSJOXbKWJcAWCEBRKrWA3JuTeLpmlOYWnpWUZwpOPOyzCUIHjBSXVFKDrcWE9UalK2A7BGrrFD9olWIyZKutyTjflP8AxYpitSKffP8AqiyBZtvEq13hHEltuhZr4Uk8PU%2BiVbCcjPPSRWRNOF5DywpRVoWUK0qAvYbXAi6ull1SZlhgMNzCEvJaBJDYVvpBO9h540cDeOgW6xlRMUilOP12tS1RTJMtz7aSwtkvJSAS1uFBJAGytwYC2FQ7vkigVWUNXK%2FdF2cqOVYUFDElcCe0dA0r8io8M%2BJJIEzSJtyYlHGulaU82ErNiQQQLjs7IDalIlKtM4do6pWtVqVcalyHegmSWniVqIVp09WwITYbbRCs0%2Bqs0CpT03ijEC32A0WAuYBYI1jpEuJKbquLAW5bxjrWN8KYTkmqdOYvxRLT7KUh4sJaRLhZSFFKQpVyBqG9oknM0sHVlnxaexviSZbBB0KTL6SO4i%2B%2B8BYJ3GeEMEhlqqYJkaq9Mlay7MPzAIsq%2BmzZCQLWHfGu8W46puJsS1CvMyCJFE870iZaWQpLMuLWDbYUSQkAC1zc84umb9QwxVHZdzCzsyuSZASjxpaFPqVoSFrXo6oClBRA5gWvGsYJhkia1Jp5uu%2BqKrdfkPu3fixi5MELtBEcTdNIzXwazh6m0WqYEp9VmqahxCZ5xyZaedQtwrShYbVpVpuQDa9tjyirVDLGfWuTlfFmHUIeQxrKw0FJvpCjuR6d403LuddP7YRv9%2Bo5S1CWknZ2v1uVnhIssTaZdth1kTCE2KmjqBKFCx6wBBBEESxdSiDEG1JXMNpUTZRAjJQ9koFjpMW4jtYakpk2SoHtt17GLbWpOmyk629huoPzlNmGQ%2FLOzDQbdAJIKFpBIuCOw2gQ2lKt1uYo9MQxVqy0W5a7im37trWVk3SnT1QE2Tbflftjz4hlaxL4bnJh7Elc6dp1hSA48lTK0dIAtC0lO9wdoxmVx9QsOyrdNqWPq%2FJzKU2WmXZSloKBuoJ1K5AnnEszmThKoWEzmLWptKCFIamJdpaFKG%2B6dQBF%2FwAkE%2FCYxUcSYOwwZVivYObqRea8ZWvxl1tS0lRu2NBsBtbvjBsY40lMVYpqmImZJuTTUZkvolmElLTCNISltAUSdKUpA3JMe7Nubw3PVKTThGbfmZBiVS0lUyU9MSCdSlhJIBKiogA7C0a%2BQbczETGaYZKzWmRspa9oi7V5JXMrjHQ4EnnEFvRKG3qXmPgNymU%2Bkz2DFVKfYSpkTYnX2HHtRuhK0C6LpvbUOYG8U5gNpecUlCm0LVdDZXq0Duv2xqyjzCGKvIvuOBtKH0LUTySL9sbvdncppxqXmTi2oNTRaT4yz4qlbYd98UKCt0nsuL98Bj4t2aomRbV76L%2BFZT8xjirH%2FuwEn4AqPHPyUqxNXp00uaknQVsOqb0LUm9usnsPmgMswH7nl9nS5ZW2Xq0eY6qlKc4z%2FwAG8pfsvmFZF0CUpV1W5HxlVvzxgOCkJOW%2BdJNwPaILkd4qEtYfljP%2FAAbpKpvMNvvlqSf%2FABKo8bpvGeC3jzfjS6uFfKaf65JWLjHP%2FwAxeKx3Jkx%2FsBGBZYEnMrBqR9%2F6f%2Fv0xn3GSsK4icUAISPc5Ikg7m7PbGB5SgHNDB2oXIr8hb8MI2aZy0apmPA%2F8WKn5V5d1Dp7whyQKBgF3clOOW%2BR7C0n5o5xzFXpzkxZ4x7oRX5vWg7390Vz7%2By8dJeELSfalgRQKbDGzGoHmT0O1vljmnNi7WbuM1Mq3RXpvSr0LNjHN9zjLuFRH8VXrTikZXmpubBeGJzFGA8OVaZxLW3JqZkgqYAcR0dwohGiydgEgC3eIyAZZ0oU6pNz01XHkLlXlJSuYBa1BBI1p09Ybco0jhXN3EWX%2BFpRh3E1Qlaa0lxuSalqeiZKNFlOElRG3WG3OKVU4l5GuMOydSx5iwsPJUlYZpjLZsR2dfaPducw%2BkO02lYbmcQ1Ggy1YVLLbaTLTLzjSDqbUSdSN73At2RYMQ5qU7FVMp9IkcC0vD7FM6ZdpJ5xxc0t0gqU6twkm2kBIFgBfvi74hxdlyrBT1Bwo5iF%2BdemS%2B47PsttNaAyUIQEpJOrUpSio7W2tGoELLa4EcTKhWWg2NMub9u8BXh2S5t6Yx1TpDew37d4omaWCABtAbFwrmJLYaTU25rB9JrsvU2W21tVBTiehUhetK21NkKSrmDzBB3EZArEkhi2SVWJTCMhQOjmPFi3IPOrZc6gUFEOEkKBO9jaNPNu37Y2blzjHLWl4WnaBjqnYlcnF1BE1IzNHLJQhvoylxDqXSLquAUqB7wYZ5ph7NH7KAT7oOtHvcxjkXrSEMZh2v1%2BpJi%2F7Xr7fDEsxUcDVmVM5gf2xt%2BJlCZtFZQzdQWeqtBaJA7iDAltTJqmv1SkVyTE%2FVGW21M9EmTm1MpQ4q5K1JA69wLb8ucbCpmBSioMKma3iVSCtIcSioLSopuL7%2Bj8sc%2B0HHycvmHatM1WuypnbtgUsNEaUWuXA4RfdQ5RdmeJ2VASZjFuMiU8w3Lywv6zBDwY%2BmpXB2I6%2FPuUaWrrMnMqYQ1VHFuKDZWrRdSSCpQAAvGvcS5mJxdJ0uRl8KUmgy1K6bo2qelfuqnSCtxxS1EqV1QB2AbRd8aY1wHW6DNS1CbxE%2FU5%2BaVMzc3VVtBJbt1G20t33uSVEnfa3bGqpRxWgbwGQpqigrUBeJnKu4sW0D1xZg6bWvE3SAf%2FALgM%2FwAGZnO4OlqnKe1ih1iXqqWekaqUuXOhW0SUraIUChW5B7wYu68TN4olk1tvDdOpHuypbo6elSWiEpBuQonrb87xqnpRzjYeBsaZb0%2FDD9DxtRMQvTaZ8zUnN0mYaQkNKQErbdQ55W6QQQdtwYnNExm9Zdue2KrZBG9%2FXFRWN8kxfRQsdnfb9Fyg2gqr4PrDRdwhI1uVDBHT%2ByjrTmsK5aej5W88QtENo5XYXp2IMKzszNzFURNCdShpyWnXGm0NgHUFJSbKJuLHmLRmdOyuoDtQYRPVLEDkstwBxDVSdQqx%2FZE7bxqDC2aEnlZSROVBWKdU864UilTEu0yG0KCbqDqValk35chF2d4tpN5JbL%2BNwneyjMSFx6m4GTHsQ1sYGdrNcZoVKrDkvNsSVqs0p8BOle4AIurYXJjAsV5lzuOVU9yaoVGpLdNZWwyxSpTxdtWtWpa1i51LJ7e7aLhmLmBgOv4acpuE6JiCWmpidXOTs1Vp1t4vKsAhKEtgBKR1udySrzRreVcIQLwQvSakpHZExqZV2RaVOA%2B%2BiUOW99AZ9hPM%2BpYQplTpEtRKHU5KrOMPPM1SQExocZJKVtKuC2SCQqx3EXScxA5iyQlsSzFDpVKecmH5ct0yXLDC0pIIOi5soXIv2xq%2Fph91Gw8F49y6pOFmaBjLCdbqb8tOvzTMzTqgmX9zcQAWlJUkg2UNQVsdyICa5PYYmF7eSY9X1SsmUlJ%2Bp1ihYB3Hs40Lj8HHocquEMSU5yr4QoVVo6JN1Eu9LT08ib6bXcpWlSUp02tYgg8%2BcBtTJ2kJqWHajKuSiXyuYbIC1qCmwBzRuLXvYxsam4GpUlPsTM1hpl5pCwVIdcWUEX5Hr8o5tGM6TgimSk3W6TVZ9U%2BHHEqlJ1MullAWUBABSSSSCbnaKbue%2BGCCGaBiRIN7g1hBuO49TeIyE2Mq89gt%2Bo1SkU%2BmTmqruSqBUGPGkhkI6qRqPZfmbnYd0YRiTMisYwXITNWkaZLCmSniUqxISol2W2tZWeqOalKJJJ5mPTjvHWGMR0KUpmH6FO0%2FoX3JqacmpkPKfcVYC1gAkJCeW97xgnSbRfJML37Or%2FUExK5WlKT9rSIs2vzQ1%2BaKoZzhzNCt4Vp0xTKZJ0p%2BXnFpdcE9JJmChaRYKbJ3QbbG2x7Yy%2BnVuoYilkVOpMybb7vMSkuGW7dnUGwjS%2FSRszCGZuE6Rh9ulVrCL07NNOaxNNzhaKm7AFopsRzFwrnuYjI1r%2FMJdSnSdr8jHnbbdCu0xRezawM6okZfzmlR7aqbj0dWPfT8S0fEjSpikUN6mssEIUh2a6cquL3vYGJGfZDM2zqwWsm15903PIfoV47xg%2FAOl5XEHSugPKkVMuJJ8pAaOofkjYOQLhRnRg8BKT%2BjZgaSL3Bk3wfk%2FJGAcAnU4gKQsoCtVJqgJPvbtHf4LRwdI%2BLDLfPmz6pbuHR%2FaaJ8rdXH8b5jYHHdhEf%2BaMcvR1Hx%2BD%2F4kYKuNxhEWH75McuRr6GfMd3j%2BGfXKl8n9fX50hiDja3G1NI8paSlPpItE5HbBPOPTNTU%2BgVYw29xMcGeFKVltUJZufpTFObmZB1QQ0uYkUlt6Tdt5BJstBOx6vfHHeb2S2YuTdFlZnMOkSdNOIGZsSLTM0h5agylOsr07Dyxb4Ys%2BCMxseZbVB6q4CxXP0SZmEhD%2Fi6%2Fc3gOWts3SojsJFxFfH2aWYWajkq7mJih6seIpcTLIcQhKGektr0pSBa9hf0QS6t4yVLY4b8mnV9Uh2T6pHM%2BxA5f%2B%2B2PTwxYl4kcM4Uwrgus5OoxRl3UWmjSqh0jaXJKnzCyslaVXQ60klaglQChyHZHI2IszMwMYUOl4ZxXiyfqtKoZSabKTKklEtpb6IFNgD9r6u5OwjIaDxG524UoMthPD2YNRlaVJNJl5VmzajLtC9kIUU3AFzbugNz8RdPy2yL4ssv8T4fkJSnU5tclXcRU%2BVQehlFCYU0H0t79GFtWd0dnRkgbxn3GBw95kZpY0oWPMtW5TEUmmiimhoTqUaEl5TgmGdR0rQ6laSVA3ukRxFVMQVqu1KYrFdqkzUqhNq1TE1NOFx102t1lHstsByEZbgjPnN%2FLemJoeDcbz0pS2%2FtMk7Z5lm5uQ2Fg6Be%2Bw280Bs%2FhzlzkJxbymEMxXpCmvtsTGHnnW3AqXl5yal21sjXyFyoIKuQKozbiO4P838xc68RYkw3KyM7ScWzDDon5uZCF0v3JKC24g9bQ0UEoKeeoW3jlDEuI65jStT2IsW1FyqVKpL6SaffA1OqAAF7AcgABblYRnVD4m8%2BcO0UYfpmZVU8TbR0bPTlLzrItYaHFgq2HK5NoDovwhNZptMwRl3lYud8erki6Ko8%2Bse6eLNSglelX2pU8sarHeySY4gO8XGr1msV%2Bffq1eqs3Up%2BZOp6amnlOOuHzqP5OUWw84CX30TJ5xKnnEyecBNAwgYBCEIBCEIBCEICB5%2Bjthf5e2Ifn7IDnz5dkBNziQi0TjnEjkBTWoi4UL25RBKtXk7W7IKWCLRKFajcbQE9ttwInQBbkIp%2FDE6B5xAehHRpbIUT5QAAFypROyQO0nlYdsbKXlPV8AY4ouEM3cYNZbNYqoLs6uecV06mZNzYS0y02dSC7psUKttYmLFlFj5GVeZWH8xHcLyOIWqJNB1dOmwNLgII1tk7JeRfUhRBAUN46vxvnTIZn5tSkjkflXlfmK7jOk%2By%2FjVdllM1KTWhPRzEvPKWoJ6VFhaxHVItAaXrXD1gaay3xrmHlpn7RcZqwLJy8%2FUpFmmvSyuhdeDabLVtc3JA7dMaN88dTYYyZzIyW4aOIFOYdEYpKa1R6IxIIM%2B0%2B4%2BGZ4FxI0KJsEr2v2eiOVlqKGyULOpJvYC5HnA7bDsgOguHbhMr%2BelDqOMJ2stULDrSJqTp80LLdmam2kaUlHMMJJGtfPsEaYx5grEeW2MqrgfFku2xV6M%2BZacQ0vW3rABuhXvkkEEHuMfQfIfOfhfwFgKRy3y%2FzAn6mKUy7Up0qpkw9Ma3AFzD7gSjqICr%2BYARzDxkYjyQx3jKnZhZRY3FdqNdQ4nELCEK6FpTSEJYebKgCCtNwpPLqgwHPN4zHCmDcw5nCFXzTwj42jD9GmBRK9P054F6RZmUhKy62k6%2FF1IVZRtY8os2D8QJwniml4nXRKdWU0x8Pmn1JBVKzIsRocA3tvf0gR1rkxxaZeYOw3inHU%2FlrgWhViaU3RJDCuHUOJmq665YgzIX7n4qNagVEE31DtgNVTvDRg%2Bdwdi3E2X%2FELhbF0xgqhKrs7T5GTebJl0rSkBK1CwvqjQ8dX4ByRzNyeyt4ha%2FmLg9NAkq1gNctIATDbjfSGeSsso0qJ6oWAB3Jjk9S13gJPfCJz5MSb33ifshA37wvXEhipYF95VFv3Kz%2FADxg2DcB4cxvxN4jYxM%2FU2peSqr8y34g%2BGXekQCU9Y3tuBy7LxnXC5%2FW3FAPY5Ln1trizZPD%2FwCZHFriLq0Tc2rv%2FtRt%2FwC%2FNHm7t87W%2Fo%2FB9gx6mJ0FuEfxZ9lotczMLmX3H3A2FuLK1BAskEk8ojndOMsZT5V0ubdeTIrmMQT5ZQNSVzBdYR0ik%2FdaQAD2C8QLYU4EJ7Sfyx5uJxxmWy9yp6Mg2YrdwBa58Ya%2BaPR5Pj8S1XLzuGtOpT7%2B3fK7iLLjCckZ9LHiLynEtqIJUkpO%2Fmi0t1NCOQMeZ%2Bb6ReuGS6TowiFwYpKfKopl2xiVFVxAWQLc4ouIWkAjtUExUS%2BkEHuiDrlwAOxQMBsmRdoCaRIS7tRbbdQxZ1voSbHnaPPON4cfSpCJ%2BWCdJTZxk7iMKXU0L1EhUedc9rad2V5JgOp8VVyrV7DeXszW5xU5MsYMp0qJhZ1LW02XQ2FHmbJsN4s%2Bb8yX8tMsqHPz3RU5hdfnRLLSotLfVMMpLxSNirQAm55Dl2x6q4rTQsBtJAF8H0zULcjpWfzxY8%2BlrYwXlXrN0ex1aKbHvnhe8TC7A5OSw4ggtT0mgjcENFP5os%2BNDLTM%2BwiXfQ6htkJ1N8lR4UVNkp6zjgPyRb3ZtKlqKSTv2iIUEspTExSiPKubtEomrwFVUukKKwL3EecMaHEhCLkmKiJgKG%2B0RYeQJlC1KsLwGxpGVDMlLOsVKXYWEWFpjo1oV5iDcQmKniKlK8bpuNJuXmWhqZfbrDqFNKG6VJIXsQY1%2B5OS91e6jn2pjzPvtuMO9c%2BSezzQWic3XOcWLatj7FtFxtiFxldYrWFKLMVJxpISl6YEsEKdNvfLCQT54x1dLq9awXjOm0SqMycyuhPOOB5orQ%2FLoWhbrdx5CiEgpVyuLbXj24%2BQ21VMPMt8m8J0VJ9PioJ%2BUx7MNyuvC%2BNJzUR0OGp0%2Bm%2BhNvl%2BSJlLa3g%2FyU5cTK72AmpsDa%2FJlR5fDHFtWWlfTrGwU88QO661bR2pwBjTlpNKH98zp%2F2JEcTVXZCv8o5%2FHVG7nnh1n%2FNLk3eP2jbehhr3lRSVzEVXd1xc5GjyT9G9mpmot%2B4TPQTEm2bTKW1Iuh5IOykarpO9wfTGi6aNBmJqnOIq0u6tuZQVty2nbWdNl3PakAm4iecn36lRJGjNstuS9KdeW1OEELPS6SWieWgFJKR2FSo8br0r0Ak0T8yphtanG0FGwUoAKI7rgC8SoqK2ZJ2msvPGVfWl1xlSRpUtIICvSASICk%2FITTLfSltKkBWkqSoEXte0ee38aPUw43oU06XUMuKSXEtp7U3sbfCflim8UFalNpsFLum4ttbtgKR5xNEp5xNASnnEh5xOe2JDzgEIQgEIQgJo9MjTqhU3FM06SemnEJ1qQ0gqIHfYR5ouNIbqKhMuUqq%2BJTDbYJCZksrdRvqCSLarWuRATopy6XOGVr7E1ILW2bBxglQvyOk9nOJZVyVlabPS6ZpTnjDgDaA3zKDdLmo%2BTcX25xRqT1RmHG1VSfemngkpC3nS4pKewajHjRrgJjyiWJibg7xLAX3Cf9XqH%2BLMZem6%2FKjDsKKKKiVDsbVGZ3gKgSNO8SBRSd%2BUTgi2%2FOJQCVXPKAqJupOq%2FbygUXBNrbxVbbCh0h74XK1fDAZDln0YzJwd0iST7Y6Vp7v6rbvf4Iv2f7pfz4zIdtYqxXU9v3wuLDl4FozEwgu24xJSiL%2F523F6zy0fV0zGFlafbVVbaf8AOVwGDagrrIQBYWO%2FOIl1QGxBVbeINoB6%2BvYHu5xIokKug3332gJ9XU1qVYqNrX5wLm1iNiPliUgHftIty5REXUi4F1ejsgKfX80TgHmRDRvcxUAHaICW56NSidtN%2Bcdh4IcQjCuHyVkL9i5eyLfsOccdzCwGlJHdaOtcCB1vD1EeUR%2FW9kJ%2Fa6f%2FANxex%2BOjzT%2BDFePivTH4tuS2KRRKemuSFLlJh6ny7jwZm06mnVFOjrAb7agR3ECN04fxqKHIycolh0pZlm20C%2FIBIA3jnyQkHa1TnaU2LmaZUhJA3QTvc%2FCmOosOYSodQw7JKmWQ%2Bp1hCy4DY3IHKNyurc1RuYaFlRNcVRMtZZ9Y2VijBjtFMy40qa1au0gWsFfAd44FqmGccZfYpkcTStXmqdOONKmKdWqa7vNy4X0ajtvdKhZTaxsd7EEGPpJjfIahYtlESjdRmJEpJTcdYKSTex%2BGOL%2BIiUwhlrj%2BSwpTK6rEDkjIKXWXmyEtyj6j7m1ztcIA1DmNrx0LOubaiKac43PR6WtNnvevjmJ3XT6FkzOR7KYMoOMsZY0mK7jeqTYpzDb6G25ZqQDeoqCUBOlWo929zFrzam5XLPKXB2VlPlZhis4rkWcVYsqPThaZ4FS0yco0UbdA0kKUU79ci%2B94xDEuHscVGmTU05hWcak2wmeeUltSXG2vev6F9YApNrpFiI3HknkHifPzLF3AuK6kwxT8PS81V8OVyaGh%2Bgtm6nGHlH7ZJPKuQ2eshV1J2uIwWltTZ1UzRx6%2BmeX8IZqLCZpyr7%2Bcx3ojk299yu5iGZlXm3ZVxbbrTiXW3EKspC0qCkqSRyIIBB80Rok7OVebnJudm3ph0uqdcW6sqUtxwlS1knmSdye0xVmMPHo1udImyb%2BSbhXoPcYjgqXSlE%2FMqRdCnkoSTy6o3jRtIqicqnQoymN1Syan1hyjS77ja%2Bq6wts77C4sfQecYJOueMDXGX1ZDZpswtDiL9GeqkfL6YxHo%2Brp74rMzqWiI1tdVo6am%2BT2AfkitWXLzcuO6VZT6hEcTshFcmWh9wk%2FJEawyRUGgR%2Fydo%2BsRrsq7UbyR%2B1jz4h%2B0Jj0Ue%2FRpPeIoYiB6JItAY8OcTjkYkAN4qAbQEsInATbyvliISk8jeA9eKhal0QX3Eu5t6VX%2FPFVgWp0sD%2BoiJscXElQQpvQRIcu%2FrHeJUn9AStv1JMBTBudMZNgDCNbxliOm4Yw7JKmqpVZtuTlGki5U6sgD4Be58wMY%2FLsKeeCEbqUbCPoh4PrJujYEwjWeKrMdCJKnSUnMN0Zx7%2B1SiBaZm0g%2B%2BUR0bZ7ybQGy8y6HNZLZPYR4OslgxMY8zAYmJFT6HehDbWgmoVBxzmgKsUIV2AbR6sGYfnuIDI7GPCbm7UKccyMuRJU12oMvh9HShoLplRSsc%2B2Xe%2BG%2FONZZDZpLxDjDOXjtzFbCKfhumpoOGZV3k2479ql2x90E9Cg23JcVHPGUWbGZeTeaaOJSr0GvTtDnqguWxROOSjiZeoS024VPNayLFY3cR52xaA0PijDdYw3WZ%2BhV%2BQVJVOnzTspOS6hYsvtrKVo%2BAj1WjG3UaVER9DfCOZJ0%2BpOUjiVwCW5yiYjal5eszUuLtuOONgyU%2Ft2PNgNqP3aRfcx8%2BZ1hSFG4sQbH0wHhKrG1oJX720RWALHtgAAbwG8ODbFuGcBcSuXuLMZVmWpVHp9YQ7MzkyvQ0yOjWAVHsFzb4Y8me%2BOFVTOjHFXwtiWcmKZP4gn5qTel597o3GVvKKFpssDSQbjzRsbwf2BKNmNjbMLD9YwrL4hKsvas5Jyb8uHj40EgNKbB5OaikJI3udo5%2BxbgjGOXlSbw3jvDNUoFVblm3FyVSlVMPBBHVVZXMGxsfNARbxdiNSrOYgqtvNUH%2Fpx21lnPSfGNkHhjKym43TQs8MolPPYbfmp1bCq3T1AgJQ%2BFaukCbJJuSFIF%2BqqOBukj1SVTm6dMtTkjNvy0wwsONPMOFtxtY5KQtNlJI7wYDq3DPDbxwUWvTmFKFhHG9Ccqrh9kVtVJTMm7c9ZbjgXpN7nrDcxlmfFbwxwz5E0zhgwjipuq4tqNV9seMqnTniENTAHucslxJBvfSDvyT5452f4qOIGcpKqHN5zYvdkloDam1VE3UnlYqACvljWE1UJiZcW668pa3FFSlLUVKUTzJJ3JgMk%2BqLjW2n21Vm3d7JzP043xwNZsS2GeKDB1bzGzGepdBZRO%2BMP1WpumWKzLqCEq1qKblVrX7Y5ZDytViY7S4NMA5Q4%2B4fM2ZHNmmyLLM7V6TRafXHWru0ebnEqblnkr5oQHy3qPKxAMBytmfOS9Rx9iCoyb6H2JqqTjjbjZCkrSX3CFA9oIIPwxikdPeEBy8w%2FlpnRTcMUKiyFKXK4UpCZ1iRZDTLk0GbOOhI2uoi5PbtHMMBWlRqWU2vcEWjsLwhyCirZQMpN9GWlH2%2BByOPpU6XL%2BYiOv%2FCIqtiPKdr7jLSjj%2FeQHHD3MRFEQe5xFBtAdWeDqxtg%2FAmdFansZYkkKNLz2EapLsPTr4abcesmzYUffHmB5jGkJrMjMGXfdaTjrEQs4q9qzMkX83unKN2cNmU1MzJ4V8%2B5yXwK3iLFFKVSPYJbcup2blnFrJWGQne5ANx22jm%2BuUyo0Kov0iryEzIzsostvy0y0pp1pfalSFbgwF%2FZzOzFUsWzBxK2oEFtaavMdRQNwrde9jHbuN6VivjCwFQuILh%2FrT7WZNFoaMM49wvIz%2Fi07MIQNnWwFDpW1DUQk3Ckq23SRHzzQ5F8wvjbE%2BB6yxiPCOIKjRqpLXS1NyEypl1KTa6SU%2BUnYdVQI80B0tgDIvjTxYy5lVTJHHNBw7NL0T6KtNOS9Ml21E61r1m5A56Umxi%2B8V2bFFy9o2DOHnJnGM77G5cSJl5%2Bq02bWyJ6oOWU7ZTZGpKTfttdR7o0Zifi44iMZUhdBxHm9iSbkXE6XGenS2HB%2ByKEgn1xqhydcc8s3gMz%2BrJmoPIzMxUP%2B93z%2FKjqTgkzom2ZbOCWzKzQfWmYwJMM0uXrVWUpLz6g5s0HFeX2WG%2B8cSocBj6G8MnD1kdm3w%2B5Wu4godPaxvU8YTc7ITLySfZhmnvhc1T3L7FC5bVYc7ouORgPnzUyhcwVtr1JKU2Ue0WEW02JvG3uKjDeHMI8QmYGHcI01unUeRr82zJyjYIbYbC9kIB5DzemNPKNjtADtEpN4io9WJeaLwEyOcVIpoipAVWjaPdKbKuY8DXOPez1RAZzQUlVHWT92fyR5qDpOZeE7%2Ff2Q%2F36I9WH1A0FZ7Ss%2Fkjw0clOY2FFj7%2ByH%2B%2FRAY3VtswKve4%2FTib58%2F6pXF%2FwkArN2kjnetSY%2FwBoiPBWKfKM45rcxPTCkJTVZzyBqNxML7I9WXsw1P5q0GYYCujdrUnp1Cx%2B2oHKA%2FSNCEIBCEIBCEIBCEIBCEID8%2BnF0nTxAZkIT%2Bumo%2BvxhyNHq2kRbmUqJ%2BMY3rxiJ0cROZiRtbFVRt%2BMORop4WkW7c%2BjIPxjAZhhr%2BtV%2FwBr%2BePW4206hTbraVpVzSoXHwjtjyYa%2Frb0f7EKi4oQtxSUNpKlqUEJSBdSlE2AA7SSQAID1VmuVnEb0jMV%2BqzNRdpkk1TZNcy4XFS8q3fo2UE8kJubCLdGYSWWdfncv8V5irflpKSwfVZGjT0nNakTSpma1FKUoI2KdPWBsd4xqpUqqUeddptWp0zJTbBAdYfbKHGyRcakncbEQHkaYmJpzoJZBUog9VPOPWaBWU7KkHB%2B5ith95MrWWnXFaU6CCYzdNXpd065tGo77q9F7wGu5ynTkkAZyVcZvyKk2vGVZX5NZg5y1ObpWX9DM8qnoQ5PTDjiWmJRKzZBcWo2Gog2HM2MU8c1KWqLbfRTCV9ceSb9kZRwyV2tSOeGAsNSFZnZWl1vFUgahKsOlDc0Ww50YcA8oC5Fj3wGvcYYUrOA8WVbBWIWm26nRZpUpNpbWFoDgAJsobEWI3jtbJIn6zNbiEg6aTXVXPfZ2OYeJVtSOIXMbpBZftimdSe0GyI6gyNuODdev3lNr1%2F2Vg7vHzT3UPm%2B7T3raPuVuthHxlf8s%2Fg5Gy3ZU5kvWl2FmsRSKie26pMj80e6QTqd097bn%2B7VEcq6XVmso69Upis0JmiPzMkTTn1qFRmJsNHQ7LgDT0aQbK1WvY2jzLmBKy77xBNmXBtz3Qofnj6RZxnS5U62nMW6QzSwkBJMmFkA7glR5xjIeIVa8ZtmpgSrZY44qmAK9PSc7PUUstuzEooqZcDjKHUlBNjbStI5c7xgiuq5FoQ9aJi%2BxgtQUb3jyhUR1HviR6Q6ALbQDoPdHmuYXMB7ErTzvFUOJHbFv1K74iHFdpgLil9zRpT33joRRS2pxd7dIhe%2FcC1v%2BWNL5X4PTmFj6h4IdrLVJbrM0GHJ11tTiZdsJKlr0J3UQlJsBzJjbrk7LlkzFy4zocSlQSUladOkK0ncX2NjygNJV0IApxQtJBkUGwO6esrY%2BeLKXTqIjN838up3KbMOrZd1OpytRmaQmWvNyyVJbeS7LtvIICgCCEuAG45gxgZ5wHrS92Xim9ZTyTFDURfeHSXse6A94WkclCJw4PuotoUe%2BJwu3IwFyDo74j01ot%2FSkdsA6b84C5iY7o6ABWlaHkjfogrn%2Bw3jTGV%2BD05iZhUDAblWTS269OolHJ1TZcEug3Kl6RuqwB2HONyuzLUuha7goabW0CBbUAkp1W7L2vbzwGjMS6A5KFCkm0k0k6e8Xiw9OL2uYznN3LqYyozAqmAJupsVFdORKuCaYQpDbiXpZp4WSrcWDlt%2B0RgF97wHqS9be8UgvU9eKd7wHV3EB7UuGKqXT3xb%2BlUIdKqAuXTEcom8YPfFtS5fmYqBxJ7TAe5EworSL7akn4Lx0G5qXiJOtVtSlm%2FcCybfJGmcrsHN5iZhULAj1T9jma3M%2BLuzfRF0sNhJUpQQN1GyTYdpjbL1UZNUdnRqWyhC2wSjSop6IthWnsNt7d%2B0BpPFKmlLli04hdpNAUUcr3VFkbWRGfZ65bKyfzMrmWyqy1VTRfFgmbbaLSXUuy7TyeodwQHbEd4Ma71kbQXe1LvYYpJKemvFHpfPAKJ7YKPb0o%2B7h0o%2B7jx%2FDD91Ae5Lgt5UTpc25iPAnl5UTpJtYGAucm9qeaTq5rR8qhG5JyyZtY84P8ERrjKnBkvmFj%2BjYMm6x7FMVEu9LOBkvKZQ00t1RSgW1GyCAO8xsGeebmHXHZfXoUfc9YsrTYAEjsO28E5six0LcL8gQL6syXCT3EUsbfnjr7geUFcOdK8zdVB%2FGDHOFHydxXnDkfiOr07H1HplDwTV26h7AuyTgcedcYS2ZgvAG6yApIF7AD0R0lwTBaOHamNuJAKG6qNu39FkX%2BSPmnuj1RvOzj%2FMp9VTt4RrqnyT64cFTYtUJgd0w%2BP9oqOgeBy31aJ3nf2vzn8ZuOfZv%2BuEx%2FnD%2FwDvFR0FwOf8dE7%2FAPb85%2FGbjt6afMFv%2FLsamH%2FKafOuWeEsZjivqjF7dNli8B%2BBVGh58jxR5CdgWiQfgMdBZy0rEda4yJGSw5VcO0p04MbROTeIHFJkRJdC6XQoo6wUoDSki5vGg6oiVdnZr2MChKqWroAokkIJ2FzuR3HujZ0NnPArt%2FLDDfPj6vOxnMdKFjErje2h2QQkdxLCCY1Qlelwxt7OPBlVpNIo2YzlQYXSsdTE54lLtvEvMmQLTDgfRawuVgpIvtGnFnS4Y9O1Ht6dWkR5plxLzo1dkUjMKSdPOJCsLVqgJlE6xbsj1JX1RHj88VEL25wHr12TsINvEHkYoBe1iYlK7HyoC7NTqlEXJ5GNnUMasI0h21tcu%2BoecF07iNPNzaUnUoEpRdVh2%2BaOgMQ4Icy5Mlgd2uStXmZCSQ4%2FMSra0NIdmEh8sjWASUBwAkC1%2BXKCc2FZnoC01F9YBdbrCGFEDulUH4ez1RrlExaNo50YAqGG6XhvHyqpLzFLx2J%2Bcp8uhxRel%2FE3hLuB5J2BKhdJTe6SO2NS3HfBMTm9qZtViOyPIty7pVEheAOmJFEc4Kq%2FSCIFYMUL%2BeJr7QFVCt49CVgR4kqIMVOk88BdG5xauZjbFDbV7XKY2rkGV9naVXjTCZlLIDp5COhqzgx3LtUngyarLNVnKdLNLm5llK0t9K8hD3Rp1gFQQHAnVyJBttvAa9zZbIm5qYCT1Kq60D2FPi7XL4TGv0OWjaueeBqphuXoGOpipycxScetTtUp8u04ouyhYeEs6h5J2BKkAi2xBjUuoDtgK5dOkiPKXLKJgp8cook3MBMt5SonaJPOKQQk%2B%2BibQByXAeoKIHZFRt4tb2EeZJsB1jtEQ5q6uqAubc4TyjbMsgt0emg9ssbejWoRpmVWpMw0lKdRWsIAvzubRvvFOE14DqAwQ%2FiFqsz9DlUS0%2FMstLQ0iaVdxbKCrdYRrSnXyJvblAa8zSZDc411bFE3OIv3i6D%2BcxhKHCBGzM6cvqvhVrD%2BMZmpy03SsdSUzWKYhC1FyXQ1Mql3G3EnyVakX22IMas6S0Ew9JmFaSLR5tZvyiBdHfEptfZUEJ9Vt7GJVLPcYha%2FbENHnMBBLpC7x7WZog848JSAq0ToVZUBfZObWp1A1e%2BA9ZjakoCmnyiVCxCFAjuOsxqGlNuzc%2FLSTSglcy82yi%2FLWpQSm%2FmuY3fWcMTWCp97BtQqctUZ2iOLk5qZlVFTK3Qs6tJIBNr2vbciAybBYR9SrPDUd%2FaS1pH%2FAHhLxnvg2ED2RzBWVkESlIGnvvNK3%2BC3yxjGVeXWYGa9MxRlnleMOio4koC2qmKtO9C85LszTb2iWB21dRJUTewJjOPB%2FwBGnMO4yzIw7UpdKZqTapTbikuaglaZpYI22I35%2BaPF6dTlgtv5Yj71LrYT8pp%2FrkYXxhg%2FXEYrUeZ8Ut6Oh2jCcqB%2F8UcGf%2FcMh%2FvkxmvGF%2F8AUPir9rKf7mMLynbU7mpgptHM1%2BRPqeTGzTP%2FAK1Tn4H%2FAIMNPyv%2FAHR63T%2FhDP7D8Ed4xux%2FuY5vzfbDWbmM0d1cmj61R0z4QGRqNSwZhKnUlDJnH8cMNsKdHVS70BKLn7m%2FPzCOe876S9TMwp6XrNXw%2FUq%2BOvWZnD7y3ZByaUdR0lYulYBAUncAgWMcz3NpzwKn%2BapbFI%2FtNTAsVLScBSSHHVaUOVSySdgohm1o0u2%2FG76%2Fgyp4tyvrlepE5LNtZeNKqlUZeUUuTDM3MssI6G2yigjUoG2xFrxox0ho7x75zsnoTMkE7xSLl13JjzKmUg7GIdIFciYIewv7WimV3jz388R1GA9SHLDnE6XyDsox49ZiBXY3gLmH9oz7LcKXRcQOhQAS5KoIPb1zGr%2FGDG7sGYSkaDlhT8ZjESZicxZMTUsaYJZYMs1KPAB4unqq1EkWG4gLdjhke1eVUVp3TOKsedw42Nv%2FAH2RrDpI3PiXAisVZS13MGUqjDCsvnpZE3KuoVqm2ahNBtKmyNgUKSNQPMK25Ro9bloD0%2BNOX0k7CJ2DpRFv8ZRAuFW6VqA9MBc%2BmHfE3TJPOLSHN7a1RN0n7IwFyL1uVoeMkDmIt3S%2BcxKp8jlAXDxlV%2BcbDy3Acp9TPcpkeomNXNOlSgPPG68G4YksO5dUfFZq7kxPYuL6zJ%2BLKSiUZlXy2FFw7LUskmw5BO8B5c0UobwpSU3AIS%2FpF9z%2BiN41P0x743jjzBDOKcoZvMiWqyWX8DTcrTJqQcYP6Ian33FNuoWNrpU2QQey1o0Ry3gnNUefKkHeKzEwA0ATHlK0kERR6QggCCFz8ZTDxlMW3pDDpDAXPp0kXBEUlzCwbBUeHpfPAOjvgPZ41GzMuujXhSpOEpKhOS6bX33CvyRqhKwVAd5jeNCwhT8J5e4erjFYfm57Gsr7KTEuqVCGZRtp91lKEOXu4slN1bADzwFmzSS2jDlISpaUq8TCwnVur9FL3I9e8aw6RUbrzAwLK1vKB7NdurdHMYcqsjhd2nLZv0iJkPvpfS4OVijSUkee%2FZGjtfngK5eITa8SdOodsUCs6rCBPp9cB60PE8yPhioHTbmIt5I7bxG6e4wHsW6b7RL05A5mPISOxRiXWEna5gPcmbUe2NqZchK6M48hQVrLeq3YdxY%2FJGn0OWJMdC0vBdLwNhigOSVWm56ZxRQpGvTfTMpbRLl0uJDKLElQSEDrG178oDY%2FD0EnPPB211pmppSO64k5iMC4BXHUZ%2BUoNEEOUWpocVpvZBbNz%2F774yzKGkVDEePKLhqhYwmcJViqVFEtKVuXkRNuS4W04gpSg8iortq7rxcOGHLZ7Kji9qGAjV2J9VHo9VlRNtpU2HkhoDUEncHbkfPHB0mnLC7aZ5s%2Bpv4flviiPKyvj9B%2BqXg1V9vaigf%2BIVHMBHaI6e4%2BxfM3CKrWAwi2Ldx6dV45ijBodP7Du%2Fmn70sV847xX55U1RBIMRMTJTfaPStUsTyh0avPHQxyHwOOFnBWcKX6j7P1%2FFUlRplPTDxfoHZ5bCwlNrhWhOxva8Z9nDk3wY5JY1GB8eVnHrM67KioIMpZ1Aly8tsDUE%2BVdB258oDj0IsYLFov9QpMjU8bP0DArczNSVRrJkaEJqwedZde0y5c7lFKk6vQY6cVwo5CMY%2Bl%2BHeqZtV5rNV%2Blif8YRJpNMS8UF0NAc1dVKjpvcpSTz2gOQomse6N0YFysyooAxhOcR%2BYisOP4PqTlJOHaWA5UKg62E6nmwbnoiVp02F1b8rRkGbHDLQsLV7LJ%2FBuOFt4YzQV%2BhZnEKEyz1LAaQ8VvHbqFpy4uAQoaTzEBzvY90QKTztHYFJ4Usgcf1rEeWuVubtWqeNsN01M%2BuZWyhdMfUvZA1J97qISbElOq%2B9jGAYCyUyxpmR8ln5n%2FX67SqLXqgKdSqdR2kuTH2xxBmFKPlJ9xdUAB5Kb9ogOfIpuJ7RzjcHExkS7kDjiVoEpWlVuh1qnpqtGqKmw244zqCVtuAba0kpNxspKwe8Rp4nULiAkhCEBPCEICNh3wsO%2BJbHvhY98BGELjvhADygOUDygOUBBUQTziKognnATRScirFNyAo2PdEEjstFQDaIAC8AidESnnEyICdCwOrq1J88VELDpOoqB5gpUUn1jePPEw6pgK6nXSnQJl8t38hT61D1ExTuIgF%2BbqxTuekt2QGW5f5m48yunqpU8A4kepD1aprlIqOhtK0zEos3KDqB0kHcKG43jFEaEIShAsltIQkdwG0QhAT3MLmJLmFzAetyqVN1gyj9WqDrB5tOTjq0Ht3SVWPIc48q13iESQE4VFQKBiiBvFQcoQOg%2BF63sXiopvqSpnke5pREa2wHUq1KcWE8xSa57Fy6qlNzE%2B94sJgGWaZWpxPRm2okCw3FiQY2XwrFJpeKirmpxq%2FwtrtGocN1GWo3FHUHagmZ6GbnajTi4wyXC2t5ktoUQN9Ooi57Bc9keauc54vb%2Bj8H2DSH9HQa4fzR6q2YstlL6OppFtQTe9gd7Ra%2BJ5gPZaZUT6VqsBXpYp7LomGlX%2FhRe2wrpfdEgKAsQOwjaLTxMq6LKrKqWCQCo4hfJ8xfZA9ZHyR6V8ehzN0oiHSCPNcwuYJVlObRTUsntiQq74l5wFTpbdsTdKTHnUqxhcwFVTl%2B2KsmgPNvlxZSlKewXjxEk849UqFFp4p5FBgOsMZyxkJjDNNUrUZXC1HTc9t5YKv8ALGN8RMmpnLjKKpBd236fXkJ86kTybn%2BGPVGXZjME4ipL5VcHDlHt5h4m3%2FPFg4l20s5R5MNJvqFLxC4q%2FcqooA%2BUGA5xS%2BB2xK6%2BDHkKiNolKj3wFZT8SF0xTJESlwCA9CXSIKcvHmLgHZAOgiAqrcvE7DMxMSzzqFpAbQdQJ7I8pWTFzkP6kf8A2SSn5IJh1TmGgtYjpssv7bL4cozTu3vhKI%2FMREH8QuYXyjxlVZWkpqTjsoinzCS%2BEeKMTKwjpyOawFISmw5FYJ2j3ZuISjMKZQnkmn00D8UaiwYgmJKTyUx%2Bt%2BYaacmpSRlmkrWAp1fjSFaUA7k2BJA7BBEN78AhBytmyAeq7P3t%2FkSY4kq5StpSm02SSsp9GtUdt8BaQ3lBOuquAV1Dccx7kY4jqH2k733Xv39YxvTGWHWf80uVYT%2B0bbzQwxSoJVBSYJTGi6qYJKuyIhsje0ZRhnBFbxQ6pijyD8ytBSlSWWytWpWyUgDcqJ2AG5jpjJ%2FgjfxRR5l%2FM2qzWFarUEoGHJCZaCEurBJUZsHrNIXbSkgXvcnlaA5DQCT1Re3dFYMhzbt7o6ZncLOZcVGp4IncK06Qfp7ymJmXmJNDryB2XcVckEEEKHMER0nlBw55KZyYFarWJsFyzc5NO6VzVOWZdbZQ0G0gadrbBRFt1G8B8zlS9jaxiVTduyO2OIfweWMMrKJMZh4Fm3cT4Sl%2BtMrLWmdp6ACS48hOxb28tPwgRyFVqQ5KOKS4m1t%2FggMdWCIkj0OoAihYQEIQhAIQiCuUAuO%2BPTJy7s5NsyjCkpcfcDaCpVhqOwuezewjxXMVUHvMBcKpTZylTJl5xlSFgkEEciNiPgNxE1Dpz1Xq8rT5aTdnHHV9WWaNnHrC%2BlPnIBjJcLPSGM5iVwtX51iWmnlBmVnZlzQ2s26qHV%2B9N9gs7b2PfGJoamZWauyp1p%2BXeUEqSopWhaTzuORB7RAXyrPU6s0VyqU7BvsOiQfbl3JllaltLUoKIQ5q3S4QkkW56TGOxcK1UKtOuaao%2B4XHCHlXsOkvuFKA8o89zvvFsgL9hQXn1H9hGYhop2EXPhcymOceY68Ku1dNNlWZF2dmXtOpZbQUjSgfdEqEdiTfBTlFJr0TOMa22vnZUyylXpsYDimIgG%2FKO16dwXZJTKxfGtc0g73mmDc%2BmL21wQ5GqSlKsc1lRJ2vNMgiA4VbuG%2BXbEUg7m3bHfknwKZGTA6NONq%2BpSuQEwydHn88XVXAVkM%2BdScW4kTsLhMwza%2FqgOGMpGUzGbmA2ngotqxTSQoDnbxpEezOZXjecmYE7e%2FSYpqxv3%2FopwR3JROBvJTDWIKRiWmYwxOmdotRl6lLhbrCkKcZdDiEqFrlJIse20SV7gfyRr1erGIpjGGJUP1ioTFScQHWihpx5xTi0p23TqUbX7ID52oaXbeJC3a8fQA8AuSJTcY8xQFA6r6mCLdot3RIOAjJEBV8eYkST5JC2NvXzgPn%2BhtTh2ipYoG8fQBHAPkzp%2Fs%2BxGv0mXF4t03wCZQLUEsZhYkZN995dVxAcHE3iVThTHe7fAFk%2B8nS3j3EylW5pSwqOV%2BIPImr5EYrl6NN1FFVpVVlzNUqpobKOnQlWlbTiPeOoJFwCQQoEQGpn3Stlwq7B2R1zhObWjDNFOnSlMhLIB%2F0Y%2FPHIT%2F2pfoMdY4WdbFAo%2Buw%2FQUv1SbkHowNvNGSxj9ZE%2BSfwYrx8V6Y%2FFtjC9VEpPSjzixo0lKxbZV439lNjNxS14SqTiT4uCqnO%2FqkvzSk95Te3oAjliVnnUdA4hG6E6VJ7oyvC%2BN2qdONmcfcadaWFSr6Sfc1jkD5uyNuf0uNz7OdzLsZcx3Rz9VODXKmuZj%2B3OpIdFGcfE9MURse5TkwPeOKPW0KPWV2m1uUZ9g3MunYhT4jMTUuidbAB0LFnPOO70RmCpxLbImFqAbvbUeV%2B68Ks6qZo5J1tiiuKKotOWGtuIpvCcjgCuYhqGFKXPVqclkyMvNvy4LrST1QlChYpSlN7Aco4nredGZv1O6jlI%2FXkCjVR9tyemUS6W56aYbSEolXXU21NgJFzbURcE7m%2FYXElXqMrLialk1GWW%2F4w2A2Vgqub8o4EqctW8Q1FVFwlTHanUF61pbRyQhIutSj3JHO0dCmmi73emqYyqza0UzebWrljiYTiaYcMqmQkUDp5shlsDsPzR6JGnIkJJmntbobG5PvlHyifhi4yFDRTNU1UHPGJ0g3NrIR36R3xFxaOk5RzbXOqc5b1NURG5hbajc0%2BYCEeQ2q%2FwCy2tGKNnqiyQYzabUwqRm27ElLSjy57RhTKCUjeMUrwwXEi2fbJPOLQFBBQLE9mkRccbSDUhiFuVbc6QKk5Z7Uf2baVW%2BCLFiZROIKmP8AGW%2BQRkWP19JiCXdH3uk0fFZAjBLLDOMkRhRjGVJXi3DKcR0xKleMUxUyZYPgoUB7qkXSUqsrz2tFuzBYoqanNTFBpBpss88pTcot7pwygqNkBZAKrDa57o8uWzmjEFPP7O3yGIY0c%2FRCv25%2FKYgYyl1QAQpthKQLWS0kE%2FDaPNNOtN6dDbe3ZpERfd0jnFumJiAuMvUmUuITNB1LV%2Bt0CUBVv3Qj2uVLCqG0%2BLSlaDwB1LMwyAru6oTtGM9IqIdJAZDNVOjzKtT1KVNuAaUvTbxUpCbWCQlNkxb3nW1rAaASgAAJHIWi39IYrsuCwJ97uYDbXDtk1V8780KLl9SitlM%2B6XZ6aSNpORb6z7xPYdPVH7JQjsPwgmcFHwdh%2BicMGXAbkqZSZWXXV2mbWZYQn9DSW3M2u6sd6k3jaXAdkfMZWZFqzRkqdJ1TF%2BPpET8oFvBLSJNOoyrCl%2B9CljWv0Adkc%2B4s8H3xV4yxFUsU4kewnO1GrTj09NPGsgFbritR7OXYB3AQGN8NWdWcWIqRReGLKijYFlHpp2dqLM%2FWpEzS5maSC9qWlfuaXAlOlCiDbSOUZv4SbNLF72J8O5PTDczK0GhSDM6VKKW01SbW2ErmC0jZKUm4Qkj3xI7Iq5S8D3FblDmNRMzMOyWCHqhQHXHmGJmsXadK2ltkKAA2su%2FwCLPi7gD4uMd4hqGLMVzmGajVqo%2BuYmpl6uBRWtRvsLbJAsABsAAIDP8AgJzMw5m5lViThJzQKZmXbpr6qQlZut%2BkuEl5lF9y5LOkPI7Qk%2BaOG86sra%2FlBj2uZe4mSFVCizSmVPJFkzLR6zMwjvS42UqHnJHZHUuCOBHi7y2xlQ8wMJM4VYrOHZ1uflHBWkWUUnrNKFt0OIKkKHcoxt3wjGSoxrlZTs9pWioplewq1LylZly4FdJIPmwbCx9sMu%2BohJ7W1nugPlg6khUUzzj0TIAXFADe8BdaDjPEuDJ0VbCtdqVHnggt%2BM0%2Bbcl3dB5p1IIJB2uPMI9GI8b4lx7NorGK8RVWsTzTKWC%2FUptcw6EC9gFrJOnfl6Yxt5tRNydoqyrdtTh0pPk6bbmA9IVflBJOoxKAb90X%2FBmFKrjXFVIwdQmm3alXJ1mQk0uL0IU66oJSCrkBc84CzxIu5PojeVN4SM4apUK%2FSGKTTmZrC%2BKJbCFVS%2FOoQlmfmFlDRCuSmioW1jYXjUFcok9h%2BrT1DqrKWp2nTDspMJS4FpDjayhWlQ2ULg2I2MBahzj3SmMq1S6bPUGRqU61TamG0z8m3MKSxNdGrU2XEDZRQrdJO4PKPIj7ZuIt8xLrbcVaAyivYxxBjOZFZxJX6jWJxLaZfxioTKn3ghAslJUrewGwizdJcxQlB0cur9lE45wHsk917R2B4RgacYZYJ%2B5y3pA%2F3kcgSAJcFu%2F88dgeEfWFY4y4SnknLuj2%2BHpYDjhfOCjbeC%2BcSuC6YDIsH5v5g5auTYwFjKt0BE8E%2BNimTqmOn03067cyLmx85jx4ixZXsY1N3EeJqxN1aozRCnpycc6R52wAGtR3VYAD0ARjRaU47oKTaPc20W5UJ5m8BVDhMTXvFFPIRm%2BVOVGM858Ws4Fy%2Fpjc%2FWpiXfmmmFupaCm2Ua19ZWwOkbd52gMOtEtzG3sMcMmbeM8JU3GuHMPsP0qrs1R6UW5ONtLX7Hi80kpUQQpIuQD5VjaNSPo0GAkDyWuss7RfaVnDjihy1Lp1FxRWJKSoU8upUplmaKRITSvKeZA8hSrm9tjc35xjziOkbUi0WzxdcBleJcR1rFtUmsT12qzFTqFTcVMTU3MKu666rylLPaYsd7qj0NsqakWwVeSnceeKI5wESkkREJ2tE45RAnsgJeUTxJE8BUbFjePc1ciPI2No90snvgM2w%2F8A1kA71R56DpOY%2BEwRe9ckBbzl9Aj00MaaKfMr5o8eHVE5k4TB7K7IH%2FbpgLdjyk1Gg4wr9Lq0spiYTUZtwAm6VtqeWUqSrkpJHaIZR6VZl4YSO2tSQ%2F26Y2DU5mg12YqmD8ZFDNNTUJw0urAEvUZxT6zuRuuWUT1kHySSpPaIxTAeE67g7OfC1DxBJKaeTXJDo3UkKafQX0FLjaxstKhYgjmDAfo2hCEAhCEAhCEAhCEAhCEB%2Bf7jTTo4k80E92Jp8f7ZcaDeJEk0DzLZP8KN%2FcaySOJLNA%2FdYpqH%2B%2BcjQTydNOa7w0bfG%2FngMuwxcSgBP9qH5Y3nwiStNm%2BIvCstUJWVmJjoqg9R0TQBaNXblHFSVwdielAIB98BGjcOD9B3%2FwAWj88XqUmpunzkvUadNvSs5JuomJaYYWUOMupN0rQoclA7gwGcLzJXLZNZl5b4%2B9lH8aYnxjTa3OTD6DZLst0vjRdUdw6Vq2TbfsjL%2BKmZqtRcysrOMUKRjuo5fyD%2BK%2BkGl9x%2FWsSzr6ex1TAQT22tePKvijxPOzMviDEGWmAa9iyUALOIp%2BnHxkui1nnW0kNuuCw3UOe8aqxLibEWNcQ1HFmLaxMVWs1Z4zE9OPqut1w7egJAAASNgAAICzlLi12QCSewQMtM9rDnxTF3wwQmuM3IGkE%2FJGfa0r98Pk%2BCA1QphaCCpCk91xGQYFoeOa1iaTTlvTqvOV%2BRUJ2VVSm1KfllIOzoIHUse0xdcbpBpssoKQVIf97z3EZ1w5LztxT7NZO5RVpvD9MxEtuZxLXm2NL9Olk2AUZkEKQCE2S2N1KJ85gNU4rkcU07EM81jaWqTNdcdL08KiFeMLcVuVrKt1E98dq5F%2B68HS0KFlex1fT6g6RGj%2BLzMnCOYmOaRRcHzExVGMFUwUKZr0wizlVfQRqcJ98E6bau0qVbaN55FpUeD0BkalKp1e2%2BB68fNvdNym4XaP8ANj7lbrYTGddf8suRcua9SahlwrCPjpTV2npafZl%2BjVZxltlWo6rWB57HnaD7C5uWflWra1trtfkAEkn5AY9WU9SfkshMVJllhpU%2FXaVLvOpQnpFNBhSw3qtfQVbkAi%2B0eVlxWtRBI1Nucjb3io%2Bj2epyp1sK4i8ZYczBzkxLjHCM69OUeoqlPFH3WFMrcS3KMtKJQrcdZChv2CNUOeXGUYklmGDJKl29Aek2nSm97E3jGHB14mEKRVvzhq88CkXiGkRIn1emGr0xJpENIgKmvzQ1%2BaKVjCxgM9yXxTR8GZo4bxTiCYdZp1PmyuZcbbK1IQptSbhI3NioRs1yVfmkLkpYe6LQsNJPL7WSPgtvHPLd1KCTyJAjpchTNQcSysgt3Tq9DZB%2FPAa%2F4jca4fzHzoxFjXCs9MztJnm5BEvMTEuWFulqSZaWejO6RrbUB5t41U4Te8ZLiGXYZMqZdJAdlULVc361yPzCMad2O8BT1w1xLCAnDkTa4pQgK%2BoQCt4pX88Rue%2BAzfKHFVGwbmhhnFOIS8KbTZ4OzJZRrWEaVAkDtIvG3HZd%2BoHxaXI1zAVoURtbSVXt6Be0c2oN3EDvUB8sdQoW03MJBVobbQUjTuQOiIA%2BW0BrTiKx3h%2FMrN2uY1wquYVSp9mnty6phro3D0MkyyolPYCttVvNaNVLNjF%2Fr0q3KusIZbCErlWl6b3sSDcfJGPuc4CGvzw1%2BeJdJhpMBOHPPEdcU9JhYwFbWO%2BHSeeKUOUBn%2BSGMKJgPNnC%2BL8SuTCKZTJzpJpbCNbiEKbUi4T22KgbRsiXkpmdnjTkkFxYdJWkWSQEKWVD9yL2jn2X677Q%2B6cR%2BUR004ywMQvo6MdH0jiFJ%2FYloiA13xMY9w%2FmlnVifH%2BFDNKpFVclUyiplnonVoZlGWdakXOm6m1G3cRGpnNoyXEMozKtSYaBAclEKNzffcfmEYuvnBdEKiYLikBaJgIKKmuGuJdJhpMBV1%2BaAcIilYwsYDOsm8Z0fAuZdGxRiFMwqmygmG5nxdIU4EusON6gDzsVg%2BgGM%2BPuGvWL9ELHTvtbsjSNLQh6flG3RdDky0hXoKxeN8zKEidmwB1ekUPgEBuLA%2BemW%2BT%2BS%2BYOXuIjV56v4rMkmWEjIqVLMOobKy2p5VkqIStJNrx0BwVumY4cqS%2FYjVLVS1%2Bf9Vq%2FPeOQMyVrRwu0JgHb6oTi%2FhNOA%2FIB6o684JSpXDZSFKI2laikW7vG1fPHzT3SIjedlOWu0pjsqdvCeLd%2Bb8YcCu%2F1U5%2Flnf8AeKjongZRqzon%2FNh%2Ba%2BVbdo52d%2Fqpz%2FLO%2FwC8VHRXAvcZ0TiveqoEwD8dFo7mmfzDbx%2FDHrhq4d8pp864Z8Yiw%2Fhfi1RPYiqiKfLzeCpeSS4ttSgh9xLiUX0gm1u23bGi54GRemEOkAsatRG42ubjzWjobN%2FXK8YEzUEMsqclssXpuUU42lwtPIZUEuJCgQFBQuDbawMc4LedmnZh6YedmHHVrW446rUtxSiSpSj2kkkn0xm0LiIwO7Zc2GC%2Bz%2BuqnyqufWIKEcust8AMTalYhwy7XXqzKlCh4p408wuXSSRYlTaSo25dsc%2BvKPSKjbGY7SHpjEU47d6ZTUpdvplqKl6Qwm4J%2FwDfZGpHidao9S1VMub7xDpIlIN4hAVA5E6XN4oRMDbtgPRruSL8okKwQTflFPXYk3iXUbEd8BVWeoofsY6dzJxdQ8ZYvfxRhycM3TqgzLLZeKCi5blmm1pIO40rSUn0Ry%2F2WjddJYEthTD6GwAhdK12H3SnCVQF74gMW4bq2XuV2CKbNvOVvCEjWm64w4wtHirszP8ASstgkWVdsarp745%2FWoiNm5ktofeqtWdSVTbtWLLjhUSShLCCE%2FASfXGrlkd8Ewa4a4pWhYwQr3ENXnincwue%2BAq6vPDV54pajDUYCo4dTRTfsMdPY8xfh%2FHGLKnjLDky4%2FTKkGSw6tstqs1LttqBSdxZSVD4I5c6SN60tEvK0OlSzDKUNmRSrSOWpQ6x%2BEwFx4isWUGpYOy4wLJTa3atgym1SWrLRZUhMs%2FMzxfbaCiLLPR2JIuBe0aBLt9rxsrNRtDj01UNRU%2B5U323XVKJKtLLWm9%2BwRq65gJyokw1eaKWrzQ1eaArhfniYLtHm1RNqMBX6QQ6SKNz3Que6A9cu%2F0LjThP2pxLnqIMdI5lYjomMMf13FWGqgJ2kVuZE7IvaSlSmyhKSFA7hQWlYIPdHMfSdkb6VKysmxTpeSYDTSZbZANwCXDf5d4CrxA4xw3WsI5aYUpk249V8HYfn6ZW2S0tKZaacqTjyGwpQAWdCgSU7C8aG6T0RsPN5lgVR6oMg9LM1Ca6VZNyuxRYn0DaNbwTCfWIiHLRT%2BGHwwQrB2Jg4I88TC8BVUu5vEmsg3uYlJtEpgLtQqgxT6zTp6aWQzLzjDzhAuQlLiSTbt2EdFY%2Fq9KxFjevYjoFRan6ZV6g%2FOyky3ezjS1qIJB3B7weUc004IXUZRDiNSVTDSVDvBWLiN8IlmJSXZZlmktMgL0ITySNahYQG9%2BE%2FMPLzKLHUxjzM3GUhQqc9QqjIy4cClzDrjgSgFCEgm1wRfzGL9wN1KUxBmRmtW6VdyReVSuicPVNlTTqgbegRp%2BjyspPZE5zOTlOlplclh2RXKOOMpWuUV7JMkqaUd0E3IJHYY2B4NZDnsrjtek9GW6Qm%2FZq6Z3aPGafU54HbTy%2Fo%2FfpdfCPlEf1yMR4uyfrhcXpO9nZY3vf%2B0J2jEMows5tYHUkK3xDIDb%2FACojK%2BLb%2FwCojGO%2F9sldv9AIxvJcFWbmCEWuFYgkgfjxn1aM05%2BB%2FwCDBT8r%2FwB0et1Rx21yUoeHMETtQuiVTjxqaecsTobal1FR235K7O6OV8wpmSqWL6pXKTUET1Oq027NSky3qAWi9iCFAEEEWNxHS%2FhDEWwVgVh9IIm8ay67XuFI6CygfXGhM%2BqjMVLOPFbj3UbYqDsuywlKUNsNpOyEJSAlIuSbAcyTHN9zincYHTnr3VXrWxOuZvFUd5Y5fENCwxk5mhT67OeKzWNaPKUygtdGpXjj8vUGHXxcCyQlve6rA8o5rnXda9o3Rjpht%2FBct4wDrlFzLrB1EBJUWgdvOI0g5ftj3zQSRFJtFOEFFYORNriiAYiATAVS5EpciQi0SnnAVNd%2B2N%2F4TxNQK1k9hnDUjNqVWMMOVIT7C2ikBuZmEracSrkq4BBHMWEc9xtjLBttGEajNJZT0jk602tzt0giw9FyYDYlQxPh%2FDmQ%2BPcIVN51FWx07Sk0VptlSkOIkp4uTKnF8kaQU2vz1Hujm2YcJ8mNxZgNJXhKmvuJKlSzc8UG%2FkXeavt540utRMBAHtioldooRG5gK%2FScoFznFC5iIO5gKvSRKpztiWJSICs26QQY3phzFtIruWGF8Mybj4qGFWZ1mdS43ZChMTZdZKFe%2B2vfuMaEBtG3MsZdr2oTM0lpIcVMJDirbqAcIFz3C3ywGeYkxZRsPZFYrwfPmZNTxpPUuYpaUNAtBinvumYW44fJOpYSlI3POOc3H7Hqm8bXzPZaOGqZMlsFxtp8Bf3QL9tx6BGn4Cr05h0xilEL%2BYwFbpBDpBFKEBOpcQDhAiWJVc4Csh1QUD543zRsV0nFWXGEqbI%2BMNzuEpF2mTzbqLIWXJl11tbar7jSoAg23jn%2BNzZeNtpwEgttIQpcwkuKA3Wbucz8EBluPMa0mhZCVDLN6Uml1fFlepuJJZ9CR0DclKImWXApV76y6vYW7L9sc6rdjbOaLTTmHJJ5TXuspLdEkn7lT6iR6941BATh098R6U98U4QE%2FSrh0q4kuqF1QE5cVEpcVbnEpCokIV2wFdDkdB0nGNNxrQcO%2BJNTTD%2BH6DJUGaaeSNLi2S4embUDukhSRvY3Ec7XtG88ApYbw1KdC2hJMs0pZSmxUolVye%2Fa0BtbJ3EMhgTHVGzBqlPrFSlsP1Jh4yNJlg%2FMvqCVrsEkiyQG1Eq7LeeL9w7Zi0rNPjRn8aUCQmJan1KlVh9lmaUFOISpF9yna%2B8eXhueeZzsw49LuFpYM2lS0qKbJVKPJNyOzeMK8Hmm2ewGkHThmrC%2Fd1E7x5zSycsHt5%2Fhq9TfuHFeaKu9LbnH4NOaWFUj9abXyPK5euOYzyjpnj6Xqzcw43v1MIsfK8qOZlxTQ75ju38v4yx33it6%2FOp3uYrNbuRQsRE6FlLgj0zUdnNtvPcAWVRSFKC8waTdduaTVnh%2BW3qjdHENU%2BIyTzRDWUWSWGsX0kS4dVO1amIfdanlPuBTQUojqhIQbd5MfOeVr2LanJSWD5ar1eakhMo8RpbL61Npf1lSC00NgvUSoEC4NzGf4jPErgemiu4sncwqNIrcDQm5uZfS3rPK6ibAnv74DCHEYgwpjpB9xpGJKLXgq00AlqRqLc1fS52BtLhKT2BMfRLDLNTxDxBUvFGPeGmew1jD2AX7JYtNVamaRLyaUqsWXEHSpxRUUJJsoNnePnLT6NiDGlaXTabT5%2Bu1WpFx1bLaFPvzJO61KHNXeSYzyhyHETiKVqmV9AfxpUGKCkS9SoSJlwiTRfSEOIJuByGkmA2PI0DNTGGOMf8AFdktQMPYtakcTVVlqjTbaZyYdaWEspWZQ7q6mlaTe9iSOUZjxbZf1%2FMKqZLSipESWZmPG%2FYefw87NFclKqSyh0uBB2aCHCpCrDrBPemOfnsH58ZMuO4rVQcW4N1IDL0%2BwHGGyn3oWU9Uju1RZaXU8xcb40lZ2nVCv13FrrhXKzDb63Ju6EklSCN02F72tAdqVHKPH2QWT7uW%2FDhgGfxNi%2FFEutGIMVttobEukoIX0QJBHVKw2gbJ3Wd7RqzGGGa3nbwAZU0rK2kzNdqGHJ5NGqEnJp1PSr2mZYJcRzSAVtqJPILvyjTkviriHncTLwTT8UY7er6HSy5Smpl0zKHALEFPNOxHrj3P5e8TOQ8hNYnRRMWYKp82hInpuTeKGVA7Dpgm6QRe2pQuL2vAbN8INWJRGJcvcAMvNPT2HMM6qiUKCuicX0TaEG3IkMqVbuIMck2tFzqlQqFTqEzUKpOvzc5NuF2YmH3Ctx1Z98pR3MeBSRAUIRNYd0LCAjCEICUqMS6jE%2BkRDTAQhE2w7YjAIRHT54afPASkgRAG0TERLpMAJvECLwiIF4Cnba0Q07RVtvaFt7QFO0OUTFO%2FOGnzwEIRNYd0LDugIDkYlHMxMORiUc4CMImsIWEBLCEICKYhEyORhYQEsTQsImAtCB0DwrpBo2J3jsTMNo9TZ%2BeLfkVOzDGdWP5uSUEzDcxPgLsLgdGsczF14WnFCg4iBI0CZSE35BRaN%2FktGM5HVWjMZxY%2Fk5qqS0vOzblT8TYdcCTNLSlZCEX5qPYO2PMXSP2tbz5vwfZcfmI0JuEd%2FZUoSvkI%2FaxjfFOtz2o5UEEhBo1UUB2bzxBPrHyRkUqHAm6xa6Qbdx7YuvEblbWsVZD5Y5m4XQqqy1JcqeGq3Ky6StyQmDMF9hakjcJWgq35XA749O%2BMw43iBjJRlzjVYJZwvU3AO1Eqsj8kRGXOO1rSBhGrDqm95Ne%2FyQSxUje8LHujKhlljotuE4UqoICj%2FUq%2Fmi%2B4ry%2Fq02ukroWGKmCiRQ3ODxNdkugC55dtzAa3Iv8ABCNjUXLeuNU2stVXCNWEw9LBUgrxNwguA8rAdvfFh%2Bpnju1%2FanVvR4ou%2FwCSAxUDzRXQtxDa9B09UxkBy7xwjnhCrn96L%2BaLrhbKDH%2BLa5JYYpmGagKhVZlmRlG3WFIC3XXAhNyRYAFVyTsAIDobGIPj9CCjqPtYopUe9XiaL%2FkEYZxQvuM0HKimomQ6wnCs0%2Bmx8ku1B4qHpugRtDOfDC8E5kzeCHZ%2BWnXcM06n0Z%2BYll6mnXmJZsLKD3XNrdhBEYjxQ5bYkmstcnc05GWM7RJ%2FDkxQXXJZBV4nPS048tTTtvJKkLCk38rSrugOVoWuDFzGGcQKWVNUKoLSnrEiXURb1RKKFV9ZApU2kHaxZULH1QFqN4hYxdm6HUPcw9IzIT0iSs9Eryb79kXvGWGJSVr4bw01MP09yXQ5qCFHQs3um%2Fm29cBhqthEtrRl0phqXcwpVpmaZeTVWX2vF2VNkFTdxqtt5yfgiwmlTrezkq4CO9BgLfY849bM6%2FLsKbb0aXO9NzeBk3wbdA58Uxd8LYPruM8Q03CeHac%2FO1arTTUjIyrSbrefcWEoQPhPqBgmHUmZpKsbvFfl%2Bx1O1enxRqLdM0mm1jLDGbNVkmJhuUkmJthS09dh8OhKXEK7DZRBHaDGR55Uabw7m1iCgT6UpmaW4zIvBKrgONS7aFAEcxcGLEHFN5b41AvpVJSwJ7LdOIIhuvgdKGsk55SU60qNRXa9tVmlbfJHD82rXLJX90FH5THb%2FAwdeR05f3rdUHwlpVjHD031ZJPmQfymN6qf2dZeeXKu0Z4hb%2BhiDhsogeeJ5fUXEkI1fse%2BKTm7hEeum7zjSP2QjRnidR9N%2FBuopzNcqXSy8rN4bwnLMzLEy7Ipbemaw%2BTocKiNR6FsuJQb7Bd%2Bdo2Jn%2FidL%2BaisJeMtTLtTZeqVHmFmzvTJHSPyer34O7jZ5g6k90aQ4MF1mkZTzdXpmoio1l1h0k3ADbaRbzDrRZs5Z3HFWzbobOG2J93E8lUJeapIZb6RTDjawrpCLaQhJHXvtpJvsYJUMb4sy3ztxEzPylb9r9fl6d4iK9PoKqTVVNqsmXm7XKLp8h4eSrnsYzvKjOhjJKhGgYxThypqlGwmWThypB983c8p5CbtkIT74KCiOyNIY2rRq2Iam%2FL0em0pipT8xOKk5BkIlta3CVltPIIKrkW2sRbaPFS2qLNYhpchWJGfVR6LLu1OqJpGhqcm5cJPuLaiCkaVJCiSOQI7YD7CZP45w3jvCC5qTeYm6e%2BkJAUm6XW1p3ukixBBtb0x8huPnJmlZL56VegUSUDFDqcuitUlIGyGHlK1tDzNuBaU%2Fsbd0dVcKWdNVp%2BBKPl64JFK6fUXESs4ylXTTcqWy4o2HVKUlaRc9vKNL%2BFGqAqmLMv51X29VEnkFRZKVKQmaFrr9%2BNzYe9ue%2BA4Jmm7R41c49cy4DHkVASaTDSYjCAgRt6IkPOKpHKJCBASQvaEICeLuxOsSlBUtRbXNTD7iEC91hO1ye4fljxU6nKn3HCqZbYYYQXHnnPJQi9h6SewCPVLUB2foczXZJ9t1Mmu0zK6rPNNm2l23vkEmxI5HnzgLapRd91JufuobBNwL%2BaJSAgdXcHs7oIUUq778h3QHUHg%2B6hT6ZnZWZqfICUYTnS2D2uBxuw%2FLFCY9gMWnMfNXMqv4nmUUnEDlPYl5CaVqKVOFDCEi4CR1VXJ2FgIxfhEfLGZs%2B5%2FwBTup9biLfLF2QjVk3mowQNT%2BLaesau8zz%2FANGAtSarkSlSz7JZmIClAtll1KSkdoVdzc%2BcR6W65kElxOutZoaAOt7um5UBtay9gTbfsjVnirimembAsZ4SCetb3W8UlyE02284taQGJ0U9Yv8A209no88BvPCUnkfjOu4cwvQse5hydbrs0zINtTAcLZmXbJQ3qS52rIF48U7N5JU2ozdPmc1sxGXZd5bDjS5aYCm3EK0qTs5zCgR8EaopM9X8HV1jFdEnvEKthepy0zLTKQlRl5tCwppYCrg6VAHcR5aw3UHahVp%2BrTaXJlmZL885p8t15RUVW85UTt3wG7WKrw%2Bql0%2BNZs5l9MLpVZmZ0mx2UOv2js7Ii3UuHwtuIczfzIQfenxaaIVv2jX3Ro6bk5uSXNofcReTZQ%2BuxJulXdEjzU3LuzDDykpVLsCYVfkUHugN0TlbyEKP0rzIzJC1FCQiY6brEixT1V%2FdHaKuMpHK%2FA%2BK6lhGuZlY%2BbqdDmVyc80Gnlo6VH3Kul88aNUl3X0IVZRlvGwUn3o3BHnBEe2tVyu4xr0xiLEtUeqNXrOqfmpt8grmFmwK1W2vsPVAbXTjHIFCUa8W5ovL31gPKbHmt7qYmqGKMjp4ynsPjfH9MShvTNie6aZK13NlILbo0i1rg9o2jSk5SpqUl3J5SkFA61r9kRbYV90IDrThyqdNazEkqvgPNLEc77EzEo3U5WdZebamJOYc6IkBxahcLKLCwNrkGNreENmWHaXlw406Cp0VFToSeSgWwb9x5RzzwgJ%2F4Z1VYAKujpA37vH03jbXHUVioYOSVkpKKgqxOwPSIgOU3%2FtS%2FQY6wpTPQ0KkNltKVJkpa5HcUAj5I5RdUkNKuOwx1bRtYoVOmluBR8Ul%2Fe8k6E3%2BHlGWx%2BH6NiltGdnl%2FXKy9K0yyEOMJ1TGi621clJiNOplTxVXJai4dlg5PTF1KJNm5ZsDrOuK5BCRuSe6J7sBaX39PVZFtjcdp9G0eygz68OZc1CekJhTNVxnMOSMykDdNJQEqsFfs3NII52EbNUz8GnXLQiIjjlDE2JKPTEHDOA1rckmFIL1aWm0xPzKCdTrfa21fZI5kC55xY8RZ1Zoy2F5rD6a%2Bt2mqu8WVoBGsDy9twfhjzM9E04Eo3LabjaLJi5SPYecnGQElTZTpv2kDeMlNfvcfoKbiLSf1kZrNXqx7IyUm7ONkmYk2luaiokLO6iLmMOn0TUi6zP0WeekZllWtl6WWULbI7iI2dmhQOhZw89T0oCjh2RcUlIte6VE384741eXnQhbTiIrVXNcRNU5y2eKmZiIyhf6pVmsxqFN1l1LbGLaM0FVRlpsIbqct%2FfaUjZLqLgOW2UCFbG8YOPdAHI91JrDuF8UU3E0u0l3xZ4NTDSt0vS67pcQR2gpUR6oqVKSladV56nSwtLyzykM3N7t80%2FIRFM816YiNSyT4CZaZUm1%2BgXffzRicsjqiMzrDaG6bMrt5TakxikkjUlNxFa442aic4asxL%2FZHUh%2Fjz%2BSLpiV4vVJoqXuJZgW%2FcDeLbiNOrE1VHc%2BqPTiIj2Ybty8XZ9WkRqzrXZllskLxPTUKICVPJBubDnFTMJKEVJ5LdrdKvl6Y8uAiRWpBQNj0osY9GPyVTxUeZcUT64gYTMnaLa55UXGY5RbnPKgJDtEhNomJikomAqpN4qtKAMedHKJ0mxgNr4N4jc7sB4fYwrhDNTElJpEqpSmJOWnLNM6jchAIOkE3NhtcmL4OLbiQKtX1b8XX%2Fz0fQjSYJtzidDpTsdxAbvHFvxJf4b8W%2FjifoRN9d1xKBOlOd%2BLAL33nEH%2BRGkw%2BnvMDMJPaYDd%2FwBeLxNJOoZ4Yo9HTt%2FQjHcb8SOeOY1HGHscZn1ysUsOdKZSYfHRqWORUEpGq3ZflGsC96PXFMrPeYA%2Bbm8UwLxEnVe8QTzEBuPhVySw7nxnDScAYpxfI0GQmljpOmmA1MTYO3QytwQt7tCT2Axi2bmX0vlhjurYNlMS0nEUvIPKQzVKXMB1h9OpQsSPJcTay09igYzThDy5pObXELg3L6uz9SkZGqzii5M02YLE00UNqWlTTo3QoFI6w88YXmThmVw1jnEuHpGacmGKXWp6RaddI6RaGn3EJUv9kQASe03gMOQ3GwslcSUzAuaeEMbVxp9ynUCuyNRnEsJ1OdA26krKB2qCbkDttGHStNW7tcAekR2NlVlllNkFkpTeI3PPDqMU1bEzqkYMwutzRLvJRe8zMd6eZA3HLYwGwqfx8YLqeIMSzWNTNO0v6otKxFh%2FxeiJbdco0u8VLS%2BUi63NJFgq6to4ZzSrMliXH%2BJ8R0pChI1Wszs9LEt6CWnX1rRdPvTZQ27I6nPH1MVJ%2FwBj8a8PuVNUww4ejcpDdPSw%2FwBFys28U%2BVbtsPSIw%2FidyEy%2BpGEMMcQOQM7MTGWWOCthElNKKn6FUU3K5RxR303SsJvuCm1yCCQ5WUlQNwmM%2FypyfmM2HqgwzmBg7DTtP6O6cQ1NMn4xr1btavL06et3XHfGHOyUw3zZUY3fwe5HYSz5zqk8t8cPz8vTpmmT88VyRQHtbDepOkqBFrnu3tAacx5hKYwLiifwjNVWlVNynuBInaVMiZlJgFIUFNuJ2I3se0EEHlGP8ou1ekU06rTsg2U9HLTDjSCEhNwk2vYbAmLYdoD103eYR3E2%2BWOuvCO7Zi4Cb7G8vKKPkcjkWlbzDY71fnjrrwkH%2FGlg1n7nL%2BjD%2BC5AceqFzEFC4iooXMQMBv3hU4Y2uI1zFMvOY6pVAZoFGm5toPzLYfEw2hKm3FtKOrxW5stweTGmcV4bnMK4gqOGZ9%2BSfmKa%2BphbslMJfl3bcltuJ2Ug8wRG%2FeCrKGUzdxBjxh3Ftaw5MYfwbPVNiapTgQt3qlK2HQdltKF9SDsY56clHFISUJSBpCtKLAbi%2FLsHmgPGhkRvvg3zPwrkrndT8f43nJiUpMtS6hLF1iWL6g86wUtXQOY1W80aVl5B5wJ0ta1KWAE38onkI7jlsIZM8FWX2Ha1mpgeSx1mziqSTUZelTyx4hSWFC6OkSdir4Dc8oC9YN41stazl9h5rMxuVlMTScjiqQn5Wl0DopMuTrWiUcDSAU3UANRG973j5%2F1VlImCRyOlO%2FO4Fifkjs%2BR40MsMeTSKBxBcOeApvC0z7g9O4ZZ8Wn6ahR2dRYAr0XJOk3sDYHlGpOK3h4TkZjpiQolX9m8KYikUVrDNV1AmbkFm2lZG3SNkgEjmClW1zAc99H3RtjKvh4xRm1h12v0DF2CKelqYXLeJ1evNSk0VpAN%2BjWbhJvseRjWq5NwEhIuPTG8OH%2FAIfMNZx4DzaxHiGqzMhN4Bw4KvTxLMtuCYd6%2FUc1b6bpSNjcXMBoiryEzSanM0qbDYfk3nJd3onA43rQopJStOykki4UNiLGPHYx65xgMHRdPVOjbltttFC1hAUoRE84JgJrGFj3RMOURgKrce%2BXFiI8DXO0XBgcoDNaP%2FWYftj%2BWLZSFqbx7h11HlN1WWc%2BKsH80XOi70cX%2B6MWFt3ocUU539TmArb0QF7fnOkqU45fypl5XxnCT67xm%2BXuK6FLVnDlJxotSKNTKrKzUlPJRrcphQ8lZTbmWDY7e9JuNriNWNvua1L%2B6UVfLFwEzdO2opHM22ga36LaFX6PiakSteoFQYnqfOtJeYmGVhSFpPaCIuEfHLgq43KrkJWZbBuNZp%2BoYCnnQ24N1OUtR5OoHaj7pI3ty3G%2F1%2FolapOI6TKV2g1Fiep8%2BymYlplhYW262oXSpJGxBEM8x7oQhAIQhAIQhAIQhAfA%2FjmMmriOzGEs04hYxPOdIVG4Uda7kfCDHOr29Pav9wB8u8dAcbzizxMZlJJJSnFE8E%2Ba61XHrjn58%2FoBof4u%2FwApgMyw6B7GHbfQ0R6zFyTsrf0x4cNptS%2BktyQ0PymN2cMmTlLzmzFXSsRl5NBocoKnVEMq0rmk6wlqWCveha76j9ykwGnm1oWFrQdSRzKQSIaArccjH07xtW8nMoMNsIq%2BGaNLIn1JkaXQabTG3JyqPHqoYYasVKJNgVE2FySY5R4sslJHL9rC%2BOqTh1rDqcSlyWq9EZf6ZqnVFKOlCUL5WUjUkgbBSTaA1TgjI%2FNTMSjKxPgnBc%2FVae3MLlFTDBSAHU21J3PZqF4yBHC3xFrc6MZb1gHvLqQPXeNwZSVqv4X4IMRYgw3WJim1CXxWWmJmXIC2wp9hK7X7xGDHPbOJRucyazf9sj6MBiznCxxFNhTjmWlWUhCFOKKlpISlIuT5XcCfgi15XZ%2FZh5P0%2BqUjBTtLTJ1mYbm5tuckw8VOIQUJsbjaxOxvvHVnCjj7HmN65jWXxbiqeqrchh0zEsmYUmzSypQJFgOY2jg6w227%2FwAsBmuZObOKM2p2lz2KpWjsOUaWck5dNMp6JNCkLWFkrSjZSrjY90dbZD%2F%2FAEf2%2B5pte0%2Bp20cKcuUd35DJB4RWh2exdcB%2BBD0fNvdO%2Bb7v%2Fqx92p18I%2BMq80uO8uNX1E8QIHkoxFTCfxVQgw4Au3LqqHO3NJH54lyxUXcjsSq7PbBTN%2F3uqKcfRqNTkzrYNPYGxlVGJFxGHngGZVDJPSI6xF9%2Bfni3%2FUgxy9qWmjlNz2uo%2BeNldTzREFA7ouhrFWT%2BN0%2BVTkD%2FAEyfniLWUeLFLAelAhPaQtJ%2FPGz9aLW0JiUqTflAazVlHiVPNoj4U%2FPBrKmtO2QOk6TtAQLeu8bL1JhqTAazdylxK0dJb37iU%2FPFJOVeJlKt0IHnJA%2FPG07piqNKxo8qA1YnKPFXjDSEttAlaQorcSkJF%2BZN426qYaVVCpt1IbU6odJe4FkkavRePE6L%2BeIBu4gNdz%2BDsT1GXllt0xV2mQhWtxIJ3J7%2FADxbTldit46zKoR5i4k%2FnjbaGtoj0cBqljJzFbp3TLpH%2BXR88ToyaxUvkiXG1930D88bS6NIN7RFXKA1gvJnFSE69UooXtZMwgn1XiCcm8TFKVXYGrl7sj542ZfzD1ROXLJ5D1QGp3cqcStnT0SSfMtJHrvEqcq8VFfRmWQD%2B3HzxtjpImL6uV4DVbGUWKXZhpCfFUXcSNTjyUpG%2B5JJ2AjcMwEomHkpdSpKVKSFp5KsLAjzG3yx4W3CT10xVUvbYQGrZ%2FBmLKgpkmjrQppoNEKcTc2v5%2FPHi%2BpVilzymWm%2FS4I26lRvE55QGohlNibuZ%2FCCJU5V4iLwaIbBPaVi35Y22UL5xRcBgNZ%2FUjxB2qZ%2FCp%2BeKX1KsQXP2vb%2FABg%2BeNnQgNYfUsxDfm3b9sIivKivWulxpR7isD88bMK7RKXb7XgNbSWVeIDMshx2UZSXWwVrfSEpBULqPmHMxt%2F2Tk1YhdnCsKlg%2B4AsclgJKQR5jsR5jFkcBMQQCEaYDDKvgfFFQalWhKS6lMy6WiRMJ5gk35%2Bf5ItQypxMo3dRLN%2F6ZJjY%2BiGi0F2uxlNiDselj%2FpUiJxlRXffKY%2BB5PzxsPfuEN%2B4eqCssA%2BpRVi24jpWgskFCy%2BjSkdoI5kxM5ldOAS4RruBaYPTNnUdXNG%2B3V7%2B2M937h6ob9w9UEMCXlhMmYmC0HBLrSsS6VOI1pV7wrPK3faPEvLKtoRp6il%2FdBwW9UbL19loipVhtAa0kMva61PSyldEkJebWVFYAACgTeNoTbl5uZKPJ6Q8ooX2vEusg2EBk%2BYf%2FwBMFF%2F%2FALgq%2FwD9cY6%2F4JFE8NdK1e9ZqA%2BDxtUchZhptwu0NX3WYS%2F%2FAPWmOweC4No4Z6KEA38Sn1K86vHF3j5n7pM5XKx%2F1KfVU7GFTx1eb8YcBubzLn%2BXe%2F3io6L4F98457zYfmj%2FAA0Rzo8LTb4%2B5fd%2F3io6L4Ff%2BOWeH%2FUEwP8AaIju6bZTgNtlzY9cNfD5%2FtNPnXrOkqTxZVPTzGVT5H4FRjnRj30dG5xlR4up5KlXH1LXUpHmLKv5zHOTHbGfQ6nc4Jdv5YYr9H6%2BYWfFdJq9Smq54tT3X0TM20%2B242BpVZlIPwjcfBGBry0xetw3pa0ftlCNtdIsRKXD2x6hq5NUoyrxWsKJk7FIKiCewROcp8XJAUqSsk8jcRtAuKtzMUisk9vrghrNOVeKFc5bT6RE5yqxCE3snV3aY2Nqt3%2BuJStfvSfXAa4VlZiMeQlB9O0UXssMStjV0CT6DGyFrevzPrinqd7z64DXAy1xSSQZVIAGq%2Bsco2k%2FTTRaHR6Q7MMzL8tS21KUw4FjrBSgm498AQCOw7R5UhfPVEOqju%2B69cBbsZUqeqgqMtTW0zYeqXjbTjSuqptTCE9vaFAg%2BiMEVl%2Fib30gE%2BlQjZ178omQbGCYazTlziA%2BUhtPw3%2FJFT6mWIv8V642SVG9w4R6DECtdt3FQMmuUZYYhWbBbQ9JtFRGVeIS4hpbjIK%2FJ3uDGwEub7qVEyXwFeUqBk127ldiBr37Z3I%2BERR%2BpriJWno0oVq5XNo2b4wTyUfhiYubQMmrnMt8SsnS62yk93SA%2FkjaBYNOp0hKuOturYk0J9yVq7OR7jtyimrr380UVbG0DJbsbUSpVjx2UkGunUao682tBGhTa2W%2Btc%2BcEekGMHRl3idZsZVtI7y4I2RE6EXEDJrxOV%2BJym6G2VE9msCJvqUYsK9HiqL%2FALcRsZG0VQvsEDJrn6kOLdwZdsEd6xb1xD6lOI0ISXS0k30kBV7GNjdK52LidKlEbm8ENbfUsxD2Kb9cUFZaYkT5SGh6ViNodIv7qKT5WoX1QGskZaYgU4kLUwhJIBVr8kd8bZmUJlUyqC4h%2Fo5ZC7tK1bFRIHmVbmOy8W70xPztp%2FbbdvpgLDmJRZ%2Brz77dOb8ZQmdmXUOIPUU2tSVIsT222t5ow0YAxIvfxFSfTGzQs90VEBajclVu68Ew1oMt8R%2B%2FaQje26u2Kgy0xArrDoyBzN%2BUbJsb7RP1%2FNBZrcZYV9SAUuslR7N9opnLWvJ5rQPSlUbNsfujE2%2F3R9cFGr15d1pLmnUg7fcmKS8vq4D1dHxTG1rH7oxHb7owGs6Xl7W26nIvzJQlhMy0p1YBOhIUCTbt2vG0Ov0DTSz1kJOrt2KyR8lvXEoWoclGJbkQGcUY6Mgs7HArSfYGnIPnBqUvt8kbL8Gm82TjyVD56QzVJdLWnmgLdGq%2FpNo1nTRp4fM6HP8AqanJ%2FwD8kxGw%2FBnoKatj18oWRppKAq3Vv0zht6dhHi9PfmS1%2FwBv3qXVwif1%2Bf8AXKwvi1BHENjG6gQXJUi3%2BQTGO5KgnN%2FA1hf%2FAIQyP%2B8jIOLA6uILGRPZMS6PUwmLFkerRnFgVX%2F9QSf8eM8z%2FwCsUz%2Fk%2FwDBhsP0r5EfxR63S%2FhBJluVwdgMqaSonGzIuRfqhkFQ%2BHaOfc60FOcWMkqTb9OH9vNeN8%2BERv7S8Ab7HGrf%2Fl0xofOs3zgxef8ArV38saPuefMlE%2FxVesxP5TUwHGTL03hpuVkpZyYdX07RQ2NSkklpSSR3dUj4I1W5l%2FihbirUaY%2BGwjb%2BuGvzR7tptQoy3xaSNVNUgd5Ij0IyvxIoXEq4T5k3ja2vzRDXeA1YMscQG95d4W5%2B58vlic5XV1P2xLg9DV%2FzxtCx%2FwDZik4og2go1ivLKsp5hf4P%2BeKP1N64Bcj5I2eo3iWA1icuqwPuz6EiM4wNSJyg4cqEjOC3jE4yptJUNW25IA7NrXi7Q0AHULA98B5cYy8zU8PSsrKJLrqvGZdbaebZKm1pWr9ibKA86Y1wrANeBsqWsO8qEbUHXc6RZ1fdRJo88BrNOW1dVc2R64HK%2FESjdpKD6VgRszR54aLQGtDlfiVKNWhv0Bab%2FliojLKuqFlBKVeci3rvGyYQGtHMtK2jk42fSQIl%2BptXv8V8cRs0pUeRiXR54DWreWtZP2xSU%2BhaT%2BeM5wdSn6Hh56nzbrfSLdFm79YpuVax2W7PTFzDdtxE51WttAWzGlPfrtCp9OpNnXUJfS8gnSW%2FdkqQbnZWpOrlyIN418cvK%2FrKVtoT6Vg%2FnjZqxvvAIEBrcZbVrtUz8cRUGWtXWLB5u%2FnUI2NCA1x9TKsfqzPxhE6csKr76baH7oRsYcoQGuV5Y1RI%2Fqtr4wikrLOq9kwyf3YjZCwbxCxgNbDLKsHk4z8LqY2DhenOUPCopM0%2B0ZkzSR0YVq6iUqPS3G1iV6bc9o9SEbXtA7QHkxjSnsR0aSk6e%2BhTni5amEOHR0a0vKULHtCkkH03EYH9TCv9JbpJX8MI2H%2FbLxWgNfoyqrS9%2FGZRJ87wiunKOrBAcXNyxSTbqvJv6ozyJ2ucBgyMnqobkzkodXk%2FogC3pioMm5tTQUqel0rSbKHTg6vRGfjlCA12%2FlDNpIQzNoXf%2FGjYx5F5R1nXpQ%2BwPOVi0bNT5XZyPKJwkXuErB7yYDWAycr5GrxmXA7y4BGe4VoszQ6ImWnX21PIUGkoTv1Ujyr8rEm3wRdwtfv1qMU1r7iYDZfDeAvOfD6VC6FGZ1%2BYeLPGMO8Hoz0mfLbtxpZw9U1KubbFKR%2BcRmPDVdWctCtuR40bXte0q7tGGeD1CznkhQUQBh2pE2F7iyPzx5nS%2BqKcGvFX8M%2Bp0MPjO8Uedtvj2A%2Bq9h%2FbcYUl7%2FhlRzO4N46W49lq%2BrRSGT5LeFJX4xfXf8kc1rAJiND%2FAJju38v4yx3z4%2BrzqELXN4isd0EDvj07TZplHmhW8nMYtY8w5TKXO1OWYcl5ZFQlS%2BlCnLAqbANw5YFII36x746%2FcxBjjLnhhzAxNxMYkdn5%2FMdLqaJhucUFrlFPMqCW0oPkWKkuFI8gNjcExynkHj7CGV%2BZkjjXG%2BGna7IU%2BXfVLyrQQVNzhSOhesvY6DqPpIPZG3s5OILh2zop1an8RZbYqmsUTNGfp9Inpioe5U55SeotLYVpA1dZRtdVrGA2Zwp5dsZDymDanjCRffx9m3NN02RabQf0npSGVPLWtdrIWsJSpXInUkd8ZBkI1Oo4p%2BJbxhtbUzMqlnJcKBT0oWtYQ6knsKgBfvBjnzL7jXzboGI8PHHdcVXMNUxDcvPyLEoyh6ZaQz0aFJcO4WCEG%2B17GMiwhxk02l5tZiZg4oodXqUliikS9EobUslpp%2BnSjK3ltodINlWU6TqG5%2BCA2hgaVzDyhyJzHY4rsfyFTkajIONyEq%2FU0Tj3WlloWi48rU4WilO5BTfaLJwmYHksmKBgnGGNabMLx1m1Ns0ejS3RkGl0rRqdmXFckawkKN7EhSR2xxCsOTEomXqT7s2vowlS3nluG%2FviNZNrx0Dl3xo5wYZqtAYxTWWqzhulFqXm5NEk0mZflEJ0htLp5KACd%2F2MBtPD%2BbuCsmuNvNeoZjuuU2SxGEystVnmlFMupIZWVKIBIacAUjWNgURe3Mtc2aHg%2FFlY4euISVzIw%2FWZNxVSomICmoOzDJQsuJZWFaQtTZtpNtWkWFxGqJXi%2BYVndiXMDE2DZbEODsQSLVARSJqWaVMyVMaUtTWlSgQXAXXtW4uFDfYR6cIcQ%2FDzkTSsQPcPeX2JJau4glxLl6rTIUxLhNy2dPvtBNx2m1iYDlhAaDLQY1dGG0hGrnYDa%2Fbf0xI5FdxzVuSFLXdS1WtqUSST5rm5igsXgKcIjYxCAgTaIXMTRDSIADeAJJiIHdEUp60BcsN4drGKsQUvC2Hqe5O1SszbUlJy6B1nHXFWA9A3J8wMZxV%2BHvMmXx%2Fi3LzDFFXi2dwa8hmoTVCSZiWBUhKgAuw6wKikp5hSTF64RcV4cwTxJ4CxDit5uXpiJ1yUVNOGyZR19pTTTxPIaVqTudheOteE3ENLy6lcacPmNJpNPzBwtX6pW6o4tRvVqe5Z9M%2Bl0eWENqFxe4SQe0wHD8rk%2Fi2fyzxHmjINIcksH1hNGxBT1hSJ%2BnLUlOl5xki4a1K0lXYQewExiCKfMvIU6zJvOIb%2B2KbbUoJ9JGwjtLEOPcJYqe4mM%2BKOtIwRiLC0jganzDg0IxDWwlN3m081FIAOq1yN%2B2Me8H5jvECMfzOTq5WlzGG6vKT9am%2BmkkrmOnalkthIcPvFAglJHMbc4DkkS6nHA02la1kXCUJKiR6BB%2BVdYUUOtutLAHUWgpV6bHs88dccO8tLZY8P7mcGHMHUrEGO8ZY5OCaG3UikMSnuxbQkFWyEkhRJ57AXjB%2BLlOeZxVhhvPejYYkJwSUw1R3aElAYdZVMIS4HFgkkpXp57AEkczAaRwhgzEmO8RyWEsJ0x2pVeoKUmWlWranSlJUbX22Skn4IueYWVOPsqKlJ0nMHDczR5qoSpnJRD1j0zIVpKkkEjY7EdkdQZL8K2buU2ZWG8zpau4FqUvSZ0NTTQrKS28y82pt1tLg26QJXqSO0ptGZ8UfD9mDnxj1jEeGq9g9qgYcpRp0m87VR0roW50qnH0jqtHUSgb7gAwHACxaJYyPHeD6jgHF9VwXV5uQmpykPBh1%2BQfD0u4ShKroWNlCygPMQR2Rj8BRKjqtE8QUntgk9kBGEIQEsIQgA5xNEoBiaAlse6Fj3RNEQO%2BAgBaET2iSAROIltteFzAl0NwvJKcNYhWTpvOI3t%2FixGqMpJKmzHEbiiYqchLzZpMrWp2XS%2BjWlEwgFKHLfdJ1EjuIB7I21wtkLwpiBKlkEVFIJva120%2FPGnsuqjRsMcRmJpTFtYbpMvVPZajpn5kEMsvPGza3T71u43VyA3jzVxmO6l4mfJ%2BD7DpPnOh2G0U8er7stkITKscm9XV992%2BmL1KV6sS8otmjTL8mp77b0LpbCuwXA2MXT2r4JQoIdzty0JINv0%2BRzHPs5eeJpTDWEEbjPHLQhWpIAr6Ra3nItHoffaO%2B%2BSTYWkfRnoWORqGLChTbWIak3o6x93IBPdbtiZusY8X9sxJVer29MQBGc5czOSE5iesYLxxnPh2n1Kny7cyy7KPdPKzCFWNm5kDQVgK6yL359xjZ7VM4WkFKXs86CopH98JGqLbuFNxV3mhGapjAp6%2BJqr8EwY9KKriQWSvEtQI7R05sfTGxM2Knw14fp9Ip2G86KM%2FVq7NeKy6CoqYaGwLr7qQQy2Cbalc%2FgjFmsPYLSNT%2BfmWIO1wK6n4ezeJ3Ud897r7y3tVbFaz7ni2rd1hMdnqioZrGNwoYtrKSOREwdvki4S1eyjwFW6RNYyzpwdN0WbnW5WZcos0Z%2BYZ1AnUWkC4b%2B6Wdk7d8b4m5nhHc1I%2Bq%2Fh5aE9XWJ9Nt%2BRhuo76Jorjknocwv4izBklHocaVe2o%2F269u4cosc%2Fj7MROpC8XVJSVbElYCh6CBcR03iiU4SWKDPVV3O6hSzUrLrfu3MB5SgBslLaestRtYAbxz%2FACOA6ZiynMVyhZqZdmnTqOllTN19uXfKSTstpdlNqHIpUAbiG6jvm4q7zW7pdfcW886px1xRWtajdSlHmSTzMXSmYmxdR6a%2FRqTiKoStOmnkzD0mh0lhbo5L0G6dXnteM5OSM84R0eZmXDiR2jE0uPz7xUZyNxC1yxtgR%2Fq36mJ5U%2Bj30M4ljqqiicqpyWamYzx22izWIpvSpOlSQhG4PYerFyFXxfNKKxVSi%2Bm9pds3I5HdPONi5O4Oylqs7X8M46zXw5T6%2FQHUCZkETqFjQoXCw7fQ5z3CSbE2MbblcteH6WFxmpQloSQSPHmvXziyN3GeWbnJuoYnOgzFWSvQLJBkmdh8SPY3iGuSiFMtOyaCkWUTIMEkfEjZ%2BalAyqps1R8P4Bx%2Fh%2Bp4lqylqlaSuptNrfZSCVLS4ToB6p2UQTba8YYnLDGz6Uq8Vo6yT1QmuyhNvP14haJzYtM1auOqSWpmSGkcl05lX8mLLO1zEyCFGVoT2kEal0dkkm3M7bmNm4fwNTaXimlUjNXEtEwpJ1p9UrT5iZqTC0zUxtZpJQogE6gN7c42jUeHbLmZcLctmZR0lXJK5hu4I9BgcUuUX8dViU1a6BhlwK56qI1f12inLZqVqmTbVVpFAwxTKnLr6WXqEjS0szDDo5OIUD1VC5sbdpjfeNuGjDdCw1UsSt5q4bSzTWS%2B4ZidbZRa9gNZNgTyF40a9kpmxOBM5JZcVuYlXkhbTrTSHEuNndK0lJspJG4I2IhnTGuTKeRgtUqFQrdUmazVp12bnZ55b8w%2B6rUt1xRupSieZJMWjMVK%2FqRVublqjNSrspU5BLjbSrNzTS%2Bku24O0JUEqHnvtGwlZK5vJWEHLXEO99xKEjb0Rh2c%2BGcWYMykqslizDlQoxqlTkBLePsFovKb1lei%2FlBIO9uVxETVTOqVoiY1t%2B8DqUMZJTKlq0pWzUXFHuHQKF44gqCgqRQpPJSbx21wWzOnI6bTt1Zaos7f5BUcSTv9bmv2kb9Ufs%2By88uTdJ%2Ft9vPmYe5s4THokXUszLL55oWCR5o8rhsuIoXGi6r6f%2BDaxfSaph3GGWU0GlTUs81iOQQux6aWcSG39IPahYQT5lR0rmfgE1zB9XRhN5yj1syTvQTUjLoU9MEC4lXCet0LpAQsJINjHx9yXzcr%2BVuMKLi%2FD0%2BZWp0SZ6eVcWT0TiCNLku8PfMuJJSodmx7I%2BvOSefmXmfVAFVwdOCVqzKQqo0GYcHjckvt0%2FqrR5pcTcEWvY7QHGmYnD5nVRMQMp%2Bp9NVWgNMtTKJqhWebbStsLWw2TZWtCipNlADa17GK9JyrxhlDmXh7Fs%2BqZncOT0uH5KbalC06%2By6DqlX2XN2n0qFloVyttcGPoQXHWjqCik9xFjHgrOHaZi%2BnO0mtMread6wWN1tq7FpPYRAWnK3CeAaXheQThSgU9llKFoa6JGoJSpWopQTuEkm%2Bns5dgj5seEZzDkMYcQM3RaSttcpg2nM0JS0cjN3LkwB2EBSkpuPuT3RvTN3ickuFqRxNgjA9eZrGNZt12UaYQoOydHTy8cWQbdKpJ6raTz3Nrb%2FNyq1eZqUwuamZl551a1LccdUVKWom5Uo9pJJJMB4Xdlc4pKNzBxd1XiQ7wE0Ilue%2BFz3wEx2ES84hq88RgEIQgL9RMJz2IqDVqpSpqWcmKKpl52nFy0zMMLJSXWke%2FDZtrA3AUDyvaTCdIVUnqo%2BiuyFNNNpcxPETUx0RnEp0hUuzfy3VBRIR26TFnZeel30TMu6tp1s3QtCilQ9BEQ1wEsPPA7wgN28KH%2FGJO%2F8AZav94mPbUZsyuSWZJSSCvEVJWCDvtNTio8fCltj%2BpK%2B5pRP%2B0TFzxPTeiyhxXLNp%2Fqyu4dG%2B1itM64T6zAc%2BrqEx1kpcWE9MHtj7%2B563p3iR2pzaw4C6uzqw6u6ubn3Xpi6ChTLqPGkoT0bk%2BmS58lkn5NucRXh50omFKSlPRT6aesE%2BSo8leiAtLtTmni6HH3FB5QWsFROpQ7T3mIPT80%2BVrffW4p0AOFSidVuV%2B%2B20XOcw47LJnXitsplJtMqoJPMm3WHmiSaw89K%2ByOtxtfsetCDpN9ZVyt64C3GoTK9et9w9KnQu6idSewH0RMqozS1LcU8pWtHRqueae6PbN0B%2BUXPoLqFmQQ2tWncKCuVog%2FQXpUzKHFIIl5dMwSDzCuweeA8AqEyFaw4q%2FR9Fe%2FvO70Q8cmfc%2Fdle5o0I33Ce4eaPc5RHW1up1oIalfGiQdrXtb0wRQphx5DCSkqXLCZG%2BwTe1vTATyLzi5Kd1OuKswDYq88Ui8ptzRrV2dse9dHm6dTZt15bYQuXCQUquSdY2jymSdW9rNtJAgOkuC9SF4rrpWq6yzStHnV48m%2FyRtbjocJqeEkX201Aj46RGqODFgt4vqihyU7RkH0Gc3%2FJG0OOfq1rCY56mZ5Xo91SIDlx9R6JXoMdZSbni8jIhRBT4lLlVuX2tJsB3xya4Lsup7QDHXlJYQuWpjj1lr8SYVbTz9zSD8EZbH4bHbZTRxsknVOexMwoC1mVBJAv73aPZMpfRhzDQSyhbapRC1B1ZShRBIULjcco8EtUA0hEnMJCmwR6Am1rHzRc6eyur4WYZXcO4am3EuoFjqlV8l%2BhKrX8xjaj4US0tdM%2Bh459yjhtS2abKsr1BSUofWSRY3ubW5xj9bnKPP0t%2BQVRWLOMqbuw8sqQe8XG8ZBoVKTXjLM06EpSW9KUIUDc3v1o8Zq0%2BhDqWGm3Okvf3NsEWO4vz7Ysruo77zYkrso6zTGZgyE0qRpzMuC08Vgti5CVEDZQuQRGE1SYw7Nuhcrh6W6QA6kF9wBZ9W3bGTzHsy6%2BJdmQeddVulDLKCpQtcgAbnYR438TU6Zw3VKZOUtE5OVBMv7HTo0o9j1Ic1OK0gXWVoujnteCd1lGfK1HigSLjTbkrRl0xS0lLrXTF1CnNWykEi4uOyJ6%2BpRrLilAgrQ2SD2HoxGd0LBLuPsYUXB0s8lpE1MeMTjyhcS0o2NTrnwICj8EYjXpB6cxBVJ2RStyUVNvLllKFiJfUQ1fz6AmME57qYjkZ6a43MZ8rHaitfsZMa1%2BU2s7b79%2FmjFJVwhSQkkeeMqqbDjMjNKcuFFtQ09wMYvIS7jnUT9zETxslEtd1eW6Wq1p87luYII%2BCJcTDTWQB2S7I%2FgCPbVU9BVK6HBbS8SofADHnxYm1WbWDdLkqwtJ7wUCNedbPDJMDG1WkjfyHNXwRUxm50kzsffKjy4LCW5%2BXU4u3WET4r%2FqlWj7oxAxOYUY8CvKMet9ceNSt4CmqJYmVEsBFPOJ084kHOJoCqOUIluYXPfAT64a4ksYWPdATXELjviWEBNcQuO%2BJYQGz%2BHnOGayIzbw7mrJ0ZiruUJ5bhkXXS0HkqQpBAWAdJGoEbdkdFVDjM4d61UJuq1XgfwnMz088qYmHl1dQU66skrWrbmSbxxOlRSdjHoQ%2BoczAdkOcV3DK%2BypP1ieGCrSeqK04B8kbnz0q1Pr6OF7OzBj2GcM4FmKe9TpZdfljO0ahzWlREvNIHNOy2wTaxTc8o%2BbDU2ocjHQ%2FDpxWTWU1Cq2V2YGEZTHmV%2BI1dJP4dnVAGXfJ3fllHZCibEi46w1Ag3uHUac2JeYnJdp%2FMbhLUiZn5uRmHXMNr0sIaCtLirjdDmlISf2Yi2YNr2E8luCzp848vabi6j4yzBn5%2BkYfU%2BuVl3mEKV%2Bi2CbKDXU1IB5pWm%2FONZyuY%2Fg5cMTZxTQsoMwK1UEkONUWrTY8RaUNwkn3yQeQJMaV4hOJDGXEFixGIMQpakZCQa8VpNJlRplqfLX2QhPebC57YDcSuJ7hHaJtwN0ci236eLvf1xe8E8cfDnlpXm8W4C4QZag11hh%2BXYnJWskqQl1BSpPWJBBB7o4jdeUs3JJilr%2FAPd4D21%2BeRUqlNz7TZbTMOqcCSdxc3i2RM453xT1QFwpKbzjCR%2BqJHyiOuvCUWRnXhhkeS3gSjJ%2FgKP545HohtUJYHtdT%2FGAjrjwl40580lr9RwXRU%2F7JUBx%2BSL84hcd8SKNjENRgN%2BcJfEfSeG%2FFuIa1WsFKxNIYjoblGmJZE2GFJQpQKjdWxBGpJHPeNmN8R3BkyhKGeCyWATyvXyT%2FHjjkHzxUDndAdjy%2FEbwaPTMsma4N2ZVhM0wtyZRXiTLgOA9JYK3087dto3dnqzO0bjQnsQzFTy6FIxPgSVnqFN4%2BYW5SpyXbCQWpZQBCZgWv%2B1Jj5psPaSFCx2sQeREdVZT8V%2BAKxlfJZCcVOX72N8JUdX6Q1aTcCatRkdjaFHdaU7AWPIAFJsIDbeK63S63gmtSjjHCmtE5hh6pdFIIdbmy4ts%2FoZkhNxMg2CeQuRvF1zExXlhk7kDkXgHiByd9vdblMKeOMy7tQ8VfpSHFbIV1gSSCBb9hGsqDmP4P%2FJ6YVirA2A8Y46xHLO%2BMU1rEiEtS0s6PJKhpSFaTY3sTtHOWc%2Bc2Lc6MbVDHGMJ7p56dVpCU7IYaT5DSB2ISNgPSe2A3wOIDguQLHg3cAAt1cQHf%2BHHvl%2BLnhzwngbHOGMr%2BHSqYWncb0VyjzM0mrJeQEkkoJSpRNkqPZ2Exxk46om5N4dMqAqzjgedKgNtRPrMeM84qLXeKcBC294mA7YDnEwF4ARaJkpMIqIG0BM2ggjYRcpdBIGwi3J5xcpQ7QGX0bajfCYsjKEqxRTypGoB4HTa9%2FNF5pK9NII%2FZGPJh%2BWVOY4o8q2jUt2dYSkDmTrERVO5iZTEZzk3JlXw5rdmZet5ly823ILQXkU6WUETDyTe11K2QPl80b6kKdgugt%2BwFGy3oTUggFa%2FGmVTBB7ErUTuTt3RfHZVqpqmVM4gQ1KIZD0zPTL4aRIHUG9TqlCyOvsE9t4kpWXOOp2sCTVTHWHlqDczPAWZclB%2FbkrSShy6eVjubR0LOxs7On9LjnyufaXi0rqmmnV3o9ffYrV8t8o8T9InE2XKJFtwW8aw%2B%2F4tMME9obWS2u3cbXjubgbo%2BHMH5Iy%2BBMP46axK1SJ%2BaLayktvsMuuFaG3WlbtqFyCOV9xsY4uq89gOqJmZdiRreHqjJTRbRIz7heEyhJKSsEAKaXbrFKhpI5GPZlTmjUcqMcyOLcPlT7QIZnGACBNS3NaCeRI5pJ5ECLXm67j6OUq3a9xaxnFWcPqbCPLTKjKVimytWp7odlZ1lEwyse%2BQtIUk%2BoiPVHOdEhCEAhCEAhCEB8B%2BOYdHxNZmG3%2FOSbUN%2B25%2BeOe3hensjuQQN%2By%2F%2FwC46F457HibzLJ5e2Oa%2BQxz08NNPY5X0D5Cb%2FlEBnWH1hNPUgeSUNeuxjbOQ2dU9kdiupYhYoaavLVem%2Bx81KKe6LdLmtt0K3sUqBv3hRjUOHlXkQP8W2Y23kThXKnE2M1O5y46pVAw9TGkTXiU9MdAqsO9JYS6V9iBYKX22IA5wG218ZmC6tiyj4%2Bq2RwmK9QWHZamVI1IFyVSu%2BrQm1vfGyuYvtGDZ9cS03nhRqJh1GFhRpSkzzlQcKpjplvulGhG9hYAFW3eYy7NHAmWGZOPKnjT65TKehykylmWkabTToRLyrKNDQUBsXLeURzMapzCy4wTg2kSdTwtnfhfGc3MziZZ6nU3V0zTZSol6x2KAQBfvIgNrYQmXGOAHGpa8tGKtY%2BGZYEc4ez9W128ZPqjpXBEozOcCeMJR9woQ5iotrI57PsKH5I0V7U6UXNzMK8%2BsfkgN%2FcBFbm5rHOYElOuhbSsIly1rEEPEfnjk%2Fu%2BH8sdg8DuHJGn4xx1MyqlFftV6M3PYXVH80cfd3w%2FlgIR3ZkKCrhBAFzen13l3aHY4TjuzIVQPCGkX6PRTa6m47bJdj5v7pvHh93j%2FNj7tTr4R8ZV5nH%2BWCNGReJh%2FwBf0w%2F%2BHMeXWY9uWiScksTt32TWqYq3faXIjyJRePotGpyZ1pNUTRVEqCgqUdJ84ir4i6nkk%2Bo%2FBF0POACRtC1gImWCm4ANwfuTEUJKz5J5bdUwEsInKPMf22k28%2B8A3v5K%2FimAgAL7xXW3YJ0xJ1Lcz8UxVQ4h3Toura%2ByTAU0t3vvyiohG8RIS3rJPLfYdnZE7Y33gJrADlEu3miKwpdyk2T27GJAOd9RB22SYCBtEhBvFZIFtXannZJvaKDi9C%2BslZ7baTATaPPFJznaJ0LBN7L523QecAjrclG%2F7AwFIRFaSOW0VC3v774pidbbegEFV%2FQYCghClaSDzNo9JRteKbagSBvYG17GPQsdT4bQFFIF%2BUVYho6MWWlzdX3Cr%2BeBWBzLnxDADvFFxAj0E2Om6792gxSXa6xZw6PK6h2%2BSA8y0RLYxW1JOoLSsW%2FYK%2BaJCtruc%2BIr5oCgR2GJdG94mLyLqGle3%2BLPzRMpOkAqQ6Li%2B7avmgJLCJdIifULX6%2Bnv6NVvyQWlNklO5Jtt3wEoG17RKsHlaK6WXB%2FaHvwavmiVTS%2BXQu%2Fg1fNAUkoV3xOExMlsp8ppz4W1fNE%2BlQNuhcuOzo1fNASWbHOHucT%2BLTHZLTBv%2FiVcu%2FlE3izqE6ugmAOy7KrX9UBRLaVHaKa2yPRHr6F8jeUeJ7uhV80UbOk26B4f6JXzQFAjbmIkQN49apSaKSRKv2AufcVfNHnbso3G8IGU5iADhaw6Cnf6oKjfzexxvHX%2FBmFDhooZKbapCfI848dXHIOZgUOGDDiT7zHq0q9PsefzR17wZuFfDTREn%2B1yM8gfBOKj5l7pXyOx%2F1KfVU7WFRx1eb8YcCubzkx%2FnL3%2B8VHR3AokHOCp%2FdGgP2%2BBxsmOcD%2FAFS7%2Flnf94qOj%2BBf%2FjjqH%2F2%2FM%2F7xEd3TX5gtvNHrhqYf8pp869ZxBauL2aCkp0nK10JI7uhXv67iOcGO2Okc3QDxcTadRucrnwUkbD3NXL0xzcx2xt6H8eCXef4YY7%2F8fV51QmJFg9kR6VAPL4YlW62RfWB8MelaiSJYlXNSx8qYQm2ytR2iXpWCojxlBIISLKHPs2gIkQtbsiCnGykkLT1ed%2FNEvjEupQ1PIHpNoCKkX3iS0T60dT3UDWnq73v88S65e1%2FGG7en5YCFj3RI6OodoqIeZKikvJt3xPbWUqQUqINjY33gPKiKmkxUCW0LUlekHvAMSrcb5a0%2BvlBMJdgbbG8QWm23LtiA3Nw6nq9kVLto6zirW23ghSse6JRzMVitsmwN7eaItto1FWknu2MEKQGo2tyiqnfaIrsk3KT6okCmx1rn1GCVQJte9jEiyFXATaJ0LQeQ3vyIMQQkOK3tAUUt7xVGlI5RMNCVKSVWI3Isd4AtmxJVax7DaC4Ele6YmCVDmPVE7QQRs5ceg7RFSkpO9%2FSUmCikEbxUG0OlSF3sdv2JiK1JQLLCt9xsYCmsoJtb4IlU2k7hR9EQ1hRsNXp0mKhuU2tt6ICgpFoJsBaKhLfao%2BT3GJkIQG0ruCDzBgKaUDnt64qp2G0QCmrXU4Co9g7Iam%2F1RPwwTCPZe%2B8VCfJF9j5okQtm2rpEbROpxnazgNxBBsL7E2gLW8nlEmpsgkLERDidP2wb784CcG%2FZEdxziZsBKeYidtKVEkEQFMdY9U%2FBAIcUu1toqqQUKGkE37hHobbSD14DLJNoo4cc6HVDcUylpHw1Jj5o2T4NOdfUrHFLCW%2Bg8bpc2Tp6%2FSXcRa%2Fda%2B3fGAJUBw1ZzoA3NPpV%2FR7Is%2FnEZz4MwKFSxyotq0KdpSNdttWp02v32B2jxWnvzJaz5afv0uphHx%2BX9crBeK6%2F1wWM9%2F8AlLBH4BMWLJO5zhwEE9uIJTf0LvF84phr4gsZDsEywj1Moi05JpUnObAQbAOjEMnc%2Fu%2BcZqpy0Xj%2FAEP%2BDFYcV7if4o9cOh%2FCIoJwpl44OScaJSfhZRb8hjQ2dBtm9i4J3T7KPWPmvG%2BfCILUMI5fIAuDjZBt32YR88aJzubLebWKCoWKqi6o7W7TGl7nPHgVE%2FxVesxL5TV%2FXIwqJImXYKuVEBQglKCLl3rK2AItePeNNLBPOIKSk7dIBq2G%2FbEVNKaT7pdI7SUnaAmimoXMTNqDw9yc1ehJMRW0po9dKwb2PUPO9j%2BaDGk6LzRKW7HlHoS0sjQrWle5KSg7gb90SlTYTqOq3fpMEqOi0Q0picuNhfRrK0qvaxQfmiYJCt0q9Y5QFHR54jaJ1AJBKkFOnntsPOYpiw69yQe3SbQEwERiRTqEW6q9%2BVkGJlahpUpp0JUNQ6h5eqAjCFlm1mnd%2BXuavmgUuDmw9%2BCV80AiXUkdkVEJfUlR6J3VcdUNqva3daJChajrKFgJ7ChXzQDWO6Ib3iu20tXOWd%2FBK%2BaIICi7ZaVJ7gUkEjlfeA860ddVohY90evxZ5xJWwy86lBssttqUB6olbkZlY6kpMnV3Mq593KAoJTfsifRHqTTKgRpRTp0nv6BfzROKbUiLilzp83iy%2FmgPFo88LGPd7FVPdCaNUVL0lYAlHDdPm2iBo9Z7aHUh%2B9HPmgPCtA5xJccrRchSKsRqNFqG228svu9EU1UWsXsmh1K5va0o4b%2FACQHkR9z8MUzzi4po1Z1JT7CVElXWB8VXuO7lFGap87IupRPyMxKlxN0pfaUhRHYReA8dt7xMDHtlqRUJ1K1SUjMzAbNlFllS7E8hsIre12uAkmiVHSOavFl2%2FJAeCK0ujUq8ez2u4g1aPYGo7c%2F0Mvb5IrS%2BG8SBSgmh1Akc7yyx%2BaA82nzxDT54urWE8WPEpaw5UVqFrgS6u34IrIwXjJeycK1PY2%2FqZXzQFj0XP8ANFSxCIuRwtihK1IVhypgovq%2FQytrfBEUYYxIsAow%2FUjq5Wl1b%2FJAWglXfEsXY4VxRqsjDdUXvbaVXufVHhmqbUZFwM1CnzEo4dwiYbLaiO%2BxgNk8MyQc4qOoi%2BlE1bzfoZ2MN8HokKztWb7pwzUSB37oH54zHhn0%2FVjpW5HuE3c2v%2Fydy23pjD%2FB5WGdTp03UMNVH4B7mPzx5bTL5kvMfwy6OHfKKfO2tx9KBzqpf%2F2zKj%2FarjmlajeOk%2BPiys6qantZw5Kj4C6uOa184y6IRlgl2834ywXyf19XnSwhGe5eZG5oZoyjtUwbhhyYpzDnRuTry0tNKUPKSgq8tQ7hHavt9u2H2fv16tIop1ZzOUMVlY2lvVubOM5YFDeN2fWf55mwOGpcE%2F8ATmiPyxVRwZcQCyoDC8n1e3x9vf5Y486WYHGu92fWhsxht7nVRLSaInjdqeDbP%2Fa%2BFZZFzbeda%2BflEg4Oc%2FxbVhKWVflafa29O8I0swOdV7s%2BtB3Mvng5aTVziEbyTwaZ9AalYUlVGxuBUWrX9cUfrOc%2BtfR%2B1Fi%2Ff46388XjSrA5%2Bt2fWg7m3rmS0jEkbxPBrnyOWE2D%2B%2Fm%2Fngvg0z9CApOEGdzYjx1skb%2BmE6VYJ41Z9aDubeuZLR0LXjdauD%2FPxN7YPQeVv0U12%2FDEx4O8%2Fhe2Dmjb%2FprW%2FwAsOFOC%2BNWfWg7m3rmS0l0YiRSADG7k8H2f4trwWgXvuJ1ojYX74h9Z9n8tK1pwfsknSPGmrqHovEcLMD8bs%2BtCIw%2B9cyWkdNoaLxvF3g8z6b0q9pxsQLpE01cG245xL9Z7n%2BVJSMGjrd840LeneI4WYF43Z9aE9zb1zJaQ0iJtCe6N1r4PuIJGq2Byu3K041v8sQHCHxAnTfARGoX%2FAKsa2%2BWJ4V4JOq92fWg7mXvwctNyaZEz0qmrdOacp9tM74uAXhLlQ6Qtg7FYTcgHa9o63yJxJwe4QxpUK7K4%2FwAc%2Bykzh2fpynsVt6G3JZ5AbebQpNyp4tgBIJ5WtGqV8IGf4KdOBXLr5folvb077RMOEHiB0g%2B0V2xAP9UtbXPLnE8KsDjXe7PrQnuZe%2FBytGOZLhvlcKLl8qcX5jv1BicZck6ZW5VCZHowdC1Eg2Cuj3Sq2raxi8cKOa2E8m8428aY1cmWqT7Dz8oXpdkuqQ8tKejBSN9Kikpv2XEU%2FrSOII2SvAywr%2FO2iD6N4gjhJ4gFA3wI8k2uLzLW%2FwAsOFWCTHyuz60InDb1Guzld8ls38tm8tK9kNnxS6hMYOqtUdrdKqdNB8bpk645qKgE7ixstKxexKgRYxPxS5mYAxwnLygZb1ufrFOwVh9yluTk80pLjyitGgqKt1qKW7qPeYtH1o2f9rqwK8ne1zMtWt6bxBfCLxAC2jAzpv1VDxpoEH18orGluA%2BOWfWhEYdep1US3HR8wMhJXggOAEVije2QYecnl0my0zKa8XSUuI7nAbEEGwHmiHCHjfh2w5kpiHCWZlaocnVMRTc%2BxXpKouLS5UJJKAZa55W3JTpsdQjTieEniCv1sCupsNrzTXzxKvhP4giAF5fzCtrn3ds2817wnSzAo4t92fWhbuXe%2FBy00hBQ2lvRpQlPVB5gdgJ7TaJbHujc6%2BEfP8o1%2FU%2FmP3L7Z%2FPFMcJefijb6ns8PP0jdvyw4W4FGu92fWhE4Ze410S02W9okKCDG5V8JfEAF9GnLydXt5QcRp%2FLEPrS%2BIHkcu5u9r%2BWjn3XvDhZgU6r3Z9aFZw69R%2B7lpvSYaTG4xwnZ%2BklJy7nQoJCrdI3v5ufOJ1cJWfyQknLuc63YHW7j5YcLMD8bs%2BtCN4XrwctMdGYBs3jcw4TM%2Fjzy4nhY2PujfybxFHCbn3ZQcy8nUEDbroNz64cLMD8bs%2BtBvC9eDlpwNiI6PPG4F8J2fSVhIwBPHzhSLD5YpjhQz%2BNz9T2dP3IDiL%2FAJYcLMD8bs%2BtCYuF65ktR6PPDR5424rhTz97MtqiP3bfzxH61PPqxP1OKncdmpH0onhXgnjdn1oN4Xrwc9DUUNHnjby%2BFDPpGjVlzURrJB6yDp9NjERwoZ%2FlVvqcz4G2%2BtHzw4V4HnlN7s%2BtCYw69VcUWctQaPPDR5426nhR4gF3Ay2n9QNra0b%2FAA3tErvCtn60RbLifWO0oWg%2FnieFeBeOWfWhacNvca7OXgyYzGpGBDP0iuuFqQqa0OeMBJV0TwGnrAe9I079hEbXfxfkXVZpU9VqtRXph%2BxcWthtRUeVySm99o1aeGLP0W%2F%2BF9W38yfnjC8V4DxdgmoN0nGmGJ6jTjrXTNtTbRT0iAbEpPJVj3RoVUYRi94mq7Ximqqrkpqic%2FQ%2BgYNp7i2A3Gm5WlhFdFGqaonOI73enXxN41F%2Fh4cJVLzVALg7FtAJ%2BSLYGch1EqD2Gtv2Ko0Fo6P3ghdPa3G3Gj9nGq0q6W%2FHutXjLjudnPo%2FJvnxDIVxZIew0Vdt7iJ0ymQLTiL%2B1hB7BpUoH1mNB2aVsW0n0iJibp0FIKe42i0aP0eFq6WKr3V7Sr6jZdH5N%2BexPD5qQjxvDaSs2FrwRKcPqSEomsOFROkagdzGgglI5NpHwRC6e0CLdwKPCVdJHuq2tPwblZdEbG%2FOhyEKQUTGGN78wRFVMrkQCFIfwwb3I9zJ2vaOfwUp5AeqJi7caSE257CHcCz8JV0rf%2BVrbxKy6PydBmnZBPJS30%2BGkBW6Ta1x6YKpuQDCEhc5hrUTYXI29Mc%2BFTRFlA27oXZ%2B5h3As%2FCVdKse6raxOe8rLo%2FJ0zgKg8OM7jSlS%2BIU4XdpTr2iZLp0oSCDYqUdgLi1%2FPG3kYP4HR1G2cBn9tMf0o4JDmvqqKVJ7uyJvcz1VNtkd1hHcwy73bDrOqiuma85zzmfyfONMMWvGld9oveVNjuacsqY4p45nPXHHxu9F4Y4I29VpLAg08%2FdAfzxBOGeCR9H9T4BCd9y4B%2BeODrNWv0SbfBEfc1dXom%2FiiOlvm5%2BB7fyeT7m3mf3%2FwBmfad6DCnBMvUhLeX5K%2BtbpE7%2BjeKD2DuCRA6TocvlbW%2B3f0o4Q0tJ5MoFuVkCJdEuDfoWb%2FtBF6b5dY1WPb%2BSO5dv4fsn2ndbVC4LW06GpHAShYmxeBtb0qiZ%2Bl8G7rmlxWCEq57TVt%2FgVHCfRsK36Nr4sR0Mp2DLJ%2Fcj5otv27eB7fyO5l58P2T7TuxWHuEOZYLRnMFOMqO7ap0lNwdrjXaIppfCu0yliWxJh1lpvqIbYrj7aUD7lIDlgPMNo4PWhrtZb%2BBIiRSWO1hv4oiYvt2j9z2%2FkrOFW8zx289E%2B07wFT4cGVnosYyCFH3ycQTH%2FqR4a%2FNcNNfQyK5WKBVESQUGPZCpqmQzqtq0a1m17C%2FfaOGS02eTKLftREOhavfoG%2FiiIm%2FWHgu38kxg9rnn7%2FPR%2FwBnYWKc6sqcuMIVGmYDmaU9MPSr7FPkKYm7aXXE6ekXbssdzHEFVSGZboUG%2BhFvki%2B6UpHVQlPoFosVXI0uftY171e98RTRTTuaaeRu3DD4ucVVVVbqqrXPm6WFOmJUGDhiVBMabfeptzRF%2Bw%2Fi%2BuYenZeo0WrzkhNSqwtl%2BWeU042oG90qSQR%2BSMbj202Rcn3ShL7LKEJ1LceXpQhPeTAdG0Hj24mqFLCVRmMZ9ASpOqoyTUwvc3vrIBJ7jFkxxxn8Q%2BO6e7Sq3mVPMSb4Uh1mmITJpWhQsUKLYCinzXjSVQkn6ZNGTmFtqJSFocaWFtuIPJSVDmCI8hPngK01UFTCypSlG5udRJJPaSTzPnjxlzsiVxdopa94CtEkL7Xj30ajLrTq2kT8lKBNhrmng2kqPJIJ7YC3kkGIavRCalX5SadlZkBDjSihQvcXBt2RJAT6vREQQYpxMDeAn5RNcRTBtE1xAR1GGowt5xC3nEBNEQLxCJkwG7eFJJOPKqrsFKI%2Fhj5ovmYAclslapOJSdMxiShNJcT70tyc0opv39YGLRwmW9vtU1cvY0X9GuLxVcNV3GXDjTE0dtt56axe64pK3gjUZeScOgXPWWEkmw3gNBCpAC3SqI1a7FXvu%2F0xBdR169Tl%2BkUFq35q7z54yk5EZiJt0tJ6O9uaxEPqE5g9GlxNOCgo6eqq5B88ApmC5yr0xmpOViXbTOXWW13JIv2%2BoRCfwTUZZh932ZlXLI1KTY9e24i7U7J3MUoalg9MsEdXQpQCUnuvyiE7lFmEypbRfnVkbEdh9WxgNcCovdbW8o9InQvfmAbgHvF4j4%2BABZZ1aSCbk3B7PPG0cBZPYuoWNsN1ms4WE5TpWpyz82y%2BgKZcYDiSsLF90lN7%2Ba8Wys5C46TPTUzK0gJknZlwyi2jqbW2VEpKT3WtzgNdeOu%2FqyvJKOfYeyKfj84jTofc6qbJ63Z3RnAyPx%2BoKKaOshBSCb2G%2FIwbyNzBdIApIHpcFoDBXJ2beSUuvuFKuYKtjHol5l4Wus2jNlZFZgpWhIpTR18j0otBeSuPmDoFPl1kXuEzCdrfDAbr4MLqxvNsEbrmaOsfuZsn1Rsrjnt7OYQHb4rOn%2FbJjEeDvCtVpWN3nJ9tCLexmpKVhSkETRIuByBsbHzRl%2FHKE%2B2XCW2%2FiM5b8OIDlxYPRuR2DJuus06RZZJJTLsXUR3tp5dwjkZbRWmye0x2W3TmHJCR8XaJUmXZ2JtazaeffF7Kcq%2FRsYrb4Dwy6XZvYhWsc09p9MXagz8zRJtuqSiEL6IFt9lZ6jzChZbah3EbeaPUzT320LW3LKU4oe5ovzV3GNn0jIyszFHYrM8G0InHPckL2vYElII7fNGxNrTTVFNU8ctT3uZjOGuMSyDTcqxPYbU49T3klRYVu%2FL96FjtA7FDmLRrur%2BzbSlzEnJNuL3Xbo%2Btfz280bZxvhfGeX1SZU5KpfSgh9LaidG%2F9pChyJ2uPgjU%2BOcz8VTqmphiaNMmHkKL7dPYSy204nZIU2LkdgN%2BfONqzimac5lq2tNecRTGvysek8yMT0Koy9Rp0wlicknNbLzaBqbXYi9jt2mLTK11c08xR6LT5io1OYXoYkmBrddcUeVh3neMYzAoePJnCrWY07JsytIq8yJYTMs30YedA3UBfvBue%2BMLwzjHHOB33p2jPPIam0Flx9tOlwpPNKXR1kE8rgxiqtImP1cs9FhVTGdXRm6ad8Wy1pU1QEVVqdxnWmejrc3KuXapbCv%2BQoUNlL5BZG3Z3xinSILfQIWEq06bxhWHcSylSlm%2FFro96ttfloV237%2FTGVy%2BtbfXPlJ0qitlEUURTnn5e%2FJaRVupmXgrNI1YfnJhWguICyRf3towWnsBsoc96nsjaU%2BGm6BU2OlWrVKKIJA3KbbeoxrBooCUnUYi0pymGaxnOGosaOrZq1aUk%2FbJhQPqAixYckq7iGqylAosu5PTsyeilZZI1KWrchCB3nsEX%2FGDXTT9ZXa%2BmZUfUYsWFqlX8P1uWxLhiaelalR3UTsvMsH3RhaVApWPQbRqVa25Gpc5PFU5SHW35ZltS2DZSHQUqSsHcGPWziWfxPNmXMnLNOFDiwdZFyEk239EWmkUeu4yrAptHkVzlRm1Lc0JsFOK3Urn289ooO0io02bclZpl2WmGTZYtYpNvmMVSoOVoLPuktb93FP2UbPJhXxo80xKrbcU2lClBPbpMUehd%2FU1%2BqA9pn2z%2FaFeuHj7f6gfXHk6Jf3CodEv7hUB7PZBj3zB%2BNEyalKDnLKP7uPD0S%2FuFQ6Jf3CvVAez2RR2Mn1w9kU%2FqJ9cePoXf1NXqh0Lv6mr1QHs9kldjPyx6peYTMpskFKk7qSe7zRaehd%2FU1eqLjTpZxvWtwWUoaUp7SID0xAjuj0Ny5PZE6pUjcCA8dj3Qj2plCewwMp5oDxRUTFUy5HIGAYV3GAgkkbxUS%2BobRTLKhEpBHOA9PjESqfB7Y8x5RLAV1OgwbJUYoKvFVg27YA8LRTAis9YxSTAXOhf1zlR3zLSfW4mOufCb9TiHk2%2B7CdHT8AZN%2FyxyRh9OqqSKf8ApjH%2B9THWvhOVauJYN8uiw1Sk%2BuXSbQHHbnOJCe%2BJ3OcSEXgGsxUbVFLTFRsQHoQq0C5btiAAtFNcBVDx74gXD3xQiIFzATlxUS6ld8TBtRiYMrPZAUxqV2w0nvMV0sLiYSyz2GAohJ7onSDE%2FQqETBlUBT0mJgbbRUDKjEeh35QEEX5xcJM7R4kpttHtloDMKV%2FWr4T%2BWLjlPKibzjwykkgNTYeO1%2FISpX5ottLJ9i%2FhP5YvuSM63JZ34bcdcLaHJlTKlp8pAWhSbjzi8VnVK1PHLtXBGJMGvVdOF8ZNPyCatPtzKKjbXKF8IKENTjXMtX3SseSrmCIzCbx81gGTnS5RlSTKXSypqV60ssp2uADpCdr3AAMYJhOQpM%2FiSnsVlxEvJqmikPTBAacWCQjUv3iVKABJ2F49WatfxJXq4cO4kwbMYW8TltUxJNKS427Y2DiXBsppQGxTcR37KmiLWZqji1%2F%2FAE87ed1XRTTTr1eTKMtc9%2Fvd9g1PnGscYkqk0zPyq6nMulyVZW5bx1F90oUrbpEptZHMjlFySmal2XaY7JFL0qoKIUAk6uRCh%2BQ%2BaKU3hPA1Pk%2FHaFMz8vPJAPsZNoS8zME83GXk7oUOehYB22MXKgS1exDPU3C1NknZmqVWYEqwBZe59%2Bo8wANyeyMN4rzztZbN1ommIsqePkh9D%2BG%2BanJzI3B7899t9jwjlbqJWpKP4ITGyotGEcPS2E8L0rDMn9ppcm1KpPfoSAT8JBPwxd45Ecet19RCEIBCEIBCEID4DcdZ08S%2BZW3lYjnPy2jnqYVeUl0294CfhjoPjq34mszOy2I5z8o%2F%2Fcc8TRtKs7HdKYDOcO%2F1L%2FokfljYmWuZ0%2FljUKlPyWD8L4iFTZbZUzXpATKWNCioKav5BN7HvFu6Ne4fT%2Bhj5m0CNkZRZQ4tzlxaxhrDLCmZVC0KqdUcQSxT2DzUs9qjYhCBupVgIDZVK4nK7XKtTqGjKrKGjipzbUoqfnKIksSoWqxdc6t9KRcmJ%2BKfN7AWL6gxl7ljh6hClUKeD87iCRkG5dU7MoQUFqXKQD4uCokk%2BUbW5XjHqtjbhvwzVH8NyGR9cxBSJJ5UvNVmq1pUrUnlIUUuONsJGhsAg2So374sWZuUlcwh0uL6Jh6tt4BnnGTSKjVGAzMdG6gKQl9sElF9wlRACwLiA2zgmcTJ8BuN5vRrLGKrpBPMl6XFvyxzw5i6eQ4v3BryvuiY6FwVJqneAvG8o04EdJixN1nkkF9gxoFzBb2tf6Pa%2BIYDpPgLxC9UMdY4lpiXQEe1RSysHlZ02Hw3%2BSORu74fyx1twK4ddpeNMdzCptDgcwr0OlKbf24m%2FwAhjkki1vh%2FLAQRHduQaQnhFS3zJptd59%2Bl6OFE847n4f3Er4STrHkSddv8CHY%2Bbe6dOWHXf%2FVj7lbr4R8ZV5nJWV4SvJLFSu1FYp1vwB%2BeJ6K0VTzS0pQVNnWkL3TcC4v5riJsn%2FFHslMZySnWjOKnKfMsM6x0hQhsdIsJvcgX3I7okp1%2BnFhfqL%2FimPo1nqcmdbDqpnbmRSyiWcrDLqgyhVzJMDmOQsjlHgRxF5kNeTUGPhlmfoRiWLajJ1GbQuQWVoaYQ0VWtcpG8Y5F0Nnr4jMzVul41RoKII2lmRYHn7yIt8R%2BZzYCRVkWHL9Dsbf7ONXwgNqHiXzWUSTXbk2vdhjs%2FwBHEfrlM1tv%2BEChY32aYH%2F441PY90LHugNtfXLZp9b9P1dY3PuDG%2F8As%2FPEqeJTNJFtFfdTblZtj%2F041VY9xhY9xgNou8ReZ7zZaXXVaVG6h0LHW77%2B5xs5pCkTInNCVL09NptcainVy9McwEEcxHVbLYUsBXVHi5uO23QwGqqjnPmRT2ZVa8RvvF1oOgrQ31b3G3U25RbBnvmGCpXsusqVcEkJvv8AuYxmuzzM4xJNtXKmJQNuEi3X1En8oixQGxRn5mOnyawtI06bAIta1vuYiOIDMpKriuujvA0b%2FwAGNcHlEhvfaA2d9cPmdbT7YHrWt7z6MSp4gMyU2tW3RYkixTzP7mNZb%2BeJkgnsgNkqz9zGVsay6R3HT9GBz8zFUkINXcsNgLp2%2FgxrfQr7kw0K56TAbG%2Br1mQ5Zk1x0IUQLWRbn%2B1jb3QIRrW1pK20laSdxqCbg%2BveOXW0qS6Li1rH5Y6rlQVPWCNd2VWTyv7mr%2F8AfwQGr6vnrmzTjKleNak94xLofBUWrAm45BHmi1DiGzTT5GJ5xPoUj6EYpX5pie8RTKm6JaTbZuRbURcn8tvgixlIvvAbGTxDZqot0eLZ5FhYWUj6EVfrjM3CvX7c565NyQpsfyI1lCA2eeInNsr6T26VEKve4W39CCuInNtV74zqJvzupv6Eax388Ot54DZ54i83TzxnOk956K%2F8SJDxD5tkpJxpPkoOpJ1N7H4kazsruMLK7bwGzUcQGbkw62h3G0%2BsFSU2V0ZFioXFtG4jZEx%2BhKrNPMJS0phb7yNIBCFhClAj0HeOcpZCmplBUdIQpJN%2F2wjp5yQbmatUE30hbT6xfs9wUqA1jW84c1KKJVhvG1UUHJZqZGpxB8rf7nvi0HPzNYkKOMJ8qBvcqTf%2BLGPYkqEvVESLkspSgxIMS6yoWupKd%2Fyxjw3MBsQZ%2FZqbasWzyrcrrTse%2FlD6v%2Ba%2FTLfGM6kHHAApXSi5sb90a9KD2RCxgNkDiIzgBSr291YlJum7w2%2BSJPrg83LlXt2qdzz91HzRrqx7jEQ0tQ2EBsRPELmyghYxlP6wLBXSC%2FrtFP6v2bGno%2FbdOaO7WPmjX3i7v%2FsRN4u53wGxGM%2Bc2Zh9ppzGlR6NxaULQHtlJJsQduREZ%2FUm0NT76G0hKQskADYX3t8saHp7NptorT1EOIKz3DUI6FqTIVPTCtQ8odnmEIF3zPSTwuYeUOQx%2B4D6fY8x1rwXo08NNHNvKlJ9XrnFGORs4KlSJLIPDOCn65ICvDFiqk9S0PpXMNS6pKyXVpB6oubb77x19wauJd4a6IW0FGiQnGzc3usTS7n5Y%2BX%2B6ZM70sIjwlP3a3bwmM5q834w4CWQqZdKeXTOgecdIreOjeBQD6sNYV2jD7gHwvIjm4E9Kr%2FKu%2F7xUdI8CqkjN2rc9SsPvEegOtn5o9Bpt8wW8eSPXDTw%2FwCU0%2Bdes1ElXGNU0uKAR9TJzn3dCdvXHOK%2Bo24o7c46OzRMjLcaE%2F7IT8uyiay7DSelcCApxbQCW03O6jbYdpjneZlX5cvyk0ytp5pa23G1iykqBIII77iNvQ%2BcsEu38kKX74%2Brzp8W5u41wROT1Kw87SWZGmzDMoy0ulMO2T0CV3KlJKlElRJJPOMQ%2BuVzNHP2BPpo0uf5MU82JyS9mK%2FTwu0wmrNrQg89Alkg3%2BGNZLFo9O02z3uJbMt2xJoItuAmiy4%2FkwRxPZnNDShNAt%2F2NL%2FRjVRAvyiSx7okbaPFHmoTfpaKPMKRL2%2FiRBPE%2FmgjyTQf3VGlj%2FIjU4BPZE3QqO9orI2wnigzQF7uUI3N96PL%2FJ1NoieKHM1TRZKaFoJvb2Jl%2B%2B%2F3Ean6BXd8kCwoKAtz80QNt%2FXQ5puf2%2Bi%2F6olvoRkTlZnsVyNPxRUm5VqeqUuXJkyzKWkrXqIC9KbAEgC9u6NFSLJU8QUxvXCsuJnB%2BHnwLoVKuov3lLqwYDxYnzUxnhlyblpFdPErLTypVhldPaIS2lA2JKbqJO5JMYweIHHilayKTfv8Qa%2BjEc15qUNSrVODoMyxXH1FsDyUFtI%2FKI1pp80BspHEDjpobJpRPLeRaJ%2FixP8AXHZiagSaYSFBQ%2FQLXMcvexq8pt2RKATygNrJ4l8ykrUsO04FV7%2FoFje5v9xA8SmYZFiafy038SZvb4kar6MxEMqPIQG0vrkcwu%2Bn%2FiTP0Il%2BuSzHA0pcpwT3GRZP8iNYGWdQhK9OoExFLClKta0BtNviQzLt1XaWP3gz9CMoVNTVdlWa5P8ARF%2BfY6VzomwhN76eSdhyjRtNb1uRvnDTCHcLUt4HUl6Vs2q1vfqSR6QRARxRnzmfg16YptLqsiiSlZlcpLMGlyxS002lISkEtlR2JuSSbmMWHE7mnr1%2BO00q%2FwCzmPoRbM05lhyenpD%2FAJRKVacS6DzF%2Bjt%2BQxrxKLQXbY%2BufzTBKhN01JO5tIMC%2FwDAiqviuzYUNJn6eB5qfL%2F%2BnGoHE3in0QPZAbhVxV5sKFjVJQ353kpff%2FZxA8UmaaiFLnJJRA03Mkxy%2FBxp8Nb8oqluyb2gNtfXQ5n7%2FoiR3Fj%2BgmO%2B%2FwCpxTd4nMz3bXmKcLbj9AMfQjVIZUVDuMCxbsMBtxriczVWpJVPU0gDSSKZLE2810RlE3NOV9MrVp9DXjVQl0OTC2mw2lxZJGvSmyQSAL2FrxoinoQrYiOgKTLpdomH5hsBQXIs6SN7%2B6KH5YDGsR5xY1wo%2BqnSXscJdDz7bTS6cyQ2ltekJuU3PpJPOLKOIjMBJ1Bqi3%2F7Na%2BjFszVcl3K7MSjb2t6Un6g08LeSrxg2%2BTeMLKEpTciA2IeIjHwKv0PRrqNyfY5rf8AgxOOJDMRN9LFEFxY%2FpWzy%2BLGsli%2FKIdGYK5NpDiXzKT5CKKkdgFKYsP4MTnidzMUCks0GxGn%2BtDHL4sarDBPbDxZX3UDJtBPErmML65ehKvvvS2efxYmRxMZjoSpAl6EQsgkGlM9n7mNWmWUOaogW7dsDJuel8TOZSXkJCqGgLULhNFlzbfzpjJDPTNW0VWbDXTziA870bYQkqJN7JGwG3IRoumpQh1hSlDyhf1iN9UhlC6JSlocStKpRJSsDYgqURaCGUF0jhszla0EDxCkHX2f1xZ2%2BSNkeDLcePt2lkukseOUp1TfYHB0oCvi3Hwxr2pliR4YM2FTc2wwufRS2pVpbgC5jTPtFWhPNVrEnutGf%2BDMSkTeNyrUF9PSgBbbTd2%2Fw3jw%2Bn85YJaeej79LqYR8ohr7iiXqz%2BxmDbqzTCR%2BBSfzxaci7nOnAaOxdflR%2BU%2Fmi48UCic%2FMa%2F5%2ByP9giLfkWnVnNgIpVYivyp9O52jatY%2FwDVo%2F0P%2BDHY%2FKo%2Fmj1uhPCHWOEMAXG4xs1b0FhP5xGjM8wTm1iT%2FPVRuzwiUxLs4Zy86R%2FowMYpcO9gEJZRdXwXEagz2aQ5mhV6nLrbfk6gvp5aZaWFtvJupJKVDY7g8o0vc6pywKj%2Bar1oxL5TUwmexxiPL7B6KthaYl2Hn51xuaU7JtPqWgJTpTdwGyQSTYdpjD1cS%2BY6iekdkDckkCRYA3%2FcRccyJtmTwBKSburpJ%2BdmC1tsQ2lu%2FwDGjS5THu2m2o7xL5jpRZL0gn9rJMD%2FAPHFEcTGaIWXBUGNSuZ8WZ3%2FANnGrltgxL0V4DbCOKTNtoaWqw0gdyZVgf8A44HilzfVzr%2FqYZ%2F9ONUCXvE4lNjtBWW0vroc31EqOI3CT2lpnut%2BpRM3xPZttp0NYg0%2Bhln%2FANONWiUFuUSBgJVyghtYcTucejohiRZb%2B4LLBH%2B6jJcK5j4qzHkZ9vGFSE6ZDoxLK6FtJa33sUJTsb73vyjRbCPPG1coAAzWwkm7SJcnbsUu35oDJ8U4sxLgHD0tN4bqAlfGUvvzGhpJU8ULQgBRUDsLmwHfGBniEzIKSkVXmb7hHP4kZTnFOsyuH6TTnFOqVPSs30Q0jSkpmEXF%2FQL%2BqNHBveA2KjiDzObv0dZ0352CfoxU%2BuKzV%2FXG9ytzTy%2BLGtlN7RIhlWu99oDZp4js3LBKcWTaQLWs4ns%2FcxKriNzeV5WMJ09u7g%2BjGvES4IvaDkrdOwgNgK4hs2FG6sUzBPfqF%2FWBFH6v2aF7%2B2OYB79X80YEJXbkYkcY0tOL%2B502gNjJz%2FzYWoLGLpkEciV8vkjKcL4xxPjSnrXiSrqmzLLAZLhuG7kg72vvtty2jTlMB6ONm5XOtuM1KXRfXLqaWv0KO3yiAynFGPMcYAw3Ke07Es5SmT0sy%2B3LKCEvul3SFL2uogbDujBXeIvOV6%2FSY5qJuLGzxF%2FUIv8Am7OMy1BpFPLLiXpqXfc1XulaUzIsfNblGoS2BsYDOzxC5v6Qn281UW2FplQiUcQecABSnHlYCSLECcWBaMAcauqJAz1tMBsMcQ2cKRpGPKyBcn%2BrXO0WPbA8QWbyiVKx5WSTzvPO%2FPGvxLEpO0TmV8nbsgM9HEDm2DqGPKyDe%2B065zta%2FOIJz%2FzdSnQnH9aSk2uBOufPt8EYGJUlShbkLxScYUEah2QGxDntm0pNhj2ti%2FamddH54zTCuJsUY4w%2B87ifEE7VFNzDTjZnX1PLbJCgrQpVyAQBdPLa8aak7BEbdyjclpmi1ZpJBXKTculW3LUlZ2PwGArZi4oxXg2jUk4brs%2FT2hKo1olZhTSFrW6slagk7q2AueQFowA50ZmlIQcYVMpHIGbdt%2FGjK88KgyzL06iLSendpzE0gg7aA84n13%2BSNTaNoDKV5yZlm98YVTfY%2Fox36UUTnDmNp0e3Cq2HIeOvbfwoxVxjUdop%2BLeVvAZc3nBmMggpxlWARtfx9%2F6cVBm9mOSVe3OrXIsf0c%2Fv%2FDjD0yu3OKzUsA4LmAyn6ruYugK9tdSNuwzrxP8AHg3nDmOggt4sqSCBpFpt4WHx4xPxZehe8SdAUpBJvAZq3m%2FmHcKdxfVbpNxpnXxY9%2FlxsHClZrWI6Z45WapOTziAkoVMvrdKArewKiSBtGk20AN2vG5MsJhqYwzMpCSHGJhtg3HaEEm0BufhrYcczip7Taes2xMuej3BzaMQ8HcWxm9Ugoe7KwxOBs32SOkbKvhIAEZbkninCmX2Mm8Y42rUvSabJpfaMw4CVOOOMLCW0pSCVEgE%2FBGKeD1ZUnOicKxYjDM6q3cCpuPK6aRHcS8T%2FC6WGxneKfO2Rx7m%2Bd0mf%2F6clhz7nVxzYuOkOPMpOd7AsQUYelQfhdcjm9e8bOiXzLdvN%2BMta%2BfH1edK5cSzznvkoUR8Aj6QS9VZyx4Y6fX6HLNBOHsHJqbDJ2Q48mWS6oqt90tW55x84H%2F6je6w%2B1KHyR9BMxWnV8IdSbSQkjLtw2PaESyCfkjyPui0xa3m42NfHTNc5x1Y9Uz0ujhczTY21VOuIhzu1xScYM8puoymVSZiWdSlaQxTXCggi43vcbEeuLhJcUHF%2BqXLjmUcnpTspa5R0aT5xf5I0RnFW65KZi1Zim12qycoJemuIZl595psa5CXJISlQAubn4Y11JVqrzEv0j9dqq9Sjq1Tzx1efyo9TZ6LYLa2cVVXejOY5Iyc20trSK545j0u45%2FPDitTT5mo4fw9Q6wmVmGpcoYkXUqWVi50gnfSAbgd0WJHEVxukXGSqlCw5U53t%2BGOQfZWdSpKhV6iFJVqSfHHbhXeOtz88Tt4prq2i%2BMR1ryj%2FdF%2Fs5%2B%2Fi3BHBOW70o3zbc52RI8R3GU7NsS8%2FlA1JNOKAW%2B7T39KE33O3o%2BWPVXOIPi0pjbDlNy%2Bp9UW90nSBmnTKej0WsDftN9hHFlOxJiSoMdKjEVUQn7k1CYPw%2BXEEYjxa9MOJ9slU6p7alMfTiOB%2BCZ5xd47dpvq25zrxrij4ykfbMlUOb2H6BeTfu9cXSncT3FpMqKajlHLU1kah070lMKGsC4RYDmeUcYOV3F4P9k9V%2F1lMfTiJxJinTY4prdue1SmPpxE6H4JV9Xjt2m%2BrbnOy53id4t5RwMMZSyk8NOousyb6Qk%2Fc2V%2BWIs8TXF2ltLk3kw22FcwZdwHzCOLHMQYiWNLmJKwodyqk%2Bf5Uef2xV81CUadr9WUha%2BsDPvG9uXvomND8Dj6vHTO031bc53O7xK8WekBGSjaVGxGptwAg8iPNsd%2BW0ef653i2l3EicyUYAUNQGlYJF7XjmPODFmJJvB%2BVzU5XJxZksGS8s2pD60KU147NqAUUnrEFRG%2B4G0axFcrJ%2FuzUfx136UTwQwPxent2m%2BrbnO8neJTilW2XmMuKMohvWGSy%2BV3t5N7WvFuXxS8YKDZWQrbovYnoXY4jNarLSA4a3UgBytPO%2FSj0VCuV2RlxMGu1RQNrAz73f8AtorwNwKfq8dM7Vpvlvl8J203xW8WaykOZBIQFX3Iej2T3E7xQSjXTS2UlLn1EizTIfCgPutxyjhf2XxQpjpTWp%2FTa9jUHvpR55Ot19csHG6nPBK03A8deFv4URwLwLku8dM7UxfbePpO3EcXfFaAQ5kE0vuN3AR8kXKm8X3EZMM%2FovI5lgu26N5bzgQnfckBJJFo4TRUa2ny6xPn9%2Bu%2FSiY1Sqffaod%2F9WO%2FShOheBct3jpnanf1vznc05xe8QMvrtk%2FJTT3aJZ57qJHabp3gxxicQU0jUMjUkp3Pu67m9rEdXleOF01epNX6OrVJN%2BemddF%2FwCFHroFTqc2uf6SrVGzSUgfox3lv%2ByitWhmB5%2FJ47dqJvtvP0ndTvFvxCplumZyImHAm%2BtwrWltJT5QvpjyDjNz7SsdJkO8pChdJQ8tQUPNZMcwVDF%2BJmuGyk0lqsTqZJOYNTW1aZcDiD7GyyVp1g30nqnTe1x5zGtUYgxA3bo8Q1ZOkWGmfeFv4URwMwKdd3jpnab7t%2Bc74c4us%2BVlpSMkJWyhfQuZd6QfwLRb5rjP4h5dS22uHicdCOsSC6QB37JjiFvE2J1vBlGKK3qUjV%2FXJ76USrxdi5ucEoMTVs6kjY1R%2FwClFo0MwOP3EdM7Sb9eJ4t07cluM%2FiPmVXb4bZ5aL809Ly9OmLweLHiJRpdc4d33EaA8pDb7urQeW5Ra8cJTeL8byelHtqrYBI2FXmPpRI5ivGziSlWKKwgHY2q0wfyqhOhuB%2BLx0ztTF%2BvEfSl3WOLriVmCoynDFWLdgV0pt6epHtkOKniYm063eHSZa2OkOF1Jv6SnlHAiMXYxRcKxdW9%2FwDrR%2F6cSOYnxE7bpsR1hdthqqL5%2FlREaF4H4v21bU7%2FALxzn0BHFDxRp6TXw%2BglIuOjmlEg%2Bgp%2BGKf11HFEFtiY4cJ0gm6FIK1XHxY%2Bej9erASot1upBQ5ETjux%2BNF2drVclaNLTMviGroU4EqWEVB4auf7OL8CsCn6vHTVtV7oXjnO95jiw4j2QgN8OtUUvdLoVqSEq97vpPOPFO8ZWf1PR0czw9zwdPaHl6U2O97J5iOSqFivEyMiMWNor1QITiuiHpFzz3StEys55CgrYHfUO2ye4Rg%2FtmxJy9s1Y5k%2F1yf5%2FGik6F4HyXeOmdp3QvHOd0TfGbnwwppP1C5gFwXILzgPq0x5pvjdz1lVlr6gFQKkGyyguKB9B0xxGzjDFLoLzWL68bEp1Cqv32%2FdQksdY4mzpl8W18b%2B%2FrMwP5cTGhuCR9Xjpnab%2BvE%2FSduN8dOcupXScPFXUBzPXuP4Mex%2FjXzmabQ8jIOd0lgTBHSLJsey2nn2Hzxw2jHeYHja2vbfiFKg0CoezUxyv36%2FhiZ%2FGeYT1r4wxELbb1qYO3xotGh2B8t3jpnanft450u2GeOLO553ohw9VgE8hZY%2BUpj2S%2FGfnvN6ui4eKqNICjqeKdjyO6Y4dGK8YPX8dxjXl353qswr8q487tWqrws9Xao4LaevPPHbu8rlE8DsC8WjpnarN9vHPl3i%2FwAXufrL7OrJiTYbmUdK2l6sNA6T33itIcX%2Bf9WmzLymUlJfWQlSWm60xr0k2Hpj5z1Ky35e1jqV2kqv6bxQbl9bzfuKdlcwLQjQ%2FA4jKLtT27Vt%2BXifpy%2BmtU4rs%2FcI02crmMuHyoy1Npra35x9mcbWW2ELQlx2wG6ElxFzy6wjJOLSVk8YcN09iSfl0repMzI1GnuLT7oz0pTqCT2Bba7EctvNHz1woqoy%2BD8dOlc2llOHVS6XA8u3WmWSUXJ7QASkcxzj6AcQM%2BuV4TJ%2BnvjWZqSoNlX5rCWgPkvHgMbwq54PjGH7yo3M1WmU5Z8k0Zcs86Yn1Ord7S1ru9rNpOeVMdufkjvOAHIpEKJ2iqo6T1ooqKido%2ByPPzxowhCAQhCARMNPbEsQIUeRgJxYkj1Q0agDblADlFQEbnugJG9Kf54mWUnkIdUcv%2FYiU6Tf83dAFlRQBsPR2xMFXUCknfkYplJvfySD1YmRc2udrQFQrUdtIgkE%2B9EUyNr3iKTba5gIk2SooAvEt%2BqlXvj2RMmwvtzMXjBmF6ljfGNCwZR1MInq7UGafLrfXpbQtxWkKUewDnASU%2FDuI6zSqjWaVh6fnKdRmfGKhNsS6ltSre3WWoCw5i%2FriRWF8QO4XcxszRJxzD7M14k7U0MlUu29YHQpY2B3HPvjtjCVPxdwiU%2BRyAlqth7EuLM0KxNTlO8aQ43S6fItS5amHZsW1OJWELsgDknzxZMN4%2Fls2cG1Dg%2FptQwXSZnE1LD1Cq2HJKZappdZe6d6SmZd5IcDi0NlSXBqB%2BCA4riIPfGeZz5UV7JnMGawBiOZk5uaYlJadRMyhJadZeSSkgHdJFiCkgEERgujzwFFzlGP1g2bX6IyFwWEY7WvtSzAYXAR6aeKf4yV1Vx1MukFR6EXWo9gF9rxWqqaT4w27RXnlSzrYUUPgBxpV7FJtse%2B47ICuMPzhpqqj4xJgpaD%2FixfT05bJ8oJ5kRbFr6kTLPu%2Bu%2FX%2Fm%2F9iKaoAHLIF1EhIsAeyL3M4bnpemqqXjUk8ltCHHWWn0qdbQo2Cinuvz7u2LImJkkoUVoJSSCkkG2x5iAlcQTFIpI7IutPFFBdcrQm1oSkaG5YgKUSedzsABFCoMyTU66imzDkxKXBZccTpWUnsUOwjkYD0TmHpmQkBPGcknglQQ82y%2BFLZUeQUPPv6otS4j9rcgTeAggOLWlvylKslN%2FkEXWs4cnaNLom3ZmTmWlOdEtUs%2BHOictfQoDkbfBFqiGvyv2XPz25QEIRcqSnDam1%2Bzb0%2Bha%2Bq34uhJCNvKVc7i%2FYI8c2wqVmHJfYlBtcciOwj0iApA32MX1qr4cQ0htWEEOKSLLWZ5YKj38tosMTQGQCs4ZAt7SWz5zUF%2FRioir4SeuxM4PVLodskzDE6pa2f2QSRZXojHgFKOlCSpR5AcyYvGIMOihiXel6pLVGWf6heYCglp8JSVsqCgCFJ1eg2NoCjWKQ5SnmlNupmJObSXJSZR5LqPzKHIg7gx4OUXOkVVmVZcplWZVM0yZN3EJPXZX2Ot9yh3ciNjFKrUl6lPNguomJaYT0krNN%2BQ%2BjvHcRyIO4MBuThPQpWPKmUHf2KV%2FGjY2W%2BJEYZyVwVjXDbEqjEOHMdVizzrIeSUuS5QEONL6ihoWrSq1we3aNb8KZCcZ1hSgbCmXNu7VG08mkU3GmU%2BFcDVVp6SpEliKriu1lqWU%2B5TA%2ByZiVmENo6y0BTSkLvsNQgLijiVzUbSkLnaSs2sSaUzc%2FJE6uJjM9ZuXaOfMaUzb8kZc%2FkHkGxZLnEsUk73Vh2YAHyRRTkfkCtF%2FroJJA12Bdocwn80Bi31yOaAsULoIsCLGjsnnz7IJ4l80E31HDxva%2F6Ssjl8EZWcjMiFFIRxVURJUbDXR3x%2BaKKckMiVBSjxZYbCUqKDemPg3HPsgMaTxK5lC%2FuWG035%2FpM1EWOJDMAHS4mgJCUhSQaQ2U7dloyL6huRqtRRxZ4T0AeUqnP7H1RBzIbJZpKek4s8FJJF7mTmN%2FkgMbVxI5i2s5KYYVsRf2HbvYxSPEXjlYCVUrCygOw0Voxk68islkoStzizwOEr8kqlJgX%2BSIDIbJYkaeLPA242Pikxa%2FqgMYc4hcaL3NDwqdrb0Rk%2Fmjzqz%2BxWWy0cNYS3IP9Ymdu%2BMyHD%2Fk4OhJ4sMEHpvI%2FQsx1vRtFZvh5ydmtmOKzBIIFr%2BLv21fFgLZkxi5OOM56BUanTqdI1CTaMqyZGSEuh1orK7L07EpKja45GHHIonEuEkk7CRnLfhxGXZVYPw3ldm7L0uiYvpGOpKuSLcmavTCUopk0p0rS042sXutLJIWO8gxhfHA4VYxwwjsTS5g%2BuYPzQHNaNVwL9v5xHbUqp5UtLJaaKFdE3fbkdA29HzxxOlJLiE2vdYFvhjuOQPRJbmFquAhIU25cbBI2i9n8Z6GG8TlZxLMcDexcvUBXsVtL9jKakOPIaSVqeOwDaQOaiTsO%2B0d25cMUWt0WVrkvKFuVCSiSYeRYto2upSDycJuCe6Pn0Ku7I4cqTlPUQ4VM%2BKt72EyVgJI7jeOjcGZlmiSrVGM0643JNJaUok2ISBc%2Bu%2FrjLaWEWlcTHea9leZs4q735Ml4npDDScPTjs88qWQUnR0TKVanALpPoCgk%2Bi8fNeapNExHU6zibF%2BI0UakUl1hiZflZVcy7OF3ZKGm026xCVEKVYbAGOreKzNianaPIUyiybk8tJbccl2klxxSFKuogDe%2Bm8c1z%2BA69henTRrDS5Gi4uqKNKp9von1MtKLrSgyeuQ3qKVLAtdVo61NnZxZ02OeeeuIaXvtcTVaz6HmzPqcg%2FwySOFMrqjWa7hXDdcfm6w%2FVKYmXm5BTqkpaCrE2ZUV7H7oWMYBwy5iYTwTjgS2ZVBYruC6ogytWp7qblKVEaX2zzStBOrY7i4jK8G1RjLh%2FF2Esfy9blsM4ql2pNNfkJZUzLtgOXbU6yNnmnB1VoBC0kAp3EYtgbJPDuYuZCMJ4SzSp1PVVp5yUpK5mQmND6tJU2hRKQUhZSUpvvcgGNa3u0xZ7imn9Gnbn617teqKK5mqrjqnXly5ZejiiF84k8p6Dk5mA41gyseP4YxDKIrGGqmhQUosL3DSyPK0nqknssecWLB2IpfEMt0CilidSkXSTsbdojXScU1Uy8r7JpWtdLW4y3LzCioMpBUlTVjyAN9u8RVwW4DLF9hzrNOFOoeb%2BYiMFpNMVZ0%2FwBd9tWdFVVOVev%2BsuzJuCroDVDqC1KSFuSi2gOZNyO34I1h0agjRfuVGauV1qo4enG5qZ6KaaZUrTbZQA2t541xMVDUAi50kbnzwrmJjNNlTMTMSwCpTLa6nWG9f22ZdTF3zYYwxI4ylzgakopEm3SKalaGlqJXMCWQHnSVEm613URy32EYlUXimrVA35zKz8sXPFTqnqvqWbqDLKfU2BGpLZiMoX%2FDiOicYdaPRr26yBpO3bcR6a0guFS1LKlK3JVuTDDTYW4yk9iQYq1VO3KDIxCfQQDFlfTvGR1RuySbRYXU84oPIRaJbAm9oqEWiUi0BAc4niQc4ngJoHzQhAE6498ix4w4QANhfePBFypYIc0X3WCBAd4ZV%2BDhwrjrKbCuZlczqdoQxHTGqgthynILcsVkgILhWAeXOMM4g%2BALEmS2FBmFhnF0pjTDiHWWZx2XZ6GYlOmWENOlFylxorUlJUk7E8o6%2Fp1LyiqfAvgCk551hymYOmqFS0zE0h5TKw9rKmQFJBIuoWtbeNQ5o5%2BZItZKyHCnww1Odrc9W3JejUx90r6CT6SZS4FF50DWsuWATbSB3AQFloXg2sG0KkUpvOXPWTwzX6wlPQ09DTYCXDa7SVOKHSKBUAbdptGvMV8BGIsG8QmD8mcRYnZFEx04%2BikYkl5Q9boUKU604wo3Q6myTa9iFXB2MdQZq5x5bOytDy%2B49sjnaJWZyX6eVqDCDUZBx0KDbrkvMS56VhZUlKltnybp57GK2I8n5vBHEnkDiqm5m4kxDhao1mak5SmV%2BoGbXITBkVuNusOkBSkLa6pCusClO5uYDhHiK4amchs4ZfK%2BVxV7PS86zIvszypfoVp8YVp0qRcgFJ3vfcGNg8SXATVMmKvg2gYCxHOY8qeL3ZthuQYpxamEOMISslABIWkpUb8rWjMePuj1iocVNERJUqbeNSkaEiRLbSiJhSXileggWJSeY7I3B4R7HeJsucQZT4twRiF6j4gpcxVn5SbYSla0JUhppXVUCCkgkG4gObMfcAFcy54cJrOjFeLfY%2FEMl0C5jDTkpq6NLrwbCC8Dsux1Wtba0cfvt2MfVTMPGOI8f%2BDUlsd4wqBqNarEpJPTk0tsI6ZfsipIUUp2GyQNo%2BWM35cB4VRKL9sVHIpwCIpUREIQE5VqEEbbxAcoinmYC84bH6aSZHMzUv8A75EdXeE%2B24pZ0fc4fpIPwS6fnjlTCgvXqYg8lT8on1vojqrwnp%2F%2Bamqo7qNTU%2F8AhkQHHznOIEgiIObKiB5QEYik2inc98LnvgK%2FSRKV3ilc98TwE1xE6Iog3MVm%2BUBfMK0NzEmIqZQW3gyqpTrEmHFC4QXXAgKPmGq8dyTPgrcSSbokpjO7CjU2o6UtOsOoK%2FQDufgjjPKxAXj7DLdudakP%2FMIj6m8Y2X%2FDVjDHFCqOe%2BcFRwXUadKu%2BxrEm90a5ljp9Sl3AJFlpsCIDg7GfBzm9gnNyj5OTdEZmqriNSlUWelXNcnPMpPuriXD5PRjdaVAEAjbcRutPgypqZU7h%2BS4gcHOYval1ProhQokWF91A6wnvVpsBvGa484mJ7NfiKy2HDFhabx1OZdonpl1Do6EVKWdaQzMoBVulPRhJC7X12PKLxL4i4Rc9s7ErmZPGmU%2BeLcz4qXUqVJTwnWwElvV1mXV2ASQdOtO3bAcwZOcD%2BYGauYmM8r6rW6bhGvYGS2Kg1UG1utrcWvSgIU3e6SLKCuRSoRr%2FKHIaq5r5yy%2BTLVbkKTPvOzjSp10KcYT4sFFRAG6gdO0fQjhYwdjLAHFlnBhzMPGS8V1p6iUedYrbqA25UJBThDC3EDZDiRdCk9hT3ERy7wkys2eOOTQuUdDstO1tUykpN2QEODr91yRz80Bg7PBxmFO8QNU4fqDPU2qVCj6XpyqtlSJNiWKEr6VdxqGywNNrk3EbEzN8HJiLCuB6pjLLvM2i44doDS3apTJVstzCAganOj3IUpKQVaDZVgbRkGaVVz0b41seYf4fK1OSVbrxl5ac8XbbW2phplo3dUsHo0pJve43jMX6zl9wKZS4qwbPY3axRmjj5Lj88hh33Fh5bam9avuQAtW53UYD5zuN9Gu0eiW7IjPKK5hR0gJPkpHZ5oix5EBllM%2FrWPOTHlwtNTUlmBSpqRUlM0zMB1gqTqSFpBULjtG2%2Fmj1UwH2LHmJi1U9T7WKpSYllWdZKlpP7hX5oiYiYykzmmc4dyYPxVSc06X7K0GXZYmlJCJmjtC62lEDWps8nWybkbahexEXhS30yLklVFuqEo34u2heslLd76Agm4SD2DbeOEsH43xfgapS1awjiCbpk7LKS4260QbKt2hQIPduI3nLccnEE8y2KrM4Tq0y0OpNTtAaU8P3SSI37O9zluavx%2FCJadpdqZ46c%2FX65hvqTwBP1xzpaRTJmYfUblthrQlIuOtf3oHnMdXcJmTGF6Wh%2FMlNQkqnUA89It%2BLudK3JuIOl1sK5Eg7G3o7I4yyAoXE7xu4hXI4oxvN0TL6RcSKw%2FSZZMiy6Ofi6NG61keeyRuewR9ScBYDwplnhOnYJwTSGabR6Y10TDDY%2BEqUealKNyVHckkxivNdNrERNWc5%2BjbPYtdaa7POZpy4uXjnZHTLIIQhGs2iEIQCEIQCEIQHwG46QPrm8yzyviOc%2FJHPM8mzUsLWuwhXyx0Jx0q%2FwDmazLG%2B%2BJJu9vTaOep03alVdol08u%2B5gM8w%2F8A1O5f9TRG4Mns6JbLWnTuHK%2FhRqt0aerdMrrf6PXJmTn5RRS0%2B44jdbIC%2BujsAuN41BQ9mVftURtnJvBOVWMhURmVjxeHn256WlpNvxlllAlloWp2aUXDdYQpCEaE79cGAyDH%2FDnnpjDGdXrkth6nYnRiioP1L2bpE60KY%2BqYWXC4Fkjo2xq99awG8XvPzN6Rcp09lph9dNqtaq8jSJbH%2BJ5Na1y1SmqejQzKyqSdAbaASFOJHWUDbnGUIyK4SpaWNOleJp2Wk373lkVVpDar87pSrSb9vfGvM08usgcK4WnZnLbNdNeqMmuSEsyibYWmb6Va0vthpHXQWkpSrWdjqsIDNMCTLEpwH49dcJs1iltYHb9ulhb12jQ7mMpXplp6F7nblG9cFsPzfAXj%2BWlUgvLxShCATYX6aXO%2FwAxzqcI11Ti1dCzzJ%2B2CA6k4E8RSlVx3jqTbbdQ57VOlBPKweI9e8cirFlEW5FQ%2BUx1TwF0Sq07MfGrj7CEMKwno1XF9fjFx8HOOVnVKW84tRuVOLJP7owBHOO4cgwr60d3QLq8Urv8AEdjh5HOO38g9Q4RXVBVyqVr1j3dV0R8190%2BI7m3fPwsfcrdTC%2BKqv%2BWXJ2WVNw83lFUK2nDck7WjOybSas6tZflWQyoKaaAOkJXc6iQTHmm5xyRk5qYlyUqDS7EdgIP5o9uV0nUncocRzjUzTBSJGakZd9tzV427MOS5U2pmwsEp31lR7RaPM1Jys%2B6ZOeWtMu4lQc0c7aDt67R9Ho1OZOti3ExhDC%2BCc6cRYbwdTBIUiVap7rEv0qndPSyLDq%2Burc3WtR817RqJznGa5m42r%2BZeMqjjfEbMo1P1AMIW3KIKGkIaZQy2ACSfIbTc33NzGELO8XQDeJgLRT1GJguA9LbSVDeK6GUDui39MpOwMV2Zk8lQHs6FuHQtxKFAi8R1CAzXJKh0PEWbuD6JX6a3UJCcqzaJmVcUUofbAUooUU72NuyNvrnksPuvNNhDaCtIQkWCUbp0gdgANo5%2Bwtimp4LxLTMX0QseP0aZRNy%2FTt62ytPYpPaN436ltE4XFuJ0%2BMNqeUlJ5FaSogea5gMC4n8NYXwnnViCh4PojdJpTMpS3GZRpalobLkgw4sgqJPWUoqO%2FMmNNuRm%2BZGNsS5k4sncb4qXKmpVNqXQ4JZnoWkoYZSwhKU72AS2O3c3MYMtV1EQAAHa8VEtpPOKW4h0hT2wHrSy35orssN35Rb0TSo9TE0e2A9aJZvVfbfnAyrYSQLWiRD1rn7rlAu2FrwGdZD0qj1XOnBlOrNKYqMo7U0l%2BVmAVNPpSlStCki1wSkbXjaM3UnUGamm0pQ5ZxWlGwFwbpA7BYkeiNC4VxZWMD4np2L8PKZTU6U8H5YvI1o12Kd09uyjG%2BZRiVVNpdm02lglTiwkE7dGTbvte0BhHFdh%2FD2F8%2FMVUXCtEl6RS2%2FEXZeRl79Ex0kiw4oJuSbFaln4Y02rmYzLM3G2JMysW1HH%2BLnZdyrVnonJgy7HQtAIaQ0hKEdgCEJHwRhJ5wE1h3RVbQk84ogwLpRyMB7mm2zsY9Al2RvtFrRMKB3MexmY1DcwHqTLt7299BUu3t%2BxiRK%2BW%2FKCl89%2BcBsfh0k6ZM53YXbqdHkqrLoVMvrk51rpJd5TUs6tAcRcakhSUm3baM6XPzD7bs4pSelmUFxRGybqTYgdw3It3Ro%2FCeL6zgXFNPxdh1baalTVqVL9K3rQdaChSVJ7QUqUPhjfS6ZKJmpiW6G8uhp4hu5IBSyopHeQCB6oDAuKukUOg5941pOG6NLUmmsTjJYkpZBQ0yFSrC1BKSTYalKPPtjTY5xl%2BYuM8S5hYqqGNcXTDb9WrCkTEy42yGkEhtKAEoGyQEoSPgvGIQFZJB2MVUoQRuRHl1d0C4obXgLghlBGxEVkMJEWxqYWDa5j3NvEgQHpDKIlWyjsiAdHfEq3RAbG4dZCmT2c%2BHJeqUyUqEsROOLlptrpWXFIlXlo1I98ApKTbvEZr0jjqumdUFKdSFqI5E2B5RpbB2Mq7gnFVOxVhh1tuqU9xRllONBxBK0lCkqSdiClahbzxuuYlFsOrYb6qdgE9g25DzdkB0BkngjAuJ%2BH3OafrmBaJUajT0yE5K1B6X1TTDqwUKIdvqSOoNuV7xtDg2QE8NdJaJsDL1InzXnFj80cpYtxhmzgvJNyrYXxfT6RhTFVabw7N0iSkkpmZhDLHTJcfeIJV1tVrG8dTcFanl8NVNWtzreLVLSr0za7fLePmHumU7q62E%2F5lP3a3bwmr4UeT8YcEKOp9xXe86f4ao6P4FEA5v1ZR5jDr%2Bn8Ii8c4oHuq%2F8ALO%2FxzHSHArb6r9V63%2FN2Y2%2F0rcd%2FTeP2Bbz5I9cNXD4%2FtVMeVdM2KbhOs8XlW9t2FZDEUrTcCMPMSU%2BpxLBmCwdK1dGQo6dW1jGjql0kxNPOvuFTjilalHcn1xtzOROMJ7jBrTWC6nQpSaYwQw7NGrtrVLuSiJcBxuyet0h1J0kdsalmn2ZqemnpUWl1vLU1z8m%2Fn3t3X7I2tDfmO7fyU%2BphvkfrqvO8vEVhPDUjgPLPG1NoypauYqRXl1qa6VSkzZl5hlLCtJ2RpQpSdudo53f2jc%2BemOKvWjScvFyjDFFwEJuUpimwouumbWl51bzh2JKgAkACwB5xpZ82URHqWrkkJiuy2hXOPNe4iYLUnkYohdWZaXVzj2tyctbYRYETLqbWMelFRdTz3gLyqTlj1bHfuMU3ZNjQkC4095i1mqKNiU8j3wXUndwlGx88B7HmUNqHQbKUUp9ZtHV2ZtJoOGcaz%2BGML0WVpFJpiWGZeSllrW22ehQVqusklSlEqJvzPZHIPjrhuF7G6SFDstHSisV1fMNmVx1XJSXl6nW2kuzKZZCkNK6OzSVpSbkakoBO%2FOAtnErhvC9LwxlniWkUVMrWMUUCfnK4%2BlaiJyZaqC223iDslXR9UhNhsI552HZG2s5MbYkxA9TMJ1BiXTSsEInaPSnG2lJcW05MqmFl1RJ1K1LsLWsABGoyqAgesbR6GZdsi6iI8usdkOlUORgL1LyDKxdR37LR600uVT1k6huL2iwonXW0%2BUY9CarMBIAWPhEBd1UyX0qSkKsdxvyihMSLTbeuytXpjwezEx90n1RI5UnXOaoD0y0u0mbZSCq6n207K33UBtHVua8vRqRmBWqJh6iydJpVOmjLSklJ6gyylKU6tIUSd1alE33JMcjtzWlesndJCvVvHQgxHiDHxRjDEbDTNSrH6Imgy3oRqvp1JT2XCQbd5MB5uKDDeHaYxlpiaj0JFOnMX4PVVKuULUpE3OJnphrxmxJ0qUhCbgbbco59125RtbO7GtbxdVKVSZ1hlul4MkV4boqm2lIKpNt5x3U7qJ1OFbqio7DkLbRqXtvBdOCVHePWyw0odaPFqPZFRLpA3MFF0ZkpVXefQY9aKZKKFwlVvTFkROOIPVO0etuqOgAAC3pgLkaZKkWsoHzERRmJKWaHV1ee5jzmrOAbBJPnjzzFSU6N7eexgLnhiUZm8S0aReSXGZqpSsu4gGxUhbqUqF%2By4Jjp%2FFdNkKPjarUejSDFOpdJqTsvT5OXuW5dlt06U3USTyuSeZvHJchVJqmz8rUpJQRMSb7cyyoi%2BlxCgpJt27gR1FTavUMZuS%2BK67JIk52uO%2BOTrLdwhDjjh1aQdwDzt2XgmGBcTGGsPUOp4JqmH6YJJeJcItVyp2cKxMTrk5Mocf38kqShu6RsNO3ONKpVrRvGyc6sYVnFlfZYqstLMS%2BGJI4bpSGGlIHiTEw6pKlkk6nCpxVzy5DsjWCVkEjsvAzV0toPNUelphkjdUeIuKEA84O2CF6Zk5UiyiTeK6adLe%2BCj3bxZmp51A5x6m6u6keTeAuDlOl7jZXwmPM7IsMpIKOovye%2B8eN6qzCjsQIoO1B9wW6QwTE5MhwdT5KexZh%2BmVBsuyk5VpOWmGwqxW0t5CVpuNxdJIvHRGJqbIUfENWo9IlEychTp%2Bak5SWQoqDDDb6whsE7mybC53McxUKrzlKq9OrFP0mckJtmblwpOoF1tYWi47RqA2jpA1maxWTiufp7cjNVwqnpiWbJ0NOuLJWEg7garmx5XghtbhjygyuzjzAqlGzSwm3W5aVwzOOSqlTLrSpVbR1pUjQQL3UQb35xkvARIU6l4ozFplOZU2iWqtMCAo3IbCXha%2Fp3%2BCNXYfzHzWycwhiPNHK2Rw01LUSRbk6zN1NtT80vx58MBLDepI0pIQb78zGe%2BDoqk3Warj6pTigqam5yluurAsCqz0eC90Sie41cx36P%2FwAlDqYR8oiP61NWcUQIz6xpcjeot2t3dCi3yRbsg7HOvAeo7e2CW%2FKY9%2FE6B9XjG1h%2FdRH%2B4bjxZAf8duA%2F%2B35f%2BVG%2Fbf8AxXP%2FACP%2BDHY%2FK4j%2BKPW6U43KNT6%2FNZU0arypmJObxbMsvoCikuoMo0Cg%2BY7jv3Mc75iGlMYyq9PoOGZLD1Mk599ErSpNbipeV6wSoo6QlQ1FOo%2BcnaN3eEIqlUpMplpO0RxLdRRiWa8VUpN0h1TDKUkjuBIv5o0bmRT8SUzGM%2FTMXO0d6vMPLE%2B%2FSAsSjqtZ0qQFEkXHONP3O5mMDoz79X3pVxGc7xX5%2FwAIeeaw5h7EeS%2BZs9W6V4zP4SpUnU6LNJcUhUk89PsNPGw2UlaOqQfgjmJ4aeUb9xpjOr4Oy1qeGqSxLuNY%2BbNPqy3UkuIYlX2X2g0RsCVjrE322jQEw5ePdNRBO8VUtgx5kuWiqmY0mCj2tMI7or9EjujyszUexLoI3gJC0mKDiGwY9K1CxtFvfc3IgJro7xHSmEZekSuQmC5iWo8jL1GqVGsvTk%2Bhs%2BMTSGphCG21qvuhA3AtHMBc3jdGVmMKtXsJnA88lgyGHFrm6ctDZS6lUy4C8hauSk9QEC1xv3wGwsS0yiVfh3zFnqpSZaZqOH5qgv0ieWCHpMzE4pt9KCDbStNrg38kGOWnhoc0xvnM7FteomA3sI0XoxTMYhD9bStnUu8hMBUv0a79QanDq77RoR5d1XAgJ06T5Rj0tsoIuCDFuUFFNwYqSswpJsowF4aaRbcROWEdwijLTKSN49XTJte0BSWwjtEeGebQ2lS%2BiCklQJSTYGPep1J5xbag5dJRAUpOYDQ06OfICOnJF6TkskMt5OWo9OYcmJSqTL843LJTNzCvH1DS%2B6N3AnT1QfJG0croWRG6cucUYjxLhpFAqzxmJCgJWmlKU2AWw87reTqHlAqAPmgNiYpkqXWOGTGFVn6VKvT9AxJQkU6dUj3eXbf8YS82Fc9CwASk3FxeOY3yOk25RuPMzF2IKJgZGAKa4luiVyYTVasjogVvzMstbcuek5hKQs9UbX37Y0sVk84CI3XvHuYYbUQSByi3FRAvFeWmTqteAuqJZrzRBUsgdkUm3T3xW6UQEjjSPKt5UeOYSwhCkW8qPW4uLVMulS1eaArNO25R1NKrlWMu8vJOUkpFlDuFmJx1cvLpbcffU%2B%2BlTjyxu4rsueQsI5LbdKV3J2jeWV%2BI8RV7CLdNrSw%2FK0Eol6O6poJcbl1Fwra1Dy0ajcX5G9jvAZvmjJ06b4d6tMvUyVenZLGNJbYnlNDxhhpyUmdbKXOYbUUglPK4vHMayDG4M4MTYilsPSWCWZlxqhzbbVXnGOiGl6oNqcbbd6TmSGllITyFztvGl%2BlgPQgI7YrNtIVHi16RvFVh7fnAewS6O6J0y6RuBErbgIiPSi4EAW0kA%2BePG8E3j0TDyUpFjFsdmesfNAV9RG0dX1Zpr2l4GZkpCXZU3g%2BkzDvQspQHXClwKcXYddZ5FRuTYd0cipmtJ1GOisrq7iyqYXZZxE%2Bt6XpKGJOndM0AtEnpKm0agLqQLq035bwG28gW5eYzZweHJGSnWJuqssPy85LImG06tSdXRrBBtqIvbti8ZG0%2BTp3GjjmSp9PlpFluj1MpYlmg22hPSNWSlA2AveMTyqw%2FiWu4uVh7CON5rBtTfW5OsVeXlUvuJQ2y450ICvJ1L0HULEWi1cB1brOJ89qriKuTkxUJ2awzOLmpp9epaip1rdR7STHlNNYjuJb582XRw35VQzXj3UlWebSku6lLw%2FKKKLeQnpXAN%2B2%2B581o5t7d46Q47zqzzZB97h2TT%2FtXT%2BeOclDfbsja0S%2BZbtP8P4y173x29XnQeSPE5jzMrPyR9BMyplpPCpMrXdTbmBUtKtz0uS7SD%2BUx8%2BZsKElMkfqDn5I%2BgmcoZleFmoyyFJSlGASBq5f1OyAPTfl548n7oMbq%2BXGI50%2Buh0MN4rvbT5I%2FFwrn60zK5iT0mz5MvIUxsE8yBJtAE9%2BwEanlWnpaWAd0ptftjYOekumaxi2tdSmGn3MNUAoBRfWfY9okqPZeNbla2pINPvatNySqPol1z94oz70epy7b4yfO9zBl9i7Mti29yrlEJRpgSKm3JxlK9bqrFW1io2jGH31lxW8SdMv7uNnNiZZR3JemyqmHppgq30qS6Ck7%2FNErb6WZl50vMWcUCNLoJEYp0p7x6hEsBmDk%2B0TvMNfHEedydZJsH2vjiMXhAZGX0K%2FtjZ%2FdCKjUjMuzcvMJCAhskqJPIW5xjzC7G0ZZTHEdHdQv1T%2BSAz3OeQW9RsuJRroUqbwTTXEgGwIL0wTfvNzcmNX%2BLKQ6UrcbT%2B6jZ%2Ba0x4zL5dPIA6P2g0xCSDe%2Bl6ZB%2BURqmrr90ig9c6y34kUsvtqcJA8sbb7x668GJuQ6GXm5dTgUlVisC4HdGJdJ54dJAZS4%2Bn2NTLNrQp3o7W1Dn6Y88qtDcohsqSnT%2ByEY7C%2F7IeqLjIXH0fdpP7oRRVMIHvh6xFiOk8xEOrfaAvoUXtmQVq7kneL5hinzckJ5c630YdKdO972veMVprgQtC79bVGcomGw35flJ%2BWAz3MOiGlcOOX8q0UnpMT1mZdUNivWwxpuO0gC1%2B60aelJck63nUJHnVG3MbVV6p8PGCUzDSkqksV1mUbVe%2BtCZWXOo%2BfrW%2BCNHzjihcAwGQNMNCrNzCXkBoShQo6h5erlFOoMpbq7Ey282psCxKVjleMWW8v7uKZWo8yYDLK0ozRBlgF6VBWrUIkcV%2B1%2BMIxW574jcd8BkC1WVcW%2BNFJbijyt64spUAOZiCXBfnAXkyszNJ6Nhq5PaCIyHxQLp0nKO9VaGxqF%2BRiyUGY%2FRHR%2FdJi9zbo6MK120gwGzKjRE0fhUmi5Ls%2BNTOOJJ4PgddTSpR4BBPaAUkgdmoxqRhCe8RsqZxNNVXhvrtIfQhLdIxZRw0u9y6pyXmir0FIHyxpSZnHdR0qIEI4hkVPQ23TVB5aG1JfcNirexOxjz0ZaZJx%2FplDdR07g9u0Y7404eZiBcJgMlMyn2QL1xoUzpO%2FbeKvsk2OZ%2BWMS1rvEekgMmdqrPYRFA1HVyVGPkqHIxMl1Y7YC%2FMSE7UJlhTLKlpSsLUQeQj2PSMxLPNraRrS2SFIvbV%2F7vFpln6itKEycx0RBteKq3Ksh3pZipeMICgCQrdQIgOvsRYdwnK8FtHmMIyqqpXsYKdn551pC1LbmEOltUm0gcy2hF1mx535CN9cTqkp4WU9EvUlTVD39Ia%2FPHMXBRX5JvH8jTcV41XQMLUWoS2Inppx8tolFNa%2BkShw7N9Oi7SxbrhVudo6c4onGHuGSbdlGujl3JmlKYR9y0p0KQPgTYR840vos5xLDKqIyytYjLlmZqpmZ7I6Xauc1Rd7amZzziJ80ccRDhPnziUg3gL35xNH0eXFScucTD0wWOVxEqLnmICNt4mhEpJvARiYWinE8BNYQtAm0AbwCJIniWx7oCGkQAtE2mGnzwAC43iA5xEiI91oBEyXCyFPBxaC2NYUhSkqSQeYUncW53G%2B0Sjl8kTNnQu8B3%2FiXK2ps1XIvHuFcfSmY2NsI0t5t6SVVWWp7ENPdbW700ktZstyXDy9OrdSUC9yDHgybyQnWM9adjDMHE9WoNSp%2BHXZeh0zEVXlXq646tK2TONhvqpYaDilJCrnVfsjirBeKatgPF9ExxhxxtqrYemkTcg64nWltSbjTY%2B9IKgRy3jIM2czMVZxYyXj3GCZVioKlmpNlEihTTUuy2mwS2b6he5J33vAWPHDVQlsZ1ySq%2BKzieclKjMSzlaMwXhPhDhSl5KjzSoAEDkOUY6sKubRXKW03QghOmyQEjYW7B3RSIPbAed6Mbrh9xc9F4yN%2Fu7xGN1z7U75kQGLyKJB4TCJ6aVLqDKlMKCNQU6CLJV3Ai%2B%2FYbRCZbkUMyxp8w66tyXC5lLjejontSgUJ%2B6Fgk38%2FmjyROiAuczJ0Vp0uy9TfdackkutXZstMzYXaWL7JB1dccxY9sW9SFqbUsIUUotqIGyb8rxEICzZCSo%2BYEx7JCsz1Ll5%2BQln7S9RYEvNsrQFJcQFBSb35EKAIIsYDwracbSCtCkkAKAIsSDyMXWqyWHZaZm00utzE5LhhpySWuWLanHDp1tuC%2FU03XYi4Nh3x5ahVqhV3Wn6nMqmHGWGpVta7XDTadLaNuwJAA7Y8vLnAe6TlqW%2FSag7MT62KiwWlSbJbu3MpJs4Cv3ik7EXG%2B4iWeapctPlEhNvzUiFIIcU10bhBA1jTfmDcDfew748pukDWkpB5EiwMNoD3VKRoctMT6ZCsPTjTbqRIOGX0dO0b6lOAm7agNO29yT3RbVN9QOBK9JNgoja%2FdEylAHnHqbq08ikvUVDwMk%2B%2BiZU0Ug2dSCkLB5g6SQewj4IDxyiJYzjDc8841LKdQl9xCNSkNk9ZQT2kC5t5oTjUuzNvNyj%2FAE7CXFBp0p060XOlVjuLixt2QdUp5xSidTi%2BwC8SgXGjkocxAetcvSVUNubaqDgqSZlbb0qtuySzYFDiVdpvqBSeVge3bxQ7bQgJYmiWJoCvT35eWnEPTbLjrKb3S2oJVe2xBPcbRXFSSKbMU5QcX4w8h26lDSCm%2B9ueo3teLfCAq679kepqcmfEDTC6pUsHunQgm4Qu1iR3XHP0CPFFVnkqA3rwpJvi%2BtL2smmC4PIjXyj20ufm6Xw8Veco0%2FOyE0cU0Vpx6WmFsrUVys2VpCkkHSRYH0RQ4R06sWYgGm96Tb0dYm%2FyR5pSrKlOHKuT6uuGsbUXbsNpObBH54DF043xggXRjaunfsqTp39cSqzAx4AFN45rtr2uqfcVv3bxicji5yny0gy3KNLNPnzNpJ5u31dU%2BbeKaMVu9G0wZZromqsaqEEcyf7X%2B1gNiyecGZcpLol%2FblPOJQSLvPFRJv2kjePQ7nXmYlpaE4zmWwoFBKFAEX7OUaucxS%2B43MIS01dypeyI298bdQfsRblE0ziyZmTPLcaZQJybam1AI2CkHyR3A2gNu4CzqxRSMeYdquNMaV6coElVGHKtLNKQ6t2VSeuhKFABRsdgYsk3m5mW2%2FMIl8wq2tnpF6ekcQTo1HRqBTsdNr%2BeNdTuJ3JyXq6FMNo9knWntubZSRy%2BWIT%2BKpieeqjimGE%2ByLbYOkeQUgC6fOe2Azt7OHNE3UMwKwpVuSnEbD4seObzxzmJSw3j6tKbbSCjrpt57dWMMexE4%2BJwKaQPGZVDNwPI08iPObRP7a5rxvxvo27%2BLJYtbaw3v6YDKV54ZwJbVrx5WylRCj7oB8Pkx76Lm9mjM1BhmYx3WlJ1W0mYA7DfbTGJvVtyeos8y7oBQGwggXuCoCKspWFN1ZpAbRbV5vuTAdT8H%2BIq9iPFTE9XqtNVJ5Nepkq25Mr1qQ2JeZXYHsF%2FyxfON5P%2FAAwwwbkj2KfUNuX6IIt%2Bf4YxTgjcEzV5N0hKSnGUinX91%2BgppWn0WHKMo43io46w0k3FqKsgd95hRgOdEKSl9BIuNabj90I7mZSFILTy21qsgJVbuA9fdHCwGp9pNrguoBHeNQjtptlOtLSLpsgWKb3BCdheMljx2k%2BZivXFZ0%2F13mRSjrS0vy7r7DbLb7c24Sm4Il3G1pQnuUoFQv5o6seyxw%2FPMmYZDqC8knpGzzQrfly5RyvhQMOOO0%2BYQNM0hTZWobb7fLyjrHLqpOvYOkpR8KTM0xHsfMJJvZbew37QU2IPnjYqp%2FSiWnTXlTMR53NnE5hLMXK%2BlNYmy1xLV2E1kpp1R8QQkv2bupqytJUnt8m1%2B2OP0DF89XHa1i84hnnWUhUzOTzjjzrLAOyrrvZsKNyBYR9cFvMvDo3UIUNXJSQRcdsWrE%2BB8FY5l5WWxXh6VnBJudIw4lAacbPaNSbXSrkpJukjmI2qLeujKKdTWqsbOqJqmP0vU%2BZM3iifxvUadlG1iiSoVLrAZl5mcWby65hSrtOOcwlCTpUVCMVpGIJvJLHctVqcpnEFfwzVQ%2BytTgFPW8wshC0qSLutKsFpItcRtbL7I%2Bt07iZpFITTZV2XwxilM7OFSQ3IuU1L5dWAV9XSGladBvy0xgOcuF5anZrY29jegdpLWJJ1mRcYsG%2FFysqaCAPehJCRbbqxsW1dcWlcTOe5yjycebHYWFFVFMat1nV58smosRF%2BpT1Srs22w3MVSdmJ99thvQ0lx5wuKCEkmydSjYdgibAMi6cP%2BM3t0z7qh6L2%2FNHsxPKuPpapsm2pb8wro0JTzueZjIpGk%2BxVLl5FAAEukJuOR7%2Fljm1TNc5y6lGVMZPFUm%2Bjp7%2F3XQmMW6AnTbtjLag2fE5jV5IaUkfmjG5cdI4Nv%2FZiqzU1TH6b1Af9IX%2BUxdcSoKK8tvuba%2FiCLbVrezVTHdML%2FjRfsatlvGc40oWKUsg%2Fg0xrzPGzcjLcFyqH30XbvZon5DFOqoHKLtlxZM4kHTYyzt9XLyDFtradDloqsxWppu2dosDibCMknwCkxYH02VaAtyhziWPWtuKCm99oCnAc4nDfmiYIEBJECbRMoWMTobv3wFOPTKPltdjEnQqvteIpQU7wHTOMONXEmNuHihcPU9gylykrQkU9DNVlplwuuCUJKCWyNIKr77xoZmtzSJluZRMutPNrDrbraylbbgN0rSexQIBB7xFh6QgxP0sB3dhnwn%2BLk4dlqbmVlPhzGFTk9OiouLDReWEgdKtpSFJQ4bdZSCLm%2B0agzs4xszc6cV0PE8zMow97WJlM7Q5amKITIzKVAh7Wd1r2ANxbTcWsY5yS8RyUfXE3Tq%2B6PrgO%2FaL4VPFLVIlmsVZOYfqtXlkm09LzRZQpZ5uBtSVFsq7QlVo5jz74kcb5%2FwCLxirFxl2PF2xLScjLAhiTYBJ6NF9zckkqO5PojT3TKt5RiTpCe2A6WneM%2BsT3DBIcMb%2BCqciQkW2GE1ZE0vp1oafLybtlOm5UbHeOa5pV184pdJEq16jfvgKbkU4qL5RJYwEIQiI5wE6U7RFKd4IO1omSbGAveEU6sRUlPfU5If7dEdS%2BE6N%2BK2uD7ik0xP8A4ZEcwYHTqxVQ099Wkh%2F4hEdN%2BEwPScWWJ0k%2Fa6fTPllkQHIbosuJCYndN1%2BiJNJJgIQicI80Ci0BJCBFoQEyRvFZJtFIc4nBtAX7CtdmcOV2m4hkm23H6XNszjaHb6FqbWFhKrb2JTYxufic4pqtxN4qpeKqrhKTw%2B9TKb7HFmVmlPoc91LhXqUAeZta0aAaWQIrIUbQGfZXZp4syjxxSswcETyJWr0l1S2i4jW08hSSlbLqdtTa0kpI9BG4EdYO%2BEjw5MzgxdNcMGFFY1CAPZkvpWdYSAFaijpDttvvba8cJ9MUw8YMB0HQ%2BL%2FNehZ5Tefzc5KzVeqKFSs9JvpIk5mSUAPFikboSnSkoI3SoX3uY3rO%2BEypUuibrWEeHih0fFNQaCZiquPtuKUvtKyhAW4PSRftjgkTCu%2BJhNEdsB05khxk17KHGGNseVHBVNxXWMbuNLm5ucmlsOsaVKUtCSkEFKtQuNraRGcYq8IPR8S0qrU%2BocMOAXnaxKuSz82%2FpdeOpBSFalN6iRe4N73A3ji3p790Ol8wgKr74eeLiUFCfepHYBtHpl7KTHhCrm8elhzRAZhT1aaWnzkx5cNSxm8byUslOouB0Aefolx6KdvS0fDHqy4lfHM1aJLnkp1039DLh%2FNAYvLAKbSo9oT%2BSM6ydwfLZhZpYQwPPOPNSVdrkhTZp1m2ttl6YQ2tSb7XAUbeeMOk5JyacUeqhllOpbhPVQPPGweGqtJnuJXK6Up%2FucijGNG8yn1Cca6x83cID7zYCwHhTLPClPwVgqjs0ykUxoNMMND1qUealE7lR3JjIIQgEIQgEIQgEIQgEIQgPgHx1WHE%2FmQBt%2FwinTf0KEc8zRJDQPINIAjoPjq%2F%2Bp%2FMne%2F%2FAAin%2Fg6wjnyY8lr9q3AZ%2FRPtKv2qI39wzqnQutJk8m0Y6Smo09bylIllFsBLumTu%2FwAg6TrOjrHou6NC0YpEmB1b2RfvjaWX7ufeCaS9inAFArDVJm1oqKpoUvp2FKZStKJhJUkgFKVLAUOwqgOrVTk80SPrDUK1G5KWJJQ%2FJGqeIJ2bOB6slfDa3gpDopgVOhmTT7H3fUQ9dr3X3f7Vv1ertvGuTxV59uISheY606hcaJZoX%2BSPTO1LiQzrw685M0yt4ipNRWyy9NStJTaY8VUVNtF1A1KQ2tSlBN7BRJgNiZcLaZ4GcfzLirBGKUrUrsTZcuL%2Boxo5OIqRrV%2BjE%2BUY3LgFbjnAZme0kXcaxEG0pHPUHZa49POOZjIzwUq0i%2F5R%2FtZgOw%2BB2qyE5jrGbEtMoWs4aSvSDvYPEE%2BjcRxu4Qpa1JGxWu3xjHT3AGzOMZo4tLss422vCawVKTblMJsPyxzG%2FwA3D%2FjnP45gJUc47e4fx%2F8AKG4Aq95XEPPs6jkcPoMdw5AqvwiPX95K4hT6kOR82906M8Pu8R4WPu1OrhNM1Wlf8suU8pdsi8Y%2F9u0v%2FwAuYkkGSp0I98bj%2BCYZWK05G4rT91X6X%2F5Yx7aDK%2BN1WVp7dTkJWcnCoSjU07pMwpI6yUAAkkXj6NZ6nLnW0pi4oW7JutISnpJBpSwlNhqufm5xiDosogd8b%2FXlJQXQw3PYqknlS6AxdE8kJsm%2FPa%2FbHnVk1hNyalEzDs4JebeSgzDDiXPc9YClJG17AkgdtouhoOEZXjOg0ik1R6Xoq3XJNtS0tOPJ0rcSHFBKlJ96SkAlO9jcXjFltnsgKRVEyFRKURMhMB62nCRFa%2FniahMSk1WadKT4eMs%2FNstPBkgLLalgK0321ab2vteN41rLPLU12eVQaRW5ekiZc8TZm5xtx9DWo6A4pIsVabXtteA0JMlWhdj70%2FkjqaSsES72oaFSqetyNuhFowsZW4LVa8rPhN9x0qdx29kZqX2Gkl5bjMtLMNnWtxXUbaCbXV%2B1A39EBz%2FiL%2BpaWdNryZPputW8YisEOKjpN%2FKbADsvKIm8cU5QalUJb91c3aPWSq4RuCDcR5XckcBFkPS2IpCfspBW1KzKumCCRqVZSQOqN7XgOdYlVzjMcXUakU2eXL0pCy2gK3WblVlkA%2Ba4AMYg4DflAUjtE7bljEpBJ5RMhuA9jbvniprv2iKmGZaUncR0qSqCHXJSYnWGphDSglamlOALCSdgqxNie2N7VLKvAIqU6un0qbZkHXXDKMuzAccZb1HQlSwAFKCbAkAAm8BoQG7zRv79I%2BUR1BMN6DMq%2B6aWf9mYxiQyswM0dUzTZh5SVAps%2BU8u%2FaMsqU1KyktMzM6%2BGJRppaXlncIbKdJPwAwHPWJb%2BKSDZRp1SDLnrBjEo6Lm8scEutyqJrED7ihJMhkrl3UhTOnqK8ne4ianZMYLmn2UNPqmEpdbVMhCFJV0AWOkCNQAK9GrSL7kCA5z0m14kPnjMcZ0ej06pzTdHQ6mT6dzxcvW19HrUE6gNgrTa9u28YgsG%2FKAkJAio27aKRF4ilJMB7W3iRFbV3mLhgKnU6q40oVOrMu9MU%2BYqDDc2yy4G3HWdYK0JUdkqUm4BtsSDG9Kvkngj2TmpqQkJqWlX33Fy8st%2FpFsMlaihsrsNRSkpBVYXIvaA55lk656X3%2F5Q3%2FGEdWzjKPZCpLI6vQzhFu2zCyIxCWyhwXLuofdlJhzo1BQT0pTuD3iMsqE8zLNOzk7MtS0klpbcw64kq6NC0lCjYbk2VAc9Y3cRMPSswerqkJXl%2FkhGHaDHTL%2BUWBHWJdE3ix1y8ugtpdkX0dI1bqEHR2iJ6NkRgGozLPi0%2BuaaKiVJDLrXSBBSXEoUtISVBJ5QHMNjEizaMtxzRpGmVqalqW0pEs2tQQCbkAE7E9sYksXMBBCt49KHrCPLpiNz3QHvS8T284iXLjnHvwFISVWxrQ6bVZdb8nMz7LcwyhehTjWoakBXvSRcX7L3jd01ltgHxyYbRRltsl1RZQHiShvUbJ1EbkCwvAaLoAvXJAH%2B%2Bm46PqTd6i8CNNl%2FkAjH0Zb4JYmGZlmSdJYdS4kKeIKgDyJHf3xkTqlOurccTdTjhVtyHm9HZ8EB7M3kn62PCqin%2Fnu4kHvAklbesn1x1ZwV6E8NFKsDdcnUFn8bVeOXM4Ej61vDJtbTj5QG3Z7HqvHUXBStauGqmpV7ySqiR6PGVn88fMPdKndXWwnvWtP3a3bwmPheb8YcEo8u%2Fe47%2FHVHSXAgAc3a4T73DzlvheR80c2o5p%2FbOfxzHSXAjc5u1sDl7XHifgdTHoNOY%2F9ft%2FNT64a2H%2FK6fO9WN29fGRjFy%2F2rLvVt2e4s7%2FBGk5ZsBhMbsxmk%2FXgZirAUCcvRcn9kywLDzb2jTtKlROOJacm5aUb1BJfmXAhtJJsLnzmNrQ7iwO6x%2FBR6oa98n9dUwnNRZ9k8SsW6iqwyD6AwCPymNOzDZ%2BGOnsSZVJrGJavP1HENKaVPTSX1yaZwaELCAB2X5An4Ytz2S1JbQXkv02dQLazLuhwovyvy2J2j1DWzc2RFxISElO5I3jcebuBcM4RmRT6GszJEvJOvOqZLZbfeY6R1kC51JQqwC%2Ffc4024CPNBZLqMNRiSyzyJhpX54ooqAxP2bxSjp9%2FJrAr9Bw5UqZTZljx%2BhU6Ymg%2BpKyubWyFPuN23S2VEaUq3FjfnAcxlBPOOocHy5cy%2FwAJP26y6eEJ%2BB1Vvki3O5OYYCTpYcvtYgA274zeiUd6QpNOoco2t7xK0vLJsLq1K2HcNzAaYzVCzUMQMDdCcRzKfU1Go3GyI6wqOSmEMRT1RrMxnThtrx2fcnHZbplnonidLib6dyLW22gjhywDMISJfNrB8w4qyUNdI4CpajZKb2sCTYbntgOTNAikvaNyZwZf0nA0%2FM0OXbSt%2BUcaS65p0nUplKlC3ZYkj4I0842e2AphUTBXdEoTaJtO0AuImuO%2BJEpjqabySwW%2BmVmaRJuS0s%2FKSqw3MhK3UvFlBdNxtpKyopG5CbX3gOXknn6DHT9EQldAoq7lSkyLQdPn1WHyRbXMl8NoQu7Q%2FB2jN6fRlsU6WpcsjX4m02gKULXVb5BAaQzUbW7OT8vfrMVuoMnzFK0i0av6DujoWtYCoFeqE1XWcdUZMvUpl2oJlumWro1um6wDp%2B6SYpsZR4enXES9PxJQFzT6wzLtKdUCt1WyRcpAAKiBc98Fs3PZaUOyIHaNs55YNoWC8SKodADi2ZFhrp1vNhDvjCmWlOoIBI0pcUsJI5pAJ3MaoWknsglS1WMTBYEQKIlKSIKKuu%2FbECkHmRE0ojXMNIukdYeXcjn2x1XWcg8HTjyZ2jSzsjIuS8q83LTqUrfQpTCC6StG2lTmtSRzCCkHeA5UaQVOpT3rSPlEddUSVJpdImFk6Zltpd73Nuk0%2FmMYu7kNTGiS3MtILfc0fgjZNKpa6bISUhLKUtUk22lCnCLrUk6rnu3v8EBzbmwjpKlMW97Pz6U%2BjxlUa36Mx0nO5Y4Vrky%2FOTWZVEJmJl%2BZDWpZCFOuKWpIOncAkj4IjL5G4PmJiXkpbGVDfmp11MvLN61Auuq8lAJAAJ88BzaWzaKJ2MbRztwbSsEYrmcP0ZxxxqTCUl1xIStZKUklQGwNyR6AI1h0Z5wENcNZiUixtCAipV4jFyw3JszddkWJhlLza3LKbUSArY2BI7L2jfM7k9g1LqHKUl1yVcZZWkPpAdSotJLgVpNvLKtP7G194DRGF%2F7I6WQeU40f4QjpCSI9hpB0K1Fxi583WMY4zlfQ5OZbnJVIaeZV0jSwgmyknba8ZM83LS0vLSkqlYQy2G7q5qsOe3nvAX%2BtuBfC7m%2BkoB0GipCu0XqDZ%2FNGeeDRU30eOEhd3lT1MOnuQEP2PxjGva1%2F9Lma7m%2F2%2BiJ9c8iNg%2BDSascazNtxPUxu%2Fms8bevePEe6Bx4JaR5aPv0urhPx8T5Gt%2BJ%2Fq59Y1R%2F1klXrZbjy8PABzzwFqUQPZxo8r3Ohyw9do9PFEf8A4%2FY065V%2BmCeYtb3JvaPNw8hK89cAINyFV5jl%2B1VF5qnglTn4D%2F8AWxWHyuJ8setvHwhylIGVYQrrnFSykdtwmX%2FmjVueaVJzgxKhQTdMyAbcr7mNm%2BELUBVMpk2BUcTrIF%2BdjLxrXPELczdxKpXlLnOcV9zyn9hWfnq%2B9KuIxlea%2FP8Ag1vmNLtuYClVKAKulfKbjcbt8o0G%2FLx1BXcFnENClaY7irDzDbLrrhKZs61hYR1TtYFJR2d5jFVZGUlSSEYgkH3NrIZnAVLJ7Nxa%2FwAMe2lpZtBhojtik4SFxu%2FF%2BVWFsPZfzWIEz06a01PhhiWDQMuuW6IlS1L5hwLCQE2sUk9ojSDgOvkYIVmHiDHq6ckc4tg1pN4mDqx2wFzExbtjzur1m8eTplxufK3LrBuMMvZ2pVKVqIrjNZDTMymZSJUyYlzqaLdtRc6QhQUDawIgNMuA32MbjyLUoUHECLixmGDa252tzi7v5O4URybd%2BPF9wzhqm4TkZySkJc%2FoxxC1OKVySkHa3pI9UBZc0VByiSiTf3STmuR730fnBjRXRk7R1dNYIw3i6nSzeIsZUyghhL2hDyHVuutOLG9kJISkKTsTz3i007ITKV6Y8X%2BqpS1OOdRKRLTRUo%2Bazf5IDmZSDaPOrYxvrMrLHAWF8LLn6LU11SZcd%2FQ05LE%2BKOs9Hc2CgF6wsEEEDlGh9%2B2A9LL1hYHsj1pmhp06heLQoqSfKiXrjfWYC8GY84jwzLilqvqjzXX%2BqH1xvHK%2FAeDcT5eNztSoziqqZ97VOh%2B6TLBASlro7bKCwVa78trdsBo%2FaN4ZKpaOHVBwpClCyL8z7sq%2FyCLqcqMFdHcSSl79qrRdqPQ6dh6Rcp1OkEDpVBZeJOpFjfSkcrXJgMczfK%2FYNpjUnSWNvT05JjShQRHTVYwpRcTU1DNZqTsoZBCnHOhkHnwlt1zql1aAQnrpISPOYscvkzgiZcRLylam5h5ZsltilTDij6ABcwGgCk6Yotq0rjeGZGX2CsL4BkH6Ul2Yq81NqmUVBt8GVmaetpPRp6IgKbdS4HNV%2BYIHMRpFbdt4D0ImSntip44e%2BLasqTEgWvvgLk9MqKdjHkJWrtEU7OKG146HwZgnAeIcuaOX8LNN1ZmZdXMVFDyrzbCmkBtlTfJJQoKVrG6r7wHPXRKMdAZRBt3ByVb6W22079h90j1fUrwcL6KaVd9lkReqXSGMPyRp9Nl0tslYcKrkqUAmyUnssLk%2BkwGJ51W9r1ObDmr3Fv8A3ixt6o0itoA2tHTlVw3hfEtLlRiWpT7K5UeLJEtTVvICSouAKWCBfdVu65EWyXyoywf6zFRrLpaSXXP0mdUQlIudr%2FLAc5utq03ii25Yxu%2FOXAeDcKYUoc1htIfmZ6YnFuToUQJmWPRKYHRn7WpAK0kdt%2FNGj3G1XOkWgPYmYsOcRMxfti3K6QQT0nfAep54q2vHmO94jZztjovCuAMCVbBtLemqA0ifZ6VL0yl1RVNBegp1pPVT0dlAEcwo37IDnAoPMx0jlxNqTQnZa4UlxiTSN720NxUTllgR4aPYhxSu4r2i%2BUyk0mjSIl6bJqRpNnVFRJPYPg2gNk8Oy1jNiSYWi%2BqRnHT6Uy6x%2BSNeeDtLQzXqaXEXWcMv9Ge73Vu%2FyRsnh5Sy7mlJr1rDzMjP2QkbEGWWDGufB8WbzimEpSLLww8pXo1tx5TTWM8DvH8rpYZ8ppZ1x2gDPgkEG9AkNu0dd2OdUdt46I48Bpz7Itzw%2FT97fsnY54HPeNvRT5lu%2FwDL%2BMtW9fH1edLMC8jMj%2FFLHyR33niVI4W56xT0juAW2U6hzUoS6QPSdUcBzJT4pMpWbJ6NRv8ABHe%2BfaXFcK0w2hGpx7CEnKtpt5Tji5VKR648xpzOWIXGPLV66G9cc97W2Xk%2FFwTxJU%2Bdp%2BZrVOm7eMSuH6GzMW%2FVESKEq%2BVMauqg%2FQfxfyxuTiQU2c05hcyAFoo9HRa%2FICUQPnjUlWDTssltsjyhH0Gw%2BJojyR6nNtZzrnzyx4pUrrRIRaLpLyraXmS%2BnU0Hm9Y706xceqK9RYpTclU1yzThdTUdMqu%2ByWB0nVPnuE%2FLGXNjWUAnkImi%2FwBSkaMxM1pEq050bbTJk9SvtaitGrV37arRESVESXTpeTooiXkpCv8AlehJKj%2BxJKtokY%2FCMglJGjqm6Wl9p3o1SazNDV5To6XSR5tm9vMYkp0nS1poRmWXVKfmnkzulWy2wtASEjsNiqAsaLhY%2FbCMrk0rTIzCW9XSKYWGiByVbaMZ6MdJ%2B6KvgBi8y8w6GyU6yAm4O4AFriA2tmlIPSdAyrbeDYLmX8k8NBv1VTk2Rfz2IjTtdJQ4m3beNy50zxfpWVCUMLbDWW9MauRbWoTEzcj1iNM1P3ZxF%2FPFBahvCLrISUmPGVTqVKAk31NBJ3DoTdJPmBj2yUlRlzVBE028pDrbpngn3xC3NJHwBN%2FQYCwRKQOyLzT5anPMUgPocLjs%2BtM4RyUwC3YJ7jur5IlelKaZGZcaaWHxVOjQb2HQaVEj07CLizxApvuIyCpSNIbNe8XbdBYfQmQOvYJLigUq7%2Brb1RLNydDEzUksIfS0iRQqWClbh8hoqv3jrL%2BSAtVLsZxtC%2BRMZbU5Z%2FoJJbeqwmkJc08gDcb%2FACRi0s0ph9LqOaFRehUp5XRpeWsguJIB2ueyA2ziinzUjwy4UcmFAImcwa%2BpkEbrQmSlU6ge6%2B3pjQ84TrO8b%2BxrOrmuF7LHWyevinEjvSb2JKJcW%2BT5Y0O8xrUTeA8Bv2xCLquWk0Up55QWZpMw2lG%2FV6PQoqv57hPyx66lIUdp2vpYD6TLFsyIvsAXAFBX7k7QGPwjIFyNF8YfQC6GxSm3miTymShBN%2F2JJV8kSM0%2BjF2nF8THRzFNfcfKVC4mE9Lpt%2BxulG3deAsUS8oyCRkaO8KGJlLyRMPuJnSki%2BgLSE6fPYnn5o8LjMiaQl1sOeOeNrR%2Bx6EIBH7q94CrQEKcmVgHkn88XZllU1XfFXFqCOgukd5vFjp63pd1TjRsTtFdFQf8eEwlZS4lIA828BtdFNfkuHzHTy2tLLmNaA224QbKUmUnCpIPK41pJ9IjSjlzG%2BETyp3hQxNNkkeMZh0xJb%2B5Uinugq%2BExpDxZffAeKJovTMlSPG5Bt1LwadlHFPlJ3LwDliPNsj5YScnSF%2BwKn0OXdmFpn7HmgLTa3wEwFliBF%2BUXeXkqYabLTL%2FAEpeNQLLqU8izpSdvPfV64TknTG5aruS3S6mJ1LcqVH%2B0kuc%2FP1UwFniW5jIZ2Ro%2FT1ZEqh4Jbbb8U1KBsvUjXq%2BAqjwVOVlG3W%2FEQsI6Bgr1m56QoBX8Gq9vNATSal9BdJ5k3t2xIwqYKzckp1Xt%2BaKsm24uXCAN0kxVQoSrqFhNy2sKse2A2RhKhVIZN5g1xSEolZqTkZdnUrd0tTzanCB3Dv77%2BeO%2BuKdtDfDK6kAAFyiJHdslEcIYbmlTHDxjVp1y4kHJJlAHNJcnQu3oIEd68WoSOG49GOr4xRufdpRfaPl%2Bl8Z47hcR4Sr71i7l0yi6W0%2BSn%2Fk4HAiVQI5RMmJlCPqEuGo7%2BeFj3RPCAgOUSxPEkBMOUTxINhE8BBUE84KgnnATc4aTBPOKqUwElvJ89%2FgiGkWiv0evSEpUTe1hcqJ7gBzh0fuetVgkJJuBe9ufLu7e6A8xHZADaKmgHdJBBF7iJFGxteAlN4nSLxLFVAgLTWqmumvIQ2vShQ1AxCiYsemptcnNuF6X6O67jdFjYK9O8XOpycrWZBNPmEJKm1Fxl3kWifK9INht2ER7cFTk7giQxHTaOae7L4qphpNQVMSaXnUsFYUSwtX2pdxbUBy9cBScv26f2Kh2xRWD3RXcX0kS7WsvqjvG8B4Xh1T1bxjVdT7i5v7xUZNMeRzjHK8P0O4bX6ioDB491JlZeYmSqeeLUoykuvrAudA7B5ybAecx42498rJzc5KTaJSXW70LYmHggX0tJPWWR9yLi%2FdAXhGMaxLgDCsmilybZLaC0wlxxXmW4oG57Y81eqtZqrcq9XWGi6kLSh9Multbo52VpsFW7Nrx66RSKlX8NqpdFn0LelJtc0%2FIKeDeoaQlL6L%2BVt1SByi1ViiVGiOMNVAsa3gSlKHw4UfttJNoD1P4vnpqQXS35KnGXcbSghMkhK06eSkrG4PninSKzLUWWEw1TmJuorJsuab1tMo7LJOylHz7CLM2T0g5dv5IzHDcjKV3DiqXUaU6kMzWuVq0unUuXUR12nkc1tHYgjdJvzB2CmjEeMZ%2BmJeqJlX6Y90sulTso10SVadwCAClQHI3izUhilMy66lWOkclmtm2Eqsp937m%2FvUjYkx6GatPYamJmnSs1Lz8itWmYlydUtMjzfcnuIsQY8VRkHgw5NyzDpkmZhTKVkXShRGpKVHsJHrt5oC%2Be3jEKW2pWQptMkWSkKaZRT2zrTfqkqWCVenti3ulyu1VDs8iWkdTYdmVMs6EoQkdZegdthyHMmPecP1bEMrT5ql1BqeaalUS2h6YShcoUXu2dRFk3JKTysYtb9JqbE09IJ0zDqWFLUJZYdCm09ZVinmBa59EBdE4qqdNbvhCisSEqUgJfdlkvPL7NRWoEAnuEV5mrqqryaJjymMysw6hKpeotSwl3WVLA0LWEgJcbO29r23B7I8dAlZyt0B%2BhSNWCXG5wTYkHXght1IQQHEE2GpO9x3GPLiFuozDknSnZ5VQflGQwlDaulDKSoqDSSOYBJNhsLm0BZJmWfkZt6SmhZ1ham3Be%2FWBtt5tokitUlOuTi1PqPSiyVnvKQB%2BaPPAImiWEBdaPhyrV1TaZBlsh1wNJUtxKAVnkNz2xQlaTNzUy5KIaSlxokLDiwjSQbG5Pni%2FSsmlqnUdipYXdnEue7ys1KLspxsq3Qvzgg%2BcRZ6jJPmenTKMPuMNzCkgqGtSbnYEjmfPAKrQKjRWJWZnm2w1Oa%2BhU24F3KCAoG3I7j1x4GzFWZlJyVZb8ZbcaQslSEquPSQI86IDoPhETfE%2BIldgpab%2BjrXizMsKc4Yq0wASV44pCf%2FAAc1GQcICCqvYsUOaaSi3rVHhkJlEnwvzNQSi6hjunABRsCUSUze%2FwABgNDeIulsLCT1nNCNvKiXxN8p1hC9OrQCE7FXcPPGRSlcMo1ItNttlUlMOTDKz90obg94iU1ZTCG2UJSlLc57IJSOxzt%2BC%2FZAY8ZJ%2Ffqr8sN8vfd3pgqQmEhSlIUAlQQo25KPIemMgXWVOBwKDZL06meNv1UDs80Qm60twzN2kpM4%2Bmac08ukFiLD0i%2FwwGPOyy0dMgoV7mQDtyvEfE3GypKkLBb8sEeT6Yv0xVlTQn1EJBqSm1OpAtpKDcWPntFGbqHjb8466hAM6kJcAJsCBtaAs65ZxsuagboSNQtyB5RJ0KuWk30g2tF7dqKn3H3Cm5fYQyr9zyMU0V0y830wk0KX0Qa59ieR9MBTl0kU6dCkkHQ2Rt%2ByA%2FPFaVbUuqtpA3Lh%2FiRLO4gcnpNcsZYJ1hPWB5AEHl8Eeum1NTs%2B2sMthK13PwJIgOn%2BBxJVPSY2%2FsxkVb%2BanzPL5IynjbX%2FAPEPD7IIsmjrWR23VML%2BaLJwNBx2cY6qSlrF8o4R2gmnTO%2Fo3i78byj9UihD%2FqS%2F%2B3XAc8Mf1ZLjsL6AfMCsXPqjtxhx6QfDPUda0pKV2soEdv8ANHEskCqelUgi5fbAv%2B3EdtuEvJJUhKNAssJ3BIHf8EZbD4yfMxXjjs4e%2BTnlMOo6BOom5snkntN421ljmUiiKRKvpWtsrKHkKX5bZ5W%2FZJO4PaNo0zKrZYQXErVcpIAPmiAm1B7pG3Skq5Ed8butzZdsydUkalKpnKfMJeaWLgg8vTHoD61ABJI9EcmYYx3W6EEolJ11CkO6ykHZwW5HstGXJ4kJ6m7VWiIdUntZdsSO%2BxjLTFM8qJrmJ4ozdAqlpRxtTMzIy7qF31hbKTqvzvtvePnlxDYE9p2Oq3T5djo5RtaJqUCe1hzkB6OXwRv6t8VEwJN16i0NtDgt0Sppw2573AjReOMa1jG9RVWMRTLczNOI6MFLYSG2%2FuB5hGaKaLOic5195FNpaV2kTlxcubTtCozbCl1qbbtNup0yiFbdEj7r9sYnmykNrQ43ce9t3xf55kdJrDiVH7nuA5WiwPrcXqQspVqjQlvROfGstU0mnTQBvZJI25G4v%2BeMekmuum%2F3QjLquSumPdKhI6ptbblGMSzajpKe8RSrWy06mmaynTXqunumnB%2FCjJsxLHMaqlI6pWzb8EiLPX5MN1yrOOuMaXH1ruV2vc39cXPFZdmsZzzywNSltm9%2BfUTvGrOtl5Gxcr2UuVBaFmwTJPm%2FcQ2bfLaLNXLl0bdsZTlMw4iqEISFKdk3kC42uUG0WDEks806C80QfMIhLEJxJIPVEWiYYJPKMgeZCzYaifRFBVOdULhPyQGPKliRsI86pdaTyjJ%2FY10Gymz6ogqlk8mj6oDGOiI5iJSm3KMkfo50X6Mjt5RY5xjoFFIPKA8hSCqK0ulYcGmKaASbxesOUibrFRl5CQllzE1MOpZYZQLqdcUbJQB3kkCA2jw%2FcMeYXEVWKhSMFGnyqKVLCZnZ2ouFqWZCiQ2gqAJKlkGwA5AkxrzHuAcT5c4qq2DMXUpynViiTS5Odll80OJ7QRspKhZSVDYpUCI%2BnMzVaL4PzhnpEr7GMVjGdbmW5iclCvQZybslUwkkb6GW%2Fc0%2FszGCcfuVlAzYy4w3xaZafphJrpsszV3Wh1nqW4f0PNLA9%2FLuEsudoBF%2BUB82lotvElyIuM9K9A6UkdsW9xFoCVB3ippKoo8oqIWRAUnJ9WrSwwkJTsCST6YrMvofTdKdDiPLT3%2BcR51ya0OdGOuD5JHyfJHolpcMoUoqutWx8wgJt%2FP6obnbf1RPpjaWSORlTzpl8cPUuuSdOXgjC8xih5E0hRE20zsplBT5Kj2E7bwGqS35okIttaNnYMyCzczHw9O4pwNl1Wa1S6aD41MSjOtKFBOpSR2rUE7kJubRrp%2BXUncg7i%2B4se3mOw3EB49HbHm8fVfqISE9xG8e%2FQoENqGyuZ7o8s3TXWX%2BqCpKhcLRv8sB6G7zEsibSjSlV0%2FCOcQQLROyjoJVLA%2B6JUO4wsewQGQ4EF8WUH%2FteR%2F8w3HSnhLSDxcYoPdJU9P%2FAIVv545vy%2FSo4uoGk2UKxIEfjLcdFeElXq4t8Vjul5H%2FAMq3AcnuIOo%2BeJT1EFz7mK7nlRKEBaejPvoCml51wBSimw5AC14m3PZEolXg4EoaUoeaK4a2gKQbB5iJwyO6KgRaNl4ZySruKsnMW5y02oySadg2pyNMnZR1SkzDqpryFN7aSAbXBI2vblAav6MCJbeeNg%2FUVzUXgNzM1nANbXhVokLq4k1GWSAbFZUPeX21cvPGDuS60K0qTv6ICh0iGm%2BkV73sjxN1ybbcupDK2yd0BNtvMe%2BPa430iOj5x5EU1fSX0HeAucwEN6FtO9IhxAWk%2BnsPnilE76dIba8rQm1x3xSJMBU6Qd8Ok88UoiOcBWSu0T67naKA5xUSID0NkxXST3RRaEegJFrwGZUz%2BtTXoMXrKZpIzRpc0sgJlw%2B4onsAZXf5IslNP6VNftTGQ5TttuY9a6RWlBlZzUruAlnCTAYBP1NE9JLkJRam5VqXvqHN1ei9z5ozThI%2F%2BpHK%2FwD%2B7qN%2F5xqNfrlA3L2lXlLuyBYIKrXTy2jP%2BEsKTxJZYBYsoYvowI7j441AfodhCEAhCEAhCEAhCEAhCEB%2Bf7jpN%2BKLMpJvcYinf4wjn143LN7W0I9cdA8ddxxPZlEA%2FwBkM7v59Yjnxzy2SLfakgiA2DSvtW33Cfyx2Y1nLh7J3AeSuLqrN42m6xLYBW9TaBIP2o9QSl19sCcSTY3Wo3sDsBHGVH8n9yIu87V6tUmJKVqdUmptimSwkpFp5wqTKy4UpQabHvUalKNu8wHT%2BF8Orw9N5QYDw5kRR8ZYbzBp1PqmJK0%2FLrcemZiaWozbbL6TplESoJAB%2B43iviKQXR%2BHrDFHwJWMfTE5S69iySw6%2FhpxZlphhFQUgLnig7pLaTpI88c40fMPHmHqA%2Fhag4zrFPpEzrDklLTakNEK8oAA9W%2Fba0erDGbeaGCqM3h3CGP63RqY0VlErJzOhtOq%2Bqw7L3N%2FTAb8yfl3neCbHUtTpJ1993FiEpYYQVrUrWxcgDfYc41qjDWLOt%2FwYrHlH%2FkTnzQyh4k8eZM4cfwthGm0mZlZuoOVJ5U6hSll1baUEgg%2Fsb79pjfuVPF1mVjDBGauI65KUIzmCMOtVimtsNKCVrU7oUHQTcp5HaAl4OKNVqbjjFoqdInpNK8OhKFvsLQFq6bkCobm28cUvga3R%2FjnP45jpWZ4%2Fs5FI0tUTC%2BoBQ6RLLh5gjv89%2Fgjmfnq%2FbFXrNzASR3DkE2HeESaQeRlsRX9TkcQEiO4%2BGFUtU%2BG1qhpdCVPzNYkXDz0Kcun%2BWDHzX3UJijDLCurVFrH3K3Vwif1tUd%2BmXKGVzY%2BofXU267tdkD%2B2tLb%2Bq9otqlPymOKBPtqdaTKsTN32wbtFRTYgjcHnyjbGW%2BRud%2BXEvVaNVMrKJjSlzhZDLDtd8WbaeZunpk6dzqTYb90Ze3gzMZJURwiYYAHIHFrhsbW%2BGPQ06YYHl%2BjerPr07WKcMveeXvVXQ0%2B5UMMJUUrxOzc7kdCv5orztYk5o092Wm1zIYRpStSSm6UqukAHstG2E4QzFUvr8I2FBr5lzFDtvXFAYTzGtp%2BtJwtvzPtme5%2BbfaJ4Y4J41Z9enanuXe%2FBVdDmqoZcTWI6i0JepyEsmZWvSJlZQlq61Hrm1k%2BnziNZYioQpE2hhD%2FAEyXGkuainSQSN0kd4MdyqwdmQ5LuMt8JuFUuLQtKVjFbgUgqSU3Fza4vfeNYTfDBmVMv9JM5Jsu6UBtOrE6eqB32TuYrOmeCx9Ys%2BvRtTGE3qr93VHniXKJlxfn8kVW5RKkqWQbpSbD7o90dVtcKuO3BqORdPR5lYp3%2FixB3hRzAsEoySpRujVqTie%2FwcucV4a4Ly29HXo9pacIvcfQnonY1b9RamUTEEuqUx9IVOXlnpd4TMpLudE4dCVqCdQB6qyWySOaSeW8Z884HHFL1Drq1Rt72jZpttJa%2BtdwWopQhGr2fdubCxPlczFT2h5pq8rhiwQP%2FwDoHfpReNMsFmPlNn16dqvcu9Z%2FFVdH5tPXA57Xjx4nadmMM1WXYTrcck3kpQOauodh6Y3Y5gTNxegjhpwQN7ajX3Vkj420XVOXeZauiaf4fsAqKrXtWX7J9JCorOmeDRqvFE%2BaqnatThN6nPOzqj0fm0vJ1WjrpNPcqGJEyy0SbLZZdaWotWQBp5W2iv7O0YNKlKVWTPlZBUhDKkI9J1Wt3Rs2Yy9zbbmXGZfhuwI62FWSsVp6xHpK94pDAecSV6W%2BGzAmkc7Vtzft564nhng3jFHXp2qzhd5j93V0Obp3LJ3EM6FmtyMmHXC37rqCWk6iQVKtyjVVeoopk%2BJZLpcSW0L1EW5iO6EYBzhUlaBw2YFaDgUg%2Fp65cagRcHXta9x54wH60%2FMWo7zWVNCKmkhpvpcSm5Snaw2%2BUwjTPBvGKPRXTtTThN6qjPcTHniXIolh3XiqiWSrbTq3AsnmY60a4SMf60snJTD%2FAFgOurExsPhiErwo5guBTf1EsOsOFJbC3MRq%2BMDyv3RM6aYJH1ijr07ScIvUa6Z6J2NYJyYw%2FSK%2FIzNKxWudl5N1l0vCVUgOFOlRsDuBc6d%2B4nlGcB5LmslQTz2vy3jcicA50MgSg4bMvF9CEt6zWHFa7ADV5e97X27YHBGc7igPrZcutJFlhNZcHr68I0ywWfrNn16dp3KvXgq%2Bq08wodJbUPXFsxiy9O4OrErLsrXMuyy0NtJFyonsEb0cwXnW0glrhny7UW0hQArDpJvtYe6bmLo3gHNTxJhc1w74D8YeQFqQmqvK6PfyVHXa8OGODTqvFE%2F742p7k3qf3dXQ02zWaOiSkfZKsPy7nizYLZlXHSkhIuAQLWEeulYgozr5bp7s3M6AXFFcuW0p7r39MbLewnnw3MJalOHDALrKLhs%2By6%2FJ7t3NopjD2fgSQeGvACkJSUkeyqt%2F9pvEzphg0fWrPrwpOGXvwNfR%2BbmOdypnK9WW2qlWpClyj7zgcmpgq6NhPWUFr0gnSbAbX3IjUFbpAptSekkulaWiLKVtfYGO9Th%2FPIy7sueGDAI6VpTRX7LOagFJINruEX32jWKeFjNCde6SYySowVvu%2FiMm1uQveI4ZYJ4zZ%2Biunady75lnFlV0OSPF%2B%2BKjMqVktISCu4Cbm1yeyOu5fhBzNKgp3J3DAHaHK8rf5Y9CuE3MtJShnJjCbRBFlCvrPbfbfaKcNsEjXeKOvTtXjB75ln73PQ1nI5OUnC2OGJyg4jXVKfS5tp6WnlSxZVMgJSono1bpsoqTv2JB7Y2gLT26l6bqKufeY2YqjcRibFzh%2BywJG1hMqsfPbpPNEBSuJQEKGRWWYI5folW3%2B0i%2FDPA%2FG7PrwThF78HV2bWtPFAzdKU31d%2B94smOqZNTGCqszIS6nZtxkdGyhPWXZSTt8AMbs8U4mUcsjcsvxlW%2F%2B0j1SUlxELcT45knl5yJu0%2BuwVtz68Vq00wOIz33Z9aFowe9ctnV0fm0grEFCQ0148%2FXELS0hKkJkFLAsOQN%2BQj10TGNLfqMvK0lNTfbYS8%2BvxhstpSVJCRZJNrkjc90bcm6fxKMrSPqGZZvpUFJJTML1AX5E648Jk%2BIkXSOHLLg3FifHFgW%2FCc4iNNMFn61Z9eFZwq8x%2B7q6PzcxzWTk9iWruvTVblpJl8uuLdWkqSgDWoE2uewD4Y0zW6QaZUXpC9y0QLkc7gH88fQQSXEQuWfk1cPWXDSHmHGDom1hQStJBsekNjbtjUr3CzmnPPl%2BZygoKldUArrqzsBYC94nhrgsR8oo69O1E4VefB1R54cilgDbtivLygcW0jdRUtKbDzm0ddjhFzMP%2F8ADuFOqb%2F19XuO7yoqMcJ2ajEw3MyOUGE5d5o3ClVxSgb%2BYqinDjA%2FGKOvTtR3KvPNnoaspWUdHw3iuVq0niByYlqc%2Bh5CzLlK3LD7knq9bb5YzIOBbiukMbxVhXiDtqc4eMsliwBtOrF7W32c80UVYbz6TpR9brlkQBsfHXNvN9s5xPDXBp1Xijr07U9yr1yWVXR%2BbS4DHaoRKtnfUlV0%2BYxuKZwbnzMC6eG3LkKP3FQc38%2F2yK0nhPP5l4OI4d8uELHvzPLsbebXGfhngeXyqzz%2FAJo2qzhN95LKroapzjWlXC7hlCFX0Y8UDbv9j1H%2BUI6j4MZliY4Z6YJa%2FwCh5CpIdJ7VJfcK%2Fg3A%2BCNA5s5E8QGZkzR6c1gTCeHpKjhwplaXUFdA444oKK1pWo3Um1rjsJEdM8O2Aalk%2FkycIYhnZV%2BalZGffmHJcktpLpU4UgkdgvePBac41h2KXexs7rbU11buJyic%2BLKrj6Zh0rldbW7UVVWtOXFP4PnSyrVoV36j%2FCMdK8CCgnNjEJ7Rht0%2FB0yI5nYPUT6FW9FzHSPAu8hvNevtKUAt3DL%2BnfmEut3%2FACiPZ6b%2FAPx%2B3nyR96HNw%2F5TTPl%2FB7cWOkcYGaNusZfBLbdvP0cvt8saNrEx4jJSc0GytEtVJZx6wuQm6r7R1HmDkjmajiJns6sESFIrlMq9KTJVGkT8%2FwCKF0FgNLSVgcgUJWCN9o8T2B8fMLBZ4WcFLsLXTit4fDuOccjRzSzB7rhV3sK7xRFVNFMTE1RExMRETE5%2BVs3jDrxbWk100TMeTLa0i5irAri%2BlcrU%2BpRFz%2Bl61G%2Fpj30Ot0Orqn5SkzMytpLbISt9kthPuuojeNsKwbmHzHCdhBCvu04tc%2BaInCOYLKx0fCphld%2FKUjFrg%2BS28d7hpgvjNn16drD3KvHg6uj83O2P8P1LFVZXMICXWhLMalpVvdlnQUgdpjUmZGB0YJrb9DVMNTExLOdE%2B4w8HWlL0hV0LGyhZQHpBHZHciMJY4S4HFcJWGDY3t7bXQPRsI19inhqx3izEExWHsk5KUTNOrfMqMUXbaUo3KUHRfSLCwO8OGuC%2BMUT5q6dqKcMvNX0Jjzw4sLITtptBuXKlWtHZLHB9i1arnJqiJKtgHcUr2899Eehjg8xk0sk5Q4aKgb3ViR38wivDfBI129PWp2skYPep1UtBUbJiQrGDaNiWSr0tMP1aXfdmZROpK5BaJhxpDa7ixKkoDlxsAsRvqmzbbVKplPU8hw0uQlZEKHIltOn80bIwrlpmvgzDkjQJXIDLafbpwWhl6bqzrjxC1lR1EEXsVG23KLg3Qs3mybcMuWRJ98Kq%2BL%2FAMKK8OcE8Zo60E4Reo%2Fd1dm1rYNJcPRhQX32MXSkU%2B9RkypKkN9KFFZ9MZ4JHOdtQUjhty0AT2JqzwPyqj3ycznUwg9Jw6YAQ4D1FIqrun4QTF6dNsEq%2Bs2fWhE4VefB1dm1yXQsUUmSkBTq4upyk3LvPpcR4mpW3Sq3%2BWLirFlAKG0SCqpMOPuNoSFSakBR1p7e6Oo6nO56zy1JHDzl86CAekXVVglVtxyi2u0vOZ8trmeHDAC9FyEivOCxPPlDhpg3jVn14Ypwu8R%2B7q6I2ubc18JVnGuM6pUWG21Sky%2B24k6wFCzaUFJHmKfljSmZeCmsGYjforM03MqllrZddac1tLWk7qQrtTuPljvxFDzUK9TnDHl8TqCrnET29u%2B0axxPw05h4rxLP4kqGTtAQ7UHlvrYRiVYYaUo%2BS2nT1U22teKzpxgdOu80daNq0YVeJ%2BhVHnhxJ0HmEOg8wjtFvg7xlpQfqQYW1AEHViR03vy7OyJkcHGMhoSrKXCarHrH2wvWI7uUUq08wDxinrRtO5N55s9EtA0zJaRquFKJXpCrJmHatImZda8nxV0OrR0RuOsSlCVXG3XA5gxv1icablpVlTwuxLsy6VE2vpSBf5I2VhXK7NjCeGpDDrPD7ltPM09tTLTszWnlOqSVqV1iCL21EcuVouLeFc3GwlA4a8sNKbm3sy%2Fz%2BNCNOcCnVerPrQmMJvWXHZ1dEbWrQhT%2BpwqHXj3yEpqC0oIJN0ae8nlGzEULOZASlHDplmAnl%2Bnb3zxcJSQzhQhJmOHvLtDgPV6OsvGw9PZFo03wKfrVn1oO5N58HV2bXJOE52nyeHZGlVh6ckJ2UDjLrK5JZCVhZ2BAtF4aq9HS%2FLtS89NTLiplj3ISi0ggOJN1E7WFr%2FBHUEwznm7NKUjITLktkggqqzuoW7zbeKKsP5uvpu%2Fw85cKt2ezryR6rRWdN8Fj6zZ9YnCLxGuirs2uVM1MGVTHuN6jWpRhKJJ9xJJ1%2B6FWlIXYdwtzjSmYuE5fB2LKlh2WnGpxunzK5YTLK9bT%2Bk21tq7UnsMfRJvDGaDakEcOeW9kEbe2CY3seR2jVNf4T8c4jrlQrU5lVhhBn5pc0WG8SOhDKlKJKUdTZO%2Bw7AIrGneB%2BM0daExhN4n6Ex542ZuHPF4nalQpVjHbyeCfE62dCcssJpcVvrViZ42%2BDREDwSYq36PLjCiSTe4xI9y7vIi%2FDnAo13inpWjCLzyx2S0I1kjS3qHQapRqkxUXKrSmahMFpS0mQfUVBUu5qAutISFXFxZY3jfoqypqVaQoAFuWaaUR9022E%2FkSI2fRstcz8L4apeG5fIfLqdaprAl23n6%2FMLeWAbgrIAud%2By0ehOFc1kai1w%2BZbtKUQTprkxy7QBaK8OsD8Zo6U9yLzzKuza1e2jXt74eV88XVVHfUx0iW1KBQuwAN1XSeXfGxG6HnK2FBvInLZF%2BRVWH1W%2BSLrLqzuQnS%2Fkxl8oosW9FTfIFv3MOHWBR9Zo6TuRevBz2bXINOqUj4lLJn5ydlH2Wg04z4k4SlY5jlaPb7N0xycpklIzM9MKFTlXFpVLLShIQsK1XMdYzwzzmgt93JbLp4qOo3qboWT3%2BRziwPUbNyYPSTHDrgZxRFjoxA6j%2BRExpvgtWq80dZSrCraNdNXR%2BblPNXAtazCzDqlTlxLhiecbKFrdCexKeXcOfrjSGMML%2B1jE1Sw94y3Mex0y5LdO0rU29oUU60HtSbXB7rR9GmKJmky4l1XDHgVakLQoE4jd96b28iNN13hMxriGuzdZmcppVtU8%2B4%2B6j20agFKUVGxKOVybRMab4J4zRPmqhXuXbzqpnocVrYSCRBuXBcA5x2aeC3FAV0icpKYUfcnFZv%2Fu4kd4LMULOljKuTZSTcn20gkeYe5xWdOsE8PT1qdqJwq8R9GeiWlJTKKXpT1LrFOqqJwOyzM4VIV1WlLBuysHktFt%2BY3G8bQcmQhHRtuoV0SQkWHl6UgXjd9FyoxzSKJTKFO8PGHqo5T5RuVM85jEocmAi%2FXcAb2VvY222ideWOK3Wi29wzUOxOrqYzII81%2BjvGWNNMGnji8UZfz07UdzbfmVdDRDk4hbm%2BnfrBIHLzR5JhQUrlaN%2BrysxCtxS1cLlGIUSb%2B3ly%2Fwe52if6k2IUaXGuGqikgnZzGSlCx%2F0cVjTfBJnKbxR16dp3MvE6qKuhpqrLI4VM1EFRsucooAHeJ1O580Z54NRZEzjdre3jNLctbYG7ov8sXDMfI7NXGuBV4FwplxR8HSs7PsztTcTXjNCcQ0k6GSjQLALIXe%2FNIjPuEDITFGRqK2%2FimpyT8xW5mUKGJUlSWks6ipSlEDclQAA7o8pphpThGIYdaXe7W9NdczTxROeqqmfVGbo3C4W93ri0tKcojvuauKg34gManunkD1Moihw3IC8%2BsvVK97XGj%2FAXEvEvMsTmfWO3pdWpIqxbJ%2FZJaQFD4CCIk4dXksZ8ZfLW4lCfZ9hJ1GwN0qAF%2FOSBHpLSmadEYpy1WH%2FAAcywmN%2BU%2BePwbn8IQu%2BJ8oWL%2F3ddX8PTSyY19nS0VZrYhCtW8wTc9u6o33xcZC4tzyGGJ3B9UkpKew6%2FMqPjSyi5c0KQtJAO6FtgkRaqrg3MeoTPjta4asEVaorbbTMz6sVPhUw4lASp0pA21kFVuzVHntD9KsKw%2FCrO729tTTXE1ZxM5ZfpTMa%2FI3b7h1vbW1VVFMzEzydDQlEq1DfosmapXkyTrCClTS2lqCd%2FMI9XthojCFytPrvjbzymwZZDCghyyr3JOw02vG5kYKx6G0E8JmBjtYp9tD4t6hFN3BWPUOahwl4IX0gCv7KH7It2co9Rw4wWPrNHXp2tSMJvGfHRV0fm58xq25XMJzVHkkIS87PomUFatgjQpCh5uYjUmJsp5rD2GJTFL1XlH%2FHZt2WMm0q7zBRoJWsdiVa%2Bqe3Srujtw4TzDU4XFcJWA1EjTc4mevGN49ygzNxtTpORY4ecL0VqVLoWJHE7gLwWoE6goHcaQAR2XEOG%2BCeM2fXp2sncm8T9CrocIOyKEm3MxRMom%2Fkx2VLcJuNn0dI7kbhzUCdXS4pcBI7NgIqnhGxqqxTklhRAG5BxM6SfNfsis6c4FH1ijrU7SMHvU6qZ6JczYAy2kMWUquz83iFiRm6X4mZOnrbUXKiHXCl3o1gaU9EkBatVrjYXMbZwBQk4TocxSVTOtTs4l7ceSNFo3Jl7kPmpl9MTr1P4ecC1JufQELTP19xxCCk3BSLj88ZQqg5xa9R4VcsCO4VV76cRw4wWfg3iz69O1M4ReaddnVPmji7ZhpFYbW4RrSbRKpjWOqbjvG9o3gig5zhICOFnK9AB2vUnuXb7%2BPdT6HnOyHG3OG7K6XRo6mmceWSb7Dy%2B6E6cYNEfKLPrwRhF5n93V0Rtc%2Fsz1Pk6i%2BzVZx6VlpiVaAdbaLg1JWrYgb9vyxcZfEOEKW6zPSmK5xt%2BWUlbbjck4FJUDcEbc43tP0XOALa8R4bcqnbj3RT8y6k3%2BPHiGH87za%2FDPlILnSbz73VHf8AbPyRHDjBvGbPrwr3KvETl73V0Rtc34qlzivDjEkzMBpfjLjzZc2Km3Soknt5%2FljU%2BMcsU4WotLqwrctNuVB6ZadlW0nXKhtYCConYhYJUm3Yk3juY4dznbWFDhhyfdKBpCvHHb2%2BFcYdmBkxnHmE7IKncisAUwSCFtoTTau42hYUbkrTqNyOQPYItGm%2BC65vNn14Jwq88lnV0RtcJvyaEqttFHxVHLaOzpfhHzGKQlWUeCFHSd3Ky9sR2nrRXb4SMzCA6nJ%2FAIWtekoVV3jpA7fKtY%2BaKcO8E8PT1qdq0YRbzriehzZgDLfD2LMOVKoTtQXL1CnusNtsaSQ%2BlwquQrkCkAbHnfzRtLCdLlsN0U0uWmQQhZJBA8kiN3YCySz4y5RVDRMpcrHUT%2FRBbU9MLfCigkpU31%2Bod7G%2FPaMhXh7iSuoqyMyYJcG5DR%2BC%2FX3tE06cYLVqvNnHnqTGEXieKmzqn0RtaEK2eqjUOxI33iLjO9%2ByOgGsM8SujUcmclEK%2B5VLKJ%2FjxcZTD%2FEcnV43lPkykAAoSiTc2NxfkruvETpzgtOu82fW%2FJPca88yrs2ucJGdlpefm01Vc4yxMtNNNrlWi5qKVEqCh3ciIu0niDDFJmkT0pWKwl5nroKJNTe4%2FZX2jfNQoXEckNGkZUZQm5PSB2TXt3W64jxN0DidcFncoslWx3Lk1%2FTiY06wOePfVn1vyRGD3ifoVdm1zNjGnHFGHJGilbbTsrocJ1DyV3JB8%2FWEazx5llT8J0egVKWrSJx%2BrNzJnJYNlJkXGnChKCo7L1pssEchcHeO504e4mQL%2FUjyUJIuAZRZsb8j14xDH%2BSmfmP3pOYrWWuVjLsk2ploSJdYQEqVqJUkKso3J35wnTnA6frVnPmnbCKsIvFP0Kuza4HmJJvV5Qih4o2nbUI7lkeEbNVTanF4EywbJGkIecmFnbtHW2iK%2BETN7pdCMDZW6fuvd%2FpXjHw%2BwTPL3%2BnpXjBbeYzylzFgLLfDGJcGTVYnKvNtViWqCGG5boby7sqptZU4Xb9VxKwkBFusCTfaNoYVYl6FRWKI3M6hLla1rPIk6QkjtAsne%2FbG9MG5JcSWXzU1LYbwflA4zOKQtxE3IrfCSgHTp1K6vMxenMJ8WpUoHAuSaEk72olwfg1Xhw8wTLObzRHpnYrOD3jkpns2tDCYl1AqS6kW7jzgtxA2sSY3ycH8WgRoGEMkj5%2FYE%2FSi50zCXFQQpdQwxkzfYJDdCUSPliZ08wOIz3zRPmmdincm9cyeza5yl5qRQp9ucbnNK1pU2plvUm2mxBuRvFV2uUWUQ54oirLcUhSUhTITe6bc7x0XP4K4oXVpMjhzJtCffBzD6zqPr2EeGawXxWtqWlGGsln229m1qoJST6Bfb4YiNPsDyzm80R07F%2B495iOOmeza5cxXQjjDDtJo0w4uVcpLrhStLetLqVtIGk9oIUk78t41lj%2FL6m4YNKcp9W8bRPSKn5lKmi2ZZ9Lq0Fq58oFIQoK%2FZEdkd1OYW4umSgs4YyZWVbEpo1tPpuYwzG%2BRnEnj6bYqmJcKZXOzTDHi4MvLqZSEAkgFAVYkXO%2FPeL8O8Dyz3zR0%2Fkr3JvHMns2uEXJRkHyk%2BuKKpZu%2FVUPXHa7fCVnW4wpasIZXBwKADamXCSO%2B%2Bq0FcJueriFoOC8rUAAAEMquq%2Fd1oxxp9gk6rxR1vyT3HvHelzrgnKjD%2BKsMIq71Wm2qimYUh1kM3YEvoulQXe%2Bsq2025b37I2hRpVqiyEtIszKtLWxUsA3PIEfBaNzYTyV4psvqXOUzDFIypErNupmHmX5XpSXEgpTp1HYaewbGPa5hjjHUsKOD8n1ECw%2FSpq3ptq5xkp07wKqPlVn1vyVqwm808UUTPRtaflF9Kw%2B5LOoLiUHQn3y97KsPMN48qwVS7U42Alt1XMG425xu1GFuMNkBxGFMnuk7xR2wofDeKQw%2FxmIHRIwhlKEXvYUtsC%2FfbVGWnTfA6vrVHW%2FJHcm9zqs6uzasPD7LPy%2BZlOnnUnxd6Rnka9hpHi7libxrTwfYIzmmL%2B%2Bww%2Bn4NbdtuyNyVbCHGPiTD1Ww9O0HLKnS9UkXpJ16VlEtPpQ4kpUWloVdC7HZXZFXhc4ZceZTY2qGLcVTNPQy7RzT2GZdwuuF1ShudthYc48%2FpVpZg98wu2u13vFNVdUZRETnnqblxuF4sbaK7WnKI7%2BTFuPNJGfCfuTQJAj%2FAGl%2FljnE8zHRPHVMJmc%2BrpWlXR4dpyDb3pGu4PnjniPXaKRMYLds%2Bb%2BMuPepztqp8qWbt7HzWnmGHP4sd3cTrvi3CQ%2B%2Bu%2B2GqVa3MKK5cAj0EXjhCb3p04kc1MOJ5d6TH0MzqwVVc2eHNjBeEPFlVCew9TDLJmHdCFpR0DhTq5AlCFAE8jaPIe6BeLK7X%2FD7W2nKmKpzmdURuqM8%2FRx%2Bh08MpmqwtojyPnvxH0aZczNmUEaQzSKMyNXaE05i59ajGsGaPNMtg6wpJO1hH0UzD4dcFYirc3iKbwdmHPPTPQtobkGJQFppuXaabQOkdAIAbuT2kmMXmuHrLuZT1shs3GDLpS2OhmaeA4d7rOpwgHltyj1F30pwiLOmmbxRnlH06NrWquFvVMzRTM%2BidjhtqRdBZUoXHTN333trEQfpE7M02balZN5wKqKghSUkgga7i47tQjrPMvC2VWV0lTKriLhtxvL9M8zKynspXpdhiaLTiXHgvogTrU0FpuORVfsjV1BzGwhTmJ%2BmzOBsQy0kKpNzNMZpGIkS%2FRybq7oZf1tqDriEgJ6QW1DmO2O%2FdrxY3uzi2u9cV0TqmJiYn0w0rSzrsqtzXGU%2BVqmbo1XmpmqlmkzLinuiLSQ2bkJUkqA280VBh2sKW4j2HmihympQk9EqwXpFxyjdqs0MsQg6MB5gFRsN8XsADv5MxOM3MukgAYJx%2BBbcDGDHP8DGdjaMZpNSE1Tumpc0oGTUFENKFlWd83nTFvkEdWkKt5D7p9PXTaN81LODBDMg4igYExi3NpZWJczuK2nGEOlBCVrSlkFSQTcpuLja8Y%2FhKYy4rLlBoX1KsQT1efbbl1NSNQbUiZn1OqJUygjUlKkdH1LmxSrexilddNnTNdc5RHHKaaZrqimnXLSnRnqmLmxLTP21DoSh1gNqQRe9hz8xvHSczkfQygzk9kbmbLOXWVyzEqlTaD2AKvuDcxXp%2BUmFZxozcxkfmTTm2iEqvKKd13G2yT1R545dOPYbVqtqetG1tzh95jXRPRLVGbExV6rQssC%2B%2BgBjAcrLNqCd9CZqZty7d7fAI1w%2FKW6LWOsG0pWfOBuY6nxJhuUxDK0Snv5KZitS2HKMijSa2qYnW8hLzjgW6Sr%2FABpG2%2Bwi1y%2BV9HqbMlJT2SeYFMRIsqS5OIp5ddnFqXfroCrDSNgRbl2xecYw%2FwAPR1o2sc3S35k9EubWmVJEwEi48TfJ9Qisyytt6kvCWdcal2yHigHZSi4QL8heN9Ypwng7C1Lln6vlDjeSlZVtUpM1R2UDCZhTurQpQWqyVAlKRyuE95i3YbzCy0wxiWrt0XDGNJbC8zKSbUiETkl7IhxCAXw%2BVoU2pJcU4UFICgnSDeN2wt7K807uxqiqO%2FE5sVdnXZzua4ylpWSp880mmNrk13Zmyp79oVN2P8EwXSqh4kUCSdK%2FHw4eqTdOkg%2FljoxecGVgKOhoWZiQCdV6pTbkdlj0PyRK1m1lN0ig9h3M5SCokFNZp6VW7BborRnUc9TlIqZFVKKe8UvTaVN%2B5ndIcVc%2FLHmnJfS%2FUwpJBbYQLEeSodECPXHRn1WMrmyhxGGcy3Sleopcr0gnUL3tcM7Hz7xieEsS5OT70%2FO5r5bYhnp%2BpTU2pxdGqLKUIYUlBl7JXbU4lwOazsFAgix2is1ZRmNL%2BLq7ImElUVIYaMwghtWpKim6hvcR1erLbIWYsmpZMZ20ZxDCW9Dcmy50m2zh3NiY88pgfh7mmlMzuU2dcobBIeakmVcrb21c%2FnjRjFLnOq0p61O1tb0tcs5pnqzsarqs3VX%2BHfBUjOLBkpHGld6FOkApLkrKqUkdpFwT8MarMp3gx2DUvqNTeGqPgBOVObq6VRahM1CVcTTGenmH32UNKStRV5IDYI86jFqZwRkfPaqY7kxnE10S9ReRT2S43dVwCNe4tFpxO5xGfvtPWjapTdraqcoonolyq5KO%2BxryQi6jMtkHzdGuKs6w887XVNsKUF6NISLke6p5x0xiHCuRNCp6%2FZXKbN9qUQC85PLk2GihF9woqUEgAG17RhC8UZMy2LJKdw3hjG1LpLkhNN1SZL8q5PvTanSWlIQT0YaDYbSUne%2Bog8o2LC3s7xTu7KqJjyTn6lK7KuznKuMvO08ZKZcqUxKtSzms09ppIIO69Lew%2BWKbLb6TJBbDgSmRdSrq8lHpR%2BUiN%2B%2B3bKFvZFTzMQo99Np6reg64kGOMryvr4jzG0ch0lEp6%2FWAv8kZlMmg5Zh0exeppQ0LdK79g1gxQ6JSKa2VpKVeNOCxFj9rSY6BexllS4DpxBj8E2uVYcp6th2fbIssvXslaziGr1DH2EsWzUoEyjdIdpz8sy%2B50aSh5c0gkJClp0kaD1bWN%2BcDJpFEs%2BeuybaVaoqeLzTk2pwhtKynknl8EdQy2XuR1XlZaalMn86ZSWmJdK2XW5dh3xhKtw6Dcix821oNYByI6QJVlFnMnoukC3jLtEOH3o032jRnE7nEzHvtOcfxRtZd72kRnuZ6s7GsMOOTLvDjjykuPEol8VUGfDenZJWiaaKwe2%2Bm1vNGtPEz91HXDNPybkMIVLCIydzXXTam5JOPTS5Fvpm3Jdx1baWzew1F4hVwdhtFip%2BBMogw7SXMkM3HzNuIdTOqk2i%2BwlANw2AqxSrmbi%2BwtEd1LnGu1p60bUUXe2tNVE9E7HM7Eorp5RK%2BYlXhb9lZwiJ6dKrceozTTXSrDrilIQb3AIUfhAjqKbwVk3S6U5JIyUzbn3QelbnTJNtLY3Opvc7p37vhjA6hiHJimroL2BMD4rQ9I1VyZqTtSqUu267JltKEtS6mwejcSrWdSgQdgY2LC9WN5iZsaoqy70xPqRaWVVl8KJj0Zetp2UolVVJyzIpc0p5E70iwGleQQnzeaJ5zDdaclKgpNHntK5u7ZDCiFJu4b%2FKI36cy8rejSFYZzKUrmv8A4UyoBPePctokazQyxbacbcw1mWdQATbFkuLDzjot4zsbRs1h2tOTNUKaPPnpUpLKiwrfdB7vMYtVXpU5IzCZedlXpZxUuw5pdQUkjTzsey4MdEJzbytTuvB2ZDxItZeMWQLdwsztGLT%2BPMA1fGLNTxJlxU6zh2Qpy5aUkZuvap3xhTgc6V2YCAFtiy0hsAWCrgwGmW6W86Lpf0%2FCYrsUB5zXqn0pIGw3tHQuBMJ4JxEmUq6MhcdTlCQ%2B4pT1M93EwLn3HWbAgXtcb7RPOZOpUlunymQuY7nRlQRM%2BLhK3EnsUL22jnWuL3CxrmzrtqYmNedUR%2BLYputtVGcUT0Nc4R6WUyZzVlJh5AUpFBdCDzUUzpG3wG%2Fwx3%2FxcrL3DY68QATUaRsOzqxzU1k3jSfy%2Bxtg7D2QeMKfP4r9impSZnNHQSvi810rinSo6usjYEcu2OkOL8mW4dJiR1gqbq1JaJHIlIIPyiPmmkN%2Fu1%2Fx%2FDou9pTVlaTnuaonXNllnlq1T0Otd7KuyuttTXExxU6%2BLv7XB6Ba14LVzES6uUDvH1yXBIgQbxAXBiaAQiaw7oWHdAIRNYQIFoCmOcTRC2%2B0RgJ0jlFdKdxYiPPy7IrIUNVrc9oDqnhdymxPllWqHxOZmUGQp%2BWsjSZ2pP1OeW24ppooKWHm2DdSlqc0hva5JFo2xhDMnJXA2ajmcuLuHuawfTsbKkWnqtOTkpMsyqJsbTDtPBKpdEwCnpFAG2oEgC5jBsqcIZ48QvBZj7Abldlp2Qk1yktgll7SmYW7IOB2YknHRt0JSUpbC9wq25EYvmZgCv8AEJN0XB%2BBcLsMV52SotKqDNQwvM0%2Bp0kSso3LzRmp5dmVoSpKtuahpCeUBr3Pfh5zOyinahivF2DpOj0KrV6bl6aqRm23pdIWtbjKEBJ6qS1YpB7BbsjTtj3R1zx%2FVbMekYtoWWFXqTCsDNUmSn6AyygBx91hoSzzswT1i4laTp7NK9rxyVYd0BS023he0TxLpgMgy5p0lVswsLUiqMh6RqVbkZKab%2B7ZcfSlY%2BFJMZhxLYNw5l5n9jzBeDpMyVEpFXUxJSyllZYR0TZKApW5TqKiLk2Bt2RYsm9CM3cBLcF0pxRTDb98It8toy%2Fi9dD3FFmmpKidOI30eghCBaA0%2BVWiUr74iU7C8SlMBQeBUk2jGa4ohh0fsFRk6tiQYxvECNUu7tayD%2BSAwds2i74bxLVsK1hit0SYDU2wFJstIW262pJStpxJ2WhSSUqSdiDFlvaJkqIMBeK4%2FQJ6YROUeTdkUuJu5KqOpDC%2B0Nq5lHdfcdt%2BceNXiKJRpthLnjAcUp1WwQpO2jT2gje9%2FNaPLrIh0kB63GKWFPKbemVJ0HoElIB1bW1nltvyiIfaalmVS8xMtzAK0uhKrIUk%2BTa2%2FfcGPB0hiIXAXvDldfwzWZSvSUtJzMxJL6Rtucl0vsKNiLLbVssWJ2PbaKuHsTzeHRNyyWW5ynVFsMz0k%2Fu3MIBunfmlaTulY3HnBINg6QxNr80B7KgKaubW7S0Opll7obfIU43%2BxKhsr0x6JKtTNEqkjWaA%2B5KTUiUOtOXBs4PKNuRSbkWOxBIPOLVrMQue%2BAvdfqNCrbgqUnT%2FAGMnHSTMyqBeXUonymu1A%2FYm9uwxPhbFtdwPXpLFOFagZCq01ZclZlKErLSykpJAUCkmyjzBiwRG%2FeYAro7bRKrmLcoidFogrmLcoCEIQgPXLVeqyTCpaUqUyyyq90IcITvz27ISlTqMgkok5%2BZZCjdQQ4UgnvPfHkhAV5mYmp13p5t9bzn3biyo%2FLEjflxICbxUHZAdK8F8mZmtY0cSjUW6M3t6VK%2FMDGJuqK%2BE%2BaaSsEuZjsBI1e99jnj%2BWNqeD5lWpus47RMX6FUhIsuW52U4sfnMbGwpwc5jYbotYwGqSwdjHCdSnU1CVRUJp6UmZd9AWG3krQCUqCXFpI3BBHdAfP8AWw%2BDcCFnRsUn1R9A1cD%2BKG1JWzlXgSyR5JxJNH%2BRB3gqxRMNoSMocBahfUr2zzW4PZbRtAcUZYZb1DMvFzOEpOu0qkTMxKzUyw%2FUnS2w4tllTgZ1WNlr06U3sLkXMYj0L67LKFDVH0awzwkZm4Tm5qdw9l9l%2FTJmekJmlvPezTz95aYRoeAStBAUU7BQsU3uItS%2BB7GQACcusAK0ABs%2Bz0z1SBa%2B6N4D58JYfC7BCoqeLvn%2B1qj6MS%2FBnUUJQX8isFuPaEpdcbxi%2BgLUBYqCehOm535xVc4NqmQh2TyQwdLTLaT0a1YtecQhwAhCigtdcA7kE72gOAMvMJO41x1QMFCqS9NViGpy9MTOTAUWpcurCOkXpBOlJIJsL2izVemO0yrzdOdfafXKTDsup1o3Q4UKUgqSe4lNxH0NoXCBmhhmsUzEVEwHgCSq1Hm256UmkVt49G%2BhQUlYSWyNlC9jt2RRmOCzGNSn56pVPKjAUzMz8yubdWjEcw2NayVLskN2AJJNuzstAfO7xdY5m0XOkMrT0rm5DCC6fRHfy%2BDHFLKUBWTmX6lAaQVYkmNwDte6OYFxfzxBPBTizo3bZQYIbW6nSCnE8xpAPO4De8Bg%2FARLLEw48NtWJZcG%2FaBIPbeu0evjgR0eZVFTpItQh8Pu6435klkLjDLrEUvO1um4YoNFp6XnZeQpEy7NuzU24kN9I864BYIRcAAb6jGiOOaYadzTpcuhd1y1DbS4n7kqdWofJaA50kf64Sf%2BctfxxHcCtADiCQrUFJsDufNHEEn%2FAFwlP85Z%2FwB4mO6HGw%2B66Gmik6hq36pO24jLY%2FGT5lLf4ER5ZeLVyCGQdtNvktEErbI6EIAU2q17879setbIDpStspUy5bVfnccxHn6NPT7I63f%2FADxtufNL0y7KXE7nkbmx3EUajJMOkomEJUFDmBuPPHplNAUpRbIsN1eaPW4y24xrQ5YgdUq7%2FPE5qzTk1vXqfMSqkqA6hN0m1wfmiwvpUgXWkalAjY7RsqelunJS4tJCR1ge%2BMPrtDclVpVLt60qNyjuPb8EM1qZYZMNhBWtG9xe%2Fd3xbHGWUrWlzZKusLHaLvM%2BUoWKEkkkFPKLNOMKUsqIsFAgm2x9EUZXgxE3%2BgHFgf2vYd8Yq2EJCSo23jJ6spQpLza1nqNCx7rEbeiMaaHSaUW6tx%2FNFatbNRPE1LiF0JrE%2BkhJCZ9pRv6YV8JTiWaaACR06huTf0eqPLislNZq57phuPTicg4qmNPLptvUI1J1s8amwsG1Gn0VSKm9QmqmthktqlpuaeSy4COZ6NSVAjsIMYzXsVtB5TkjKVBlKyVFlVTccbQdtk6he3pi40xRFNdX22tGI15I1nTtziEpkYpUp0qflpnQRulE4oG%2Ffe0SrxAt4KGidSDyAnFG3yRY2wpS7R7G0pA3EBcF1w6dNp29rbzivmiMtXRLkuOMT7hB2CagoXHcerFpfVc8oghyAyTG9eqdCqLMvRKlMCXmZNt4oeWl0ArFyLlIMWybBfsv3yk6lRRxuormqYrsNOa9dz8wj19Hv%2B5H5IDxMS6lKsI7w8HTkFJVOuTOfeMmm2aBhMOJpq5hNmnJ1KdTkwb7aGUAm%2F3RHdHJ2UuWVfzVx3R8C4ZZ11KrPiXZJ8lsc1uq%2FYoQFKPojvXjPzAw9w%2FZLYe4XstnA2uakG01BSTZaacCSdZ%2B7mHQVK%2FYjzwFpwlS8L%2BEF4h8ZVLGtWq8pg%2FBtMZZoEjIupbdfbcfLZeUpQISSR0h231JHZF34PcXUTCGY2Y3BDjKoe2DDwqFTZw05NJCfHGxdM9JEcgpxs9KkD36F2jXngtamfq%2FYipTrh6Odwo8sI%2B6LMy0on4AqOZsW46rjebdTx%2FQKiZGsS2I3qvITbZsWJhEypaFeccgR2gkQE%2FEbkvUci8061lzOF56Vk1JmaTOOD%2Braa71pd6%2FadPUV3KQqNROIPwiPqHxGYdpPGdwrUHP%2FA9KSrFeGJV6amJJg6nNCTep0%2B3O7ah07Q7U3tzj5kVBgJUVtm6Vbg94PIwFqWCDyidtAPOIqRY7xO2AIDoLg%2Fy8yRzDx5P0bOfFCqcx7DzrkhJFpYE6sSziitt5JAS6zpDiUHy7EC8aXxTTqFTMQT0hhavmu0Zl4pkamZVcsqba7FqaX1m1d6T3RvzgTyxwDm%2Fm9NYSzJw%2BmsUZnD1RnhLl1bel9pq7awpBBBG9vPGgnJYJNumWvzqSb%2FDtAeBtsHnG8%2BGHN6nZN1vFDVbwVP4opuNsMzGGpqTps0GJtLTqwpSkEg3ukFPeLgiNONy7SGVOukHQL6QkknzAR3bOTdM4H8D4YoOAMHyuJc6sZ0tNZqFQmZEzZosotIKENNgE3383IkwFpwXxKYXySoFFpUvw%2FwCZNGw9hWsuYlwuudqXQnx91ktutzq9AS9LnygB1hy9PGeManMV%2FE1Sr82w01MVSbenXUNJ0oC3VlatIGwF1Gwjq2mcbfFZRJ5ycx1LzOM6HMBRqWH67hw%2BKTLNuukK0e59UmxNx3iMW4t8n8vaFKYLz1yYQ7L5dZpSS52SkXLn2InkWL0qDudNybA8ilQuRaA5fW0AY2HlfgvJvEtJmpnMbOv2kzzcz0LMougzE6l9gpB6QONbA3uCk2It54woyyVcnUR0Pwd5SZeZpqzXlMe0g1EYfwLM1alLRMLZMvOo1e6pKSLkADY3G8BzZV5eSlKpNylNqTdQlGH3G2JtptSETDYUQlxKVWUkKFjY7i9o8oAtyistvtinpEBkWXYSrG%2BHULHVVWqcD%2BNNGOgfCOG%2FFzjEH3rcon1SzcaEyzSDmBhdOoC9epoueX9VNxvfwjir8XGMz55ceqXbgOXlxAAxMYikCA6R4csmMi8ycqsx8Q5i5npw%2FXaBTm5iVZMq6pVPHToSmaskWmW13KFITdSL3tHPM5KJlJt6XRMNzCG3FJQ81fQ4m%2ByhfcAixsdxfeOjeHLKnAWOsis8cZ4rpr71ZwNRpacok0zMqaVLLcJ17DZQNhsdrAxz2tm%2FbeA8rbVzaOjMgs2MA4byvxtknmPl3ivE9NxtUqfUj7XJptqaaMsmyU2WCd1b3AjSmGMNTmJsQUrDNL68%2FWZ1mnyybX90dWEg%2BgXufRHcOY2Y1H4LptOR%2FD5hqQncZU%2BXbOKcXTNPM5M%2BMqAPRoFiEADv28xgLFMcWuH8C4GThZGVWOqbWqfhOdwDRUVeZSimP0qYcKkvzUubBU0hJKSQCFG%2FYY4lqEuG3FoRsE%2BSnzDlHYmF%2BODGdUnW8L8UtCpmYuXlYeRKVX2Ro3QTcg04oJ6dl0ADqXvbZVhsbxqjityJkMhM2JvCNLqqqhh%2BelmavQJx1V3HJB8EtpWffKTYpJ7bA9sBoMo35RtTC%2BW2TdfwS1WavxC0fD1fcYcU7RahRZtSmXklQSguoBSpKgEkKH3Ua6XKpK79KjT2bx0JlVlHgDGHB9m1mjWJF9WJsJ12RkqRNtzCkJabcS2VoUjksKJUN999jtAczOBdvdNle%2Bsb79ov2xCKjgIinASWPdCxieFjABziqkRKALxVSmAqtdkesD3MR5mxHrtZAgMopqr0xsfsTGQ5WqtiiacJOlFMqSlEcwPFHIx6kDVT0D9iYyHKn%2ByCrufqdBqqv%2FCuQGsMFTU1K1CWVJzLjDim0o1oNjYjeNp8MQJ4p8vRv1ccUocrf8sajU%2BEiUT8qu1ykINo23wyf%2FVTl%2F8A%2Fe9KP%2FjWoD9B0IQgEIQgEIQgEIQgEIQgPz%2F8diyridzJSSDpxFO8v28c9q8ptfnEb%2B45CFcTuZpA%2FwCcs%2BD%2BEMaAPvPggNgUfyf3KY9l%2FPHhpiltoWpDXSaEpJR2qAVuB57cvPG3c2coqVheh03MrLWuuYpwDWujZl6ihnS%2FKTZsDKTLYvod13A74DV2o3tEwPfGd4vyJzawNV6DhzEGCJwVjE6%2BipMnLlLypl%2FbUyCkkBxNwVJPkjc8oyCdyfwrJZo4GyZlcWpruJalUWZHFi5KxkKa8p1JMoy7%2FbXEoSvWrkDsIDZnDhwjox9QZfMbM6Zmafh%2BbAdptOaPRvzrQP25xX9rbNtgNyN%2BUbqmcw%2BEXKKXnsISkpQZRuoM%2BJVFmVZU%2BZlq4Oh5W5WL72MeLjrzMnMsctJbD2FHFSLtVdVIy6mTp6CWbSBZHd1bAR866ZNTk80pZn1tqUr3qBue8k9sB35W%2BHfh%2Bz5oMxWsnanIUiqJF21SLl5crtsl1o7oB7xHFOKsM1rBuIqlhbEUkuTqdKfVLzLK%2BxQ5Ed6SLEHtBi45OZnYhymzQoFap1QcWxMVBiSqLJSAmYl3VpQQbbEgqBB80dMeENwnJM1jBWYMqy227W5Waps0pIsXFy9lIUrzhKiB5hAceXN7XjY%2BU%2BeeLcnxNStIl5apUmdc6eYkJokBLtrdI2oboVYAHsNhGuoRp3%2FD7ridhVdr3RFdE64leztKrKrdUTlLqJvjqrqAE%2FU%2BkwO39GE39aYfX3Yi19bLyQKf2Mzv%2FFjl2Eee4DYB4v8Aaq2tjft4iMprns2OoVcd%2BJf7Xl3Th%2B2mb%2FyYrp47sQ6d8upAnv8AGR80crxPE8BsB5LCOtVtN%2B3jnz2bHUqeOvEFhfLunC3%2FAEj%2BjEDx14hB6mXcgBfsmRv%2FAAY5bitIyU3U5%2BUpdPl1Pzc9MNSsu0jm464oJQkelRAis6DYDy3eOmrajftvz57NjqH6%2B%2Bv%2FAODuU%2FGh9GJTx3Yg99lxJ2%2FzofRi2I4La0Ku5gU5rYVcx43IGoqw80tS19EDb7YBbntfzjsjniflJiRmpmnzbZbflXlsOoPNK0KKVD4CDDgNgHi8dNXtG%2Fbxz5dNDjxr4%2F8A49lE%2BiZH50xD6%2B%2BvoI04AlVADmuZTcn4E8o5c0HviFzExoNgHi8darab9vHPn%2BvQ6m%2Bvwr2kWy8lArtJmhv%2FAAYlTx44mB3wBJn98j6McuBQ74jcd8J0HwCJ%2BT%2Faq9pbf15589mx1QePDEhG2X0iP3wD%2FJib6%2B%2BvFN1Zfyt%2FNMp%2BjHKsLiJjQfAfF461XtIm%2FXjlrnsdSo48a%2BFe6ZfSpFuQmRz%2BLyic8eVd19XL2V0%2BeaF%2F4scrw8lCne6I4D4B4vHWr9pMX688lc9mx1V9fhiA%2FwD8eS%2F42n6MRRx44ht1svZQHzTQt%2FFjx1jhZypwvW6Jg3FnENKUrEtdk5ealZKYpykhfTpHRWN%2FfKuBe140xiPKXG1AzPquUQo0zU8Q0l5TSmZBpTvTN6QpLybDyCkjc9u0TGg2A8lh9qr2kTfrxy1z2bG8%2Fr7sQ%2F4PZL8aH0YfX34h%2FwAHkl%2BND6Mc6YnwJjTBEwzJ4zwtU6HMTABaTOsqbDgPalR2PwRvzFnDRkfl5W28MY%2B4kGaPVjJy887LOUlaiGXhdKk2O4Iv59oidBsC8BHTVtVm%2BW8%2FTn%2BvQ9quPLEawUry7kwDz%2FRYP8mJE8d%2BIe3Lunn99f0Y54oeEK1jLEz2F8CSEzXJlappyTbZbs5MSrOpRe0ndI6NOog8r2ixAhTfSJBKR2CLcBsB8BHWq9pMX23589mx1QeO7EBKQnLingdv6Kv%2FACYnVx3Vwt2TlzT0r71TW38WLHhfhQw64vDuG8dZ3UGk4yxZLKm6XRZNHjdkBN%2BjW4k26S3MDuIF7RjeDuFvFuJs0MX5dVWuSNHl8Ao6WvVZaSthtBTrbCE8ypaOtbsAN4cCMBni3vHTVtJv14j6c9mxnw47q7zOW0gfROf0YlPHnXOX1NKf%2BOH6MYlXOHCiyGHsGZjYQzEZxLgPEtelaDP1hmULa6a4%2B70SXFNnmnX1Tysbd8enEnCu7QuJmg5CM4kcdkK1JpqYq65Wy2pVDbin1Fu9rpU3p5%2B%2BEV4C4DHH7xHTVtRv%2B8c%2Bf69DJfr765%2Fg0kPx0%2FRiZzjvrgFmsuJIHvVN7fxYxPFfC%2BrDHELgfJxivzE1TsaNtzLdRVL2cYYSFmZVo5Et6O%2FfUI1tnLgulZb5nV%2FAVFrTlWl6HMJlFTbjQbUt3o0qWCkEjqlWnn2Q4D4F4COmratv68c%2BezY3mOPHEIFjlzT9XeJs2%2FixAceuIOSsuqf%2BMn6McpknXzgom%2FOHAbAvAR01bTf14589mx1aePfEOq6MuqalPnmjf%2BLEF8fWIT5GXMkPTO%2F0Y5R1HvgVbc4cBsB8X%2B1V7Rv68c%2BezY6vTx94hsQrLqSvbY%2BOdvxYgnj5xF0l1ZeyBRbl4zv%2FABY5NJN4iCbRHAbAfF%2FtV%2B0b%2BvHPns2OsnOPqvKQOiy4kEq7Sqa5%2BpMPr%2BsR3snLqn37%2FGzb%2BLHJ1zFzw7RKjiWt07DdHlw%2FUatNsyMm2pWkLfdWEoBPYLnc90TwGwHwEdar2jf14589mx1A1x8YsSPdMvaZ%2B5mj%2BdMQHH5ijXvl5Tykqv8A1XYgd3kx4PrK5eZxZVcsKNnlQKjmBSKZ7IzGH0yTyAEkJIHTEabHWmx%2FZpva8cwk9fQpBbUhSkuIv5KkkpI9YMI0IwGPq8darab%2BvHPns2Orhx9YkKv%2BLqQA7jO3v%2FBib6%2FfEihvlrTT%2B%2FvnTHKGsfcmGtPcYtwKwHxf7VW039eOfPZsdYfX64gAv9Tan3%2Fzz%2BjEv1%2FOItW%2BW9M0%2FwCdm%2F8AFjlHpB3H1xKVgnkYcCMCn9xHTVtRN%2BvHPns2OqZjj3rrjgWzlvJIWn7ucuD6LJjEsyuMXHmP8MzuFafRJLD0rUmVS84%2FLuqcmHGVeU2hRsEAjYnnYxoJUQuIz2eiGC2NpTa02EZ06s5mdXkmckTeraYymqcpOzqdVI8nzDui%2BYQxjX8C4hksV4XnvFKnILu2vmlaDsttaeSkKGxHo7osSohHftbGzt7ObK1piaZ4pidUwwU1TTOcOqJTjyxY1Lobey%2BpxesNbjc6pKSrtskg2Eeo8fOKSbnLuQI%2Fzv8AoxygkxNHl40HwDPOLvEemra2IvtvGquXVp4%2BMSk%2F8XEhbvM3%2FRiVzj4xGfteXcgn0zhP8mOVIRPAfAvAR01e0nf14589mx1Yrj2xEdWnLunJvsn9Fk%2FyYN8e2IgrrZdyNu9M2foxyqOUZblbl1iDNjGkrgTDK5NqcmWXptb84%2BGWZeXZTrddWo8glIvEcB8C8Xjpq2m%2Frxz57Njf6OPfFgVf2hU%2FT2Wm1A%2FxYnVx94oOycASCT3qmyfyJvGqc%2BcjZnIeoUGRm8Ty2IPZ%2BRXPMLlGFItZ0NhAB3UVEixHO8Z61wW1RVWlMDTeaWHZXMOoUcVqWwo6hwPKaIN0Fy2kKBSoHzpPZF%2BBGAx9Xjpq2o35b8%2BexeDx%2B4pKd8vpAq884bfxYkRx74oT5eAaer0TZH8mOYKhJzVNm5inz8q5LTUo84w%2By4LKbcQopWk%2BcEGPNcQ4D4BVru8darajflvz57Njqn6%2FnE3%2BD2S%2FHf6EPr%2BcS%2F4PZL8d%2FoxypriGuK8BsBjVd%2FtVbU78t%2BfPZsdWfX84l7MvZP8AHf6MTK498Tq%2B15eSifTOX%2FkxykF7xU1xPAjAvF%2FtVe0b8vHJXPZsdUOceWKwepgSQI802q%2F8WIfX6Yov%2FYBK%2Fjh%2BaOWdcNd4RoRgHi8dNW1G%2FLzz57NjqlPHrioXvgOTN%2BX6MO38GI%2FX6YtR1k4AkD6Z5X0YwjL7IjL6q5OSmc%2BZmbSMI0ydrMzRmAqRLyOlaNgCoHylWUQLchFhzuySTlV7Vq1h%2FFbOLML41k1TNDqsqyUqmHEW1taN7mygUkc9xzEUnQbAPAR1qtpvy8c%2BezY2t9fxivT%2FAGASF%2F8APj9GJTx74r%2FwfyH48r6MaJr2TmamFaEjE2JcucQU2lLbS4ZqYk1JQhKuRV2p%2BGNkYKyEy2qWSlBzizGzdGEpOvVOcpsulciXUdIypSQgEG5WoIUrlawiY0IwHku8darab8vHPns2Mvc4%2BcTgNhnL2TJsekK55XPstZMEce%2BJdHXwBK6vNPG38WOfszKDgvDOK%2FYjLnG5xfSPF2FCo%2BKljVMLvqaCTz0nSL9pMW%2FGGEsSYAxNOYNxjSXaZWpANmZk3tlthaAtN%2FSlQPwxadCMBn6vHTVtN%2B3iPpz2bHRw49sWg3TgSSt3CeVf%2BLE%2F1%2FGK1JKVYClbnkTPKNv4Ma1yryVwjinL%2Bo5q5i5sUrBWHZGaVItpcSHpp9xJSkrDQNwjUoJG29j2CLvmTwuYrwdmNgnAGGaxJ4gRmGha6JPAdGkhAC3C53JS2Q5qGxB74RoTgMfuPtVbUxfbxzvVsZqjj2xWkf2ByY85nlfRiK%2BPTEytOnAcok%2B%2BAn1fNFurXCHRZuWxpQ8uM25HEmNcBynjNWoSpRTP9r16ULPvjYgdmrY2JjCsy8h6dhHIrL%2FOrB%2BIJuut41XKsOSz0uGxLPzDaujbSQST7qhbZv3Xi0aE4FP7jtq2m%2FbfnerY2L9fvie9zl%2FLek1FX0YlTx8YjH2zAUqfRPr%2BaMd4k%2BFVGQ2XFPx1I4km626KkzTqtLrlw23LuOMkpKCCSR0yS3v3gxjfETkTSsjFYQp7WJZipVXENNdqM6wtgIRKpT0YASb3N1LUnf7kmMdWg2Aa97x01bUb9vHPns2Nhr4%2BcT6rN5fSum%2FbUVXt8WJhx74i0K1YBl9XvbT6rfxY5YKQO2JYpwGwHlu%2F2qvaTv28%2BEns2OplcemIykWwBLFXb%2BmCrfkgrj2xJcJRl5LWsLk1FXPt7I5XJtBK94tGguAeL%2Faq2k328%2BEns2OqEceOJua8AS%2FwVBXzQPHticLWU4Algn3t6gokenqxy10kQi8aEYDH1eOtVtU35eInPdz2bHU54%2BcVE2TgGUSPPPqv%2FFiY8euJP1gyp9FRV9GOVo2Bkzk7iDOzEU5QcPzUhINUyU8fqE7PvBtqXl%2BkDYO%2B6lFRAAEOBGA%2BLx1qvaXi%2B3nnz2bG8Bx7Yq6MJRgeVbsRuqfUbj4sRTx8YoCvdMAsFNvez5vf4safzkySreUuYVNyzRPM16o1KVlX5QyjSkl1yYcU2hkJVvqCk8%2FPGdVzhNp1AdmcLVHPfBctjynyTc5NYdm3%2BgCVLTqDIfUdJXYj4SOV7xWNB8C5LCOmrab9vHPns2MhPH3ii9jl5L%2F6wP0YmVx619ROnL9hItteoG4PxeUcp2Lbi21hSVJUUqB7CNjEsTVoPgPLd46atqsX288%2BezY6s%2Bv1xIP%2BYMt%2FrA%2FRh9fzibsy%2Bl%2Fx8%2FRjlMG0TBQ88ROhGA1fV46atq2%2Fbxz57Njqpzj3xKlIcXl%2FLWN9hUFX9WmLZW%2BOvHU%2FTHpWg4SkKXOupUlE28%2BX%2BhJGy0osAVDsvtHM6iFGIRajQfAbOqK97xMx5atvYiq%2B3iYmma5mJ834Qrz81MVCdenJyZdmH5hxTzzzhupxxRJUonvJJMQk35mTmmpmUmHJd9hxLzLzarKbWk3SoHsIIBihEwURHqaqKJp3ExxasmvE5TnDpyiccuMpKUbZr2CpCoziftk0xMqY6bbcqRYgEm5Nu%2BLkePjEh3GXUqPMJ9V%2F4scp9IYdIY8tXoRgFXHveIz701R6pbG%2FLxH05dV%2FX9Ynt%2Fxeyv4%2Br6MRHH1ibR%2FxdypVbtn1EX%2BLHKOsxHWYngTgVMfEfaq2p37eefPZsdWjj7xPq62XUlp806b%2FAMWJTx84l1dXLmUt3ePH6McqazHqpElOVmrSNEpzQdnKlMtSUqgqsFvOLCEC%2FZdRAvFZ0IwCdd3%2B1VtN%2B3nnz2bHUyePnEqQbZeSoOnY%2BP8AI%2FFgnj9xRffL2Ut5p8%2FRjAs3eFbEmTuXsvjjEGL6PUJg1ZukzEjTiXUMuKC9Z6byVaVIKTbtj0YT4ZafNYHwpjXMjNak4KGO5tMrh2TmJRyYcmwsgNqJR5JWTsDyFrneK8B8A8XjrVbU79vEfTns2M2%2Bv8xMTvl3Jkdxnv6MF8fmJveZdyg9M7%2FRjQmbmV%2BIcmsf1TLzE6mXJ2nJafbflzdqYl3U6m3E9ouAQQdwQYw6474tGhOBclh9qrajflvzp7Njqg8fuJgLDLyTJ%2Fz7%2BjEPr%2FMU9mX0l%2BPf0Y5RV5cIngTgXgPtVbTflvz57Njq36%2FrFJ54BkRv2zx%2BjEy%2BPrE502wDIm3lfo0j%2BTHKAPbE2uHAnAvAfaq2m%2FLxyVz2bHWH1%2F2IA2R9TyU19n6ONv4sSDj%2BxR%2Fg%2Bkh%2B1niP5McpBcQVuYcCcCj9x9qrab8vHLXPZsdZL4%2FcVG3QZfSydvf1Am%2FqTFZHH3iXrdJl9LfsbT5%2BXqxq7IrJLDGZuF8cYvxjjs4XpWCUybkxMmW6ZPRPhRLitxYJ0gfuor5t5CUHBuXUlm5ltmZJY3wi5UfYWoTTTfROSU5vp2v1kkjT2EEjsN4jgVgXgI6atqsXy3509mxsc8fmLQDbAMke79HqH8mKQ4%2B8ZE3VgGRtbkJ9XP4saJZyXzamMMnGctljiZ2ihBdVNpkV2CALlWnna297Rl2SOSuEMycDYyzGxzmKcKULB8xKS8xMol%2BmT7ukkLXvsAdKfTDgTgc%2FuO2raTfLfnT2bGyRx74tVucv5b%2FWBt%2FFib6%2FrFvbgCV%2F1kr5o0zm7hDKPCXsOvK%2FNj26CaS%2BakkSZY8TCbdGrUdjquRbmLRidfwliXCzNHmcRUCakGsQU9NVpbjqerNyiiQHUHtFxy5jbvhwIwLlu%2F2qtq0X23509mx0cePvGRPVy%2FkiPPUF%2FNFRPHzii3umXcqT3ipK%2BjGncmMoWc2JiszdWxzSMI0DDzaHKhUagsayVBSg203cFatKFKJ5C3njJc2%2BHaVwZgDDua2XWN2ca4VxJUGabKvMy6mng68VJZ6p8rU4hSNtwoC8OBOBR%2B4%2B1V7Rv23509mxnY4%2BMVDlgKT%2BCfV9GJ1cfOJylIby%2BYv768%2Bq38WKcrwX0VGIqfllWc56ZT8xqnSjVpehqk1qaDYBulTo7bgg%2BZKjYgRhaOHpk8PGKc3ZuuPyuJsE1WapVcoPRJU1KuS0wlt%2B7oO46NaXAbWIMTwIwKddh9qrab%2BvEaq%2FVsZsjj2xT7%2FL%2BW%2BCoL%2BjE54%2BMTg6vaDLf6wXf8kWGb4TvFuGj6t6sQzgrjVEbxC9SOgBbTKF0BQCr6tQZIXytzEYhiXI%2Bl4c4bcL53z2JJg1bFU40zKUroB0ZZWp09JrvfZtsK5e%2BivAnAvAfaq9o33bz9P1bGzVcf2JjzwEx%2FrBXzRSHH1ijtwDLn%2FvFY%2FNHK0ScocCcC8B9qraiL1b8%2FsjY6rPHxixQsMAMJPf7IrP5omTx74lB6%2BAGzt2VNfP1Ryr0kIcCcC8B9qr2kb7t%2BfPZsdVJ49sUk2GX0vbz1Rd%2FwAkVV8euI0iycANpX3ipqKfyRylcd8R6Ta%2FZExoPgU67D7VXtJi928%2FS9Wx1R9f1ia%2F%2FF8x%2FrNX0Ym%2Bv4xRq%2F4vmtP%2FAGmb%2FwAWOV7o0%2BeMxykysxHnNjWWwJhZLCJt5Kph6YmF6GpaWQRrdUfNcWHMkgQnQbAPAfaq2k328T9P1bG9%2Fr%2BsVf2vATPo9kj9GKiePvFnbgFk%2FwDeJ%2BjGD484YZegZf17MTLvNCi45kMITypHETUglTa5FSSAogHytJUCodxuItnD%2FwANWJs%2FVViZka21QqVS1tSyKjMMKdbfmlG6mUhO90o6xPZcDtiY0JwONVh9qraU368R9P1bGyhx84oBucv2QO4VE%2FnTEq%2FCAYqA9zy8Y1X99USdvi845cnGFyk3MSa1hSpd91hRTyJQspJ%2BSPMpRBiOBWB%2BA%2B1VtJvl4n6XqdXfZAMS2UDl63c8j7I8v4MSnwgOJhbo8BMDsN5%2B%2FwDJjlGJTbvi0aE4DH7j7VW0i92%2FO9Wx1srj%2FrRCP%2Fh01ffXpnhb4Lpi31bj6xa7LuJpuApVmZULNuvzpUlHnIA37I5auO%2BIK3sTFqdC8ConOLvHTVtN%2B3jn%2BrYu%2BJcSVzF9anMS4kn1ztTqDpemX1ciTySkdiQNgIs8R6f3kSLMempopopimmMohrJr%2BeN%2FZUcW9ay%2FwtKYQxPh97EUvS0dDTptmYS1MNy48llzVssJ3CVc7bGOfbnvi60RpbrzikshwIbKlX5AXHzxzsXwO4Y7ZRY3%2Bz3UROca4mJ8kxxstjb2lhOdnOWbq5%2Fjrw480W5jLWtWVuNNQYvf02iGGuMKk4ixRRcOMZf1KXNYqLFP8YeqDWlkurCQsi29iRtHNyJZgo1mWaKVfsORjz15LEvTKc5JlxifbnVzHjCbJKSkJLSk27UqF%2FVHlrz7nWCzZVRY2cxVlOUzVVxTyTr9bfs8Tt6ZiKquL0OwOLfKmv5o4Gp6cLtGYqWHqiqcTIg2VNtKaLTiUX21pNlAdojh6Zywx3IPql57B1cYcSSCFSK%2Bz4I6xwzxo4emaUycbYdqqaylCUzSpBCVy77gACnRqIKdRudPYSYvJ40Mt9ZSMN4lItsQy3ufjR5DBbbS3Ru7zcaLnu6YmcvTrymM84meP09G%2FeKrhe6%2Ffa6spcYKy8xknY4UrBPcJNd%2FyRRVl5jUHfCFb35foJzf5I7XHG3lkkJCsOYjUvvDDf5QqPU3xw5VIAExg7Eal%2FddEnf1Kjs06TaW%2FwCHx0zsa1Vhh3hJ7HDXtBxmfJwlWj6JJz5o27wwZIY9qObFCxTUsOVKk0nDc0KpMTc4wppK1NpVoaRfcqUpQ5R0WOOPKZW4wdiK3maSf5UU5jjdyqU3qThjFC1JHVaLKRf90VWEa%2BI4xpZiNztLpNx3MVxNMzGc5RPFPJEal7vGH3e2ptoqmcuPLy%2Bhec7c%2FwBjJyqUanzlCnao5V5V2aCmJlLfRJQ4EWUDvuTtbujW6eOKmI5YCrJ%2Ff7YjRmcGZ9Tzdxm%2FiuoySZFpKBKSEmlWrxeVSSUpJ5FZJKlEdp80YhTZVtyeaQBqSbhQjcwn3NMKi5WfdKyztsv0v0p1zx5cU5cWprW%2BKW9VpM2dUxDqRPHFSLJvl%2FWgTz%2FRze0TO8c9FZCnBl1XHNPJCag1uI56MjLe9YB089ot1ZlGWJYuoSE6FJSTbzmOjPucaOzGUWP2qtqtOK3qmc93PZsd0Zu0OpZ48PbtOoarTVfpcpV5OXfd2U6FIebZKjsDYKTfvj591TLfHFCnXafVcIVmUmGVaFtuSa7g%2BkCx%2BCOj8kOKenYFwdLYIx3SKhPM0m7dMnJPStYlybhlxKiL6SVBJHYd%2BUbJ%2BvQylKbroGKCBsB4qk%2Fyo8lhFnpNohXbXO7XT32ymqZieiM4mM9cRGcTGeboXi1uV9im0rqynJwscL14K69FqI9MqsfmiKsIYlSNSqHUgO%2FxVfzR3IONXJxIKXML4iASNgJJs7effaPYONvJVLY6TCuJHNRsLSiefm60d7hTpPEfNvbPstPe2Ha%2FfZ7NrhBvBuKHSEtYeqzl%2BxMm4fzRleW%2BRuYmPMVU2kSGGKnLMqmmVzM7NSq2mJZhLiStalKA5JB25mOyGuNvJRRs1hbEiACAbSqe34YgrjaycOoCj4kSjl1pa%2B%2FfbVGtetItLbexqs7PD4pmYmM%2F0py9GUMlnZYdRVExaTOXfbBzezUVlVg%2BZxtOS85UJaXnJeSbl2Jno3F9IrSkgqNtgLkRpEcdGG9Z6TAmIFW7RNN7%2BsxrPiJ4iWc42qfhzD1Kep2Hae4Zr9E26ecmbWC1JFwhKRfSOe5JjTEmywuba1jWlSusmNfRn3NbjVh1NeMWX62ZmdcxMRyROXLy%2Bla94za%2B%2BZ2FXE6z%2Bvmw0o%2F2CYhSO8TbJiZXHVh1oEs4DxE4oC1zPMpPrvHN%2FsbKe8lkD9zHjqMkw1LOFMsgHvSneO9%2F400f5LKetO1rd175P05%2Fr0O%2FZuaGe%2BQj7cm%2BuSZxvh90MpmHCsSy3kkIDhHPStIBI88fOPEOV%2BPcJ1J2j4hwhVZKblzoWDLKUhRG2pCwLKSeYI5gx0Tw98T1Ky2w6cE48p069TJRS3aVOyKQt1oLVrWw4i%2B6dRUUqHK5B7I239elkmpJQ5T6%2BtPIA064%2BU7R5PB7tpBoZeLxdrrdZtLKqqZpyzyy5JziJ48somJ73T0Le1ul9opqta%2F0sv8A7cDKoVWb6zlKnRbvl1%2FNFM0Sq%2FbDTZ2x7pdfzR3yeMvIJR93o1bBA5qpqTaPQzxm8PnRgPUWtqaVyV7HoAPwR6HhZpJEfNs5%2BefZaU2Fw5LWeiNr5%2FKodUUnq02f%2FF1fNFxoeWmN8WTyKLQcK1WcnJodG0hMqtKdR5FSiLJHeTHev15PDoo6WKVWb8h%2Blg3iZnjQyGKdLcviBjpB1v0vUB8NjGK00o0promKcOy8udU9m5j1wmiwuGubSZ6I%2FFmGIMTPZJ5Py9RqHjM8nClJkJB5qTesXVoCGiGyTYgEn4BGovr5cHa%2F7DsTKHf0jfy7xr%2FiN4lqXmtQZXBOC5Cfk6KicROT782gIcnFtg9E2Eg3ShJJUb8zbujno90c%2FRr3O7vernNvjdnPvtVUzrymI4teXLM5z5ma94taxazFhXxOyE8ceBym68J4nCr3IC2%2FpRKjjjwSTqcwdigFPKz7e%2F8AC2jmz2IpyW0JcYbuEgnq%2BYR536fIhCujlkeSfex3v%2FGmj%2Fg56ZYKcYvccc1PoZlPmpT81MFt4xoqalJSszMOywam1%2B7tKZXpcvpJ77x84Mwso8cYBxRVaPWcOz5bZnHixNtS6lsTLSnCUOoWBYhQIMbd4beIynZQSs9hbGUlNzNAnpnx%2BXmZNGt6RmiAld0e%2FbWACbbgi%2FfG%2FE8ZeQ52cTWlJSdh7GLA9NuUeTw%2B443oXid4s8Puk2ljVqyzyyiZmnjjPjiJynPvZty1vF1v9lT7%2FVlMdnfjJ8%2FXKDV2kJccpc6lC76FGXXZVudjbeKKqFWLFQpM%2BR5pdZ27%2BUfQYcXnDg22hDkrPtoQSUJVSjZJJubC3fvHpY4xeHNIKlN1JItpOmmG1u7lHoI0r0knXhk9NXstTe2Hx%2B9noja%2BdooNcXsijz6vRLrP5ors4MxTNvJl5TDNXfeWQkNtyiyon1R9ERxhcNwJDcpUiQLkCmHl6omRxm8PZutpysskctNOWCfUIpXpXpP9HDe2qf8AgvF2w%2FXFrM%2BiNr25PUrEeUvDnSJXE8lMtzeG6JM1KakGVnpEoBU70Q3sF6eY7zGAI458BBGpOF8VdYA2UhNx5j1osGfXFzhrGOCZ3AWWclUAmsJLFSqE40WbSxtraaTe5K7AFRtYX745Vjn6OaBxilNtftILOYtLSuZiI4so5c48%2BrPjyXveLVU1xTdp4ojJ2WeOnAhFzhfEpPcWW%2FnjS%2BfXEc%2FnBIyuGaRRJmlUKTmRNrTMOBTs2%2BAQlSgnZKUgmw33JMaZiCo9ph2hODYTeKb1YWc7unVnOeU99z7e%2FwBvb07muriSWT2Q0mIad4AKHbHrGkiEmJgLwAvE0AiSJ4kgJ4gQTBO8Rse6AhpgExGEAN%2B6IggG5MBcnntECBpvaAvtOxpi6lUKpYXo2La1TqPV1odnpKSm1MtPuJFkrITuFWAFwRewve0b0zY4zMT5qZMYdywXTKnTKrTnpNdZq7dRV%2BmKJRsoa0aSFpKlaVrv2p7bxoiiS7T8otbqUqJdAB7vN8MXJUhLp5sJ9UB48UYtxRjSooq%2BLsRVCszzMs1JNTE8%2BXXEMN30NgnsFz5zfe8WI84uVXbDVQblWEpu%2FwBGgWGwKlAX%2BW8b6XwX14NJcbzxyoeUo2KU1wDSfSRvAc5wjogcGNfJUhWdmVOtJsUivC4%2BSJRwXYlGrVnNlWrSdKrYhGx7uUBqzJxCXc4MANKIAViqmDf%2FADhB%2FNGU8V4%2F%2BZ3NW%2FP20zf5Exs%2FAHCbWcLY%2BwtiafzcywfYpNakqg%2B0zXUlbrbTqVqCQQNyBtvzjUvEzVqdXeIzMytUmaamZKdxLNuMPNKCkOIFk6kkcxsd4DV0SRUX5oaRbrFMB53BflFum5Rt9tSHB5XVPw7Rdi3FBxqA1fPUSoScwphyXWq24UlNwRFDxGZ7WHfiGNrIY3vFJ9p37uA1YZV4c2nPimJSw7f7Wv1RspxBHlpB%2BWPDOaW%2FKCB8AgMB6F37k%2BqJmpaZeVpZYW4R2JTGSzk2w32oPwCKFJqV6gptCyOlacbVp27Lj5RAWHxWYG%2FQqiHRujYojIek19RxStMUJphtJGmAs4adVbS2o322BMTGWfG5ZcH7gx1PwkVLLf2v4iomOF0Rqdbn2JinrqVkqKFtlLgQo8rFKSfTHRBpOU6kBZmsNKSBcfo1opHwQHzNLS0mykqHpBidLCynV0aiO%2FSY%2BjdWcyGpjfjNTmMIEj3y1ocV6k9sa%2BxXnzkfS6RN0ii0ynzhdZdZSmWpSNIKk2vqIvcX2N4DiFxoo7DEoSo7BJPwRdJsobfWhoKUjUdJO5IubXPfaKSVLQ4laDpVAeQyswEdIZZwIvbUUm3rinoX9wr1RlaKjUlyhlJmdeclVFKlNFXUJB2NorMPI%2B5R6hAYd0bn3CvVE4lphXksOH0JMbBlrLGyW%2FiiL5RGULnEIeSlSVJPVsOcBqdElOHrJlXClPMhBsPTFVqSm3DZMs4fQkxvRFPlLlIlRY8wOSvT5o89Qp8rIsIWhgJVq%2FKIClkTj3GeTE5NVzDy5UO1VtDM7JzTXSMvMpN0g9qVA7hQ7433K8c%2BaEoU6MMYbKU7AHpY50iSA6bHHpmevdWFMOA%2FtnfyQHHjmaB%2FYvhwnvId%2BeOZ4a4DptPHrmaPKwlhtW%2Fe6IHj1zJKrpwfh4Du1O%2FljmTX5oqy3ujwTaA7Jym4xsb5gZiUnBdUwfRJNioMzqlvtPuBSFMyrryPK23U2B8MYkxx9Zkvy7TysC4dRqTf7a7zIjn5qRZW6kpUW1DktKikj0EbxLNyTLcnML6Me5J1J9YgOlaTxp53VwOO0HK6k1JMtpS%2F4s1MOhBIuCrSDa4%2FJHvc4xOIVtuyslpRpf3Qk5u3qtGHcKqs1hI1FeXFXw3Jy5r7CVIqiHlK8d8UXocu0dm%2Bj1J6%2FV1EdsdGqa4tVo2xjlsk%2BdL5%2FKYDRtU40M%2B6Q0JyvZYU2Sl7pSHZqUmGkXVyF1dptHmY8IJmlLNnXg3DDgJv1lvCJuKBWdKMG1JOYFYwpPyaZ%2BltzqqW2%2BHFkpdVKqQpZ0KSnrhencFQBjUOTuMqXhmbqEjJ5VN42xjV20yeH25ohcrKOHmpbPNZJI37AIDaVW48szKmyvxPCGGZNaxZLiFOuFCu%2Bx5xztirFFcxjXZrEWJJ9ydqM4suPvL7T3AdgHICNz8XFFwvRMS4Xbp1IpVHxO5RUnFVPpNvE2pwlJBQkbJPlcuy140KveAnkloTUpErB0iaZKrc7a0x3NOSzq33EJUUjXq6nb%2F%2B44Wl06p6UT3zDQ%2FhpjvctuM3ZU3ZxsJvbfb88Xsp%2FTnzQpb8dnE%2BWfweHoVoCtlLJ3NxFPo1FSQGli%2B5uOyPeJkujTdNhsbcjEoQm%2BprUCnyrna3mjaaSk3LvpWXD9qWBqB57RXeadLNmgDtdN%2BV49rTClN3WoabC%2FpiV9rU1ZsHqjqmLZlSyzMqVyikKbBUkWUB%2BaLUJAFLri9SlK3Vq74v6pd8taVk3AIudrxRclXCnrjZYNz3mGasQwSrYeZWXHpe6VXuQRsYw6ryTqG1B5gAp7u0iNuTMgpSQBayuYP5Yxaq0kLaKnUFJCTpBHOGWa0TlxS09XVkUeaXo1aU8x3FQB%2FKIx2SQpSwEje23pjYGLqQfY2ZW23bqdbzG4jFKbJjX7oFDfUnT6YrVTxs1E8TQmL0lNerKVc%2FGWSflhiK4xdNA%2Fqw%2FipitjtJRiauaeaHmyPTEMUnVi%2BZV3uIP8ARp1a2zGpllMN6a%2F6IxKupOr1xllK3p74%2FYxjVdQLiISsLOytVto96Ftlm4TvHlSSDp0x7GigtaAmA8T4TfaPMNRVtHrmgAdo8zYVr2gLnjb%2B452uaY1yN%2FfKH5ouLbetxN%2FuR%2BSLZjhet6kC46tMaG3pVF2UCEp0qCTpFiRcXt2jtEB9GOCrLuhZAZM13ibzHY8WmKlTlrkGnAA41TUm409ocmF6QP2Nu%2BOHs1swq%2Fmxjus47xDNFc9WZpUyps3s0nkhpI7EoSAkDzeeOzKJ4TXBK8O06l4oyNfcflZNmVfYlpuXXJqU2gJBbQ4NkdUEAi4ionwi%2BSijqc4diD%2Fkqef5EBzlwk0PJ%2BpZhTozgzdrGXrUnTVP0yoU2fMgt19SwlaS%2FbYJTZXRny%2BXZGn69KyUtXajK0yrJqspLzsw2xPBoo8aZS6oIeKewrSEqI7yY7tX4Q%2FIR4aX%2BG0OAHYKl6cf5MV0%2BEM4eyi54dAFd3ish9GA1N4P3iCaypzQXl5iGqNNYbx682wDMEBqTrCUlMu6b7BDySWF9m6LxhPHDw%2FJyJzZmUUaTW3hTFRcqlCJG0vdXu8mT3suEgfsFIjod7wgvDw%2BAHuG0KCVBQ%2FQ1P6pG4I22I7DGoOMDjJwtxGYJo%2BDKHgCbpIpVRXU%2FHZ2YQ46HC30ehGjkkpPWudyBAcfKTBO1oqLEU4DZWQ%2BeeN%2BH7GqsdYCFNcnnJJ6nvM1CX6Zl1h3TrBAIIPVFiD398byV4RXNh5fSLy%2FysV91fDKCb%2BkmOR0GwiqlW0B1mrwh%2Ba60KDeW2VjpA1FHtZRdQBuQLHmQCB5zG7s%2BMQytHzwwFxXU7MjEWEMAY2wUxJyuKMO09NQckJ5CLKknW1JUlIUD2jmgjsMfOZlYSQobEb3jeORXFXjvJSl1DB6KfScVYJrKlKqGF6610skpSvKcZ2JaWeZABBO9gd4Dff10qK7Iy1EmOMrNGbfq9HmZebkvaTLuhyfVZKJcJCL6HQVDbltuLxfcZZq17g14e8p8mVUPDNYxb4hMVet0yuyKZxqnJfXqQhI94u6j8AMark%2BNDK3Azq61ktwo4RwpiJzWoVOZmVzZl1KHNpJvax37I5rx3j%2FFOYOI5%2FFWLa1MVSqVJ0uzMy%2Bq6lq7AO5IGwA2AEB0evwhmYbN%2Biymyn352w4gR5J7wheZUxS6rSZbLPLmnN1mnTFMm3qdSTLPFh1BQoBSSOw9t45RKllRvEqtV4AskbI3SPk80U4niBSecBleVDQfzMwgyff4hpif%2FEtxujwiT3S8XWPE%2Fqb7Sf8AYojn%2FC9dmcL4jpOJZNlt2Yo9Ql6i026SELUy4lYSq3YbW%2BGMxz%2FzZdzzzZxBmo9RhSV194PmSDvS9DZKU6dVhq8m97dsBreIg2hpgBbtgN4cPHFHjXh3lMSSWF8P4brMpipuXRPsVqWU8k9CFaQADYpOo3BB7I2WPCEY5UdslcoW%2FRh8ERyQCRyishRgO0cvePyqnHmHnsY5SZXydGFUlRPTshRAzMyjCnAlTza%2FelIOq%2FcDGd5v1urZB8SubVaqudlcy5l8ZtSdcw3OSOHm6tJYma0KIQVKB0LbKinY7g37BHz6bctqQvSpKtilXIjuMdH5acYlVomApbKLOPAFEzUwRTiBTZKrrLc7TUW8liZ3OkcgCQQLC5AAAbJx%2FmrNZ0YYxDlFg3itxDj%2Bp4gakpOj0GbwCzLN1VTq09Ihx1CQWS0QVBfZpEbA4nuKV%2FI%2FFVJyfoWCMCYwOF6BIU%2BenK9IibdbmktAONIVvZKbDa%2FMmNNL42sJYCpE7JcOvD7QMA1KfaLK6u9MGcm2Qb3LalX0nc23jlmsVqpVudmKpU5x2am5lxTrzzqtS3FqNyok8ySYDqD6%2FwDxGkBC%2BH%2FJ1wJNv6wj5osWYPHDijHeW1eyxTlZgfDlMxC6y9OLocqqXUpbSwpKikdUm4tc72jmnpD2mJFKvARWEr5RRKQmJrmJSL9sBLE1hEQLRMBAQSLmKyU%2BaJEjeKyRAVGUAkR6FCydopNi1o9CE64DKaO1opjaz2pMX%2FKv%2Br66r7mg1Un0eKr%2BcRZpIBFLbT3JVF4yxYdmJnETDFukXh2qhF%2B%2FxZVoDU%2BFyTOS%2FoQPyRt%2FhhTfiowDtyxrSv8AzrUa6w9huckFtTdQelGQkIWoKfAULdoEbE4W30TXFLgCZbVqS5jWlKSpPIgzzdjAfoNhCEAhCEAhCEAhCEAhCEB%2BfnjgOrifzLT%2FAP1NUP8AemNDpZ1AG33Mb%2F43Je%2FFFmP%2ByxLUFf7UxpJoNIl0qmFBKGyHD1bk72sBAZJIKc0qbZWELWlI1kX0bi6rdtuYHabRt3MnNSiO4ekso8mJKdouX1JmGqg4%2FNAJqNfqiCFGemj70JcF0NDYW3jUOH3qfUnnWKTMuPzIYLoZWyULITuq3eQN9o9txcgkXGxgNpYs4mM5cX4iwvi6cxGxJ1XBjjkzSVycslpKZhwAOvLF%2BupxIKVdhBPK8XKtZuZeOZl4BzmwphqYoFZkqk1U8Y01tIMmZhDo1vyp5lLjZcUoHkQBGmb%2BeIjvB3gPonxsZUPZw5WStawUfHpqjrNWlOgOvx2Sdb94BzI2ULeePmO3UX6K4qTel1FaCUqQoFKknuIO4MdecOPGDN5V02WwFjqnTFWwrL3EjMS3Wm6Yk7lsJP2xq%2FIc03tyjetRxnwQ48vXarUMMF51Qcd8bldDoV%2ByFgb%2BuA4x4aspcQZ45lUea9jX2cNUKcZn6xUNB6JIaUFoYSrkpxxaUgAchc9kdBeEMxjLTGJMGZaSz6FTOHqdMVWqISbll%2BcI6FtXcrokaiOzUmMyxfxmZQ5Z4fOH8iqIxW6hLkiUUJXxajyK7fbVJsFPL7gBueZtHD9ertYxLWZ%2FEGIKo%2FUapVJlycnpx5V1vvrN1KPcOwAbAAAcoC2qNoBRPbBQ3gBALmFzEdIhpEBC5hqMR0%2BmGkQEY9MmiYVMMtSbT7sw44hEuhg%2B6LdUoBCUW31FRAHnMeYbmPTLTD8pMS85KvKZflXm5hlxGykOIUFIUPOFJB%2BCA7LwjlvirhRwk5jVjBdTxrnBimXMmy3KsuTUvQWx1il1wXKimydXMqUkJGwJjjOfem3pt9%2BfeW7NvvOOzK1iylPKUSskdh1FW0bEb4l8%2FwCXmFzTObFdS66suLWHEglXfsnvjW8y67MzDs2%2BsrdfcU64s81LUSpSj5yST8MBKCSOcRiGw2vCAliNzE2gQ0CAgeW0Q35xNEQICERcNpdz9rEYiptL6C2U6knnaIzyQ7l4iMz8psvcx8NTOLMnBi3EknhymVKRqLs10bTQ0XZbKffFKkkg22jCMO5kY3xBkTm9nXhN8tZi17GsrK1%2Bcp6CuaplC6NKmWpYWJS3tYqt3nnHO2OcxcW5lVlivY1qCZyflZCXpjLiWwgJlmQQ0nSNrgE3PbE2AsxMZ5Y15WJcDVx2mzzjJl3tICmpho76HWzssX5X3HZEpbvkcQ4zxtwb5qTebNRn6hSaPPU17CFVqqf0WaiqYSHGG1qAUtFrj90R2RmnGlVcFuYrm8GN5SVKpYycoVLdYxTLrWWpNm10slsX1kISpJ%2FbRzhmPnbmXm0xKyGO8QCckZJXSS8jLsJl5VtzmHOjTsVDsJ5RncvxrcREq2yJbE9LS4whCEurpTS1nSLAqJ5mwF4DK%2BDPHGW1KxzTsPVPBTMhihMjWH14vmKnobDAaKjLdCqwTdA0X53JjSWZWKcvsXV2UquXGXwwXT%2BgSzMyxnTMiZmCs%2B7gnyAQoDT5iYw%2BccVUJl%2BbnAh12ZfXMulSBYuLUVKIHIbk7dkSC6tSHka0q2UnzRcdUcPFIeyFzZw3gLM%2FIWZfxTiSpqmKPX1DpHqcw43p6iRdBSFAqKybp1Rs%2FA2HKjJVjivy6mcRPYkxA6tqeVPLATMTDUxTnC0khOwKSOjsOW0c04d4tM%2FML0KWw9T8ZtuS0m0GZZ2blEPzDTYTpSkOq3IAAtfuEYXhTNfMHBWM38wcPYom2q9OKUZ2bdV0hnNRJUHgdli5uB2dkREZImM29sNl2R8GxiybnGXpV2rYhK6QlYLalTInpctKQD3KZc%2BKY6TrFWo9bpcjxaameip%2BUlTShHvjMTZSsEHs0rC0fDHA2ZGemZWa%2FiUvjavNvSVOUXJWQlZZMvLNuWt0nRp2K7E7nvMUkZ25mJyyOTnth%2F4IFvoDIhlIV0PS9L0XSeVo172%2BCJMnc%2BQsnLZhYRyMz2rtQLk9gzCVZplT6UXW88UhtxSldik9CpX7uPnnibED2LMQ1bFkySXa5UJqpKubkdK6pQHqIjJ8PZ75rYPwZP5e4axR4jQKkuaW%2FLplkKXeZSEvBLh3SFAchyNzGvz1EJQjqpSnSn0RRKGk6tRVErriRsDCxtuqJCLnlANd%2B2FzENBiGkjtgJtcNcS2MLEbwFSMuymoy8SZoYPw6zXVUR6oV2RbaqYteTcDqSl0X21ApFr7XIEYeL%2FdRWaWEFLgWpKkKSpKkKKVIUDdKgRuCDYgjtEB9TWasjFfEDj%2FACuby2quF597DDLKsyZZlLbz6FJQCnURZKkqXZNtyW1A2smPlvUJRunzj1NZeQ8mSfdlQ82bpeDbhR0gPbq06vhjYFV4ks%2B63h13CVSzbxA%2FS32yy4304StbZFlJLgAVuNjveNagAWSgaAjYDuERMZiKib2uYgFKsbC3pgdRPIem8U7He5MSBcXeJ%2BkVYRT0GKmg7bwEinVElI5fkgFKHMxOUc7cjziHXTseW9oCZBKucTKuOUSJQtXIxMUqHbAErVEVKVeJN%2ByJwDAQ1xHXEpSYhbziArtkcyuIzU1NS1MqRk5p%2BWW9ITEu4tlwoUppaDqQSOaVAC45Htijcd8TL66FNq6yXElKh3gixHqgOuuNBTdOxbkLPPISiXlML0951IHVQhp%2BVWojzBIMbYxFhPFE54RrDWNJelTLlCmMMJm01NDZUx0Il3kLBcGw6629v2Qjg%2FE2P8b43RSmsYYlnKsihyfiFP8AGSk%2BLy%2B1mxYDbYc78hF%2Fl8984pPCBwJK5j1tqiaOjEsmY3S3YjQldtQTY2tfltFpjMeXOGr0%2Bv5tY1rdIcS5Iztfn3ZdafJWjpSNQ8xIJ%2BGMMue%2BJkFvRoT1Up8kRAgHthEZCEIm280NvNFRKDaIlfngEjviVQHfAThV%2B2KiAe0GKFx3xX6Rei9xp1D5IjPInjdaYCxLgnC%2FBDh6sZjZcpxlSRj2oS6JDxjoeimFKUG5i9xysUkfsouuSeb8jnRxG4Yp8phCl0CkYDwfWPaBQHFhbYq%2FRpKHF%2B9KtN9KRe1r7mOU38wMWu4AYytcqt8LytYcrsvIhAGicWjSpRVzKffBPYokxa6VU6jRqnKVykzz0pPyLyX5eYZWUONOJ5KSRy%2BaJnjRDrDhMzA4g8W8QbGGsxatXatR5tM37fpCuS58TlZYNKKrhQAbIXpSkDYi8XbCmIMtMKcHWBji3LOazDoBxxiCWplPlVEKZ0TUwWpnUNwno7Iv%2ByjRGL%2BKnPXHWH5jDGIsbuGRnUdFOeKy6Jd2Zb%2B4ccQAojvhlvxQ5t5U4SbwTg%2Bp0tmkSrjjsqy%2FT0OqYLh1LCVHsJ3tERGSVuyvxFgTAeKJ93M%2FLB6vS00uX8RYfmlSy6W4JpKg6q9taQgp37dF%2B2Ns8bmNctaxmJiTDFKwfKzWLJScp7z2MmJ%2FpETTIlwVMBtJKTYKQjzWJjQuY%2BZWK82MTu4zxnUGZqqOyzElraZS0hLLQIQkJTt2nc7m8YxoCG0oB2REomM218t8G1fA0lJZ%2BYmyTRj7Ar0tMSLTZc1IXMLc6NKwlNzrQtKk6VC11bx2PiCXZleLDIzHM5VZlmSxRhirUenUObaS37EPiTQ4A2nsK0noz2habDsjibK%2FiHzYycp71IwLiJpqmPvqmXKfNMJeYLqralpB8kkgE25kXi04yzdzDzDxRK41xZiWYfrcgUGRmWT0XiehYWnoQPI6wBNuZ53iJjMiMnYXDTTqpTOMDPbENak3ZanSJmlTsy42UNLQ5NoeR1jsfcklUOGWlUvOnhkpmBFPBKsG5itTzewI8Xbn%2FHmEpHYFNurSBHNuL%2BKnO7HeFpjB2IMVsinTzfRT3ikomXem09ocWncg8iNrjblFiy1zvzLyfbqTOXddZprVWW09NIclkuhTrSSltY1eSQkkbebui0JdhyNal%2BJdjiHy3mJ5CzKY%2Fp0%2FSy4rU01JsPNJ6vcnpJV0G3a4Y5846MXoxPxIV%2BVlrJlcOyktSGkX8hekvOj4zo9UaywDm3jvKmrT9fwNVm5KdqrYanVLZS6l9PS9KdSVbX1kqv3kxjGI8RVrFtdqWKMRTqpuq1iaXOzswoAF15flKsPQB6BCR4tfvr84lOpfKJQlR3vEw7rxAKCuUSpKuZiZdyLX5RKD2wE8IXHfC474BF3w49NIrFORLzT7YfqEm06hpwo6ZPjDZCFAc06gDY7bRaIqtPuMutvsulDjK0uNqSbFKkkFJHoIBgO2eIapSNG8ILltP1hSGZOXTR%2BlU4QEtqU7MpQTfkNZRGyEyq8fcR%2BYuUuY2StBcwDJUZM45iCZpYE25NFprU%2BqaIsSoLcCdJugMA98fPfGON8VZiVh3EON67NVmpzDTbDk3MqBcU22SW03AFgkkkW7TeMmrHEFnZXsJjA9ZzLrM3Ry2lhbSnQFuNJFg2twDUpNtiCd%2B2IiMhgs03LMzExLycwZiXYfdaZfVuXW0rKULPfdIBihESQE2FgBawES3HfEgeUS2PdE1x3xMAO%2BAkuREpMVCkHtiBRAU7mJomCB5om0CAkuYXMTaR5oaR5oCQkxOi55iIFPcREQFDugJoqybr8rNszMs%2Btp1pxK23GzpUhQNwoHsIO4MUwlRF9oii2vchMM8x1BjV1ct4PHAUy4VOFWK33HFqJKnfd5tRuTuVEg3jcmH5xzLPJvIaiVnL%2BazWFWnZXxadaYSsUJKwl1pTSgDfouksCbbIVc7COGpnG2LpvB8pl%2FNYjnHsN0%2BYM3K0tSwWGXiVK1pFr3utR5%2B%2BMZDgrPXODLeiDD2DMwqpTaUNRbkkrDjTV%2BegKB0gk3sNr9kFpjNm%2FGnh93DvEFW0TOJ3629VJOXqXSPka5VCwpKZYBOwSjT1e3SoE7xofUe%2BLjV63WMQVGYrFeqkxUZ%2BcX0sxNTC9bjq%2B8n83IRbVJN9iIiIyRkkUbxKDY77RUCQeZESlNjEoSnntyiZI7%2BUFt9YaTtFTQAkaiLQEl9MRbVqdB7BziGka7X2iZbdusD%2F788RMZodV8JNToVFySz3r%2BJsPCvUaQkqa5U6X0gT47LpQ6S2CeRJI9UUqRndlzmLi3LXJei5b07BGWbmNJOqVuXW6FqnZkKPRBw3sG%2Bk0XJO9gOUaBw1mPi%2FC%2BEMVYEoFWTLUbGTTDVYY6NKi8GidOlR3TsSDbmIx7V7nocSPX3bg7dt4ZERk6rxpj%2FisY4t1U1io4nYqbGJUSUjSmWVCmmlqfASFNgdGpss3u4T391o2kg5fYRb4sZmTwQ3iTCcji6mF7D8gOpNKMo2ZhpsJ2Gl5Sjty0mOX5bi54hpPDrWGGMxZgSzLHiyJlTKFTgb7B05GrYbXi0ZXZ%2BZmZOCrDAFal5RNdmG5ufE1LJmelfQFDpLqN9ZCjc9sWickqc3iPBMhm1MYwreTU03g96YfmG8IPvLY1MlrShtLx56V2Xse2143pxJ5i5N1HLLAdCkcuWak%2FVcDq9gZtqrn%2FAIK63EWZISeutJTcg90aCzTzuzLzkmKZ9ULEDE%2B3Ry6qRZYlEMIZLunXbTub6RzMYOUhKFaAgJUq5SNrnvPniwzrLbA%2BJa049mTJZVqxthvBU0mYrksD7ktARrUysDrG6Dq6oJ2jqfMWo0TF2R%2BRmcdHk5rBmFaPjmjl%2FCTzaW5dLa5tSA6kWClFs3UDyKVknfeOSMts1MfZRVpzEGX2IXKbMvoDUw0pIcYmEg3AcbOyiOw8xc7xccz878xs5fFWswK01NykiVmWk5dgMy7alCxVoTsVW2B7ATaImB11jqgV57wk2FpluRnFSyaSzNomUtnoCy3KzLbvX5bLWgW71CJcB1Kj5q454rslZSbaRK4mfVNy8wnkguM%2BITK0jt0uttqPwRzjT%2BLvP%2BRwwnCzWN0uNNM%2BLtTjsqhU222AAAHedwAADa8YJgLMvGGWeIXMVYLrBkao6w%2FJuvqQHOmZdUFuJWFeVdSQq%2FO%2B8RkO7WsVStS4jMUcO%2FTj2NcyhlqBLt%2B9bnW2Cp0kctRafSfQmNGcaK5fBuHMn8j5FaFIwjhhDz5bV1SvQiWQoj9kGnFC%2FwB1GkJfNzH0vmY5nCxXyjFrsw7MuTwbTpUtxvo13b8mxRYW8wi3Y%2BzExbmfiJzFuNqmmeqbsu1KKdS2lsdC1cISEjYWufXETCYYwsK1G3KJVcuRislaRsAIkdUpPICCFNCNyomKhRdQCVXgdNhci5iLY5lJAgJVMkHYwsQNAFgOd4m6I679JDoSlKldLq80TE5JickoUeUZhlVl%2FizNXHMhgbBUwuWqU227MOTQfW0mVlWhqdeWUkEpTdO3aSBGHAX7RF5wtinEuCasK9hGvzdIqAZclzMSqwlaml21oJIPVOlNx5hEzGazqjiEp8%2FkTkjPZFZR4MrjlKfLU7jfGD0koML1uNBXulrG%2Fueq2yEAJ5kx0BlQzg6gVvBuCsqcc4cqWEsMUKdMzSabMh6fq086psKnFhO3RpOq5JvqWOyOAK9n3nVimhTWF8RZmVmoUifZMvNyby0lt9oq1FChbkSAYxzBeNMVZeV4YlwHXZihVRDC5bxqUCUrLSyCpO4IsSlJ5cwIjJXJ6Mx8Py%2BFcd17DUrXafXWqfUX0JqVOc1y8wFLLl0nvTr0K7lIVGML2iuV2KjZIK1qWqwtdSiVKPwkk%2FDFNSCvlFcjJTBJNj2eqILNtki5G14nU2sC1wB8hiUNa9gDfkREoSJC0%2BUQR5ojz5XtES1bdPKJ0NrPNQAgJUpTzMSrAJ2MVy0kdsSloXveAo6bdkV5Wem5NSjKPraK0lCik8xtt8kOiUrkREoYPlE8ouPWiqVFXlTLnV88UZudmZrSh55TiUXCb9nfFO6uQItEq09oMRMZidsgA27Y9Uh4r45Lrn2ph2UQ%2B0qabl1BLrjAWOkShR2CyjUATsDaPEi4O5j2U9MmuoSTdTfdYkHJphE460LuNy5cAdUkdqgjUR57RE8SZd4ZB40wznXW6nR5bIfDmHMl6JRFS9QmalLIMymcAuSJgbKAbBJIN0kXvyEY7w80mkSHDROVnBCcAqqczjmoytLqGM0tqabp%2FjCWmkuKPW1qQEaR2kkx6sY52cJmKsEyuU1MzFxHhXBUoQw7I0ijrQucYCtg64oXN7alfdK57bRoHCFG4WMZZdzOEcyMSV3B2JZWsOus18MrmGKtTOlV0SegB0NO9GUg9oUkEbG0TE5qxGSnxO0TMOgZouSeZ2EsNUKpmmS6ZU4aY6Knz8qkrCZhA7Vk6kqvv1U3jUK%2Bcbp4qs6qBnTjekT%2BEmZpFBw5SE0qRcmWyh2YOvU44UncAlKQO02J7Y0ruuGRMJSe%2BDDy2lpfYWUq3sqCm1dkSoF%2FJimeSXp9kp9CSlE0sj09%2FOJH6jOPtKbmJhbiCblJ3F4p6IhovtoPqiRJqCiDy7OcehsJ0gDe3LeKCmiix32NjtFWWBVYHayvzwHUfDxmTRXk4GygyryVp1QxNNz6XMYVmvMImEPShuqZW2RfQgDZII5ADmY2nhDIvKhziUzexDhPC0hV5HBUlTm6ZRHFgSDFdmGVuvp7koRpRsbhBcX3RheR%2Ba3DhlllD7BS%2BYM%2FhvGOJJPViGrs05Ts5LTC%2BbTKrFKUoSBottc3O8YzlVmhkvlJjHMXLOmY2r1Uy2zCozMurFb7CjNStWUw4h51YHXKSHbFfYpIgJuKWjY2dy7wxi3E%2BXmXTgdnQz7dMEThUyonUPFZhkACyj5KrmymyL7xy04vsjonMzH%2BV2EeHLD3DTlLi17FbEtU1VSp1ky6mGkkOqc6NKFfdrVew5AHfeOdlt7xaEwpE9sELW2vWg6VJ39HniYo6wAPOJujiqHoXVqhr%2Fq5frim7UJxwdd%2FWCeUUy0BseZiXQOV4CUquYqNpvFPTaKjau6A6NyPzLwXQcOYfwBl3kS3i%2FM%2Br1FpqozlZlkPSi5dTl3VNEXKEIQABcC11Ek7CMg4g6vltw78SlafwVlthSu06pYelHajR6gFKlKbPKWpSlsWvoUpKUkp7NXntFx4aMyeHjK7KyZdXmW1hzMnEEs6ahU101b71LGshptkEaSAkBVr2JO%2FKNN1qh5HDO6g0%2F6r05iXAtRmGKpifEc7KrS8p%2FWtx1haRcqKyhtOobDpPNFoG6%2BIuoYUlOF3DlYr2UuGcM40zEm2JuSlqSwELkZJtXS9KpVgQS3oChaxLgEcdOOdII27xT5wy2dGbU9X6K8VYcpDKKRh9ASUoEsgArcSns1r5fsUpEaehAgVEbQBMQ0mGkxUXFNbqKUJQHfJASD22AtFNdUn3PLfV6hHk0Hvico88F1Owt2xXAJRteKCgR3xP02lHIwUbnyXx5lTgDDdTmahlnNY5zNn5tMvQJCcltdMQ2SkIGoG%2FSG6irY8gI6Gx5k9kO1xJ5NU7FmGqdhv20UidmcQ4elnCJRVRQ0gyqVAHq6lqdTtYK6MRrrg0xLw%2BYBptRx9mPjCnU7GxmVStNbn2lKbkpVKAQ%2B2ALFSySCeYCbdsXSjZlZQ5d8UeGs6K7nIvM5qtyNQka5UVUzQ3QZhamxKuoaF7MhIWja5TcmLQMxziy8pUlkhmdVs3so8K4KqNEnlS2B5%2BiAh6b6yfFiuxIPSHqkK7CeVo4YIOsx2bXszMqcFZMZsYZm88U5qu5hTM5M0alLbWo0zxjVpBUv7WEKKV3TYAtp0gXji99dxspSlK5qO1z2mKzCYSKB%2B6imVEczENQO14aQe2CDVfthEQiJwgQEoHfAi8TEWgBeAhCJtENEBTO5iJTcbRWDBIvEob3tAU0c4qAX7YKRp5JiKSfuYCms2O0LbXiZaQTEwTtAQbtyKQfTEdIN9wPNEQEg7i%2B%2FZEQD7025wHol6hOyksZRh5HQLVrKCkc%2B%2B%2FOKvs3UV%2BXMp%2BFIi3rC%2BUSC%2Fv4CvNTTk0vXMXKrBO47BHmTIU8cpCX%2BBpMVhZfUXExSAQkQFEyNN5%2BIMX7%2BjT80RRKSV%2FwCpGviCKhREu4gJ1SUisHXKsG4IN0An8kQQUoSlCEJSlsaUhIFgB2DzRFG3m9MFc%2B%2F0QEh%2F9%2FNEdB56Ij6Nj3GIoK7wE6N9iOr2xBbSfJHI9vdE%2Bm%2FWBHoiRaSOsDseYMBJoKPJsfPFJxGo2Ij0FvRrbXqIT29gik4QjtgLe%2BhLYJsI1hMmp1SZfW2pxaEOG5BNkC%2BwjZU4tZO3cYxCkMBijzS0OqQt2cWhwX2ISARcekmAx5VMqPa0s%2Be8eqkyk6zVJZKroKl6d%2FOLRfdbkUFurTMy7wUbh5A9aoC4rob%2FAOpqigujTqSLtqsOe0XpdUeJVol3h5iIl9lpsp6Myy1DvP5YDx0yQcaWovo6v7IeeLn0Et2Mp%2BFMUpZ599aitohIEekg25QHlmEIQ3slKfQBFmnFnX5Ai8Tl9HKLNMXDnum0BF%2FD84V36BUUXaHNoVuwofBGVMYjmmW0JMgTpSE7pubDlFByszDiAHJR1ZTfcg8jAYvPSk03Tn7oWAlsqvbujG22p%2F3hd9ZjP6jU1uSj7a5SySysDqnbaLIw%2BvoEi6fJH5ICysvV1hQUy68m3n%2BeNj0KYm2peXmHFrDoTdWoWJPK8YwlxZUkBW3Zt2xllM6R2VQ88rWpZUSbW7YC9t1mc7kxJM1CZnEBDxRZKr8t%2B6PMltXYLROGTuU6gT3wECfNEp9ETBDnbaJg0s90BTBtEqucVlN25xKEd8BJ14nYW4wvpPuTCJiLi0B6TW55oWQUW7ymCqrMzLLjLhSEuiyrCwMeIoN7xMBbsgNq5Jz2R0nIzyc2Xao1NrqCSFSc3MshUgGDYILOxdD1vL208t42qqpcCSnLmqYwv%2F2nO2jlWEBubOWb4eXsLqaylqlXdqCZ%2BWVLNTc7NO2YKVCZC0OjQOtoKVA35x5eHjOnCOSc1XKzWsEzFarNRQ1Lyc4w8hCpNgA9IlOrkpRINx3RqOx5Whpv2QGbZr4ry3xfVmavl%2FhCsUJ%2BYLzlWXUqn44qceWoFLgPvSBcEecd0YJE%2Bm19ohAVZFAM%2FJ%2F5yz%2FvEx3sq7s0tCSSpR7Y4PpS2GalJTU4VCWl5ll58pTchtCwpVh2mwMdPP8AFbk47NeMMOVcpV1rmT0281ozWNO6qmfN%2BLFeJ3NERxzr1Rn3m0W0oVq0EJ96bJvYxP0MalRxR5So3ZXVka1b3lDsfXE6eKTKq51v1S2ra0mrl542tzHf7WlnlyT0S28y3YC8VtCbczGoG%2BKPJ0q685VwP8yVFccUuTidkztUI88iqLRT5UTV5J6JbRmGb2INrc7xAtJcSUpVv2AHaNYJ4qMmlCyp6rAg9kiokRTHFLk0XCFTlVCexQkVExaKeJG68k9EtlexwB90jy1OhocQLIvccowBXFPksry56rn94Kic8V2SRb1qn6sTysZFd4ruTdeSeiVlx5TpyTpk442LkINj2Edv5415TJYqUm%2FYmNhYnz4yIxFRpylytaq0vNPNnonFU1egqG4BPwfLGpGs3MKSR1%2BxVQdSe0NDcd%2FOK1617Kau9PQ0lmMjo8U18bfbkc%2FTEuJ02xg%2BBy1tn%2BAmLhjOSmcRVGr1ySkn0ys0tEwgFs6ggnbb0xap2YNRrblQCbBwpVbu2At6xGhVrdCNTM6GgmXdBHMRj%2BI5fQrqiMiojhS0oHlaMdxVOfogISNgIhKwIZ1KsSTHvblVBNwgx5pB3W4AtPbF%2FbbQUC1xAY9Ny6hzEeQNqDlrRkM1LX97HlEndwdWAt2MjZ%2BneaRSPUpUX59OlCdvepitVcD1jE0vK1GmMhbbLPQKJcQnrAk9pHfGZnLOorZavPISCyggFBPZyBHOA104tSeRil0y%2B%2BM%2Fcynqf3wZ%2BKYpfUhqx39k2fiGAwXpl98OmX3xnX1Hqrf%2BurHxVRP9R2qdtXl%2FiGAwLpl98R1lQ60Z79R2qdlXl%2FiGIjJusEXFYYv3dGqA14uxMUo2SMm6x985f4hiIyZqp39lZcfuTAa3TFRHZGxPqNVcH%2Bucv8QxH6j1XH902PiGAwJEIzs5R1bf9M2NufUMR%2BpBWPvk1%2BDMBgR5RTIMbC%2BpFVOXsm3%2BCVEispp9I1KqrIHf0aoDXtld8LL742EMpKkedRbH%2BiMPqSVH76tfgVQGuwDeJ7bRsIZRVM%2F3Ub%2FAmI%2FUhqf30b%2FAmA14lveILSQY2QjJ6pkf1zR%2BAVA5PVH76JP73VAa0KTziGk9xjZX1HZ4m5qn%2Fh1RN9R2et%2FXY%2Fi5gNagbxWQnaNifUenfvwPxcxKrKGoJ5VUH%2FQKgNf6RE0Z59SWf5eye%2Fd0JvFT6kdQPOoK%2FAGA1%2FFNeq%2BxjYysnagP%2BXr%2BBoxTOTtRvf2Q%2FwBkYDXNjCxjYv1H5%2F74jl%2BpGIjJ%2BeB%2FrkPwKoDW9ieyJtEbJ%2BpDUbf1en8EYgcoaj98B%2BCMBrfR54m0eeNi%2FUhqn9%2FJ%2FBmJ0ZP1QjedT%2BDMBrgJtFVMbDOT9QHOeHwNGJhlFOgbzx%2BBswGANpVaPWynvEZsjKt1Gy514%2BhqJ15cKZSCH5gq7OraA8DB%2FS5O%2FvDF6y1W22%2FiBbt9Aw%2FUb25%2FaVcosdQpdSpzRl2mXHBvpJEZBg2WOFsNYgxVjFpynS03Spim04vJIVMzTwCbJTzUEpJKjyGw5mA15dtcovbrdFz%2FAHMZ%2FwAI6R9cTlqpP67aJ%2F51qNezk9TH5UtSCJgFaCF9IkJANiNt42fwhyZc4gculJv7liyin1TjRgP0DQhCAQhCAQhCAQhCAQhCA%2BafGL4OrM7MjOmo5kZXJkJ%2Bl4gWZqblnphLL0rMqt0nlkBSVKBVcbi5FuV%2BJuJPhbzH4fKxI4fxbTkFc7IonJdyXWHEOJ1FK0hQ2KkkbjmAUnkRH6BYwPODJPLzPLDScM5g0QTjLKy7KzDaujmJVZ5qact1SQACNwbC4NhAfnEZTPyM03Nyi35WZl1BbbqbpUhQ7QY2vKThqUq1M1Ki09595pC1OoQWiu48pQSbE784%2Bjte8E%2FhqaqTjtEx%2B%2B3JFV20TSApwJ7iUpsTF%2BoPgv8ABlPkmJapYumZhxpJQpSNgU32sCmA%2BY%2FilP8A1vS%2F4ZfzxHxSnj%2Fm%2FL%2Fhl%2FPH1Q%2Bxn5WHnXKgPQ4PoxD7Gblb9%2Fql%2BEH0YD5XhmmJ29rzCvS%2B4In0U%2F8AWvLn0zDhj6kK8GXlt7zEM8PSv%2BjEyfBmZZe%2BxBUPgWPowHy2WKerlhdhP76c%2BaJehp5%2F5vS34y5H1NT4M3K731fqPwOD6MVfsZ2Up51yrD0PD6MB8sAzSPfYeZP75ciPQUTtw%2B3%2BMrj6nDwZmUV%2BtXqzb%2FLD6MVPsZmTfbWq1%2BHT9GA%2BVvi9HPk0BH4yuI%2BL0j7wI%2FGFx9VB4M7Jgf3arn4wn6MVU%2BDSyRHlVavH98p%2BjAfKjoKRz9gkfDMLiIZo429rzf4yv5o%2BrafBqZFDyqlXz%2B%2BU%2FRiceDXyGG3j%2BIDf%2FpKPoQHygEtR7kqoAI7B4yvb5Im8Xov63x%2BMr%2BaPq99jXyD%2FAL%2FxF%2BNI%2BhE32NfIH%2B%2FsR%2FjaPoQHye8Xov63h%2BMr%2BaJSzSDscOpP74X80fWM%2BDXyC7J7EQ%2FfSPoRH7Gxw%2F3v47iT8cR9CA%2BTnilFP%2FN5P4wuBk6Rvpw8PNeYXt8kfWUeDcyAH%2FLMRfjaPoRP9je4ff1fEX44j6EB8mEylK99QE%2FjC%2FmiomTo9uthwE87%2BNL5%2BqPrMnwcPD2nm5iI%2Fv1H0InPg5eHo8ziH8dR9CA%2BSyZGkJ5UAfjC4qGUoqueHR%2BMr%2BaPrSjwdXDunmzXlemeT9CI%2FY6%2BHb9Qr348n6EB8kvEqNf%2Bx4fjK%2FmiLdPp3ZQx8D6vmj63p8Hdw5jnKV0%2Fv8fQiP2O%2Fhy%2FvKu%2Fj4%2BhAfJP2NpCd1US%2B3ZNK5%2BqKXilJ5Gg3%2FfC%2Fmj66I8Hlw4oFjT64r0z4%2BhEfsenDj97q5%2BPj6EB8i0ydKHOhAfvlfzREytKt%2FWEfjS%2Fmj65jwefDj97a2f3%2BPoRN9j04cfvZW%2F9Yf0ID5ECXpKT%2FY6b9%2FjS%2FmgZajq54cc%2FGl%2FNH15%2Bx7cOP3prH4%2BPoxA%2BD24cDzpNZ%2FH%2FAOhAfIUy1J5e186e7xlf5bRT8UoyeeH1H0zavmj6%2Bq8Hrw3K50is%2FBP%2FANGJfseXDZ96Kz%2FrD%2BjAfIFTFI7KBb98r%2BaICTpCh%2FWUj0TC4%2BwH2PTht%2B9FY%2FH%2FAOjE32Pfhs%2B8lW%2FH%2FwCjAfHwyFKII9hVb9vTr2iKKbSrf1lWf3wr5o%2BwX2Pfhs%2B8lW%2FH%2FwCjFT7H9w3%2FAHjqn47%2FAEYD48LptL%2B87g%2F0yvmh7HUz3tFA9LqjH2EV4PnhuVzotWHonv6MPsfPDd95qv8Aj39GA%2BPfsdTfvJ%2FtFRKadTfvMfwio%2Bwv2Pjhv%2B89Y%2FH%2FAOjD7Hxw3%2Feisfj39GA%2BPXsbTPvOfwqoj4hIEWNI2%2Fyio%2Bw32Prhu%2B8tW%2FHv6MQ%2Bx9cOF7qpFYVsBvPf0YD48%2BxtM%2B85%2FCqiomm0xA1ewRAVsD0iucfX%2FwCx6cNvP2IrH4%2F%2FAEYm%2Bx8cOB50qsn0z%2F8ARgPj14jTidqKfwijE3iVPtb2FHx1R9hWvB98OLXkUir%2FAAz1%2FwCTE%2F1gHDl95ar%2BPf0YD46mQkPvIj46ogabJHlRW%2Fjrj7F%2FWAcOP3lqv49%2FRh9YBw4feOqfjx%2BjAfHlumSIG9Fb%2BOqI%2Bx8n95mtv2So%2BxP1g3Dpe%2FsHU%2FxwfRiCuAThyVqvQ6mNXO07z%2FgwHx39j5Q8qM18ZUSCmy196Q0PQpUfYkcAHDkL2otVF%2F8Ap3q97D6wPh0%2B9FX%2FAB8%2FRgPjyJCV5exLXrVE3sXJczSUetUfYT6wHhytb2Fqvp8e%2FowPAFw4q50Sq%2Fjx%2BjAfHv2Op%2F3oa9avniCZKRC9qMz8JV88fYZPAHw5o8mi1Ufv3%2BjEVcAvDosWVRaof37%2FAEYD5ACRkiNqKz61RA02TP8AcNn4yvnj6%2FJ4AeHJOwotWt3ePf0Ym%2BsF4c%2BXsJVPx7%2BjAfH0UyTO3sMwP3Som9jpMW%2FSRjb9v88fYBPANw6oWFoo1VBHL9Hf0YK4B%2BHhXOl1j8e%2FowHyA8RkxzojHwqWPzw8Tp%2F3jY%2BOv54%2BviuADh0X5VJrB%2Ff%2FAPRiX7H7w4%2Feer%2Fj%2FwDRicx8hfEadz9h2PjK%2BeIeJyH3oY9avnj6%2BHwfvDif7jVYfv7%2BjEPsfnDl2Uir%2Fj39GGY%2BQniNN7aM18ZXzwElIjyaMwfTqP54%2BvX2Pzhy%2B9VZ%2FH%2F6MQ%2Bx9cOP3qrP4%2F8A0YgfIkScp95pf%2BF88TCXk07GiS3xVfPH10%2Bx88OH3prI9E%2Fb%2BTEB4PnhyHKmVv8A1h%2FRgPkaWJXso8r8U%2FPEvQS33ml%2FwZ%2BePrqPB9cOI%2FuVWT6ah%2FRiJ8H5w5H%2B5VZHon%2F6MB8iejkwbDD0tfvIX88R6KWJuqhyu%2FMAKA%2FLH1z%2Bx8cOX3trf%2Bsf6MPsfHDl97a3%2FrH%2BjAfIky8n76hyqvSFfPEOikQLewEp6dK%2Fnj67Dwe%2FDmBbxCun%2FvAfQgPB7cOI502tn01D%2BhAfIjoZHsoMr8VXzxN4vKnrewsvf91b1Xj66%2FY9%2BHH711r%2FAFh%2FRgfB78OCudKrX%2BsP6MB8jUtSgtqoEme%2FZfzxBLMoTvh%2BUT8b54%2BuX2PThv8AvZW%2F9Y%2F0YmHg9%2BHBJuKVWr9%2Fsh%2FRgPkd0Mr945P%2BF88TpTK20roEiodmyxb5Y%2Btx8Hzw4n%2B5da%2F1h%2FRh9j44cvvZW%2F8AWH9GJich8kujkuj0e1%2BTv9117%2FliCmpIjq0GUSe%2FrfPH1x%2Bx%2BcOf3qrP4%2F8A0Yh9j84cz%2Fcus%2Fj%2FAPRhM5j5GFlqxCaRJAn9grb5YrIRLp5YfkT6Ur%2BePrZ9j54cT%2Fcutf6w%2Fow%2Bx9cOX3rrX%2BsP6MQPkitphSioUCRTfs0K%2BeHRS9wfYCR27NCt%2Flj63fY%2BuHL711r%2FAFh%2FRh9j64cvvXWv9Yf0YD5IltgoKRQZEE8yEK%2BTeHRS1iPa%2FJXItfSrb5Y%2Bt%2F2Pzhy%2B9VZ%2FH%2F6MQPg%2BeHFXOlVo%2FwDeH9GA%2BSAbZAsmjSRT29RXzxFLUsAU%2BwMiQe9Cvnj62Dwe3DiDcUytj%2FvH%2BjEU%2BD54ck8qbWz6ah%2FRgPkp0En945L4qvniRcvLHyaJJJ%2Fcq%2BePrh9j84c%2FvXWv9Yf0YmHg%2FwDhyH9yKufTP%2F0YD5GpYlh5VDkj%2B5V88TdDKfeGS9Svnj64%2FWAcOX3nq%2F4%2BfoxH6wLh0%2B9FX%2FH%2FAOjAfI3oZT7wyXqV88OglD%2FcGS9Svnj64%2FWAcOf3orH4%2Bfow%2Bx%2F8Of3orH%2BsD9GA%2BR%2FikmRb2CkvTZfzxDxOT%2B8cn6lfPH1xHg%2F%2BHEb%2Bw1X%2FANYH6MRHAFw5DlRat%2BPn6MB8j0ysiOdAkz8f54j4vJfeCT%2Fh%2FPH1yHANw5D%2B4VTPpnj9GJxwE8Og5UGpfjx%2BaA%2BRXi8n94JL%2BH88Oglf1vyHqX88fXb6wvh0%2B8FR%2FHT80SngI4dT%2FcOp%2Fj39GA%2BRYYlb%2FwBj9P8AUv54qhiVt%2FY%2FT%2FUv54%2Bt44COHQb%2BwVS%2FHf6MTfWF8OvL2CqP47%2FRgPkcWJW39j9P9S%2FnimWJa%2F8AY9Iepfzx9dPrCeHX7xVL8e%2FowHAXw6j%2B4dS%2FHT9GA%2BRgblh%2FcCQ%2BKv54m0yv63qf8Vfzx9cvrDOHb7x1L8dP0YlPATw6n%2B4dT%2FHf6ME5vkfplf1vU%2F4q%2Fnhplf1vSHxV%2FPH1w%2BsJ4dfvHU%2Fx3%2BjD6wnh1%2B8dT%2FHf6MDN8j%2Biluftfkvir%2BeJg1J9uHJE%2FuV%2FPH1u%2BsJ4dfvHU%2Fx3%2BjD6wnh0%2B8dT%2FHT9GCHyRDcoP%2BbsifSlfzw6OU%2FW7IfEV88fW%2F6wvhy%2FW9Ufx4%2FNEfrC%2BHL9b1Q%2FHj80B8jujlf1vyPxFfPDopX9b8l8RXzx9cfrC%2BHL9b1Q%2FHj80PrC%2BHL9b1Q%2FHj80B8juilP1vSN%2B%2FSr54m6GW2PsFT9hbyFb%2FLH1v%2BsL4cv1vVD8ePzREcBvDiP%2Bbc%2F%2BOq%2BaA%2BRoYYSUkUOR25jSqx%2BWIqRLE%2F2OU8ehC%2Fnj65fWH8OP62Z78dV80TfWI8OP615z8dVAfIroZa9%2FYCn%2BjQq35Yh0cuP7gU7lbyFfPH15HAtw4D%2FmlMfjaon%2Bsa4cgdsJzHo8bVAfIMJlh5dAkFfuVj88R6KVVuMOSHqX88fX76x7hy%2FWc7%2BNriP1kHDj%2Bsxz8bXAfIHoZfsw9IfFX88OgY%2FW9IfFX88fYD6yLhx%2FWUv8ac%2BeIjgl4cR%2FzIJ%2FfTnzwHyA6KW%2FW3IfFX88QLEsTcYbkPir%2BePsD9ZNw4%2FrHP40588TJ4KOHJP%2FADGv6Zpz54D4%2BdCyP%2BbtP%2BIv54j0LH63ZD4q%2Fnj7CfWWcOX6xEfjDnzxP9Zjw5%2FrAa%2FDufPAfHroZUn%2BxqRt%2B7%2BeIiTlxuMPyQ%2BBfzx9hfrMuHL%2FAAftfjDv0omTwbcOaeWXzH4w79KA%2BPPirP3hk%2FUv54h4oz%2Bt%2BR%2Fh%2FPH2I%2Bs44df8H7H4dz54m%2Bs64df8Hsv%2BHc%2BlAfHb2Ol17%2B16S%2Fh%2FPEPY%2BXH%2FADekvWv54%2Bxg4PeHUf8A8dyv4Z36UQ%2Bs74dN%2FwD4dyu5v9vd%2BlAfHVUhKkb4dkz%2B7c%2BeJBIyQUb4alCOwdI5H2P%2Bs94dP8HEp%2BGd%2BlE31oXDte%2F1OZMH%2FLO%2FSgPjeJOWTyw1J%2FGc%2BeJxJSA8vDMor0uOD88fY%2F60Xh4F%2FwD4dSm5v9vd%2BlEyuEjh5VfVlzJG%2FwDjXfpQHxw8Tpd%2F7GZX8I588RVJUoo0jC8qD363Pnj7G%2FWi8O1iPqayO4t9td%2BlEw4SuHkCwy2kfwrv0oD43rkKQrTpwpLJtz92c3in7GySvIw9Kj92sx9lhwm8PQ5ZbSH4V76cTq4UeHlflZZU4%2F6R76cB8ZhS5Um7lCl1j9uuCaZIptfDzBsbnrr5d0fZtHClw9ovbLGmnULG7r304DhS4ek8sr6b%2BGf%2BnAfGM06UNwnD7G%2FLrLiUU%2BWGwobA9Clx9nzwp8PZsfqX0wEciHXgf48SHhP4eSLHK6m2%2FwAs%2FwDTgPjGmmSp54dY%2BBa4ex0lYj2uNXvsda9hH2dTwo8PSfJywpo%2F0z%2F04fWo8PV9X1L6bfv6Z%2F6cB8XzTJbmmgMj4VxAyMsNhRGfjrj7PnhN4dze%2BV9O35jp3%2F8A1Il%2BtJ4dP8FlM%2FDP%2FTgtm%2BMpkZVI61CbH%2BlXEqpOQJumhtgf5ZcfZ360rh0%2FwV0s%2Bl18%2FwAuJ%2FrUOHf%2FAAVUn47v04IzfFwyEkf7jN%2FhVxMmSp6fKoTSt%2F1ZfKPtD9ahw7%2F4KqT8d36cQPCdw7HnlTSPju%2FTgnN8XvEad20RH4ZfzRHxGlD%2B4KDtb7esb98fZ%2F603h1%2FwU0j47v04j9abw6%2F4KaR8d36cDN8XvY%2BmXv7BIt3dMuBp9Nuk%2BwSSBzHTKF%2Fkj7RfWn8O3%2BCqkfGd%2BnEn1pfDp%2FgppP4R76cEZvjAqTk1EfpA1bt93XvFMych94W%2FwAOv5o%2B0f1pfDp%2FgppP4R76cQHCTw5jllVSvwr304Gb4veLyJBvh5B9EwsH8kRTLU8csPkeiaX80fZ%2F60fhyvcZV0sE%2FwCNe%2BnAcJHDqk3TldTR%2FpnvpwTm%2BMAladYp9guYtcvqNvkiAk6X20BJ9Lq4%2Bzf1oHDn25YyB85fe%2BnEv1nnDj%2Fgykfxh76cDN8ZzIUxXOgt%2Fh1fNA02mhIHsGDbtD6vmj7LDg64c08stZP8Ye%2BlEDwccOJGn6mspa9%2F6pe%2BnAzfGjxCn%2FeFv8KuHiFL0afa8L9%2FjCvmj7J%2FWZcOG98t5bfn%2BiXvpRKeC7hvUnScuJe3%2BdPfSgZvjaafSbb0A%2FjCvmiXxCji%2BnDwF%2B6ZWPzR9kfrKeG3%2FB0z%2BNPfSin9ZJw2f4PG%2FwAbe%2BlAzfHHxGk8vYBf42r5oIkqOhVzh534JxXzR9jPrIOGz9YA%2FHHvpRD6x%2Fhvtp9opt%2FnjvzwM3xzNOpCt1UFZ%2FfavmiPsXQe3Drh9E2r5o%2Bxf1j%2FAA4frHP42588Q%2Bsg4crD%2FgQrb%2Fpbm%2FywM3x2NNw%2BrysNzHwTZ%2BaHsXh8bIw9MD9%2BX%2FNH2E%2BsX4cP1mPfjrkQ%2BsW4cf1nP%2Fji4Gb4%2Bik0HcmgTRvy%2FRnL5InRS6Ennh%2BZ%2FG7%2FAJo%2Bvv1ifDl%2BtOZ%2FHVxD6xLhy%2FWpN%2Fjy4Gb5A%2BxOH7degTav35b80UfYygpFlUGbJ7%2FGv5o%2BwP1h3Dn%2Btid%2FHlfNA8B3DkRb2rznp8dVf8kFXx%2BEnQkAAUOcA7R45z%2Fgw8VoA%2FuHOD0Tn80fXz6wbhy%2FW7Ufx9XzQ%2BsG4cv1u1H8eV80B8gzLYfUCkUWdAJF7Tab%2BvTEFU2gq%2FuJNfjX80fXr6wPhytb2AqXK1%2FHj9GJfrAOHP7x1X8f%2FowTE5PkKql0I8qLNj98%2FwA0R9h6IRcUeb%2FGP5o%2BvJ8H%2FwAOZ%2FuJVfx%2F%2BjETwA8OhUVGi1Ug%2B98fNh%2FBgnN8hBRqKP7lTv4x%2FNFQ0ugm1qNODbf9EDc%2BqPruOADhzHKiVYeioH6MPrAuHX7y1b%2FWB%2BjAzfIYUiinlT5n8MPmgKTSE8qc%2BfS9%2FNH16%2BsC4dPvHVfgnyP5MQPADw6E39hKqP8AvA%2FRgZvkP7GUrkaa9%2BG%2Fmh7FUb72zH4f%2BaPryOAPh1ASn2FqpCeX6PP0YK4BOHYm4otVT5hPf0YGb5D%2BxlIAsKdNW%2Fy%2F80U%2FYqm3v4lM%2FhB80fXg%2BD94dTv7FVkHvFQ%2FoxD7H7w63v7FVj0eP%2F0IGb5E%2BxdO%2FvKZ%2FC%2FzRL7E04gjxGYueR6b%2BaPrz9j%2B4dfvTV%2Fx%2FwDowHg%2FuHcJCPYyskDlefF%2F4kDN8hjRKceUg98LhiBosj%2FeL34Ux9evsf3Dv97Kz%2BPj6EPsf3Dt96qwf3%2BPoQM3yHbplMSClynPLFtvdrWPqgqk0w%2BTJPp9Dv8ANH1z%2Bx78PG48Srtj2ePp%2FwDTiH2PXh3%2FALyrv4%2Bn6EDN8jvYql%2F3lMH%2FAEv80QNHph8mnzH4UH80fXT7Hxw8f3lXPx9P0IiPB9cPINxJVznc%2Fo9O%2FwDAgZvkWml01J3p79%2F8oPmiPsbSfvfMfhR80fXX7H7w8%2F3hW%2Fx9P0IlPg%2BeHcgj2OrQv%2F08fQgZvkUaZS%2B2nzFv8qPmiT2NpH3umPw380fXNXg8%2BHdX%2FI64P3%2Bn6ESnweHDsf8Akdd%2FHx9CBm%2BR%2FiFJG3sZNfhh80S%2Bx9K%2B90yP9MPmj64nwd3Dv2Ste%2FHx9CIfY7eHj%2B969%2BPp%2BhAzfI72LpWsL8Rf27Om5%2FJExp1ITzp8wfQ9%2FNH1u%2Bx18O9reK130%2BPJ%2BhEv2Orh6%2FUq%2FwDjyP8A04Gb5JeI0oeTIvj0u%2FzQ8Spf95u%2Fhf5o%2Bth8HTw9EW6Ov%2FjyfoRTPg5OHsm%2F%2FCD8eR9CBm%2BTBlKUU28RdHnDsSGkUhzdUnM%2FA6Pmj61q8HLw%2BnkcQj9%2Bo%2F8ATiQeDi4fxyexH%2BOo%2FwDTgZvkbOUyjU%2BQmKiulKdXJtqfShyYOhenfSoAcjyjW0mqVnKCpwyDkvUXam%2FMP6T7iphxCShCU80lCwrfkUqHdH2srfg0sh6vSZulJqOI2BNN6C4mbbKk7329zjAG%2FBP5fSq3UyeMJ%2Fo1G6OlIKgO7ZNoGb5HdAv9RVFWnSTiq1SAto6TUJc7jl7oOcfXP7Ffgz9eUz8QfRiH2K%2FByXG3UYzmQtpYcSdA5g3HvYGb57uU9Gtf6FR5R94O8xJ7HJ%2FvZPxBH0mV4OKnq3GPXQe%2FoU%2FRiU%2BDik1ABWYLx3uT4ujn3jqwRL5qT9FlptoNvMFuxvqRZJvFs9qtM7ETnwER9QXPBvUNxLiV41eXq3TqaT1T8CeUUx4NjD6eWNH%2BX3A59%2FkwQ%2BXrmDqQ55SJ74FCLXVsByjbLjkr4zdFylThG3Kxj6ujwbuGtRvjB%2FTfYdGm4HxYO%2BDYwk%2B2WnsYzpSpWo2Cb%2FB1YD5topBKG1GVRdTY1dQGxtzvEwobX96D1R9Lx4O3DSfJxhNXta6m0H%2BTFRvwd%2BFQbu4umjY32aRy7vJgPltjSly0ng%2BsTQk2xplFBJ07hRNgRGkmmujGhKFA%2BdJj7W1rwaeW2IJRqQqWK6ymWQ8l1aGFoR0gSbhJ6vKKZ8F7koskqrNbHcA439CA%2BLrbZsLkgjzRteh0SluUKRW7KOdMpvWXA5soHzWj6pI8F5kCNnKliEg87Ptj%2BRF1Y8G5kdLtNst1jEmhtAQkGYa2AFv1OA%2BVBolHK%2BozMpT51i8TGi0s6QqXmSO2yx8kfVk%2BDkyR7KriEf6dr6ESq8HBkio%2F14xGPRMNfQgPlO5QaTe7TE5a52UpPLsiT2CpXvkTg%2FaqTH1dT4OLJBP91cRH0zDf0IlHg5MmN%2F06xBv%2FAI1r6EB8pDQqOUm7c%2FfsOtO0R9gKKQnq1C%2Fvusi0fVr7HJkxt%2BneIdhp%2B3N2%2FiRA%2BDiyXVzrWIPwjX0ID5U%2BwFE%2FU5746IkFFo45szR%2F0iY%2BqyvBwZOe8rte%2BFbX0YonwbmUIPVxDXQP27X0ID5YCjUbslp3reV10%2FJEDRaSrmid%2BMmPqarwbmUh%2FwCcFZP7ZTf0YpOeDZysXYIxLWUAdiVti47vJgPlmqi0vsamz6VCCaLSzzZm%2FgUI%2BpP2NfK69%2FbHVfRdH0YlPg3MvQB0WJp9BCbbBAv6erAfLhdDp5Vfo50%2BcrTBNDpo8pE2f3Yj6gr8G1gdV7YsnzcW3Cdv4MUFeDUwb7zF038IT9GA%2BY66JRz5DM7y7XE8%2FVEgolLHOUfPpdHzR9NFeDUw17zGT3wtj6MS%2FY08PdmM1%2FC0PmgPmNO0dmaZEu0ksNjmE3JV6T2x4BhGWPvx8SPqSnwamHffYxWf9EPmib7Gthv9d6vwQ%2BjAfLgYQlwLh0j0Aw9qUqTZS3DbzR9Rj4NTDh%2F54uD%2FAEY%2BjEp8Gnh3WpftzcurmejH0YJiZjU%2BXftRlPunPVD2qMdil%2BqPqKPBqYdTbTjNwWFt2wdvVEPsaeHbf2Zu3t9wPowTuqu%2B%2BXRwkwT5S%2FVEwwkwBsfkj6hDwaOHL74yct%2Fkx80RHg0sOjljR38GPowN1PffLv2qtBWzhI9UTe1Rr7ox9QvsaWG739ub1v8AJj6MR%2Bxo4Z%2FXi98QfRgbqe%2B%2BXasLS57Fje%2B0Q9q8re%2BpV%2FRH1F%2Bxo4Z%2FXi98QfRiH2NSgI%2B14zX%2B6aB%2FkwRM5vmdJSlXp%2FRpl65MpQ0LIRpCkhN%2FJsRy80Wl%2FAlDfmlTqpd9t1a1OLDS7JKjzIB5R9Rz4NWg26uNFg%2F5MfRiI8Gph7txo7%2BDH0YIfM%2BUw7hqXb0CQnz%2B%2BEn80UJjCOD5pa3HZGoFSgRp6VOm3n2j6cnwauG7f2Zu37%2BjH0YgPBq4bsUqxm9Y%2FsE%2FRgPlunLbBzZ1NN1VJ7ukQY9AwTQUiwNS%2BOiPqF9jVwx%2BvB74g%2BjD7Grhj9eD3xB9GA%2BX3tMonYuo%2FGREqsH0AHrpqJ%2Fdoj6h%2FY1MLW%2Fsudv%2B0H0YgPBp4V99i534g%2BaA%2BXb%2BEaWpASJdS0dgdSFH5Iy3DGL8S4Tpwo8l4hNSTZJZanJYOFkk3OlXO3m5R9Fj4NDCZ54uf%2BKPoxIPBm4T1XVi163cEj5oD5%2FjMzFd7qkaCfMaePnideZ2KCQWZChNi24FPBv8sd%2F%2FAGM3B%2F67H%2Fij5ofYzcH%2FAK7H%2Fij5oDgBOZ%2BK%2BXiNCPpkB88QVmZi9aiTLUG3YPY0flvH0B%2Bxm4O%2FXXMeofRiZvwaWEG%2BWKn1ftgPowHz%2B%2BqTiw%2F8iof%2Brx88T%2FVLxdfV4pRL2ttTwPzx9BvsbmEP1yr%2BIPmiZPg3sIDniRXxB80B8%2BPqmYt%2FvSi%2FiI%2BeIpzOxckg%2BJUK%2Fb%2Bl4F%2Flj6D%2FAGN7B365V%2FE%2FmgPBv4O7cSLI%2Fa%2FzQHz6%2BqljD%2B8aD%2BID54kVmhjNR2lKGkd3sck%2Fnj6D%2FY3cGXv7ZHPi%2FwA0Q%2BxvYQB%2FsmXb9p%2FNAfPj6pGKe2Uov4gPniqnNHF6eUrRf9Xj54%2Bgh8G%2Fg7bTiRY7%2Br%2FNET4N%2FBvvcRrH7n%2BaA%2BexzPxiXelMrRL%2FAPZyfniP1TsU%2Feqgf6vHzx9Bvsb%2BEP1yL%2BL%2FADRD7G9hD9cq%2Fi%2FzQHz%2BczSxKs3TRKAjbkmS%2FniYZr4qHOjYfPpkP547%2BX4N3CStk4mWB%2B13%2FJD7G5hDVf2yrt%2B1%2FmgOABmxiVOyaHh4HzSZ%2BeKn1W8UfeHD34l%2FPHfh8G5g3sxG58UfNEPsbmEL%2FwBkq7ftf5oDgQ5vYstYUbDyf3j%2FADxT%2Bq9jRP2um4eHpkP547%2BV4NvCJ8nE7g%2Fc%2FwA0Q%2BxsYQPl4odP7n%2BaA4Bdzbxo4dQkcPJPmpw%2BeJF5uY5WnQZegAdwpgH54%2BgB8Gvg47e2d237X%2BaJfsauECetil0j9r%2FNAfP45rY4Vzboqf2tOT88Q%2BqnjbvpP%2Brkx3%2BPBoYPvviyYt6P6MSnwZuDyP7Lpm9%2B7%2BaA%2Bfy8y8cLOy6SP%2B70xT%2BqJjnTo8YpVv8As9N%2Fyx9BD4MrBh%2F53TXr%2FoxL9jIwd24xm%2Fgt9GA%2Bfn1QcaW3mad%2BIJiRWP8AGauc7T%2FxFMfQI%2BDEwdz9uc76x9GIHwYmEezGk58n0YD59px3jJP%2FAC%2BR%2BCSSPzxBeO8ZKN%2FHpL8TTH0E%2Bxh4RPPGs58n0YfYwcIfr1nfWPowHz3GNsYAhXjkiSDfeTHzw9vONNevxuncrW8RFvyx9B%2FsYOEb%2FwBm078n0YfYwcIfr2nvWPowHz2GNcaAWFQkh3ESSdt798R9uuNfvpJ%2FiKfnj6DnwYGEf17z3yfRh9jAwj%2Bvee%2BT6MB8%2BRjfGYASahIkA3F5FPzxSRjDGyfKrEqr94o%2BePoX9jAwj%2Bvee%2BT6MPsYGEf17z3yfRgPnmrGGNTcCsyoB7DIIiKcY4yTcipyBPYTTmzb1x9CvsX%2BEv18TvyfRh9i%2Bwl%2Bvid%2BT6MB89X8c48blnXWK%2FLyykp1XYpzCST8KTGlMQ1jF2Kp8T%2BJ6rUao%2BgaW1TBKggdyUjZI8wAj64P%2BC7wu6ytpOOJsa02ubfRix0XwVUrKz4VVcwULk77pYQQ5b0lNoDhHhX4XsWcSGPDg%2BlrYp8uzJOzk7OTKVFDDSSEi4AvdS1JSPhPYY7p4dPBlYnyxzRpmOMY4zpi5CiVJipS0tIBanHlsq1tpUVABKdYST2kbR2Jknw%2F5cZBUSYo%2BAqY4hyeUhc7OzKw5MTKkiydSrDYXNgAALmNkQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQCEIQH%2F2Q%3D%3D%22%20vertex%3D%221%22%20parent%3D%223%22%3E%3CmxGeometry%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%225%22%3E%3CmxCell%20style%3D%22vsdxID%3D3%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%2C%5B0%2C0.24%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22414.91%22%20y%3D%2279%22%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%226%22%20style%3D%22vsdxID%3D4%3BfillColor%3Dnone%3BgradientColor%3Dnone%3Bimage%3Baspect%3Dfixed%3BstrokeWidth%3D102%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D0%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%3Bimage%3Ddata%3Aimage%2Fjpg%2C%2F9j%2F4AAQSkZJRgABAQAAAQABAAD%2F4gHYSUNDX1BST0ZJTEUAAQEAAAHIAAAAAAQwAABtbnRyUkdCIFhZWiAH4AABAAEAAAAAAABhY3NwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAA9tYAAQAAAADTLQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAlkZXNjAAAA8AAAACRyWFlaAAABFAAAABRnWFlaAAABKAAAABRiWFlaAAABPAAAABR3dHB0AAABUAAAABRyVFJDAAABZAAAAChnVFJDAAABZAAAAChiVFJDAAABZAAAAChjcHJ0AAABjAAAADxtbHVjAAAAAAAAAAEAAAAMZW5VUwAAAAgAAAAcAHMAUgBHAEJYWVogAAAAAAAAb6IAADj1AAADkFhZWiAAAAAAAABimQAAt4UAABjaWFlaIAAAAAAAACSgAAAPhAAAts9YWVogAAAAAAAA9tYAAQAAAADTLXBhcmEAAAAAAAQAAAACZmYAAPKnAAANWQAAE9AAAApbAAAAAAAAAABtbHVjAAAAAAAAAAEAAAAMZW5VUwAAACAAAAAcAEcAbwBvAGcAbABlACAASQBuAGMALgAgADIAMAAxADb%2F2wBDAAMCAgICAgMCAgIDAwMDBAYEBAQEBAgGBgUGCQgKCgkICQkKDA8MCgsOCwkJDRENDg8QEBEQCgwSExIQEw8QEBD%2F2wBDAQMDAwQDBAgEBAgQCwkLEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBD%2FwAARCAGPCigDASIAAhEBAxEB%2F8QAHgABAAAHAQEBAAAAAAAAAAAAAAECAwUGBwgECQr%2FxABzEAABAgQEAgQGCQkQDAwFAQkBAgMABAURBgcSIQgxEyJBUQkUMmFxgRUWFyNCkaHR0hgZM1KSk5SxwSQlNENTVFVWYnKClaKywtMmNURzg4SFo7Ph4vAnNjdFRldjZXR1pMM4R2S08ShmdqW1SFh3hpb%2FxAAbAQEAAgMBAQAAAAAAAAAAAAAAAQIDBAUGB%2F%2FEAFIRAQABAQQEBwoICwgCAgMBAAABAgMEBREGITHREhZBkZKh0hQVUVJTYXGiscEHEzNCQ1SB4SIjJTI0NURicrLwJEVVY3OCwuIXJpPxNrPD0%2F%2FaAAwDAQACEQMRAD8A%2BqcIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgOB%2BN%2Fj%2Fq%2BVuLH8pcn3mWqzS1INWq7iUuIYdKQrxdCFJIWQkjUew9XmDblH65RxOaNQzMp5I8oex8uCPjRGj%2BIqemp%2FOHMCdmnluTDmKaoouLVuT424N40%2BtyA7Sb8JLxOOLA91GmpB33p8tYW5gnTHic8JzxPl9Yax9KabqSm9NlwPTfTHGqzcX7gYpm6uZB9JgO1HfCV8VLTiks48l30fBWaUwm49GjviT65bxXX%2FAOPEv6qUwf6EcqymYOIpCTbk0iVdaYSlCekl0qISBYDzxU91HEf62kPwVMB1R9cy4pxzxox%2FFbH0IHwmHFOtSy3jdm3cKSwbfyI5WOaGIleVKyB9MqmJDmbiXfSiRR3WlE7QHVP1yzis7cct7%2F8AdDH0IfXLuKs8scI%2FiiX%2BhHKwzQxZyDkr5rSyBAZoYt59PKj%2FABdJ%2FJAdVfXLeK0c8bN%2FxQx9CIjwlnFWrljVP8Uy%2FwBCOVjmhi4i3jEv%2BDp%2BaKZzPxeD%2BiGvVLo%2BaA6wHhKeK48sYj1Uhj6ERX4SXiwI6uMFD%2FIzB%2FoRyYczsXE6vG0JNrdWWQPyQOaOMTznQf8AApH5IDq8%2BEn4sxzxgr%2BJmPoRD65VxY9uMF%2FxMx9COU%2FdPxj%2Buh96T80PdRxmP7rT95T80B1inwlnFbpsnFJWf%2FJmfoREeEu4qeRxPv3exDH0I5MOZ%2BMFH9GBJ70tAfkiVWZmMrdaoesMo%2BaA63%2BuWcVx5YiV%2FE7H0ImHhJ%2BLA%2F8ASM%2FxOx9CORRmXjL9lFj%2FAAafmiPukYxP%2FO7gP7xPzQHXY8JPxX%2FtiP8AFDP0InR4Sjiqca6lfuq99QpTPLutojkIZkY1T5NZcHobT80S%2B6Rja9zWHye%2FYfiEB179cl4sf2wf%2FwAJY%2BhEfrknFn2VvV6KUyf6Ecg%2B6Rjf9mH%2FAIk%2FNEpzExornVn%2FAFWH5IDr5fhJeLQ%2BTXFJ%2FwAksfQiX65Nxab%2FAJ%2FHbn%2BdLG38iORRmNjRP%2FOrx%2FfAH8YiT3QcZ9lYd%2BIfNAdfJ8JNxanf2d1D%2FwApY%2BhFRPhLOK5xWhFXUD56Qz9COPTj7Gat1VqZ27rD8kFZg40WnSa3NgeYiA7EHhKeLBStAq6SfPTGR%2FQh9cl4tP2UH8Vs%2FQjjg4%2FxkP8An6c%2BMfNEDj3GR516cPrHzQHZP1yXix%2FZf%2F8AhLP0Ij9ck4sf2W%2F%2FAISz9CON%2Fb9jC1vZ2b%2BT5oj7fsaXCvbBOXHI3G3yQHYx8JLxZfst%2FwDwln6ESK8JLxbDnVrD%2FwApZ%2BhHHwzDxqkaTXptQ7jY%2FkiCMw8ZoBSmuTgB7Li34oDsEeEl4tQbGrgemlMj%2BhE6vCS8WY5VX46Uz9COPfdCxpa3s2%2FbusPmib3RcajnXHztbcA%2FkgOvvrlPFmOdUH8Vs%2FQiqnwkvFqvyZ9J%2FwAmM%2FQjjwZj40ShKDW3ilNrDbs5RJ7o2M%2F2bm%2FjHzQHZP1yLi3%2FAF4j%2BLWfoRBfhJOLZs6VzgSe40xn6Ecb%2B6NjT9m5z4x80TjMLGwSpCK3MpSrmBAdiDwk3Fr%2BvRb%2FAMtZ%2BhD65NxZnlPpP%2BTGvoRxx7fcZjf2dm7%2Br5oj7oONORrs4PQoCA7H%2BuS8Wf6%2BT%2FFjX0IivwkPFs35dQSP8mMn8SI42OP8Y%2Fs5O%2FdxIcwMZ3v7OTP3Q%2BaA7MPhIOLhPlT6R%2Fktn6EPrkfFrfT44fT7FtWPo6kca%2B6Jjb9m5r1EfND3RMbfs3O%2FdD5oDsz65Fxaj%2B6VH%2FJbQ%2FoRFHhIuLa9lPk35fnYz9CONhmJjIA667OEntKr3ikMw8ZXP57zVj2A2vAdp%2FXHuLPQR0x132%2FOtnTb06YkX4SHi0Pkvgf5Ma%2BhHGAzExkOVWmh6FxN7o2M%2BytTg%2FhfPAdmHwj%2FABbpAPToN%2B6ns%2FQiUeEk4tD%2FAHQkemmtD%2BhHGgzFxolWpFdmknzEX%2FFEpzAxiedZmvurfkgOzPrkfFr%2BuUfxc19CIjwkfFqo6UzKSe72OZ%2BjHGSswMZrveuTYubmy%2BZ%2BKI%2B6DjPf8%2Fpvfny3gOzvrkHF2DpLo896az9CA8JDxc9ryBbvp7IP8yOMDmFjEC3szMkdoJiU5hY0P%2FO8zty3F4DtH65LxZfq4%2Fixr6ED4SLi3HkuBf72mtfQji%2F3SMa%2Fs1M%2FJFX3Tsb%2FALOzA9AtAdmnwlXFihSdTaRqPbTm%2FoRMfCW8VX2qP4vR9COLU5l43bXrark0g94tEDmXjg%2BTXp0elQ%2BaA7T%2BuXcVPc3%2FABej6EQPhKuKwdYqSAe6nN%2FQjiwZk452vXZo25XsfyQOZGNCQTWZrbl1rWgO0E%2BEz4pFmyXGie7xBv6EVPrlXFX9qn8Ab%2BhHGHulYyI0GvTiU%2BYxT90nG3L2dm%2FjEB2n9cq4q%2FtU%2FgDf0InX4SbiuRbZBvy0yDZ%2FoRxUMx8ZjlXpwbW8r%2FVEfdIxmdIFdmxp2Fja21u6A7RR4SriuUvTYfxe39CKi%2FCR8WKPKSn%2BL2%2FoRxR7oGMLW9npq172v2xD3QMX%2Fs3NfdQHazfhJuK937GhBH%2FgG%2FoRX%2BuT8VZ%2FudscrfmFve%2F8COIRmBjAbJr06PMF7fiidOYGM0iwrs3b98PmgO2z4SbisHOXa%2FAW%2FoRIrwlfFSlWky7Y9Mi3b%2BZHE5zAxiTc1uav%2B%2Bh7f8Y%2Fs1NfdwHbI8JVxV%2FrZo%2F4k39CI%2FXKeKo8pVv8Cb%2BhHEozAxlf%2B3s593E%2FugYx%2FZ2d%2B7gO1%2FrlHFYOUoj8Cb%2BhD65RxWDlKo%2FAW%2FoRxKcf4zvtXJ375D2%2FYx7K3O%2FfIDtr65PxXnlKI%2FAW%2FoREeEi4sTv4qg%2FvZFq%2F8yOJfb7jD9nZ37uI%2B33GH7Ozv3cB2yfCScWIO8in1yDf0Im%2BuT8Vg%2FuBs%2F4m39COIzj7GnL2dnrf3yJDjzF%2FZXZ37u0B2%2F8AXKuKz9jm%2FwADR9CH1yrir%2FY9v8ER9COJPb7jM%2F8APs790PmgMeYyHk1udH8OA7b%2BuU8Vn7Htj%2FE0fQh9co4q%2FwBaMj%2FE2%2FoRxL7fca%2Fs3N%2Fd%2FwCqIpx5jRPKuTv3yA7aPhKeKlJ0mSQVdwkkH%2BhER4SfirHlU9PrkkD%2BhHEvt%2Fxp%2Bzk592Ie37Gn7OTv3YgO2frlPFV%2BsGvwVv6ED4SripH9wI9Um2f6EcSe3rGNtPs3O27ukiKcd4xT5Ndnh6FwHbH1yzin%2FWSPwFH0Iqjwk%2FFUjy6e0dtW8o2NvuI4l90LHA2GIJ775Epx%2FjVQsquTh3vusfNAdvJ8JfxSLQCmlS%2B5sD4qnc%2FcQPhK%2BKgC5pbHqlEH%2BhHDxxzi9S9aqxOFXO5cionH%2BM0eTWZsefXv8cB279cs4pP2OZH%2BJo%2BhBPhL%2BKFStHsfL388okf0I4iVmBjZaQhVendI7NYh7fMY6NHs9OW7tUB26rwlvFMjyqOj8DR9CIDwmHFErb2Jbv55NH0I4jOPsZjya9PJ9C4icwsbkkmvTpJHMqHx8ucB26PCWcUJ509kemSR9CIJ8JZxSLbLqaU0UJNifE0D5NF44iOYGNVJ0muz33yIDH%2BNQor9nZwqKdNyu5t3XgO3vrlnFJa%2FsZL%2FAIKi%2FwDMiX65fxRlZQilMrI56ZRBt%2FIjij3SMd3v7Pzl%2B%2FUPmiRzMPHTgIXiGeIPZrAgO4FeEy4n0eVQG%2FwRP0Il%2BuccTZOn2AZv%2FwCGT9COH%2Fb9jX9nJz7uJjmFjUo0GuTmnu1wHcJ8JfxPgXNDYHm8WRf%2BZEUeEt4oHPJoTX4In6EcOjMLGoN01ubB7wuAzCxuLWr89t%2F2kB3GfCW8UKfKoLY9Mon6EQPhLuKBI1GhMAXAuZZO1%2B%2FqRw8cxMdKJJxBO78%2FfIl90LHH7PTv3cB3MrwlnFAhQQrD7Goi4Hi6bkfcRI54TDicaQlxdDZ0r8kiVSR%2FMjh8Zh41S30Qrs6E9wXtEfdHxz17V2c65urrjc98B26PCY8Tp5URn1yifoREeEx4nR5VEZP%2BKp%2BhHD%2FuiY3%2FAGdnPu4e6Jjf9nZz7uA7lb8JdxMr%2FwCYZY%2BllI%2FoQR4THiVUSn2Alkkdhl0%2FQjhkZg40tY1ucI7iu8VDmNjUp0GuTtvMofNAdwJ8JnxKrcLaMPsqI7pQfQib65hxLX0%2B15i%2Fd4un6EcPrzHxstOldemyO7Vb8UURmHjhKdCK%2FOpTysF9kB3M54S7iYb8rDzPqlkn%2BhEv1zTiT7MPsH0SyT%2FQjhpvMHG7Ru3XZtJ8yomOYuOVX116cVfndcB3H9c04krXNAa9Hiib%2FwAyH1zTiSt%2FaJgdvWlk8vuI4fOZWOlqCnK5NEgWBuBb5InOZONzb8%2F5oW9HzQHbg8JrxJqGpNCliO8S6foRA%2BE04k%2F2Elh%2FiyfoRxIrMnHayNWIZqw7AAB8giYZkY5AH5%2FzRty6wgO2nPCacSTK9DtElkHzyyR%2FQj0fXNuI61%2Fa%2FK%2Bjok%2FQjhr3R8a9a9ZnDqNzdQNzE3umY5vq9mpm%2FfZPzQHcB8JzxH67DDjB9DA%2BhEfrm%2FEhY%2F2Ns%2Fg4%2BhHD5zLxyRqNdmr%2BqJfdMxxy9nJr4%2F8AVAdwjwm3EgBq9rrB83QD6EPrnfEf%2B1hr7wPoRw97pWOQf7dzfyfNEwzOx1%2BzMz8SfmgO3VeE94jkbqw0yB%2F4cfQiY%2BE74kEmysMtj0y4%2BhHEAzNx2OVbmx6xAZnY7H%2FPc38kB3APCd8RyhdOHGDbn7yPoROPCccR%2FI4bl7nl7yPoRw63mjjpC9Rrcz6CAfyQVmdjlaiVVmZ37gNvkgO3V%2BE84jE7HD7AIO9pcH%2BhFVrwnXESr%2Fo3Kq9LaR%2FRjh5OZuOU8q5NfEn5oJzNxsj%2FAJ4eV%2B%2BSk%2FkgO5keE44il6tOFZbq8%2Fev9iKTvhQ%2BIRlQSvC0tv8A9l%2FsRw8rM3G6yFKrMxcctIAg3mZjZtvok1qZ09xtAdyq8J1xFFGtGE5e3eGwf6Eeb66LxC%2FtXl%2FvP%2BxHEiMz8bo5VZw%2BlCTFNWZ%2BNyb%2BzL9%2F3o%2BaA7hHhQuIcjUMLS1vO1v%2FADIj9dC4hv2qy%2F3n%2FYjh45o476mirPJ0crITv6e%2BInNPHJ3cqzx%2FgJ%2BaA7iPhQeIQc8LsC%2F%2FAGH%2BxEp8KHxCjnhiWAH%2FAGP%2BxHEAzWxt%2ByCt%2BXUERGamNefskrbndsQHbg8KPxAKTqTh2UI8zP8AsRL9dKz%2FAL29rkp96%2F2I4nOa%2BM1c55P3kRJ7qeM73NQB8xZSfyQHcKfCnZ7q3GGZE%2BhP%2BxBzwp2e7SlJcwvKAp5jQNv5EcPLzRxgsAeOoABvswn5onRmxjRsdWdbPpYT80B22fCp55%2FBw3JetH%2BxER4VPPM%2F9GpL1I%2BdEcRnNvG6lX8aaHoYT80FZr40WbmfSB9qGEAfigO3VeFPz0QnUrDUl9yPoRA%2BFSzzSDqw3Jju6nL%2BRHEfup4wtbxpoj%2B8o%2BaIDNfGCb2da35%2B8J3gO2%2FrrGd2rSMNyaje1gkHf7iJk%2BFVzxN74WlBbndHL%2BRHEhzcxkRpLrJHnl0bfJEhzYxjf7K395TAdv8A11TO7sw3JH0Jv%2FQgPCpZ5KBthiUNuZCOX8iOIkZs4wQm3jDB57mWSfjiZGbuL0fp8ufTLJgO3G%2FCpZ5G39jEqq3OzY3%2FAJETHwqWeWr%2FAIrSgHdo%2FwBiOH3M28XOcnZdG%2BrqS6RvD3WsX%2FqrP3kQHb6vCrZ4JAUrCcoBa5JHMfcRBXhU88k2WrC0kEnldP8AsRxB7reLraStkjzsgxA5rYrVzMqfTLiA7gX4VXO9Hl4Yk0%2BlH%2BxEq%2FCs52o54YlOV%2FsZ%2BhHEXus4stpLksRa1jLpO0Dmxi1QIDkuAewS6doDttPhWs7V%2BThqRP8AB%2F2IirwrGdyTpVhqQBtyI%2F2I4lbzcxg35K5T1yiPmiVzNjFyzq1yl%2B8yiT%2BMQHbjnhWM707pw5IlIJBIQfj8iKY8K7ndr0%2B1uRUO%2FQR%2FQjiT3V8Zfrtj8HTEgzTxYnk4xzv9gTAdwjwredqhqThuSIUbAhPb9zE%2F12DOkHScJyRO3f8AQjh0ZvYuSpSguVGrnaWTEHM3cXOk3fZAI8kS6bfigO4x4WHOjyfanI3uO%2B%2F8yIjwr%2BdVwDg%2BUBJsAQQSfuI4bbzbxa2RZyWNr3vKIN9rd0TO5vYrdSlGqWQlIAsmWT2ct%2BcB3EPCvZ1KcUhOE5HUjykgKuP5EB4WDOdZs1hORXvY2uLfGiOGfdYxTb7LL9U7HxdOr44e6xilTZQVyllHf8yoveA7nPhXM7Bf%2BwuVFueoH6ESK8LBnS39lwjIN7fDuN%2FuI4cTmxihABSiTuDe4lkg%2FJEHM3MVuDT%2BZEi1tpZP5YDuP67BnSSVDCcgU9hF%2FoRVR4VjO94ktYSkLW35%2FQjhZObmLbaBMMbCw%2FM4ioc2sUHykSazzBVKpuDAdyHwrWdYKknCkldPlWSo2%2FkQT4WLORKOkVhOQKEmxNyB%2FMjhlGbeK0q1KMqra1%2BhTe1rfigrNvFawUqdllAixCpZJBHxQHdCfCzZvlWkYOkSe7Ur6ETJ8LFnEq2nBkodXLyvoRwoc1sUqIUpUmSFhwEy6eY9XLzRMc28XggpnWE2FrCXRAd2q8K9nE3zwfTz%2FDI%2FoQT4VrOexBwZJE%2BlW38iOFBnBiwgIWqVUkAgDxdHKI%2B7Bim50OSiARY6ZZIv5%2FT54DupHhW86F%2BRgiTV%2B9KvoRD663nJc3wbJfGr6EcLrzexSsqUp6WuvnZlI%2FFETnDiw83pU733YTAdynwrmcV7jCMkfMLn%2BhA%2BFbzoBCfaVK3O42VuPuI4aOceK1eUqR%2FBEmJTnDixWypmXIta3i6bc7wHci%2FCx5whVvahTr9wWT%2FQiZHhX85Fm6cGyRHdc%2FQjhv3XsT6QA3IbcvzEmIrzgxUsWS3JI8yZRIH4oDuZzwsOcLZKfaRT1Ec9LhNv5ED4WPN34OCpE3Fxcq2H3uOGPdbxdcqvK7ix%2FM43ERGbWKU3sJQEixtLJ3gO50%2BFizgPLBEgbqsLKV9CIq8LBnEnngaRH8M%2FQjhj3W8V7XbkzZOkXlwbCHutYq6Po9Mrb%2Fw4gO6keFezgX%2F0IkwbbAFR%2FoRIvwseb7IBcwPIC%2F2zhTf%2BRHC%2FuqYoOx8WBt%2BtxcxH3VsUKASWpVR7NUsFQHcw8LLm924JkD%2FhD9CJleFkzbQ2CrB9NCr%2FAKoq%2FwAWiOGk5uYvR5KJQf4smJPdWxT%2BpyfK36HHzQHcn12bNzY%2B1Cnfdq%2BhAeFnzeKSE4JkCewhav6uOHhm3ilOoiXk7nkfFkm3yRD3YcV7am5M25fmYAfEIDuZvws%2BbSfsmCaaSrld5Q%2F9uJl%2BFozUbIDuCqag2JsXVfQjhQ5u4oUgIMvJkA9suN4nVnBitd7y1O3NyTKpJ%2BWA7mT4WnNdZ6uB6bbu6VX0IiPC1Zq7n2h09XodUf8A244W91jFBIUqXkCAnTbxRNrQ91zFt09WS6vZ4omxgO6R4WbNxQuMAyQHeVL%2FAKuA8LPmuqyW8FU1a%2B1AcVcen3uOGk5u4rupRZk7r5lMuBEnus4sN9Tcmvzqlhf4xaA7pPhac1GiUu4JpgNuReUP%2Fbh9dozWVpCcDU7ft6RRBvy%2FS44XGbmLBfU3JquLEmVTc%2BuIHNrFaiLsyhAN7FgW%2BK0B3WrwsmayEJK8E04XvzcUP%2FbiT67VmkfJwVTVeh4%2FQjhj3W8XHUF%2BKqCuxUsk2iX3V8Sp3TJU4f4omA7vb8LJmslxKl5fySkg3KelULj09HEx8LJmooJtgGnpve3vqjf%2BRHCC83cTLWVrlpE3BSR4sLEHmIkTm1itPZKeqWSIDvJXhZM1UAKXgKmpB5FTyhf%2BREp8LRmgEgjA1MNz2TB%2BhHCQzdxTbrolif3TCVAeoiDebeJUC3i0gfOJRIMB3WvwteZ6ClK8DUxJUdKQX1bn73ER4WbNVZ0owFTie4Or%2Fq44WGbmJbk9BJ7i1vFk%2FND3XMUhICW2E2N7pZTv6doDulfhZ81UHT7Qqbfu6ZQ%2FoRD67Xmh1T7R6Rc3unxlVx%2Fm44VObeJe2Xkzvf8AQ4iPuu1%2F9jqcfOZVJPxwHdf12nNI20YBpir8rTCt%2FwDNwPhas0G9ncC0xBHYp9Vz6Pe44PezYxM5ptKyKLG5tLDn%2BSIqzaxGu2uWk1W5XlUmA7v%2Bu2ZmJFzgqlehUwpP%2FtwT4W7MtzdGBKXbttMLP4m44QOb%2BI3equUkVJ5aTKJ%2BaJhm%2FiW2hEpIITy2lUD8kB3d9duzLJOnAdMOnn7%2Bvb%2FNxD67dmYo%2B94GpSrcwJhf9XHCfuw4sa6rTUhb91LJPqikrNvFKxdTMkjzplUi3yQHeSvC3Zljf2hUy3aS%2BsW%2FzcR%2Bu2ZmgajgKlW7CJlRv%2FIjgv3V8UjqXZIVz1SiDb5IpnNPEgsCmWcCfJSphOn4rQHe%2FwBdqzPJGnAVMt23fWP%2FAG4ivwteZoNxgClgdwmVn%2F244JRmzidNxaUIJuQZZNvRyib3WcR3KixTzfs8TQLQHeX12zM%2Fn7QaZ9%2FX%2FVxE%2BFrzOSpOrANLFud5hdj%2FAJuOChm5iVLQYEvJ6AbgeLJO%2FwAUSe6ziG2lTcoodxlkQHfH12vM8csB0hW2rabVy%2B4idPhbsylISU4DpB1b9WbUT8XRxwErNjEa7FaJI25DxRHKCs2MRBsAtSaQk7FMqgE%2BYQH0A%2Bu3ZkJOn3PKYtR%2B0mlEj1dHED4W%2FMdIurAFKSbFRBm1XH%2BbjgAZu4iBv0MlfvEsgH4wIkXmxiRw6ldFe9yRLo39PVgPoH9duzKDYWrLim2JsCJlZufvcB4W3Mi9l5d09JO4u%2Bu%2F%2BjjgAZu4nA2W2Dtyl02FuW1onGb%2BKDbX0CrG%2FwCh0i8B38rwtWZCEBRy8pgJ7FzS0lPxtxKnwt%2BYxRrOXtLTva3jaz%2F7ccBqzZxCslS5eTVc3sZZJsfiiJzexQSCVSxI23lk7ju5coDvz67ZmSrdGX1LP%2BNr%2Fq4gjwt%2BZClpT7nlN6%2Fk%2Fmpf9XHAfusYjHkpkx6ZZBgvNzE%2BsKQ5LthIHVRKIty9EB38fC2ZjncZe0ob2%2FRav6uIo8LTmSVG%2BXtJ6o3BnFD1%2FY4%2BfKM1cSISGwWCkcgZZFvxRUXmriJxNleKctP6EbuB8UB9BVeFszFbXpOXVKULXBE2sX832OH12vMRRJGXVKSB2GbWf%2Fbj58HNbExQWi60Um23i6ezl2RFOauJ0G4dTzvbxZFvxQH0FPhbcxNQHueUkJ7SZpz%2BriZXha8wwEqGXdKso23m17bdvvcfP4Zu4nvqIlCf%2FCoB%2FFETm9ipSejU3K6L3%2FQqCfxQHf58LZmJzGXVJA%2F8Yv8Aq4k%2Bu35i%2FwDV1SPwxf8AVxwIjN3EaBp8WkyLad5RPL4omGcOKEfY5SnAeeUHzQHfo8LVmJo1nL%2BjbGxAnVkjz7N8oHwtWYadOrLylDVyvNOf1cfP9OcOLEeQ3JJ3v1ZVI%2FJEpzdxUrym5M%2F4smA%2BgZ8LPmINV8vaR1Rc%2Fmxf5W4lT4WrMVSSU5dUo27BNr3%2FAM3Hz8TmxiZKisNygvzAlk2MTqzdxQtJQGpNNze6ZZIt6rWgPoK34WrMNsBT%2BWlMCTtdU4tPxe97wHhb8fKTq9zOlWNtzPLHP%2FBx8%2FRm1ivQlOiUskWHvCfmgc18RptqkpHY6heVQd%2FigPoB9dxx4Tp9zSl37vHV%2FwBXFVPhaMfqF05a0tRAJI8ccFrf4OPn2rNrE6h%2Bh6cNrbSifj5RA5uYtPlCVUf%2FAA6YD6Br8LZmChxKPcypQChe5nnBbzW6OInwtuOxyy3pJN9O08v%2Brj5%2BHN3FahpKJaw5e8J2ij7qWJbqVpl7qNz%2BZkb%2FACQH0KPhbMeC%2FwDwb0nmB%2BjV%2FwBXA%2BFtx2k75cUgecz6xv3fY4%2BfIzbxOLa5eTWB2Kl02MQVmzWySr2Mp4JtezJ3tAfQZPhbMfHY5b0dPbvPL%2Fq4gvwtmP0%2F%2FLejnt2n1%2F1cfPlWbldOy6fIK7N2YgM1a0vcUqRH%2BC%2F1QH0J%2Bu1ZgqsBlxRQSdOk1Fd7%2Fe4m%2Bu3450kjLSjXBIsak5%2FVR89VZoVpeyqZJn%2FBxT90erISfzulBq%2F7OA%2Bh6vC345R0g9zKjK6IAqUKmvSb8rHot4iPC3Y5IAGWdFud96k4Leb7FHzqOY1WPlSMsfS3EnujVT9ZSv3uA%2Bix8LhjhSUrbyyo5CrkD2SXf4uiidPhb8a6QVZaUjc2Nqi5tt%2Feo%2BcSswKko3LDF73HvXKIe6BVP1ux9wYD6Pq8LZjUeTlxRlWNjapLNu4%2FY4lT4XDGilaV5bUdH76ort%2Fo4%2BbjmN59xCkKl2BqASTo3IEeVeKp9flb%2FwAGA%2Blx8LbjNKSs5c0TYXsKku%2Fo%2BxxH67ZjLpA37ndE3F7%2Byarcr8%2Bjj5lLxDOK7O2%2FKKBqz7h66doD6c%2FXb8ZWBOXNEBsSQamser7HE6fC5YvSetlvQ1C1%2FwC2a%2F6uPmH7IudmoeiIGfePa5AfT8eF1xUVIHubUGyxfeqOben3vaJvruOLLqHubUDq%2FwDerm%2Fo97j5dmoTI5FXriHslM9xgPqMPC4YsWoJRlrQCT%2F3qv8Aq4mR4W%2FFS16Pc5w%2Fe5FvZVz%2Brj5b%2Byc1tz9QiKZ2YUTbpCQLm3dAfUf67di61%2Fc2w%2Fe9iPZZdx%2Fm4m%2Bu14tJt7nOH79p9ll2H%2Bbj5aLqbmkJ61xvEzdQfUQTq1c4D6kK8LXi9LXTe5th%2B17WFWXf0%2FY4L8LXisAKRl3h1QJt%2FbZdx%2Fm4%2BXPsi53qicVB3sKjAfUVvwtOLF6bZeYcTfmTVl7d36XEU%2BFqxcVb5cUAC9t6qv4%2FscfLk1B%2F4aFiICfX2BcB9S%2FrteKtake5ph3qgG%2Fsyuxv%2FgomHha8Thzo15a4f9Iq6yPj6OPlp4%2B73Kh4%2B%2F2BUB9SVeFrxQG9fuZ0AkmwT7Lr28597iP12rE%2FX%2F4NsO9QX%2Ftw51vR71vHy0M4%2BTfr%2BqHj7o7FfFAfUseFpxQpGv3NsOeSFWNYWDv2fY%2BcQ%2Bu2Yl0avc1w%2FfVpt7LuX9P2PlHy18fe7lfFD2QdHYr4oD6lq8LViXWoJy2w9pRa5NXX1vR73vD67Via6f8Ag3w7ZQJH57ubW7D71tHy29knuV1fHD2RmO9UB9SV%2BFqxOhOr3N8OEbcqw52%2F4KJh4WnEg6TVlvh89GARarr69%2B73vsj5ZGpvdpPxQ9lHe8%2FFAfU367PiW6U%2B51h26u32XcsD3H3rnEw8LViE2%2F4NsO7kjesuDcf4KPlkmpv9iFGJlVN3TulQ9UB9S%2FrtWIffD7muHuoLj8%2BHLq8w96iP12nEBcS37nGHEhSAvUqsuAAn4J965x8sPZRz7VXxROKmr9TPxwH1LR4WqvrAPub4eF%2BYNXc2%2FwA1ER4WnEBv%2FwAG%2BGxpJSsGtuBQI83Rbx8sjVZj4F4lNVf%2BGi8B9UHPCzYjStaUZbYcXpFwfZlwBXo96h9dlxLpSRlrho3Ok2rbhsfvUfK72Vc%2FU%2Fkh7KufqfyQH1UPhX8VWujLHDa%2BrqFq4vfzfYucSp8LBi1V%2FwDgvw1sbbV1Zt5z71Hyt9k3juG%2Fkib2Ve%2B0PxQH1SPhXsXFtbjeVuHFhCiLezi7m3m6K%2Frib669i0hxQypw4ehSFL%2FsgUNj6Wt4%2BVyaq92oPxxBVUcPePXAfVJrwsOJ3SB7l2GUg9pxCvb%2FADMQHhYMWqQpacpcPHTe4FfXfbzdDHyrNSeJupsKHn3iYVJQ5NesDlAfVL67Bi0uJaTlLh1SlJ1C2IV2%2BPoYnHhWcaFBd9yLDYbC%2BjKvbIeffboeXnj5V%2Byh%2B1v6RERVDfZv4hAfVH669jHe2UWHDY2H9kShf42YijwrmM1nScocOJN7b4lP9VHyxFSctyMU1VJy%2FIwH1UPhWsZJWpJyhw71ef8AZGf6qA8KzjYgH3HaBYi%2F%2FGMjb71HysFSX2oB%2FHE6ai4dw1aA%2BqI8K1jS2r3HKFuQB%2FZEd%2F8ANRBXhWscBKj7jFDHRi674j5D71Hyx9knftDEwrDqO0iA%2Bp%2F11jG2rT7jNC%2F%2FAOjP9VEE%2BFaxobXyVoxv3YiI%2FG1HyzFcmPgqUPSAYrpxC8n4CfuID6gT3hacRU6VMzN5N0xOl7oVJTXiojq3v9i5eePE14XyvutqLeTVMUq402rauXn95j5lT1Wfn220KSkJbJIsgDePCSu%2Bo2H74QH1MT4W3E5Rr9xam27zXCP%2FAGo2VkZ4TjC2Y2OaZgTMDBJwu9WZhEpJ1BmeTMy3TrIDaHNkqQFEhIVYi5F7DePjahSFeVpPoEZBhGZdla5IvSqy043MNqQpHMKCgQR64D9KUIQgEIQgEIQgEIQgEIQgPzu5%2Bf8AKrjf%2FwDeSpq5%2FwD1bsandjaufm2aeOB9riOp%2FwD3bsaqcgPXQ6Y5VZhEuhxtsFY1uubJbRzKr%2Baw27bxkntfkEbBT7g1eWQE3HmHZfnHnw115DpPtfe%2Fii6wHiRQaPyWJjn2LHzQ9rlE%2FS2ppSvOtPzR7eUQ1%2BfTAeH2uU%2F7Rz40xA4ZpZXbQ9b98n8ce%2FX%2B6vEOkMB4fa1TUpult0G%2FMrSYmOH5EHT74R3C0e4dbY374lPO4BHogLecNyF%2F06%2FnKbRFOH5BJsFL%2BNMe1RPK8EuFOxV6oDxOYekV8tZ9Fop%2B12QR5Rc9ZEXLWPPDWO8%2FHAeEUGUt8Mj0iBw1LPHZDqSf3YsI9oNtwSPODeI9JfZKtQ7Cb7QHgOGpZHV64I7dSYm9rkoeaXFehSY9wK%2BwD1fjiKSRcqUogeYnfu23vvAWxeGpY%2BT0qfWkwGGpUc1OH1iN24s4Ys4sD5dPZn4soMpSaSwwy%2B9LTE6gVBtDywhrVLi6klRUDYm4G5tGpO2At5w1LadmXLd%2BoRAYZlVHcuJ7t0xckk32JB7jygpVjyue%2FugPAMLS%2FwBu58aYmOGJZvVrLl%2Fg7iPaHF90XSh0asYkq0nh7D9MmKlVKi6liTk5dGp19w8gB3cySdgBcwGOKwywdwtwesRD2uS%2F26%2FjTG0s48ncU5JYjp%2BFcVVSkzs9UKY1UymnP9KJcLJHROciFApO%2FIixFxGBkKQhala1BHWIHPaAtQw3L%2Fqiie0ak8omXhuWCdnFJ9Yjb2POH%2FHGAMC4azMmXJGq4bxLIsTfj9NdLrcit1N0NPm3VPZqF06ri9xHjyfypnM3cSTeGpbElGorspJGcDtSe0B%2F3xKA00Oa3LqvYdgMBqhWGpU8nV%2FEIqt4WliLl1fyRuDEOQeOqLnH7h9PZlq1iF4sLllSSz0TjLrQc6VSlAaEpTfVq5WjJcyeE7MPLXCE7jdVXoOIKfSV6Ku3R5rp3qeOWtabC6QTuRuOZFoDn32rSdvLc%2B6EUzheT%2FXDo9QjbNQyVxRT8mKVnqtTT1Aqc%2BqSWyyFLflE9IW0PuAC3RrWNIsb3t3xHNbJDGuTkhhmaxmZNp%2FFEk5ONyrDup2TUgp1MvDkFgLSdrjcjmIDUvtXk%2F1y78QiY4Wkh%2FdLo9QjamBcqVY5ewhSG8VUmh1DFPspOrerD3QykpT5RSW0OFXNTjrgdCU9yB3x780MhsW5bZhUzLhxbFeq1blmJiminaiJjpVFKUgKsQbi5v2bwGnBhWR%2BFNPn0BMQOE5E%2BTNvD0pBjpTFPBfmnhfCFQxIuo0GpT1Ia8ZqVHp03001KM2uVEclEC5IHcbXjE8ouHbHGcVNnsR0iepNFw9T3Ogdq9WmOiYce2u20OayLi52AuO2A0ycJUscpqYV6gIiMJ0z9UmfjEbZx1kbjvLzMOlZa16WlzO116WRSp1t28pPNvuhtLiF9gSo2UDuPPcRfn%2BGTMKWz4ayGL0kqdeZ8eRV0lXiIp4Tdc2VWuEJUCgi2rVYW3gNE%2B1Km9r8wR3XTEfarR7eVMfdiM4qGBqlI5oDLB9aXJ1OIW6Atxs9UqU%2BlsuJ8wBKvVGw8EcLONc0qVXcWZd1Wjv0CQq9Rp8h7IVBDc5MtyqiAtTaR1dYAIvYb%2BuA0J7U6P8Aq0x90Pmh7UqP%2BrzH3Q%2BaNj5XZPZg5x1d2j4DoZmlSiQucmnlhqWlEk298cOwJ3sBcmLxm%2Fw%2FY6yTl6VN4um6LMM1hbrUuafPB9QW2AVBabApFiLG1jAaiThGlJN%2BkmSP36fmgrClKPJ2YHrSY2RlDlZXM48atYIok5KSMwuTmJ0zM2FdEhDKQSDp3ubgCKGa%2BWtbyix5PYCrc3LTkzJsMTHjEqSWnEOthabX3BG4II7IDXhwtSB%2BnTHyRJ7VqVqv0kzb98IuR5wvfY7DvgLf7VqR9tNfdj5oicKUwm6VTAHcVJP5I91mx8Mx76DSJzEVcp2H6epAmqpNMyUv0iglHSuLCU6lHZIubk9ggMf9q1L%2B3f8A5MRGGaUnn0x%2FhAR0x9Qpn344ZFpeEH3tam0JarzSisg26ot6PjjnybZdl335V4BLss%2B5LugKBAWhZQoXGx6yTvAWo4aphUVfmgX5WUnb5IlOF6ceTj49JEXCI3PeYC3e1enfqj%2Fxj5oj7VqcnrXfN%2FOPmi5es%2FHELm%2B5PxwFt9q1OP6ZMfdJ%2BaI%2B1GS7H3vjTFx9Z%2BOI%2Bs%2FHAWz2rU89UKmCR3FMS%2B1ST%2B2f%2B6EXX1n44hfz%2FLAWoYTkl8nXU%2FviIj7UpAc3XT6FJi5gk9sTjftgLT7U5Hscd9akw9qcl%2BrOD%2BEmLtb0%2FHENxyUYC1DB0r5RmHLHziI%2B1Cnp3U8%2Br0ERd0qtzXEdY%2B2gLQcIU0%2BS6%2BPSpPzRL7T5D9Xe%2BNMbfytyEzIzekKhV8JSEg3TKYsNTVRqU4mUlUOG1kdIvYq3Gw74seY%2BWeNcp8SKwrjmjKkagGkzDYCwtt5lXJxtYNlpuCLiA18MHU%2B277%2FxpgMI0sE6n5nzWUkWi7rUexUUxzgLanCFN%2BFNTA9C0%2FNEfahTP13M%2FdJi6iJ0oUSbDkLkk2AgLR7Tqb%2BuZn7pMR9p9N%2FVpj7tPzRtw5E5goyYmc9J2TlZHDjU1LsS7c0%2BG5ucbdc6MPtNHdSNXbcEi5AIEa67bQFo9p1O%2FXMz8afmh7T6d%2BuJj40xtnLjInH2a%2BFcT4rwQxJTwwoWhN07p7Tr%2BtJVdlq3XASknsvyFztGBy8q5MTTEqLNmYebYSpw6UoWtYQNZPkgE735WN%2BUBYhg6mjk%2B%2F8AGmAwdTR%2BnzHxpjeecXDVjXJLDknizE9aw9P02dqCqalymThe0OhpThUTYAo6qhcdoi%2B4U4L85sV4Xl8StS9Hp66gx4zT6dPTyWpuabIulQR8G4II1EcxAc4e0%2Bm%2Fq8x8aYe02k9szN%2FGmNt5b5F4%2BzPxLiXCGH5JmWq%2BFJR6ZqEpPOdC50jbnR%2BLoFjd1S9gDYHvjz0XJjG2IcsMU5tyUo0zQ8JudFNiYc6N55aXEoeS0j4Ra1DWLi3LcwGrPadSxymJv7pHzQ9p1M%2FV5v7pHzRllGpUvPU%2FE9YqE4ZSSw1QnqqV9GV9PMl1tmWlv3PSuO%2BV2BJjaWZHC3mFlZl2nMev1XDs5INzEqzMt0yfEwtgTAHRrNgARqIBsdrwGgfabTf1eb%2B6T80TjB1KA6z038afmjoDLnhLzczMwlL4zpLdIpshUNRpoqc4GHJ5INtaE28gnkTzjCqTlDmNXcxHsppLC8wcWSjrjU3T3FJT4uGwFKcUs7BvSpJCuRChbnAa09p9H7Hpv7pHzRH2nUe36Jnr%2BlFo3lmnwwZl5Q0VGKMRN06fohmG5V2oUuZD7cq8s6UpeGxRdXV1WtfY2jH8QZO4yw5lNhzOealW5jDuI3VS7ZllFx6WcK1IaDqLdUOqQpKTvdVhtcQGrPadSe2YnfukfNEfadRv1xPfdo%2BaNnZr5MY6yamqDJ46lpWWfxFTvZJhph8Oql0hYSpl0DyXU3F072vzj14CyQxbmbUsPYewU9Kv1utYZmcWzUvPuiVak5ETKmpfSs36RTiE9JYDa4HngNTe0%2BjE7Pz33SPmiYYOo%2Fwn577tHzRsTF2VuNcE5i%2B5VWaT02JHFSwl5WSWH%2FGvGEami0U%2BVcA%2Bixva0ZvifhFz2wfgup47xFh6Qk6dRpNdQnkLqLZfal021HQDuoXF0g%2FHAaE9qNC%2FVp%2F7tHzQ9qVB%2FVp%2F7tHzRd5dlx99pltIu64hoEmwBUoJF%2FNcxtfO7hsxzkRSKXWsWT9HmZaqzrlPR4jMFxTbyG%2Bk6wKRYFN7eiA0j7UaEf06f%2B7R80Q9p9F2PSz%2FAJ%2FfEfNFwc6h%2B2iHSQHg9qdBH6bUOX26OfxRD2pUP9Xn%2FukfNHuUq8XvB2E8S44r0rhfCFEmqvVp1RSxKSzRWtVhcqPYlI7VGwF4DFvalQzt08%2F90j5oDB1H5l2eP8NA%2FJGyMzcp8e5PzdMp%2BYFDRTpmry6pqUbQ%2Bh0rbS50ZvoJsdW1oztvgt4lHz7xl%2B2vq69qpLctOrlrvy%2BaA599p9H%2FAFSe%2B7R80PafR%2F1Se%2B7R80XJzrub9XmlWrY7GxB9BBiXWYC3nCFFBPvs992j5ol9qVEHN2e8%2FXR80XBS77RAknkBvAeH2p0a32afA%2Ffo%2BaJkYUofY9Pn%2BGj5o9Z5b9nniLagPIFoDxnCFF1X6WoWvy1o5fFEpwhSP1ae%2B7R80XLWo81GIqJ7EA7W3EBbPanSEnd2f37NSNvkgcJ0dVrOT33aPmi46lnYg3PMjuiFljt%2BXnAW84QoyRqLs8P8Ij5ogMJUwA6nJ4nsOtA%2FJFwSu%2F23riJN%2Fh%2FyoC3DCdJH6bOk92tHzRH2o0o8lzv3aPmi49kTXbbb6RxaU9XyoC1HB9PPkPTQ9Kk%2FNETg%2Bn7aXpoWG91p5%2FFG36tw45yYfy6mM1cRYSepVAlWmX3PHHUtTIadWlCF9AevpKlDcgbbxccBcL2dGZuD5THWDqFIzVHn1zDcu47UW2nFKZcLa7oUbgagQL84DSAwhIq6pff9akxBWD5FOwfe%2B6TGyM0spMd5PViQoGP6YzJT1RkjUZZLMwh5KmAstlWpJsDqSRaMJ1ud0Ba%2FafKcxNPfGIDCMoOc06fWmLpdw9ttMRG8BbPalJ%2Fq7vxiJThGXt1Zlz5I29k3kLjnPGZqzeEGpKXkaHLOPT1Sqb%2FQSbTiUFYZLlj1ykE27ALm0a5l3C%2FLtPoOhLqdWlXOAtKcJyva6791%2FqicYTljyecH8IRszKLK%2FEOcuOZXLzDdQpknUZuVmZtp2oPdG0pLKQpSbgElRuLADvPYYx7EmGq7g3EdRwrielzFNq9JeLE3KvCxSexSTyUhQ3SobEQGK%2B1CTO5mHfjES%2B1CU%2FXDvxiN%2By%2FC7jibycezpla3huYpkvSTW3JFmd1zaZYXuCkCyXBY9QkHaPNlBw0Zg5z0SZxRQl0ulURiZ8TbqNVmOhamH9rtt7EqIuLm1gducBo32oyNrdK%2Ffv1D5ogMISf6s98YjcdQyJx7Q83KPknXKexJYhrsw01IuLeBlnmXNVphLg2LdkKv2i1rXi5Yb4Ys0sUZt1rJyRlZGXq9BQqYnJmamOjkxLHZh5LljdLxUkI23JN7WMBotzCciR1XnvjESpwjKW%2BzvfGIzPCOHJnFGM6Ng0lUq%2FU6mmnuqIB6ABZDy%2Be%2BhCHFW7dMbOwDwt48zKyyVmrhav4dcpLzFQnJGUenQiddl5ZawC4gAhtaw2SEqPd3iA0B7UZH9XmPjER9qdP%2FAFeY%2BMRuPJvIDH%2BeEvOVPCTUlKUqnlKJipVR7oJZLik3S0FWOpdiLgcri8eDMrJXMTKrGkrgPFFEC6lUtBpapNzpmqiFrCAWFDyuuQkjYg8xAapVhKR7Jl4ekAxEYTkRzmHj6hHSmIuCvO%2FDuE5vFCpCkz8xTpUzk5R5GeS9UG2kpKlEN8lEJBNgbmxteMCwJkzjPMbLvF2ZeGGpeYpmDWw7NtdIfGHwGg8sMotdZSzdwjbYHtgNUjCcj2uvn%2BEkfkiCsIyR8l54ekpMbWqWTeLqVkxR885zxRugVup%2Bx0o0pwiZUlWro5jRb7EsoVZV99jaxi1YawHP4vkae3R3VOVquYlYwzRZDZCZt5TJcdWp1XVQlsFob3vr7LQGvPabLfrlz7oRH2nSY5zD33QjbeceReYGRc1SmMfSsigVgPiVdkpxMwguMqSlxtRA2V1gQO0GMwwlwW8QmMqTKVeUwlKU9ufCVSrNSn0SzziFbpUUq8m%2B3lW5wHO3tQp%2F6tM%2FdJ%2BaJDg2V7Jl31kRkcwy9KTTsjMNlD0u85LupuDpcbUUqFxsd0ncbGNqz%2FDVj2SyOZz5XOUhVGcprNYMp4wfGkybrvRpXp021XIJTe9t4DQ4wbJ%2FCmnPjETJwfTh9kffI8ykxd3PuYpFfrgLYrCdP5JffHpKYgnBsmrfxl7%2BTFz3UE6%2BV49lLp85VKhK0imST85Pz76JWVlZZBcdfdUbJSlI3Jv8kBYvaXJj%2B6Hv5MSnCMiNuke%2BNMb0xnwqZ8YAwnOY1xHg9KKZTWTM1BEvONvTEiyLEreaSbpABuedhvFPAXDBndmThqWxfhXCIXSZ9JXIvzc03LeOp%2B2ZCyCtJ3seUBov2oyROzr3xpicYNk%2BfTO%2FGmMlxBQa5hetT2HcRUuYptUpr6paclJhOlxh0c0qHrBuNiCCDFsuRvAWxWE5IGwW9t6IlGE5Mqt07o%2BKLqFqO5X6IHTbUT6YC1nCUnyDzvyRKcIyX6s98kXQr7lG3piS55hcBbThKU7HnfkgcIs72dd%2BSLkHF38oxU6ZY%2BGYCznCTHwnnB8USHCTPIOr%2BIReVLJ3KrxDUoch8sBZxhFu32VY9IEPamP1VXxCLzqfcWkG4HpjJMB4AxhmdiiXwZgekOVKrzLbjrcuHUt9RsXUoqUQAADzJgMAVhP%2FALU%2BtIiX2rqT%2Bm%2FyYy%2Bt0mr4dq9Qw3XpJySqdJmnJGelnLa2H21aVoVbbYjmNjFusP1RUBYfanr%2FAE3f96IlOE3E%2Fp9%2FUIvylKG2s%2FHENShyN%2FXAWL2rL%2FVfkEPas4f035BGyctcrcfZvYiOE8vKCqrVZMuubMul1LdmkWuoqUQBupIG%2B5MYvMNTMrMOykyw4y%2FLurYeadSUradQooWhQPIhSSCPNAY6cJun9MT8USnCT%2F6qn4oyAlQ5qPxRIXCPhGAx9WEX7%2FZEfFEycHvKHUIJ8wi%2B9K59sIm1ufbmAx72ozQJBUkemJfafMFX2VHxRkYU4Sev8cQ1uA%2FZIDHvabMj9MSfVBWDXSN1pvseUX9RcvfpFJ27TESpwDyirbvgMcVhGYHII%2BOKZwrNDkG%2FjjJelcPwflgCs%2FAEBjPtVm%2B9ER9qc53D5IyW2%2FWBHoVEyilI2Kh%2FCvAYx7UpoDcARIrCs6Ds2D37iMn6RI%2BER6YmDiexfrtzgMT9qs9%2BoiKiMJTxH2MCMoUq24cvcX2Vy80SiYUjZKgb%2FwC%2FbAYwcHTfPSPiiHtPnSCA2SfRaMpS%2B4o6lKIsexUR6Z0kFDy%2B3nAYecIVMWtL3894ijBtTXuWEp85PKMyS4%2BeTi9%2B%2BJtavhkkwGGHBs8PK0%2FHE6cGTp5afjjLlP220iIdIpXJYHrgMWGEp9vmlB9ce6QwVVp50sS8s444kaihmXW6oDleyATF799%2FVB8cbl4Z65iPDc1m7XcLVqap1XpuVVVnJSbll6XWHUTcqQtJtsbXF%2FPAaSeyyxNLJKn6PUUJACio0mZtY8t9HbD3M8TWSr2GqelR0hXsTMWv3X0RuSn8SnEfNNhx7P3HN2z1QmoNgev3veK6uJDiStpTn7joC1t55v8Aq4DSy8scTo13o1Su2nWoexUxdKdtyNPnEQGWmJbal0ioti4F10t8c%2BXwY3TIcRmfr%2BJKdTa5xJ40olKmZlhucqb06HESTCj13ihLepQSLmw3MbC4jMw88Mm8bUOk4O4nsxKzSsQYYksQys1OzDbLmiYUsAFvQQBpSlQ7etaA5TOW%2BIk21UuoC%2F8A3Y%2Ft%2FJin7Q6tqU2JedK0X1J9jXwU%2BkFO0byHErxHLbDXu9Y2UlKtQ0zzQPx9Fe0PqkuJG9%2Fd4xte1r%2BNs7%2F5reA0YrAdZb2mZWca3A61PeHPl8GIt5e155OpqnzygRqBFOeNx3jq7x15w45n5s5uYkeouKOJHNj2VemZWVk6Zh%2BnNTzyZRZCXqjMOqQG2pZpSkhfwt72sY8OX%2Be%2Bf9K4nsM5cVbiArGJKLKZgSlGdmW1sqlKlKNzOgqSkNghKgmxSDzvAcjpwmtSdZqTVj2hpRiBwms8p5J9LChG3cQZSZwv16tzbeU%2BL20vVWfcuKI%2BRZcy4oEHRa28WwZN5zKbLoyqxsUFOrUKJMWO1%2BeneA1r7Twec%2Bn7wuHtPH6%2FT94XGypbJzOd3V0eUmN7I7RRJi5%2FkxUOT%2BcqRdWVGNRY6T%2BcUwSD5%2BptAaz9p4t%2FbJH4MuIDCH21QT6mFxs73Gs5VBSm8p8aK0p1W9gpkXHm6u8SnKnNtYUXMqcaAJQXCVUOZASkC5JOjsEBrb2pd1Qb%2FB1xVlsDz86sMU9app6yllpiTdcWEJF1K0pSTYDc9wi7MP69Lja%2FK8mO7OAbLtNIwnVM16vh52VxDOVIytEqL6VJWKcGNDpZHItrcKgSQb225QHz3ThBxYQ41UpZxtwBSVoaWpKgeRBAiUYVcKyEzrCkjtDS946R4wcsZTLbOCcXhjDC6HhitycrO00MMrTKKmCk%2BNoaUbgELsooB6urYWjRfSL5%2FwCv13gLOjBzir656XTb%2Fslm%2FwAkUfaqv9eS33tfzRfVvvC6VGxKgo25gQ6T3xf73%2FcgwFl9qBKL%2BPy2ru6FfzRL7UV2UFTsskDt6JfzRfUKWQk3OoAnnziLi1rc%2ByL%2BKAsvtOFv7ZNct%2FzM7sezs3iPtOI%2F5yl%2FvLnzRd0F083DFXpHCoJ6QwFmRg15wpQ1OsLWo6UoDLhUo9wASSY9zuWWIWUrU5T59PREBwKpE2nTfle7fbG7uEtyZa4i8HOsEhbXsg6hQSDoUmQfKVbjYgi4PYYyVOYfEa%2FkBQ888K8SOMKnTWFrpWLZGaebZfpc90mltbSlJPTtKBTyOoXB77ZrKzm0jOJ8PJns%2B1q294ixqiiYjOcts5bZyiNk8rmGZwHVJWXRNTKVNMOqCEPOyT6G1KPIBSkAXMeM4Qd5ePSmrusu%2FwCKOmsIZxZnZoZS53SOO8xqvieQp2D5SaaZnHW1oYe9kmQlxGlIssC%2B%2FPeNFlblvLitdnEUxXTOcT5sl7G2rrqqorpymPPn7oYwcIzg2Q9KqT2m6vmgnB02d%2FGZQ%2Ba5%2BaMjSHlndRV6IBTjaj1V%2FHGNnY8cGzxFuklU%2Bs%2FNEEYOm0nrOyp9Z%2BaMh6aZJ6zpMTKfeSNlGAxxWFXkq3XKenWfmiJwy4N1rlrd%2FSH5oyNMw7putw%2BiKb7yym5WPReAx%2F2tOlOpK5W45guf6omVhxa%2FJblyQd7LHKMlkUpmkO9KogoQCn5jHpbkkISdThsTz0%2F77QGIe1h8HWlMupO%2FwxEDh1aRqUhhI71LAjJ59tco40jWVJdTqTtbTvYxt%2FKafpeFMpKzjRzC2CarU3MaUbDyZ7FsmqZkaZKTLLqluKAI0gLCSpW9gk7Ramma54Mf1lrYre1iws5rmM9mr0zl73PHtfUeSZU%2BhwRFzCs2pHSIZY0eZUdK48zXxzlpi2cwXjTILJ9qdY0vNPtYfUuWnpRwEtTMq6F2cZWncEbjcGxiw5xT9KxDl9lhmHK4Mw9hyq4hlqw1UWKGwqXlXky80lDKy0omy9NwTfeMs2GWf4UdfviGvZXybSqmKrOYidUTqmOXwTPgaEGGphHU8VbWD5JCufnib2pzarapdoX527IyPprHUbgi3bAzKex1QjA3WNKw242vQZRGrVa%2FZvEThV7tlm4yRub66hr%2FAIXKKwnOvpWjWmxO1u6AxRGGnydHiyeQ5Ed8TjDT6OoqUTfvuIyLxsrICAUknf1dkeiXbm56YblZKWempl5WlthhpTji1dyUpuT6oDGPau%2F%2BtEfGIqJws9baWbG1%2FKEZNJydTnq4xhmn0ucmq3NzCZNmmtMqMyuYUQA30flA3O9%2BXbG8cPZX8PWEMbyGD8888EJqbK1IrEjQ5Va5CSe0byz1SF0odSeehKgDte8BzD7AvDypVKfSYgmhvKveSbMZ7jMYWkMXV2VwZWXqnhyWnnk0mdmUhLr0qD1FLAsL27bC4sYsgnNLXSCx1fCTyPcYDHnKE8gp0yjaR6R%2BOJxh%2BbUP0CjnbdQG8ZAmcK9V1BW21x%2BIRWanEqUlAUVAqN1AD1bd%2FfAY4MMzp%2FuBr1uJiU4ZnTqtItDSN7LHOMxaprsw0p5Lii2kgElNggkcvP6IgqRV0Liw99ibUtPV8qxGxJ5bQGGHD0wkALlmtjfdaYnGHlFJuzL3tyCxzi%2FFxRPWTba4N%2B2Jw4kJF0q9IPbAY57XnPtWfR0gh7X3v1Jv7sRkPSa%2BxXzWibpj9pAY97X1kEBhhR86hEEYcd6XQmVbse24i%2Frc3UtAIAG%2B8SqdQEk3JJHmgLSMKvlVugY5X3cA9UVU4RfV5LMof8MiMlVT%2FeEuomDcgGxRyitLUlcwtLTcwu6l2uEXPogMW9qTw5syn31MTowo%2FwBjcmB%2FfUxtrIpzDAxw61jHBdQxLKv0qbZlpaSpjtRLE0dBRMOS7S0LWhICxcKFioE35R0y%2FwDUlL9%2FmOGDH6V77JwfUEg9%2FwCm77wHBq8L2RpKZIK7%2BlH5IkThW%2FlOSo8xXzjtDH7fC47hCqTWGsh8Z0pySpM6C%2B9haoslp1aPeJhUwXdDaW3LFRWlQKbjbnGneHLJaYzxx2nDkzPuSlLp0sJ6sTjFulDJVpShq%2BwWtWwJ5WJgNLDCR5Ayo9Ln%2BqHtSV9vJffP9UfSnG%2FDbwsYGwDO1LFuEXqPS5EobXVWag%2BakX3SENob5h11SiAlAQbm%2B1rxxJnXlZVslsxqjgOpVAVJhlpmcp8%2F0XR%2BNSbydTS1I%2BC4OslaexST2WgNYOYRUyy5NNtS00hoanOgXrKE9qiOdh2kcotiWqWpRSpLNvRGUy07OSk01Ny8wUOsKC2za4BHeO0dhHbG06DwuUbFlEkMU%2B3c08VhkTniiJIlMuVm5QDfcXvbzbdkRMzsiM5T%2BDEcKqcoaCLVJBAShvnblDoJAn7G38UdIK4MpI3DGYRcNtW8kQOV9zfaJGuDWUdsE5jtoURyNPWRfuuDa8MrSPmyjhWfjQ51EvIfqbfxRMJamfCCB6Ex0WeDBaFaPdDl97WPiaiN%2BV99o844Npxywax9LE73Bk17W9fbExFfiyjh2cfOhzyuWpSSQUpO3dBDFGsSU9sdCu8G08xqtmBIEAXv4o5HhXwhzguEY%2BlFEG36EXE8GvxZPjbPxoaKMtRyArqW9V4CUo6ybNpMb2Rwdzrg62YMiFX5GUXE%2FwBRzVE30ZgyAH%2FhVxOVfiyfGWfjQ0KZClq5lHrEPY2kd7XxR0Arg0qDLCpqbzOo8sy2kqW48ytISLX3v6DGJTHD7h9K1Jl88sKrta2rpEhXoOm0IornbTPMr8bZ55cKM2sDTqR1d2uXdEfEaKGQFONDfujbDHC6%2FPAGSzawe%2BFIUtHRTajrSkAqKdtwL793bFJ3hibYmBKTOdeCWnSAQFTptY%2Be1oqu1a1J0IatXR7eaJPFqA6qyENkd5TaNuOcKM61MGVRm5hJ57mlMu668V9nVCEkn1RK3wr1J%2Bbfk280sI%2BMSrpZdYcedQ6hwc0qQUhQI7QRtAan8Qw8nZTLR%2BOIeIYd%2FU2Y23McKFZlh79mlhBBI2CplYv8aYoJ4Vq4pQSM0sE7nmaibD5IDV6afhvtQ3o1G9udrQVI4cWoFXRXKbE%2Bf5o2RN8NVQpxQ1O5r4ERrUQrRUVOFIAvq6qTtFncyQ6Pf3UMKLSeS%2BlfAPrLcBiCKXh4iwLQKd0i2xHbE4kKAnZxDYT36YvL%2BVtNk3G2Xc1MJIW5yBeeG3eD0djHlfwDT2E2VmXhhztsiYdJI%2B9wHk9jsO6tGlm24vta47Yh7H4dK2tCmet8NPwSLbkRM5g%2Bn395x7h1XpmXB%2BNEedeHZJJ0pxvRlb22ccsPjRAexcnh5bi%2BndStWo9Y8jEiaXhvfStobbdljFvNEZVYnFNJNuV3FfRiAoidW2IKYR39Iv6MBdXKdhpTiUhTKd9lH7W3zxUNMwmhCHOqsG5OlN9MWRVMCBdVdp9v36r%2FAM2KXibCCUprElcdylW%2FFAX0UjCKbFpbLjak3CrGx%2BLl64iaPhdRbcdSyhpRspSVX0m217cu6LClhLSrt1aSKhsSsnceoRTLDYJUanLEnmQo7%2FJAZGqj4VQbFTa%2BSgE2spNjqAP2wNtoi3R8HBSEOFkLKesFbb%2FFGOCVGrSibRq32Tft9UehNDq6rILTu24UWldvntAXn2Kwn0l1ltpJOk6Re1uZiZdKwuXOjbDadKtKbbk%2Bfu2izGhVlHwHfW2rf0bRKaNVkbmXmEq%2BDdpY%2FJAX1ukYYDYKuicG5UB2DzRH2MwcqVW60lpSkhSgnTZVgeVuYMY8inT45suavtujVFUUycI3Nj%2B6CgfV3wGQ%2Bw2DQtJs0CUgt6uR7bGHsVhHygWCgm6dPd2xjTshPoO4X6FINjFMSs0CbHSQOWk93ogMpbo2DtXvrjSAsApVbl5rxO1RsJAL6Qsak3CRrvew5xivRPhISXkpJOyjy%2BOIpkXFkkLaChy61ifRAZEqjYWcstxLKAB1wRfQf97RV9hMHO6ve2RYi2ntEYwunziTft7t4Jk5wi4N%2FNv80BlXsBg64DRaJF9QtuDEHKTgtsJLZbVc6VotYp8%2FojFQ2%2BoaFOAWV1Sb2MVW5Z9Z1oWyTsNzuo%2BiAyhVDwU7pLDjbqPhAAg%2BoEfLE4w9g1rWCGNSVbJVzI7PTGJLkp7XdKlAnewBttASdTKSN1cjZQJO3zQGVewmDV9sv5OpNk%2FGIqDDmD19JoeZVoFxtbUe4bc4w9UtOuJGtwbEpCzcc%2FPE6JCdHvfjTf3XZAZR7B4LQla1PttqTptcc79npEVjhvBalLb6RhS0eSQdlRiTlNnNIu8gk8wImTSau6oLQ1MqTtuhpZHp2EBlS8L4JCVIbeaUokKbVoICk25b8jeCcPYELyWkvoCilKkjlv2iMbNGq6k6SxMEd3QOfNEgoVaVfo5KZXfnpYX80BlaaFgIhVn0EqRqKTsUq1W9e1ztFNNDwUpSk9E2CoHQQdQ57evvjGPYSrC%2F5im7jn%2BZ1bfJEF0utKNzJTPqYUPxCAy%2F2BwKhtpWpK9YVqOjZKhyB7bHviX2GwDZRdLJKW7gJ%2BEvu80Yj7G1ZPKUnQfMyqIimVX9j5vnb9Dq5%2FFAZYii4ECC5paACQTffftEVU0bL9bRUp9tJSQkoLe49cYoihVx37FRZ9e9urLrP4hE3tdxPp1CgVG1r38Vc5fFAZQaHl4lSUqeYGq9uqb7R6E4bwF10BTCzpulQSSL35beaMQ9rmLVjScP1Qpve3iq%2BfxRWTg%2FF7XPDVTR%2FiqxAZ4jBeX3izbxDKgp0IISvrpSeatPeOdvNGE40wfQ6dIVR%2BXfQlcsx08mpKwUv6XACO8XQSR5xHkFCxCCCae%2BgE298aXue7viM101LcZGIacmaYdJ1Srq1o6UDs1DrJPngMKpDYdCulGrext2RecKb1ySSP1y0P5QivUJCkSqTP0RwqkXV9GG3nAp5hVr6VWAuO5VhFDBfXxFIJte84yLfwxAfpYhCEAhCEAhCEAhCEAhCEB%2BdziB%2FwCVfHV%2B3EtT%2FwDvHY1K6eqT5jG2%2BIY3zbx0ocjieqH%2FANY9Go3fsN%2FOr8cBl2FWwuklxR%2BFFzvcbRasMk%2BxWkH4Qi5FzQNJgBMSE3iJN4lJMAPLaIp2F4A9W0DsmAFdoilyKSoJgKi94ghAiATeKoSRAS6TDSYmiHOJykQA7LxMGwYhoMTAKEMpEyQRyIFh3RUQtfVBc0qSpJSrkQpJBB9NwIk0KO8RtaGUjqhrE%2BKMYcCmZOIsX4jqFcqdQxg2pybnXy4sgvS3K%2ByQDewAAGrlHKZ8tX76Mwk808b0%2FLKoZPSU9Jt4Vqc6KjNMeJpL7j%2BtC79Ne%2Bm7aOra1hGI9GvnaGUiBF%2BSogUHsMOjcHNMRBUPgwykRF46%2FwCCx7CwwfipvLxume7X4rMiTFbVZkyhA6ES9vgE6uktuVBIPVMchJN%2BcXCj1mqYeq0jiCgVF%2BnVSmuh%2BTm2FWcZWO7vB5FJ2I2MMpG4qurKtvJPGE1mZ7OucQwrDyqgJ1DiZlMwXkpaQlJ97Mt0Grt2VbTtaMlxAvgvGamXfsA3UfaY3JTbmKOu8Wi%2BGU%2BKJfJ6wPSdJ0mjbZMakzfzdxHnTiOQxXiai0mRqMnTWqc45T2ijxsIueldJNysk%2BgAACMH6%2F7pMMpHavDtOSrOJczWcL9CvhkY6ZSFYi1dAy4ptJcblSvrKbK9epJ2HVIss78qT68K%2B6i3PYKbm28Oe2WVdovjYs%2BzLmab0k%2Bje3bpteLvjPPHG2OcD4Yy2qCJKn4awtJNyjVPpyC03OrRyfmPtl7nblffcm8YGzNOy03LT7ASXpaYbmW9SdSdbawtNx2i6ReGUjvyRQG%2FCOYnDhT0r2D3AynTvrMsi59NheNNcJhnGqfxDmoOvusows%2Bmf8YKggzXSPC69XNwp2vztaNV4nz5x%2FijN%2F3cmZiXouKELYUhUglXQoDTXR6ClZJUladQUCd9XZYRkmY%2FFlmPmPhWdwa5QsO4dkqvb2XdpMtoeqIFuqs9gNhfmbbXhlI3lk1mvhvKPhDywruO6NM1ChVOanqdMhlpLymXUrdeZUWj5adTYSe4kHsjCeOPEa8U4YykxmzJuNOV2iTdTaavqXd0tqCPOrcD0mNHVXNbE9YyjoeS83J04UXD1SmKpKTKWleNrdd1dRR5BCda7WG9%2FNF0rmctbxTK5byGLqFJvyGWzbDEiiUCkOzjbSkq98UokaldG2Dba14ZSMczcZkUYlewwlIXLYTp8lh1CSLgql2gp5duxSn3XifOI7KxcqXTxzZGOKKQmYw0yghfaoy7oQoHvjhGdemarMTs9OqPjNQmH5t9Q59I6tS1EfwlGNhY%2BzzxzmFjTDmPp5EnSK1hSQk5GmPU5Kk6DLboeOom61Em%2FZY25RGQ3zw3t1D6sbNF18zXTIka77JLWFaVDpQGOkvtYAdS%2FZe0YPXkyzvg7MI%2B%2BFckjG9SM8QbIdHTvadens1FBA77R5cV8ZmbGK8Kz%2BGhSsO0d%2Bss%2BLVSsU6U0Ts03YgjUfJJBIvc2ubWjFcpeIXGGT1KnsN0amUer4fn3xNOUiqSweYQ%2FYArQD5JISm%2FeQDzhkNzZrOuDCnCVMz6nVvpVT1OB4kvLHSy5uq%2B%2FPTz746DqeeuFJTiMRkg%2Fh2aTiaYqjVPYnFIT0RkHW1TKj0vlCykhPRdpsY4FzBzqxxmhjmnY%2BxI9KomqM5LKpcnLt6ZaTQy6HEoSnmbqSNR5kRcpvP3Fk9nzK8Q0xRqYqvys21OCRGsSgKGi10Y31WKSb73vE5SLriOZFLz4zaxupxClYUNbnpYKFgqcf8AzJKpv2HXMEjtuiMm4CkeK5r1CnNzawynCFQR0RUbOaEIsbcrgX35xpeu45m6%2Bxiqbqcv%2BeuNK2xVai6wkIYQ0z0jgZbTufsy0q9CBF3yWzfreSuLJrFtDpMpUnZmlTdLVLzSilAD6AA5cb3SQDbt3EMpG3sEzxoXAVXatS6jUJBubx221iObpiSZtNNMw2hxQtuCGiNO4uCe%2BLHnxkxldg%2FL%2FBuZ%2BVmNMQ1uiYufdZamKkrWtbKEdJrbCushY0uJKFbaow3JjPjGGST06xRpCRrFGqyAmo0eoAmWmFAW1230qttyII7IuGcnEJM5t0DD%2BF2cA0fC9Lw889MS0tTnFKbCnE6SEggBCQL7AczDKRvTCmE8icp8NYd4o8OM5syNJbmehbQ%2B21qcl3AWwuZaG%2FizihYWO5t2RRx3gvIPH%2BCKxxRYjZzWm6fVppwLW222HGm0J6NDzbagB4slYShKibbm8aXqvE3jGr5MS2R7uGqUiks06Xpjk%2BFuLmHWWXekT1SdAVcAX7uUJXidxlJ5HryKRhyjGmqpS6N7IOqdMwJZTvSHq%2BTqHIHkOcMpGmvfP0xHRfuTYlI5gEjtA2iQkxWc0fqmqJIZSJNGvrridHX977IaP3MTdGtaFeV5JTq5W7NoZSOnclGkZD8NuK%2BIN1K0YmxslWGsGKdWpSmm1akuTKNR5lQWrV9qyO%2BOYOjQ002wlRWGk6dSjuo95PaTzMZxjrOLHeZFEwzhnEr0i3ScISvi1Kk5KWDDSOolGtQB6ytCQAfOrvMYNoiMhBVoAi0FIMQCCIZCJVEhPdE%2BmJtETlIpA98ThUTaIl0nsiBCIEkGIxAi8ATziYq07GIpTbeIKTcxOUhqPZC5gEeaKgbBhlIkvtuYi2QDuIKQAbAxUSkgbARGQ6OwVXstswOEicyAxtmAvLt2SrjtSRWZyReckKiku9L0ZcbFlLAVYt3vdCCLxlPHSqkJw3lFLyk27Mus0V7xaYmLh%2BZkOiYS24tJ6ydSgF2P2xjSeWXEPmNlVQ5vCVJTSKxhudmDNuUWtSQmpVL5tqcQk7pUdIv2bDlGO5l5l4zzYxU9i%2FHNTTN1BxtMu2hpAQxKspvpaaSPJSCSfOYDFiodwimTeJrXhoicpEoJEbH4e5TLGoZv0CSzgdLeG3VrHXXol1zth4s3Mq5hlS9ieV9IJAJjXWiIhtC21Nrb1JUkpUFclA8xDKR25nQ9I1DiSp%2BGOKp00fKhmmOvYNEi%2B4xTX5sBACplxsXS8lHSAIsEpskJ2NzpdqU4YE5YZqKNXnTjKXqVQGBS68sOTEl1fEFIRbSsHr9IV2IAv3Rj1T4gsa17JVWSGK5KSrcqzMyz9Nq08VKnae00q4bQb2UbXQFnraCUm%2B1tYL6Q8ogdQUwYIw9irKmc4KajUKjmRU2g3iGUmJh1cs7IpZbU8KilVksaXte6T1bXTvaPFxt03LmQzQkjhpEtL4snZZUxiyTkiFSjbp09EvuS8rr6hYakhKiASY1zlDnzi%2FJah4rpWDabS%2FHcToZQmrPtXmqfoTYhvsUk3KtJ2CgDvyjXT78zMTD05OTb01NzLinpiYeWVOPOKN1LUo7kk9pgN%2BY3bbb8HzltZtQS1jmdCkqUTsXngRY8wQbRn%2FEnPVOX428tJeVfnWkol6AmmoZfUhAQpwiYDaU7KSRYLFuQjnio5oVerZK0LI%2Bcpkp7D0OtzVZanQpRfeLuqzShyCUlajcbnblbfZuGONHMDD2H6bTarg7DmIq3QJUSlGxDPs2mpVrRosoWOs2AuQRe28MhvPAU4ikcZfElPyMu26un0RuohpDgSXVtaHCkK5JKiALntihX838vs4eGrNteXFEmafTaRR5eZnA%2FLCWCp%2BeKJh9OjtUldwtfJRNxtHLGX%2BeuMsv8S41xmG5Ou1rHVJmabUZqoagULeVcvpSjmU7gIO1rd0WrBOa1bwJl3jvLOlyUlMyOPm5RubmX9XSSnQgJJbSNjqSLG%2FLnE5SPGZg0nKuZl9CdWMcRpJUr4cjTG9Rt3DxuYA%2FwcbapiDL%2BDtx%2BzKI3ON2EoTcqITds3Fzta3LlGlMSVxipyGHKXKSzrMtQaT4rpcA98mnXVvTTwt8Fa1JsOwIi%2FwApmtXJTJSp5GKpMmqkVKvNV1U8Srp0KbCT0AHklJWkKKudiREZDdfFjUJyUXw9ClTE9JMJw9TFyCJR5bWh4uy19GnZSym%2FfsTG%2B5sgcaWbE3TSlM%2BzlLJ9ApqxcS%2BSSk7b6xZPxCOWcvuLvFmCMJUbCVbwFh%2FGCMLH84J2rAmYp1hZIBsdWkbAiyrbXjDaJnzmXRM3Hs8Wa4y%2FiqeW4JwuNAy0ywtISZZSB%2BlpSlITbdJF%2Bd4ZDY%2FDpMO1DhR4iGqhMzD0m3JSThD7inAJpTepxSdRNlFekq89o3FgjNrAmU%2FCdlHOZl0V6dw9WpKaadU2wJlMvPSi3ZyX1Nc1BTqAEqHkrsTtHPeaHE9inMvCTmA6bg%2FD%2BC6BNzHjdSlaMCFVFwEKAdVYWTqGo23UbXNhY4bibM%2Bs4oydwZktUJCWbp2Cn5x6XnmnFF%2BbD%2BsBLgPVToS4R1eexNrQyG8OOyYqmNatlG%2FJyy2J7FOG1vsMrUFKaenZhnSlSu0guC58xjRmJK8w5nJ4%2FQJ19iRolZkKBSXpVxTKkSMk61KISkpN9KujWojkdZ74yLEefNTxvivLjEGKKJIMJy6oppku3K61iddbQeheWlWyDrS0SASOqe%2BNUyL7si5KTTakuzEq7Lv3cGzjjTqXLn98pO%2FpMMh9D5CmSD3hHMVzs0llyZkcAMzVNbUi%2FRuFCW1FI7wgkbdijHPOHcAUHO%2FJPGmadWzuxZO4%2FoEpOVPFGHppavFJKYbcWWmFtkgdGpDR0qAtcAWBBjFMd8ReJ8S8Q6eIzB8ojDlWl0SrbEktZmGi2210bjLp21tuAqJG1ur2iM3rvF9QKxg%2FGFFp%2BR9EoFaxxILkqxUKfMhKJgqSU9IsaQpdgpZAPIm94nKR4uHnIvKTOnCVSVWZ7H7eJKJLzE7UUUmVR4qlkLuw3LrIPSTK0DUlFwdQ2G2%2B3nZjKLjIVTsEM46zOmzgamLm5sTFKQwH5hNmi%2B%2BpQsZpf2MJTsSFbXjn%2FIbiUxDkBK1yUo2GafW2K1Nys6Ezcy430DjDZQLaB1gQQT2i3njzZK8RuIskK9iqu0%2FDchW%2FbY%2BxNTKJl5bXQutvuujRpvcEuqBv2ARGQwDMiVwVIY0qMhl2%2FXHsPyxQywutyolp0PJFnkONfB0ruN7E25Ri8XbElZnMTYhquJZ5lDUxV5%2BZqDraCdKFvOKWUi%2B9gVWi2BtQPKAlsYvWGMcY0y7eqmIMA4gfo1UmaRN0tU0wAV%2BLvpHSJST5JOhNlDcW2tFptEVtNvsuyikE9MktrsbEBQttAdUce0u%2FNYsyvSlxyYXM4TZQhDaSpxxwvtFWkfCWsnYfbGMyGIsjOKrP9OCcR5XZgUDEEzh7oZWrv1NchNSaJcA6PFEmwB1LIWvZRsLdo5jzSzkxlnHMYbnMXIkZaYwvICnSD9NaVLqCApKg4TqJ6QKQkhQIsQSIz5fGpnKZHUZXDK8SKkBTXcVrpwNUcYHLr3tq2uTa197QGlMV0NzC%2BKK3hZydTOGi1Kap4mEm4dDTqkBfrABPnvFrXyEVphRceW4pxTinFKWtazdS1qN1KPnJJJ88UlDflDIU%2B2IpuNonAvEqtoZCRUE98TEQAJ5CJykQ1QC7crxCwMNIiBMHV9kThaztaIJSSeUVktm3KGQoqMSgxVW2e6JAjvicpCJ2y2450b7YWnUFd3L0RLpiZCLwykddM4%2FxtmDwP5q4pxviaaq9VexJLyaJh8JGmW6SUCW0gABKR3Rqjhdy5qOa2dFIwr7I1Bmg07VW602zOOtNmVZULIISoAdI5oBNuQVGLU3ODGFIypq%2BSsu3TThquT6ajNa5W8yHUltSdDl9hdpO1u%2BK2XucuMsrMNYroGEBIMe3KWMnPzy5cmcaZ6MoCWXQodGBqUrkesb9kMpF14ks105x5u1zFUhMaqNKOCk0ZI2SZSXJT0gH7tfSL9BEapXpWbk2tFRAQ2htllsIaaSG20%2FapA2ES6AfXDKRT9ceukqp5qcn7LqmEU%2FxloTq5ZIU%2BiX1jpVNg7FYRqsO%2BKHRRFsFtyIyHcPET4phzLTL6j5bFEhw6VGcllYpq2HyXJxco4%2BgrW6QNWhSblS91FYKVAaQDgEtTeCZHEBPtTlcdRlwMMMLkyiamPF11XplJeSl7T0n2DQtNxYuXHmjWWUHELjDJqlVnDlNp1OxDhyvsPMzVDq6VOSiHHUFKnkJHIm%2FWT5KrA7KF41WGw2hpgKUromw3qUT2QyG8aWrh3lMk6tVKHXa%2FLZySuIZpeDvE1vJn9YnEinhttI0rQZcde9lalKjb%2FFVKMz2ROFK3ntLUuQzrLbbUkilgBx5npB0qZlPINhBKlcwh3ZBIJEczZQZnVTJvHUpj2j4epNampRl5hEtUkq0JLidPSoUndDifgqHeR23i2Y3xriXMHE89jDF9VXUKvUF6nXTshtA8lptPJCEjYAenmSYZDd%2FDY3o4fuJNhjylYeadTvsT0bl9uQNxEmcs2pXATkwyh9Ylpmdm1TJZcUhp52z5bK9NutrFxf4Q741XgvNfEOBMFY8wLRZSUclMxKa3Tp%2BYdB6WTCCoFxoDYlSFqSdWw2IjLcpOJfEeUuFpjALuF6HivC65oz0pTKu1q8SmVEKWppQv1VKAVpI6qrkEXIicpHQeL%2BlVxDcI01UnlqmZijNpmVuAlxS%2BjA61973Ktz23jamAc8sFYpzvqGVcphqYlcYSExPyNYmOjTpVJSCkmWcD4%2ByBfTDS3zRdV44UqnEHjuuZzUTPKuiSnqvh6dbmKfTylSJNmXRq%2FMqbG4SdaiVc77%2BaI4Sz9xTg3Oyo560%2Bj0ybrFWXPqmJJ5S0ywTNAXCSnrXQUIKT2235xGQsmHump01j7GiXAlzDsjPSks4kdZFQqM0qTYUk9ikoVMq9Ubd4HJeXk6lm0thvQU4Be3TyISV8%2FOBbfzRoJdaZGEHsOBpxU7P4h9nJ59adIcDbC2mWrg9YBbzznLYqFoyjKXODEGT72KF0Omyc8jFtBeoE2mZUpJZbcvZ5sp%2BGnUbA7G%2B%2FKGQ2YpxTHg3KAhqdUwzM42dRPFtxSEuoUtQ0uEEbDSnt7BG15QPzk5wSNVl5UzOLdfcW5MqK3VJRKAouVbnYJ9YEc55KcQOKcmKNOYPkaVR8R4Un3Uvv0KtM9Iwl4JALrarEpJ0p1Agg2vsY8mZGe2YGZ2M6LjaoT0tR5rC5bNAl6Y3oZpmhYUC3fcqJSASdiBa1oZDorIqbqX1w%2FHEvN1CdUno6ymZQ68sp8WHQlhJSTp0JudPdc95jw8IeNqdl1kXm9jypyD83TqNi1MxMNMJCnFyq2w0spSdlWQu%2BntAI7YwbEHG%2FmPWKPUZan4QwzRcRVaVEjPYjkZa027L6Sk2B8lVlKsSSBe47Lawwnm1XMG5SY1yeptOkl0nGypZcxMLKumlSyEpIbHIhaUgG%2FLmL3icpHTPEpj7C2Y3CZKYkwVJpk8NS%2BM2qNSQWegCpWVLqEudFb3oGxsg7gAXjlDGyBTaHg7CzTS5OYp1EXWJyzhSvx%2BpOmYBNjdK0S6JVIPMCPfO5n1ifyQk8gZuVlmsOtYhXW3Z5pBM4pK1ErZAJ02BUsg8zcA2Aix40xAMXYvrmJkynizVSnCuXZNrtS6EJaZQbbXS022k22uDDKR1Xi6Vkqz9RZR66tc4xUFMPTZmll0zCkhtXXKt1FSwm5N4uVbwjSs%2B%2BKrMjLnMLOnGmH63I1RmVw3RKUVtIXSxLJW6%2Bk3CVWUTcHcgmxPIc2Y%2FzmqeOcJ5YYUEgmkvZY05cnK1KXmCX33%2BkSpp9I%2FSygNp23uq%2FZG5sN8dM0zUaVi3HeUFFrmMqNKqk5fEUo8Jd95sjrJWCkkBZ3UkEjdWm14jIa5yAyuy8zJx3Ucs8bVbFsvXFzjsnSXKJKoclQywXA%2FMzS1X6JIKU%2BaxHOOgpdzJuu0GW4KE4%2FzSE3J1VUkptyjBt4y7Q1iTdc0afEkn33X2gp62mOXsos4qnlBmBOZiSFEkqlMT8pUJR2TfdW02kTTgcUpKk3PVIsAb7ReGeJPEjXEDOcQ3tdkTU56UckXqYX3BLqZXKpl7ax1rgICr9pv2QyFt4h8F5c5cYybwVgWdxS%2FO0oPS9cTXZZDXvgUCw7LlNtbS0EnVyNgQd9tVxm%2BceaNUznzEn8w6xTJenPzcrKySZWXcUtDbcu3oT1lbkncn0xhRTDIIvWEMSYswliem4lwPOzMpX5N7RTnpRkOvh5wFvS2kggrUFFI27Ys0ZNlzjWr5Z41pOPqAzJvVKiPmYlkTjfSMlehSbqTte2q4sRYgGGQ6mm63M8LuWWMMS5t4qmK7mzm%2FKrbNGmZrpGZJtTSm%2Bket1RoS4suEAAkJbTexMa24ZcRYWpmPMDULPbEmYYnKVPyMtl7LqLqaUhCmig6kmxKFL0AaLp07E2MUsQcaGZuJ6LU6HWMKYGmGKvIPU6aW7Ry44WnG1INlqUVAjWSN9jHkwHxd5k4Jwph%2FC83R8M4sVhCXTKYdqVakiqcpbSUaUpQtPlAAAb2NgBeGQsfFa1jKW4gMXox49Tnaz0zC9VP1GWMoWU%2BLBvUAoWa0ghW9wey0aj1E84vWLMU4gxxiOoYtxVUlVCr1Z4zE3MFOkKVawSkDZKUgBIHYBFmKbdkMhTheBG%2FKFj3ROUiERvE6EX5xKtOkxGQliUk35xNEp5wAExNfe194It2x07mJk1lvSuCXL7NakUFLeLKlNyDk5VEur1zAmXH0OMrTfSUp6NGmwuN%2B%2BA1plZw%2BY2zZwLjDH%2BG5ymtymDUFT0rMrUl6dUGFPKQyQNIIQknrEAmwG8Z1wFuGYz9RMI%2BxO4Wqjiduwhrf4jGxeDQBrhzzxVc2aW%2FdQvYD2IWRfu3jW%2Fg%2FzbO6SHfhGoj%2BSxAYTntT5us8SGO6XJJDk3U8XOSbIUbBTzrjbabnsF1C57otmeGTOJchsbIwLiio0%2BozTlPZqLc1IFRZWhalpUmygCClTahvz2PbGX43s5xj1MGxBzJl0%2Bb9FNCM18IsNOeNNJ8pvCrSj338ZmOfmI5QHLfONl4TyFxjjLJ%2FFmdVLmqc3RsHqWJmVfcKZmbS2lCniyALEoDiTYkatwOUbOz2yYy8wbw05U5gYaozkpXK14p7IzZfWvx4TEot5RWknSClaAE6fgkg3jMMhmNPAfnC4lVys1ZR81peXFoC1eDj2zlxF%2B6w4n5Jxr540TO4XqeYmes9g%2BghlNQxJi2oSEp4w5pQhxU46AVq32ABJ9Eb38HGnVnXXE2VvhtA25foxnnGqsnVJ%2Bq2wm4FdU5hzQBPnmpiAxbOPKavZL4%2Fm8vsSTspOzLEvLTrE5JrJYmZd9GpC06gFJOygUqAItGCOW5Ax0Jx9Lcl%2BIOszJ5tYXpC0DnYCXcI%2BO20X7jLyVyzyvy%2FymxDl%2Fh5ymzeIGHG6i8JhbiJwCRl3wteo2DgW4rybDSfRAcs3N%2BUR1GI7CIah3CAmhEExOOUBKpQuL3v2eiKZuPhbdkVSFckqEQ0C%2BwB3%2BWAp25HURAXGoa725WioQBc6bxTIPVGm1ucBNcxCEICRZPwVE357XibR1NISfit6oitHWCQjYch%2Fv3wuL3CtxASIUlW6RYfliZToTtpN%2Bz0dsU0oWo7C3d27xPcpFnB6LQFRBRbbf0xKbavLt6IkCk37%2FTE50diICfWkAXWYjLMTk9NJlZOVmJl5y5S000pxxVuekJ3PntEg5%2BRfaNy8HS5hniSwtMSbq2piXpeIH2nEc21opMypKh6CAfVAasOHsTJISvCddSTyCqY%2BL%2FyYiMLYnUtTacIV0qSdKh7Gv3B7vJjNaJxOcTb0tK%2BK5%2FY3JfaSuzk%2BlVyU35rSYuzmf8AxTvIRqz4xqlKORFUbHx2Rv64DWjWHsSpsUYWrZvf%2Fm57s5%2FB7I2XkzI1el0HPGZnqPUJLpcp6iyHH2FshQ8elNSQVAb27O2ITHEPxPSLOuaz0xetG6NPsgg3J%2Fep7YynL3NzNrMDLzPOkY5zErmIafLZazUwzLz74cQ26Z%2BVTrAtcG1xe%2FbAaKlp5cskDowsrVq52iquv73MqnV5JIVzjyStLm5xsLb0qA59YD%2FcxXOHp8JS4ppFiLi7g9XqgPDVZhdULp09Cp1kM2ve3VIvGxc7s3U5xVbCVdXRVUteHMJU7DDjZeDnTrlAoF9JHJK9eyTuLbxg0pQaxUKzK4fplLmp6rTzyJaUkpRsuuzDq%2FJQhKdyT8kXrH%2BVuY2VVQk6VmTg2o4emqgyX5UTbdkPoBsrQ4LpUUnmkG4uLiAsrddSjRrlFfvkqv649DVblgVlbRKikgBRPPsigMPzykBaWkEHucESOUKqNFV5W%2BlJWbKHIC5MBsvJLNTLnLaZansVYAr9QrlMqrNXpldw9XTITSW29JMhMIUChyWcUm6ttW9uUXLKvEyce8XeCsXP0eQpasQZgS1SVIyqNLEvreU4UIHYB8pue2NVYYwtiLG1cksMYToU5V6zUFFErIyjet54gXNh5huewRsXhllnpTijyukpxhSHZbF7DL7LgsUON9IFIUOwhSSD5xAYxU8zsxBWqg7L5o42baFRmwyUYhnACgTDgSlI6TYcgBFMZmZxKGpOZWPinzV6dt%2FPjLMhcMUqu4qxFVqlKtzJpM26ZZDidSW1uPvHV5yANrxtCuZw5b4Uqb9ErlRQ3PShQHWG5VSy0SAoAkCwuCDaOJesWtLG8TdrGymuY2vpOCaC3S%2BYTZ4tiV7ixotJmKdUTsmY1zMxrnKdXgaAGY2b2oJVmPmACNx%2Bf88fX5cGsxM2GlKU3mLj9BWdStOIZ8aj3n3yN3HiIyWSnSvEBaVe9jJOD8kVU8RGSt0gYtl7G4UfFnth9xGHvpiHJdp5%2Fub3EvRmNuLU81PaaQOZGcCmwDmRmEUJOpIOIp2wPm68RTmfm%2BhCwMzMelExs4FYgnClwDsI12IjdSeIDJ9XXTX20gAgASzhv%2FJisM%2FcnXblOJGNI59JKuAn0DRCMVv%2FAC3fr%2B44l6Mzsxej1e05rcYfmG1IMsttK0lPUbI280dM5Q8XOPG6rTMLZo5nNYWwpS6StiWn5TDLc2%2BlTDNpdhaeZCrcwBdQF7XvEnu55NuKSBiaWUntIlXNv5EVV5t5TqbEw3XWlJPJSJRa%2FwASdvXE99b99Wnn%2B4p0J0aq2YvRzU9pq3MjiLzezjoMnQcfVaXmpGWnDUpZmXpSJQpeKCgKOkki6DunvPmjWa0Pr6jjLnldUaT2b388dMozjyjBKRiBoWN%2F0Esb%2BpEV1ZuZWNi4rrDn2wEqu6e6%2FViO%2Bt%2B%2BrT17iNCNHJjPvxRzU9py%2FwBA4g6XGVJGrkU2Px%2FkgttxNwJd5Vh2IMdMKzxynbC0Cf1I7SJRZHr6sROfWUTVyK1Lt9cneUdBG3Z1Id9b99Wnn%2B5E6DaOTsxej1e25oB6M9dDl0p2skxWDS%2BkOtOhSbc0kKF46gwzxC5I03E9EqU7Vpd%2BVk59h55JkVkBAUNR0lFjYdkbtc4vOGMOrDNRln0pUSHEUQEG%2Fn6OO3hc29%2FoqqtqYs8p2TO18%2F0tudx0evNFhcbfumKozmqnZE57NUz6XzzWgg7uBXq3iPREfBJ9AvH0Dd4v%2BGEFXSTcoNXPXRgP%2FbiLHFzwsajpq9MbUoWUTSQL%2Bn3uOtGHVzsqjneQnGIj6Orr3OQOHzGWHMEZwYfxFimqJptJbTOykzOrQpSJcvybzKFqCQTp1rTew7YzDDriqLIYIkHeKbKycp2Am3DR6RN0iccky8rWC8%2B10Gl5wBRstW42PZHS6OK3hevqbq1H9IpKf6qKg4reGDbVV6V6qKk%2F%2B3G3Y3Kuyp1zE%2Fa5l%2BvcXuqKspp1ZbM%2FROzVMZuccb40w4jDWZFSquaeAK%2FV8WYVk8NU%2BQwjSn5O7qKgiYDrqC0hBATruq97WHZHPyxvawT6VcvSI%2Bh44reGBtsJbrNISF80ew6R8Y6OPMvil4V0e%2Bqq1ECrX%2FtQCr%2FRxFvdK7xlGcREedfD75RcLOaODVV%2FXofPpetoi6QARfs3ESLWT5CkqH76PoC5xYcKt%2BjcqdJO17Gigj%2FRxBPFlwoNA6atRE2uQBRUi5A%2Fvca04bVHzo52%2FwB%2BafJz%2FX2Pn6S2OZSP4QhrY0X6RH3Qjv4cWPCW8oFdQotyOaqEnbbv6OH1VvCgW7pmqKRa2n2DQPxtxMYbX40c535p8nPXufP1IbKrBaVdpSCL2ik50bcfRuo4ayL4j8DTsrRqRS1NBpxMlUKfKIYmpF8i6HEKSBex5pNwRcGPm3WOlkX35N5YUuVecYWRyKkLUgkekpjXvF0ru8RVMxMS3rnf6L3M0RGVUbYlVZqTMkpwuA2XtZPZERiSXA0LaUSOXnjBKhWplUwoMKKWwdIPf3kx41VScPlPq9W0arcbInsSNTqWAUqSWWyi6u3flG2Mr2J%2FFOR9fw3QaNTq%2FPtY9olZmaLNzyJcTcixLu9JqK1C6FEhB0m4Crxy8KnMj9PX8d4nVNuOJuolXpjJZV00V8KqM419cZMF5sqraz4NM5TqnmnPze12%2FMU%2FMjElbqNfzW4c6Pi0AIYw%2FJtYxZkpOhU9INpKXbbcN06tJ1%2BVtyjWmdUvUcJYPywwZXJNuQq9IkK45N0xM0iZMmh%2BfK2ElxBIUOjIAJNzp3jmkTTg6wsLRH2SmR5Lqh6I2K7xTVTMRE5zy6vNuaVjcLSztKapqjg08kROWyY5apiNuezWzh2oAuWVdO19olE8f1NXxE%2FEO0Rg5qs%2BD%2BiFRAVaoptaaWLcrGNN1Gb%2ByTbcTCpsufCMYMKpPD%2B6D8QiY1eoK5zjnqtAZx7IW8jeNl8PWePuF5lM4%2FXQE1llmSfk32ErDb7aXQB0rC1ApQ4kp5nsJjnv2Vnv1478cVfZyf0hK5pZA74Dr%2BuccGJJjMGpY7wflvgmkzE8dPjc3TOnqbrenSQ5NJUCCpNwVIANjzi%2FM4upeaeEE4iyO4fcq5qtyKCnE2DZqkF6oMqG4npJXSpM1LrB6ybdI2oEEEbxxD7LzKv7oPxRO3WJ1t1D7U4tp1s3Q42ooWg%2BZQsR6oDtisY2zE4dp%2FC2L8xeGvKOXaqvTLp6ZWmWfSUIGttV3FhpQDidSVoO1xHOOLsWSWK8S1DEUrh6kUFM86XfY6kMFmTYPI9G2SdINr2BtcmwHKMYxNm5mTjSmU6jYvxxVazJUm%2FiLU490gl7oCDpJF7lKUgkkk2EYymqTiVHTMKgM08fb74rt1FhKkpQndO4APMiMF9l579cq%2BIRKqqVA%2BTMr9VoDZ6MUNIZMv0bmgm5621%2FRERimU6B%2BXOsKdYLae7USO%2FstGrvZaoHqmZXt3xEVWeH90n1iA2Q3MNuNq31dURL0izyMWDDtUE%2BlTDwSl1sXKhey09%2FmMX0dXlATalw1K7Ykurthc3gJirVtvvEUtovpWuxiQX8pKheCtQ3JEBf2q1KpShGhZUEgEWFto9NPrEvJTDMw2halJUCpJsLg8yPPvFgRKTKkBfi6yk9oBMTdBNJVpMq4D3FBvAbf4b0Y%2BcxvVhl9VKJJzfsDNCfTVJF%2BaRNSZcZC20NS5D5XqLartm4CVE7XjuUUzjn63%2FCflF%2FEtQO4H7%2FAL4%2BemT%2BWFezaxJN0jD9Yl6bNUqmvVQvLD5XoQtCClsMAuFRLovYeTqJ2EdCHgDzr8hGZlIV%2B9n58ens3EBsjOJni1lsJVd3F2Nstp4S%2BHK1NK8SpNSb1SQYSmbZS4SWUvLbUAgO87HTuDHPPCDmdgvLzG1XoeP5kSeHsbUcUOYnVLU2mVd1Etla0nU2hWtaOkHkKKT5xd8c8GWcWCMOVCtVLMGQm2pGlztWflW5moFD7EqhKnEFZHQhZSoaUrI1WNu2NCUHDuI8YVRug4Vw9PVifmAQ3KSbJccUO24HId5O0B9FcMZO4ioGIKbVMzM1ZbFWA8BBT%2BCBUHEB1C1A6Ziou%2BQ%2B4wg9G04Cdusd4444ss1qHmxm%2FPVrDr6ZqkU2WZpUhNgECaS3creF99KlqVbzAGNZ4rw7izBFSdwNjGQqlJnKdoU7SZt5dpcrSFJs3qKRdJB22ixL5iAjfc2jrnLOxy8wuFrNk0pm21rm55n0RyGj9N8qOzMrUsoyzwwpaQU%2Bxbd%2FjMWs5ytIjzT7lLePxE%2BmPeztiSCZVgoAAUjTcgeof64k6EyzulsFISAoK7Fkdnmj04fmmpmWQkt62QglKVp6yjyO0VHrM3ZWdK3bqHba29vX3%2BmN5yZqmJyeFxZbWkr06PJ897bRRccb8fQWfekaRp5C%2FpAi8yuH6lXW2ZWSYDU64sBtDjidBJ71HlGKY3RL4RrD9LrmLaK4ZNLSlNyUwHukDoNyCkEK0kWUAQU3HMGLUxM7FZmMs5e2ozQSHOjcTqUAnq7EA9seZZl3G1L6T33T1VJVzt2ee%2FfFrRW8BzUpMTreP6V0so0FiXnA4y4%2FZNyloqFlHsAJF7i0ebFlPrGDZ4MVLxR9icYbm5abk5pExLPtLvp0uJNtQsbpO%2FLncRMxrylanXGcL2zUJdDSnZpNwls6lX3vyvFgqeOZCmthTaSnUrqrCbG1rEj44xJ%2FEbrij0i7ApBJB3%2F%2FADGITlbemZcMOKDvUVpJA5dhi35rJk9mYeMZirSrjLU2pTOkFSU76U2PP0fljVtFqTrTSUqdSS2dhYEc%2B6Mun1teLOvPNL6FtlxboQkAqNja3p2%2BKNeyyVMNoCjqO17RS1rmZjNlu9MRE%2Bdg2YVSmGcVz7cpMLaS4gAhs6AAoDUAByBI3748FZUyWKb0aEovT2QqwtdQvcxTxy70uKp1Xc2iIV5Jb9jU2IBp8uRc35pvGhP50ujT%2BbD3YdqdapU01MUetT8i82Qpt2WmVtrbINwUqBBHIfFE2K8TYkqE85Wp%2FEFSmanNOrdmJ56bWp95w2utaybqUe0mPJSli6Y89e8kemKyStLlQqMy5qmKjNuq71vrP5YqJdmAmwm5gDuD6%2Fnjwg2N4qhwxCHp8Yfb6yZt5J7w6q%2F44qCqz42FRm7fa9Msj8ceHpYgFEwGc1PMfF89gKiYEqdW8YolNqszU6chbYL0s84gJdQl3yujVsdBNgrcRk2Esx8Z4FlFO4HxyqnCpMtmcS1Jsu6ikkhCumQvySTum3PtjVVTnzL0GSZRLMLWtx%2F31y6lJFx5IvYfFHtlJo%2BIMOW%2FSxAbZmeJPOoEqOZc1cm5IpcgLn1MR5HeJrOtwFKsypyxte1NkU3ty5Mxqh6ZQ4T2GKJWO%2BA2ueJLOm2kZmVEDuErKD%2F2Y9DfFJny0fe82q0kW02S1LAAd32KNPdL6IdL5xAbld4ps9ZhRVMZr1pd7XuzKnst%2BoxR%2BqSzdIVqzMq3WGknxeUvb7zGoOl84h0vogNwscSearYN80Kwm%2FP8zSh%2F9mKrnEzmq6nQvNOrlPd4nKD%2FANmNKlVzuYa%2FNAbmXxKZquK1KzTrZNrX6CV%2FqYmHElm2Qke6zXgE8rty%2FwDVRprX5oa%2FNAbjHERmmtsNOZv1wJBKrFtg7%2Feol%2BqCzMKSheb%2BIFAm9rM%2F1caf1GJ0dYXtAbd93vMVwaV5q4hI9DA%2F9uBz6zIA0jNPEAT5xLn%2FANqNSWhpMBtpefOZDv2TNqvq9IZ%2Fq4irPjMVY0qzXrpH7yX%2FAKuNRnlFI84Db7meGN3EaHMzq%2BpN72tLc%2FvcFZ7Y4XbXmZiI2Fh%2Bhv6qNQDaKgWRAbdGeuO3raszsTG3K5lzb%2FNxM7nfjtRK3M0sQG3VJvLG3mPvcalaLimnbLt72qOv%2BPrDeGaMjJyZouHpCmTM5lzTFTipSWQyX1i%2FXc0ga1%2FujvAaaOdeLlIDTmadeUgG4Fpcb%2FeonXndi1dtWZ2JFW5WVL%2F1UahhAbeczrxU5bVmhio25avFzb%2FNxTfzmxNMqK3808TqURpJ94uR3eRGpYQG22c4cQtJCG82MTISnyQUMED%2BRtB7NWszFy9m5iIgkqI0MgXPmCI1JEQkk2gNonMKYPVVmxiIp86W7%2FzImczIm1gpGb2K7EWNlhII9QjV4YJiRbakmA2gMcKVcrzbxUdXOz1vyRIcWyavKzYxTtsPfze0auiSA2onElAKD0%2Ba%2BKAe7pF7j0iIpq%2BDl6Q5m1iUX5klZA9V41XY84DnAbdFRwkUEpznrWrsBcdH5IjLTuF30KLmddVl1DkHJl0X%2BJMamG1oqBzsgNqsVWkLXpazwqzKftzPvIHyJiv4%2FS79GrPOrqTe101R4j07CNShzaKjRuq8BtcTlNcGk56VkDuVUX9vkirLHDTrw9ls2q1NMWspTNTdJt6DGrEpBG8e5tDfRp6kB0uvAnDM3hyXrdF4m8Tzc4sJD0g7JvoeYUQd9wQQCLE37Y0ziCYR7NtYWGIHMT0iqPIYYfmGNExLPLOlCgoC9wojccwTHnoqGzTFEeVqi3tpLmMMOICgCarKWJ7Pf0QFkelZmnTE9TJxGiYk31yzye5xtRQofGDEcCke2amj%2FwCtY%2F0gjMMV0Wm1DHWIpCjViScm5qrzqm2lTKbqPjDh0XNrEefnGJYMln5THNOk5hoNOt1NhC0A3sekEB%2BlWEIQCEIQCEIQCEIQCEIQH53%2BI9Ns3sdt%2FwD7T1T5Jt6NQu7yyPSVRuHiT2zkx%2Be7FFV%2BWcfjTzn6DSrzqH4oDK8Mf2sv5xFyWm8W7C39qPPqH5YuZHbAUiYgTE%2Bi5IiGjYmAkJgryYHsgeW8BLEUxEERMCICMdB8OnDTTc06C9jXG9TnpSi%2BNLlJGWkCA9NLbt0i1KOyEAkDa5Jv3Rz6ki8d68Psx4nwlylSRqbXKU6suhSTY60hxQI897R4T4QcUvuGYZZ9w1cGq0riiZ5YjKZnLz6svQ6WF2VFpbTVaRnFMTLxfUicP5ASJushRNiDVR1T5xpgjhByHKSkT1XOnmfZVNx%2FJjkfAkth3FGGa%2FO1PEUrh4TVGkaAp6fampl56qFQmXZtotXCTpb0K1fb8oyao0LBVTma23Tc0ZFs1R2lraDdLqKxKplEaVBO3N1XWVf5I5VWimL0zNMYjaz5%2BDVPg%2Fe8%2FU2u%2BdU08L4ujmpzdKDg8yPCivxqs6jyHsmm489tMTfUf5JWsHq7Y8z7Jbfzdo5XxNhDDNXxJUq57uE5LKqE45NeLyNLqCGmdRJ0IHYBe0W6XwLh9b6nVcQNRaSlXVYfk5%2B6we3ntFJ0TxnV%2BUrXP%2BGr3VlOIzyUWfNG510eDzJNRKNNe1DnqqY%2Bj%2BWIJ4QcimwTrqx9NXTt%2FJjmGew3T602yxM8QRSWKYxTEhqQnkFYbOrpNj1nTaxJ53jHJzH0wifnKonM%2BsMzU1WFVRXR0NaB0%2FRdGDo1206eSd0jsivFHGZ1Tidr0a%2B0mcRqjLOzs%2FV3OwBwfZILNgqsKKTpP57JsPMbJidPB7kgo3CKwvVe2mr%2FADCOIma%2FLMsGUZzWxMhlUm5IqSac6SWVudIpPl3uV76vKA2vaJpjEGtDj5zQxM8pxTSyBJPoAU2NKCLObWGxtztveMkaG4tMa8TteartHfKY2WdHq7nbY4QcjiQQmt9Xs9lDb%2BbD6j7I0DnWjbsNWI%2BW0cszmFKRKudBKcTdQfSlQ8mVqCLhW6lEX2323jyu4Vwql51tPEVW3myQC4mnVA6u86SoHntz35xTidi%2BX6ztujV2004jVM6rOz6tzrJPCBkcANaKqdO%2Br2TOw8%2FV3iqOEbJcXCWqvdQ1XFRAsPN1bgeeOSZKh4blZdxv3f6sbr8j2OqG49S9vliR7DuDlalPcQWIJpYOlltEjULqv2C6torGiOL07cStujV21oxGrP5Ozjm7LrccIWTI62qt2PYagFD49MQXwiZJjylVpP8AlAD%2BjHIowjh8rQpGeWJ5QJ2JNLqXVP3UU3cLYcIKpjPqvdItYSQ5TagLjtJJV8kWjRDFp24nbdGrtlWIVeTs%2BrsuvRwiZI9pq59NSH0Yj9SHkdflVf40H0Y5KGX%2BD1klOf8AVlADUUokZ0LIG50gr6xtyHabRgHSUZ1x5SsycWobS6sMpVJv61ov1SqzpCTbmN94mNEMWjbidr0au2icQqmOFwLPqz9jvdHCDkgDdRrNu4VNP0YiOEPI0ndurj%2FKf%2BzHBaPECBpzSxekWNx4rMXI7j75yiT8xISFJzJxi4e1JZeH%2FuRM6IYvOzErXmq7ZTiNVWr4ujq3O%2BTwhZHqbCGpesBQN9Qqe59N0xH6kHJVW5TXDcWSRU%2BXqCY5EVl9hGXWp6W4ia44S2nS4mlziVKUQLp3c7Dcee0SMYBwc7Nty7nETiNpoWHjBpk7oRtc7a789oidEcXjZiVr0au0mMRz%2BZZ9XZdc%2FUdZLatXT16xPL2T2t3eTE%2F1HmSXIKrx%2FwAqp%2BjHIPtHwYhtXR5%2B4t63NKqXNi5HImzkVG8J5dstFRzuxcp8HqBmRm7rWTtp98iOKeMf4ja9Grto7tiZymiz6tzrZzhDyMa5qrd%2F%2FN02%2Fmw%2BpGyL8rxmrW7vZZP0Y4%2FmsAYcS44uZzSxvLKJuUPUWbCr95BXtzjxuYCwclWtzN3FiE%2FbuUd9P43ItGieLTGffG15qu0mb%2FXEfm2fV2XZq%2BEjIoDrGrC%2Fb7Lcv5MUhwkZCA3LtZJ89YH0Y5ElsCYCcTZeemJ1tkdZAkXUHz7FyMMUnCRmHUIxvjpKAs6QZbraATzs9YG1ojiji8%2F3ja5eirtp7sqqjZZerud4J4RshAvUv2X%2FAIVXAH82Iq4RciFKul%2BtDzezN%2F6McIdDg9zysd48T6ZW%2FwD7sQcl8NNAdBjjG7hCxb3rSLX3P2XnEcUcX298rXmq7avdlccll6u53keETIxQsXq0f8r%2FAOzEPqQMi%2BfSVm3%2FAJsPoxyE9gHLxqZcQ3nxi55pJslwU54FQ77dJcRK9hbAEslUtKZy45daULuWklhK%2FNYubQ4pYtEasRtuartIi%2B1TOqLL1ey6%2FwDqQsih%2BmVn%2BN%2F9mIjhEyLKQkPVhQve3sqDb40xxunCWXbmy81ccADsEmq%2F%2Bkj0S%2BEst3U9GvHeNyT5IRKrWpZ7gA5CNE8XjXGIW3NPbZYvdXLFl1dl2AOEjITa6qobdnsqLfFaJfqRchft6n%2FGg%2BjHH68vcFN3TM40zBYA%2BCqmPC3puvaPO7gjLxtelWPsfNJ%2B3ckFpT8ZchxWxXlxC25p7ae7J%2FyursuyvqRMhwQUuVUd49k02Pxp2h9SPkQBbpKtvzPsqnb0dWOPZPA2XUy822vNfGZUT9iSwvURzNj0lr2%2BWMHcVh0uurYxHjfo9aujQXkFSUA7aiHLXtztE06J4tVsxC25p7bFN8q2xFlPN2XfJ4R8iyd5qrn%2FACon6MDwiZGrKdM3WEgc7VJG%2FwAaY4ICKL%2B2bG339H9ZEqmZHSeixFjJZ7CqaSm3%2Bci8aIYxP95WvNPbV74WlO2mz6tzvlXCDkTcgTtYF%2F8AvRG38mJfqP8AIXZK52sq1K1XNTTceYWG8cgrwdlczMKQ%2Fmtj1ZCrEpkVAjv2Lt9opKwllkEJW3mTmCpztBldNh6ekjHxUxbPKcQtuae0yTfap5LLq7LsM8IGQl956rj%2FACmn5olVwicP%2FwAOpVX11VI%2FEmOQfa5lG3svF%2BOHOt5a2t%2FSR0kUvahlQ4slWOseIB7BLXt%2FLi1Oi2Lx%2B323NPbU7sq8FnzR2XX44TeHhpQK6xVRbygurNjV%2FJ2jG8ccGODl4cnKjlxiKoioy7C5hhqbWmYZmNAJ6O6QCkq5BW4jkTMLAlHouGafjHCdWxHUqRM1N6jzMxUk9CGptDSHktpso3JbXqvy2jurgdaffyBkHJl1x1ZFRWhTiyqyEvAJAv3bxz8XsMX0asaL5Z36uueFEZVRq15%2BGZ8GX27WWxrpvVc0WlFExEZ5xHo80OESSTugoPIpPYe0fHGX5T5cVXNfHMhgmlzDcr4ylx%2BamnElSZaWbF3HLDmQLADtJEYtNEKn5kp5eMvW9HSKjoPgdbDmck2k8hh%2BbPr1ItH0PSTELbDcJtr3d9VcU6vNM8v2ORcrGm1t6aKtcZtrMcHuRlOQ3LVOv196YKRqcdnmmQsjtCbbA%2BuKo4RuH42DFeq3SJOo6Kq2o3%2B5jQnF5Q3Mb8TEthuYrfsXLN4dYmHZxSXHGpRltpxxxxSEb7mwuB2iNZjKHCzSA6nPaXCza4akJq9j548JhmB4xidzsr5XiNpE1xE5REzln6Jh0ba%2B1WdpNNNFGXnyz9js1PB1kY8Atmq1pSfhD2TRufQExP8AUZ5JqVfx%2Bu27k1JH0Y44lcv8C08uiZzoEwv4OiWnW%2FkSYg9g3DUxMtN03P5Uo2pO%2BpE95XmuY3OKmL1TwYxG15p7SsX%2FAD202f8AX%2B3J2P8AUY5Lk6BOVxR7hUEE%2FwA2H1F2TSBqXM1%2B3eagj6McfM5eyvTA%2FVMPAjktaZzb0G94x%2FFNNbw9VnaQ9njXpxbQbUp5MtOFtRUAq6Fa9wARvYRE6I41%2FiVp0au0rOJcGfk6OaOy7h%2Bozya5Ccr38YI%2BjEfqMsmVADxuuggW2qKPj8mOCUPS6l3OctfPnEtPX%2FnxV8cDKitjOfEgIF9peeTf%2BXCNEcaj%2B87Toz2jvr%2FlUc0dl3gODTJS%2Bn2SrOru9kUfNEU8GGTWqyZyvLCd7Jnm%2FoxxvQcKKrFIl6wriOm5JL6nEmXfRPhxGk2uRc8%2BY3i5u4KlvF2y5xUP616itu1Q97ty37b%2BaInRLG41xiVp0at5TiNUzqs7Pq7LrU8GOTquU7iIHzTiLfzYingwyfP%2FADjiFPn8bbH9GOP04TaCTq4oXQo%2BSkCoX9J7ory%2BHJSVshziWmXQT9lT7IWR3A7jz9hitWimO5asStOjO9kjEJ5bOz6tzrhXBflGqyUVPEbaO0%2BOtG%2Fr0%2FJD6i7KBH%2FOeIbnkTOtcvRpjj%2Bdo1KffLiOJKbQsiyj0dQVe3be9opGgS6LITxMTbd%2BYU3UN%2FReJp0TxyduJWnRneTf45KLPq7LsccGOT42NUxCRzsZ1r6ESr4McnVeTU8QJP8A49r6Mcgt4NU4duJmaAKbgq8eT1u43O0Y1iZh2g1lVNlM%2BMR1FLLaelmGJac6MuHykoJX1kjbrbXi3FPHM%2F1ladGd6s4lMfR0erudxt8FuT4CkuVTEbhHYJ9q%2FwDNiJ4K8oCoEVTEQT2pE63%2BPTeOCzUJwpCPdqxZZIsB4vOcr3%2B3gmdm%2FhZ0Yr9TE39OJ4p45%2FidpzTvR3xidtnRzRud6HgvyfTzqWJUjtInGzt60xMeCvJ9StRqeJvR4%2B2B%2FMjjSjYTm6nR2KqeIaqyq3SoCWmUTqXUAKtcjVYA8xvFV3B%2BlRC%2BJeeChcaUpniRYc%2BdvlieKmOR%2FeVp0Z3nfCPJ0dXZdjDgsykSQU1fEuwsAqebP9CCOCzKMqK11bEiyb3JnWjf%2BTHHKMJp%2FwD7m5%2Fq%2BTdE7b03vFzZwtRQjoJviWnJkDk4lE8pIPaAAQfXFKtF8cj%2B8bTozvZKb9TPzKOrc61%2Bonygtq9lcRW7%2FHWvoxD6ijJ79lsQ%2FhrX0Y44qVEpfSEy%2FERVGk2soBioaQfNvHkTQ5Rd78SdUCLhILjM%2FY%2FGYtTotjkx%2BsrTozvJxCI%2BbRzR2XaaeCvJ0AE1PEBB5Hx5ux9emJjwZZMq8qdxF%2BGN%2FRjjprAi3wGlcSM02NN7HxzSPN5UWGtyqKDU1Uw5%2FYjeUykB51EpPdH0nchQV1k2%2BFYRbirjfLiVp0Z3qziPgs6Orsu4RwY5MAk%2ByeIkg9njjZt%2FJiH1F%2BToOpNTxEBz%2FRjXx%2BTHBxmkqGg554oPVP8Acc9b0eXEPe7WTnRiNItawkp36UOKmN8mJWnRnepOJz5Kjmjsu9E8GOTqb3quI13OreebFh6kw%2BowycNrVXEBJ5fmtv6McXU%2FB87NSMjVGuIKosonGek6N7x1DjBClJ0rTfY9W%2B1xYiKwwrOynRu%2FVITyFNqukNePKKD2EWNh6YjitjcTrxK06M7ycSnZFnRzR2XZA4LMohfRVsR%2Ba842bfyYqDgryd0jXVcRKNzf82oH9GOMva1MoKmU8SU%2FpJ5ATwSfTvePTLYcpqW7Tef8%2B4onrnRPnc8yOuLxE6K43t75WnRntL04hHLZ0dXZdhp4L8mwetVsQq%2Fxxv6MQXwY5McjU8Q%2Fhrf0Y4wmaBSVuAyefs82yUiyujn76u0W1GPK7huWCgo8QU1dI5lM%2Fse7cwjRPG5%2FvK06M9onEPBRZ80dl2yeDHJIiyajXgQDzqCN%2FwCRtBPBhkp0elFTr1yb6hPt%2FRjjFGAG1tKfb4g5hCkpubCc1E9o8rl54tNfpicMVOcovu8V1apQI1LlpWe6NaynVZPW3FiOtaxieKGM8uJ2nRntHfCrkos%2Brc7kTwW5MpN1VnEJ57Gdb7f4EDwZ5LlIKa1XjbkBOtb%2Bm6Y4HWFu3LmdOInAVAlSpWdsT38%2FlgqXaslK85awsIN0hcvO9XfsuraMlOieMcuJ2nRntKTiFXk7Pq3O91cGWShWNdYxEO782tc%2B89WJzwa5J6LKq9fuRYkz7Yue%2FwAmOJpLAyKhTJeojiB8W8ZZU4ph9M6h9lWsjQ4nkCQAoWJBChEzuBGChDT3EKh5CUnSlaZyyfNaE6KYv%2FiVp0Z7SvfCfJ2fVudo%2FUb5FH%2Fnqsp%2Fe1Jv8dt4kVwb5Dg6vbBWU6%2Bw1Jq3q2jjOVy%2FwfKnQvN5p1XlKUGJwWPxx5pnLXDjzi1yuc0s0g2snoJsj8cRToti2eU4ha809pab7OWfAs%2Brc7T%2BpC4edwvE9UQT8H2UauPURFCa4MsmZ%2BUcTh%2FFNdS%2BdSW30zTL6G1gbFSQNx3i42jiHEGVTcphusYoo%2BYMvW3KC0xNTUs0l9L3QOvBkuJKuYSop1dwUI354OZM8vFeNE%2BNPKl2paSc6Iuko1qeKSqx7Sm4vHOxjCsVwa42l9oxC0maNeUx54jlmfD4GS72sW9rTRVRTlPgiNzUGO8FVfLrGVVwVXFtOTdJe6FTrQIbeSQFIcSDvZSSDFolJSZn5uXkJJlTszNPIl2W081uLUEpHrJEbl4yG0t8Q2IGkIADUrIN3A52ZIBPqt8UYJlchv3TMFhwXQcRU%2FUO%2FwB%2BTHvbriVvOCUX%2B1j8Z8XFU%2BDhcHOetzosqZvXxXJm6jw%2FwT5eUejNnMTFdWfqRSgTbkq%2B3KyjLvMtoKgSqx21G17G0e0cIvDsvqpxzVU9v9t2Pi5RZPCOTj8vl1QZFkuqM5iFYLbZPvqky5UlJAO%2FWUPXHJ1SySoFLqDkjO5wUcTMsotvgS0z724B1k8huDsbx880dueM6Q3KL%2FbX%2B0pmqZ1Uxq1TyZbPQ6t6tbOytZos6KYiPDludpHg%2FwAgXFdInFlXWFfqdWa0n5IDg1yGuL4irhPbeqN%2FRjiqUy%2BwFJrCZ7N5l5vQSUsSs0NK%2BzYRVmMIYJeTeSzYXKOk6gpxE4L9lr32jr1aNYvH5uIWvR%2F7MUXuPBZ80bnaY4OchBe1crJJ2%2Fti380FcGWRStVq9XRvfq1Jof0Y4sVlhQLKKM8mVkC4CWJvfl3n0%2FFE1by%2FoNBpclUZjOuoTPjsw42PFJGadS0G0AqKzrFiVKSEje4udrRWdGsZjX3xtOjVvRN7%2Fcs%2Brc7QHBxkYEa0V6vBQN7GoN7ebyYqDg2yPULprVe3uSBUmrjccrp5RwailUNQcBzPrigshX9r5o3I5E%2B%2BRFFHoiVBac06%2BhQSUgpkJoEA8x9k5GFOjWMzr75WvRneib74aKOaNzvEcGmSF%2BvXa4U9mmpM%2FjCYK4MMkh5Nbr38Ytn8kcQ0HBGHaoZxCc5qhTlSwQfzRIzSA9qNuqQre3M3tFyOWOHGWnnns%2FnkrQkFoIlJtQcPaAQrY%2BmLcWsZq%2FvG16M70xe8%2FmWfVudnJ4MsltIBq9eJB3V4%2B3y%2B5iC%2BDHJZVv7IK8m3O88yb%2BnqxxecCYdQXEIz9qxQo72kpvrDzjVFaTwbgZl94TedNQnUp%2BxpckpxvVbtF1c4idGcajX3wtejO8i9TVOXBs%2Brc7KVwX5KNhLYruIVX3JE%2B0D%2FADYfUZZI9uIMQcrb1Bnn9zHHU9gnA7xApWbFYBT9kW1T50gH7XyyO6PKnANCUm6c38Q6rXI9i57Yd560RGjeMTrnEbWP9s71arxEfNo%2Fr%2Fa7UPBvkoG1tez1eAXz%2FPBr6MS%2FUa5Jk2VWK8fRUGh%2FRji5eX%2BGJhZ6TPGpG6gklcjNg7CwNiu8efE%2BCsNYblZJ2XzexHUn5110K8WkJgNtNoAtdZd3UVHZI7NzaJjRrGZ%2FvG06M70xe55KbPq3O2l8GWSKkpJqmIBp3uKi0L%2FyYHg1yUKQBWK%2BPOKg1v8AyY4EMlTynScx8VHa28o9a3o6WJm5aSZIDeYmLAAbgplnk2P32InRjGuTErTozvRF8qz%2FADbPq3O%2BBwaZKqSEisYgJ%2B29kGrn%2BTE31GGTHSBz2XxDYC2jx9qx9em4jiPDOG6NiFE27N5tYqp7UoW20Ovy7yg6pdzoSEubWAvv3xeF4Gws0ga898TadiNElMKNxz26TaK8WsejZiNp0fvW7qz202fVudhq4KsmVA2reJGiTe6ai2fj6kRHBVksqxVWMSKF%2Bfsg19GOMl4RwinSk52YwWL3NpB5O33zePXJYZwKgL6TNzF6tth4q8AT6Okis6O47H94Ws%2F7Z3rReafFs%2BeNzsFfBTkqNjWcRJ%2Fx9r6MRHBVksNxWMQD%2FKDX0Y5C9pOGqi0FUzH%2BYD6WwOlVLUuYdsT2XC7R5jl7ShdDuN8yDqt1TSpi59PXisaOY5O3ELTo%2FwDZE3nwU2fVudkngqyZXzreIgfNPNA%2Fzd4h9RXkzyFbxL%2BGtfRjjP2oYN1hQzkxelaBb3yVeQpJ7t3LxQxHh%2FCFBkKZNyGauPKiqol%2B70syeiR0RAUglT19dzfla3bFo0bx3kxC06M9paLaJ202fPG52mOC7JkCxqeIT%2B6M83%2BLTFP6ivJkn%2B3eI%2Fw1v6McJh3Dyx1sdZiKT5%2Br8nTRFpzDlhrxxmQgk2ISUmw7%2Fs0J0ax3%2FEbTo%2F8AZE23gps%2BeNzus8FGTpFhXcRj90Jxr8WmIo4JsoCAEV7ERAN7eNtG%2FwDJjimi0vC9Wl5p5%2FNDH8kWXEIa6bk6CCTuHTYjbbzxcjQMIMrujN%2FH9reUnVe%2F3yJ4uY%2FlnGIWnQ%2F7Ji8URtps%2BeNzsL6iTKLVc17EZ3vYTLXL7mIjghyjBv7M4kV3hU00PxJjjk0fBgJIzazHVvcDrA3%2B%2BxUZkMEJUrpsysxnBbmpw3Hp98hGj2Pf4hadH%2Fsnuiz8Sz543OwBwRZQNps5WsRk95nGx%2FRiVXBPk1%2BzmIx%2FjrX0Y5HXhvDVTbSul4pzUnmULKFOMIWpu%2FcLLNjFNvBkg9pBxDmsSokW6JZPq60Txcx6dffG06P%2FAGVm8UclNn1dl2CeCvJrpFlNVxGCo6gPHG7D%2BTEv1FGUJUT7O4j0nkPG2tv5MccpoODQoJms0swJMoBC0vFQKCAerbXcdnPvijian4VoErSDI47zDnnagy9MOuonUoaQEuFCUJ691K2uTyFwIRo3jvLiNr0f%2ByO6afFs%2Brsuy18EOUmyPZzEiVDvmmrn%2BTEVcEmUKhb2bxGFd4mmvxaY4abqcgg3GKsx0m1rpqqN%2FN9kiCqvLoVqbxXmKbdnsqkE%2BvXFo0cx3PKcQtOj%2FwBlIvUT8yz6tzuT6h7KjSlXtjxJYdvjDW%2Fp6kTfUP5UKTpOIcTAE%2FBmmuX3Ecc4XlqPWJOamq1mFmPJBLiUSwRUQ6HE26xPX2sdovjdDwWlSbZoZm6QLkpnbH%2BfDi7j0f3hadH71otqJ%2BbZ8%2F8A1dT%2FAFDOVA54ixV65pr6ERTwOZTH%2FpDigemYa%2BhHK4puBQ4tcxjXM6aO6klyoJvc8%2Fh84kmKbgOb6zeLc0GDptp9kkG57N9cRGjuP568QtOjHaJtrPwUf1%2FtdWq4IcnGhZ6vYkBUOqTMtC3o6seab4JMoHEFEvifEqXLbAPsL37yNO8cy0XL3DuLKkzhfDuOMx1VefamEU3xidSWVTKWHHG0KCV30qUgAkd8ScEuMcVVnPGnUqZr0%2FOSD9NnH5tiYmlqSktt3StNzsQr47mNe%2BYLjVyu1pepxG0zoiZymmNeUZ%2BFawtabW0pspoo1zyZbluzgyrrOT2NXcIVeZRONuy6Z6nzzbZQmZllqUkEp%2BCtKklKk9hFxsYweOouP5pLOP8ABBTbU7hdTqj3kzMcuntj3GjN%2Bt8SwmwvV5%2FPqjX58pmM%2Ftycq9WcWdtVTRGqEoNovcxjfF85heQwPOYmqb%2BHaW8uYkaU5MFUtLOLvqUhHYSVKPmubWvFiPOJ08o7rXXqj4uxXQKbVqNQsRVGQp1eZEvVZOXfKGZ5oCwS6nkoW29BtGwOGzN6kZL5sSuOMQUaaqFMFOm6fMNSih06A9os4gGwUQUAEXGyj3RsrIPhDoeNcvms282cVu0PDk2y5MyjLKksqXKpOkTLrq9m0KIOkcyN%2B0Rg3Edl3ktgWj4arWSmOfbExUvH01EGfbmAwpkI0HqAKRfUq4I7Nj2QGu8d4o9uOOcQY1aYXKKrdYmaqhtLnWY6R0rQAoW3SLbjtEeTEmKsTYxqasQYvxBUK3VXGW2Fzk88XXVNtiyEXPwUgmw85743Xn5w8YMypyky%2FwAf4aqtXmJ%2FFS2kT7M6ptTKdch05LWkBQIXcWJPVjJcuOGnKKUyZpudWfWM6jSadW0tPSjcgrQ1LNOrKWulWELUpSilRsBYC2%2FOA5wnsZYvq9BpeFaxiipz9FoRUaZT5h8rYk7ixDaezYkeYGwhIYtxVTKDUcKUzEtTk6JWXEO1KmsTBRLzi0W0KcRyJFh3XsL3tGQ5p4cwBI5kOUPJSuTOKcOzyJFNKfUrW87MvpAUwSEpuQ4bchsRHS7HB1kxlvhWWqHEDmYKfU5tYbKWpxuUlmnbdZltRBW6UnZSrAXEBpnhXz4ofD5mJUMWYjoVSqtPqNJEj0cgUdK26l9DqFWWQCk6NJ32vfeNUTNVmX629iKUdekZtypTFUZXLulK5Z1cwp5BQsbhSCobjtEbCxXlBIzWfU3k%2FlBVBiKSm6izL0SeU%2BhwOS7jKHVPLcR1SlsFd1D7XvjopfBpw54Zfp2Fcd5uzjeKKgAhkCfl5QvuK5dFLrBNvtdZGqA4zxNiPEmMqxM4ixhX56t1acCUzE9POdI86lI0pCjsLAbAAAeaJK9jLGOKKfSKLiXFlWq0hh6VMnSJecmC4iQY2HRtX5CyUje5skC9gI2RxFZA1vILEclTJ2pirUWspfco9UDPRLd6IpDrDze%2Bh5AUkkA2UCFDtA1AuApnmYlA3vEV9sTIG3OAAWiMIQAm0AbxKqIpgJiFeqJCRE9ydrxLpEBEcokiflEkBPaJCnzRPEdt7wFHQ4T1TYRA6%2B%2B5MVFJJHOKZHPSecBKj8fxemI9IUedX23ZDdHOIc%2BvAVEuGxN%2ByNzcIWn3dZZ4%2BUxhLFTyDbbUKPMCx9RPxRpVHkxsnh3x3hXLXNiRxdjf2R9hBSavS5lVOZDsy345JOy6XEoJAVpLlyLwGucMuJak6W4vyUy7ZP3IjJ26nL9Vvp%2FgjrbW5c9uYjNWMPcIcihthvM7NTom2kttq9q8v1bJtvZ7fkIyXBWV3C1jhFfk6PmZmf4xhvDk9ieccew3LNgycqEl0IBd6y%2Bumw7e%2BA1BUnG36U6UODpUvNWR9sk31H1bRnGSVm8E59uKSSPcycRYG3lVOU%2BaJm6TwoPoQt3MnNphZB1A4VliVDstZ6wMZThaucK2CaVjWiU%2FH%2BZ0%2B1jjDntbmXXcMMp8VR4y1MB9IDvWILWjTtssm%2B0BpOkzbDbDofVpV5SVJUL37LiPT7IS%2FX%2FNSezyT57%2FAI4zpmkcJ6ylL2Z%2BazbZBUE%2B1GXJbWbblXTdYbcolFI4T1IQBmfmmhRVZwqwjLmw70gPfjvAWrL9jEdVzgw1I4Bxo1hauT003KydfcfSwinBbSulcK1bA9H0iQPhFQT2xuTjLpxwZhrLvKjDbkvP4GwxMT65CrTFbbn6lVqm6kKmJl9KFEsNkKUUpPNRPKwjWM1hzhGfbDZzXzLW24LKZXg5ohHr6axEX7AOUPDFjiszNDw9m9jhE7K0mdq7y3cHobvKSbKnn7HpDuEJNh32HbAapE%2Bn9X%2BWJhMbrLrgOptQF1d42jM0UPhSdbaU3nJmE1r3Ut3BibAeYB3eKsxR%2BElCymXzgzLUE263tMRZXou8OUBt7gVxXlRgiqyc1O47kKLmLiLEUtTWW6hJuKbTRmx0jjDT32Nt2ZWAgrURpCbdsYNlQzSJfjmwsxhupN1GnDMiZXLzTaVJQ4hSn1kDVv1dSk3PPTcbERi%2Fte4T30kPZ34%2BOxAQME3PmNuk7YyfKur8LeWWZWE8yGs2sbzy8KVVupIkXMHKbEwEoUnRrDh031c7H0QEnDGy0qdxuhRsjxnc%2BYLmDGl8XUerY34h5%2FClLZmXHqviBqU6OWWkOlFk6ykqISCEJUesQNt43PwvEOKxrNpHVecS6lKj5IWp5QHxKtGtsMtr%2BrEb6NIUoVqd2Ive0qvaPPXWPytbzy5R7n1vGpmjQK4T%2B%2F8A%2FwCjKJWi5Z4ZkXaBKYGbryEz82%2BmrVaZWJt9hSgGG1IQejQEJTc6b6lLVvYCPNPUzLOdnKfMTeWEuw3IzfjK2pCqvNJnW9Niw7e5Sm9lBSdxuO3aabjL8CZS1TGmH5%2FGU7ibDuFsNU2YTJv1ivz4lJYzKk6gyhRBK123sBttHfyjlfJomZ5WJKomViyCcq5ZLi7cqzMad%2FNz%2BKL4jK7C8thuvVt7Juak%2FY%2BkzUyl%2BZdnNDDiUjQ4QpICgCb2JANxGbU3LXLuiByvfVFZXTQpjL8yEytYK3VuIaUpKUp0bqKgkJ85Ecu13NHMBFKZk8Q5gYuqErOIs5LTdZmH0KBsSlxClaVdmxFtojKPAnOfCtE7W5JtKGl0GlsqPWKmUuC%2FqK7RbpiqyTrxmGpiclVK5olrIQPVcxZ6pUm55xDsqFAEWNxyMeYrIHOJjgwrwpZUjFk4htLbU2%2F1fhdE2FH1gxnmVuLapVcSSNOmqVRas3O1KVl1t1GQU6tYKko6JKm1pUkKCrG29yLRomb6QmMmwriyTodKVKKQ%2BJlbxc1geTa1rEbg%2BfsiZiDOXT2I8P0eiTU27U8kZ2nSrU6ttap5U40gFKyNOspAHmvvyixD3L3VHxrK5pSCCCGKy6hQv2glJsR2Racoce4nxrjaiULFuclVplArPjEjMu4irEy5T1NqaV9l6RSkBJKQASOemxBjcL3DfIOdG1SeI3KGoOunQ0gYgDWtR8lAK9rk7CLcCFs58LVlMayzpVKkKacunKjMSaCH6hOVVzpZpwrUoqKUgJSLKSkAfaXvvFd73OF1OQqrWCJphiXlXpaapTFTUliacJu0%2BVkFaCi51JGyrDlvebG2CsUZc4oqGDMZ0lym1imLSl9hZBBSoXQ4hQ2WhQ3SobERk%2BXeSGM8yKHUMUUh2j06jU19Mo7UazUWpGWMwRfokrcPWWBYkDlcRHApkznwsafGU02UF%2FLGddWT1h7OuC%2FmFkx6ZzC2XKcOYjqtOybrjD1Mpbs0h2dq73i7B1oSlaylIJHWIttuRGdryExJg9p%2FGE3mLlx4tRpZ%2BfKpTFMs9MBTTalI6NvfUvUE6R9taNBYtz9zcq9FVh%2FHGaOKKrS59CVuyM7Olxl8AhQ6RAAvY22PbDgRBnLH367QEPpb9rbcskHrJTU3lhQv3lNxHhmaml2adekZ1MpLKWFNsKBdKR2jXYX%2BKMVqM2xNv3YXqRHm1uNwzVzZuirttoSlyZDxF7qCim%2FqsYzjLr2hYnnqZh3EOCq1OOVKpJbeqVMrgZmG2CN0NMONFta%2BZupQ5WjQkxNTTatSH1p9BjPcA47XhD2Jr1GrCpWu0x8Tcs8gdeXfSTpWL7E79oI3iKpOE2qnBOTLjoZdrGNlqCykkKlNx2EAE7%2BaKdRy1yoekZhui4oxdJT6myZZ6elWHWEujklxKFatCuRUm5FwbHcRlmXWYWcHEDW05dPN0XEIqcnNPsSzdFkJWZU%2B0nWHG320IUlQIud7EXBEZLMcLXEazsrJuvqUeQZDLt%2FuVmI4MJ2bGtZPK7Jt6TljPY5xgxMlpHjKW6c0tvpdI19H1rlOq9r2NucYtmJl3J4Zp0%2FijBuMGqpRZES%2BuXqMuqWqCVuOlsgIF0LSOqoqChsrlcRkr7E7T5yYptSk5iTnJR1TExLTDRbdZcSbFK0K3SRHvKl%2B0fHyQm7RwpN9MhR6qvfmCkkd4UAR5xFuDEKTr2uk%2FB5L15Yo6T%2B7KtPuKHcUtEbebaOE8RvdJUJ92%2Flzswv43lmO1%2FB41BZy4RKunqMT8%2BU%2Fw2T%2BURw%2FXAEuzCUkkB98XJ5%2B%2BKjo1T%2BTaI%2Fen3uPdYnvlbT5o9rCZhXXUPOR8sVpGWk3gVTz7w36rbCQpdrXJ32AEeVw9eCHOjWlfbHOdrJcbYYH6bVvuEfPFNZoHwH6l62UfPF2oFCkKtR5mbdf0Ll1gPONklyTQdkvLR8Nkk2UU7oI35i9jqdNnaPOrkZ9oIdQArqm6VpO6VpUNlJI3BECYVUChKVZUzUR2CzCT%2BWJqjJSsktKWJxTt7pW240W3WlDmFpO24IIIMW7WIip1SlFSiSVG5JO5MEIkiJbnviETwEtz3xCJieyJCowEYRLc98LnvgKtx3wuO%2BJIQE1xDUO%2BJYQFRJvFTsik11lhMXGdl5MScvN09xxST7zMpXbqvDclNvgkWt27GA8JPbEt7mIXMSkmAyDCiwmdcSRfW2QPNvGYIcjC8K71IJ%2B2QRGXo5b%2Bf8AHAV0uEqtbaCSb2vziQKsnSRzh5W6eyAqC97E29EVEqTa%2Bm8UxqsBa3fAqBNyrlAZnLz%2FAOZ2m3EBKkI6253tve3ZFeUnC1NDpHU%2BQqxIve4MY1QGVVStUiiF9bfslUJWRLiU6lIS66lBUB2kBWw7bCLrmRhFWX%2BZGKsB%2ByZqLeHKzNUtubLegvoacKQ4U3OkkWuLne8BkWScxl3K4nmZnMt2styjdLdVT1Utc2gicK0J9%2BXKJLyW9Bc3A06tGraOjG65wGPe9uYyzPQ5ur80VCtg9xN9Fr2sI5tyczcrOTeJZ%2Bv0aQZn0VKmmmTLLk47KLCOlQ6FtvNdZCgptIIsQpJIMb%2BT4RzMLWtS8rsNWUOrpn3wU%2BvSbjzQFuzGnuD9GD6ujCGMMeKXN0ibRLJmajWFJ9krJMndDrYacaUdYX0igALEXjUeRWPcZYEzHpLWC685SVYkqNMpNTWy2hTj8p422tTQUoHQFEWURuRtGzMe8dmNcd4YqeGZ3LqkSyKtTZqlPKZqcwplLMwkBayyUhLjiQnqFXk3No5yo9Vn6FUpGt0yZMtO02ZampV8AKLTzSgtCrHY2IBsYDdvHYQjiixZKJTpEu3JtgX5DoE7RocEW3MXzMHMHE%2BZ2K5zHGM51qdrVT0GbmG2EtJcUlISCEp2HVSIx25gPQjReO0cuaW8%2FlphhLBbK00trpErJG5BPPvjir9LUuO08v6ghnAmG2i6tK%2FYuX2tzOmJsYzt49E%2B5jvE%2FiZjzx72e06SclXWuncc1NWXZQ6qB5rdkbEeyvqGMW5Vinl6V8al1vJdZZC1qUke96Qojq67aj9rfnFiy9bYnq9JS9Sel0tHSSt1Q06SQAfPueUddZb1Gk1cO1Nro0NsJMnT0kBNpZCrFY861DUfVGxbV2lM5Uc7UsLOztZzrc04tyamadSvz0RNzcwiXbU%2BwwpXRBKR74oDt07kX5iOZMxKPTqN9hb6JtLii1dARrbJ6pA7NvTH0YzvrFLkaQ5MTE2hlDTZbcdvYNlXaT5u6OAsfdBiZt2q0WbpVclGjpnfEZnpF00gH3p5vymyQLgkad9iY690omqx4VXK5d5yotpijYx%2FKfJh3NWbm512pGWlJJ0MuhPWWFc02B7xfcxvWQ4YcOUFhaKUqeDbgPTS10%2BLPX8rU0BpJJ3uLEdhjAcmcYUjLXAGP8w9Mu43SZJgykoqZDbk68tVmkgnmgX6ygDblG0p7icYxTkbP4xwBRZmdclvFpLESzpbmsOF0C7rjJPvjSwFht1skdptY206LG0rtZmdmeUdW9uza2cUcGNuWc%2BHbO5xtmtN4awliyeotDqM243ITHQTaHEhbKQRsW3b3IBulQVy2sTGKBxb%2FUfN1NtjT%2FC5emNqcUWKcj8XuUCpZJ4dmpSamJYS9VYUlVn3VEABIJJWsm4JHPq9sc80CszNGnVyM8l1yUQtbSUvJIcasbaTfe4IsQdxFr1T8VXGrLOM8vB6fOy2NHCoyic8tWezNsi7D1Jf6fR700VHriy7DYWPPb8sa0W4G27xsFh6UnKfOOIWFLclVKFk9QGx29Nrxq2pzjbDH2x%2B1jXqnOM2azjLU13jBWrFE8e9tB%2BSK%2BKZN%2BRFG6Zp1vxikSkynpE21pWFWWnvSbbegxbcSzBnK1MuKWd5dtFxzFgRGws98ylZjLy8aVT5KV9qOAKNhkKlwQqY6BLiukX%2B698t6o0%2BWW3E5RDDaTeyT5opV8kISb9sV6QQUD97FDEJ96RFRYAbRNFIExNATE2iZBinEyTAerEH9oKOjuVNK%2BNSY9UmR7CSyu1SVD5THkxHcUmip7FIfP8AL%2F1R6pc2o8mgfaavxwHkWlV72EEhS9lRMEq5kGKraVOdVJEBIGe4RIpsDsjrngb4V6Tnbi2oV7H8k89grDrSfGW23S0qfnHBduXDg3SAAVKI3tbvjxcb3CrSchcZSFYwJLzgwbiltTkg3MLLqpCbbA6aTU4d1C1nEE7lCje%2Bm8BycrqmClbRXmG9PKPORAS33iaIAG8R88BUAvFQIFoybLDL3FGauN6Pl7guVZmK3XZnxWTbeeS0hS9JUbrVskWBjotfg0%2BLFKCpGDKEuxtZNfl7n5YDlJDYMbHyayKzHz0xOMJ5bYecqc4gJXMuEhEvKNn4bzh6qB8vcI3OfBt8WEqjWvANJd8zddlifxxvDF2Acx8jcgctOGHK%2BizEhmZmrOTExiFcgtKXnVI3WwqYB6rSE7qUDbSk25wGsE%2BDUx%2FMqVTKVnRlVUMQpH9omqwpMwVb9UK0kX9ItHMmZGV2N8qcWzuBswsMzdDrcgAXpWYA6yDfS42sXS42bbLSSDHRk94PDicpldpkvSML0OsGemQlFbotXQtuTfBvqfe6rrRB%2BEL79sbUnsCZkcX%2FAAxP4arMgzXs5cmMVvYaZqC5xoKqUnb31pyY8h2ybEKvuWwrmo3D53uN2iipABjqZXg6uLlQ3yvY%2FjqU%2BnEG%2FBucXL6ujbyxly52J9mpSx9euA5YhHvq9KnqJUpuj1RhUtOyLzkvMMqtdDiFFK09xspJG0eEi0BWY8hz%2B9qjs%2Fwhiy4zkotXM5c0wn1hXzRxgx5Dn97VHY%2FhClgzOTKPtctaT%2FTgON3D1ohfeIOHrRCAnhGb5Q5M5iZ5Yncwhlnh41iqNSy5xxnpkNBLKCApRUsgc1D443CrwdfFum5GU2q3dVJX6cBzW23eNsZI8NObHEDUHpHLnDhmGJM2nqlNLDElKX3Gt5W1%2FMLmM8Pg%2FeLaXl1FOTcy44dkhNSleff5cdHZ0YNzJTM4K4G%2BGxiYk5Sj4YareJX23zKoU64m6picmBuEElQt2qI5wGoKt4NLPBinzUxhPEOB8XT0k2XH6XSK0PG025hKVpCVHzaheOU67h%2Bq0GoTdIrVNmZGdkHlS01LTLRbel3U%2BUhaFbpI88dQyHBfxl5d4uNVwphSapVWpco5V5XEdLrbQllBqytpnUErUbbtODrC99jG1M98oMa8aGV2WPEjlhl%2F47jav0xdOxfKSzjUsl12XJQiZOsgHrJWjmTpUkckiA%2BeBa57%2FLEnR2PP5Y6YX4Pji33tktPbd1RlPyuRbq1wF8V1Co87Xqjk1Um5Onyy5uYWmclHFJaQnUpWlLhUbAE2AvAc8HYRIVb3j0ON2jzqTvARConCopjsgSYCsFAxVbVaPKlW8VNVu2AuDblxHvYcBRaLOyvePdKuEqtAZrQP7WOE%2FbRbpYFWN8NoHbV5Mcv%2B3RFxoRtSHfOoiPFSrnMPC6E81VqRA9PTogMfrTi%2FdJrK%2Fta5Oecfohz5IuuHwDmdThtdVUlOQ%2Fdoiz1r3vMSt%2FC%2FPic%2F%2B4XF4w0k%2B6xTEdnstKD%2BWiA%2FSNCEIBCEIBCEIBCEIBCEID88%2FFCnRnXmGnuxTVf%2FALt35400reUR%2FC%2BO8br4rUaM9sxkd2Kar8sy6Y0mf0IPNr%2BO8Bl2GU2pXpt%2BMxepGQn6pPStLpck9OT08%2B3KysswgrcfecUEobQkc1EkACLThkfnZ60%2Fijf3Bw3hd%2FOlljFNCpc2linzFTp9TqdS8UYo07LDpGpkjUkOkr0o0k7AkjlAYrlnkxXsYZiYcwpiaSqlApdXxE5hx%2Bov050tpn2UKcdkgQPsxSkpB8lJ3OwMXfPPKnC%2BBaBgvGGFqXiygy%2BLHKpLOUPFbSU1JlyUcF5i6Bo6FSVoSkc9QVzG8bsrEnnMjI3Mt%2Fiok6Pi2cpuitYUkHa23Kvsuua2nqnK9AUlbKNaChIBKrKF%2Bcch1qu13EM0mp4lxDUq1P8ARNsrmp%2BaW84pKEhKRdRNgABsIDyyVNdqD%2FQS5SFkX6xttFx9p1W7HGPjMeajVBmn1JqZf1dGkK1aRc2tGRnGFHGwL5HfpN4DG6tQZ2jIQ5NKaUhatIUg3sfPFsJ7iDGR4mr8jVZFhiUK7hzUu4t2bRjVx2QFS9o7syRdbl%2BDIvPlJbTTMQFZVytpc%2FEY4RB7DHdGTaUzXBe%2BysJCVUqutj0gOH5Y%2BbfCbOVxuv8ArR%2FJW62EfKV%2Bhx3gNv8A4KXm3NQ6PEjKut3mQVv6bGMyy2l3K%2Fjb2vPVGqMSApMzNKZp810CnHQpIQpSrHUE77RiuAk9JlLNTB5%2B2WXCh6ZAxdaJO1DD9ebr9FfXLTqJdxkPtpClJaI1KASdje3Ix9Es9VLmVznk277nCEJK%2FZrEQA%2BD48pRjB82qBJYexbS6LS5qdcTMshxT0y5qc67oFirt7T5ot8%2FxNzLIbQ%2Fi%2FEyekGoKXRZS%2FqsuMaXm1lvVsQS2IcXVrHFVcl3G1qbalZVrUlCtQQkqUQkEjfYxlhR4qhm3K4PqTrbOWlBmplLL7LEy7MTClNFYW2HAkq0lSQSoXFgqxttGq5vEKX5tbjMoWkq%2BCV6j6z2x68W1WVrFRXNSd%2Bit1Qq9xdSlW33NtVr9toxlbehy8Fl%2FZq4t1pcn0ER7RV23W1NrSpGsWuCLjzjzxjbavNFVLunsgiW3nc3pavzDMlM5aYbbemlttLmpV%2BbbWFEBPSJR0hQk9trWuTyi4zDfRrUj7RWmNO0aotyFXkZ99txxmXmWnXUNqCVLbSoFSUk7AkXsTsDG553MjJB11wyUvmElsuKLaX2pIlKCdgSle5A7drxVLwOd0SOTM3IMmakJp2VmWtJafaNltqvbUnuO8V3Mb5QLYWRJ44BIJSejk9IPZfrXt8sV5ukt9I7KzS1mVRcuqQgqWUAaiUp77RZSYzdJTWG5ibDTgbqmlTLZ%2FRj6k6tAuoaj8I7n07Ri%2BZ2DJGXwDUZl5meQ%2B080rpXppxXVUoC2hW23O%2FONMDOuhSaW0jEWN2UONhQF0EaTsCCly%2FZEqc4cvZ19o16vY5nZRDiVuy6W2E9IB2alrVb02iMiYzeOpZrs4RqD0kzgShTDrCClmccQ8tYJ2Dukr06hzG1r9kaum8RS6ptSpNt1aXAFKLwGrX28oq4qqrVbqLk5LI0IcPVBN9rm3zeqMYcBRMCE61oZRL11xbdvFkpj1%2ByZW1pUgjULAhVoxxhywj0pduPRDJDbKs3%2FZt9iXmcv8MsLcLcut2TadlyT1U6wAsgK7eVrk7RdH%2Bo4pv90U%2FEY07ITqJOek5xxsuIYfQ6tANitKVAlN%2BwkAgHvIjbk3mPku%2FNvuMUrHrcut0qabLkkVto%2B1J5KPn2iUwlci11WYmZKQenJSYdYeZF0ONqKVoNxuCOR35x7049ynW2oJpeNkr30EuyduW1%2FX3R7PEEPO%2BJPhRlnFe%2BBIBV0YGokA7E2giJdDOYQdqiZeYXJ1MkyrKVuCafUXVaR1jdXMxYsf4NprOX9Wbeps0mbbW0pD7s06SlGsApCVG1vPzjUEzndl3KJbZapWOUK0IUjpJqWto7DseZES%2B7flFOlCapQsfOtpUhTiGp%2BXQV6TfTck2B7TYwFhq2bbmE6g9T5LAGFHtLK0NPTEm44tGtJTq3XYrTe4JHPe0avXiFC5hXQNqCVfbKF4rYsqUtW6s9OyQIZVcpBO4BJNvVyjGwND4tETrM4llUvWSv4EVhUVuoKRdPnTsR6IsDbmiK7cxEjbjucDuJKtLpncvcIsvTjjMs47JSS5dW9kFYAXYKNrk25xVmEIbWtA%2BCop%2BWNYUKps06t06pTTBmGJOcZmHWQrSXW0rBUgHsJFwD2Xja8%2FmBkPMTMy7J4VzCaaceUthpdSkldG2SSEE6etblfblETrFuK97CFYedlaFMzMpMOszKAgtONLKVouoAkEbg2POKq8bZK2szhvH6VaCEqVUpJXW7yNHLzD449b9JtVF0p9a1sJUpKyEbqQlJWQBy1ED44RA6TmsIGtqYqLsgUqVKsNuKbmFpS4UtgBagXDdRtcntNz2xh%2BbGEqdTMup8Kpuid8aZW1MKfUV6CpIUhIKiLWN%2BV7xpGYzbwHIuJWuj4tSpaekT%2BbJYjT2fB5xQRm3ly7MsLnaTjB6XS6HH2UTcq0XkjcI1aTYE2v5olaYzUp3N2q4IqzzNNwfhNxTaHG2X3qcpbyAtJSVAlzSVgE2Vp2O9o1i1iF3XpQ2kAcgSdo9OKaq3WKg5OMoKELNwg%2FB80Y4z%2BiVXgqylqurUOshPqisKyhXlAj0GMeSrzRMFHugNsrzXn8UzaKbMYJwk09PrQy7My9PU2%2BRsNST0lgs9qrb77RK5724pHSK6iikee0a9w1VmKRXpCrTUuZhiUmEOushVi4gHrJB7CRcX7I2RN46yimZtx6Ww9jFppSiUtrnZYlI7tWkXi48uvzRMjnETi%2FLJfVTQ8WIBOy%2FHJY27ri24vz80V%2FF1tudGvrKT1fyxTLNaYXrG4twxyh78ylH%2FAPhgjsPgWdW7w8yGr9KTVWwe8dMD%2BW3qjkHHTKU8MUkNRsrMle3d%2BdgjsPgYP%2F6c6anRYoTVQT9t7%2Fe%2Fyx85%2BEXVcaI%2FzKfZLtYT%2BdV%2FDPthwdMJ0zrw%2FwC3eP8AnFR0HwM392mcv%2B1%2Bb%2FnIjnyZCkzzyV8w%2B8D98VHQnA5YZzztxf8Asem7eY6kR2tNJ%2FIFvP7u5qYdqvVPpT59noOKDEKCNJXlq%2BSvV2KYt%2BIWjTclOT0g0ZmnzypWaVNyLTb6La2wqYSlRTcEA2JF7RufP5oHilrwF%2Bvle6Tfv6E8vijSTiUFnQ7cthbbxSDa5bVqHyiNjRGM8Eu0%2FuR7GvfdVtV6W%2BalhObmqk%2FMIquJUNFzqJXOKWpA7r6Bf4oxPNfDMvRcGtzztSqs1M%2BMttlE68HEouu%2BpsWBSbbHfeLK9mpMyQKa1mnXpOZaDfStpkwtpClDUlKVqWCbAje1rxYqzjvDOKAhmuZqVSdaSQvQuUbtqHLbX2R6SNbWW16u4awpTmH61hZmrl5hp9x12cfbUelKrICWiAAAnne%2FOMDx5mFSMVVuYqspTkySpherxaWQpLLCAlKUIRqJUQAnmSSTvF6zNquEqiz0OF5%2BZflG5WSlWxNqb6dbjSVlxwpbulKSV7C5IAFzcxqOaQph8Enc9sWyRMMjbq0moD3xYMekTjSyPfFERi6XSkC5BMetp9W1yQIqltfCmYOFqNhyWotcwPTqpMSbzriJxc1MsurbWQoNqDagkhJvY2BsYus1NSk70U%2FIy%2Fi7M2ymYQxrKuiSrkm53IFuZjTHSdI2rrxuyiV7KGewzQzU8T1%2BRqsrTmpafZRJMOtF1BIu2ouJOkp0%2BUL3v5oSngwtjjljEEalutpB8pQHxxkCJnJ3bp8b14d%2FR0pk3%2BN2LTUhS25kTuHai9OU59BdYdfYDTmxKSFJBI5jmCbxGRk27glrEOIcC02aXi6tsq8Zm29EutpLCWW1hLTaUhu4IsSTc3uIv7GEp%2BZZfYn8dYpAEu4plLTrJQVgbBwLQbt2vcDfujWVGzFbwDRzQWcb1SmutPFbzLUi2tgOrSFqSkqVfkoX29Ee1zPSUqTCGKlmdVnWlGzjbVNl2wU9o1Fd%2BUMjJgc1iagYdkG3qzheWnxNFQS6qcfb0q3JTpb2tb1xhWL8dUbEVefq9PkkU9l8JKZKWQpLEsALBCNZKiLAbkkk3MXPNOZwvNysozhSfemJZgIQDMFHTLUlB1uLSglKdSlWABOwjVtih%2B0SrEZMmXWpBxvZx%2F7iKaazIJ%2FTH%2FuP9cWMLNt4lWu8I1JbcoWamDpXD1PolYwlJz0xJ6z44t6ZbecSpRVoXoVpUBewNgbRdHSy6pMzLsdA0%2BhLyWQoqDYVvpBO5A8%2B8aOBvHQbdSypmaRSnXsTVuVqIkmUT7QblnGA8lIB6IhQUEmw2ULg3gLVqT%2FuIoFXWGvlfui7uTmVoWFDF9bSntHibKvxLjwVBMk2BMUicVNSjjXStLeaCFncgggEi%2B3YYDatJbrT%2BHKMZTEVck1ty9ngzNXZeJWohQQUdSwITYG214lrEtWkUCpT05jHETjzAaLCFvoVLrTrHSJdSpFzcWAt23vFgYxvhfCci1T5zHeKZSfaSnp0y8uymVSspCihOtepQGoC9olns0MJVpjxWfzCxJMtgg9GZeU0kW5EahfeAx2cxfgrBYabrGCJWrPzJW4XX52aRayr6dLRCQLWHfGvMXY4pWJcS1Cuy0giQanXekRKyqVpYlk2sG2wslWkADckk7kxc84JzDFRdl14VmJp6SZASlU2W%2FGFL0JC1rDV0pClhWkXJAtfeNYQTDJU1qSRzee%2B5is3XpD9Wd%2B5jFSYIXaCI1N10jNPArWHqbR6vgKSqs5TkOIE%2BqZnJd15CllaUOJaXoJRcgKABIsDyiep%2BKmfWuSllSzDqEPNsFwudEFJvpCiLkDfc7xpuXc98R%2B%2BEdAPzWU9QlpJ6cxRXJOe8RZZm22JaWfYTMITpUWldIlSkKFj1gCDcQRLFlKIMQbUlb6EKUbKIEZME5LBY6THWIrWGpKaYwVA9v6bYxbK1I06Rnm3MOVJ2fpr7QflnphgMu2JIKHEXICgR2EiBDaUsuuu0emNsV2tsluWu4W3kltSys2KE6OqkJATa55XvvaKGIG621hucfexZXVPNOsKSl11tTDjesBaFpKN7g7WPOMbk8f0fD0o3TajmTXZCZSmy25aVSGkqvdQTqXuATztEJvMjC1SATN5n1adQiy0szMiytC1DcXTrAIv5%2ByCfzmK1DEOCcMmVYxDg9VRU814ytxM8%2ByVoKjdsBs2SNrX5xg2McZSWKcVVTEUrIokUVGZL7cqwFBqXb0hKWkBRKtKUpA3JJ5x7s3JjDc3U5NGEZ9%2BckGJUNJXM6Q%2BpQJ1KWlJKU3UVEAHlaNfI2iJ1phkzNaZ%2BE4qDtWklc1rjHA4EnnEFvRKG4KZmJl67S6fS6hhCYqVRYStrxtupTEst7UeolbYui6b6dQ5gbi8UZgNh5xSULQ2pV0IUsq0Duv2xq2jTCWKxIvOOBtKX0KUTySL9sbveeyonWpea9u081NFpPjLBkkrQh34WhYX1k91wD3wGPdXvV8UTItq5q%2BKL%2BG8qv8ArEqBv%2F3Pcn1BceKfkZWXmiKfNqm5NwFTDxa6NS03t1kG%2Bk%2Ba8BluA%2Fe8vs6XOv8A8nq2%2FMdVSlOfmjP%2FAAbyl%2BzGYVkXR4pSrqtyPjKrfljAcFIBy3zpJJA9oguR3ioSxA%2FHGf8Ag3SVTeYbffLUk%2F8AqVCPG6bxngt49HvpdXCo%2FtNP9ckrFxjm%2FEXisdyZMf5gRgWWBJzKwanur9P%2BPp0xn3GSsK4icUWQke9yRJB3VdntjA8pQDmfg7UL2r8hb78I2aZy0apmPI%2F8WKn9K8%2FCh094Q9IFAwC7vdOOm7WNti0n5o5xzGctnHizxn321fm9aFb398Vz7zyvHSXhC0n2pYEUNFhjZjUD5V%2Bi2t8t%2FVHNObF2s3cZqZVuivTZSr0LNjHN%2BDj9RUR%2B9V7U4pGV5qbmwbhyoYowJhyrTOLK2uampIKmEJU0GkkEhAbsjYBIG3eIv3ua0xVOqTNQqVffQuUeUlCn0FoqCCR0idN1J25CNLYSzhxFl%2FhaUlncUzcnTWEuNyTbFKTOKTospZUVKT1RqHeYlqvEzJ11h6SqOY%2BKQw%2BlSFdBQmWzYi23vm0e7c5hNIcpVMw5M4hqtAYrXiy22kyr8y6wg6m1KJ1t9a9wLdkWLEOaNHxRTKfSKXgCnYcZpnTOK8Umnn3JxxwpJU6t0k9UJASEgAAnvi74ixVlv7SXqFhOdxFNz780X3HJ%2BUaYZ6MMlCEJCVKUV6lElRNrCwF408hZbXAjUysVhkN9WXVft3gK6keTLqt6Yx1TxDdwN%2B3eKJm1A2A29MBsXCmYVPw4mptVDBNKxBL1JltstVB55oy6kL1pcaW0pKgrmCDcEHcRf14ipeLJJVXp2DpLDobmPFizJTTzzLvUCgr30lQVc72Nt%2BUaeQ6Vb3jZuXGLcsadhWdoOPJfFQnV1BE1ITNFal3G0t9GUuIdS6pJ1XAKVJNrXBhnmmHr0%2Fux8UEp98HXEXFzFmQ%2BtIRNZlWv17SMiNv3J6T8cSTM9gSrSpnMCzGJiJMpROIrkuw2pQWeq4gsqULdhBtAltXJqRmqjRq3JN1asSrTamuiTIzhYQlxVyVrSB75dIsBcWO%2FmjYNMwW%2BioMKmcU4rUgrSHUt1JSVFNxfe3dHP%2BHswBl6w9VpmtV6RM7dsClssuApRa5cDpG11C1t4vTPFBLWSZjHGMzp5hqmygv8avxwQtWP5mTwhiSvT83RGMRMSUyWEt1V5xSw2Vq0FSmyCpYAAuY19iXMuXxZJUuRkcHUjD0tSi8UNU%2FpFF9bpBU46txSipXVAHIAbWi742xngGt0KaYoT2J5yq1CaVMTk1Vww2jo%2FgNtoaJudRJUpR7rDnGqZRxWgbwGRCqqCtQHyxM5WFrFujv%2FAAosod2sYmDgHf8AHAbAwZmWnCEtVJN7CFBrstVEs6mqoytfi62iSlbKkqSUKNyDzuDF3XiWVxPLprUthanUQdMqW6Gn6w0dKQdRC1KOrfcg%2BqNU9Knz%2FHGw8DYxyzkcLv0PHNNxOZ1E%2BZqTm6M6xo6JSAlbbrbvM3SClST2kEcomZRMZvWXT54qNnULm8VVYyyOF9EhmKd9vfJEbQXVcG1ZvpcHy9fZDBHT%2BzCmFageWjoeVvPELRDaGV%2BG5GvYWnZqaqNYYmhOpQ0uUqDrDSWwDrC0IICibiyuYtGZU7LKivVBhqexBiZcstwBxLNXeQux7lFVhv5o1JhLNKSyspPjlSmcWoM884Uoo65RDAbSoJusTCFalk38nYCLw7xcU94Fv2Qx5bsURSrj1BqBkxnENZawQ9WK6cOUivuS80xJaayhbwSNK%2BsAlSbq2FybxgeKsyn8bmnrcw1QqG1TWVsNS9HlDLtrK1aluOXUoqWSLXvsABFxzGx9l%2FXsNO07CNLxO3OTM6ucnpqtTbLnSqsA2ltDSQEpHWJJJJJHK0a1lXCEC8EL2mpFHZExqmr4MWhTlx5UQDtvhQGfYTzOmsJUup0dOG8PVmRqrjDzrVXp4mC060SUrZWCFNkglKrHcRc5yvJxVIy%2BJFYeo9FccfflyzSmFMS60pIIVoKlWULkXB37o1f0w%2B2jYmC8dZaUzCrNBxthnEc%2FMy08%2FNNTNJqDcuC04gDolocQoEhY1BQI5kWgI38xiYcuRj2e6JkikpPtExssA7gV2WTcfeoru1PB2Iac5VsGUet0puTdRLvy1TnWZsu67lLiFtoTptaxBB5ixgNqZO0YVTDtRllyRmdUy3p1LWFtWHNFlAC97E23jYlNwFSpSfYmJzCweaQsFSHnXSgi%2FI2WNvXHOCMZ0fBNMlJuvU6tzqp8OOIVIzrcuhltKygIGpKiokgnew80Su58YUIUlik4uSFXuFVhk3Hcfe94jIS4yri8GTFRqdOpNJqN6s5KoFUYM4kMhHVA1KG4v5Rudh3RhOJMx6njBVPfqVLpMiilyniMrLUyUEsy23rKydIJupSlElRO8enHmOMKYioMpTMOUWoyJamHJqbdnplLyn3FWA06QAlKQOW9yYwPpNovkmF79nT%2Bt0%2FHEHKyVJ%2BxJHrMWXX5oa%2FNFUM7w5mfVsLU6YpdPplFm2JxxLq%2FZGQTMKaWkWCmlEgo22IGx7RGW0%2Btz2IpZNTqEpIS7zvNEjLBhq3ZZAJAMaX6SNnYPzKwbScPt0uu4SnJycac1%2BNMz3Q6mrC7RTpUOYuFbHc3iMjavkwHUp0na%2FIxQbQ6Fdp%2BOKb%2Ba%2BX7qjbAVV0k9tYFx6OpHtkMR0TEbSpiiUSbpzDBCFImJsTBVcXvqASfkiRn2QzP%2FDVgtZNrz7puTsPzK8d4wfgHS%2BriDpfi5vakVMuJuOs30R1fkjYOQLpRnRg%2FqJP5tmAUKFwQZN8H4hv6owDgE6nEBSFlCVaqTVBc8k3aPW9Vo4OkerDLfPxZ9kt3Do%2FtNE%2Bdurj%2BN8xsDjuwiB%2F6oxy9HUXH4L5kYKvzGERYf4zHLsa%2Bhn6ju8fuz7ZUvlX4%2Bv0pDEHG3HG1Nt%2BUtJSn0kWicjtgnnHpmpOp9Aq%2Fhqa4keC%2FCVMyxnZVM3TWKa3M091YbadfkUlt%2BScI2Qq9lo1dU9XvjjfNnJrMbJ6iy8zmLQJakGvszYkW25tt9xYZSnWV6CQny023337ot%2BBMzcwcsKg%2FVMvsWz9EmJpITMBhQU0%2BBy6RpQKFEW2JFx3xWzDzZzFzbclHMxsTrq4kEuplGyy222x0ltelKUi2qwv6IJdVcZC1M8OGTTqyEkOyfVPafYgcvR%2BWK%2FDHjDiIw5hLC2A8RZHrxVl5UGmk0iqIU2FydPfWV3dQvU28yglSgFBKgBYHlHJeJc08xca0ClYVxfi6eq1IoJSaZKTGjRK6WuhBTZIJPRgJ3J2EZJh%2FiYzzwlh%2BUwjh3MGelqVIsplpRpTTS1S7Sb6UIWUagBc2uTaA3BxC0fLPIXixy9xJh%2BRlKXSekkq9iCnyyT0EkoTKmg%2Bhs3LaFt2d0ch0aiAIz3jH4fcz8y8cULHGXMmxiWTboopnQInkILV3lOCYZCyELbdSpBK0m%2FVHZHE1YxJXcQ1SZrmIqtM1SpTqtUzOTjhdddNrdYnsA2A5AcozHA3EHnJlpSUYfwdjicl6QzsxIzCUzDMuCblLYcB0Jv8ABGw7AIDZXDXKqyK4tpLBuYiqfS5pLEzh9xaHUrYlp2al21sp6QbDUVBBPIKVaMw4kuETOXMPO3EeI8OU2TqNKxZMMON1Gam0tqpQ6NCOiebV1wlkoJSUXvcW3vHK2KcTV3HNcn8S4xqK6rU6msOTT7wSC4oAJGyQALAAC3KwjYFC4qOIHDtFTQKdmZUlyrTfRsKmkomH2Baw0OrSV7Dlcm0B0N4QqrU%2Bl4Ey5yxfnjP1%2BTe9lHZhabOGWalBKl5QO4LzguAdyEkxw8d4udbrtbxJUZitYirE5VKjNHU%2FNzbynXXD51H8Q2i1HnAS%2FCiZPOJU84mTzgJoGEDAIQhAIQhAIQhAQPPly7Yavl7Yh%2BXsiI58%2BXZAR5xIRaJxziRyAprVbyhe24iCVavJ7NoLUCLc%2FwAcShQUbjYQE9tuQidAFuQin67xOgHvEBXQWUMqU4uyUqHZe5vskDtJ5WHMxstOU%2BIcC41omEs18Xs5WtYvoD06KhOKLoTIO9XxeZZZJWgu6bdGq3YTFiygx5K5W5l4dzDnsJSWJZaiTYecps2BZwEEdI0Tsl5F9SCoFOob946vx3m7Rc0M3ZaTyRyTyrzXmcbUn2ZROVdpxmqyxQno5hif1qCUvN2FrEWSU274DS1b4dcJO5c4zzEy34g8L44GBpNifqkhJU%2BYl3Aw66GwQpfVvuSB26TGjo6mwtkrmlkvwz8QhzIwo7Q26xRqIxIB%2BcaecfDU%2BOkA0KUbJC7AnmO%2FeOVlqKG7oX1km9rXt5wO2w7IDfvDzwm4nz1otSxa%2FV2aBhxhEzKSE6qzjk3VG0jS0W%2BYYBUNbnMchcxpvHODMSZc4vqmCMXSiJasUZ8y06024HGw4ADdCxspJBBB7QRH0LyIzh4Wcusv5DLjA2arlV9jW3alOKcp007MFbgDkw84lDZ6NsK9SQOccwcZlcySxrjSn5h5R5gMYiqGIEODEMqyFFmXW0hCGXm1KSCOkTcKTuLpBFrmA54jMML4TzH9qVVzVwkmel8O0qY9ga7Vae8C5INTSAlfToSekEupC7KVaxvbnFmwfXmcK4ppmJZnD9NrrVNfD66ZUwoys2LEaHNO9rkHbtA5jaOuck%2BKrK3BmG8V48m8qsBYbqM4W6HJ4Tw248Z3ETzliBMNu%2B9CUHSKBcIJvqG19w1LP8MOHpjB%2BK8TYD4iMD4xewXQ1Vyfp1LYfSvxZK0p6q1DSPKHP0RomOrsvcj81coMreIev5j5fzGGZCr4CXLSHSOIcaCzPJUWUEKJ6qVgC%2FMJjlBS13gJPhCJz5MSb33ifshA37wvG0jipdr7yqLfwVn%2FAF%2BqMEwdgHD%2BOOJvETGI56rSsvI1V%2BabVTX0svdIgEp6ygbbgct7XjPOFvam4ov2OS57e1tcWbJ%2F%2FwCJHFribr0Tc2rle%2FvRt%2Fv5o83dv1tb%2FZ7n2DHqYnQW4R%2B9n1Wi1zMwqZfcfcS2FuLK1BsWSCT2eaJs7ZxpnKXKykzb7yJBcziCoqYQNSVzJdYb6VSfttACQewXiUtAuBCRzJHyx5uJtbMtl7lV0ZSbMVskAWJPjDV%2FxR6PJ8fiWq2JrDOnUqad6vfJm4iy4xm5GfTL%2BIvl1LaiCSgpPxGLU3UkI5ao80xNBxeuGS6n0YRC4MUlP6okLtjvEqKjiAsgW5xRcQtIBHaoCKqHkgg90SuuXAA7FAwGyZFVAFHkGHKmw24hizrZaUbHnYx5p2Xw6%2BhSET8np0lNnWTuPijDV1NC9XlR5lz%2BtpzyvJMB1Pi2v1jEOHMvZuuzip2bYwXTZQTKzqWtpsupbClcyQmw33iz5vzSpnLHLLD89PpZprLlfn%2FFXEqLK5hUwygvlIFisIASCeQ5dsemtq0ULAbSQBfB9MJFuRKVn8sWPPpa2MF5V6zdPsfWinSrvnk3vEwuwOTp%2BHEEKZn5BBG4KWynf7mLPjXxeYn2ES8w26htkJK2%2BSo8aKmyR13FpPouItr04hbiik6t%2B0RCiCWEpiYpRHnXNiJfGgYCdUsnUV2vcR5wwEOJCUaiTyismYCuZtBh1AmULUuwBgNjyEm4xJyr0tUWJdaUbFMyGltq5dUggiJ3qzi%2BjrE7S8c1CWm2RrZfarjra2ljdKknXYEERrxybl7q99HPtTHlfmG3Jd3r%2FBPwfNBaJzdd5y4vq2YGMKPjnEBlzWK5hSizVSWykJS9M%2BLBK3dvhL0gnzxjblMrNZwVjOnUKpS0pMuUJ1bqZhkrQ%2FLIcQt1sKH2NZCQUqItdNri4Me3HzbbVUw8w3ybwnRUn0%2BKgn5THsw1K68MY0nAsp6HDU6T3G%2BhNvl%2BSJlMNreD%2FJTlxMrvYCam7dW%2FJlR5euOLastK%2BnWNgp54gd11q2jtTgDGnLSaV3zM6f8AMkRxNVdkK%2Fvjn89UbueeHWf8UuTd4%2FKNt9jDXvKikrmIqu7ri5yVFlJijezczUWtLEz0EzKNH81IQpF0PJQdlovdJsbg8%2BYjRdNGgTM3TnkVaWeW1MtlbcuEbFd0kLB7CkAm4iecqDtSoshRG2GnWqU48pqdNw4UuaT0O5t0aSkqSOYKld8eN16W8XEkmozC5dpa3G0Fu1lKACiO64AvEqKktmRepjMw8ZR9xLzjKkDSXEghKu8EAkbd8BSfkJphvpVMgp1adSVAi9r227bR57fzo9LDjfRqZcU6hhxSVOJbRfdN7G3rPxmJH%2BjK1KbTYKXdNxa4t2j0wFI84miU84mgJTziQ84nPbEh5wCEIQCEIQE0eiTkJ6ouKakJN%2BZcQnUpDLZWoDvsI88XKjJqo8aeo1WMlMIbGoNzRYcdb31BJuNVrXIvAGqeqnzZlq6zM09amzpDssSoE8iUmxtz3hKuSsrTZ6XE30vTugNoS0bkoN0u6j5IIvtzijVJmqzTrblYqL84%2BEFIW%2B8XVpT2AqN9u4R40a4CY8oliY8jEsBfcJ%2Fo9X97MZeLrPWjDsKL0VEq7m1Rmd4CoEp07xIFFJ35ROCLb84lAJVc8oCom6k6r9vKBRcXAtvFVtsKHSXtY8oXK1d28BkOWnRDMnB3SJUT7Y6VpA5H81t3v6ov3EA90%2BfOZDtrasV1Pbu%2FNC4sOXgWjMTCC9O6cSUoi%2B23jbcXrPLR7umY3lafbVVdOnf%2B6V9sBg2pKuuhAAAsrfmYmLqkgEW1W33iVtu%2FX1iwPdziRZIN0EHfc2vAVNR0aybaja1%2BcQKwRYp2UO%2FkYlKQdwb3FuXKI7qRcC59HZAU%2Bv5onAPMiGje5ioAO0QEtz0ajfbTe1xHYeCVoThXD6i4Qr2Ll%2Bpbl1OccdzCkhpSU91o61wJ0qMPUN5WnanshP73T%2F8AmL2Py0eifcxXj5L7Y97bstiduiU9FckqRKTbtPYce6CdTqZdUU6NwLEWKgoWOxAjdWHsaoocjJSaWXilmWbbbFzcAJFt%2FwDe8c8yMg7Wqa9SmhdU0wpCSBug87m%2FZdMdRYdwfQ6hh6SVNNB9brCFlxJsbkDlG5XVwao4MOfZUTXFUTLW2fmNlYpwY7RRMuMqm9Wra6uVgrnbY72POOAqhh%2FH2XOLJHFMpV5ulT7jKn6dW6a7cTsuFdGpQtz0qBStpwbHsIIMfSHHOQtGxbKIlZeqzMgpJKSbagtJN7Ht5xxpxEU%2FCuWOP5DCMpX1Ygfk5BTtZcZsluSeUfe2jc89ABUOY2vHQs7SbeiKac44PN9rXmz7nr%2FCmJ4XP9iyZoNvVjBtBxvjfGr1dxtVJoUyWlnGGmZVqQDepTiUtpTpVrO%2B29zFqzXm5bLDKTCWVkhLzkvXsXSLGKMXz5fSpM22VLTJSTJbNvF20hSyk365Fze4GG4jouNarSpqdGE59Mgzadedbac1MtDyX9C%2BskEG10ixHxxuLJbIXFfELlkcCYkqMs1K4cl5qq4Xr8z1H6IySVOy0yo7OyLy7lKPLbVdSercRgtLamyqpmjz888vuhmosJmnKvw5zGWyI5N%2FhcuLxHMyj7b0o6tp5hxLzTqFWWhaVBSVJI5EEAg94EKPPz1ZnJ2cn5x6adU8p51bqypS3XCVLWSeZUq5J7TFR%2FDyujW5rT1b%2BSbhXoPcYjgmXSlM%2FMKRqQp1CEk8hpG%2F440bSKonKp0LPKY4VLJ6bWXKLLvuNr6rrC2%2FK2FxY27ja4%2BOMEnnPGPfIy6rIb9jJhxtxv7Geqn8fpjEej6unviszOWS0RG1rqtHRU3yewD8UVqy5eblx3SrKfiERxMyG63MtD7RJ%2BSI1hq1QaH%2FANO0fjEa7Ku1G8kfvY8%2BIfsCYr0f7Gk94ijiIWaSPNAY8OcTjkYkHOKggJYRP1fth8cLJPJQ%2BOA9mKRalUQX3DDm38K%2F5YqsC1Olgf1ERNji4kaCC1o%2FMHx9Y7xKk2kJW36kmApg3OmMkwJhStYvxBTsNYekVTdUqk23JyjKRcrecISkeje58wMWCXYU86EI8pRsI%2Bh3g9smKPgzDFZ4qMxkJkaZT5SZaozj3JqWQn81ToB%2BFt0bZ7ybQGzcxqHO5F5LYS4Qsl0MzWYWYTMxIB5p%2FoNKSi9RqLjvwAbFtCuwA25R7MJ4dqfERkRi%2FhVzemqc3mflyJKmvzrMwmYR4yloLpdSS4nmFJvLvee%2BrcxrPIjNP2z45zk47cxmw1SMKUoUPDUq8QEtrc%2BxS7d%2FhaOiSbblTqo52ybzozByizaHEjVqTXKjQqjUHJXFc4ZR0S09KzjhU630ltJcSffG973bAEBoTEmHath%2Brz1Fr1PVJVKQmXZScllixYfbWULbPoIMY86jSoiPoT4R%2FJCSmpyk8SOA%2Bjm6HidDEvWZqWA6NcwtsGTn9uSX2gEKP26B2mPn7OMKSTcWINj6YDwlVja0Er%2BDaIrAFj2wAAVeA3lwZYpwzgfiZy7xRjGtSdIpMjWEuTE7NuhtpkdGsAqUdgN7b98ebPjHkzP5045qmFsWT8xTJ3EE%2FMyb0tVJjonGVvKKFo0rAKSNxbsjP%2BATL%2Bg5l4zzCw%2FXcIy%2BJQMvas%2FJST0qH1CbCQGVtDmHNRSEkb3ItHP2KMH4twJUG8PY3w1VqDVWpdtxclVJNyWfSkjZRSsAlJsbHltAehvG2KlKs5imtAeaqTP9ZHbWW84OMnITC%2BXWHscGiZ75OqeeoDkxPrlna5TVAgFqYCtXSBNkqNzpUgauqu8cBdJHsp9WnaXNsT9PnZiUmZZYdYfl3VNOsrHJSFpIUkjvBEB1RhTIXjnoNdncIYbwhmLQXqw6fZINVBbMo8Sestx0LLe9z1k7mMzz0q2H%2BF3Iam8MeGcVoqONqtVvbJjKpUyYUlMu8B73LBxBCtXkg78knvjnx%2Fi54jp2kKoU5njjJ2SW2GloVP8AWUnlYrCQs%2Bm941PN1KZmnXHnnluOOKKlLWoqWsnmSTuTAZR7p%2BPraTjOv27vZib%2FAKyN88DGbaqHxRYOquYuZz9NoLSJ3xh6s1l3xUqMurQlXSLKblVrX7Y5UDytVjHZ%2FBtltk9mPw%2F5rSObFMkZcTdXpVEpVfeZu7Rp2cSpuVdSvmhHjBbC%2BwggHaA5ZzRmmJ%2FMDENQlX0PMzNUnHG3GyFJUkzDhCgRzBBB9cYnHTfH3lthzK7OWm4Xw%2FQafRlS2FaQJ%2BWkGQ0w5N9DZ10JGwKlC5PbtHMkBWlRqWU2vcEW747C8IagoquUDINyjLSj7dvJyOPpU6XL%2BYiOv%2FCIq%2Fsjymb%2B0y0o4%2F0kBxw9zERREHucRQbQHWHg5MYYTwXnVWpzF2I6dR2J3CFUYYdnplLDbjtk2bClEAqOxAvfY90aSms1czpZ95kZi4pFnDcCvTZF%2B4e%2BWsOyNw8OWUtFzH4V8%2BaoMCIxHiiimk%2BwDjUut6blnFuErDIRvcgG4sb2jnGsSE9R556mVKTmJSblllt6XmGlNOtLHNK0KAKT5iIDKGc280lLTbM3FjSwoFtaa3NdRYNwTde4BHKO2ce0zGvFvgKh8SPDpWJ1vMGk0JGFswsL0yo%2BLT7gQNnEJCgHmlDUoJPlJIKTqSRHzxQ5F%2FwljzFmX9cYxPgvEtToVVlwUNzlOmlMOhJIJQSNlpNh1VAjzQHSGX2UnG3jGWcyhoUnmJSMPTi%2Bjn2Ks%2B9LUuWbUTqW4XTqKRz0JNjGTcVebFMyvoeC%2BHXJjG9QTJ5cyJYqlWpU6uXE9UXLKcAU2oakJN%2B0i6vNGj8U8ZHEnjOjroGI85MSTUg6nS6yhxtnpB3KU2hKj8cafcnnHNlm8Bnfu55wjyM2cYj01qZP9OOpOCTOmsvyucMrmZmrNzCHMCTDVLl65WVKS6%2BoObMh1W6%2Byyd944dQ4DH0I4Z%2BG7IvOHh%2Bywmq7Q6e3jqpYump2TfeBPs3K0%2BYC5unuX6pQqW1EWsq6Lg84D5%2FVTSqYKkLKklKbKPb1RvFtNibxtzilwxhnBvEDj%2FDODqainUSn16bYkpRu%2FRy7QXshF7kJHdftMagUbHaAHaJSbxFR6sS80XgJkc4qRTRFSAqtG0e6U2Vcx4Guce9nqiAzmgpKqOsn7c%2FijzULScy8J3%2FAGdkP9OiPVh9QNBWe0rP4o8NHJTmNhRY%2FZ2Q%2FwBOiAxuq7ZgVe9%2F7cTfPn%2BiVxf8JAKzdpI76zJj%2FOIjwVinSrOOa0%2FPzKmwmqzl9CdZuJhfZePVl9MNT2a1CmJfUW3K1J6dSbG3SoHKA%2FSNCEIBCEIBCEIBCEIBCEID8%2BnF0nRxAZkIT%2B2mo%2FH4w5Gj1foEW5lKifjMb14xE6OInMxKezFVRt6fGHI0U6LSLduZbN%2FujAZhhr%2B1V%2F3v5Y9brTTyFNPNJWhXNKhcH0jtjyYa%2Ftb0f7kKi4pBUbJBJJAAHMkmwAHaSdgID2V3EFdxO%2FITOI6vNVN6lSDVLkXJpzpFS0o1fo2UE7hCbmw88WyMukctcQ1DAGKcx0uykrTsI1SRpE9LTSlNzSpmaCihKUEbaQnrBVjvsIxqep1Qpk05I1KRmJSZaIDjL7ZQ4gkXF0ncbEc4DzNMTEy50EsgqUb7J3Meo0KsJ8qnuj0oivh55MtWWnXFaEhCgTGcpqlMJSVzaNR6wuodlr3gNcTdPm5QDxuWcZvyKkWv8cZPlnk7mFnDVJmkZeYdcqTkg2l2dfUtLTEohRslTriiAnUbgDmbGw2iOOqhL1Bpro30r648lV%2ByMp4Y8Q16nZ24FwtTq7PSVJr2KaealKS7xQ3NlsOdGHQPKAuoWO28BrnF2Fa1gXFVVwXiNhDNUosyqUm20LC0pcABIChsRYg3Eds5JH%2F9Ga3EJB00quqJ7L2djl%2FiVbUjiFzGLibL9sUzdPaOqiOocjf%2FAIN16%2Fg06vX%2FAHVg7vHzT4UP1fdp8FtH8lbrYR8pX%2FDPucjZcMqcyXrK7CzWIpFRPbdUmR%2BSPdIp1O6e9twf5tURyqpdZRlHXqg%2FVcPM0F6ZklKkZh9Sao%2FOBo9G7LISCktJBsvWRyNuQv51zCZVh95V7Blwbc90KH5Y%2BkWcZ0uVO1pvFoSlmlgJ0kyYWRfcEqPPzxjIeUFWvGa5o4FrOWeNqpgHEU5JTdQopZbefknC4wvWyh1BQpQBI0rT2De8YKrquRaEPWiZvsYLUFG948oVEdR74kekOgC20A6D3R5rmFzAexKx3xVDiYt%2BpXfEekV2mAuKZhzo9IF97x0IdLS3F3trQvfuBb3%2FABxpbLHB6sw8eUTA%2Fs1L0lNZmgwuemELWiXbCSpThSgFSrJSbAC5Jjbzk7LFkzGouMaHEpUlJTrTpKQrSd032NjuL2gNJV4IApxSpJCpFBsDuOsoWPn2iyl06iIzXNzLqo5T5g1bLur1KTqE5SEy%2BqblAoNPJdl23kEawFX0uAG45gxgp5wHrS92Xim9ZTyTFDURfeHSXse6A94WByIicObc4toWftonCyPhQFyDtoj01ot%2FSkdsA6b84C5iYjoAFaXG3kjfogef7jeNL5YYPOYuYFAwEKu3SxXp1EoqecbU4mWSblSylO6rAHYc43M7MtS6VrukoaaW1cDZWlJTqseV7Xt2XtAaMxMEJclCkpNpJpJ094vFh6cXteM3zay5m8qcfVPL%2BfqUtUHaciWX41KoUlpxL0u28CkLAULBwA37QYwK%2B94D1pe0nnFEL1PXine8B1dxAe1Lhiql098W%2FpVQ6ZcBcg%2BRyibxg98W5LpPMmJw4k%2FCMB70TKlLSm%2FNST6rx0E5qXiJOtVipa9%2B4Fk2%2BSNMZYYOTmJmBQ8Brqqaa3XJnxZycUyp7xdASVKWG07rICTZI5m0bafqbBqjs5crZQhbYV0ekqT0RbCtG9jbfTfntAaTxUWiuW6NaFfmNGrRyBuraLI24e%2BM8zyy2eyfzKreWz9al6qui%2BLJE4wyppDqXZdt5J0K3SQHbEd4Ma91kbQXe1LvYYpJI6a8Uel88Aontgo93SfuodJ%2B6jxeuH8KA9yXNvKiolw6djFvSdvKMTpUexUBdJN7W60nXzWj5VARuOcsibWO24P8kRrfKvBbWYePqNgt%2BtJpLVSLvSzpYL3QobbU6ohsEFZsggC43IjYU883MPOOyxWUEnoy4nSoptYEjsO24gnNkWOk24X5A2vqzJcN%2B61LG35Y6%2B4HlBXDnSrHk3VQfN%2BaDHN1KyfxnnBkfiGq0jHOHqZh%2FBVYbqKqC9JupmH3nGEtmZL4SQpRSFJCb2AHIbR0pwTBaOHamNuJAKG6qNuR%2FNZF%2Fkj5p8JFUdx2cf5lPsqdvCNtU%2BafbDgqbFqhMDumHx%2FnFR0DwOW92id539r85%2FObjn2b%2FthMf%2BIf%2FwBIqOguBz%2Flonf%2FAN35z%2Bc3Hb00n8gW%2FwDDuamH%2FpNPpXLPCVMzxX1Rgc3ssXgPvKo0PP8A6EeQna7RIPqMdBZy0rE1a4yJGRwxPYap7ysGNtzkziSYUzT0yXQul7UtHWSsgWSQDv2RoOqolXJ2aFL1eKFaugCiSQgnbc7nzHtEbOhs54Fdv4YYb5H4%2Br0sZzHShftlca20OyCEDuJYQSI1Qlelwxt3OLBtZpNKpGYrs%2Bwuj46mJsyDDT5LzZkC0w4H27WTcrBQQTcX5Rp1Z0uGPTtR7fGFWHmjzTLiXnRfsimZkpOkxTKwpWqAmUTrFuyPUlfVEePzxUQvbnAevXZOwg28QdwYoBza2q0QK7Hy4C7tzqlEAnsMbLoadWEaQ6BbXLvkecF0gERqBqbQklS7kIuqw7duUb9r2CJjLkSOB5muyNXmpCSQ4%2FMSSXAy25MJD%2FQAuAEqQHACQLXO17XgnNhmaCAsVKYWB0rdYQwsgbbSqD6%2ByNctzFo2hnPgGqYbpuHceu1OWmKRjvx%2BcpjDbyi%2Bx4o8Jd0PoICUqKxdOm90kdsamuO%2BCYnN7kzagCm20eNa%2FfSq0SF5INokURe8FVfpBECsGKF%2FPE19oCqhW8ehKwOceJKiDFTpPPAXVudWrYqMbWoTa%2Fa5TG1fqS%2BztKrxplMylkB1XIR0LV8GzOXhksGT9alqrPU%2BWbcnJmWCw0HXkId6JJWAVaA4ElVrEg2uN4DX2bCCJyamAk9SqutX7Cnxdo7esxr9Dlo2pnjgasYbZoWOJqoyUxRseNzlUpjDLylOyxYdEs8h5JA0q1IBFrggjfsGptQgK5dOkiPKXLKJgp8cook3MBOt5SuyJmiTziloSfhRMEW5LgPUFEDsiq28Wt9MeVJ28uIhzV1dUBc25y%2FKNsyqCijU0H9bG3o1qEaZlFqTMNhKdRWsICb8yTa0b7xPhR%2FAk8nBM5iKWrVRokqiXqExLNuJZbmlXcWwhSwC50YWlJWBYm4HK8BrzNJkNzjXUsUTc4i%2FeLoP5YwlDlhGy86MAVzCzdAxhOVKVm6RjmTmKvSQ26ouMNtTBl3G3UKHUXrRewuCCN41b0loJh6jMnSRaPLrN%2BUQLo74lPPyoIT6rdhiVSz3GIWv2xDR5zAQS6Qu8e5iasY8BSAqJ0KsqAv0nOLW4hOrtA%2BWNpygKafKBQIIQoEH9%2BY1DS23ZqflpNlQS5MPNst35a1KATfzXMburGGZ3Bc87g6qVOUqE%2FRVrlJuYk3CthToWSoIUQCq17E23IgMnwWEe5VnhqPWGCWikf5Ql4z3wbCB7IZgrK7WlKQNPfeaVv6rfLGLZXZeZiZp0nFWWuVcph12pYmoC2amKvUhLPGXZmm3dMqkmxV1ElRN7AnlGc%2BD%2Bo85h7GOZGHqpKhE3KNUptwhwKCVpmVgp22PPn5o8Xp1OWCW%2FniP5qXWwn9Jp%2FrkYZxiA%2FVEYrUrmfFAPR0O0YTlQP8AhRwZ%2FwDvDIf6ZMZrxhf%2FABD4qv8Aayn%2BhjC8p21O5qYKQjma%2FIn4nkxs0z%2F61Tn5H%2FgwU%2Fpf%2B6Pa6f8ACGD%2Bw%2FBB%2B1xux%2FoY5uzfa6LNzGaO6uTR%2BNUdM%2BECkqjUcF4SkKQ0wudexww3Ll0dVLvQEoub7Jv5XmEc%2BZ30iapeYc8xXKlhudxCffKy7hycXM05c0o6joUsakrAIC0bgECx325nwbTngVP8VS%2BJx%2FaamBYqWFYBkkLdVoQ5VDpPIKIYtb0xpdt%2BN3YgwbV8WZYVmvUaZlUMZfNqqlWZecKHX2JuZZYb6AAELKVDUsG1gRa8aNdIaPKPfOdk9KJogmKJcuu5MeZUykGwIiHSX5EwQ9hf2tFMrvHnv54jqMB6kOWHOJ0zCgdlx49ZiBXY3gLmH9oz7LcKXRa%2B6FJAS5KoIPb1zGr%2FABgxu7BmEZWg5YyONTiRiYmcWTEzKilJlnAuWblHgOmU6eorWSRpG42vAW7HDF8Lyy9SbFM4qx57OND%2FAH9Eaw6SNzYnwG7inKit5hSdUlmBl89LonpR5K9c01UJoNoU0QNN0KSNQURsra9jGkFuW5wHqE44OqTsImYJSiPB4wiIF1R8lxQ9EBc%2BlibpQYtQcN%2FLVE3Sn7dUBci7blaHjJA7ItvTfujEqnyPPAXEzar842FlwA5T6me5TA%2BImNXNOlagPPG6sGYYlMPZeUnFq60qYnMXF9YkRKrSJNmVfLYUp09VanFEkJHIJ3gPNmihKMJ0kXF0pfCfOfGN41QHiO2N34%2BwOjFOUczmVKVdplzA03K0udp7jCgqYbn33FNPNuDYlKmyCk22ta8aJ5bwTmqPPqUg7xWYmAGgCY8pWkgiKPSEEAQQufjKe%2BHjCItvSGHSGAunTAi4IikuZWDYGPB0p74j0o7TAezxqNmZdBCsKVJ1RTqE5Lpt27hX4o1OlYKgO8xvCgYPksJ5fUCutVt2cncay3so%2FK%2BJ9G1JNNPuspSl0n3xZKbkWASO%2BAs%2BaSEJw3SApSUnxMKACt1fmpfMfljWHSKjdOYOBJet5RO5sNVhCHsOVSSws9TXGDdxMyH5hMwh0HaxRpKSPPfsjSGvzwHoL6gm14p9OQecUCs6rQJ9PxwHrQ8TziqHCe744t1%2FTEbjvV8cB7Fum%2FK8Q8YIHMiPGT%2B6V8cS67dpMB7kzij2xtTLoJXR3HkKSrpCi9uw7gg%2FJGn0OWJMdCUnBNNwNhihOylamqhM4pocjXpkOyyWUS3SlxKWUWUSsJ0C6ja9%2BUBsjh6CTnng4%2FDTNTKk91xJvxgXAK443n5Sg2UkOUWpoWrTeyS2bkd3p88ZZlDSqriDHtFw7hvGbmEK7U6giWka43TfHlSwW04gpS32FRXbVvYX9Me7hey2msp%2BLuoYBdq8tPuUaj1WV8bZCm0vANAFSUqF7m3I8t44Ok05YXbT%2B7Psb%2BHZd0UR52W8foPul4NVfb2ooH%2FqFRzAR2iOnuPsE5m4RUBYDCLYt3Hp1XjmKMGhs%2FkO7%2Bif5pYr5rvFfplTVEEgxExMlIO0elaqER0HvMdBnIPBQ4XcF5yJnqp7PYgxTJUaZb6VHiwZdnlsL0i2oLCE3Bva%2FwAUZ9m9klwYZJY09o%2BYWNcfyc%2B5KioN%2BLIS8gSxeW2DqSm2q6Dtz5GA5ACILFov1RpMjUMaTFAwImanpKfrJkKCZoBD8wy49ply4BslRSpOru3jppXCRkczjmX4fapnXWWM2n6WKhdNPSaUl0oLgaHwldVKjp1ailJI32gORInsY3NgPKfK2jt4wqHEfmc3hBWDqi5SXMP03Q7VKg%2B2E63mkq3LN1p0EC6t%2BVov%2BanDDTML17LNeCcedNhjNNVqfOYhaRJPU0BpDxW%2FyBQWXNQJAOoFJFyDAc9RAjtEde07hIyMxvWcRZa5XZ21Kr48w3TUz7ilyra6W8V7ISFoJ6uohJ0qJSVC4NjGA4AyPy1lMlJTPrP%2FABVXaBQa3UPY2lU%2BjyyHponpFtl9ZNwUXadUAkeSi%2FaBAc%2FRTcT2iNu8SmRMzw%2F44l8ON1v2do1Yp6arRan0QaW8xq0rbdSLgOJJTuDZQWki24GoSQoXBgJIQhATwhCAjYd8LDviWx74WPfARhC474QA8oDlA8oDlAQVEE84iqIJ5wE0UnIqxTcgKNj3RBI7LRUA2iAAvAInREp5xMiAnQu3U16kxUQ4HSSVKChuFIWpCvugQY88TDqmA9C33ynovHJlTX2jky4tPxKJEUriIa%2FN1Yp3PSW7IDMMus0sf5UT9VqmX2I10l6uUxyj1IBlDiZiTWblHWB0KBNwpNiN4xFGhttKG%2FJbSEJT3AbRCEBPcwuYkuYXMB7XaxWH5YyUzXKo9Lq2Uy7PvLQoXvYpKiDuBzjxrXeIRJAThUVAoGKIG8VByhA6D4XbexeKlJvqSpnke5pZH441tgKqVuS4sJ6Wo9cRS5ddSm36g85KCaSZZplanU9ESNRIFhuLEg3jZXCuUGl4qKuanGr%2FAHtVo1DhyqyVD4pKg7VFvNszk5Uab0jbRc0OPMltBUBvp1qSCewEnsjzVznPF7f7Pc%2BwaQfg6DXD%2BKPZWzJlspfR1NItcJJvYHcCLXxPsdNlplRPJWrSBXpcp7LomGlX%2FlRe2wrpR0idKgLEdxG0WniYV0WVOVUsE%2BUrELxPmMwyB8dvkj0r49DmbpREOkEea5hcwSrKcimpZPbEhV3xLzgKnS27Ym6UmPOpVjC574Cqpy%2FbFWUR07b%2FAEjmlKU%2Fa3jxEk849UrqLTxTyKDeA6wxnKqkJjDNNWrUqVwrR06uV7ywVf5YxviJk1sZcZR1HpLtPyFeQnzqRPJ1fzx8UZdmOwr2x0l4m4OG6OB5h4m3%2BW8WDiWaSzlHkw0m%2BoUzELir8rGooAt6xAc4pfA7YldfBjyFRG0SlR74Csp%2BJC6YpkiJS4BAehLpEFOXjzFwDsgHQRAVVuXidhqYmJZ51CkgNoOoFXZHlKyYuchtKP8A7pJT8kEw6pzDR0WI6ZLK%2BysYcozbu3whKI%2FJaIPYhVhbKPGVWYo5qjj0oinPpEwG%2FE2ZlYR4woHdaQpCU2HIuAnaPdm4gIzCmUJ5Jp9NA%2FBGosFeek5TJTMBx6YaacmJORl0BawlS1GbQdKAdybC5A7BfsgiG9%2BAQg5WzZF%2Bq7Pk2%2FvJMcSVYpU0pTYsklZT5xrVHbfAWkIygnXVEi66gbjmCGTHEdQ%2BwncHde47euY3pjLDrP8AilyrCfyjbeiGGKVBKoKTBKY0XVTBOqIhsje0ZLh3B1YxI4pmlSbswpATqDTZWQVbJACQSSTsAASTyjpTJzgkncZUWZm8xKzM4TqU8lHtbp82yEJmlgkq8bv12EK8lBte9yRtYhyUgXO28VgxrHnjpWawmnLqfqWCp7BtLkZiQeXLzLE5IoemUdwLqrk7EEKHMEER0jlJw0ZH5y4HZreIsGMys7NulCpqlumWU2UNBtIAF0lOwWRbdRvAfNQsWNrGJVN27I7P4h%2FB742ylo0xmDg6cXinB7G8zMBnRO09Nrlcw0m6ejvt0iTbvA5xyVVqS5KOKS4nT2wGPLBESR6HUARQsICEIQgEIRBXKAXHfHpk5d6cm2ZSWKQ6%2BsNN6lWGo7AX852jxXMVUHvMB76nTpylzJl5xlTaxcEKFrEbEekG4ieiU56r1aWp8tJPzjjqtpaX%2ByvWFylPebAxkuF3JPG8zK4Wrk7Ly06%2BoMys7NPdG26bdVDjh2Qu%2BwWdjyUeRjE20TUnNhTK3mJiXeISpKihba0HncHYg90Be6q7SazRV1Wk4Nco7ci%2B3LuzTTq3mHFKCilDhV5DpCSRbYhKttox6LlW6lWJ5emqvO63SH13ASHSdwtQFgo87Ei%2B574tUBfsKJvPrP7iMwDZTtFy4X8pXc5MxV4VNXRTJZmRdnJqYKdS%2BjQUjShPaolQtHYkzwO5YSyrPY5xChXPdxhJ9NiIDiuIgG4jtWncEGUUysXx3iPRfclyX3PpEXxvgSydUlKVY%2Fr6iTt75Lgj4hvAcLN3DfriKRzNu2O%2BpTgFydmB0ace4mUpXkhJYOg9%2FLeLovwfeSr5unGmLEiwulHQEX7bC0Bw3lK0mZzcwGy%2FqLa8U0kK02vbxpHfHsznV43nLmDO3v0mKaqb25%2FmpwR3DQ%2BA7KPDOIaPiemY4xcJyiVKWqculxMupta2XQ4lCwEg6SRY2N7RJX%2BBHKCv1%2BsYifxzixt6sVGYqS2tLKkMrecU4tCdt0hSja%2B9oD53obXaJVN2v3x36fB75RabpzFxcFA6r9DL209oItyiQeD6yiAVfMTFaSfJIaYNvjG8BwEltSz1TFQAtjc%2FLHfqPB85U2%2F5RsUuemXl03i3zfg%2BMsVq0S%2BZWKWTfcFiWXtAcIE37YlU4Ux3mPB85WLTpTmRinVbmJaXMcsZ%2FwCRVcyIxXL0Oo1Buq02py5m6TVGmy2JlsK0rbcbN%2BjdQq1xcghQINjAapmHS4y5q7B2R11hKcWjDNF6tkpkJdFz%2Fex%2BWOQX%2FsS%2FQY6xws637AUfX%2BspfqlVyD0YG3mjJYx%2BMifNPuYrx8l9se9tnC1UTKT0o64pOggpWm2yr%2BeN%2FwCU2MnHCvCVSWkqlQTT3Rt00v8ABSe9Sb29QjlaVn3WwwttHkJ0qT3RluFsbs06dbM5MOMusrC5V9N%2Fe1DkFebsjbn8LW59nPBl2I5MRzxVeC7Kuu5jnF9SW8mgvP8Aj01Q2h73Ov8Aa24snUEKV1lG5Jtp5GNkYNzIp%2BIkGSfmJdudbSNQQ4Clzzp7fVGWmbShsOrNkcr9kKuFVTNnnqna2KK4oqi05Yaz4ipTBkngOuYmqeD6TP1yalkyErOPsXeZSeqlLahYoSlN7Aco4srWd%2BZ4y5qeUjtbYTSqs82uoTzUqlqoTcs2gJRKOuosFN2SAVaQpQuCTc37C4k6xSzlxNMCdl1vCZaAQVgqub8hzjgCqsVquVBVHwpS5iq1BXSLDTQJCEJF1qUR8FI5neOhRTRd7vTVMZTm1oibza1Z641MKxNMLEomQkUDp5shloJHI%2FNFeRpyZCRZpzW6GwSpR21LPlGLhT6Iin3nKi8JicIuCB72336RFRxbfSRzbXOqc29TVERwYWyo38QmNCPIbOrl1trfJGKNnqjqXjNpssKkZxve6W1G9ue0YUyglI3jFK8MFxIpn2yTy3GwoIKBYns0gxccbSDdPxC3Kod6QKk5Z3V%2B%2FbSq3qixYmUTiCpj%2FtLfEBGRZgL6TEMu7%2F3dJI%2B5ZAjBLLDN8kmsIIxjSTjLDSsR0oKV4zTEzhlC%2BChQFnkgqSUqsrlva214t2YErQ0VOafw%2FSXKfKPPKU3KPPiYLKCo2RrKQVWFhcjsjzZbOaMQU8%2Fu7fIYhjRw%2BMK%2Ffn8ZiBjKXLAIUxLJSBayWE3PrtHmmnGWykIabPf1BEXndI5xbpiYgLlL1GXC0Jmukbav1jLttlVv4Qj2rqGE0NoMqzXw8AdSy7LhJPZZIRt8cYx0ioh0kBkM3UaJNLCpiluzzoGlD04%2BSUJtYJCUaUxb3nG1qs0AlACQEjkLRb%2BkMV2XE2BPwdzAbW4e8naznbmdRMvaOpbJqTuucmgNpOSR1n3yeQskWH7pQjsrwgObtFwNhih8LmWwbkqbTJSXXV2mrWYlkJ%2FM0kbcyd3nPOU35xsvgNyPmcqckHM1WaVKVTGGPpAT0i2uYS20iSTcyrBcIsgLWNaz3AAjaOecX8A%2FFrjbEtTxXiWWwnO1Krzj09NPe2NsFbjirnmNgNgB3AQFk4bM7M3MQUKjcMOU2EsvkTU09O1NqfxBJqmzNTSQXtam1%2B9JdShOlCiD5I5GM58JLmrjBzEOHMmn2JuToFEkWZ9SlJSy3V5tbYSuYDSLBLaDcIBHNSiOwxSyh4KeLPJ7Mih5m4foGCJieoDrjzMtNYiQWnitpbZSrSAbde9vMIs%2BM%2BBDjEzAxJUMX4uThmpVeqPqmJqZexI0SpSjySLWSkCwSkbAACA2TwG5k4bzlyixLwkZoqTMMy9MeNKCzdb1HWq7jaCdy5KPFLqLbhB7hHCucuV%2BIMo8d1zL7FKAalRJtcu46gWRMt82phH7hxspWD5yOyOocCcD3GHljjWg5h4RpOFmazhydbn5VftiZsvTstlQ2uhxBW2odyjG4PCMZKoxvljTs%2BqfRPYyuYXZl5OuSqnAsqp75shGsbOKl31FKVdra9uUB8tHUkKimeceiZAC4oAb3gLxhvHOK8CT4rODsRVah1AILXjdNnXJV7QfKRqbIJSdrg7bCPTinH2K8xJ5Fcxjiis12oNMplzM1WdcmnggXISFrJOnc2HfeMXebUTcnaKsojynDpT8HT2mA9IVflBJOoxKAb90X3B%2BFatjTFFJwhQWG36nW5xmQk23F6EredUEpBUdki55mAtMSLuT6I3XTeE%2FOSq1CvUmVoMg3N4XxPL4Qq6Hqi0hMtUX1lDQ1XsppSk26QGwuI1NW6LPUCqTtEqzAZnadMOSsw2HErSlxtZQoBSbpULg2UDYwFrHOLlJ42rtJpVQw7T6tPs0qrBoVGRamlol5zolami62NlFCt0nmDyjwI%2BybiLe%2BwttxcBleJMb4lxzNiu4qxJU65OhpEt41UplUw%2FoQLJSVq3sBsIsZcudooSnvcur91E45wHsk917R2B4RgacYZYJ%2B1y3pA%2F0kcgSF9Yt3%2FljsDwj6wccZcJTyTl3R7eg9LAccL5wUbbwXziVwXTAZRgnOjMnKxycGXeOa9hxFQ0eOClTypfxgpvpKwLgkXNjz3MeDE2MMQ42qz2KMV1qdrNUnCFPTs650j71gEgrV8IgJA9AEYspsuO6CLR7m2i3KhPM3gK3SEmJr3iinsjNMrcq8aZx4rZwPl5RxU62%2FLvzLUsXktam2UFbnWWQLhI2BO52gMRiW5jbOGeGrN7GeFKbjTDOF0zlJq7NTek3TOMtqc9jxeaTpWoEKSLkA%2BVY2vGqX29BgJUvJa6yztGQ0jOrH1AlKRTKFi6tyMjh6fXVKOyzNFIp82u%2Bt5gAdRSrqvzB1EEbxjLiOkbUi0WzxdfeIDLcU4mrmMKvOYrxBVpiq1KquqmZucfILrzqvKUsiw1eqLDe6o9DbK2ZFvUrZKTceeKI5wESkkREJ2tE45RAnsgJeUTxJE8BUbFjePc1ciPI2No90snvgM2w%2FwD2kA71R56DpOY%2BEwRe9ckBbzl9EemhjTRT5lfNHjw6q%2BZOEx%2F37If6dMBbcd0qpUPGOIKVV5VcvNNVKbWUKNwpCnllKknkpJB2I2MRyjKVZlYYT31qSH%2BfTGwao%2FQMQzFTwfjNbctItz84KRWSCXqMtT6zpWRu5KKUesk7oJKk7XEYngLCtdwfnRhigYikFy8y3XZAJXsW3kl5BS42sXC0KBBCgSCCDAfo3hCEAhCEAhCEAhCEAhCEB%2Bf7jTTo4k80E92Jp%2F8A0640G8bSTQPNTZP8qN%2FcaybcSWaB%2B2xTUP8ATORoJ5OmnNX5hs29Sv8AXAZdhi4lBc%2FpQ%2FHG8%2BEWSpk%2FxFYVlajJSs3MJaqEzR2poAtLq7Uo4uSCknZXvoBA%2B2AjRuHNpMH%2FALNH5YvclOTtNnpaqUydfk56ReRMysywvQ6w6g3StChyUDygM4XmcBktmZgDH79UmMbYpxlTa7OTDzZ0pdlul8bU8s%2BS70irBNt%2ByMv4qZuq1ZzKzEmMG1N47rOX8hNYr6QaH3nwtaZd59O2l1bAQTte1o8r3FBWajOMYmxNlBl3iHGMrZbeI5%2BQUl5bwtpfeYQQ084LA3UOe8arxTirEuOsSVLGGMa1MVat1d4zE9OPm6nV2sAByShIACUiwAAAgLKoOKWQm5vEpZf7Wl%2FFF5wxYVxm58kE%2FJGf6gvmr5B6oDUxaUk3II9Ii%2F4HpmN6hiiROXElV5rEUisT0maS0pyZl1oOzo0g6bHtO0XfG6L02VWCnUh%2F4PPcRnXDhO54YiNayayYq0vQJXEym5nEWIW5cpmaXKJsNZmgQW02BCWxupSjbtIDVGKmcUS%2BIZ842aqaK888p6f9kgoTK3Vblbmrck98drZFgO8Ha0nZXsdX0%2BmwdjSHF%2FmRg3MPHdIouDp96tDBVLFCnsQvIAXVZhBGpZI8sJ0nrciVKttG8sjEKPB4AyNalU6vbep6%2FwCWPm3wm67hdo%2FzY%2FkrdbCYzrr%2FAIZci5d1%2Bjz%2BW%2FtR9kUprLb8tPMShSq7rLbKtZCraQRvsTfYwfYcm5Z%2BWZAK1trtflYJJPyAx6spqi9I5C4r8VUllc%2FXKVLPPJbT0hZDCl9FrI1BBVuQCL7XvaPKy4daiCRqbcGxI%2BAruj6PZ7HKnawviNxjhvH%2Bc2JsX4PqLlQo1QXJ%2BKTK2FsqdS3KMtqOhYCk9ZChuOy8anc8uMnxHKy8uZNUs2UJek2nSnVexN9h5oxlwdeJhCkVb84avPApF4hpESJ9Xphq9MSaRDSICpr80NfmilYwsYDPslcUUfBuaeGsUYhmnJam0%2BbK5l5touKbQptadQSNzYqHKNluyr0y2uTlk%2B%2BKQsNJOwPvZI9Vt456RdSgg8iQI6XIWxUHEsLspu6dXobIP5YDAOJDGmHcxc6sR4zwnU3qjSZ5unol5p6WVLqdLciy0s9GrdIC21AX5jftjVLhN7xkuIJdhkyqpcEB2VQtV1X61yPyCMad2O8BT1w1xLCAnDkTa4pQgK%2BoQCt4pX88Rue%2BAzjJ%2FFNEwfmlhjE%2BI3HkUynT4dmlst61pRpUCQntteNtvS79QPi0uQVzAVoJ5EaSq9vQL2jm1Bu4hJ7VAfLaOoUKZbmEp1dG22gpGncgdEoAene0BrXiNxzh3MjN%2BuYzwk%2FMO0meZp7Uut9ksrV0MkyyolB3A1tqt5rHtjVKzYxf69KNyjkuhlvQlcq04E3va4O1%2FVGPuc4CGvzw1%2BeJdJhpMBOHO8xHXFPSYWMBW1jvh0nnilDlAbAyOxfQ8C5t4Wxdid99ml0ydLk06w2XFtoU2pGoJG5sVA2EbHl5Kanp005ACnXA6StA6pAQpZUP4IvaOfWOu%2B0PtnE%2FjEdMuMMe2J9HR%2B9dI4hSf3JaIgNfcTePMO5oZ2Yox7hF2Zdo1UclUybkywWXHEMybLJWUEkpuptRtfkRGpHNoyTEEozKNSYaB98lEKNzffcfkEYwvnBdEKiYLikBaJgIKKmuGuJdJhpMBV1%2BaAcIilYwsYDPMmMZUXA2ZtGxPiMzIpkoJluZVLIC3EpdYcbCgDzsVgkd14zz7Br179EnSrTvtbsjSNLbbfn5Rp0XQ5MNIV6CsAxviZQgT00kDq9IoeoQG5cCZ6ZX5Q5MZiZdYnnapN4kxT4j4qzT6etbDDiUFZQt5RCSQlaCdN%2B6N%2FcFbvjHDnSX97Klqpa%2FP9Fq%2FLeOQMyVuI4XaEwD%2FwDMJxz1mnAerYD4o684JSpXDZSVKttK1FIt3eNq%2BePmnwkRHcVlOW20pjqqdvCdXD9HvhwK7%2BinP787%2FpFR0TwMp1Z0T%2Fmw%2FNfKtu0c7O%2Fopz%2B%2FO%2F6RUdFcC9xnROH4KqBMA%2BnWi0dzTP8AUNvH7se2Grh%2F6TT6Vxz4xFh3C%2FFqiexHWWKZLTeCpeTS88lRQh9xLiUA6QSBbtt2xomc%2FMTz6XVC7NypSTdJG5uD3WtHQ2b6TK8YExURLsOOSuWTs5KKdaS70T6GVaXEpUCAtKhdJI2IBjnJ196cemX5uYemXXlrW668rUt1aiSpSj2kkkn0xm0LiIwO7ZeLDBfZ%2FHVT55Vc%2Bq9QTlvlrgNifK8RYbdrz1ZktCwZITTzC5dKiQAVKQkqsm9u2OfHlHpFRtjMhpL81iKefKn5sVKXa6daipekMJuCe3%2FUI1I8TrVHqWqplzfeIdJEpBvEICoHInS5vFCJgbdsB6NdyRflEhWCCb8op67Em8S6jYjvgKqz1FD9zHT%2BZmLKFjDGMxibDc%2BJ2mz7Mstl%2FQpAPRyrSFpIULgpWkpPojl3stG66SwJXCdAQ2kJQ5Si5YfbqcJUfXAXziAxZhmrZdZWYKpdQcermEpCtorksphxBknJmodIy2SoBKiWxq6txvHPy1ERs3MptEw%2FVaw6FKm3qsWHHFKJuhLCCE%2Bok%2FHGrlkd8Ewa4a4pWhYwQr3ENXnincwue%2BAq6vPDV54pajDUYCo4Spopv2GOn8f4uw9jbF1UxhhucXM0upBgy7ym1NmzUu22oFKtxZSVD1Ry30kb1pTctK0OlSrDIQ2ZFKtN7jUoXUfWYC5cReK8P1HBmW2B5KfL1XwdTapLVpnoVoEq%2FMz5eba1KAC1dHYnTcC9r3jQBdvteNlZqtodfmqiVqXMO1J9t51ayoq0staQb90auuYCcqJMNXmilq80NXmgK4X54mC7R5tUTajAV%2BkEOkijc90LnugPXLvllxp0n7E6lw%2BgEGOkszcQ0TFuYNexThqppn6RWpoTkjMJSUlbRQlJ1JUAQoLSsEEcxHMXSRvoykpIsU6WkWAyymWuEA3AJcJPy7wFfiCxfhms4PyywtS59UxV8IYen6bXGOjWkSk05UnHUN6lABatBBOm4F7XjQnSeiNhZvMspqr9QZv0s1UJrpVkkldiixPoBtGuIJhPrERDlop%2BuHrghWDsTBwR54mF4CqpdzeJNagb3MSk2iUmAu1CqDEhWqdPTbhSzLzrDzirE2QlxJJsOewMdF5g1WlYgxzX8Q0GpMVCmVaovzsnNMk6XWluKINjuk94O4jmenBC6jKIcRqQuYbSoX5grFxG%2BW5ViSl2WJVoNMpC%2BjQDska1bCA31wl4%2By9ynx7MY6zNxvSsPU12g1GRlzMLUqYdcWEoBbbSCSLgi%2B3IiL5wOVGUr%2BZOa1apV3pF5VK6J09XZU06oGx7wI07SJKQqGRWcjs9S5Wacp%2BHpFySddYStyTX7JMkqaUd0E3IJB3BIN42B4NZDnstjtWk9GWqQm%2FZq6Z3aPF6fU54HbTy%2Fg%2Fz0uvhH6RH9cjEuLsn6oXF6TvZ2WN73%2FSE7RiGUes5tYHKdW%2BIZAbf30RlfFt%2F8RGMd%2F0yV2%2FwAjG8lxqzcwQi1wrEEkD9389o2NmjNOfkf%2BDBT%2Bl%2F7o9rqnjtrknQ8OYInKgro5VOPGpl52x6jTUuoqO2%2FJXZ3RytmFNSNTxhVq5SKmxUadVZx2alJthRKXEXsR1gCCCLEER0v4QxH9hOBmJhAKZvGsuqxOy0dBZQI8940Jn1UX6lnFilTgDbMtUHZaXlkIS21LtpVshtCAEpFyTYDmSY5vwcU8DA6ZnbwqvatidczeKoWSWxBQcNZOZpSFdnxJzeM6NJ0ygsqbWoz0xL1Fh19KSkEJ0N73UQDyjmqed1r2jdGOmG38Fy3jAVrk1zTzHXICSotBW3LcRpBy%2FbHvmgkiKTaKcIKKwcibXFEAxEAmAqlyJS5EhFolPOAqa79sdAYUxJh%2BtZO4Xw7Izuus4YcqYqMsppSClExMpW04lRGlYIBBANxYRz1G2MsGm0YSqM2lkdK7OtNLcN76QRYei5MBsWexLh7DuQuYGEapNONVfHDtJRRGG2FKS%2BiTni5NKWsDSgJBTa562rblHNkw4T5O0bizAaS5hKmvuJKlSzc%2BWzq8i7zQO3n%2FJGl1qJgIA9sVErtFCI3MBX6QbQ6QbxQuYiDuYCr0hiVTnbEsSkQFZt0ggiN64dxZR67ldhXDck%2B97I4WZnmJ5txrSi0xOKdZKFfC6pNx2GNBg2jbmWMs17UZmbS0kOKmEBxdt1ALIFz3C3ywGe4ixVRMP5D4twhUXJr2UxnPUp%2BkoQxdssU994zLi3Ser1lhKUi5JHZtHObj%2Bk2Bv642rmew0cNUyaLYLjbT4C7%2BUC%2FbcdnKNQQFXpzDpjFKIX8xgK3SCHSCKUICdS4gHCBEsSq5wFZDqgoHzxvqj4ro%2BKst8I06nrmUT2E5F2mVBp1uyCXJl11tbarm40qAINiD3845%2Bjc2XjTScBJU2yhC3JhJcWB1lm7lrn1QGXY7xnRqFkFUctX5acVWsWV%2Bm4jlHUNgy6JGUbmWXNa731l1dgkDsuTyjnRbsbZzRZZcw5Ivqa99lJbogf3Kn1Ej1neNQQFQOkdph0x74pwgJ%2BlXDpVxJdULqgJy4qJS4q3OJOtEpCu2ArocjoSl4wpeNKDh009E2y9h%2BgSNBnGX2wAtxkuHpm1JJughSedlXHLkY51vaN54BQw3hqU6BtCSqWaU4UpsVKJVcnv2tAbWyexJS8A46o2YlclqzOSOHqmw8uUpMn41NPqAWsJSgqTpTZtRKybC1u2Mg4esw6Pmjxp1DGWHZKaYp1SpVYfZanFJLqEqRffTtffsjycNrz7GdmHHpV1TTl5tClpWU2SqUeSbkdm8YT4PNNs9h1b6cM1Xf7XqJ3jzmlk5YPbz%2B7V7G9cMovNFXgltzj8GnNLCqf%2FwBk2h8TyuXxxzGeUdNcfS9WbmHG9%2BphFj5XlRzKuKaHfqO7fw%2B%2BVL7qt6%2FSp3uYrNbuRQsRE6FlLgj0zUdnNtPv8AWVRQlSgvMGkgrCdik1d4fjt8Ubl4iqvxAyGaYZyq4ecNY6paZcOqn6tR0zDrM6p9wFkKJHVCQkhPYSY%2BdjGJ8YT9LksGs12szFNbmW1SFKZmHFNImNZWgtNDYL1kqBAve5EZ9iCtcTeDJFNaxVWsyaLJuOBpM3PTEy22XDyGtWwUew3veAwcpxDhTHTK0NsUjEtGr4WlucAQ1I1JuauG3QdktpcOg3Ngnt2j6IYZl5jEvEXS8TY54X6%2FhXHZoKxUsTPVRiZo0pJpQoa2XWiULdJUW0k2UGzv3x85pWmV7GVZckpSSqFdqtUU464022qZmJpR3WpQ3KyeZO%2FnjPaKviQxBTqllbQZ7HlRlKGgS1RoLT7yvE2%2FJDbqCdQTyTpJ80BsZig5pYqx1j%2Fiyydwhh3G0hIYnqsu3SJxpM888hQSylZkgNSurpcQb3sbgG0Zjxc4AxHmFP5LNCmuSWY%2BP2vYebwvMTZXIyjgZQ6XENnZkIcJQuw6wT3pjnxFBz3yVmHcUtUbGWB1OISw7PNNuyzS0jyUrI6h82r1RaZCvZk41xrKVaUq%2BIq7jBbuuTmWn3HZ0KSk3U2U7psCb6bDvgOz5zKjHfDvlA9l7w6Zd1XFuN8VS626%2FiuXl0oblEaCFdCFEEWSVhpsct1q3sI1djfDlazk8H5lLIZX0ecr87h%2BeTRZ6VkW9b0tMaZmXPSo5psVtqJPILvyN41Czj%2FiPmsRKwfIY0zAerodLKqUzMvGaQ4BYpKPKTsRf0x6Rg%2FicyBkprEkvRsa4Dp8%2BlCZ2bllKbl3L7J6a2pIVvbUoA7gX7IDaPhCKrLM4jy6wChxt2oYfwx0lR0qCiytfRNoQbcr9CtVu6xjke1oulWqdSq1SmqlV56YnZ6ccL0zMzDpcdeWfhKUdzFvUkQFCETWHdCwgIwhCAlKjEuoxPpEQ0wEIRNsO2IwCER0%2BeGnzwEpIEQBtExES6TACbxAi8IiBeAp22tENO0Vbb2hbe0BTtDlExTvzhp88BCETWHdCw7oCA5GJRzMTDkYlHOAjCJrCFhASwhCAimIRMjkYWEBLE0LCJgLQgdA8K6QaPid3kTMNI%2BJs%2FPFvyKnZiXzrx%2FOyJSJluYnwF2BIHRrGxO4i68LTixQMRBVtAmUhN%2BWotG%2F5IxvIyo0lvOLMCUfqcszOzK6mZRhxwJVNKSlZ0N38pR3sOZjzFzj8rW8%2Bj3PsuPzloTcI%2FrZVveaV8hH72Mc4p3HBhHKixIQaNVFAemeIJ%2BMfJGQyod03WLXSDbuJ5xcuJLK%2BuYkyGyvzQw2hVUkKYuqYZrLEugrXT5ozBeZUsDcJcQVb8gQPthHp3xmHHUQMZB7RMWqF2sOVFY70SqyPxQGBMZLWkDC1UHVN7ybm%2FyQSxsje8QjJRl7jIocUcNVMaQo%2FoRfzRfsV4InZldJXQcP1G6ZFCJxPia7JdA33A7bmA14ReEbAouAak3Tay1VsNVRMw7LBVPUZNwguA7iwF7mLD7QMYWv7Wqp%2BCLv8AigMbA80V23FobXo6vVMXk4Ixajnhiq%2FgjnzRdsLZV44xfXJLC9Hw5PLqVWmmZGTZWwpHSvOuBCRcgAC6rknYCA6MxiD4%2FQgo3V7WKKVnvV4mi%2F4hGGcUMw6xQMqKYmZDrCcLTcwmxuEl2oPFQ9N0CNoZz4WmMDZkzWBpuclpuZwzTafR5l6Wc1srfZlWwsoPO1zyO4NxGHcUuXeI3MuMm80ZeW8ZoVTw3MUNT0ugqErPS068tbLttkqUhYUm%2FlaV%2FamA5Zha4Me72EqxWS3S5xSRuSGVEWiApc%2FqIEk%2BAdhdtQsYC3G94li5t0uZ97DzDoT0idZ0Hyb7%2FJF7xlh2nSNfDOG1uTFPdYQ6FgE6Fm90k94%2FLAYirlEtrRlUnh6SewpVpyZ1pqku%2B14uwpJClN3Gqw9ZPqixGnzKPsjCh6oDxWPOPWzOvyzCm2wjS53pubxAyzgP2NXxRdsMYUreMK9T8LYepz89VarMtSUjKso1OPzDiwlCEjzk%2FEDBMOpszSVY3eUvyzTqdq9PijUW2ao9MreWOMmatIsTCJKSYnJdaxZcvMB0JS4hQ5bKUCORBjJM8KNOYdzZr9AqLaUTVLWxIvpSoEBxqXbQoAjYgEHeLElxTeW%2BNUi9lyUsD9%2FEEQ3XwPFDWSc8oJ1pUaiu17agGj80cPzitcuF%2FbBR%2BUx2%2FwADHvmR05%2B5bqnxlpVjHD031ZJPmQfxmN6qfydZemXKu0Z4hb%2FYxBw2UQPPE8vcuJOjX%2B574pObuGPVTf0Y0j90I0Z1Oo%2Bm3g3WKW3Xqil6UkZ3DuEpZmcanXKelp%2BarLxPRrUpQ1EMtl1KDe1l3IuARsjiAxMH80l4UVMMTL9QYeqdHmVHS90iR0kxJFXJYHWdaVzHXT3Ro7gwfrFGypm6vTQSKjWXGHCpVwA02kW8w3iy5z1TG1SzcoLeHGp53FEjUZaZo6GWulW06hwK1FNtOgEde%2BxSVXsIJU8dYny2zuxKzP03EKKBiRqm%2BIms1NH5y1lTarJl5tQuWjp%2BxvjYK2V1TcZ5lNnKxkjQTQMcy2HJtUogJl04arCJqYXqc8p9lF2%2Bon4YWlShbYxozG1YRU6%2FVFyVBpdGlajUJicVIU9oJlQtbhK%2BjG4CCrUU22sRba0eKls0KYxBS6fWZWoNUajS7lSqxoqW252altJ95aKgUDSpIUSocgodsB9hsosa4Zx1hByYlHpacpz6QjSpOpLza07hSVCxSQbW3B3j5BcemStLyUzyq%2BHKLKdBQ6jLorNITawTLPKVqaHmacC0J%2FchPdHV%2FCjnZUabgOkZeuopzb9OqLjUtOs6g%2FOSpbLiuqOqpKSpN1eoRpbwo1QTVcW5f1BVvGF0SebUssKSpaEzQtqWSQ4BqNgLabkHnAcETTdo8auceuZcBjyKgJNJhpMRhAQI29ESHnFUjlEhAgJIXtCEBPF3YnGJShKdX0a5p99xCN7rttcnbqj8ceOnU5yoOOfmhplhhJdfec2S2i9r%2BcnsA3MeiWw%2B%2FPUKYr0k8283Jr0zUuFWeZQbaHSntQSbFQ5HY2uLhblKLp6Um6u1Rh1Qi%2FPzRKQEDa6knkIIUUqset3CA6h8H1PU%2Bm521maqCgEownOqbB7XA43Yfj%2BKKM0qi4xczFzUzMxXixxmkYgcpzEtTZpRUUqc0MNoTqSlI6qrqOwAAsSYxbhEfLGZs%2B5%2F3O6n43EW%2BWLohOvJvNRggan8XU9YCttzPP8A0TAW1NSyMQpwjFOarYUoFssBKVAHmF3dNyOwiPU1WchUuJ14zzaCAnrXKblQB2Fndgdt%2ByNUmVdU10zSRYzokU9a13b8opLkZxDbzqykBidFPXvyePZ6PPAb2wpJZLYwreHsNYezXzIlK5XJlqRbYmW3ujMy5ZKG9aHe1ZABjxTk3k3TqhNSExnjmKw6w8thxpclOBTbiFaVJ2d5hQIse6NS0aoYhwXX5bFtDnEyFXwrU5WalpjSlZl5xDgU0oJUCFWUAbEER5ayiov1Gr1GrzSHJpqZMxPuafKdeUVE2HeVE7d8BvBiqZDLl0maz4zNDwulQErO6TY7KHvnIjs7DEzdRyFU24hzP3MpCvgnxKeKVb9o6TbaNFTcnOSS5tD60JVJtIeXuTdKu0d8SOtTjDr7DxSlUux4wsE%2FAPaIDdk5W8jOj%2FOvOXM3UooSETKJkayRYp6rn2x2v2RUxhJ5b4KxTUMKV3OPMBqp0WZXKTzHQTK0B1HYlYe8%2FdGiil3X0QUUqMv42Ck8kg3BB7wRHurtfr%2BNsQTWJsT1V6pVmtlU%2FNzj1tcws2BWqwAvsOQ7IDbaMYZCoSjXmTmy8rfUEqW2PNYl4xGoYoyTnTKewuaGYdNSlvTN%2ByaZmZKl3NlNll4WFrXBBNxsY0fN0qbk2HJ5ZQUDrW1dkTNsL74Drjhzq8sxmHJVXAmcOIqmilzEq1VZOeYmW2n5OYX0RUA84oagsoAFgbXIPMRtPwhswy5SsuHGnQVPCoqdCTfrAtg37jyjnjhAR%2FZpVVgAq6OkDfu8fTeNtcdSnBUMHILhKCioK0k7A9IiA5Tf%2BxL9BjrClM9DQqQ2ppKVok5YEjuKAR8kcouqSGlXHYY6to2sUKnTS3Eq%2FMkv8HknQm%2Fr5Rlsfz%2Fs98KW0Z2eX9crL0rTKtodZGt%2FR121cimFPptTxRXJWiYclelqE0SQNVm5dAHWccVyCEjck8rRUuwFpff09VkW53HafQCI9uH6gvDWXVSqNPmSzVcaPuU59AHWRSUBKjZXKzjmlJtY2BjZqmdlO2WhERGuUMTYjo1IQcNYCdW%2FLMKQZivLTZ%2BemUE6nGe1tkHZIO6gLnY2izYizyzTlsKzWHfZ0u0xV3iytsW6QDywRuD6DbzR4mA004EoNy2m4uLxZMXKb9iJ2clwAVNlOnV2kDcRkpr%2BLj8BTgRaT%2BMjNZ6%2FWfZKSlHpxBJmJNpaytSlFLh3URcmMNnPHaa%2BxUqDUH6fNML1sPyjhQtsjuIjZuaFA8XZw%2B9T0t6jh2RdUlItclKib%2BfzxrEvuaFtOIitVdVcRNU5y2dVMzFMZQv1WqrGYtCm68pDMtiujthVYlmmwhupS5%2FuxCU2CXUkgOgdUghYsbxg%2FwBkHSR7qRWHMLYqpuJWWUvBh0MzLKh1XpZwFLiCO26FEem3dFSoyMrTatO02WFpeVeU2zc3u3zTv6CIpnmvTEU7Fkn0hMvMqTz6Bd97dkYnLI6ojM6w2humzLn2zakxikkgKSm4itca2ajXDVmJf%2BMdSH%2Fbn8UXTEz5eqTRUvcSrA0%2FwOcW3Eab4mqo7n1R6cQkCsN6eXi7NvRpEas7V2ZZbJC8T01CiAlTyQbmw598VMwktoqTyW7W6VfI7c48uAlFNakFJNiHRY3j0Y%2FJVPFR5lxRPxxAwmZO0W1zyouMxyi3OeVASHaJCbRMTFJRMBVSbxVaUAY86OUTpNjAbfwTxOZ85fYcl8I4MzbxLSKNKFRlpKXmx0TGo3UEBSSUpuSdINrk2G8X0cZHE9qv7u%2BL7%2F8Aim%2F6uNFAm3OKiHSnZW4gN7jjJ4oP%2BvfF34S3%2FVxP9WXxRAaU57YsAvfeYaP%2FALcaJD6B2mIl9J7YDfH1a3FOk6hnrib0a2P6qMax5xPZ9ZmUT2tY7zTrdZpPSB5Um%2B4hLa1jySoISNVjuL8o1UXvN8sUi4rvgD5ubxTAvESdV7xBPMQG4eFfI2jZ%2FZv0rL7EGL5CgSU0sF0vzSWZmaSduilAoEOP9uj7UKPZGMZt5dJysx3VsFoxFR8QNyDyktVOkzaZiXmE6iBunyXBay0HyVAxmfCLlzTc2eITBuX1Xq1UpcpVJ0qVO0qY6CcYU22paVsu2PRrBSOsB3xhmZOF2cM44xJh6TmXppil1qekm3nQOkdS0%2B42Frt8IgAnvNzAYchuNh5JYjpWB81sHY1ryH1Uyg16RqM6JdGt0MNuguFCdtRCbm3baMNlaY87sAY7DynyqyiyLyVkOJHP%2FD4xPO4heU3gzChe6Nia0XvMzJPwL3IBuLdhgNlU7j4y%2BrGI8TP4zfK6YMxqViCgGToCWn5iiS7xUvxgoF3HQCLBd1bRwrmnWJDEeYGKMRUlJ8Qqlanp2VJa6O7Tr61o6nweqobdnKOp1celMq7vsZjjhkygqeFnCG10uXk0y82GuVm3yny7ctk%2BkRhnE7w%2F4Cw9hXDGfOQNRmZ%2FK7HWtqXlptRVM0OoJuVyTqjclPVWElW4KSkk7KIcsKSoG4SfijP8qMmqpm69UWKdjfBVAep3R60YjrTVPL%2BvVYs6%2FsgGk6rcri%2FMRhzshNNneXd%2BIxuzhDyKwrn7nPKZa43m6jJU%2BYps9PdNIpb6cKYb1JCekSU2JIvtuBAafx5hCdwFiifwfUahSp%2BYpzgQZulTiJuTfBSFBTTyOqoWNj2ggg7iMf5Rda7IpptWnae3p6OWfcaQUpCdQBtqsNhfnFtO0B66bvMI7ibfLHXXhHNsxMAtdjWXdFHyORyLSt5hsd6vyx114R%2F%2FAJUsGs%2Fa5f0UD7lyA49ULmIKFxFRQuYgYDffCvwvv8SCsTsLxtSKCxh%2BkTc20qYm2g%2BJpCEqbU4yohfipJst4bJjTeLMNVDCeIKlheqLk1zdNfUw6uTmUTDDhHw23UEpWg8woHeN%2BcFeUSc3MQ47ZbxrW8LzNAwbPVFqbpKkhT6SkpXLPBWy2Vi%2BpB2Mc%2BOSTpQkobCU6QrSgWG4vsOweaA8KGRG%2FwDgyzNwnkznhT8fY6qL1PpEtS6jLF9qUVMWedYKWgUJBJGq3m740lL059wApYUtRWLJ%2B2J5CO4JHAuSPBll5h3EecuBpXHmauK5NNQk6FOuhNPpTB3QXQdirvuDvsBteAyHBfGhlRXcu8PN5jppdNxHJyOK5Go0%2Bj4dLUj0s41ok3A02FIusAalAnrXvaPn1VGUpmCRyISnfvCbE%2BjaO0ZLjCyYzBmm8PcQPDDgIYYmfeXKnhFJl6hS0qNg8kAJUvRcklKr2BOk8jqHir4dnciceN0ql1f2cwvXpFFZwzWAQTO09ZsNdtulbJCVEABQKFbXsA596PujbGVfDjjjN7DruIsK17BMs21MLlTK1XEktJTRWkA%2FYnCFAG%2FVJ2Ma1XJupNkpJEbtyE4eMPZy4EzYxLXqxMUyby%2Fw6KxIhiWbdE051%2Bo5q3CbpSLpIIuTvygNF1enzdIqczSZ5CETEk%2B5LvJQ4lxAWhRSrStJKVpuDZQNiLER47GPXOMBg6Or1fe%2Bry22280ULWEBShETzgmAmsYWPdEw5RGAqtx75cWIjwNc7RcGBygM1o%2F9ph%2B%2BP44tlIWpvH2HHUeU3VZZz7lYP5IudF3o4v8AbGLC270OKKc7v73MBe3PlAXt%2Bc6SpTjn20y8r7pwk%2FHeM4y9xTQGazhqj42dLVHpVVlZmn1AIK10vQ8lZbI5lg2O3NBJttcDVbcw50i1%2FbKKvlj3iaSRp1G3faA%2FRhRq1SsQ0uWrdDn2J6QnGkvMTDCwpDiDyIIj3R8eeCbjfqWRFWlcC48nHp%2FAU86GyvdblJUeTiRzU39skb23FyLH69UirUyvUyVrNFn2J2QnmUTEtMMLC23W1C6VJUNiCDzhnmPZCEIBCEIBCEIBCEID4H8c3iR4jsxvFW3UrGJ53pdZ2Kitdyn1gxzq9vT2b%2FaW%2BXeOgON91Z4mMyUlRKUYnngnzXcVcfHHPz5%2FMDSe5u%2FymAzHDoHsYe%2FQ1b4zFzT5Qjw4bSBS%2BktyQ0PxmN08NOTVNzozEVR8QOPt0CiyvslVgwrS5Mo1hLUslXwekXso%2FapV2wGn0vMnWQ6g2523ibo77iPpzjOfyRydws0qt4UoEhKzikyNNolOpLb07VHz1US8uzYrcUokAqJsL3JjlDiuySkMu28MY4o2G04bZxN0kvVKCiY6dFLqKUdKEIWNtKkXBA2C0m20BqfBmS2amYFIVibBWBqrVqeh9coqZlUjSl1NtSbkjkFC%2Fpi%2Fo4Z%2BItbnRjLHEIPeSkD49Vo3RlDXsRYT4IsRYiwxWJimVKWxWppiaYtrbC32ErtcEbjaMKPEFnSo3OZ1Xv5g39GAwlzhj4ikBTjuVlfWhCFOLKgkpSlIuSet3An1R5cquILMDJym1aj4LTRlydbmG5ubRPyXTFTiEFCbHUOrYnqm%2B5jqzhVzEzBx5XMaS2MMVztVap%2BHlTMsl%2FRZpZUoEjSkcxtvHBdhtt3%2FAI4DNsys2cRZsztKnsSUugyK6NLOSbCKPTUSTa0LWFkrSjZSrjY9gjrXIffg%2FwD3tNr2n4nbRwpy5R3fkMgHhFaHZ7F1wH06Hrx82%2BE79X3f%2FVj%2BWp18I%2BUq9EuO8uNQySxA2nyU4jphP4KoQl3AF23HVUOduaSPyxLlkou5HYlUOXtgpm%2F%2BLqinH0ajY5M7WCz2CMaVRiRcbwvNgMyqGSrUjrEX35%2BeLd7kOPX9TicPvJ%2FfKR9KNmdTzREdGDewi6Gr1ZQY7T5VHI%2FwqPniLWUmL1LAep6kJ7SFJP5Y2lqbt5CYk1J%2F3EBrJWUmKU85VY9Q%2BeINZVV12yEodLvakNbfHeNnak%2F7iGpH%2B4gNYvZTYoaOlUsoHuOn6UUU5W4oWbCVI85sPyxtUFMVbJX1NlQGqk5S4t8YaQmWRdS0glbiUhO%2FMkmNvqmG1VQqbdRoU8oFy907JIvftF48Tov54gG7iA11P4QxRUZeWW3SXSWmQhWpaU33J7%2FPFsOWOLnTqMiEA9hWk%2FljbqGtoj0cBqZjJ7GDx%2BwMAed9H0oqIybxevlLsja%2B77Y%2FGqNqBtAN7RFXKA1a5kzi5tGstSqhe3VmGyfi1QTk5ipQSeiZGrld1v542ffzD4hEynbJ5D4hAakdyrxQ2dPioJ8ykn5QbRKnK3FpXoMkAfOtPzxtvpImL6gLXgNUsZR4temGkJalkkuJF3H0ISN%2BZJOwEbjmAluYeQHUKCSpIWk3SqwsCPMbbemPC24SeuiKql7bCA1XUMHYtqCmVewTyFNNBohS0X2J8%2Fnjxe5ZixzcyjbXpdEbfSo3ic8oDT4yoxV%2BotffE%2FPEE5WYlLoa6JFz26xb8cbdKF84ouAwGsPckxJbfovvqfnin7leIwT72nb92n542hCA1d7luJL%2BSi3pF%2FxxFeVOIrXT0Sj3FaR%2BWNnFdolLt9rwGtJLKzEZmWQsyjILrYK3JhASm6hdRN9gOZjcXslJqxC7NlwKlhMODWOSwAUgjzHa3mMWNwExBAIRpgMLq%2BCMV1BqVb9j2VKZl0tEiZRzBJva%2Fn%2BSLT7lWKlWLkvLt%2Bl9J%2FEY2TohotBdroZTYl7DLn%2FDI%2FLEwyoxD8JLPqeR88bFt%2B5T8ULfuU%2FFBWWvvcorRbcSFNhZILay%2B3pA7QRe9%2B60TOZWz4EvoS7e1pgl1o3Ormjrfa9h7Yz%2FAPgp%2BKH8FPxQQwBeV84ZiYLQe8XUlYlgtaA4FfA172t32jxLy0ryEadKVL%2B2DibRs3X5oipVhcQGs5DL6vtT0qpSGkhLza7qcSAAFAm5vtG0ZxwGbmtG6ekPKKF9rxLrINhAZPmH%2FwDDBRf%2FAPIKv%2F5cY7A4JFlXDXStXwWagPV42qOQcw0W4XaGv7bMJX%2F8tMdg8FobRwz0UIvfxKfUr98Zxd4%2BZ%2FCTquVj%2FqU%2Byp2MKnXV6PfDgNz9Euf397%2FSKjovgY3zjnvNh%2BaP8tEc6PC02%2BPtX3f9IqOi%2BBX%2FAJZZ4f8AcEwP84iO7ptlOA22Xix7Ya%2BHz%2FaafSvWdJUniyqenmnKp8j7yoxzox8KOjc41LPF1PJUbj3LXUpHmLKvykmOcmO2M%2BhtPBwS7fwwxX6Px8ws%2BLKXWKjNV0S1OfmETM20%2BhxpN0KsykH1jt9EYCvLbGK3DejvI%2Ff2H5Y250ixEpcMeoauTU6MrsXLCiaepJSCogjsETnKjGKUhaqaoJPIkc42kXFd5%2F39cUiq57fjghrFOVmKlc5Ep9KYnOVeJAm%2FQp1d2kxsjVbv%2BOJStfwSfjgNbLytxKPIYSfVaKT2WOKG06vFAfQY2Stb1%2BZ%2BOKep3vPxwGtk5bYsJIMiAANV9Q5RtSYpi6JQ6NSZh9l%2BYlqW2pZYcS4LLClBNwbarEXTzB2MeZPSfbxLZKNhp%2B2%2BOAt2M6XP1MVGWprInA9U%2FG2nGVAoW2phAvc25KBBHeIwJeAcUfCpik%2BlQjaF78omQbGCYaxTl1iI82W0%2Bsn8QioMtMSfaNfdRssqVe4cIiBWu27ioGTXCMscSLOkJaB8%2B0ToysxKXEtLDKVL8ne942Elz%2FtFROl8BXlqgZNcO5YYja5hs7kesRS9zfEitPRNIVq5b2jZ%2FjCidlm3niJc2gZNWOZcYoZOl2WaSe7WD%2BKNpGXVTabISzzjbjjEkgHolar7cj3HblFNXXv5ooq2NoGS243olTq%2FjsnIS5mFmqOvNqaIKFNrZb6wV6QR6Qe6MHRl5ipZt4gEjvLgjZMToRcQMmuxlhiopuiWaUT2awIj7lWMCvR4gNX74RshG0VQ5blAya39yLGO4MkAR3qAHx3iHuVYmShJdQ0kk6SNV7GNk9O52LiYLUrcm5ghrT3LcSdgb%2BWKCstcTp5stj0rEbT6Vz7b5YpPqcUPKgNXoy1xIpxIUGEAkAqLnk%2BeNtzLYlUyiFuIeLcshd2lBXVKiQNuSrc08xcXi3emJ%2B7T%2B%2B6vb6YCwZi0aoVWffap7XjKUTsy6hxvdCm1qSpBB77bW7LRhntDxKvf2OWn07Rs8LPdFRHSKNypVvTBMNZDLnEvwpdKN7bq7YqDLXEausENlI5m52jZe94n68FmtRlliJSAUlkqPZc7RTOW2IU%2BUpselKo2dpP25iax%2B3V%2Fv64KNWry8riXNJLZ2%2B1VFJeAK8D1Uo%2BIxtjSftzE%2FwDDMBrCl5f11uqSL0z0aGEzLSnHLE6EhQJNu2wvG0%2Bv0DTaz1kpOrt2KyR6NrfHEoWoCwWbRJe0BnFGOjILOxwK0%2FnDTkHzg1KX2%2BSNl%2BDTebPt8lRMWcM1SXCzp5pCnRqv6TaNZ0waeHzOlz%2FuWnJ%2F%2FiTEbD8Gekpq%2BPXyleyaSgG3V%2BzOEi%2FfsI8Xp7%2BpLX%2Fb%2FNS6uET%2BPz%2FrlYZxagjiHxjdQILkqRb%2B8JjG8lf%2BV%2FA21%2F7IZH%2FSRkPFgdXEHjI%2FazEuj4mExYsj1aM4sCq%2F%2FaCT%2Fnxnmf8A1imf8n%2FgxWH4V8iP3o9rpfwgkw1LYOwGVtJWfbsyLqANkhkFVu4naOfc62ynOLGSVI0%2Fnw%2Ft5rxvnwiN%2FaXgDu9urf8A9um8aHzrN84MXn%2FvV38caPwefqSif3qvajE%2F0mpgGM2XZrDLcrJyzsw6vp2tDSSpQUS0UkgdhsRfzRqp3AOKVuKCaJN%2BtNo3Drhr80e7abTyMusXqPWpLqB3qt88elGWGJlC%2FiTpPmbv%2BWNsa%2FNENd4DVQyzxEb3lHxbn7wdvlib3L8QJ%2ByNvJ%2Fxcn8sbT37z8cUnFkG1z8cFGr1ZaVxPlIcH%2BCt%2BWKRy5r9r9Ht6N%2FxxtBRvEsBq85eVodiz6ERnWBqRO0LDdQkZ1JHjE4ypsFQCttyQkG9trXi7QCLHUkJB79oDyYyYmanh2VlZNCnnF%2BMy620DrNqKm1pWruSoagD3pMa3VgLEANjJqA7yR88bW8tzpF9b7aJNHngNYoy2xAu56NPxw9zHEyj70ylX8ID8sbO0eeGi0BrI5Y4oSjUZdHoCkk%2FjiojLKvqFi2lKu4lP47xsuEBrJzLWvI5Fs%2BkgfliX3N8Qfqbf3YjZ5So8jEujzwGs28tq4r7JZPoWg%2FljO8G0uYoeHnqfOOtBxTos3qGoi5VrHZbs9MXMN23ETnVa20BbMaSExXaDT6dSAH3kpfS8i%2Bkte%2FpUgkq2UFJ1WtysQeyNenL3ERXpWwlJ860n8sbOWN94BAgNajLevfatfdj54qjLatrFg43cd6h88bHhAa39zKufqjP3Y%2BeJhljWTzmWR5tQ%2BeNkDlCA1uvLGsD%2B6Wvuh88UlZaVn9WaP8ADEbKWDeIWMBrQZZ1s8i199QI2FhanO0PCgpU2814yZpI6IL1HSlKiXbjbSSvSN73B7I9aEbXgdoDyYypUxiKiyMpTX0OOeLFuYQ4ro%2BhcS%2BpQsT5QUkg3HnEYD7mOItdvzN9%2FT88bF%2FTLxWgNeIyqryt%2BmlEnzviPQMpK2Eh1x%2BWKCbdV9BPxRn0Ttc4DBEZPVk3vMyh1eT%2BaUC3pioMnKgpoKM7LoWk2UPGEnV6I2COUIDXL%2BUFQSQhmaQu%2FL31OxjyLyjruvSh1j0lwWjZyfK7OR5fkioEgG4Q4k95O0Bq0ZO4iI1dNL27y6BGf4Uos3RKGmXnnmy8ghoIQbnSkeV3WJNh6IvAWv4bioprXvsTAbL4bwF5z4fSsXQozOvzDxZ4xh3g9GC7ny278FnD1TUre2xSkflEZjw1ArzloVrkjxo2Bte0q7tGGeD1CznkhQJAGHakVWF7iyPy2jzWl9UU4NeKv3Z9joYfGd4o9LbfHsB7r2H%2B%2FwBqcvf0dMqOZ3BvHS%2FHstXu0Uhk8m8KSvPnqL67%2FijmpYBMV0P%2FAFHdv4ffLHfPl6vSoQtc3iKx3QQO%2BPTtNmuUWaNVyZxk1j%2BhUej1GoybDjMsipyynkNqcsCtsJIKXbApSRc9Y25x2ArEmPsEcLuYWK%2BKDEbs8%2FmIlxFBw3O2W5KF5lQbbSg%2BR1ih3TzbDYJIJjlHILHeCctMzZHGeP8ADb9dptOYfcl5ZlCFqbnbDoHtKzpIQdR37SD2RuHOnPvhrzsp1ZqWIsB42msUvUaYkKLOPz4TL059SeotLSV6QNfWUbFSrWPZAbF4TsvpTImXwdWcayzrmYObk0il0mWbSQqk0pDKnnHVqt1VrCUqVyNlJT3xkeQSZ0cU%2FEv0yFNTL7ksphJunpCtS9DiSewqA37wY0Jl%2FwAb%2BbVExHh1OYNYTWsM01DcvUZOVp7CJmYbQz0aFIcO4WFBBO4uLiMhwfxlUWm5u5i5g4ro9an5DE1Hl6HQG5NllqYkJRhby20PWUAohTpOsEqPqgNn4GlM08rshsyWuLzG0pPU6fp7jchLzdUbnHzqlloWi6R1gp0tKQnchSb7RjfCRgmm5N0PBWN8dST%2FALes2ptqi4fkyghdOphRqemln4GsJCjex0qQBzMcTPF6clEMVaZfnVhsJUt%2BYcdIJ8ojWTa5jobLrjZzew5VaBLYuqcrWMNUstS05LNU1lM49JoRpCEOnkoAJ6219O8Bs7Deb2A8n%2BN7NmezJnvYqVxFaTlKvMIVoYcSllZ1qAKg24ApHSC4CkC%2B0X2by5zvw3g3FlXyL4gafmthmtyTpqNFxIE1B99goUXQwtK9Gst%2FA6urSCBqEaoY4vKZMZ34lx3i7A8riTBNfp7WHmqXNSTKpyRpjKlqaUlSrgu3de12IulQsbpEenBfEBw3ZAUrEMxw94KxaK7iCXEtrrUwDLS4TctG1%2BtoJvyubWJtAcqthoMshgqLYbSEFRudNtr33vbviRyK7jmq5JClrupagLXUoklXmubm3nigsXgKcIjYxCAgTaIXMTRDSIADeAJJiIHdEUp60BccPYfq%2BJ67TMM4fpzs9VKxNtSUnLNi6nXXFWAHx3PmBjNa1kDmVIY%2FxXlzQaC7iupYOdQ3Un8PIVOSydaEqFlgDrAqKSki4Uki0ZBwhYnw5g7iWwDXcVvtS9OTPOSnjThsmUffaU0y8SdhpcUnc7bx1rwl16m5eSWNMgsbTQpeZGF8Q1StVkurIXVZFwh5FQQ6PLQhtQuL3Skg23MBwzKZSYuqGWVfzVpzDb9LwpWE0WvSh1Inqc6pKdLrrCgClrUoIKuw32sCRiJlFlJUllZCfLKUqIHp7BHa%2BIcb4SxTNcTmelFWlWBMQYVkcEyc4tPRtYjrwSkF1rtWpIHlWuRuecY74P3HVcGPJrJl6nUaaw7WJWfrc2uYkUuTXTNSyW9AcNwW1AglJBsRtzMByOWrqCAVXI2CRcxBxkpKhdSVJAugpII89jHXPDpISWWeQrmclBwLTMU48xhjc4Iw%2FLVFSQzKnpi2hAKtkgkElXOwAuBGD8XC88ncV4Zaz3wrhaiTyJKYZpC6ClAYfZVMISsOuBRJUhekb2ABJ7TAaQwpg%2FEmOMQSeFcJ0p%2Bp1eoKUmVlGACt0pSVEC%2B2wST6ouWPsrcf5WVGUpWYWF52hzU%2FLeOSjcyke%2Fs30laSCQbHY9ojqLJXhSzvykzQw3mS2%2FgipMUmcDc3Lpr6NLsu%2B2pt1KHALdIEr1Ab3KbdsZrxU8PGaOemYErXsMTeE26Dh6lGnSL71ZAdmStzpVOPIsUskKJQN9wAbwHz%2FWLRLGR47wbVsvsX1XBNedkXahSHgw%2B5IzAmJdSihKrocTsoWUPQbjsjH4CiVHVaJ4gpPbBJ7ICMIQgJYQhABziaJQDE0BLY90LHuiaIgXgIAWhE9okgETiJbbXhcwJdDcLyVJw1iFZISDOI3I%2F7MCNT5SyFLm%2BI3E79Wp0tOGkS1an5dEwjWhEygFLblu0pKtSe5QB7I25wtkLwpiBKlm4qKQTe1rtp%2BeNO5b1GjYd4jMTyWK65L0hmqirUZufmyUsMvumzSnVfAbJG6zsOZ2EeauMxOKXiZ83ufYdKM%2BJuG0Rr2fyy2Q2iVY5N6ur8Lt9MXySxFWpOTcYoc1MSSnvswYdLYXYWBIGxNu%2BLr7TcLIUEPZz5VkqBt%2FZWxzHP1eeIyeEMPt7pzpyrIVqSAnFjFwRvzO0ei%2BMpnlfI%2Fia%2FBPMscjV8YlCm2cTVNrR1j7%2BQCe4jtiZvEGYTn2TFFX6v%2FbEARneXCMmqhiisYKxvnXhSl1anS7cy2ZWbEzLTDarH3uaSOiUsBQ1N3uPUY2ezhrhnSUpez4w0ogb2m2xq%2BWJ4UKcGWgma5jdQ6%2BLKt6pgx6UVvFQ6rmKajY8x0%2Bx9IAjYubLnDphun0in4ezvw6%2FV67NeKyrKntTKOQLjzyAUsNgm2pexPoMYs3hPDYGp%2FPXKdJ2uBipk%2Bns3ic4OBV4FubruMlm7eM6x3WD9tviip7I45uFDGdbSRyImOXyRcZap5WYCrlImMc51YEcos7Otykw%2FRqkKlMMFQJBLLQKg3t1nDsnbneN8zcrwoua2%2FdkwytCOrrFVbtvyNwdxDhR4TgVeBzA%2FirMmSWeixxWLBX6qDbuHkxY5%2FMbMpOpK8Y1FQOxVdIUPQoAEeqOm8UUHhTlqDPVZ3PTDcmzKS63ypM4l8kAXsltF1rJtYBIJJMc%2FyWXLeLacxXMPZk5cO0ydR0so5M4pl5Z5SCTstl0pW2ocilQBBBhwoRwavA1o6p%2BYdXMPuqddcUVrWs3UpR5kk7kxdqXi3GdEpUxQaPiWoSlLm30zL0ih0mXW8OTnRqunV5wLxnRyHxE4QWsdZcOJT2oxdJberXvFRnILGrW%2FthwS%2FwBW%2FUxZIn0fDhnEqVVU0TlVOSy0vHOPW29LeIZnSpOhaQy11knmD1YuIrWL5pZUKmlBOm%2F5kZO45HdHONkZOZfZZ1qdr%2BGMb5p4apmIcPOoE3TEz7bikoULhfSA9GvnuEKUQTY2jbcrlBkhLj%2FlQoi0JIJHjzFvT5USjh057XNyKlic6PGanLuaBZI9jZewH3EexrENZlEKYaFNQUiylKpksSR9xG1M1MH5c0mao9AwHjigVfE1XUtUnRTVWGnpllIJWtClKCDYJOylAmxteMMGUmY76Er9rssu56oRWZMm3n982gtnmxCZq1ZdUktKpYCQdnKTLq%2Fo7RZJ6t4gQoKXScMP6RbUuhMEk9523MbTw%2FlymnYppVFzVq9KwbK1p8ytOmKjUZfTOTG1mWylZGo6gLG3MDntG0KlwyYOmVluWzDpKSobJW6i4I9BgapcmP43n5TV0mE8HuBXPVQGrj0ERLJZo1KjzzFaoeE8IUmrSrgelqjIUkMzEu6PJcbVqISoXNjbtMb9xrwsyFBw3UsSIzKw2GKayX3TMzrcui3IDWs6QTyF40VMZK5uTVpqUysxO%2FLODW261IdIlaDuFpUg2UgjcKFwRyhnEbZMp5IYPVqlUq9Vput1mednJ6feXMTMw8oqW64o3UpRPMkmLPmGHk5RVubk6pNyjkrUpBDzTSrNzbK%2Bk97cHPqqCVDe3O47s%2FVk3m6hYQrK7FQvexFLcI%2BSMQzjw3ivCGUdXlMVYYqdG9kqnT0y5qMoqXLqkBwqCNXlaQbm3K4is1U8krZTG1v7gdQljJKaU4oJStmouKUewdAsXjiCoEGRQpPIpuI7a4LZkJyOnEi3Vlaiybf3gxxJO%2F2ua%2FeR0Ko%2FJ9l6Zcm6T%2Fb7efQw9zZwmPRIupZmmZg80rBI80eVw2XEULjRdV9QfBt4spNWwzjHLSaQ0ubk32sRSSF2PTSrqQ28Ug79RaU38yo6QzPwAavhGrqwc8qi14yLwZm5GTQ49NWTfxRwnrdC7YIXpIVY7doPyDyTzfr%2BVWMqLjHDs94tVKJMdLLKcJ6F5tQ0uyr4HlMupJSR2Gx7I%2BvmS%2BemXufOHvZrA070NRYSFVKgzDg8dp6%2B24%2FTWvtXUXSRa9jtAcUZiZCZz0GvsNO5b1Co4fZZamG5vD6fGmmkLbStbDaiAorbUSnSpIG1r2Memi5Y4vyjzMw9iqpLencNz8uH5Gel5JTa5uXeB1Sz0u91mn0qFltrG1jYkG8fQwuutnUlZEW%2BuYbpmMqe5R600t1Dx1JcHWcbX2LSe8XgLRlZgvL2j4XkE4Tw9T2GUNrQ10SNYQhStRS2TuEEm%2Bns5dgj5u%2BEczAp%2BLeIGaoVJUhUtgyms0NxaL28cuXJgdx0qUlNx9qe6N8ZtcTMrwoyGJcE4RrrFZxxNOuystIpPSylGHLx1xQOzikm6WUnytzYDf5r1aszVTmXJuamnn3nFqcdceUVLcWo3UpRPMkkkmAt7uyucUlG5g4u6rxId4CaES3PfC574CY7CJecQ1eeIwCEIQF9ouEqliGgVar0h%2BWddoamXpin9KBNPMLJSXmm%2BbiUGwXa5SFAna5EMJUd%2BpvVR9it06nGmUuYnlibmwwZxtOkLl2b7OOqCiQ38IJPdFmYfflZhE1LPuMvNG6HG1FKk%2BgiIa4CWHngd4QG7eFD%2FlEnf%2FK1f6RMe6oTipXJLMlSSQV4ipKwQd9pucVHi4Utsf1JX2tKJ%2FziYuWJqb0WUOK5ZtJJnK7h4bm1itM64T8ZgOfl1KYGpKXHAnpw8LHk5c9b0784leqk2sODplkPOB5dzzc%2B285i5ChTLqPGUtp6JyeTJCx5OEm3q25xFeHnlIfWW0pDU%2BmnrBPkrPJXoMBa3apNvF4OPuKD6gtwFV9Sh8I%2BfzxB6ozb5WuYmHHVPABwqUevblfvtt8UXGbw49LJnXlFBTKTaZVWlXae0eaJZrDsxKio9IttZp60IVoVfUV2tb44C3qqU0vpNb7h6VOhd1X1J7AfREy6lNuKW4t5awtvo1AqvdPdHrm6BMyi59CnEKMghta9JvqCuVvjiD1AmJYzKHSgiXYTMEhXMK5AeeA8QqMylWsOKv0fRX1E9T7X0RDx2a979%2BV70jQjrbpT3DzR7HKI82t1JWg9FLeNKIVtpva3piKKFMuPIYTpKlywmR1ttN7W9MBUknnVyM7qecV7wDYruOfnil0623Oj1q7PhR710edp1Nm3Xi2lDkuEghVyTrG0eUyTy3tZA0m0B0lwXqQvFdcK1ErLNK0edXjyb%2FJG1uOhwmpYST2aagR92kRqjgxZLWMKooclO0ZCvQZzf8UbQ459q1hMc9TM8r0e%2BpEBy4%2Bo9Er0GOspRzxeRkUrIKPEpcqty%2Bxp2Hnjk1wXZdT2gGOu6SwhctTFv2WrxJhVtPP3tIO3dGWx%2FPY7b8xks6pz2JmCBpsyoIIF%2Fg7R7JlL6cOYaSmXS42qUQtQdcKEKsSFC4BI5dgMeCWqCW20ScwgKbuOfLTa1j5oucgy5V8Ky7KwoO4anHG3kAXvLOHZf71KrX8xjaj86JaW2mfseOfVRENqWxTZZheoKSlM04SRY3uSm17xj1cm6HP0t%2BQXRmU9IypAUxMrUpCu8AjeMh6NcpN%2BMNTTgSlJb0BptYNze%2FX5R4%2FZSfbbdDEs270l9ww0Cmx3F7X7Ysjhed58S1yTdZpbU0KfMqkaczLjoZnWC0LlIUUjZYuQR2Rg9TfwxNOhcph5guAEqQZxwBZ7N7bdsZPNKq63Qy3TnluHcJZlmySLXNgLk7R5JjEdKmcOVSnTtKRNz0%2BmX9jJ5IQ2KepDmpxSkgXcK0XRa4te8DhZRnm1FidNPW025JUd6lqWkh5lb%2FTILgVspCiAQCOzsipX1KVWXFqBBWhtRB7D0YjOaLgh%2FHuL6JgyUeQ2JyZ6aaeULiVlUdZ1237lAUfVGJV%2BSdm8Q1SbkUuPSipt5UspQsfFwopaJ8%2BgJjBP505cjPTXHBjPlY9UVr9jJjW55Tald%2B%2Ff5oxSVcIUlKVW88ZTU2XGZGaU4SCW1DSewRjEhLuOdRH2sROtkolrqry3S1Wsvn9LmCCO3cRDEw01kAdkuyP5Aj21RHQVSuhwW0vEqHqBjz4sSRV21XuFyrC0nvBQN4152s8MkwKfz2kj9q4FeqKmM3Okmf4So8uCwlE%2FLqcXYahE%2BK%2F0SrR9sYgYnMKMeBXlGPW%2BuPGpW8BTVEsTKiWAinnE6ecSJ5xNAVRyhEtzC574CfXDXEljCxgJriFx3xLCAmuIXHfEsIDaXDrnC9kPm9hzNZmhtVk0J5bi5Fb5Z6dKkKQQFgHSoFQIuLbW7Y6HqXF7ws1yozlXq%2FAlQJmfn31zMy%2BrEKgp51aipa1WA3JN9h2xxOlaknYx6ETCxzMB2Qvie4R3mVAcBFH1aT1U4kcA%2BTnG5896lTK6rhbzfwV7UsPYCm6c9T5D20sGcoVHmtCiJacAPWFgttJJB1IueRj5stTihyJjorh04rDldhurZSZm4MlcwMqsRL6adw9NrCVycyTcvyi1bIJNlFNx1hqSUkm4dQDMeUmp2XZfxFwVOJm56bkJhxyjO6ZdLQVZxZPwHNICTy66dzFpwTWsFZQ8FCns68upDF%2BH8X5hT87RsPtTa5SXeZQpX5qllqsvoBoKkX8pK035xraVxr4NbDE2cT0fLfM7EM4kpcZoFXmUpkWlDcIKj5SQeQJVGmOIjiUxfxCYqarlbZZptMprPilGo8oAmWp0tfyUDtUQBc9tuwQG3lcR3BU2TbgWYItt%2FZK4Tf7qL7gTjX4WcrcQt4xy%2B4PnqBXpeXfl2JyXxBrKUOoKVJIWSCCD3RxC68pZuSTFPpD3%2FLAeyvzzdSqU5PstqbTMOqcAVz3N94tkTOOd8U9UBcKSm84wkfqiR8ojrrwlFkZ14YZHkt4Eoyf5CvnjkeiG1Qlge11P84D8sdceEvGjPikNfqOCqKn%2FADSoDj8kX5xC474kUbGIajAb%2FwCEfiOoPDji7EdYxHgl%2FE1OxJQnKK%2FLMTiZdaEqUCo3VsQU6kkbHe4jZLefvAwyhKGeCuaATyvia5%2BMuG8ccg%2BeKgc7oDseXz84GnpmWTM8HE3KMJmmFuTScSkmXAcB6SwXuE8yO21o3dntJz1O41KjV5tzLCbpeIsCSk%2FQ3sxg4KRNyzYSCiVWkFKZgW%2B4UT54%2BabD2k32O1iDyIjq7Kviry1xNlbT8g%2BLTAM3jLC9DV%2FY7XqcsJrFGb7Gkk2LiU2ABBPVACkqsCA2viyYo9ZwRW2F4T4QdE3hd6raadOvNzoKmz%2BZ2SEXE2k20i4GojeLrmHiTKXKjh8yIwPxG5OTWOq3KYU8clmBVBJzFLbcVshfWSVEpKRbs0co1nQMa%2BDyyemTizCOF8cZjYhlHvGaZLYjYTLysu6N0lY0IC9JANyCdo50zrzqxdnZjifxzjCdDs7Nq0IbRs3Lsp8hpsdiEjYD0ntgN7DPDgVQLHg6rAFrdXE5JP8AnIuMnxYcMGDMDY7wzlTw84jwvP44oi6NMTSqwiZbCbkoKkqWTZKj2b2JjjBx1SjubxDplQFWdcS86VAdXUT8ZjxnnFRa7xTgIW3vEwHbAc4mAvACLRMlJhFRA2gJm0EEbCLlLoJA2EW5POLlKHaAy%2BjbUb1mLG0hCsUU%2FWjUA8CU2vfzReqSvTSCP3RjyUGWVOY4o8qhGpbk6wlIHMnWIiqcomUxGc5NwZVcOjs3My9azKZnZemrQXUU%2BUKUzT6T5JKldVsec3PmjfchR8AUBoYfpGV9CTT0gqWZ5C5lV%2BxLiyoXJ25AbxkDsoKmuY8XxC2iWDAeenpmZQw3IEKDZU8tY0tjX1Qk877dpijS8vceTdaEgujzMtNOKDU1OaChlyVHN9K0ktugp5WJBNo6FnY2dnTnXrnzufaW9pXVNNOqPBHt8PWxOrZX5OYn6ROIMuV0ptwECbw1Mlh9i%2FwugcKm3Ld103747r4GqHQ8G5GyuBqLj2XxQ1SJ%2Ba6J5IU28wy44VobdZX1mVi5BTyvcgkERxbVZzAFVRMMyTVew%2FPyU0WkSFTWXfGkJJSXEKACmV%2FCLbg025Kj3ZS5qT%2BUuO5LFlCUqZZJDM8wkKHjUre6kX5FQ5pvyIi15unA%2BblPgRdr3FrrirONX9a31LhHmp1QlKtT5aqSDwdlpxlD7KxyUhSQUn1giPTHOdAhCEAhCEAhCEB8B%2BOYFHEzmXsdsSTahv23Pzxz48L09gb7IIG%2FZf8A%2FMdCcdAB4m8y7gW9sc0R6jvHPTw009jYX0C3qJv%2BSAzrD6wmnKQPJKWvjsY25kFnXNZG4sqdfRQfZmUrFNFPmpQP9CQpDmtp1KrEXSbgi24UY09h5V5ED%2Fs2zG28icG5XYvxkpWcOP6NhzDlMaRNLk6hOiVXWXC5YSzbh5IFruEG%2BkgDneA287xk5dVnF9FzDq%2BRkxM4gw8w7LUupeyyVKlErvq0IsE3upVlHcX2tGD5%2FcS7meNFomHJfCa6LKUqfcqDqnZkPLmHCjQjcAaQAVbdpIjKs0ct8vMx8eVPGMvxH5KYdkH0MytPplMm0oQxKso0N60g26QjyiOZjVOYWWWE8E0iSquHc8sFY1mZmcTLO06jvlcwygpJLxT2tiwBPeRAbXwhNOS%2FABjUteWjFWsfhLAjm%2F2w1bXbxj%2BTHSmCZRmc4EsYSj7hQhzFRaWRz2fYUPxRon2pUvpblyZV5wsW%2BK0B0BwEVyanMc5gSU84lbSsIly2mxuHiPyxyf3ev8cdgcDmG5GnYxx1NSq1FftV6M6lX2Lqj%2BSOP%2B71%2FjgIR3ZkLdXCEAL3NPrvLu0OxwnHdmQqgeEMJv0einV1JPfZLv44%2Bb%2FCbrw%2B7x%2Fmx%2FLU6%2BEfKV%2Bhx%2FlgjRkXiZP%2FAH%2FTD%2F6cx5dZj3ZaAnJLE7d9k1qmKt3kS5jxpRfnH0WjY5M7UmqJoqCXQUkqcQn0mKnii09o%2FwB%2BXxxdCiBcjaGmw9ERWtCL9dN7wQpC79ZO3KAQhqa%2FVUfvr7efeIgtXv0ggIgC%2B8V1t2CSna8Uullx%2Bnt%2FJFRMzLu6dLyF7X2N9oCCW7xUQjeIFbLeu7yP4JB27OUVWxvATWAHKJdogtaV6ih5AT278okStvtcBB2Ft4CJtEhBvFRK2vK6RF087c7RQcmGkLstwb9bTeAqaPPFJznaCJlgm%2FTJ52t54jdrV9kTv64CQRFaSOW0RPR32dRFRZlggEPC%2FpgKSEKVpIPM2j0lG14otvskhIdTsbc%2B2PUsdSAopAvFWKetlvy3h5Xnv54j4ywOcwkekQEx3ii4gRVL7IOkzCL91opLfl7q9%2FTdHlbcvTAUVoiWxifxmVOrU%2BgW88UzNSX65HxwEhHYYl0b3iXx2UuodOjaJi7LpTqU8ACL7jsgI2ES6REPGZcjaYQRyv2fHFRaUgJINyTaAlA23HyxKoHu39MTpKB2n4jEqlI5XPxGAglCu%2F8ALE4R2m8SpWyOax6wRFQOsDbUm48xgFmxzh73ENuzUr%2BCeXfyiazaE6tSwOy6O2AkLaVHa0SONkdu0VyoEXKFE%2BZBiiXkk23H8EwEh5cxEiBvFcoWoGyVEc%2FIMU27KNxvCBlOYgA4WsOgjf3QVG%2FmNOP%2B%2FwAcdf8ABmFDhooZKbapGfI848dXvHIOZmscMGHEnmnHqwr0%2Bx5%2FJHX3Bm4V8NNDB5NyE6geqcVHzL4Sv0Ox%2FwBSn2VO1hUa6vR74cCOfoyY%2FwDEvf6RUdHcCiAc4Kmfhe19%2B3qcbvHOB%2FRLv9%2Bd%2FwBIqOj%2BBf8A5Y6h%2FwDu%2FM%2F6REd3TX9QW3oj2w1MP%2FSafSvWcQWri9mgpCbHK10JI7uhXv8AHcRzgx2x0lm6NXFxNjWd8rnxpItp97VyPbfnHNrHbG3odrwS7z%2B7DHf%2FAJer0qhMSLB7IiXmkmyiIlW80Rs4kesR6VqJIliVyblD5U0ym2ygpQA%2BOJenl7lPjbVwQkWWm1%2BzaAiRC1uyJVPsKSSHm%2Brz64HKJRNSqlAGZaHmKwICZSL7xJaJula6nv6Osnq9cG%2FzxL0sta%2FjbH3Y%2BOAWPdEjo6h2idEzLFRT4y16QsRUt0mlbelRG2xuIDyoippMT2aQtSFlCVemIOOs8ukR91ygmEvVBtsb%2BeIOJ7OXbzvEuu5uHm7J7iIn1sp3W6BbbdUEJACYlHMxVLzB2DqD64i2lnUVXuOzeCFMDUbd0VU3O0QWptJuSIlDjI63SpglUSmxNwCPTEq7KuEpt6oih1kmwWm9%2BRMRQkOq5JPoMBRS3vFUaUjlALYQtSFPNgp5gmxgHGCAS8LWPM7QXTBJWbpN4m0KHMesc4mbUwRtMII9MFPMJ5uo9JO0FEmjeKg2iXxmW1%2FZEfJEVvMIHXcTvuDcQEqygm3yXiVTaTuFn0XiXp2SdnE%2BmJytBTspJ894CkpFoijlaIlxm%2F2ZPk98VENoDaXOqpKoCmlsXvb%2BVFVOw2iXWzbrOo1dwPL0jsiOtrsdR61QTCbkLxOTbSL8%2FNFNC2LX6Vr1KidTrIt76jfziCEdhfmbQTpty5RJ0jVjZ1G%2F7qCXm9P2dG%2B%2FlCAqX1dkR3HOJm9ITzHrIiZsIUTZQ%2BMQEg3PUPqhocWuwTtFQp6NQItcx6G203uvtgMtk29PDjnQ6oWKaZS0j11Jj5o2T4NOdeUccUoIa6HxulzZVp6%2Bu7iAL%2Fa2vt33jAEqA4as50gdY0%2Bk39Hsiz%2BURnPgzLip46JbVpU5Sk6rbX1Om1%2B%2B19o8Vp7qwS1nz0%2Fz0uphHy%2BX9crBeK6%2F1QWM7%2Frli33hMWLJS5zhwEkduIJTf0LvF84phr4gsZDumWEfEyiLTkmkozmwEG0g6MQydz%2FD5xmqnLReP9H%2FAIMVhqvcT%2B9Hth0P4RFBOFMvFjkMaJSr1sot%2BIxobOg2zexcEbpFUese8XjfPhEFqGEcvkAXBxsg277MIt%2BONEZ3NlvNrFBULFVRdUdrdpjS%2BDnXgVE%2FvVe0xL9Jq%2FrkYXEkRcKUKBW4EBQtvBJZO5mEajsATYmPeNNCIp5xIotnYzDYvsLrHP44ioJZTdxxKB3k8vP5oCeKahcxBuYZdHvcy0r0KvEXC00TrdSD2jz3sYMZ0XmiUt2PKKqSgjSp9KV7kpPaBv8AJEpflQnUZhNu%2FVBKTRaIaEwM3KBzolTKUrvbSSLxOgtuglt1CrdxvaAp6PPEbRFam2k3dIbA56jYekxTDrA64fQQfPtAVAIjFJU1LItd0b8rdsFPtDSpSyEqBUICrCKfTtbWWN%2BXPeHTtj4XyGAqRLqSOyCHgtKlautcDSBva3dziVTjajr6RIA5g7fHAT6x3RC5vE7aml%2FBP3JiLakuuWuLjstuRyvvAUVo66rRCxj0OIsCpOpQB65SkmwiRtrpN0BxWruSTv3QEiU3ifo4qplnyNKGJknv6JW3yRP4vMH%2B5Jg%2BboF%2FNAefR54WMenxWZuUJkJ0r0lekSyzdPeLCIGSn%2F2NnvwZz5oDzLR2xJccrR7RJTihqVTpzbbeXX3eiKS5Cd1WTTJ25vYeLOG%2Fo2gKSPtBFM849aZCoakp9jZ4lQuD4uvcd3KJH5WYl3QmblXpcrTdKXmlIUR2EBXZAea294mBj1MU2cmQsysq%2B%2F0fldE0pdr8uQip7CVUE%2FnVP6U81eKrsPkgPLFaXRqVfsj0ewta1dH7DT9xz%2FMy9vTtFaXodeClJTRp8kcx4ssfkgKWnzxDT54uTWG8TPKKWsPVJZHMJlVnn6oqowli1zZOF6pzt%2BhHOfxQFn0XP%2BqKlrI%2F1R7zhzEaVqQrD9UBRfV%2BZF9W3ftEU4fr60gpolSN%2BVpZe%2FyQFrJX3xLFzOHcRaiE4eqirG20m4d%2FijxPyM%2FKLDU7IzEq4eSH2lNqt32UBAbK4Z0g5xUdRF9KJq3m%2FMzsYd4PRIVnas33Thmom3fugfljMeGfSM46Vvb3ibudN%2F7nctt6Yw%2FweWkZ1Om11DDVR9Q97H5Y8tpl%2BpLzH7sujh36RT6W1uPpV86qX5sMyo%2Fzq45pWo3jpPj5srOqmJ7WcNyoPoLq45rXzjLohTlgl2jze%2BWC%2BT%2BPq9KWEIznL7JTNDM%2BWeqOCsJTE5T5ZzonZ1xaWWdQ5pQpZGtQ7QLx275fLvh9n8deq4op8NU5RzyxWVjaW9XBs4zlg0I3P9SLnvsPackE%2FwD17BHx6oqI4OeIVZUBgprq9vsgzv8ALHInSrA423uz6cNiMNvc7KJaZRE8bmHB5xCbXwQhFzbedZFvl5RAcIHEGLasCoVq5aagzt6d4RpXgc7L3Z9ON6e9l88nLTCucQjdieDvP8DUrBCCbG4TUmOfpvFH6kDP7V0ftF3%2FAPHM%2FSi3GnBJ%2Fa7PpRvO9t68SWl4kjdZ4O8%2FgbDA9%2F8AHmfpRBfB5xAhIWMCHfa3jrJI39MJ0owX63Z9KN53tvXiS0rC143KrhHz%2FTe2A1nlb80s9v8ACiZXCHxBC9sBE27pxjf%2BVE8Z8F%2BtWfShHe29eJLTHRiJFIAMboHCLxBC2vL9wE33E6yRsL%2FbRD6kbiBWFrRgN7Skm35pZJUO%2B2qK8asD%2Bt2fTjeiMPvU%2FRzzNL6BDQI3W7wiZ%2FN6Ve0OYsQCU%2BMskg23HlWiT6kXiDUpKU4Beuq9rzbA%2FpbQ41YH9bs%2BnG9bvbevJy0vpETBAHKNyr4RuIZGq2Xcyu3LTNsb%2FwAqIDhJ4gyE3y2mhqF%2F0Uzt6etDjTgk7L3Z9KN6O9t68nLUMmmRVPSqKuqYFNW%2B2idVLJCnky5UA4ptKtlLCbkAkAm28ddZEVrhAwpjaoV%2BXzZx1MVaaw5P05TuMJbxdtyWfQGnkIWkKK3%2BiACQTyAtyjUC%2BEjiBBTpy6nbr8kdO1t6ettE31JPEJpB9zqcsQDfp2drm1vKieNGCct7s%2BlG9Pe29%2BTlb8cUzhxkcIqlcqMyMyp%2Bdl51l2So9cpqGpAtg6FrKkmwWG90qtqNrHmYvPCdmnhDJ3OVvGWOJiYlqT7D1CUMwwwXih5aU9GlSU76VFJTcciR2R4%2FqUOIU2SvLubCvPMsEeohW8So4UuIFQP%2FAAdTqSBcAvsi%2FwDKieNGC5Z912fSjejvdeo22cshyXzbyxXljXcgs%2FJKpe1GpVV2u0esUsK8apc845q1WTuNJstKwDbUtJFiIn4qcycAY1Tl1h%2FLjEc9X5DBeH3KY%2FPTrK0uPLK0aFLUvdaylu6j3mMe%2BpP4gbXVl3Op3sSXmbW776oivhO4ggE6Mu5w3ulSfGGQoH0auXnisaV4F9cs%2BnTvIw69TsoluqjY2yBlOBz2iorlA9siaA5U1UgOLTOIxB0pKHEDmHUm2kg6beaIcIOLOHOiZJYkwpmbiDD0nVMTTU%2FLYhkanNLbdqEkhAMt28tyUlFjqG%2B8aUHCjxC%2FCy6nRpG132fi8qJXOFniCUAF5aT6urfdxo2819UJ0rwL65Z9Onet3svfk5agbQUNpb0aEIT1b87dlz2m0S2PdG4XOFDiB0dJ7mtR%2FgutH%2BlFIcKefqjYZaVYeno7fzojjXgcbb3Z9Onejvbeo20S1EUbRIUG%2B0bfXwqcQIX0acs6qv8AdJ0afj1RD6lTiCBscsKpe1%2FgfF5UTxrwOdl7s%2BnTvVnD71H0ctQ6TDSY26OFfP0lSTllVApKQq129%2FMOtziZXCln%2BkJJyyqnW87e38qHGrA%2Frdn043q9w3ryctP9GYBs3jb44Vc%2Fjzywq4sbHdr5OtEU8K2ffWDmWlUQQLi%2Bg3Pd5UONWB%2FW7PpxvO4b15OWow2Ijo88bZXwsZ9IUEjLiqHzgIsP5USDhaz%2FACTbLSqHu0lFz%2FK2hxqwT63Z9ON60XG9eJLVPRw0eeNrHhcz97MrayPU39KI%2FUu59aSfcwrdx2aG%2FpRPGnBPrdn06d53DevJzzNUQ0eeNsK4Wc%2BkaNeWVYGskeSg6fTZUBws5%2Fk29zGrAbbkI7f4UONOCZ5Te7PpxvTGH3qrVFnLU%2Bjzw0eeNrI4WuIFdwnK6r6htp6lz%2FKtEr3C%2Fn4yR%2FwYVdY7dAQf6UTxpwP65Z9OnemcNvcbbOVHJXMWjYG9kKNXnugkamtDomtJUG3h1euB8EjTuORHnja0ziPIesTi6hV6th5%2BafsXFuMtLUoja5JTe%2B0amPDbn0Lf8FFe3%2F7EfPGG4nwTirB1QTSMZYYqFFnXGumQxOsFtS0XsVJPJQvtsTzjn1WeE4tbzXdrxTNVW2KaonqfQcG0%2BxXArhTcrWwiuijZNUTnEeCeSdupvSoy%2FDq4SqXmsNFwdjiEpT8Yi2CmZCKJUHcKkj90r540H0fR%2FpcOr8JuNqMAs42WlXO6EfCza5fhXKzn7Pub59gsgnVkpdwspR5gukfJflE6aPw%2BtuJ2wog9gK1KB%2BMxoPQyrYtpPpETEhSdBQCnz2i0YBT5WrnYqvhWqq%2FYLLm%2B5vv2t8PWtCDN4XSVmws4T%2BWCKNw9JISiawupROkalkXPojQQShPJtIh1O20T3hp8rVzlPwqVR%2BbcbLmjc32aZkAQFIfwlv8AbOERVRR8hrhSXcJm9yOZuL2vzjQA0J5JT6xExcChpKU2vfZMT3ho8pVzrf8AlWv6jZc33Ogjh%2FIB5KWw9hVGvdJ12uPSYirD%2FD8whIXN4V1E2F3hb1xz4SyRZQJHdbaIXY7vkEO8FHlaudWPhUrpnPuGy%2Fr7HTOAsI8N1RxpSpTEKMJvUt5%2Fo5kuvaEJFiQVKJASLi179sbeRltwNDqNy2AFfvqh8644KDmvqL0qT9r2fEdomsyeqploju0pjuYZdrth1nVRaUzXnOecz9z5xpji1vpXfaL3TTTY8GnLKmNU65nPVMa9bvJeX3A81q%2FO%2FAA08%2FzWD%2FSgjAHBA%2BjaUy909%2FjaR%2FTjg8pZ%2FUE%2FJEdLKur0DfrSI6fdNy8j1%2Fc8lOG3qfp%2FVntO8xl1wRLCkJl8ujr61vG0kn0db8UUH8tOCFA6TxXLsi1v0bb%2BnHCIQwm1mGxbl1BtEvRS17%2BLsX79A%2BaL03u6Rssev7le9l48v1T2ndTWCeChtHRtU3L9aQCQFTiVWtztde0Tv4V4NXXNKzgVC736tS07%2BpyOE%2Bhlzv0LP3A%2BaI9GwkWEuwf4A%2BaJ7tuvkeuNyYwy9eX6p7TuxeCOESaliyZrBDrCz1mlVUqQSDtdJct8cVG8OcLzEuiWk8VUBhlrqNtS2KJhpCB2JSlLwCR3AAARwYtDP6g0PQkfNFMolu1lv7kfNExfbrH0PX9ys4VeJnXeJ5p7TvZL%2FDyws9DjqVQo%2FCRiyZ%2FrrRbsSNcNmJW5cYjrVCrKJAKEuKpWlzQY1W1aOkcVa9he3OwjhfoWeyXbt%2B9HzRDoGP1u39wPmiJv138l1%2FcmMItonP4%2FqntOxcTZw5TZX4OqNMwJM0Zx5yVfZp1NpVlI6ZxOnW5p5Jsdz5o4dqqQzLdCg6tCLfJF90IRuhCU%2FvRaLFV%2FJc%2Fexr3q9xeIpoop4NNPI3bhh%2FcfCqqq4VVW2fR5s59rCnTEqDBwxKgmNNvvU25ojIcOYzr%2BGahLVSg1udps7KKC2JiVfU062q9%2BqtJBHLlex7YxiPbTZB6oOltt5lpKE6luPOBCEJ7yTAdLULwgfE9RZYSxzAYqiQlSddUprMw4bm9yvSCSOwmLJjnjc4jsc012k1bMmakZOYSpDrNHZRIhxChYoUpsBRT640TUJKYpk0ZOaLZXpC0LbWFtuIPJSVDYgiPIT54CvN1BUwsqUpR1EklRJKieZJO5PnO8eIudkSuLtFLXvAVokhfa8XCjUV%2BuOraZnZKVCbDXNzCWklR5JBPMmAtxJBiGr0RGalpiUmXZWZT0brSihSSb7g27IpwE%2Br0REEGKcTA3gJ%2BUTXEUwbRNAR1GGow0mGkwE0RAvEImTAbt4Ukk48qquwUog%2Fdj5ovmYAdlslqrOJQq0xiShNJcSPJLcnNKKb9%2FWB9EWjhMt7fapq5exwv6NcXisYcr%2BMOG%2BnGjS6X3JnGDjiwp5LYV4vJOnQLkBSwkk2G9oDQYqQCdPTqI1a7E%2FC7%2FAE%2BeILqIXr1OX6RQWvrHrKHInz%2BeMj9xDMNNulpPR3t5TqfniHuI5gltLqaclSVHT1XASD57QFSm4LqFXprNSXV5VtE5dfRuElRF%2BZt6IhP4Jqssw%2B6avJujRrWmx69twIulNylzILbMql%2BaYI6vRqWEpT5rnaITuVWYjKltKmZ1ZGxT2H4tjAa8FRf6wW%2BolxOhfW5gG4B7xeI%2BPi19atWkpPWJuD2G%2FMRszAeUWK6LjfDlXruEvHaYxU5Z2cYmEBTDsuHB0gWAb6Sm9%2FNeLXWcisdNz00%2FKUXTJOTLnii2lamnGislJSruta14DAPHn%2F1dXklHldh7PR5op%2ByM63p0PudVNk9bs7vR5ozIZKY%2FUFFFFcVoKQTew35GItZI5huqsmiK9bibQGFOT86%2BkodmHClXNJVsfVFeWmnk2uskRmasjMxAtCRQwdfI9MLRFWS%2BYTCuj9h21qF7hD6Da3rgN28GN1Y3m2Fc1zNHWn%2BDNk%2FFGyuOcD2bwgO3xWdP%2BeTGI8HWFKxS8avPz7AQkGmBYSoKKFCaJAUB5INjYnnYxl%2FHKE%2B2XCW2%2FiM5b7%2BIDlxYOhyOwZJ51inSLLJKlJl2Lq097aeR7BHIy2itNk9pjspumsLkJDxdtRUmXZ6pNrWbTz74vZTlX9m5jtvzHilw5N7HVr%2BEntPpi7Yfn5miTbdUlW0OhsFqYYWeo%2BwoWW2odxG3mj0syDzSFuNyy1LULNI5XV3XjZlIyPrUzSGazPJabbm3PekLNr2B1JCh2%2BbmY2Jtaaaopqna0%2Fi5mM4a7xNIssSjE9hx1yYprySrolC78t%2B4cHcOQX2i0a7rDlYl1rmJWSZWvddiiyifPG2MaYcxnl9U2Omkw%2BlBD6Gio6bH9JCk9p2uL%2BaNWY3zSxTNFqZknxSHphClPNU2WS0004nZIW3uodgNzvzjas4pmnOZalrTXnEUwx6RzKxRQalLVOmuol5yTc6Rh5tsEoVYi9jseZizMV%2FpnGKXSZGZqNSmXNEvIsJK3nnVHkAO8xi2P6PjyYwy3mFNU5iSpNXmRLialWujS86BupIv3g3I2vGHYXxxjjAc07OUZ51tM4gsrmG0hLxSfKCHrakEja4IMYqrSJj8XLYosKqYzq5s3TbiWcsqXN0NVVam8cVtjoq1MSjt2qRLK5yAUNi6RYOW2A2vuYxHpG9HQIcSlWnTGGYdxJJ1KVbMqSkHZaF%2BWhXbq7z54yuX1uN9f4SdKorZRFFEU55%2BGfDJacLhZ1LdWaOVYfnJhQQXEBd033023jBqewG1IX8FMbSnktooFTY6ZatUoogkDcptt8R3jWDWgJT75EWkZTDNYzMw1FjN1bNWrSknZyYUPkAixYela5XanK0Ojyzs%2FOP%2B9y0skalrVuQhA7SewRfsYtdNP1hf2syr5D%2FriyYUquIMNV2VxThebflKlRXUT0tNMeXLuIUClY9BtGpVtbkbFyksVzVIcamJaXbcUzspDoKVJWDuDHsaxNO4omzLinyzThQ44PfSNRCSbb%2BiLPSaTXcZVj2Oo1OcnqlNqW70bY67qt1KsO08zaKDlKqNNm1ysy09KzLRstJFik25fEYqlRcrSVn3yVKf4Y%2BaKfso12ML%2B7HzR5X5ZTbikBJVp%2BFpMUuid%2FU1wHu9kG%2F1BX3UPZBv9QV91Hj6NX2ivih0avtFQHs8fl%2FhMK%2B6idNRkwLGWcP8MR4OjV9or4odGr7RXxQHt9kW%2FwBRV8cPZFv9RV8ceLoXf1NXxQ6F39SV8UB7PZM%2FqHyx6pd9EynqXSpO6knu7xFp6F39SV8UXGnSzjetxwWUsaUp7SID0mIEd0ehuXJiZUqR2QHkse6EexMoSNx8kDKemA8cVExVMuR3wDB7jAQSSN4qJfUNoplpQiUgjnAenxiJVPg9seY8olgK6nQYNkqMUFXiqwbdsAeFopgRWesYpJgLnQh%2BecqDyMy0n43Ex1z4TYlHEPJtnswnR0fEyb%2FjjkjD6dVUkU%2F%2FAFjH%2BlTHWvhOTq4lUt%2FqWGaUn45dJtAcduc4kJ74nc5xIReAazFRtUUtMVGxAehCrREuW7YlAFoprgKwfV3%2FACxKXD3xQiIFzATlxUS6ld8TBtRiYNKMBTGpXbDSe8xWSyvuicS6z2QFEJPdE6QYnDKhEwZXAU9JiYG20VAyoxHod%2BUBBF%2BcXCTO0eJKbbR7ZaAzClf2q9Z%2FHFwyolhNZx4ZSpVktTgeJtfyElX5It1LJ9i%2FWfxxfskJ1Elnfhtxx0tJcmFMlxPlI1oUnUPOLxWdkrU65dq4IxFgqaqwwpjEP072Xn25lFQKQ5IuPJQUoYnW%2FKDd90uJuEqvqBEZhMY%2Flsv5GdQ5RV0%2BXS8WVMSt1yilJ2JSAShKdr3AAMYHhSnUqpYkp8tWHES8qqaKA9MkIadcBOgKc5ISpQAJOwvHqzWxDiCvVxWGcQYInMIGTl7zVP6riXCDbWHBsppQHVKbg77x37KmiLWZqjVt%2FwDqP6yeevM1V0U007dn2Rltnw%2BDwsIkZpOOsS1Wal52Vdqkw6XJaXU9ZU8i%2B4bUqyS4lNj0d7kXtflFwQJmXYdpjkipL8qoKIUAg35ELHZ6R3bxRnMH4Ipsl4%2FQp6oMzqQD7EzzSXW3yf0yXfRbSRz0OJBsNjFyobFdr87TcMyEi9NVWqzAlGBsslSvhKNyQANyeztjDeLSJztZbF1ommmLONfJD6I8N83OTuR2D5ie%2By%2Bx4Ryt1ErUlH8kJjZMWfB%2BHZbCWFaThiU%2BxUuTalUn7bQkAn1m59cXiORHndfYQhCAQhCAQhCA%2BA3HWdPEvmVtbViOc%2FHvHPUwbyksnT8AEj0x0Hx1b8TOZdri2I5z8Y%2F%2FADHPEyQJVmwO6UwGc4d%2FQtv%2ByR%2BONh5a5lO5aVCpTyMBYSxUmpMts9BiKQEymWKFFQWyfgKN7HbcW7o19h9P5mPmbQI2NlLlJjDOXF8vhbCcqtLSVJXUqmtsqlqdL8y44RzJAISgdZarAQGy6TxJzddq9OoUvkbkpSVVSbZk%2FHp%2BjDxeV1qt0rpCQQhIuTFTinzVy3xNUGMvMrML4cEhQp4PVDEdNpzUsZyZQgoLEsUAEy4KiSo31EADleMeqmL%2BGHDVTew3J5M4rxNSpN0y81X6jXjI1B5SSUuONSqU9G2kEGyVm%2FfGP5l5TVvB2vFlEw%2FXxl%2FUHGvYSsVWS8WddbcQFJS63clB5hKiAFgXEBtzBM4iT4DsbTZR0hYxVdIvzPTS4t%2BOOel4vnW3F%2FmZryvtyY6DwVJrnOArG8o04lJdxYm6zySC%2BwbmOf3MFzHSL%2FPCX%2B5MB0rwF4hdqOOscSz8qhKPaopwrCuVnTt67%2FJHI3d6%2FwAcda8CuHXqXjXHcwubbdS5hXodKRbfpib%2FACGOSiLW9f44CCI7tyDSE8IqW%2FKJpld59%2Bh68cKJ5x3PkAtDnCSdfwZOu39SHY%2BbfCfOWHXf%2FVj%2BSt18I%2BUq9DkrK8JXklipXaisU4f5gxPRmiueaUlDalNnWkL3SSBcXHaLjlE%2BTzcu%2FkljSW1tma8dp0yy0FjpChDYDi9N76Rfc2ttvFOnfZxYX6i%2F5pj6NZ7HJnaxGp545j0wolnajJuqS0hVzTZVNrjkLN8o8COI%2FMdryZqT9clL%2FwBXGH4tqElUJxC5BwrQ0w20V6bAlI3jHIuhtJfEjmWt0veOygUQRtJS4AB5%2FpUTN8SmZzYAFQljbleSltv8zGq4QG2DxO5rKUVKq7JJtzk5Xs5fpMR%2BqazW2%2FPpAsb7S0qP%2FZjUcIDb31TmaXW%2FPpHWNyPE5X%2Bp88Sp4m80kW0VsptytLSot%2FmY1NY90LHugNqu8SOZ7zaml1hBSo3UPFZXrd9%2Feo2U2lSJkThbQpRT02ki41FOrl2i5jmC1o6rYbClgK6g8XNx2gdDzgNW1HO3Mqnsyq3MQuPF1oOp1MMjTe4sOptyi2jP3MQFSvZQlSgQSUt335%2FAjFq9OsTbEi20SVMSgbcuLdfUSfxiLDAbJHEHmQnZFV0jTpsEN2ta32kTDiGzLSq4rSh3gJb3%2FkRrM8okN77QG0xxHZo20%2BzzlrW8lr%2BriRPEPmWm2msrFiVbBvmefwI1dv3xMLkQGzVcQmZC%2FKqyyO4hv6EDxB5jqSEGqqsBYDqbfyI1npV9qYaVfan4oDZf1QOZTgDBrSwhRA06W7c%2F3kbZ6BDetbelS20lxOqxGoJuDbkbHeOXWkqDouDtY%2FLHVUqNT2kNld2VDQPhe9q%2F%2FPqgNa1fP7N6nGW6TGtQe8Yl0TAKksAAm45BrzRahxHZrJ8jE00n0dF%2FVxh%2BIJlid8RTKq1IlpNtkqtbURck%2FL8kWMpF94DZieI7NhFujxdOIsLC3Rf1cVfqlM4NZWMZzgUTckBkX%2FzUashAbUPElnAV9J7dJ8Kve46H%2BqgriTzgWDfGc%2Bb87hn%2BqjVe8N4Dah4lM4VbnGM0T3lti%2F8Ao4lPEhnAopJxnOkoN0khnY%2Fe41dv54b9t4DaSeInOKZdbQ9jWdWkqSmykMkWKhcEdHuI2G%2BBJ1Wael0JZVLrfeRYAhtYQpQIHLZW9vNHOMslTUy3qOkIWkm%2F74R085INzVWqCQdIW2%2BsX7PeFKgNb1rOvNqiCVYTjiqLDks3MgrU2T1tx8CLQeIXNoqClYxnioG9zov%2FADYxnEtQlqomQclVqUGKewwslNuslO%2F44x4bmA2T9UPmxtqxdOq08rlGx7%2FJiP1RObvTLmBjWohxwAKVrSb2N%2B1Ma3KD2RCxgNnDiUznBSTj2qkoN03dTt%2FJiT6o7OLUVe3ipb7n3xP0Y1nY90TdGojYQGyk8R2b6FBxOM5%2FWBbXrGr47RT%2BqHzd09H7bpvR3ah8141v0DkTdA53wGy2eIPOCZfaZXjaohpxaW1oDo0qQTYpII5EbRnNRaQzPvttJCUhZsAOV97fLGh6ewfG2taeqlxBWe4ahHQlTZ1T8wrUnyh%2BIQgXjM9J%2Bpcw8oeSMfuX9PsefyR1rwXo08NNHP28rPq%2BOcUY5IzgnqZI5AYYwdMVqnprhxYqpO0pMyhc03LqkrJdW2kkoSSbC9jvHXnBs4h3hsoimkFOmQnGzc3usTS7n8UfLvhMme5LCI8pT%2FLW7eExnNXo98OAlkKmXSnl0zoHn98VvHRvAoB7sNYX2jD7gHreQI5uBPSq%2Fvrv%2BkVHSPAqUpzdq1ydSsPvEegOtk%2Fkj0Om36gt%2FRHthp4f%2Bk0%2Bles1EKXxjVJDikhHuZOc%2B7oT%2BWOcV9RtwnbnHR%2BZ6JVvjSqCJ2cYbE1l2G0hbiUalqaAS2m5F1nsSNyeUc6zEs%2Bx00rNMraebWttxtaSFIUCQQQeRuI29D9WCXb%2BCFL98vV6VXFeb2McDzc7ScPtUBuRpkwzKNNu0WXfOnoErupa0lS1EqJKifRaMR%2BqWzG7ZHCx9NAlj%2FRilmxNyXstX5AOWfTVm1oQfKKBLJBJ9caxWLR6hptovcS%2BYrtryWFk23snD8sB%2FNgjifzHaGlFPwsB%2FwCQSp%2FoRqggX5RJYwG3TxTZmk38Xw2B3ChStvi0RBPFBmSk7SOFj%2B%2FoEor%2BhGo7G9on6FR7IrI22nihzKF7yuGFXN%2F7RSu3o6m0RPFHmMposmn4Y0E3sKJKjtv9pGo%2BgV3fJAsKCgLc4gbf%2BqjzOc%2FScNfxFKf1cX52szmK5KQxTPsSUvO1OXLkz4owllta9RGvQmyQSAL2AjRUizqdKVJje2F5fxjCGHngm6FSjqAe8pdWDAePE2a2L8Mrm5WSapHisrPKlWGV0thVm0oHNRTqUSdySYxk8QWOCrWZShX7xTWR%2FRiGa8zKeyNap%2FTJ8ZYrj6ujHwUFpPyXEa00%2BaA2ajiDxs0NpOiE2tdVPZJ%2FmxN9UjmBqBMtRTZQUPzuZ5jlzQY1aU27IlAvAbaTxNZjJWpwNUcFV72psv2m%2FwCpwPEtj4jeXpN7abinsXI9OiNT6IiGlHlAbV%2BqUx7%2Bt6T%2FABfL%2FwBXEv1SuYYGlDNHCe402XP%2FALcatMu6hCVlBUCYilhSlW0keaA2s3xJ5jW6rVEH%2BTJf6EZKqbma5LtV2eSyH59jpXAy0ltN76dkpsBy7BGjaa3rcjfOG2Eu4XpjtwpLsr72q1ttZSR6biAnxLn7mZgx1%2BmUubpCZKUmFykswqiyag002lKQNSmytR3NyokkmMXHFDmfr166Lf8A8plrfF0dotWakwwudnpH%2B6ZSrTiXgdiL9Hbb1GNdpRaC7bf1UWZwJUPYZNzc2pcqLn73FZfFlmqoaS5RwPNSpT%2BqjTjibxT6IHsgNyq4r81VpKTNU0g8702U3%2FzMSniozPUQpa6WogabmnSvL71GnOiHdFUo0pvaA279VLmZv1aVuLf2ulu%2B%2FwCpRI7xQZlu26tHFjcfnZLc%2FvcalDKlKAF94Fi3YYDb7fFBmgtSCpdEIA0kijSilW8124yWbml19MtVp1phMzUZdDkwphpLSFuEkawhNkpuALgAC940RT0IVsRHQFJlw5RcPvtgKC5FkoPO%2FvihAY3iLOPGGFHlU2TlqOZZDrzTLTlJYV0aW16QnUU6lHtJJO5izDiKxyk6hT8PX%2F8AKmPoxa81XGHK7MSqHgt6Vn6g28LeSrxg%2FjG8YUW0pTciA2MeInHF1fnZh%2B6jcn2KZ3%2FkxUHEjj1N9NMw4LjT%2FaeX5fcxq9YvyiHRmCuTag4mcxE7IkMOJG1gKNL2H8iKh4n8xVApNLwvYi39o5fl9zGqAwpXIw8WX9tAybTHEtj%2FAH10rDS7m%2B9GY2P3MTI4mcwEIWj2Jw0UrIJBozHZ%2FBjVXiyx8KIFu0DJuml8TeYaXkIErhlAUoXAw%2FLG2%2FnTGRGemKtoqs0hlL84gPOBlsNo1Em%2BlI2SNuQjRVNQhDrClKTuofjEb7pLKV0SlrStDgMokhaRsRqURY9vOCGUF23DZnK1oIvIUg6%2Bz%2B2LOx%2BKNkeDMdfUMbSqXSZfx2lPKb7A4OlAV9zceuNf1FtElwu5tPTT7THjiaW1LoWsJU%2BUz7RIQOarWJNuVjGeeDMSgTeNySoL6elAC2xTd25v33jw%2Bn85YJaemj%2Bel1MI%2FSIa%2FwCKJerP7GY26s0wn%2FMpP5YtORe%2BdOBEfb1%2BVH4z%2BSLjxQqJz8xr5p9kf5hEW%2FIsas5sBaVaSK%2FK%2Bvc7RtWtP%2Fqsf6H%2FAAY7H9Kj%2BKPa6E8IdpOEMAX8oY2at6Cwn8ojRmeYJzaxJ%2F41Ubs8IjMMNYZy8DkwGwMZJcIvYBCWUXV6riNQ58Mf8KdZn2yh2Wnl9PLzDagtt5F1DUlQ2ULg8o0vg5pywGj%2BKr2oxL9JqYTOY5xDl5hBNXww5JNvTE443NKmKezMqUgJTpSC4lWlIJJsBuTzjETxM5hqv0jVJ3JJApksBvz5Nx78x5tmTy%2FlZN0qDk9OzBa22IbS3c%2FGfxRpYpj3bTbXd4mcwkIshFJT%2B8psqP8A2opDidzOCy6JiT1K5nxKWN%2FT71GqltgxL0UBt1vipzZZGlmoyrY7kSEqP%2FZiJ4rM3lc6w16RKSwP%2BhjUQl7xMJXY7QVltj6qjN9RJVXrk8yZaW7rfqMTN8UmbbSNDNaaR6JWW%2FKzGpxK%2BaJQxpVyghtv6qXOPR0Xs%2Bkt%2FaGVlSP9DGRYYzKxTmXIzzeMJ9ubVT%2BjEqtMs0hTVybgFtCbg33BvyjRLCPPG1coAAzWwkm7aJe%2B3YpVufqgMoxPi%2FEuX2H5acw1PNy3jQeemSllClPFC0oAUVpNgm5sB3xgyuIrMgoKfZFO51boatf1Nxk2cM4zK4fpVOdU6pU9KzZZGgFKSmYRcX9Aub%2BaNGhs3gNko4icz279HVkJv3JR9CKv1SWa%2FwC2Fzlp%2BBsPN1I1ipvaKaGVazcm0BtT6pjODSEpxZNJAtaykdn8CJVcS%2BcavKxhOK3vutPP7mNbIlwREHZXqwGxlcR%2BbijdWKHie%2B6QfjCYo%2FVDZp3v7Y3799x9GNeiV27YkcY0tOLB8m3ywGzE8RObq1BwYumARyusbfyYyXDWNsU45p6nMTVfxsyqgGFOEEN3NiL2vvtty2jTVMB6ONm5XuNuMVFhF9bCm1L9Cjt%2BKAyzEeYePcusNyqcFYmnKSwrpJmZbliEJmHS7oCl7EqKRsN7CMId4l863r9JjyodYWNnbX%2BIRec3JxiWoFJp5adS%2FNS76780rSmZFiO63KNQlsDYwGwvqkM59ISMfVYWFhaaULRIOJDOpKShOYNaSkjSQmdWAR6o1041dUSdD19MBspPEnnWkaRmFXALk%2Fo9ztFoHiPznUSVZhVwk99Qd%2BeNcCXuk7ROZbyduyA2IOI3OUHUnMOuA31bTznO1r84gjiMznSnQjMWupT3CfdH5dvVGvBLXUodwvFFxhQRqEBsw8Qecak2GYldT501B0W%2BXaMvw1izFuP6A6%2FizEc%2FV1MzDTjSp%2BYU%2B40SFBQbUq5CSALp5bXtGmZOwRG28pFy01Rqs0khTkpNy6VC3LUlZ2PxwHqzBxfjDA9FpPtXxDUaYz4qjpG5SYU0hxxbqyXFBJ6yrJABPIC0YGrPTNRSQg42qpSOQM69b%2BdGS54T7LUvTqK4k9O5TmJpFiLdGHnE39N%2ByNTaNoDL1Z4Zpm98a1cX2P5vf3%2FlRROdmZ2kN%2B3asaRyHsg%2Ft%2FKjD3WLnYxT8W8reAzRvOvM9tQKMdVsEbA%2ByUx9OKnu05oklXt6rVyLK%2FPGZ3%2FlxhCZU2iu1Le%2BC5gMv92jM3QF%2B3GrG3YahME%2Fz4g3nZme2QWsY1VBSNIKZ6YFh93GG%2BLuaF7xL0CkpBJEBnbWdWZd0qcxrWbpNxoqEwLHv8uM9wvXq9iemiertXnqg62AW1Tcyt5SArewUskgbcrxpFtADdjG5MsJliZwzMpTs4w%2B2yr0hBJA%2FwBcBufhsl3HM4ae22jrNMzLno94d2jD%2FB3FoZvVLUn35WGJwNG%2ByR0jev1kAD1xmGSGJsKYBxo3jDG9dk6NTJND7Spp8m63HGFhLSQkEqUQCQAOyMR8HqypOdE5rFiMMzpt3Aqbt8keV00iO8l4n910sN%2FSKfS2Tx7m%2Bd0md%2F8Ai5LDn3OrjmxcdIceZSc72AOacPSoPrdcjm9e8bOiX6lu3o98ta%2BfL1elK5cSzrvJSEKI9Qj6QSlUl8ruGSnV6iSjQRh3B4qjLJ2Q48mWS6oqt2rWrc84%2BcD%2FAOg3usPsSh8kfQTMRt1fCFUm0WSRl24bHtCJZBPyR5H4RqYtbxcbGvXTNc5x0Y9kzzujhczTY21VO2Ihzy1xZ8W88tuoSmTXTyryUrSJelTCkEHlYgnv74uMlxWcXDkuXF5HMFKdi4uRmU2PnF9vRGiM4MRYjkcw6tK0nElakZIS9OdbYlak%2B00NchLkkISsAXNz6411J4gr0zL9JMYkrK9Sjq1VF86vP5ceostFMEtbOKqrtTnMckZe9zbS3tYrnKZj7Xck%2FnxxXIp0zUqDgmh1puUmGpdSZSnzQUpSxfqgnewBJA3FjFhRxMcaxFxkBMKFr3FImo5BFZqSVJWmv1UKQrWk%2BPv3SrvHX5%2BeKjeMcTLaL4xZiDmT%2FbWZ7OZ8uLcT8D5bvSjuq28Z2PI8TfGI9OMS09kZ4i26oBb79MnAhCSd1Gw7LfKI9Vb4j%2BK%2BltsO0%2FKyn1Vb3SdIJemTw6IItsbgbm%2Bw7Y4tp%2BLMWz7HSoxTWUJ%2B1VVZr49lxBGLMbPTDifbXWrpN7mrTXPze%2BRXibgeecXeOved1W3jOu2uLHjBT9kyCW5vYWps2m59Y7YudO4rOKyaUU1DJNmmtDUPGJmQnSnWBfR1U%2BUeyOMXMT43v%2FxurX8bzP04mOLsZadJxliG3Owq01z%2B%2BQnQ3A5%2FZ4553ndVt4zsqd4qeLCUcDDOSbE%2F1dRdlpGbCUn7U6h8sTM8UvFoGw7NZCONpVzBk5gK8wvaOK3MT4rcGl3FleUO5VVmD%2FTjz%2B2nEyqhKNO4mrSkLX1gak%2BQbch5cTGhuB%2FV4553ndVt4zuhzih4rFJAZyBdC7i92H7bjbsigOKfixl3EpneH5aQpOoDoXwSL2vuI5hzgxlimbwflc1OYgniqSwZLSyFtzDjalteOzagFlKuuRqI33A2jWIxHiC%2F%2FGCrfxg99KJ4m4F9Xp553p7qtvGd5u8TnFEtsvMZR0pdm9YZLM4XL28nybXi3L4sOLlBsrhwedF7EiUmvmjiI4hr7SA4rENWAHK1Qe%2BlHoqGI8SSMuJg4jrCgbWvU5gf0opxLwKf2eOed6Zvlvl%2Bc7bb4uOKpZSF8Nz6ArtLc19GPZPcU3E3JNdMzkfIz6iQA1LibCwD8LdFrRwt7PYvWx0pr9T02vY1V%2F6UeeTxDiRcuFt1ipBKxcAVF8W9WqHEnAuS7xz1b0xfbePnO3kcYvFKAQ5w2vL7jpmAR%2FJi40zjG4g5pn808PjrCnbdE6t19LY33J6hJFu6OEUVbECfLrlSP%2BUXvpRN7M1kbGt1Tnfafe%2BlEToTgXLd456t63d1v4zumd4xc%2BJbWVZHtTL32sq%2FMnQkfCILdzfzRBjjNz4m0ak8PsySnnZ9255Wt1OV44WRXKw1fo65VkX56ag8L%2Fyo9dBrFZm1z%2FSV2re9JSn9Hvct%2FwB1EToVgWeq7xzzvRN%2Bt5%2Bc7qd4wc%2BUMFxnh7qLpQCXF3cShNue%2BiPKONfO5Cx0vD3UClQukoddUFDzEI3jl%2BoY1xU1w2UmktVyfRKJzAqa2VCadDyPztlkrR0gVfQeqdN7XHnMa2bxRihq3RYorSNIsNNSfFh93FeJWAztu8c87zuy38Z3u7xiZ2rLSkZBoKVC%2Bhc48HB6uitFvmuNzPeWWtpvhtqroRYqI6cpA79m%2FljiJvF2L1uhlGMcQalJ1f21mPpxKvG%2BNm5vxQYvxCQpI2VWJgAfy4tGhWBx9BHPO8m%2FXidXCdtS3G7n9Mqu3wxVdxF%2BaRMcvT0cXn6rzPxGh1zhqqa0FAeUhp98r0HlzateOFJrHWYEnpR7c8QpSSLaa5M%2FTiRzGuP3EFJxhX0AixtWpk3%2BNcJ0LwL6v11byL9eI%2BdLugcY3ELMFXinCriYj4OpuYV8fvUe6Q4s%2BIydGtfDFVW7A2C0zCTf1tco4GTjfHabhWNsQ78%2Fz4mfpxTcxdip23TYsrzlhYaqpMH%2BnCNCsC8h11b098Lx40voCOKjicT0mvhnnuqLjo3nSQfQWvXFM8WPEyFtJmuF2uAKPvaktvKuPvcfPOYxHXgFFrENVSobgife2P3cXd3EWJJSiy0zL4orjZcCVLCKm%2BNR37NcW4k4FP0HXVvR3wvHjO9Zni74gmdCE8M9fU5YhxK2nE6Fdn6Wb3jyTvGrnjT0dHNcN9aQ6eXvrgSkXsb2b5jzRyVQsZYtTkRixCMR1RWjFdEIdXUZgPMkys5shQXsFb6huDpT2gGMI9t2K%2BXtur3Mn%2B20xzPM%2BXFJ0JwL6vHPVvO%2BF48Z3NN8bOdMuppJyDnx0gvZT7o%2BQt3jyzfHXnHKOFo8PdXKkGy9JcWPUejjiZrHWM3AX2sc4kJBKNQrMzfbs8uIyWYuYc2rTL43xPz%2BHXpkf04tGheBx%2Bzxz1bzu%2B8T852w3x8ZoBR6Th1rygOdg5cfyI9j%2FHNmm02h1HD9VCksCYPvqydJ7LdHz7CO%2BOHkZkZl%2BNqa9vOKUqDQ1J9n5nlfv19%2B8TTGP8zXyL47xXsLDViCZVYfdxPEzAuW7xz1bzu28eNLtZjjvzcfdDSOHTEFzySEuX%2BVEe2W4186pzV0HDZiM6QCbrUnY8juiOHvbrjuZv49jvEq789VamVX%2BNceZ6uVx8aX8SVh0adNl1J89Xu3XyieJmBfV4553qzfbx48u9HuL7Ppp9m%2BQDjLUyjpWg%2FVWgSg%2BkWivIcX%2Bf8AVpoy0lkVLvrISpLTNYlivSTYbW3j5v1Lrvy9utqV2kqv6bmKCJcLeb94TcK5pFomNDcCiMu5qevev3ZeJ%2BfL6dVTiyz2whTpuuY44asRU%2BmU1Cnp2ZQ62roWULQlx22ndCS4i6hsNQ3i%2FcW0pI4x4cZ3E0%2FLpW9R5mRqFOdWj3xnpinUlJ5gLbXuOVwO6PnvhN6psYRxyvp51LScOKYSsTDhASqaZ1IuTyIAukcxzBj6AcQM%2BuW4S5%2BnvjWZqSoNlX5rCWgB8UeBxrCrng2MYf3FRwZqtMpyz5Joy5Z8aYn2Opd7W1tLvazaTnlTHXn5o8D5%2FuRSIUTtFVR0nrRRUVE7R9kefnWjCEIBCEIBEw09sSxAhR8kwE4sSR8UNFwDblADlFQEbnugJG9I57en%2FfaJllMOqOX%2B4iU6fR6O6ALKygbAejtiYLuoFJO%2FI%2F6opkG4IBSQerEydR5kWt6xAVFLJ20iIJF%2FgCJCNr3iKTbtMBEnSlSkC5ES36qVHyj2RMmwvtzMXfBuFqrjjGFDwXQksmo12oM0%2BWLy9CA44rSCo9gHMwFGTolcqlMqFWptBnpuQpDImKhNsS61syrdwNTiwLJFyOcSuYdra8OLxe1Rp1dDamvEnakhhSpZt%2BwPRqcHVSdxsT2x23gyRxjwh0iUyDVP4ZxTi3NGsTU3TGpkus0iSkWpctTL08SnWtCghYCAD5J5Xix4Zx%2FT82cB1Pg%2FoE5l9R5zEdLD9CquFWps0dxxl8PvyU0y%2BkOpfUhvUlwakqHbtAcWREHvjOs5MqcR5M4%2BmcA4odk5icZlJeeRMyaiph5h5JUhSbgEHYgpIBBEYPo88BRc5Rj9YNm1%2BiMhcFhGO1r7EswGFwEemninmZK6q663LJBUSykKWT2AA7XMV6q3SRMNuUWYeclnWwsofSEutKvYoVbY99x2QFYYdqBpqql0sp1Wg%2BZczCen6Im2sIvciLYtfUiZz7Prv1%2F9XzbRTVAEu2Qm6yQkWAPZ6BF7mcNVGWpqqmp6TdQ2hDjrLMwlTzSFGyVKRe9r%2FF22iyJiZKlIUVoUUkgpJBtseYgJXEExSKSOyLrT00W7rlbVOFtKRobldOtRJ71bAARQqDEkzOut02aXMylwpl1aNClJPYodhHIwHoncOTtPkRPrmJJ1CVBDyGZhK1sKPILA5X3%2BKLUuI%2FY3IE3gIIDi3Et%2BUpVkp%2FIIutZw1UaJLom5hyUfZUvolKlphLvROWvoXbdJt3xaoh0nlfuvK89uUBCEXGkt4bW2v2am59pa%2Bq34u0lYRtspVyLi%2FYN7R5JthUrMOSxA1Nm1%2BwjsI8xG8BSBvsYvrVUwuhpDa8IKdWkWW4aioFR77adosMTQGQCrYTAscDqPnNUX9CKiKpgx4FiYwfMSqXLJ8ZZqCnFs%2FuggpAVbuuLxj1iTZKSpR5AczF4xBhxVCEu61VJSoy740l%2BW1aW3glJWyoKAIWnVY7WO9rwFGs0d2kPtWdTMSk0kuSky35D6O8dyhyKTuDHg5RdKRVpeWYcpNZZXMUuYOpSUHry7nY81%2B6HaOShsewxQq1JfpL6ELdQ%2Bw%2BnpJWab%2BxzDf2w7j2FJ3B2MBuXhQQpWPKn0fP2KV%2FOjY2W2ImMMZL4KxvhyWkvbDhzHVY98mGRMNlLkuUBt1lZKFdRxRSrTcHkdo1vwpkJxnWFKvYUy5tztqjaWTqKVjPKbCmBaolynUqVxFVxXK6mUW%2Bqk9MyZiUmA21dTjeptaFlXVTqG4gLqjiZzQQAHFUBZtZR9hZe6v5MTq4m8yVm5Zw8fMaKxb8UZO%2Fw%2FZFMWS7xVUxBIvdeHZoD8UUk5F5ELRccWmHEDXYF2jzKN%2FWIDHPqk8yhYolMLAAEWNCYI357WgniZzKTfVJ4TN7cqAyOXoEZJ7hGSCyA3xeYMBUbALp0wN4pJyMyROonjDwEEpUUHVKPg3HPa0Bj6eJfMMXtTMIpvz%2FOJqJmOJLHV9DkhhdCUpCkg0VBTt2WHKL57hOSqiot8YeXJSB5SmH9j80QXkFlA2E9JxhZYpJF7kPi8BYF8SWPrWcouDVbFN%2FYNu5B9EUVcRWMFgJXhrBikjsNBaMZEvIbKAIStzjByu0r8kqMwAfjiAyCyeUerxg5WcuYU%2Fa%2FxQGOucQeK3Bc4TwWdrdagNH8kedWfdfLZaOCcD7m%2B2HmrDv2jLRw%2B5SjoSeL7K49P5HXfGr0bRWb4dcp5q6WOLjLG6RYnpHrau7ydoDwZM4tl8b50UCpz1JpVMqEo0ZVr2OkBLIfa1lfvmjZSk6iBcHY%2BaHHIonEuEk32TIzn%2BnEZZlTg3D2VubsvS6XjGg48lK3ItyiazRHdTNLmlOlaWXW1jUFrSyopWOwkERhvHA4VYwwu32JpcwfjmDAc1o1XAv2%2FljtqUW6qWlktNFCuibvtsk6Bt6LxxOhJLiE2vdYFvXHccgroktvqXqSEJC23Lg2CRt6RF7P5T7GG8TlZxLMMDilM1EVzFqVopdNR0kwltJWp3kAhIAJKiTsO02Ed3ZcytDrlFla3KyikyaAUyLDzekoRtdakHyXCbg9w9cfPoVh2Qw5UnKes6wpkyjRvbxnWNJHcbx0hgvM00WVZoqpx11Ek0lpSiTY6QLnz73PrjJaWEWlcTHga9leZs4q8H3QyLiepmGhh6cdnXzKI0nSW5dK9ToGpBtcbJUB6ATHzXm6PRsS1Ss4kxbiaXoNHpbrLE1NS8q5NOThc2ShhpFiVkJUQpVhtY846t4sM3VvUWn0%2BmMGbOptxbKLrdUlS%2BsQBvfTeOapvAlfw3S5tdWYclKFi%2BpIS2%2FUGiy4tppRdZUllXvig2FFKlpGm6gLx16bOzizpsc889sQ0vja86rWfsefNGqU48MVOwjljWariTC2H66%2FNVacqlG8Um6ep1SUtIWApQSysr2IPlAgxgPDNmBg3CGNhI5o0Bmu4IqyTLVaQdTdTeojTMNquClaCdWxFxcd0ZVgusyuXT%2BMME5h%2BzdPw9iuWak0YgkpRc1KJAXqQXmBs%2By6OqtKSHEEAp3BjFMEZIUXMPMZOE8GZrUOSXVZ1yUpKpuSmtEyoIKkIJKAUhZSUo1b3sDuY1re7TFnwKafwad%2BftXut6oornhVa6p8Hmy9EaohfeJLKKjZK5guy2Eqx7IYar8oisYYqySFdJLr3DayPK0nqk2FxY84smD8QS2IZYsjSxOoSLoJ2Nu1PfGu04rqjstJ%2ByqXHFUtTjLUtMqKksoBUlTOknYBV9u8RPgty8v07DnWacKdSfN%2FqIjBaTTFWdP8AXhbVnRVVTlXt%2FrLqybgq7YaodRWtSAtcotoA7k3I2v6o1h0awjo%2FQqM1drrVSw9OImZoMzTTJVotsoAbW8%2FbGuJmoA9Qk2IuTe28K5iYzTZUzEzEsBqcwhyp1hvX9lmXUxdc15XC1NxlL%2B0KlexEmik04LSh1a1LmfFkdO6SskjpF3VpHVF9gBGJ1F8irVA35zKz8Zi54qdU9V9S%2FKDLCfibA%2FJGpLZiMl%2Fw2joXGHmSG3NuugaSCO24j01pBdUpxaytSt1FXMmGGmwtxlJtskGKtVTtygyMQn0EAxZX07xkdUbskm0WF1POKDyEWiWwJvaKhFolItAQHOJ4kHOJ4CaB80IQBOuPfIsCYcICU7C%2B8eCLlSgoOab7rBAgO68qvBtUfMHKvC2ZVTzvFDGJKY1UTLO0hKkS2skBBcLgB5c9owziE4AcY5HYZGPKNimSxphxDzLE49KMKYmZIvLCGnFNEkLaUtSU60KNiRcW3jsSnUbKOtcC%2BAKJnjiFdFwfNUKlh%2BeRMGXUl7WVMpCwlRF1C1rG8alzRz2yOkcj5DhS4YK9O4mqdaXL0alOrUtbMn0kyl0KVMPBIWvpLAIACQO4CAx3Dng0KFTqRTE5u57U3C1eq6UdDTUS7ailxVvegp1aelWCQCE9ptGucUcBWKsH8QWEslcR4nlUUnHDj6aPieWk1FDnQoUXW3JdR1IeRZJKNRBCwQdjbqXNfOLKGpytCwBx%2B5IzOFK%2FMy%2FjMpO6TPyCnNQbedlJyUUXZdRUhKltKB03Te%2Bxj0YkykrODeJPIDE8rmzifFeE5%2BszcpJU7EVQE49T5kyK3G3WXtKVONuNdUhY1gpBJNzAcG8Q%2FDQchc3pfK5vFiMQNTrMk%2BxPiV8XUBMK06Vt3Nik9t9wRyjPuJDgLrmSNUwfRMG4mmMf1LFzs3LtSEnS1MzKHWEpWdCdRDiSFHuItGacf1PqM5xV0VmWkZhxdRkKCmRCWyfGFB4pX0f2xSdiBy7Y3P4RrH2KctMRZTYywLiF2jYhpUxV3pObabQ4pCVttNKuhYKVJIJBuIDmLHXADibL3hymc7cV4tbptck%2BgW%2Fhd6SJW2l14NhKngqyXLHVaxG1rxyM%2B3Yx9VsxsaYkzD8GvL4%2BxjP%2ByFbrUrJPTsyWUtB5fsgpIUUJsBskcrR8r5vy4DwqiUX7YqORTgERSoiIQgJyrUII23iA5RFPMwF5w2Pz0kyOZmpf%2FTIjq7wnwtxSzo7sP0kH1S6fnjlPCgvXaag8lT8on430R1X4T4%2F%2FAKqaog9lGpif%2FTIgOPnOcQJBEQc2VEDygIxFJtFO574XPfAV%2BkiUrvFK574ngJriJ0RRBuYrN8oC94WobuJMQ0ygsupZXUp1iTS4oXCC64EBR8wKrx3C54KbHrK%2FFV5x4NEzfSGlsTCSo%2Bba5%2BKONsrEBePsNN99akP%2FALhEfU7jFy24c8cY4oNUzvzxnsA1CmSrop0vKPhpyaZ6cKU4DYkELTYEQHBGMeD%2FADhwTmzScm5%2FDiJms4hUVUWblHekkqgyk2ccQ7YWDfNxKgFJFttxG7R4MHEb7TtJk8%2BMCrxS1Ll9dDPSEgAX3Wm6kp%2Fd6NI58oz3MLiafzO4istPqZcKz2Ys5l2iemJlsJLQqUs80hmZQlS9wA2EqDhHl2NrRdJWtcH2e2dqalKTeOMos9ETJliu66fUBPNpCFNEK1yzy9ICCm6NaTa28Byzk7wRZkZs5gYxyynatScI1%2FA4QKkxVkuOILi1lKUoU1e6SLKC%2BRSoGMDykyGrWbGcMvk1K1mnUmpvOzjSpx%2FU5Lo8XCisjT1lA6Tawj6F8LGEsdYG4ss4aBmZjI4srz1Fo821XVNBpVSkFOEMOrbGzawLoUnsKeZFo5b4SWX18ccilTDnSsz1cU%2Bkp3ZAQ4Dr7tyOfmgMDb4PcyJrP2pcPtEmKVVatSdLs3U2XFpkWJYoSsvLKhqSAFgabXJ2EbFzR8HBjXBeB6jjXA%2BY1BxwaG0t6qU2RbW1NNpQNThbuSFlKQVFs6VWuRflGTZpV%2FPin8a2PKDw81ealK7iEy0rNoYl2nUOMNMtG7i1ghpKSb6rj1xmZqmA%2BBPKTFeFK3j2XxPmnmElyYm5aWfHQsPLbU3rIvsAFq3PWWfNAfORxvo12j0S3ZEZ5RXMKOgJT8FPaPNEWPIgMspn9qx5yY8uFpuZkcwKVNyJSJpiYDrGtGpOtIKhqHaNt%2FNePVTAfYseYmLVTlvs4qlJiVVZ1kqWk%2FwFX%2BSImIqjKTOYnOHcuE8T0fNCley%2BHpZiXeUgImqM2LusKI66mzezzRNyCBqF7EdsXYvOqp65OpvOLRJNeKtoUpatDd79GEE3SkHsG28cLYLx5jLANTlq3g7EU1TJ2WUlxp1uygFAdqVApO224jerHHVn5MttKrMrgasTbI6k5O4bbLw9aFJB%2BKN%2Bzvc5cGr3%2B6JadpdqZ1059U%2B2YbxksBztcdC6JTZmamVke8yjBASL7EHmAO25jrDhOySw3SVP5kuz0lUaih12SaTLu9MiRcSdLrerlqB2NuXLsjjPIaR4pON7ETlHrWNXsOZfyK0itzNDkkU9laefi6CganHFDs1WSNz2A%2FUjL7L7CWVuEKdgbA9HaptHpbXRsMt7kkm6lrUd1rUSVKUdySSYxXmuLWIias9fJs3zzQvdaa7OZmactXLOc7o55ZFCEI1myQhCAQhCAQhCA%2BA3HSB9U3mXewviOc%2FFHPM8LNSw72EK39MdCcdKv%2F1NZljffEk3y9No57nTdqVVttLp5d9zAZ3h%2FwDQ7l%2F1NEbiybzokctqbO4axJhP2ao09XKXXmlN1RdPVJ1CUUUtPOuoBK5cBfXRbYDUN409Q9mVfvURtrJrAOWOORURmHmGrDT7U9LSso14zLMI6BxC1Oza1PEFaUKQlGhHWu4DygL9mFw5Z%2F4uxvWKw1ghjEvtpqD9SFYoUy0qkzCphZcLiHdQDbY1fCtYC5i%2F5%2F5uSHsbUMtKGaZVMQ1uRo8tmFiSReW7Jzk1TkaGZOTQT0aUNAJC3UCylBVuZjJ2%2BHvhelJM0uT4rFSsjMXvKt1mWbaVfndCVhJv298a7zTyuyLwdhWdnMu84GsQT8kuSEuw3Nyrjc30q1peaQ02S4gtJSlZWRpOqwgMywHMy8pwIY8cdWQGsUtLA7fs0uLes2jRTmMZTplp6F7nbyY3ngtiYm%2BArH0tKo1PLxShCATYX6aXO%2FqBjnQ4TrynVq8Wa5k%2FZBAdTcCuIpSq46x1JtIeQ77VOlF7W0h4g%2BveORFiyj5ir8ZjqjgKotVp2ZGNVzEqltlWEtGq4vr8YuB6OccsOrU486tRuVOLJPf1jAQRzjuHIMK%2BpHd0JurxSu7fwHY4eRzjuDIMqHCK6vUCVSle027Oq6I%2Ba%2FCfEd7bvn5WP5K3UwvVVX%2FDLkzLOlYabyln6%2F7WZV6u%2BOybLdXded6aTYDKgpppAUEaXLnUVAnutHnmpxyQlJqYlyQpLSwkjmAQfyR7crpSpu5Q4im2naSKPIzUlLzAdUrx1yZXLlTZYAGnQnfWVHtAEeZuTlp9xUnOuLRLuJUHCgb20Hb1mwj6PRscydrFeJXBmF8C5z4hwzg2nKkqRKtU91hhT6nynppFh1fvitzda1HzXt2RqNznGbZn45ruZuNKljjEMrJy07UEsIUzJIUhlCGWUMtgBRJvobTck7m5jB3DYxdAN4mAtFPUYmC4D0tspUN4rIYQOwR4enUnlFZmZJ2MB7Ogbh0DcShQIvEbjvgM0yUoFCxLm3hChYgpqKhITtVbbmpRbikJfbAUooUpJBANhexjcC55Eu%2B68y2ENNlaEoSNkosU6QOwBJtHP%2BFMVVLBOJ6XjCiiXVP0WaROMJmW9bSlJ7FJuLg37434ltE4XFrSUCYQp4pQeRWkqsD3XNoDAeJ3C2FMH50YgoGDKKKVSWJWmOMSaHVuIbU5IsuLIUslR1KUVc%2BajaNOORnGZWOcSZmYunscYoEkmo1NqXbcRJsdCyhDDKGEJQkkkWS2Lm%2B5uYwVarqIgAAO14qJaSecUtxDpCmA9aWG%2BUVmpZq%2FKPCibMeliaPdAepEq3qJ%2B2gZRsJKQYlQ9uTfnygXbC14DOMiaPRKxnRg2l12ksVOSeqaTMykzqLUwhKVK0KSCCUkpFxfeNpzVScb8ZmmkJbXZxWlGyUgg3SO4WJHojQ2E8XVfAuKadjHD%2FQeyVJeExLdO3rb1WKesna4soxveUYlVzaXJsaZYJW45pudujJt3kXt8sBg%2FFVhvDeEs%2BsU0LCNDYo9JZ8RdlpFgqLTAdkmHFBJUSbFa1nc9sadVzMZnmfjnEeZuL6lmDixUqatWuiW%2BJSX6FhIbaQ0hKEdgCG0j1RhB5wE1h3RUbQk84pAxEulHKA9rbTZ2MVxKsjfaLYiYINzHsamNYgPSmWaF7fCgqWb2%2FcxKlfLflBS%2Be%2FOA2Nw7SFInM7MMMViiSNYlQqZfckZ5suSz6mpd1xCXUAgqRrSklN97Rni5%2BYfbdnFFPTTKC4dIskFSbFI7huRbujSGEMYVnAeK6fjDDxZ9kaYtSmA%2B30jataC2pKk9oKVKHrje6qZKImX5TodUshp4hu5NilpSki4sSAoD4oDAuKiiUDDufONKNheiy1IpUvOMmWkpZCkNMBUqytSUhRJA1KUbX7Y04OcZhmPjfEmY2LKjjfFrzDtWrKkTEythgMtkhtKAEoAskBKEj1XjD4Cskg7GKqUIMeXV3QLihteAuCGEEdkVUMARbmphQNt49zbxIEB6AwiJVsoHKIB0d8SrdEBsTh4ptJqOcuHZSr0qSqUmoTjjkpOtdIw6pEq8tGtNxqAUlJtfmBGb9I48svOkFTiQtVthewOwEaYwZjSuYGxXTsWYZWymqU5xRl%2BmZDraitJbUlSDsoFK1C3njdMxKOMOLYb6qdkhO9htyF%2BwcoDfmS%2BX%2BXuKsgc5KriDL%2Bh1Kq04SE5J1N9gmbYdWChRS7e6R1B1Rte%2FONqcGyAnhrpLSjYGXqRJ7rzi%2FmjlTFONc3MDZKP1TCeKKRRsI4trLeHJylyVPQJ2aSyx0yXZh9SST1tVrG%2FqjqTgrW%2Bvhqpq1udbxap6VembXb5bx8w%2BEynhXWwn%2FMp%2FlrdvCasuFHm98OCFHVMOK733T%2FLVHR%2FAogHN%2BrKPNOHX9P3xF45xQPfV%2F353%2BeY6Q4Fbe6%2FVesP%2BLsxt%2FhW47%2Bm%2FwCoLefNHthqYfH9qpjzrlm3SMHV7i7qycZ4TksSSdMwKw%2BzITrzrbCpjoDoWstKCzp1bWMaQqRcmZt96YcK3XFK1KNySfWbn1m8bczk9uU5xgVprBM5h1maYwQw7NezSXPFnJREuOkQNHW6U6k6SO2NSzbzMzPTTsr%2Bh1PLLPPyb7c97d197c42dDY%2FId2%2Fgp9kMV8j8dV6Xj4isIYYkMDZbY5plIdl67i1NdXW5kvKWiaVLzDKWFBJ2b0oUU2HO1455f2jdGe2O6pWxR8uVSMvL0fAInJSnON61PvmbWh51b6z1T1gAlKQAADz5xpV8kKIj1TVySExXZbQrnHmvcRMFqRyMUQujMowrnHtbkZa2wixNzTqbWMepFSdTzgLsqSlvJsrfuMSPSTBQkC4095i2mqk2JSdj3xK5U3dwlGxgPY8wlpQ8X2UopT6ybR1ZmVRsP4VxlPYVwpRJej0ilpZal5Fh5x1DaiygrWVOEqKlqJUd7XOwAjkPx5xV9fVVdJCu60dKO4tquYjctjysyEtKVKuNJdmW5VKksno7MpWlKrlOpKASLkXvaAtXEphfCtJw1lriej0bxWsYqoM%2FO114OLUmbmmqgttD1lbIPR9UhNhsNrxz3sOyNt5y45xDiJ2lYRn5WVRTMDtTtHpbzbaw6607MrmFqdUSQpWpdhawAAG%2FONRFUBA9Y2j0MyyDzIjy6x2REPLTyMBeZenMrF1HfsAj1ppUqnrJKhuL2%2FFFiRPOISOsY9CatMBIAWPWIC6qpbGlSUhdjumKExINtt9JZWr1R4vZl%2FvTEjlTdXzVAV5aXaTNspClXW%2B2g2VyuoDaOrc1JSh0TH1ZoOGqHJ0ak0yZMtJyMmVlllISnVp1qUq6l6lEk7knlyjkluassLKt0kK%2BLeOhDievZgKTjLEMsxLVGsnxmaSw2UN6r6dSUnlcJCrd5MB4%2BJ7C%2BGqU1lviei0MU6cxjhBVVrGl1a0Tc6memGvGQFE6CpCE3CbJ25c45%2F125RtfO%2FG9ZxhU6RRpuVl2qZgqnqw1RltNLQXZRt5x3pHdROp1S3VEkWHIAbRqTtvBdOCVHePU1LNLHWMePUeyKiHVAc4KLqzIyyrc%2FPYx6kUuVI2DlvTFlROuN%2BSRaPU3VXgNgLemAuRpUsR8O%2FmtFF%2BRl2htr89yIoGrOgeSgnzx5pipKdFth32MBc8MyjE5iWjyD6VLZmqlLS7iQqxUhbqUqAPZcE7x09iml0%2Bi40qtEolPYptJo9RdlqdJsFSkMMNunSm6yVKPaSeZJjk2Qq01TJ%2BUqciUpmJKYbmWVKFwHELCkkjt3AjqGnVmfxs6xi2tSKJGbrzvjk4w2TobW64dWkHcA87E7XgmGA8S%2BF8O0Cp4LquHqaqTXifCTVdqg6ZTgmJ5ycmUOPi%2Fka0obugbAp25xpZKtaNzGys68ZVfF1el5apScrLS%2BFpE4ZpSJZtaQqTYmHlpW4VE6nCpxVyLDkANo1glZBI7L7QM1ZLaTzXHoal2iN3I8ZcUO6CX3B2iCF6ZkZa1lKJvFZNNl%2FhBXmi0NT7qBzj1N1d1PwbwHudpsvcbK9ced2QYZSUlHUWer33jyO1aYUdiBHneqL7idJWfVBMTkyHB9Okp%2FFeH6XUUFyUnarKSswhKikqaW8hKwCNxdJIv2R0PiWmSFGr9VotHlBKU%2Bmz8zJycslxSwww28tLaNSt1WTYXO57Y5joVYnKTV6dWpAJVN0%2BbZm5cLTqSXW1haAQOYKgNo6QVW5jFilYsnKainzFdKp9%2BVbUooZdcWStKdXWA1XIB5XghtPhoyayszqx%2FU6LmphVValpPDM47KLTPPMKlXGjrSpAbIBJKiDquN%2BUZPwDU6nUrE%2BYlMprS20S1VpgbC1XIbCXha%2Ffff1RrHDeZeamS%2BE8RZo5XUTCxlaLIokq1PVcLfmfzc8GEpYZC0p0pIQSd%2FKN4zvwdNVm61Vsf1OcUFTU5OUt11SU2BVZ7s7N48F8IlM95q5jw0f%2FALKHUwj5eI%2FrY1ZxRJKc%2BsaXt%2FbFu1u7oUW%2BS0W7IOxzswHqO3tglvXuY9%2FE6AM%2Bcbaf2UR%2FoG48WQH%2FAC24D%2F8AP5f%2BlG%2FbT%2F6rn%2Fkf8GOx%2FS4j96Pa6T43qJT8QzGVdErEsX5OcxbMsTCErKS6gyjQKPNfcbb9Y2jnjMMUaVxfVaXhzC8phykyM%2FMNylIlX3XWJTrAK0F0lVllOsjldRsBG7%2FCDVWq0eUy0qFEWhFRbxNNGUK03SHTLspQVDuuRfzRozMiRxNTcYT9OxgKL7YGXnBUF0VThknFazpU3rJO45729HKNP4O5mMDoz8NX80q4jOd4r9Puh5ZvDWHMSZMZlVCt0xUxUMH0uUqlEmm3lIMm8%2FPsMv3SOqtK0WSQeVriOZHhp5Rv7GeNarg3LSq4apUrLOt5gNex1VceCi40xKvsvthm2wKljrE322Fucc%2FzDl4901EE7xVS0DHmS5aKqZjSd4KPa3Lo7or9CjujzMzQO1o9aXQRygJCyi0UHG2wY9K1C20W99zciAn6nmjpLB8nRZTIbBs5KUSQl6pVqjWHZ6ooQfGZttmYQhttar20I5gADeOYS5vG6crsZVSvYS9o083LeJYaccnKc422UvXmnAXkLVeyk3QCNgRvvvAZ%2Fiek0GtcPOYdSqtIlpmqYcmqE%2FRp9RUHpMzE4puYQixsUrSBcEHdIIjlx4aHNMb5zNxfXKFgGYwhRUMmmY06N%2BtBxjU4n2PmQpjol36gKnDq2ubCNCPLuq4gJ06Tsox6W2EWuCIt51EXBtE8rMrB0kwF3aZbtuIn8Xb7opS0wkjePV0ybXtAUVy7fdHhnm0tJUvotSCoXTqteLgp1J5xbag5dBR2QFOSfS0CkoO%2FIA3jpqnrp0jkllzLydCpbD81KVOZmag1LJTOzR8fUAiYdG7oTp6gPkjaOWELIjdWXeK8R4nwy3h%2Bruh%2BRw8laaUsspSpAfd6R5JUPLBUAR3QGwsV0%2BkVnhnxdWahSJR6o4exHQm6bPlFpiXamPGA%2B0FDfo12BKTcX32jmR8jpNuUbkzLxjX6HgQZe01baKLX5hFWq6ehBdemZVa25ezh3ShIWeqOZue2NKlZPOAiN17x7WZdtZBIEW8qIF49EtNHVa8Bc0yjVuyCpVA3im26e0xV6UQFNbLY61vKjyTCGEIUj7aPW4uLVNOlS1eaArNO25R1LKeJS2XeX0pJU2nMB%2FC7E8%2B5KyyW3ZmYU%2B%2BlTj6wLurtsCeQAEcmtuqSrc7RvLLDEuIcQYRaplaUh6Ww90crR3yyEOIllFxSmSofZEBRuNW6TfextAZrmlIUub4eqpOP0qTfqMji%2BlMy9QUyPGWGHJWZK2Euc%2BiUUglB2uL7GOZFkGNw5v4qxDLYck8CsTCm6JOoarM6z0CbPVBtTjbbvS%2BUbNLICLgC5Nje8aW6WA9CAg84qttNqjx69I3iqw9vzgPWJZHdFRMukbgRK24CIj0ouBAQW0kBXnjyOpRyEemYeSlIi1uzI1Gx5QFfURtHV1VYl04KwO1T6bLMKRhCkzL%2FAIuwlsPOlLgU64Uga1nYFRuTYDsjkZM1pOpXKOisr8Q4sq%2BFmGMRuqeYo7bEjTi6wlLiZIJKm29QAK2xdWm%2B433gNtZCsSc1mvhBE1TqdUZSdqrLD8tUJVuaaSVBSdRbcBSbBRF7dsXjIqmyFM4z8cSFLpsrT5dqjVMol5VoNNNp6RqyUoGwF7xiuVNDxZWcXKoOCMcu4KrDy3J2XrDckmZWlttlxwspSryNS9B1psRbui18CNermK8%2BKtiWvzs1UZ%2Bcw1OOTc2%2BvUsqU61uo9tzHlNNYjvJb5%2BLLo4b%2Bk0Mz491JVnm0Uu6lLw%2FKHRY%2B9pDrgG%2FI35%2Ba0c29u8dIcd51Z5sg%2FBw7Jp%2Fzrp%2FLHOShvt2RtaJa8Fu0%2Fu%2B%2BWve5zt6vSg8keJzHmZWfkj6CZlTLQ4VJlSypTbmBQyq3PS5LtI%2FKY%2BfM3qElMkfqDn4o%2BgmcoZleFioyyChKUYBI6%2FL9Dsgeu%2FLz2jyfwgxwr5cIjxp9tG90MN1Xe2nzR73CufrLUrmJPSbN9MvIUxsE8zaTaAJPabARqeVaelpYJdCU2vzMbBzzl%2FG8ZIcVVX2n3MNUEoCm79ITT2iSo9l%2B%2BNblbjckGn3gopuoqV3R9EuufxFGfgj2OXbfKT6XvYDBsp2ZaFtzdQ29USyjLIkVNuTjCV9I6qxWLWKjbeMZfmF9IreKfTufbxs5sTLaMpmmyimH5lgq30qS8kpO%2Ff2XEStPdDMvul1mzigRpeSSIxPpD%2B5%2BIRLAZi5PNk7vtffBHncnGb7PtffBGLQgMkL6FfDbP8ADETsyU07OS8wlKAhskqUVDYW5xjzC7G0ZZTHGy31%2FtT%2BKAz3OeQW9RsuJRlLKVN4KpriQCACC9ME37ySbkxq%2FwAWUl0pUttPpUI2fmtMeMS%2BXbyAOj9oNMQkg31aXpkH0biNU1dfvkUHrnZdIkill5tThIA64233j119DU3IdFLzMspwKSbFYFwOdoxMueeIdJAZU46n2NRLtqQp3o%2BWoc%2FTePPKKS3KJb1BOn90IxyH3EXGROPJ%2B3Sf4Q%2BeKKn0jtHxiLCdPaB6oh1b7QF9Ci6PeQpZ7k84veGJCck%2FHlzrJaDum1yDe178oxemOdGtDnwtUZwiYb6Py%2FLT8sBnuYVEVSuHDL%2BVaKSXcUVmadUkWK9bDOnUO0hItfutGn5SWWo63XEJHnVG28b1Z2qcPGCEzDSkLkcV1mUQon7IhMrLnUfureqNHzjqhcJPbAZA1Lo9l230uoDQlChR1C2vVyinUJcN1diZbcQpsJsVJWOV4xZb7n28Uy4s81GAy2tlUyUmWRr0qCtWobfLEjhP%2B6oxS57zEbjvMBkKyQq%2B3xxSWtXd8sWTUAL3MEuC%2FlfJAXgyszMp6NhgqUe0WjIPFNdNk5RzqrQ2NQ1cjFloMx7%2FANH9smL3NODQFa7aUmA2XUKGmj8Ks2tyVZ8cmccSTvjA%2ByKZMo8EoUe0ApUQOzUY1Kw2PNGy5nE0zVeG6uUh9tCW6PiyjhtZO7ynJeaJt3FIHxGNJzM45c6SQIRqGRU5tDdNV0y0tlMw5sVC9idjFCjESa3%2BnI8o6dwe3aMdM44ee8SlwmAybxhPsgp240KZ03894reyDQ5n5YxDWu8R6SAyhyqMnkReKBqAPIiMdKlA7KMTIeWO2AvzMjO1CZYUywtaUrC1EHkI9jslMSzza2kdIlBIWi4BV%2FveLVLTFSUlAkpgNG9r3EVVvVlLvSzVREwgKAUUq3IIgOu8S4cwhTeCukz2F2jUq7jBTlQnXmkuEsvJeLSpNtA2UpCEXcNjubjYRvzidUlHCynolakqaoYv5iGvyxzLwS19j3QKdR8S45Vh7C9FqMviNybdmeiTJFvWHktuK6rQfbu0tNjrBtztHTPFEuXd4ZJpyTa6OWXM0pTCPtWlOhSAPME2EfN9L7OznEsMqojLK1iMuWZmqmZnqjX58nZudUxd7amdecRPojXEQ4T584lIN4C5POJo%2BkS4yTlziYemCxvuIlRc8xARtvE0IlJN4CMTC0U4ngJrCFoE2gDeARJE8S2PdAQ0iAFom0%2BeGnzwAC43iA5xEiI91oBEyXSwDMJdW0Wuulba1IWgg%2BUFJ3SRzuNxaJRy39B9MTNnQu8B9AcVZT4klqtkXmRQcbs5l40wjS3m5uTTVGGqhiGnutrdExIKcOl1yXDyrahdaUJJuQYt%2BTGRtccz2puN8e4mr9GqFMw87L0OQxRU5FzELr60rZ8cabZOkSzIdKk67nVe%2B1o4qwTiurYAxlQsd4cUyirYdm0Tcg48jpEtlNxosT5BBUCkWG8ZDm5mfinOXGqsf4tZk5OoGVakmGqchTTcsyhJAS2okrGq5Kt97wFjx4isM42rspiDFpxTUZSozEq%2FWvGS%2BmfLaykPJWeaVAXA5C9uyMbWFX2iuUIR1EaU6bJSlKdhbsHdFIg9sB53oxuuH3lz0XjI3%2B7vEY3XPsTvmRAYvItyD4mETs4ZZQZUphXR60rdFrIVbkCL79htEsy1JNsyypCacfW7LhyYStrR0LupQKBudQsEnVtztbaPLE6IC6TMjRmni6xVnXWlySXWj4vZYmbC7KxfYA6hr3BFj27W1SVFBUEmybXNuUR0oOw5%2BYx7qdW56mStQp8rMJMtU2BLzbK2wpLiQoKTz3BCgCCLGAt5QpKNRSQUi9jF2q0hh%2BVmZtNMxA7PS4YacknFShbLrh0623Ek%2B9lN177g6R33jzVKr1CsOtTFTmVTDrEu1KNrUACGmk6W07AX0pAF%2BffHkgPdJytMfpVQefqSpeoy5aVJy6mromkk2cGu%2FUUnYi4soX7RvLPM0uVny3Izz03I6kHpiz0bhSQNfUJ5g3A3sbX7Y8moclbX74jAe6p0%2BiSsxPokq45OttOpEg4JYtiZaN9Slgm7SgNPVsbknfaLapAtqAVY8iREVKSDuoCPY3Vp5FIeoiXUqkn30TRbUgHS6lJSFpPMHSSDvYjmNhAeKUbllTjDc6%2BtmWW6hLzqG9am2ybKUE%2FCIFzbttCcZYYm3mpWY8YYQ4oNO6dPSIubK0ncXFjY8rweUXXFLUsFa%2B4RKkXGntEB61y1KVQm51qpr9kUzK2npNbRA6KwKHUL5HcqBTsRYHcHbxQ7bQgJYmiWJoCvT3peXnEPTjTrjKb3DSglYNtiCdtjaPR7JJ9jJinL6RwzDyHrqWNKSm%2B%2FfqINrxboQFXXePW1OzJp%2FsWp1SpVL3jDbZ36NdrEjuuOY8wjwxVZ5KgN68KSL4vrSzayaYLg8iNfKPfSalPUbh6q8%2FQqpP02cOKKK05MSkythwlcrNlxAUgg6SLAjkbco83COjVizEA06r0m3o6xN%2FkjzylVMrw51yfV10tY2ovV7DaTmwR5u%2BAxpOYOOm%2FJx%2FiI2O%2F56vK38%2FWiVWZeYo3bzBxARe3XqK1fjvGHyOLVU%2BWp7Lck0tUhUDNgnm9fV1D5t4kRitfRNS6pRromquqq6COd%2FwBLNvgwGyJTOnNGWl0S6sazrqUXGp97UVG%2Fabbx6Xc880UsrQjGr7QWkoJQpNwDzG4jVTuKnltTCEss3cqfsiPSbe9j9ztyiaZxY%2FMmeUuXl0CcnGptSQjYFB3SnuBtAbhwFnji2m48w5UccY7r03h2VqjC6vLshp5bkok9dKWykBRsdkn5osk1nNmk2%2B%2B2xmPWnGelXo6QtE6NR0agUGx02uO%2BNbTuJ1TkvV0Klm2%2FZF1p4W5tlJHk%2BmIT2K3p56qOKlZdHsg235N%2BoUgC6fOe2Az9%2FOvNhXWGYlWUbclKZ2%2FkbR45vP3OslLDeYVZU22kFv7Hbz2siMIexEp8ToUygeMyqGgQPI07gjzm0VPbXM%2BN%2BNdE3fxZLFuzbe%2FpgMsXn7nKG1BWYNaKVEKPXQPX5Me%2BjZ05sTU%2Bwy%2FmDWlI1adPTJHYb7aYw5%2BtuT1EnmXQ2lTYbCCNyoFQHOK0pVyirNI6FPld4%2B1MB1RwhYmxDifFbE%2FiKsTdTeRXaZKNuTKgpSGwxMuWBsLC%2FwCOL1xvJPtwwwdVx7FPqG3L80EW%2FL64xTgjcEzV5J7SlKk4ykU6yfK%2FMU0rT5xYcoyjjeKjjrDSSSLUVZA77zCjAc6IKUzCCRca0i3f1hHc7KAtBbfW2pVkAKt3Adg587RwqBqeaSRcF1AI7xqF47aaZSFpaQSiyBYpvcEJ2BPyRksddpPoYr1qs6Y%2FrkZFKONOIflXXpZtpuYam3CobEMONrCEfu1AqHqjqp%2FK6gTrSphgvNqdST0jfLSrfly5RyzhRMu6t6nzCEkTSFNlahYb7H4%2BUdZZd1J17B0jKTAWmZprfsfMoUblK29hv2gpsQe0GNiqmOFEtSmvKmYj0uauJnDmZOUtMaxTltiqqyya1pp1QXIMtmZAbuprSspUtHb5Nr73jj9M1i%2BsV52u4xm8SVJ%2BXSnxmeqDrr7suxfZRK76Wwo7gWEfXFbrD46J5ttQ1X0qSCLjt37Ys%2BKcAYFx5LysvivDkrN%2BJr6Rh1pIZdRfyk6kAakKGykKukjmI26LeujKKcsmrVY2dUTVP53s9D5nTmKKpjWep%2BT8rien0Cm1gMS8zNvLvLLmVKu044dw2gK0qKhGKUXEE3khj2Uq8t0OIsQYXqwfaHSpTTlvsLISoOJBLzSiAtKk2uI2hl5kjWZDiao9BbpUm%2BzhnFKJqeRZLcgumB8uKAKzp0BpWnQSbWKe6MFzlwrL0rNfGzdOTLuUmXxJOy8iuXsGhLlZU0lAHwQghItt1Yz29dcWlcTOfBiI82vNisLCiqimNnCzq9OWTUeIi7U5%2Bp12ZZl2X6pPTE%2B81LtlDLbjzhcUltJJISFKNgSbC0TYBknjQPGgbB591Q9F7fkj2YnlnHUM0%2BTbWp%2BYV0aEp53PMiMikKT7E0qWkEJA8XQE37D3n445tUzXOcurRlTGTxVJHRyD%2FwBt0JjFSwTpt2xl1QbPicwF%2BSGlJH5IxpgdI5y%2F3MVWanqY%2FPeoD%2F6hf4zF0xKgory2%2B5tr%2BYIt1Wt7NVMd0wv%2BdF%2Bxq2W8ZTjShYpSyD97TGvM62bkZZguVQ%2B%2BjU3ezR%2FEYkqqByi7ZcAJnEhWmxlnL6uXkGLbW0aHLRVZitTTds7RYHE2EZJPgFJiwPpsq0BbiIlj1rbigpvfaApwHOJw35omCBASRAm0TKFjEyW7wEkemUf6NYCvUYp9Cq%2B0TJQU7wHT2MuNet424c6Bw8zeBKbIs0FFOS1V5aecU46JQkpJaKdIKr72Vsfk0GxXJtuabmmpt5mYacS8082spW24kgpWk9igQCD3iMf6QgxP0sB3phzwn9ddw7K07NTJjDuMarJFJTUS6lkPuBIBeUy42tLbirdYoIBN9hyjUOd3GdmZnPiyg4n6ZGGU4Umkz9ClaYo2kppJBD5WrdxewSbi2kkWsY5rD6hayj8cTeML%2B2MB9BKN4VWsCkyqcXZHUKp1qUSdM7KT%2FQtFw%2BU4ltxClMlXaErI88cw8QHEtjXiCxgnFOLES0oiVaErI0%2BVv0MmwCToTfckqOpSjuTblYCNM9Oq3lGJOkJ7YDpud40Z%2Be4W6fwwv4EkG5WRbYYTWW55ZdWhqYLybslGkEk2NlWjmaaVdfOKXSRKteo374Cm5FOKi%2BUSWMBCEIiOcBOlO0RSneCDtaJkmxgL1hFOrEVJT31OSH%2BfRHU3hOjfitriftKTTE%2F%2BmRHMGB06sVUNPfVpIf8AqER054TFXScWWJ0%2FqdPpnxGWRAchOiy4kJid03X6Ik0kmAhCJwiBRaAkhAi0ICZI3isk2ikOcTg2gL%2FhOvTGG69TMQyjLTr1LnGJ1tt2%2BhxTSwsJVbcAlNiRvvG6uKHionuJzFlLxXO4NlsNu0ym%2BxxYl51Uyl330uFepSUkbki1o58aWQIrIUbQGwcqs18W5P46pWYeCJxqXq9JcWpAfQVsTDa0lLjDyQRqbWklJF78iNwI6xe8I5gKaqIxvN8KGGVY7CBetKm0LJcSnSFlZb6Q7bXPWtteOD%2BmKYeMGA6KoXGNmtQs9pziAQ%2FJzlaqTapOfp7yVJkpmRIAEtZJ1ICNKVIUCSlQvvciN5zfhLsJyZncQ4N4a6PR8XVNoJmas9MsrK1nmXFNtpW6PTa%2FbHAgmFdpiYTR7YDqDI7jMquUeNMcZgVrAchi6tY4caVMzkzPLlXZYJUpS0J0pUClV07bW0jnGbYt4%2FsG4opdYkqlwl4BmJisyrks%2FOzLqHnyVIKQsrUzqJTcEHUDcDcRxX0%2Bruh0vmEBWffS88XEIKE%2FBTz2G28eiXspMeEKubiPSw5ogMwp6tNLT5yY8mGpZU3jeSlkp1FYdAHeeiXHpp29LR649WXEr43mrRJfeynXdx2WZcP5IDF5YBTSVd6R%2BKM4ygwcxmHmjhHAs48%2BzKV6tyNMmXmQCtpp59DalJvtcBRIv2xh8nJuTTigkIQyynUty%2FVQPPGwuGqtJneJXK6Sp3UkUYxo2%2FJUwoTjXWPm7hAfePL3L7COV2EafgfA9HZplIpjYbZZbG6j8Ja1c1LUdyo7kxkcIQCEIQCEIQCEIQCEIQHwD46bDifzIA2%2FsinTc8tlCOeZokhoHkGkAR0Hx1f%2FABP5k73%2FALIp%2FwBXWEc%2BTHktfvW4DP6J9hV%2B9RG%2FOGtJWutJRkgrMAIn5Bx5aZeUdLKAl20n%2BaDZIeKgslHXPQ9140PRrCTGyb2Rc9sbPy%2BqueeA6W%2FiXANAqqKVNOt1FUyui%2BMy5cZStKJhClJISUpWtIWDyUqA6pVMSDJI%2Bt8zJ1G50yNPV%2BKNWZ%2FdCnA9ULHC8vAqXvY1IqCpKRaFOJfUel1tXdPTj3qxAR1dt4wM8WvEAtCULzDQjULjo5FgX%2BSI1TEPEZnVQH1TlJrOIaZUVMMPzcjQU%2FmjxVZW0yp9tOoobWpSgi9go3gNjZcLaZ4GsfzLirJRilK1K7E2XLi%2FxGNIJxBSdavzajyj2xuPATi18BmZ7YTdxrEQQlHbqDstcHz845lMnOBarSb%2FAJR%2FSzAdi8D1UkJzHWM2ZaabWs4aSvSDvYPEX9G4jjZwhS1qTyK12%2B6MdPcATc2zmli0uSziELwmsFSkkDaYRYfKY5jf5uH%2FALZz%2BeYCVHOO3uH8X4Q3AFXvK4h59nUc2jh9BjuHIFV%2BER0faSuIU%2FEhyPm3wnRM4fd4jysfy1OrhNM1Wlf8MuU8pf8AkLxj%2FwCe0v8A%2B3MSSDRU6E%2FCNx%2FJMMrF6cjcVp%2B2r9L%2FAPtjHtoMoqbqktItVGmy03NlXirU5MdGZhSRulAsSoi8fRrPY5c7WlMXdGp2TdZbQkOSLalhCbDXc%2FNzjEHRZRA7436vKKjP9A3PYskHlMIDHvdSaCbJvzuL33jzKyYwo9NSqX5qdEvNPJQZmXWh4aNYSpSQLarAkgdtrRdDQ0IyrGVApFHqb0tRXnXpRpS0tuvJ0rdSHFJSsp%2BASkAlNzY3FzGLrbPZAUiqJkKiUoiZCYD1tOEiK179sRocvKTdYp8nPl%2FxZ%2Baaae6C3SaFLAVpvtq03tfa%2FON4VrK%2FLP2dnvYCn4iapCZhzxJuem2VzCWdR6PpVIASV6bXttflAaHmSrQux%2BCfxR1LJaQmXe1DQqVTdVrG3Qi0YSMqsFqtdqpBN%2BsC4jcdvZGb9MwgFwuMy8sy2Qtby%2Bo20E2uo9yRzPmgOf8AEX6FpZ06byZPputW8YisWcUI6RfyjwG9LyqJvH1HV0MqhCPzWrrNnrJXcN7gg3EeR3I7AvRJdl8TU2oHUgqak58qfCCRqVoUgAhINzvAc8RKrnGYYuolIpc6uXpYcU2gK6yzuuyykHzXABtGIrBvygKR2idtyxiUgk8omQ3Aext28VNRMVMNSspPYipUjUEvKk5idYamEMqCXFNKcAWEE7BWkmxO143nUspsAJqU6qnSFQap7jrhk2n5kOOtN6joC1pAClBOnUQAL3tAaHFy80f3aR8ojqCYb0KmVfbNLP8AmzGKyGVGBWzqmpGbeUlQUjTMaBt2HY%2FJGX1GZlZWXmJidfSxKNtLQ84dw22U6SfUDAc84l%2FQkg30enVIMufGDGJx0TN5YYLeblUTWKVuKTJMhnUw8gLZ09RW7e9xCn5KYLmn2UNThmEh1szIaSoLDAWOk0a0gFejUUi%2B5AB2gOd9J5xIfPGYYyotHptTmmqMHfEw%2B4JdT4AWWgshGoDYK02uBsCTbaMRWDeAkJAio27aKRF4ilJMB7mnSRFXVfti4YDptNq2M6FTKyzMPU%2BZqDDc41LuBt1xjWOkShRBCVFNwCQQCQY3hV8j8EipzUzT5WdlpR99xcrLuzHSuMMlai22pYAC1JTpBVYXIvYQHPssnXPS%2B%2F8AdDf84R1bOMt%2ByNSUU7dDOEW5mzCyLRhstk7gth1Ew8xNudGoKCQ6U7g99oy%2BfnWJdtybnZpiVkktLbfedBIaQtJQo2AJJsrsF4DnrG60TD8rMeTqkJX%2FAEQjDtBjpZ%2FJ7AzzDDc3jUOfmdJbS5JTLZcaA6igejtuImo2QmAqjNMiVqvjjRUStKGnm1LSgp6RKFOICSpKTe1%2FVAcy2iRZtGWY4o0jSqzNStKbWmXbWpKNRuQATsT2%2BeMTWLmAghW8elD1hHl0xG5EB70PE9sRKzbePfgOnyNXxpQ6XVmHHpKZnmW5hptehbjRUNSUq30ki4CrGxIMbsmsscv%2FAByYbRSX22S6ospExqUhvUbAqI6xtbewvAaNoAvXJAf%2FAFTZ%2BWOj6i3eoujTpsv8QG0Y63llgmXmGZlmVfJYdSsBT5BUAeRIG1%2B8Rkjy1POrddF1OOE7bgeb0DYeqA9mbyT9THhVRR%2F03cSD3gSSjb4yfjjqvgr6NPDRStPNcnUVn8LVeOXc4Ej6lvDJtbTj5Y5f93qvHUPBS4tXDVTUq%2BBJVRI9HjKz%2BWPmHwlTwrrYT4LWn%2BWt28Jj870e%2BHBSPL9Ljv8APVHSXAgArN2uE%2FBw84R63kRzajmn985%2FPMdJcCNzm7W0jl7XHifU6mPQacx%2F6%2Fb%2Bin2w1sP%2FAEun0vVjdvXxkYxcv9iy71bdnvLO%2FqjScs2AwmN2YyB%2BrAzFWnUCcvQLns1MMCw828adpUoZ1xLKpqVlEXCS%2FNOhtpJJsLqO25ja0O1YHdY%2Fcp9kNe%2BT%2BOqYTmq5%2BeeJWPgqrDKfUGAR%2BMxp2YbjpzEmVLlZxLWJ%2BoV%2Bks%2BPTaX1SKaigpbWlAABJF%2BQJ9cW17JOltoU901MnECwWZWYS6UX5XANwDyj1DWzc3xFxITpKTckXMbhzbwDhnB0wKfRHRNqEvJOvPFgtFp55jpHWLEnUEHYLGyr3jTrl4LJdRhqMSWWeRMNK%2FPFFFQGJ%2BYilHTcxkrgR6hYcqVKkZtoVCh06ZmvGVIWVTa2dT62tO4ZKiNAV1tjfsgOZygnnHUOD5fpMAYTf%2BEunhtPqeVb1Wi1O5M4YAIS05faxCQfTGdUSkP06kU6hyiHHxIAS8sgJF1FS9hblzMBpnNXpPH8QS%2FwEYjmU%2FE1Go1t2jq%2Bp5IYaxHP1KszGdmEmUzs%2B5OuypniSy8TpcT5G5FrWBiVHDXgqYQkS%2BbeBJlxRCUNJnF6lrUbJSDptcmw3I5wHJ%2BiKS9o3Fm9l7SsCz0zQ2G0rmJRxtLzgRpOpTKVKTa5tYkj1RqBxuAphUTBXdEoTaJtO0AuInimlMdRTeRuCnkyszRpV5iVmJSVWETaUrdS8plJe3TtoLhVoBuQm1zeA5iT2%2BgmOnqIhC6BRVE6lCQa6U9x1WHyRa3MlMNpQrUhP3u35Yzmn0ZbFNlaXLN6zJNNoBIAuq3LzCA0jmq2tybn5e%2FWl61UGVeYpWkWjV5YjoSuYAotdqM1XGce0BEtUZp6oIlTOKUW1ukFaQdH2yT2xRYygoM66iXpuI8NOzb6g1LsGcVqddOyU3KQBc2Fz3wWc%2BlpXdA7RtfPDBVCwTiM0Oglx5mSYaL7rzfRu%2BMLZaW62pIJFkOKWlJB6yQCbE2jVSwTyEEqWqxiYLAiBREpBEFFXXftiBRfmYmlEa5hpvq%2BUPLvbn227I6nrPD9g6beTOUNh2SkHJeWebl6ghKplKlMIL2pTfV0l3WUDmEFOreA5YaQVOpT3rSPlEddUSWJplImVk6ZltpYVe5t0mm%2F44xN3IOnNEqbmWUFvtDR9UbMpNMcpshIyEspbi5FttKFOWBWpJ1XPYAST6oDm7NhHSVKY%2Fcz8%2BlPo8ZVGt9EdJT%2BV%2BG67NPzk1mdhu78y%2FMhnxhSujLrilqQDosQCSPVEsvkThOYmWJGVxphyZm5xxLEsymZUFPOq8lAJSACfOYDnEtmxiidjGz868F0rA%2BKpjD1HeceakwlJeWkIUslKSSUjYG5I2PIAxrHozzgGuGsxKRbaEBFSrxGLjhuTZnK7JS8yyl5txyym1KKQrY2BI3te0b3ncmcHIeQulF16VcZZWjxhAS6lRaSpwKCTbZZUE96Qkne8BovDA%2FsjpZ7pxo%2FyhHSMmR7DSDurV0jF%2FR1jGMM5WUOSmmpyUCWnmVBxpYQTZSTsbExlLzctKy8tKSqV6WWw3ddrqt27bcyYDIK24F8LubyejB0GipCu0XqDZ%2FJGd%2BDRLfR44Ac9%2BM9TOr3JCH7H7o2jXta%2FwDhczXXf9PoibemeRGwfBotWONZm24nqY1fzEPG3x7x4j4QI4WCWkeej%2Bel1cJ%2BXiWt%2BJ%2Byc%2BsbI%2F7ySr42W48vDwAc88BBSrD2caPK9zoXYfHaPTxRG%2Bf2M%2BuVfngnstb3pvaPNw8hK89MAIN7KrzA2%2Feqi81TxSpmfIf%2FAM2Kw%2FS4nzx7W8fCHqUhOVYQoavbWspHnCZf%2FVGrc80qTnBiVCgkFMyAQOQO5%2FLGzvCFkCp5TJsCTidZtfnvL9ka0zxC3M3cSqPlrnP9UU%2BDyn8hWfpq%2FmlXEYyvNfp9zW%2BY0u25gKVUoAq6Z8puNxu3yjQb8vHT9ewU9iGhStMXijDLCGHXXFEVIdIsLCOooabApKOzvMYmrIumqBSjEVNfdPktsVBC1uHuAta%2Frj28tLNoYNEdsUnCQuN24uynwxh3AE1iIVOdNZangwzJ9ADLrli2VKcLt7hwLCRotYpJNwRGknAdfKCFZh4gx6w%2BSOcWsa0m8TB5Y7YC5iYtzMed1es3jy9OvvjcmV%2BW%2BDcZZfztUqDdVTXGax0LLyZhsSSpMS5Km1N21l3pLKCgdOkEHeA024FXNo3FkWpQoWIEXFvGGDawudrc4uj%2BTOFUcg%2F93GQYXwxTcJSE7IyLCiZxxtanFL2CUg7W7723gLPmirpKJKp63vknNcvO%2Bj8oMaJ6MnaOrZzA2H8YU6Vbr%2BNaNh4MpeCEzRdU6604sbhLaFBKQpNrm199os1P4f8AKt2Y6FWb2H1OOdUJCZsqJ9TP4oDmpSNo852O0b4zJytwJhbCy6hSKyqqzTjv5lm5NRVJPM9HckFQSvWF3SQQLWjRMB6mXrAAGPWmZ6tri8WdRUk7KiW7nPXAXgzG%2FMR4plalqvePLqc%2FVI3fljl%2FgvFOXqJ%2BpUh9VWM%2B6FTgmLtqlghIS10VtlhYUrXfcbW7YDSPLnG8clUNnDqukKQoiyL8zd43%2BQCLj7kmCtGoSri%2Bt2qtF4otCpmHZFynU6QTd1SVF4rJUixvpSOVrkwGO5vlfsE0xdOnoOr6enJMaUKCOcdM1nCVFxNTW2azVjIqkUKW70dOmH7NuudQurbSUo66SEg77mLAzkvgl9aWJbEbr7yzZKGKTOOqJ8yQm5gNCKSdMUW1lK%2B3443dmNlzgvCuAZCZpa35iszU4qYTPtTAVJTVOW0nowlsgLbeS4HNWrYggbERpNbdt4D0ImSntip4554tqypMSBxfaYC5OzStOxMeUlaopHpFDa8dCYNwHgDEWXVIW9hYNVlqZdVNVFEyq04wppAbZU1yQpCtSisG6r25QHPpaUe%2BOgMo0tu4OSrfS222m57D75tFf3JsGpvop61fbWcItF8pNIl8PSJp9Nl0ttFYWpRJKlAJISg9lhcnvuYDFM67e16nNhzV7y33fqixt8UaRU0AbWjpur4ZwvielygxLWZyWXKjxZKZakuvp0lRcAW4khOrdVrchcRa5fKPK97rs1yrPFsFxz84ZhVkJFz1Qfl7IDnV1tWm8UW3LGN25yZf4NwjhShzeHD4zNT0xOKdnUuK0TMt70pizZHvSkArSoXN7jlaNIuNkE6RaA9iJiw5xEzF%2B2LerpB2wSXD2wHpeeKto8x3vESF9sdEYWy7wDVsHUuYmqChFQa6VL8yl9ZM0F6CjUg9VBbsoAp5hW%2FIQHOZQTzjpHLicWmguypspLjEkkG5NtDf%2B4iZOVuAnho9i3lK%2B1LlhF9pdHpFFkRL02UWjSbOqUsknsHq2gNlcOy1e6vJMOIuFSM46e%2B6ZdY2jXfg7SyM16mHEXX7WX%2BjPd763f5I2Vw8oadzSkl9IsPMyM%2F1EjygZdYMa58HwA3nFMoSkEOYYeUrzDW3HlNNYzwO8fwulhn6TSzrjtAGfBIIN8PyHpHXdjnVHbeOiOPABOfZFueH6eb2%2FdOxzwOe8bein6lu38Pvlq3r5er0pXxeRmR%2F2Sx8kd954laeFuetpLjuAUMpChzUoS6QB5%2BttHAcyU%2BKTKVKsno1G47rR3vn2lxXCtMtob1uPYPk5ZtFr6nHFyqUj448xpzOWIXH01e2hvXHPua2y83vcE8SMhP07M1qnTYAmJXD9DZmQP1VEihK%2FlTGrap%2Bg%2FufxxuXiR6NeakwuZGlbdHo6LHstKI%2FLeNSVdDTkslts%2FCEfQbD5GiPNHsc21nOufTLHSFKOqJSLRdJeVbDzPjCdTXTNhwd6NYBHxRWqMtSWpOpLl0OqdRUdMoq%2FVEuOk2P7q4T6rxlY1lse4xPF%2BqVPosvM1luVS6WmmmVSZWryFKWjVq79iq0TCRoiS4fzQkIoiX0p1C%2FjehJJN%2Fg3KokY%2FCMglJCjqm6Wh9D3Rrk1qmutzeHS6Sk92ze3p74kp8lSnE0IzLbylTM08md0qFlNhaAnSOw2KoCxt3Cx%2B%2BEZXJpWmRmEt6ukLCw0QPhW2jGej98%2FhFXqBi8y8y6lslJcICbgi4AFriA2rmlIPSdAyrbfS2lTmX8k8NBv1VTk2Rfz2I%2BSNPV0lDibdt43LnTPh%2BlZUJbZW2Gct6Y0SoEalCYmbkX9IjTNU9%2BcRfzxQWobwi6yElJjxkzwWUiTfWzo5h0JugnzX5x7ZKRork3QRNpfKH23TPhP2wW5p0%2BawTf0GAsESkDsi8yErTX2KSH0uF16fWicKeRYBbsE9x6yvkiR6Tphkpl1pDnTpqfRNm9h0GlRI9Owi4tEQIvuIv9Sp9IaNe8XS8DLPoTTzruCguKBC%2B86besRCbkqGmZqSGPGEstyKFy2o9YPkNFV%2B9PWXb1QFqpdjNttrvYmMsqcu%2BGJJbWsATSEOaL7A3Fz67Ri0q2ph9LqOaFRfBU55ehLy1kFxJANhc9hgNsYnkJuS4ZsKuzBAbmcwa%2BWbp6y0pkpUage6%2B3pjQ84TrO8b%2BxtOqmuF%2FLIKaPXxTiR4ub2JKJcW7uz5Y0O%2BxrUTeA8Bv2xCLouVk0Up19WszSJhtKBfqFsoUVX8%2BoJt6THrqVOo7LlfTLqmEmVLapEG3IuAKC%2FQk7QFghGQLp9F8YfQFuhtNKbfaJPKZKEEg%2FublXyRTap1GLlP8AGFTAbmKa%2B68pJTcTCel02H2vVRtzsTAWOJRF%2FkKfRn%2FYQTPTIE0%2B4mdKSLhAWkJ0X7bE8%2FNHhcYkfYhLzanfHPG1ottp6EIBH8K94CtQEqXMrseSfyxdmmlzVc8UW4sI6C4HebxY6ct6XdU42TuI9CKi%2BJ5MwlwhxKQB8fKA2q3TX5Lh9x06tnSyvGlAbbcINlKTKTpUlJ5XGtJI84jSrlzG%2BUzyp3hQxNNE2EzmHTAW7nqqRT3QpXrMaO8Wc7oDxxNF5ZkaR43INvdOlt2UcW%2BUnfpgHLWv2bI%2BWIyclR1%2BwS3w4C%2FMLTP2PwAtNin1EwFliBF9xF3l5GmGnS00%2Bp7pjUCw8lPIsaUnbz31fGITklTW5aruyqnSqXnUtypUbXZJc3UO%2FqpgLPEtzGQTtPo4fqyJQPhLTbfimog9fUgLCtu4qtHgqcpKNOt%2BI9Jo6Bkr1nfpFIBX6tV7ea0BPJrc6C6TuSSbdsSMLmCs6iSnVexirJocVLpQlNiFEbRVQpMq6hei5QsKIPbAbIwlQ6p7jmYVbLQTJzMnIS7JUoe%2Bqbnm1OWHckdvp88d9cUzaGuGV1IAA6SiJHdslEcI4bmlTHDvjRp1y6ZByTZbAvdJcnQvT6CPxx3pxahCeG5XRC6fGKMfVpRfaPl%2Bl8Z47hcR5Sr%2Baxdy6ZRdbafNT%2FycDgRKoEcomTEyhH1CXDUd%2FPCx7onhAQHKJYniSAmHKJ4kGwieAgqCecFQTzgJucNJgnnFVKYCS3k%2Be%2FqiGkWiupCNIJJ22O%2B94goJSyHnFoQ3puF3uD57wHnI7IAbRVKBfb0xTUbG14CU3idIvEsVUCAtVZqi6a8httYSgjVeJaLi5yam1SU690suUda4F0WNgr0xcqrIylZkEyEwhPSNqLjDvItX8oedJsNuwiPbgmcm8DyGJKbSm6VMMYqpZpM85NyKX32mSsKK5dxX2Fza2sA7efeApufwbfBUO2KKwe6K7i%2BkiQ6bdfqjv5wHieHVPVvGNV1PvLm%2FwFRk0x5HOMcrw%2FM7htfqKgMHj3UmUYmpkmdf6GVZSXX3ALkIHYPOdgPOY8bce6XlZmak5tEqwt0MoS%2B8Ei%2BltKhdSv3IJFz2bQF5bxnVJQhGEpFmlyrd0IUiXS88sfu3FpNz6LR5q9VavVkSr9dk2Q8kLSmYRKIZU8Odl6AAq3YbXEeykUer4gwyulUKcDzspOOTcxTumSgkaQlMwgHyxbqkA7d294tVYolUobjDNUbbSt4EpSH0uFPffSTp9cB6X8XTM1ILpb9MpPQLQlF0SCEuoKeSkrG9%2FP2xTpNYk6NLCYTTJeeqK72M23rZZR%2B85LUfPsIszZ98Hr%2FFGY4cp8lXcOqptQpL7RZmtUpWZdsuFlRHXZfQN1t8iFDdBJ5g7BTGJcX1GmpXUmpGYpj3SsIU7IMhpKtPWCSlIKVAcjeLNSJalNsLqVaLi5RnZDCFaVzDp5Iv8FI5qPdHpYq8%2Fhp%2BZpbMxLVGnuLtMyurXLTI709qT3KFiDHgqUk6llUxLsvGTbmFMoUoXCVEBQSo%2FbEfHaAvgxzW0ttytNo1GkWSAUMopjbhWOabqcBKz577xb3dddqqHJtmVp2tsOTKmWejQ2hI6y9APOw5DmT2RcVYfrmI5WnTdKnEVJpqVblQlb6Urkyi92lBRFkgklJ5WMWmYpdUlZl6RUEvOpYUtYl3A6FNJ6yrFN7gWufRAXRGLJ2lptg%2BhS0lLlPVmJiVS%2FMODlrK1gpTfuA288V5irJrL4omOaVLyM44lJYqUvKiVdZWsAoU6lICXGjtvYEA3BPKPLQJWo1zDz9Bp1VutudE37GreS2h1IQQHUEkAqTuCL8jePHiX2RdVJ0ycqBnn5JgMJQhfSCXQVkhpKhzAKibDYajaAskxLTElNvSc2nS8wtTbgveygbfFtEsV6mp12ccW%2BT0wsly%2FwBsAB%2BSPNAImiWEBdaPhus11SE02UDgccDSVKcSgFZ5JBJ5mKErSZycmHJVpizjRIWFqCNJBsb3tbeL7LSbLNPo7FWwvMTPS%2B%2Fyk1JLsp9tSt0r84IO43EWepyryZ%2Bd8XafcZbmFJBcGtabnYKI7YCNVoFUorMrM1GXShqdC%2BgWhxKwooICgbHYi4594jwNmKsxLTkuw307bjbayVISq4HcSB%2BWPOiA6D4RU%2F2UYiV2ClpB9HWvFmZZUvhirbNiSvHFIT%2F6Oa3%2BWL%2FwgIJr2LFDmmkot8ao8dPmG5PhhmaglGpQx3TrBRsCUSUze%2FqMBoTxJ0t6wDu5pTt5USeKvFJWEqsFaL6dtXd6YyWUrnijUi0202VSMy5MMrP2yhuD3iJfZYsNtsNoSlLU57IJT9q52j0X7IDHDKP9yvK0cvhd3pgqRmEgqUhQSlQQTbkT2emMiXWC4HNSG7vTyZ%2Fq%2FqoHZ5ohNVpTpmveUpM4%2Bmac08g4LEWHdcX9cBjjkupHSpKT1CAYj4o4gqSpKgW%2FKBT5Ppi%2FzFWVNCoLKUpNSU2pxKR5JQbix89opTk%2BZt%2BcddQlJnkhLgCjYFI2tAWVcu4gr1A3QBqHcDyiTojysfJBi%2BPVFTzkw4pNzMS6GVfweRiRFdDE30%2FiSFL6IM%2BUOSeRt3wFGXH53ToIN9DZH3QH5YryrZXVW0pG5cNvuIlncQKnpNcv4ro6QJ6wI2AIPIeiPXTamXJ9tQYa0rXc%2BpJHOA6f4HE6p6TT1b%2B3GRVuewU%2BZ5fJGU8ba%2F8AhDw%2ByCCE0dxZ7wTML%2FIIsnA10jk4x1ElDWL5RzzgmnTO%2Fo3i78byv%2BEihDvol%2F8APrgOeGP0ZLjsL6AfMCsXMduMOPSEwlkpbdb0pKXLEKBHb%2FqjiWSBVPyoFrl9sC%2FK%2BsR224S8klSEo0Cy0pNxcDv9UZbD5SfQxXjXZwuEnPql3UdAnUVXICN9PabmNt5YZlNUYolZhLjjallDyFLvqb7LfukHkTzG0aXlVMy6S4lxVykgA%2BbfeAm1Je6Rp7SVHY957o3fS5su2ZWpSVQlkzkhMJeaXuFJP44riYWpISi49EcnYWx9XKClLcpOuoUl3UpAPVcH2pvtaMvTxIzFOFqvQQtSdrsPDl32MZaYpmNqJrmJyiM2%2FVyci80pmapss8herWFsIOu%2FO%2B294%2BePEJgT2m45rdOYl%2Bjk2VomZQJ7WHPJA845eqOhK3xUqTJuv0SgoDibdEqbdITz3uB%2BKNE47xvWMdVNVZxG8y%2FNOI6JPRtBIba7EDzDzxmimizonOdvgRTaWldpE8HVG3NpqhUZtpa63Nt%2FmtxOmTQrbokfb%2BdR5RVm9HRrQ436NPfF%2Bn2PfOk6RKv3PcBytFhfccXqbWUq1RoS3onNZKppNOmgFX0pJG1iDcbfjjHpJrrpv9sIy6rEuUx7pW0p6p06duUYvLtrOnT3iKVbWWnXDTVZTpr1WHdNOD%2BVGTZi290aq6fJ1s6fvSIs9ek%2BjrlWcdXLhLj6136S17m%2Fxxc8Wl6axpPPLT1lLbN77HqJ3Eas7WXbDYuV7CHKgttZsEyT5uewhs2%2BW0WWudZ0emMqyll3U1QhCNanZN5ABFxcoNox%2FEjDjboLzZSruAiEsRnE3HkiLRMMEnkIv7zSV%2BSq%2FqigunuK3CR8UBjy5ckbCKBZWk8jGS%2Bx7g2U38kQXTL%2FAKWfigMa6M9oiUptyjInqOdNwgj1RZZtgsKI7RAeQpBVFaXStLg0xTQCTeLzh%2BlTVWqDElJS65iZfdS0yygXU64TZKAO0kkAemA2bkHwz5i8RNZnqLgRqnNGlywmp2cqL5YlmEqJDaSsAnUsg2AHYSbARr7HGBcTZe4oquDsW0h6m1iiTa5KelXbamnUnsI2UkiykqGykqBHOPp6mo0PwffDNSkzNKarOMq5NNTM9JhzQZybISp9Gob6GGjoT3rNu2MA8IFlTQc0Mv8ADnFplqfZGRep0rL1h5lO71McP5lnFgfDZWSw72gEX5QHzdWi24iS5EXGdlegdKSLb2i3uItASoO8VNJVFHlFRCyICk5PnVoYYTpTsCon1xWZfbfT1UhC0eWn8ojzOSi0OdGOv9qpPyfJHplpcMoK1KutexHcICO%2F%2B6Ybnt%2FkxU0xs%2FJXI2sZ0S%2BNn6NWqfT1YIwzMYnmETgXaaZZ2U02pIOlZ7CrbvgNWFvzRIRba0bIwjkXm1mFQJ7FGBst6%2FXKVS0lU5NSMqp1DNk6iNvKUE7kJubCNfvMEAKG4UNV7Wv80B5NG9483j5%2FS0J0%2Fuuce%2FQQQ2oWC%2BZ7o8k3TXWH7BJIULhadx8cB6W%2FzRLom0I0JVdPrHOIIFonYR0Eolj90VKT3GFj2CAyHAn%2FABsoP%2Fm8j%2F8AcNx0p4S2x4uMUHukaen%2FANK2fyxzfl%2BlRxfQNHlCsSBH4S3HRXhJV6uLfFY7peR%2F%2B1bgOT3EHUfPEvkILh%2BDFdzyok0a0Fv7aAkS866ApRTYdgFrxNueyJRLPJcCENLUPMLxXDW0BSDYPMRMGU90VQi0bIw1kniLFOT%2BK85KXPSApWDqlI0yflXXFJmXFzXkKaFtKgDa4JBtuL2gNZdHbtiXT5xGdHKDM1WB3MyW8A15eFWl9GusinuGTQQbXLgFgm%2B2rl54w1yWWhelSbH0QFHpG22%2BkWfJ7I8bddmW3AVNMLbJsUBNjbzHvj2Ot9Ijo%2BceNFMXrvoVvAXSYCG9C23elbcQFoI7j2HzxSid9OkNtnfQm1xyvFIkwFTpB3w6TzxSiI5wFZK7RPrudooDnFRIgPQ2TFdJPdFFoR6AkWvAZlTP7VNegxecpmk%2B6lSppZASwH3FE8gAyu%2FyRZaafzqa%2FemMhyobQ5j1oOLCUGVnNSj2ASzhJgMAn6miekV0%2BTcU3KtS9ysb9MvRcX7h3RmnCR%2F8SOV%2F%2FwC91G%2F%2B8ajXzkqGJc%2BLvlQ6EDyCbXTyNo2BwlahxI5XhQsr230a47j441AfodhCEAhCEAhCEAhCEAhCEB%2Bf7jpN%2BKLMpJJuMRTv84Rz68dRZuBbQ38d46B469uJ%2FMoi5%2Fshnd%2FPrEc%2BOW1skWPvSQR%2BWA2DSvsW32ifxx2hLZ04fycwBktiusVnHkxUpbAS3pDDFNWPYWqJS6%2B2BOBRsLrUb2B6oEcXUfyf4Ii8z1arNVl5CUqtWm5yXpMqmRp7T7hUiTlgpSgy0Pgo1KUbd5gOmMNYblcNz%2BUGXlH4faVjah5j06nVXENceYdXMzD82tRmWpR9B0yjcok2sftN49mI2ncM8PWGKNgjFeYfj1Kr2LJDDzuF1OGWnmUVBSNc%2Bps%2BQW0nSU3%2BFtHO1EzNzEwzh1%2FCWHcc1um0aYCwuRlZxbbVl%2BUEgHqg9um149WFM5c2cCUNrDWC8xa5RKUyVluUk5jQ2jXfVYEG17m%2FpMBvbKJlZ4JMdsyMm6847ixCQyyhS1qVrYuQBvsOcaxRRsR9b%2Bx%2BreUf7hd%2BaPRk9xL43yVw3MYWwpRaPOy03UHKm%2BueSsuF1baUGxBtbq3NxzMb%2FwArOL%2FMbGOCM08S1uk4fTNYHw61WKc1LoWEurU7oUHgTfTyNwRAeTg0plQksc4uRP0ydldWHAEKfYWgKPTcgVDc232ji18DW6n%2FALZz%2BeY6cmvCB5ulOhvCuE9YChrSh4jcEctXnv6o5g56v3xV8ZuYCSO4cg2w7whzSDyMtiK%2FxORxASI7k4YjL1PhraoiXQlb8xWJFwncIU5dP9MGPmvwoTFGGWFdWyLWP5K3VwifxtUeGmXJ%2BVzY9w%2Bup%2BG7Xaef31pbf4rxbC49J46w%2FPtOOMCVYmT4w2FamlEpAIKdwefKNq5bZKZ3ZdS1VoddydpuNqVNlnoWBiQSbbT7N09Mko3VqTYWNrWjL28H45SVW4MaUANwDjpZsbW9cejp0uwPL8G9Wc%2F76Y97DOG3vP5Kr7IajcqGGUkpcxXJ3O5HRuH%2BjHonqvJzZp7svOqmww2EBwoKQUpV1QL72tG004Txupdl8GVEHSb3dxq5b44oe1bHNtP1G1F37fbk7cHzb7RPHDBZ%2FarP%2FwCSnenvXe%2FJV9FzZUct53ElRaTKVGnS4mlr0CZdLYbutR65tZPpPmjWeIaD7DzaGEzAeS40lwK0lJBI3SR3gx3CrCOPXJdxlvg6oqXFIWlKxjdYUgqSRqso2Nr33vGr5zhlzImpjpJrImYdCEBCdWLWhYDtJCdzFZ0xwaP2mz%2F%2BSjtLU4Ve6vo6o9MS5WMuL%2BV8kVW5RKgpdj1UkgfbHujqVrhZxu6NRyBSj99jJIP82DvCpj0AJRkMxco16k4wSfVy5%2BaKcdMFjbeKP%2Fks%2B0mcIvcfMnmnc1kMlJOh4gl1S%2BYFKqbEq%2FLveMyLDy2VnQlxQSVJSeqolskgdZJtcbxn7zgdcUu466tUbZ9pWZCGktnhIwsopQhGr21vXNhYk9fmYq%2B0bMhXlcJmFB%2F%2FALa9%2BRcZI0wwaf2mz6dO9Heu8%2BSq5vvaiuO2PHihp2YwxVmGEFbi5J5KUDmrqHYRuhzBGaTnRkcKmExvbUrFby7j75tF1Tl9mEro2n%2BGnBBUu3LE0zt6SFRWdMsGjZeKJ9FdO9NOFXqrPOzqj7Pvack6pSXaTTnZ%2FFDEstEmy30L7bhU0AgAI5W27or%2BztGS0qSpddTUC4oKUhplaUelRUAB3eeNjzGAM0W5lxljhYwa82FWStOJn7EelTm%2FxCKQwPmwhehHCtg3SOdsTu79vMOw444Py3iz6dO9WcMvMfRVc33ucp7LGaxFPBaazTpMOuFsdMpQS2nUSCtVrAW%2FJGqq7RPYyf8AFUvFxPRpXqItzF47lRgXNdSVpTwrYPaDgUm%2Ftqd1AqBFwekNrXuL7XjXx4U8xakQZnJymFTSQ030uLwCUp2sLAb%2BcxMaY4N9Yo%2ByujetThN6qjPgVR6Yn73Jglh2i8VEyqTsU33AsnmY6ua4S8edIllWQ9LJUAdSsYiw9JG0JXhUx84FNjISkMOFJQlbuLjsfthva%2FdCdMsEj9po6dHaJwm9Rtpnmnc1ojJSi0bEEjMUvF4n5eTdZdL6JRxAcKdKjpSrcAk6d%2B1JPKM76UOazcJ59Xu3jbwwLm8ykSf1KeBHOhCWyo4kdXrskDXs7ve19u0mHtLzcWoD6kvAYSRZYRiRwfGeluImNMcFn9ps%2BnTvR3qvXkq%2Bi1GwodJzEWzGLTs7g2sS0uy4uYdlVpbaSkkqV3C0bvXg%2FN9pBU1wm4EUW0hQ04jeUTc2sPfdzF1RgPMvxKXXN8MOCxMPoCy2nEEwro9%2BSj0lgfNDjhg07LzZz%2Fvp3p703rb8VVzNPs1mjpkpE1OvLlnDLNAtrlXnSkhIuAUgiwj2UrEFEdfLVOmpmc0AuqJllNoT3XKrd8bHfwxnezMJZlOFfBLzKLpaIxE55Pdu6LH1RSFDzySkhXCjgdSAkpI9n17%2Bvpd4Tpfg8ftVl06d6ney9%2BRr6P3uZZ%2FKmo4grLbNQq9OpUq%2B84FzU0tQaYHWUFuFIJCTYC4B3IjUNao5ptSekQ6VhogBSha%2B147yNEzmMs7LnhIwT760por9sLuoBSSLi7pFxfbaNXDhczNn3%2BlfyFktW%2B8xiwG1uQvfeHHHBfrNn9lpRvO9d8mM4squZyeZbvidqVKiW0pBXewubAnujrZjhEzMUoKdyOoNu0O4oO%2FxGK54UMyUFKGch8OtKBFle2pRvvfa6opx0wWNt4o6dO9k7z3zLP4urma5kMmqdhTHTE3RMT%2By8hSptp2Xn%2FFFs%2BNAJSokNK6yLKKk789N%2B2No7T%2FNenrFXPvMbHVSuIFNul4YMstrCwqTlja29um80QFP4iwoKHDbloCOX55LsP8APRbjlgf1uy6cInCb35Krmje1x4qGbpCblXfvf0RZMdU6aewVV25GXLs04yOjZQnrLspJ29QMbqDPEgj%2FAPpxyz%2FjJfW9Hv0eqSYz%2FccT45w9ZepBSTdqfcI1Gx3982iKtM8DpjPuuz6cLRhF65bOrm%2B9pNWIsPJZaM9UayhaWUJLYprjgTYcgb8hHsomM6S%2FUZaTpDlUm22EvTCw%2B0ppCSpISLJJtckbnuja83K8RTK0hXDjlq%2BlQUklFRc1AE8ieljxFjP1N0jhXy9NxYkVV0Aj79e8RGmeCzsvVn06d6s4VeY%2Bjq5vvcyTeTlTxNWHXZitScky%2BXXFOupUUoA1qBOkE9gHLtEaarVINMqL0gTcskC9rXuAfyx9AOgz9XKvyZ4X8u2UPMOS5KKo4lQStJSdJ6U2Nu3nGpJjhdzQn5gvzOSdKWrqpBcxMomwFgL3hxzwWI13ij7K6N6Jwq8%2BTqj0w5LLAG3bFeXlA4ttJudS0psnzm0daDhJzJ%2F6jsO9U3P9lC9x3eXFSX4Us0mJhqZkMkMNsPMnUFLxMpQN%2FMV2%2BOK8d8D%2BsUdOjtHeu8%2BLPM1jScoqXhvFspVpTEipmVpswh9DniqkqcsPtCbp622%2FdeM0DnSOK1xuxWGs%2BNOp3hcy2ULAG1XcHK2%2Bz23KKKsP53J0oHCxlqQBsfZd3bzfZufyRPHPBp2Xiz6dO9Peq9cllXzfe04EMn4QiC2SDqB6npEbcmcI53P9ZHCll%2BFH7StO7%2Bf7NFeSwvnoy8HEcLmXqHB8JVYcKTbzF0iM0aY4Hl%2Bl2cT%2FAB071Zwq%2B8ljVzNW5xqCuFzDKUG4RjxSVWG1%2FY9R%2FEofHHUfBjMS7%2FDPTBLEnoJCpIdJ5lYmHCv0jcD1Rz5m1khxAZlv0alyeWmFsMyFHDivE6XV1Ll3XXCFdIsOLPXSBpuOwkR07w44BquUWS%2FtRxJNyj05LSM%2B%2FMLllFTSelKnCm5AvYXv2R4LTnGcPxO7WNndbamurh0zlE56sqterzzDpXG7Wt2oqm2py1T7nzqZVq0K79R%2FlGOleBBQTmxiFV9xht0j78iOZ2PIT3WVb0XMdI8C7qEZr19snruYZet6A83f8Yj2Wm%2F%2FAOP28z4Kf5oc3D5%2FtNM%2BefY9uLHSOMDNH4Rl8ENt28%2FRy%2B3yxo2sTAkJKTm%2BjKm5aqyy3rC9k9aOn8wsls0GOI2fzowVR6TiGkVmlJkqlR5yqCQW6CwG1p12OwUhK0qG%2B0eF7BOMmFgs8IuF12Frox07b02I5xytG9K8HuuFXewrvFEVU0UxMTVETExERMTn52zeMOvFtaTXTRMx5tfvaWcxTgNxfTO4kmlLI1EmmuqVfuv3x76HW6DV1T8nR5%2BYebQ0yErdZU2Ee%2B6iN%2F8Ae0bTVhDG4NxwdUBtX26cdr%2BYxE4VxqwvqcIdJXq8pTeO12%2BIixjvccsG%2Bs2fTp3sHeq8eTq5vvc9Zg0Cp4qrK5htAeaEsxqWhW4LLOgpA7TtGpMx8CjBFafoTz7T81KudE%2BpmYS81r0hXUWnZQsobjkbjsjuBGFcVpcC1cHVINjewx24AfNsI17ivhtxvizEMxV3cifEm5p1b%2FiftxQW2So7oQro7lIsLX3iOOeC%2FWKJ9FdO8pwy81fMmPTH%2FwBuMSyE7aYiiXK1WAjsJjhBxWtVzkfIJKtkh7Gm4PfcNiK8vwf4vbWSclaGVA3urGC%2FyJiOO2CRtt6elTvZIwe9Tsp9rRFHyWlavg2jYnkq9KTLtXl3npiUbKg5T1ImHGktu3FipSUBwaSQErT2xv2mzKW6VS5Bx5LhpdPlZHUPJJbTp%2FJvGwcKZbZm4Nw3IUBnhpy7qSKaFoafnMRvLeIWsrOrSpIVYk22va0XJqiZotElPCXlxc%2FCGIpkX%2BJcU48YJyXmjp07ycIvUfR1c0b2u%2BhDnvd9f21ouVIp96lJ6krQ30qSVnbtjOUyubTRCm%2BFLLoaftcRvg%2FKu8e%2BTns3mEXc4XcDIdB6hRiF7SfSCT%2BOL06a4JV%2B1WfTjerOFXnls6uaN7k6g4toUpICn1uen5Ocl3n0uNmTWogdKreLkrF%2BGyhtEhN1GacfcbQlPiK0BR1jt5R1BVKnnRPrUn6mDAbwIBLiq%2BoEqtuOV4tjshm0%2BW1zPCzgdQRchIxU4mxPPlDjlg%2F1qy6cMc4XeI%2Bjq5o3ucc2sJVvGmM6rPy7CFSkw%2B24khYChZtKCkg8rFPyxpLMrBSMF4jfojc03MrllrZecadDjSlpO5QsAak7jf0x30ijZj69TnCbggnUFX9uDwv6bRq%2FFHDbmBi3Es%2FiOfyRpTS6g%2BuYVLIxeRLslR8ltOi4TbaxJiJ03wOnbebPp070xhd4n5lUemHFXQHuh0B7o7Jb4PcXlKVe4nh%2FUAb68Yr37uSeyJ0cHOL06ArJnDSiD1j7bnbW7vJjHOnWA%2FWaOlTvT3pvPizzS0NTMk5aqYVotfp9WRNO1eRM040m48VdDq0dCq4FyQgKuNrLA5gx0AxNtty8qyp0EsS7MuknYHSkC%2FyRsPCuWOZ2FMMyGHU8M2XlRapzamW35rFD5eUkrUrraVAG2ogbcgIuTeGMz2wlA4UctdKbmwxRMbnznXCNN8Cn9qs%2BnBGE3rLXZ1c0b2swhb%2Bpz7ePdT5TUFhG5N0aR2nsjZCKNm2gJSjhby5ATy%2Fspe2%2FlRcZSUzVQhJmOGTALbgNk9HiV4keve0WjTXAp%2FarPpwnvTefJ1c0b3JWEqjSZXDsjS6vPTFOnZQOMuy7kk4dKws7AgWi9M1mipfl2ZeqvTTi5pj3hEosA2cSbkkAWFr%2BqOnZgZ0OzSlI4bMvVNkgpKsQuagR3m2%2FxRQXQ80pgHpuGLL5VuY9tbyQfVpis6bYLH7TZ9OCcJvEbaKuaN7lfNfBtWx7jio1mSlQmSfcSSvXdwq0pC7J7hbnGlMxMItYMxXUsNtTjM4mnTK5bxhhwOMvFJtrbUPKQew9sfQ9vDeYrakFPC5l%2FZBGxxhMb2N7HaNTYg4Usb4krtQrU3k9QG%2FH5pc0JZrGC9DBUokoQejvoF7AXNgO2I484H9Zo6Ub0xhV4n5kx6Y3ZuIjL3idqUClWjthPBTidbWlOU2G0uKNwtWNHDb1dEIgeCbFW%2FR5W4bSSbg%2B3J07d32OLcd8CjbeKeeExhF55acvslolrI%2BnuUShVSj1OWqblWpbNReLDix7HvLKgqWeCkj3xIRqOm4ssbx0AKsqalWkKFlNyzTSj%2B6baCPxJBjZVGy4zGwvhql4cb4csAT6KYwJdD7%2BLphbzoBuCspABO9tgB5o9CcMZlt6izwzZetKURfTiqZsB2gAg2vEceMD5bzR0oW70XnydXNG9rNtvpP33wvni6KpDymOkCFKSUrsACSq6TytzjYKKRm22FBvhyy6TtsVYmmFfk3i7y7%2BcqEgP5B4BJRYtaK%2FMEC38DaInTnAo23mjpQjvRevJz1b3IVOrFLVIywnqs%2FJvNNBtxgybpKFDmLAWEe72epLk3TJGRqE3NKFUlHFI8WcQhOhwHVc%2Bbtjq2fczqmtb73D%2Fl48VHUfz%2BdSsnv%2Bxc4sD9KzRmD0kzwwYOWoix6PFq0X%2BJuLRprgtWy82fSVqwq25aaub73K2a%2BBq5mFmJVKlKtMdBOuIKFreCOxKeR7Bz%2BONIYvwuvDGJalh4zLUwadMuSxfaXqbd0KKdaFdqTa4PaLR9FpekZitOpeXwnYPcUhaFJvjFfwTe32ONM1%2FhQxniKvzdZmcn1Nmefcfdb9uLagFKUVGxLfk3Jt22ieO2CfWaJ9FdO9TvXbzspnmcZLl0g22MQblgXAm0djngvxMFdInJyXKPtTjVF%2F9FFN7gvxOo6ZfKUMpJuScZNEjzD3qKzpxgnl6elT2icLvEfNnmnc01KZQt0l6l1in1ZqdS7LMzuptd0tKWDdld7aXEW6w3AuNzeNpOTHRo6NtxtXRJCer8PSkC4jdVFyrxjSaJTKHUeGqmVV6QlGpVU%2BrHqG1zOi%2FXcAZslRuAbbbROvLPEDrRbd4WZMXOq6MwEhQ82ror2jJGmeDTri8WeX8dO9Xvdb%2BJVzNGuTaHHN9P2wSE8vNHkmFBauVo3wvK%2BrrcUpXCiyQre%2Fuj7j0e82if3KaujS43wvyqiCbh3H4ULH%2FAxWNNcFmcpvFHTp3p72XjxKuZp%2BruKTwqZqIKrJXOUUAd5E6nn5rRnng03D4zjdq5t4zTHLW2Bu6L%2FLHrzHyUzTxlgNzAmDMrafg2Wn6gzOVVxeJxOCcaaB6NnR0YsA4UrvfmkRsDg7yGxZkgiuP4tqFPdfrkzKFuXlHCsNJZ1lSlKIA31AADujymmGlGEYhh1pd7teKa65mnVE57KqZ5PNEy6NwuNvYVxaWlOUR4XN3FQb8QGND3TyB%2FmUR5%2BG5AXn1l6pXwa40f5C4hxMTDE1n3jx2XVqSKsUE%2FuktICh6iCIk4dHQznzl8pS0pBrzCTqNgbpUAL9lzaPR1xMaIxTlssP%2BDmWE%2F2yn0x7m5vCEOE4nyhl%2B32ddX6%2Bmlkxr7OporzVxCFarmYJue3dW4jfHF7kRjLO8YWn8FVCRk57Dr8ysibeLVy50akLSbEEpW2CQRyi0VfCOPKlN%2BP17hXwpVqm622man%2Fb08kzDqUBKndASANagVW7NVo8%2FofpThVwwqzu9vbU01xNWcTMRl%2BFMxt8zdvuHW9tbVVUUzMTPJzNE0Sq0SYosmqpYhZknGEFKmnWlnTc94Fo9fs%2FRGG3JSQxC3OPPqbBlW2VhLllXuSRYabX3jb6MHYvS22TwcYTO1ikY3fFviESO4MxelzUODjCq%2BkAV%2Fx4fsi3ZyEeo47YNH7TZ9One1Iwq8Z66Kub72gcbNOVvCU1SJFoB52oImUFxWwRoUhQv2c0xqLEuU0%2Fh7DMpiqZq0k8mdmnZUSjK9T7BRoJU4nmlCtY0K3CtKu6O2ThXGqnC4vg0wgokWucavf%2FAI%2BSMax9lLmNjWnScjJcNNDoTUsXQ54jjRZLwWoE6gtJ6w0gBQtteHHXBPrNn06d6%2Feq8eJVzbnCrsghJtsYpGSR9rHYctwoYymEdI7kDSNQJ1F3Gqk3HZsAIqHhIxidJTkJh5AG6gcZuEnzX7IidOMDj9oo6dO9MYPep1RTPNO5zbgHLOTxdSq5UJjEMpIzVKEmZWnOtrL1RDzhQ50SgNCehSOkVqIunlcxtrL6gHCdCmKSuYK1OzqXrEW0p0W7I29l5kXmZl%2FMTzspwyYOq7c%2BgIUioYsccQ2Um4KQFA39N%2BcZQuh5p69R4OstrdwxE%2F8AkciOO%2BCz%2BbebPp07096LzG2zqn0Rq65hphxCFrIJBtEipdSthcjsKd7emN1N0PNcABHB9logA7asQTHLt%2FTY99Po2bLIcbc4U8sZZAR1LVh9wkg7D7J3dsROm2DR%2B0WfTp3kYReZ%2Bjq5o3tCMTshJ1F9iqz7slLzMq0A8hhTgKkrXsQncc%2Fli5S2IMI0l9ioSmM3mpiVUlxpxqQe1JWDcKHV53jeE%2FR80Ura8R4UsrH7j3xT9UfRv326T5bx4hQc4Ta%2FCTlMLnSfz8f6o7%2Fsv4ocdsGn9ps%2BnCveq8Z5fF1c0b3OmK5ZzFmG2JOXeDa%2FGXXmy4CNTbpUST287%2FHGpcY5XqwtRqXV1VqTml1B6ZaclWgrpJTolhKSu4sQ4CVJtfZJvaO41YezYacCjwh5QPFA0pV7MvcvW7GHZg5O5t5guyBmOHXA1HTIoWhKKZiNxttwKN7rSVquocgdrDaJjTbBuW82fTgnCrzyWVfNG9wu%2FIoQq20UvFEHYWjsdjhKzCUkBWSeDVK0ndzEz3PvPW%2F1RWb4S8xyA6nI3AoUtekoViN46QO09e1j5orx6wTy9HTp3rRhFvPzZ5nOWAstKDi3DdSqU3UlS0%2FTnWWkS5ST4wlwqupKuQKQkbHc6tuRjamEaSxhqiexctMghCybEc0kRujAOSueOXDdUNIyMyqmW57ogpmpVNyY1FskhbXvg0Hexvz2jIV0LiFupSuGrJK7g6xDit%2B69nt7Qp03wWrZebOPTXHuzTGEXidUWdU%2FZG9ovU11W9Q7Ep7%2FAFQcYN%2BRA74301h3iJ06jw7ZGIV9qvpCfkdi4ydD4gwFeNZEZIISAChKG3tjffk4ey%2FriJ04wWnberPpfcnvNefJ1c0b3O0jPSsvPzias%2FOS0vMtNNNrlWVOhZSolQUB2ciIu8liDDNHm0T8niKroeZOtBbkHGzcfuuyN51CjcQbYaNIyKyZVcnpA606Ld1vfBHibonEk8NLuQGRjYPYtDv9bExpxgk%2FtVn0vuRGD3ifmVc0b3NeMqcrFGG5GipU009K6HFG48ldyQe49YRrHHeWEnhKj0GpsVtqdeq7cyqblktqSqnuNOFCULURpXrTZxJSTYXB3EdxpoXEba5yByKUVC4CkOmxvy%2ByxiGYGTOe2P3pKYq2TmVEo5JNqZaTTpt9hvSpWolSOkIUq99%2BdtomdOMEp%2FarOfRVviEVYReI%2Bjq5o3uDH5BOrYiKHiSE7EiO3pLhJzSW2p1eWGViDbSETFQmln0iy7CIr4Rs2%2Bk0IywynKd%2Bv43M2%2Fn3jHx8wTPL4%2BnpQvGC28xnlPM5pwHlrhvEuDZqtTdcmWavLVBEuiT6D8zuyqm1lTvTX6riFpSkNkdYKJBFo2jhRhihUSXojc1q6ArWtRtYk6Qm3bayd79sbuwXktxHZeszUph7LLJaYZnFNrcRPMuzIQUX06NSxp5m%2FOL2vDHFYVKT7kWQjaSd7UglJ9QcvDj3gmWc3mzj%2Fd9ys4PeOSmere0YHmCCpLqR6%2BcQWtvtjeasKcVYToGV2QJ8%2FsMu%2FwDPi6UzC3FAoKXUcuMiQdggN0ZwkenrHaJnTvA4jPuqzn0TO5TvTevJz1b3O8vM09Kn2pwToSpaVNqZa1oI02IO43iq5XKJJoc8UVV3HFIUlIMqEXJTbnqjoafwdxNuLT4hl7kWlHwg7Q3jc%2BgKsBHgm8IcUzSlpTl1kK%2Bhv7G4aK4i%2FoGvb0mKxp7geWc3miPTM7lu895iNdE9W9zDi2hHGOHKTR3nVSjtJdcIWG9aHUraQNJtulQUlW%2FKNZY9y8kMMexTtPrCZ1ufkVTD6eiLZlX0urQWiTsu6UoWFD7e1to7mcw5xaMFCmcuMiVlQsSilqGnzHUuMLxxklxHZgTkvVMR5eZSqmWGPFx4olbCAgElIKErsSLnfnF%2BPWB5Z91WfS3wr3pvHiVdW9wu5JNA8x8d4omVTfqkR2e3wm50OS6nFZdZThwKsG1re1Ed99dvyxBXChni6hxPuZZSt2AFwpd1X7vfIpGnuCTnleKOlC0YPePFnmc%2BYLymoeKsMorDtbmmKimYU27LdBdgS4RcLDl7lZXtoty3v2RtKiyjdFkJWRZmiUtbFSwDdXLa3mtG4cI5OcUmXlKnKXhrBuT65WcdTMutTLfTHpEApGgrXcDT2DYx7XMP8X6lhSsrskVEC21Mat6bdJzjJTp1gVUfpVn0lasJvNOqLOqebe1JKKLrD7ss42pxKDoT2r3sqw8w39EeVy5l2pxsJS06ryr3G3ON0N4e4u2AHW8s8kOk5XTSkBQv59cU00jjEQnoUZYZMpbvqsKc2AD3gdJGSnTXA6v2qz6Sveq9zssquresvD3LTDOZ1OnFtlTD8jPoCwANNpdzc%2FjjWng%2B7jOaY%2FdYYfT6tbdrDs743BVcNcYuIsPVbD0xgbKmlM1SReknJiTl0MzCEOJKVFpaFkocsdlW2ipwscNWYGVGOKji3FrtMZl3KOZBhqXf6Z1TqlDuAsLC5Mef0q0rwe%2BYXbXewvFFVdUZRETnm3bhcLxY20V2tM0xHhY3x5gjPdI%2BD7ASBH%2Bcv8sc4nmY6K465hMxn1dKknRh2nJNjyPX2PnjnePW6KRlgt2z8X3y496121XpSzdvY%2Ba0c%2Bgc%2Fmx3fxOOmX4SX31XunDVKII5hZXLBJHoIvHB83vTpxP2zDieV%2BaTH0KzuwXV81uHFnBmDUSztRncPUsyyJh4NoWlHQOKSFHYKKEK0k7A2748hp%2Fb2V2xDD7S2nKmKpzmdkRwrPPP2%2FY6eGUzVY20R5nz54j6PNLzNmUEaegpFGY6199NOYudvOoxrBmjzbLYVdKk322j6HZi8OmB8R1ybxHN4azNnXZnoWm2qbTZMlplqXaabQOkmADYN3JtuSeyMXmuHjLKZTvklnhLql0pQOhbpdnFb3WdTxAPm5eaPU3fSjCYs6Ym8WeeUfSUdpq1XC3qmZopmfsnc4gaknQWVKFx0zd997axEkzTZl2nTbLDDiyuoqCCATqA17XHdcR1lmPhLJ7LGTptVxFw55mMB11mVlRVa3JycvOKbcS4%2BFloKVrU0FpBTyKgRyjWmH8xcF0yWqFLewZi%2BSkU1SbmaYzRcSMMlMm6u7bUz0rKw68hICelTpChzF9z3rveLG9WcW13riqmdkxMTE%2FbDStLOuyq4NcZT52o5umVGZmasWaa%2B4p3oi2lKTchKklQHn2ioKJUVLcR7GTBS5TUoQejVYL0jblG9FZn5WpQdGEc0yo2G%2BMJJIHedpaKgzcy2SAkYWzSAtuBjGS5%2Fg0Z1GhGpCcTN04PSL5Bk1BRS2RZVnfnTHjp6OrR1W8h90n7tNo35Us4cBsSDicP4OzCE2llYlhP4tlVy6XSghKlpRLhSk3O6QRcbXEY3hRzK%2BsKoNFXlfiucrzzbbC2KfPsONzFQU6oksII1pQpAbsgkkEK3taK1102dM11TlEa5TTTNdUUxtlpXoz1TFyYl5r7IhxKG3WA2pspvyHMdxvHR0zknhcoM5O5M5syi7rKpVima0NnsSFX3vcxWp%2BVGCJxozb2TmalNaaISvpKa46F3G2yL6fMY5dOOYdVstqelG9tzcLzG2ieaWr82JmsVWhZYF11tIYwHKyragjcoTNTNjt272%2FgxreYk%2FsWsdYNpSv0gbn1x1FiWg0XEMrQ6c9k%2FmazLYboqKNKOtUPrvpS864Fukr7ndOwv1YtcvlphmqMyUlOZP5kUoSTKkuzoo63nJ1al367YVZOkGwKbctwbxknFbh5anpRvYu5bfxJ5pc5NNKQmZATcCTfJ82wiq0gMPUh5TS1NMtkPFPMKUXCBflvG9sS4WwDhqmyzlUytx9Jsy7apWaqjtNLDcytzVoWQ6oBKgSlIAtcA9pjy4Zx9ldhbEtXYolCx7L4WmJSTbkFpdppqZdQgF8THSoW0pPSqcLakBKgnSFE9m3Y21leKeHZVRVHhic2Kuiqzng1xlLSMjKzDSaYhyXILM2VP9YeQVN2PyGILkZoSak%2BLqK%2FHwsjc3TpIP446TXm7lMCjoafmwkAnVeaolyOyx6D5IkazYyh6RYdpmbZSVEhSKhR0m3YLdBaM6rnWcp08U1UolHCh2bSpvqndIcVc%2FLFCbYs9UgRYty6APModECI6P8AdXypbU24ij5tPFC9Skrq9ITqF72BEudJ89jGI4Sr%2BSdUen5%2FNnL7Fj8%2FUpubU4qhT8v0aGFJQqXIQ4UlTiXA50nJKgUkWO0RM5DS3i6%2ByJxJ1NSGG1PoPRq1JWUkq53EdTqy54c5iyahlpnxQ3EMJb0CjsOdJts4bqNiYoSmCuGqbaLU1gPPWTVYAPN0eXUOzcAL58%2BztjSjErrOy0p6VO9s9yWmWc0z0atzWVVnKrM8O2CpCcUkyUjjSvBkBIBQXJaVUpN%2BZFwT%2FCjVfikdeVJeRE3hejZfDAOca6ZRajNVGWeTQmTMTT77KGlIWSsdUBu4tvdRi0M4L4fZ7VTXMsM62SyvUX0URlTjd1XCVDpNxYW5dsTOI3WIz%2BMp543qU3e1qnKKZ5p3OW3JR40x5IbuozLZB83RritPtLcdrriWVFK9Gi3MXdTz9UdJV7C3DzRJFSKnl9nS1LgF5c8qkyzWlF9wrW4EgAG17dsYecRZJyeLZKcwxRcf0ykuyE0irTq%2FEnZ9ybU6S0W2VLDXQhsNpUFHVcqIOwvsWNvZ29PCs6omPNOfsVrsqrOcq4ylpsy7q6lMSjLKy4ac00lJ7V6W9h39sU2dQMkFIICZF0K25KPSj8ZEdA%2B3LJ5H2PEmZ6FefD1MVb0Hpop%2B3TKwr6%2BMsxCgbDpcJ01fxgPfiMZVMmgJVpQ9iroI0rd19YbDWDeKIbIpjaiCD404Lf4NMdBPYtyldSbYvx3c2uV4Lpqth2fZosrFYyPrmIqxP4%2Fw7jZ2TSmURSH6UZNl58toKHnJtoqCEKWnQUhskJtY35wMmkUS8weuwfJVqip4vNuTa3ClpKtPJPL1R00xgDh%2BqsvLzEnlznpJy77CVNPJpsu94wFbh0EKIsfNsRBrAnDuXAlWXud6ei6QOPqprBS4fggJBuO%2FsjSnEbpEzHxlOcfvRvZfiK4jPgz0Z3NcYcdmXeG%2FHlJceu3LYroM%2FwBHp8kuImmisK7b6bW80ay8TX3x1o1JZESGD6nhD3NM310%2BpuSTj06ukN9My5LuOrQlrraRqLxSrUDsNrGLBT8D5IFh2kuZTZzPrmnEOtz6qU100ulANw2kL0qSrmdSb7C0O%2BN0jbaU9KN6KLC1tNlM807nNzEosvyiXOaZV71Ks4RE0hLKW7RkNtdIoOuKWlBv1QQo%2FEI6cm8G5D0qlOSnuV5x1B9J6VqfFJbZXL3J1NEKVYp3vy9cYVPVvJGlOUCYwFhHGyn5GquTFSfqc%2FKS7ypItpQluVU0FBtwK1q1LBBFge2M1jebK8ZzZVROXgmJ9iLSzqs%2Fzoy%2ByY9rTMpS55UlLMiQfW8md6RYCFHqWTv8kTzlDqbkpUCmmzYSub97IYUQpN3De%2FrjoT3Ssq%2BjSFUrNxSua7YnpyQT3j3i4iRnNHK9tpxp2l5vEKASm2K5AADzjoN4zsbQ01Rak5M1Qpp04rpEpLSiwqyt0X7PMYtlUps1KvpYmZZ1hamGHNLiCk2087HsveOjRm3lUndygZuPGwFlYykkgDuFpfaMUqOOsuq3jJmpYpy8r9bw5IU5ctKyk3iJJqKpguBwOPTKWwlbQstAbSkEBVwbwGl26XMOi6X9PrMehigTLmsqn0pIGwuSDG%2F8D4Wy5xB4rUxkjmLNUNt9xS3qW340Hxc%2B867AEC4Gob7bxNOZSSCkt0%2BTyPzTdU2VBE0KfpW4k%2FbJvp2jn2mK3GxrmzrtqYmPDVEe9sU3W2qjOKJ5pYBhHppXJnNaUmXUBSkUF0IPlEpnSnb1G%2Frjv%2Fi6UXuGx16wF6jSNhyHVjmVnKLFc%2Fl7jfB%2BGsg8eyVRxX7EtST88wgS8r4vNdI4p5alahqRsCkbduxuOleL8mW4c5iRKgVN1aktEjkSkEH5RHzTSK%2FXe%2FY%2Fh0WFpTVlaTnwaonbNllnlOrZPM613s67O621NcTGqnbq8O9wegWteC1cxEurlA7x9blwSIEG8QFwYmgEImsO6Fh3QCETWECBaApjnE0QtvtEYCdI5RXSk3FiI8%2FLsishQ1Wtz2gOpeFnKbE%2BXeIKHxLZmYZkpDLGQpc9U36xUltLDLYQUsvtsG61rU5pDdk3JIsNwY27g3HWROCs1Hc58V8OlYwbSccLk2VVmpvyUxIyyZz%2B6HKclRXKtzQKekVpIGoEhIJMYNldhfPniJ4K8eYBVVJWfkpEycrgdpxKUTcwuQcDszIOOCwUyElKW9YB1WBJTvGIZm4EqnEPO0XCOXGF6ecSTEjRaTPMzeFZ%2BnVuk%2BLSbcvNmdnHAJZTaFJVt5SkhASdoDX2eXD5mflDP1HEuL8CM0Cg1SuzktTDKTbT8slJWtxltvQolKS1YpBtsLdkaise6OuuP2t5lUnFFByrrE7K%2B0VmlSNQoKWGkhybel2RLPPTJPWLiFpUANgErHO8ck2HdAUtNt4XtE8S6YDIMuqbJVfMDC9GqjXSyNTrUjJTSLkamXH0pWLjvSTGXcSeCsOZcZ947wRg2VXK0Oj1Yy8lLuOKcUwjom1FGtV1EBRVa5JAIF9osuTehGbuAlOJulOKKYSO%2FwDNCLfLaMu4vnQ9xR5qKSq%2BnEbyPQQhAtAafKrRKV98RKdheJSmAoPAqSbRjNcVZh0fuFRk6tiQYxvEKLyzu1uofxQGDtm0XjDWJ6rhSsM1yivIRNMhaClxAW0%2B0tJS4y4g7LbWklKknmDFkvaJkqIMBeK45h6dmUTlFln5JDibuSizrTLrvultfNSO7V1hyN%2BZ8ahINyjSJcOmYDilOnYIKdtGntB53vtyt2x5dZEOkgPW5L0sLeLczMqToJYSUAHVtYLN7d%2FLuiZMw2zLNKlZuaamAVpeSlWlCkHydJG%2FfcH1Rb%2BkMRC4C94crjmGqzKV2WkpCdek3OkQxPyyZiXWbEWcaV1Vjfke0A9kVsO4omsOonJQy7c9TKm2lmfkX90TCEm6DfmhaTcpWNxcjcEg4%2F0hibX5oD2VBNNXNrcpaXvFl7oRM2Ljf7lRGyvSLX7hHpka3NUGqyNaw%2FMOSs1IFDrazY%2B%2BAda45FJBIKTsQSDzi06zELnvgL3X57D9acFSp8gaXNOkmZk0gqltRPlMnmhJ%2B0N7cgSIqYTxfXsB4gkcWYUnhI1WmLU5KTHRIc6JZSUkhKwUnZR5gxj8Rv3mAK6O20Sq5i3KInRaIK5i3KAhCEID2ylarEjLqlJKqTTDKr3bbcITvzIHYfREJOq1OnIU3I1GZYCzqUG3CkKPee%2BPHCA9E1NTk%2B7084%2B4%2B5y1uLKjbu37Ipt%2BXEgJvFQdkB0pwYShmK3jNwI1FujN2HpUr8gMYo6VK4TpptKgSvMdgJGr4Psc8fxxtTwfUq1N1nHbcwSGVyEiy5bnZTix%2BWNg4V4Osy8OUKsZfzNFwbjXCdRnkVGTM5Un5Cal5hAWlt5K0JOlQQ4tJTuki3dAcBrafSb2%2BWIjphzSfiMd9q4HsUNlK2cm8GFKR5KsZzRv8bcRd4KcTvtpSMj8F6hfUr27TW4PYAGhYQHF2WWW1VzMxazhGm1qkUubmZaZmZd2qzBYYdWy0pwMhdiA4sJKUg2BVYXEYl0Uw575oV14%2BimGOEnM7CU3NT2Hsq8B06ZnqfM0p55zEz0z%2BZphGh0JS42QlenZK02Ukm4i0L4HcZgJCcqcCq6MANn22zOxAtc3a3gOAEszAX5CoqeLvq%2BCr44%2BiMvwYzzaUKf4esMLeLaUurazBcQlSgLFQSZclNzva5iq5wZ1EhDslkDhmWmW0ktqXjtx5tLgFkKUgy41i%2B5SSL27IDgbL7Cb%2BNccULBSKnKU1zEFSl6Y3OTeroJZTqwgOOaQToBIJsDtFnq1NeplWm6c88y85KzDsup1lWptZQooKkntSSkkHuj6D0DhBzRwtWqXiShZYYDkqtRpxufk5lOJ3SETCFBSVBBaIsFC%2Bk7W2ihM8FmMKnUJ6p1TJfBMxMz80ubcW3jJ9pIWslS9KQzYAkk27Oy0B89PF3IudIaWkuOHkwkuH0R3wvgvxO0lIVkTgZSgnSCrGb5BA5XBa5gXF4gngoxWG3rZIYRaW6nQNONpjSAedwGfywGHcA8uvxlx9OwXiWWB84Eg8bfHaPXxwI0ZlUVJSRahDn2%2B%2FrjfGR2QuM8usRS03WaFhjDlEp6Xn2ZGlVB2oTE5NrQGw4864lOlKEXAAG%2BoxozjmfaczSpUuhd1y9DbC09xU8tQ%2BS0BzpI%2F2wk%2F%2FEtfzxHcCggBxBOrUFJsFXJ80cQSf9sJT%2FxLP%2BkTHc7jYeddDLSgdQ1WtpJ7xGWx%2BUn0KW%2F5kR55eIKFgEMgi2m3yWiCVNlPQhFlNqsTfnftj2LZSHShxCkqZcsTfnccxHn0I6f7H1v9%2B3tjbc%2BaXpl2Q6ndRNje4PKKFRkZd4lEw2lQV8ICxB7xHqlNAUo9Gobbq7xHrcZbcZ6RDm4HVKu%2FzxOas05NbV2nzEopJA6hN0m1wfmixPoUgddA1KFtjGyp%2BVL5KHFpKUjrpPfGHV2huSi0Kl29aFG5R3Ht9UM1qZYbMNhBWtG9xfzDvi2OMMha0uGyT1hYi0XeYIuoC6Ekk2KeUWacZUpajbZQIJtt6ooyvBiJq0g4u1ve%2BXfGLNhKQnUrTvGTVZavYl1txfkNCx7rEbfLGNNjpLN26lx%2FqitW1monU1LiF0JrE%2BlSUkJn2lG%2FphXwE4lmmgNI6dSdyb%2Bj4o8uKyRWaue6Ybj04nKfbVMBPLptviEak7WeNjYWDKjTaMpupzFCFVUwyUKlZmfmGmXLjmS0tKgR2WMY3XsWtpeU5IM1ZpCyVFhdXW623y2SVJ1W9JvHvpiiKa6vttaMRrqQFnTtEJToxWVOlT7E7oI8lE8Qb999PyRKvEa3gpJNRQFcgJ0m3xpixNhSl2j2NpSBvAXFdeVp066iTa288rn9zEZfEBlz0jqaoux5IqRAI7iCneLQ%2Bq55RBDkBkuNsQVWg1FmWotUmFS8zKNvFEwUPadYvYK0gxa5sF%2Fr81KTqVFHG6iubpiuw05o%2BvcfkEevoxf%2BCPxQHiYYKjaO7PB0cP8AKVvEcxnrjBltrD%2BENaacqYT709PhOpb5vsUMIBUTy1Ed0cn5U5bV%2FNLHNHwNhdjpKnV5gSzF%2BSL7rcV%2B5QgKUfRHfXGTjzD3Dtkfh7hfy2cCHZ6QQifWk2WKdclSln9UmXQVHt0JPfAWfDlKw14QniGxhO4tr1Zp%2BC8FUxlmgylPcQh%2BZQ6%2BWy%2BpSwQm6h0p23ukdkXrg8xXRsLY9zH4G8cVEYioTM9U2cNuzCAjx9gXTPyWnkFLQemSBsFpXp7I114LWpE5%2BYjpTiz0U5hR1zR9sWZppRPq1RzRizHtdl836lmHh2oGQrUpiV6sU%2BbbuOhmETK1oV5wRsodoJEBS4iMmalkbmlW8t59Tz7EgpL9LnHB%2Bjqc71pZ8HtOnqK7lIUI1O4g%2BsR9QeJfDdH4x%2BFnD%2FERgOlBWJ8NSj01MyTB1OdCk%2FnnT7DcqZWOnbHam9ucfMmfYCVFTZulW4I7QeRgLWsEHlE7aAecRUgg79kTtgCA6D4P8scl8zsez9CzhxcaWymjzr0hIdE6lU8tMs4ouNPINg6xpDgbO7guADyjS2KKZRKViCep2GMRt4ho7DxTI1ZEq5LCda7HCy4AtsntSrtEb54GcrMv85c3JnB%2BZlCNWozOHqjPpYEw4yUzDTWptYWgggje3ZfmDGgXEsDYz6HPOpQv6%2FPAeRtsHnG9OGDOGiZL1jFSMTYPqeI6VjbDEzhmZlqVOJl5xDbrgUtTZUCD1QRtuCQReNMNplEMrddmGSEC%2BkKuo%2BYAc47smZygcC2BMMSOEcHyOKM7MaUxNYm5%2BekjNJoUotIKEtNJBOrfblyJJgLXgPihy%2FyToNDoklkpmpSKBhWtu4mws5PVREup6fdYLbrE%2BvQlD8sSdSdN1AbHlvxtjGpv17E9Tr81LNMP1ObenXW2U6UJW64pagkdguo2EdV07j24mKdOOO5iNy%2BOsPTYV7J4cruG9MrMs%2FDQlzo%2FezpJsVBSb8xGJ8W%2BTeXmF2MGZ25MuOM5a5pSK56mSj5N6POIsXZPUSTpuTpBPV0qTcgAwHMa2rHnGw8r8C5RYppM1NZg58SWA51qZ6FmSmqBOTomGSkHpUuMApG90lJsRbziMILUur%2B62Pux88dC8H2UOXGbS81ZTHdPVUPa5geYrFJXLzi2TLzqNXvgKT1rADZVxvuIDnCry0nJVSbk6dU2KjKsPuNMzjCFobmWwohLqUrAUAoWVZQBF7HlHlAFuUVltxT0iAyLLwIVjfDqF%2BSqtU4H8KaMdA%2BEcVfi5xiD8FuUT8Us3Gg8s0g5gYXTqAvXqaLq5fopuN8eEdVfi4xmfPLj4pduA5eXEADExiKQIDpHhzyNyUzPyqzIxNj7NhjDdaw5Tm5iWZXKvk00dOhKZpwIBEyy5ctlKLqRqCiI55nJMSk29LJmGphLbikpdZuUOJB2Wm%2B9iLEA7i%2B8dFcOuUuAcd5GZ3Y3xXJTa61gOjS85RJqXnFMeLrcJC9QGywbJuFbWB7458WlB%2FTm%2FuhAedtq8dF5C5t5aYZypxxkpmlgjGVdpuN6nT6kHMLzDLU20ZZNkpAdve6t7gHujSWGcPTWJq9S8N0paHJ%2BszjMhKoG93HVhIPoF7nzCO4cw8x8McD003ktkThukVDHkpLNqxTjCoSJnH0zBAPRNJtZISDfcgeYmAsp4v8ABmDMBjCMtl3mDKVqnYRncAUeVq8y23SZumTDhUibm5bbVNoSSklKSFG9jY7cSz7HRuLbR5KfJT5hyjsTDPHbXcTzzWDuK6h4ezIy%2FrT6JOpOTVJErP05txQT07LqQB1L3IGldh1VXEak4qsipLIHNicwZJVn2Roc3Ls1WgTzyx0j1PfBLYWdtS02KSq3WsDzMBoco80bUwvldlLiHBTVdqXEfhfDtdcYcW5QqpSZ7pWHklQS2p5tBQoKASQpNxZQjXKpdsrv4w1p%2FfiOgsrMoMAYy4Qs2M1qvLTRxNhGuSMlSJlmaUhtDbiWytC2%2FJWFEqG%2B4vsdoDmlzpP0zqq%2BFvfftF%2B2IRUcBEU4CSx7oWMTwsYAOcVUiJQBeKqUwFVrsj1ge9iPM2I9drIEBlFNVemNj9yYyHK1WnFE04SQEUypKURzAEo5GPUgaqegfuTGQ5U%2F8YKu5f7HQaqv%2FwBK5AawwTOTkpUJZclNOS7im0o1oNjYpsY2nwxj%2FwDVRl6PtccUoeTb%2B7Go1NhI6J%2BVXa%2BkINu%2BNucMn%2FxU5f8A%2FwC%2B9KP%2FAK1qA%2FQdCEIBCEIBCEIBCEIBCEID8%2F8Ax2rJ4ncyUEjq4ineX7%2BOe1eU2vziN%2FcchB4nczSP2yz4Pp6SNAH4HqgNgUfyf4KY9hjw0tSm0rUlou6EpJQOagFbgee3LzxtvNvKCn4Po1MzFy8xCrFmAK4ENydXaYKXWJogBUpMtC%2FRvBVwB29kBrDUb2iYHvjNsX5I5sYFqtDw9iXAlSZq%2BJVBukSTOl5c29cAsp0EgOJuCpJsUjc8jGRz%2BTeG6dmdgfJpvGLdcxTVagzJYrTT7KkKS6p1J8TaeH2Z5KAvpFDqg7CA2Tw4cIysxqFL5iZkzc1TMNzY6SmyDBDczUGwd3VrIPRNEiwsNStyLDeN4v4w4PsnZaoYPYlsOyKKpL%2BI1RlhCphc21cHQ%2Bu5K033sY8XHNmdN5V5Zy2H8IuGQeqbhp8spnq%2BLyzaQLI7urZIj51UyanZ9pazPltSlfBbSST3kne8B3xX%2BGnILPCgP13JSq0%2BkVJIu0ZF7XKLXbZDrRJLd%2B8cu6OKsTYcrOEMQVHDGIZFySqdKmFS0ywsbpUO0d4IsQe0GLtkxmjiHKTNCg1iQqC1y01UGJKpsaAlMxLurCCDbYlJUCDa%2B3njpPwhuEZKXreDMwpRhttyuyszTZpSRYuuS9lIUrzhKikeYCA4%2Bub2vGyspM9sVZPJmpKmycrVaPPO%2BMPyE0pSdDtrFxpad0KIABG4NhGt4Rp3%2FD7rilhVdr5RFdE7YleztKrKrhUTlLqdvjtqSEhPuby9u3833%2FGiH1eNX19bLSTKf3M4L%2FKmOWIR53iJgHkPWq7TZ7uvMRrrnq3OplceVa%2FS8spH%2BFOA%2FwBGK6ePCq6d8sZMnvE2n6McpRPDiJgPJYetVvR3dePHnq3Oqk8dtUAF8spEW7PGh9GIHjtqoPUyykwL9k0mx%2FkxytFaSk5upT8pS6fLOTE3PTDcrLMti6nXXFBKEjzlRAiJ0EwDlu%2FrVbzu68ePPVudTfV41T%2Fqzl%2FwxP0YlPHhVb9bLCXI%2FwDGJ%2BjFkHBRitqpuYLdzNwecdtyJqCsNIeWp8NA28sC3Pa9rEkdm8c9z0rMSUzMSE02W35V1bDqDzStKilQ9RBhxF0f%2Brx0qu0d3Xjx56tzqAcedU%2F6tpdPom0H8aIh9XlVEEacuGV2F7rmkAk%2BgItaOVtB74heJjQXAPIetV2ju68ePPVudWfV5VLSLZasBXaTOJ%2FFoiRHHpWwbKy4lj%2FjSfoRyuD3xG474idBcAj6D1q%2B0t3defHnqdWnjyrJG2WsoPTNI%2BhEw48anbrZbsg9wmkfQjlCFx3xMaC4B9X9avtK933jx56nVSePOqBV15bs2tyE2nn9zyic8etS19XLZnT55tF%2F5kcpQHVSXe6HEXAPq%2FrV9pMX%2B8%2BPPVudX%2FV51T%2Fq1b%2FDUfQiKOPOrAdbLVgHuE4m3yoi2VThQy4w5WKLhHFXEhSKTiWuybE1KU%2Bapy0dIHkjotJvyUq4FyCY0tiTKzGmHMy6plM7R5moYjpT6mVS9PZU90yQkKDqAAeoUkG%2FqhGguAclh61faJv945a56tzfv1eNVP8A8tZb1zifoRD6vCqj%2FwCWksf8cR9COa8RYMxfg6ZakcYYYqlDmnwFNtz8uprWD2pJFleqN%2FYo4XsnMAVhvDePuJ2l0SrKlGJ12UfpDpUll0XQpNibgi%2Fn25RHEXAvIetVvV7tvE%2FPnq3Lorj0rCwUqy0l7Hn%2BbUn%2BhEiePGqjyss5M%2F48PoRzlRsJ1rF2JHsNYGp83X5krmlyaJZk9JMyzOol4I5pBbTrIO4BtFjBujpBqKYvOguA5fIetX2kxfrx489W51aePGpkp05XydvhEzgP9CJ1ceFRLdkZYSaV95nRb%2BbGPYZ4RpBw4foGPc68N0DGGLJVU5SaCygzay2E30LcQrT0ljulPnAvYxi%2BDuF3GmKMz8WZcVGsU6jt4ER0tfqzwUuXZQU6mwgc1KWghQG1hcnlEcRsBnV8R61W8m%2F3iPnz1bmyBx4VEc8r5Q%2BifH0Yl%2Br1qF7e5XKfxgPoxhNd4badTKHgzH%2BFcx5LFGBMUV2VoM3XJWTU2aa6%2B70SHFtE3KNfVO4sbX5iPRiPhXm6DxLULIFrE3TStalE1JNZXJ6VNSqW3FPqLV%2BaFN6ee5UIjiHgMa%2FiPWq3o7vvHjz1bmXfV5VH%2Fqslf4xP0Imc48qjazWWMtfvVPC382MKxXwvv4Y4gcE5Mt4jdmpHGaGphqpmV0uMMALMwot3sS30fK%2B%2Boco1znHgmnZa5mV7ANKrq6wzQ5hMqucUyGit3o0qWnSCQNJVp59kRxGwHyHrVb093Xjx56tzfQ49KsE2VljJ6u8Tu38yIDj5qvJWWMl%2BGD6EcmknXzgom%2FOJ4i4D5D1qt53dePHnq3Oszx81XV1MspBKfPO7%2FIiIL4%2Fat8DLKWHpqA%2BhHJeo98CrbnEcRcB8h61XaO7rx489W51qnj%2Bq1iDlnLA22Pj4O%2F3EE8flX6S6stZMoty8bF%2F5kcjEm8RBNocRMA8h61faO7rx489W51y5x%2BVMoHRZXygV265wW%2BRMS%2FV%2BVf4GWUnfzz1h%2FNjkm5i5YfolSxJWqfh2jSvjNSq00zIybOoJDj7qglCSTyFzuewRPEXAfIetV2ju68ePPVudTtcfeIgLu5aU7%2BDPfOiIDj%2BroXvlpJFJN%2F0eAQO7yIsx4KHn8T1TLekZ6YTqWP6RTfZGYw03LTCFpQQkgdMRosdSbH92m9rxzMT19BQppSVFLiDzQpJKVJ%2BMGIjQfAY%2Bg9artHd148eerc60HH7WSbjLGVA7lVAG%2FwASNoj9XzWFc8rJE%2F5SH5URyVrHcqHSDzxfiTgPkPWq3p7vvHjz1bnW31fFU039y2Tv3ePj6ESfV%2BVYK%2F5L5DT%2FAOO3%2FmRyZ0g88QKxfkqHEfAZ%2Bg9arerN%2BvGf589W51dMcfVSW4Fs5YS6VjsXPix9FkRiOZfGVjbHmGJ3CtJw9JYcl6myqWnJpmYU7MrZVspts2AbuNirc2Jjn1RiF79sZ7PQ%2FBbG0ptYsIzp2ZzM7PNM5Im920xlVVOUn7zqpT5PmHdF%2BwbjTEGAsRSWLcLTvitTkFHQojUhxs7LacTyU2sbEeg8xFgVEI9BbWFneLObK1piaZjKYnZMMFNU0znDq6U49sQtS6EPZayXT2GtbVSUlBPbZJSbD1x6jx%2BV5SrqyzlCP%2FHf7MclJMTR5aNBcAzzi7xH%2B6rtNmL9eI%2BfPVudZnj7rJP%2FACYSlv8Axw%2FIiJXOPqsHZrLOUT%2B%2Bn%2F8AYjk6EOI2A%2BQ9artJ7vvHjz1bnWSuPirnUU5ZyKexP5vJ27%2FIiDfHzVwqyss5QDvTPf7EcoDlGWZXZc4lzaxpKYCwmiV9kJpp2aU5NzAZZYYaTrddWs8glIvDiNgPkPWq3nd948eerc6GRx9YhSon3OZPT2Wn1A%2FzYnVx%2FV47Jy5lEnvVP%2FMi8agz2yNn8hZ%2BhyNTxPI1%2FwBnpFc6wuRYWjSEuBsIsrdRUSNJHMGM9Z4LMROVCVwdM5nYUlcwJ%2Bjity2EHulTNrZIPVLltAUCFJO%2FNJ7BeL8RsBj9njpVb1e7bfx56tzIT4QCvEXOWsoVdxqG38yJUcfVeH2TLqSV%2B9nrfjRHLE9KTNPmX5GelXJaZlXVsPMuCym3EKKVoI7wQRHnuIjiLgFW27%2BtV2ju238eerc6uPH7W%2BzLWX%2FjAf1cR%2Br8rX%2FVrL%2FxgPoRydrhriOIuARssPWr7R3bb%2BPPVudY%2FV%2BVrsy1l%2F4wH0ImVx91xX2PLZlP76fB%2FEiOTAveKoXDiNgP1f1q%2B0d23jkrnq3OrHOPXEIPUy8kyO8Txv6PIgOPivX%2FAOTlr8P%2FANmOU9cNd4mNBsA%2Br%2BtVvO7bz489W51enj5xB25dyx7vzwI%2FoQPHxiNPWGXEofTUyP6EYDl7kFget5QSucuY%2BcUpgylTlXmaOwH5BTqOlaNgCsHyldYgAckneLBnfkkvKQ4ZrFJxdJ4rwtjKTVNUSsyTRSJlaSNbWi5uqyklJTfUL8iLRSdBMA8h61XaO7bx489W5t%2F6vzEOnfLmVv8A%2BZH6MSnj7xD%2FANXEp%2FGR%2BjHPlcyozMwvRG8S4ly7xHS6S6hLgnJuQW22Eq8kqJHVv57Rs7BHD7gCsZMUPOHMHOaWwbI12pTlOl0v08ut9IwpSQjUDcrUEKVa1rCJjQfAY2Xf1qt53bePHnq3M2c4%2FK6kNhnLZhRsekK6kQL9lrJgjj6rejr5ctavNUtv5kc8ZmYdwfhTFRo2X2PWsa0oSzC%2FZNmVUwC%2Bu%2BpkJJ3KeqLjYkxbcWYVxJgTEc3hDGNGmKVWZEIMzJTCdLjWtAWm486VA%2BuJnQbAZ%2Bg9areib7eI%2BfPVudLDj7xIk3Tl5LhPcKkb%2FwAyJ%2Fq%2FcQrQUqy8Zv2E1I7fyI1hlVkZQMYZf1HNjH2a1FwNheQmlSCFzSemmJh1JSkqDQOpKNSgkGxJN9rC8XHMnhexjgrMTBmAMPVSQxH7oKVKoU80OibXpAUvpOekJbIcKhcFPLfaEaD4DH0HrVdpMX28T872bmwG%2BPrESR%2FyeS485qZ%2FFoiK%2BPivHTpy9aT9sPZNR%2BI6Yslc4P5F2SxlSsvM3qRinGeBJTxqsYfTKLYWkdHr0oWfhEAgXFrixsTaMLzLyFk8G5HYBzqwpiSZxAxjZUsyqWclAz4s9MNqLTYUCb%2B%2BoW2Se0Xi8aEYF5D1qt53bePG9m5s76vyvczl0j0mqkD5ERBPH5Wv0zLxs%2Bipq%2BjGI8R%2FCo5kJlzTsdy%2BKJiurVUWqdVZYynRIlXHGVKSUKBOodKlTe%2FeD5ox3iEyHp%2BRftRkTil2qVXEVOdqM3LGW6NEohHRgBJuSq6nCne3kkxjq0EwDb8R61W87uvHJXPVubNXx%2BV3VZGW7Wm%2FM1ZV7fcRMOPusaFasu0avg2qZt%2FNjlEpA7YlinETAJ%2Bg9artHd158pPVudWL4%2BK0Ui2XaCrt%2FPVQH82CuPmtXARlui1hcmrK9fwY5RJtBDm8TGgmAeQ9artJm%2B3nyk9W51cjj1rnNeXSfVVFfRiJ4%2Bq6Fq05dthPwb1RRPr6scp9JEIvxGwD6v61W9Tuy8ROfDnq3Orjx%2FYhKrJy6YCe9VUVf%2BbEyuPmt8xl20fRVT9COT4z%2FJvJrE%2Bd2IpugYXXJSqabK%2BP1Cdnnw0zKy%2BsICjfdRKiAEgXieI2AfV%2FWq7S0X68%2BPPVub3HH1iHQEt4AaRpI8upkgj7iIp4%2FK8FXcy7SU2%2BDUt%2FlRGlc4slK9lHj2nZbOz0tXqlUJWVmJUyLax0q5hxTaGQlW%2BoKTbu3jPaxwiqoi38Mz2eOAmMeSMi3OzWF5qc8XWnWm4aD6yEldiLbcyL2BBikaDYDnqsPWq7R3defHnq3MoPH%2FXuRy1T%2FGn%2BzEx4%2BaspR05daQRtqqm9%2FueUcm7tuLbWFJWlRSoHmCNiIli1WguA8th61W9WL7efKT1bnWX1fNbH%2FwAu2z%2FlM%2FQiP1ftcH%2Fy4Qf8pn6EcmA2iYKHeYidBsBq%2Bg9arev3defHnq3OsHOPqtpQHF5coAPYKqdXxaYtlc48MZT1MelsPYLkqbPOJUlubmZozCWCRssN2AUodgJtHMKzqMQue%2BLUaDYBZ1RX3PE5eGqqff1K1X68TE0zXOv0e6HoqE3NVKefnp6bdmpiZdW8%2B86bqdcUSVKJ7ySTEJKZmpGbZm5KZclpiXcS8w82qy23EkKSoHvBAMeeJgoiPVVUUVU8CY1bMmvE5TnDqKicdWKZSVQ3iHAUnUJ1P2WalJxTAe23UUWIBJuTY23i5Hj8rR3GWjY%2Fymb%2FAMyOTekMOkMeVr0GwCrX3PEZ%2BCao9ktju28x8%2BXWP1f1ettlq1%2FGZ%2BhEfq%2Fa3o3y0aKrdtTJF%2FuI5L1mI6zE8SMBpj5D1qu0nu68%2BPPVudZjj%2BrhV1ssZfT5qhv%2FADIgrj8rWrq5ZNW%2F8xt%2FQjk3WY9VJkpysVWSotOZ6adqUy1JyreoDW84sIQm55XUQPXFZ0HwCdth61XaO7rz489W51Ynj7rIBtlq3e2355DY%2FcQT4QCvA75bM281T%2F2I1zm5wq4wybwAxjbFGKaJNPqqjVKmKdT1qeDDikr1EveSrSpBSbdsejCPDG1UMEYXxrmFmvQMCt44mxK4dk5%2BWdfdngogNqujySsnYHkLEncRXiNgH1f1qu0nu28xtr9m5n54%2FwCuKO%2BWbBHcakPoRBfH9WvgZZsj01AfQjn3NjLHEeTmPapl7ioMmoU5LTyH5dWpqZl3U6m3UnnYi4sdwQRGIXHfFo0IwLksPWq3o7tt%2FGnq3OrleEBrgFvc1YJ7%2FZIfQiX64BX%2FAPq1l%2F4xH0Y5MV5cIniPgXkPWq3ndtv409W51oOP6vnnlzLDe29TP0Iivj%2Brp02y5lT9t%2BeJH9COSge2JtcOI%2BBeQ9ared23jkrnmjc62%2BuA1UNn%2Fg2Z19n547fzIlT4QGu%2F9W0uP3tT3%2BVEcmBd%2ByJVC5hxIwLyHrVb0923jlrnq3OuV%2BEAxAbdBls2Nt%2BkqYN%2FiRFVHH%2FWutry4b%2Fc2qX4%2BrGpsjMj6BmjhnGuLMV5gN4TpeCkya5maclOmR0T4US4rcaUp0gdvlRXzc4f6ZgbL6SzXy%2BzOpmO8HvVA0eenZVHRLkZzfSCL2UkkaewgkXFiDEcScC8h61W9WL5b%2BNPVubP%2BuAYjF%2F%2BDmXPd%2BeZH9CKQ8IBijV1suZYC3ZVDz%2B4jnxnKbNCYwycaS2WmKXqElBdVPoprhbSgblR2vptve1ozPJLJHDGZ2CcX5h4zzMawhQcITEpLzE2Zbp0e%2FpJC1m%2FVF9KRzuTDiPgc%2FQetVvJvtv409W5tH6vzEahvlwj%2BNdv5kTfV%2FYk%2FwCrlH8bK%2BjGk83cE5VYNNHVlrnDL46E4l81FDEmpjxEIt0aio7ELuRbmLeeMRrmFcR4ZapT%2BIsPztParsgiqUxx9uyZuUUSEvNnkU3B847RuIcRsC5bD1qt6Yvtv409W50seP8AxOT1cuGCPPVV%2FRionj8r1vfMtW794q6voRpjJfJp7N%2BYrE1M4zo2E6Bh1pDtTqlScHVKgpQbabuFOK0oUo22AHnjIc2%2BHVGBcB4fzTwDjqTxzhPEc%2BzTpWak5dTbwdeKks9Q%2BUFuIUjbcKABG94cR8Cj6D1q%2B0nu238b2bmxRx%2B4gTsMu2B6Kor6MTL4%2Fa7oT0eXCdXwr1M29XUvHglOCuT9nqflzV86aDTsxqnSjVpfDrko4pPRAG6VOja9wQbcglRsQIw1HD0FcPOJs4pqvvSuIcGVWapVcw6phKkybstMpafu8DvZC0uAgWIMTxHwGdth61XaR3deI2Vezcz9HH5X%2Fh5dI9VVV9CJzx%2BV6%2Br3PEX7%2FZVV%2FwCbGLzfCe%2FLcNXu6qxLNCrN0VvED1G8VBbTJl4BQC76tYaIc5W5jzxiWI8jZDDvDhhnPGfxQ6aliicaYlKR4sNBaWp33zpb9iGwq1vhCK8SMB8h61XaO7LxPz%2BqNzaqvCBVw88vBf8A81I%2FoxSHH%2FX%2BRy8Sf8rKH9GOUIk5Q4j4F5D1q%2B0juu3n53VG51kePzEShYZdhJ7zVln%2BjEyOPqufDy7Xy7Kurn9zHJ3SQhxIwLyPrV9o7rt%2FHnq3OsU8feICbDLgW89ZXf8AmxUXx9VpAsnLtSV%2F%2BcKKf5scmXA7Yj0htfsiY0GwGdtjPSr7RF8t5%2Bd1RudX%2FV%2FV2%2F8Ayc3%2FAMsK%2BhEfq%2FK9r%2F5OFaf%2FADff%2BZHKPV037YzDKbKvFGc%2BNJXAeD5dpU%2B%2BlUw688rS1KyyCOkdWR2C425kkCE6CYB5D1q%2B0mb7eJ%2Bf1Rub%2B%2Br%2FAMQ%2FpeXnq9lv9iKieP8AxF8LLsH%2FACp%2FsRr7H3C%2B5hjAVczDwJmfh7HlOwnPKkcRN0rUhynLSQFGyvK0kjUOdjcX3i15B8N2LM%2FXKw7Sq1LUOmUlbMuKjNy63Wn5pZuWEhO90o6xPZsO2JjQfAo%2Bg9areim%2FXiPn%2Bzc2qOP6vg3OXNh3Cq3%2FABoiRfhBMQAe95ai97daqA7d%2Fkc45WnGVyk0%2FKLUFKl33WFFJ2JQspJHrEeZSiDEcScD8h61W8m%2B3ifnex1r9cErdlD3OF3PI%2Byg2%2FkbxKfCCVwW6PLxPcdVSB%2FoRyVEpA74mNB8Bj6D1qu0mL5ePG6o3OvFeEBnylH%2FAAZm%2B%2BvTUE%2FJdEW%2Brcf%2BI3JdxNMy7ZbmVCzTkxUNSEecpSkFXZ298cqRBW9iYtToTgVE8L4j1qt53beeWvqjcvGKMT17GVcncT4mqCp2qVF0vTLx8m%2FYlA%2BChI2AizRN0%2FwLRTWY9RRRTZ0xTTGUQ1dqa%2FnjoPKbi7qmAsLSeEcX4dmsRNUpvoKdPSswhqZRLjyWXteywjcJUN7bHleOeLnvi6URouPOKDIcCGypV%2BQFx88c3F8DuGO2UWN%2Bs%2BFETnG2JifNMZSzWNvaWEzNnOWbrR%2Fjrwg%2B0UTOXGI7KNxpnpW9%2FTEMNcYOH8RYoouG5XAFbYXWKixTkzD9Ql9DJdWEpUQBvYnl2xzQiWlinWZVkpV%2B4vYxQrqGJWnU56RU5L1FqeXM%2BMIAToKQlTSk23ulQv8AFHlbz8HOCzZVRY0TFWU5TNVWqeSdutvWeKW9MxFVWr7HXvF1lXiLM%2FAlN9qzKpuoYeqSpzxBOy5tlbRbcDd9taTZWntF7Rw3M5d4zkH1S09hOuS7qSQUuU9wbjn2R15hnjRwrOUplWNqDWGKyEJTNinspelnnAAFOpKiCnUbq09hJi9fVnZW6iBRMVEWvcSiOfd5ceRwW86WaN3ebjTcuHTEzl9u3KYziYz1x6fsjfvE3C91%2FG1V5S4kVgfFKbg4aq5PcJJy%2FwCKKC8D4sSd8L1oX5fmB3f%2BTHcY42cpUlKVUfEqnD2CTbv8i49SON%2FJ1sWmcNYnK%2FtvFwL%2FAMuO1TpTpXl%2Bro553Naq74d5Sepwd7TcVHlhisn0SLp%2Foxt%2FhdyXx3Vs26Diebw7U6ZScNTaarNTk5LLZbUW0q0NIKralqUoWA88dLJ44Mml7jC%2BJrHlaWSfxLinMcbWT6mtSaFixxSfJZ8USL%2FwiuwjXxHG9KsRudpdJuHB4cTTnGc5ROqeSI2L3anD7tbU20VzOWvLz%2FYu2dXEBJ5OVOjSFRolSqblXlnZpKpWZQ30SULCLKCt9ydrd0a5TxyUJHk4FxGf8fZEaJzjzRqOb2NH8VT1PFPl0IEnT5IL1GXlUklIUobFaiVKURtc%2BaMOp0qhyeaR5STcKjawn4M8K7ispxKyztsvwsqpjXty1TlqjU17fFLeq0mbOqYh1Snjjw6Qn%2BwLEYJ5%2Fm5iwiZ3jow0yFOe59iZ3T8BE8xuPNHOhkJXbSyk6ee0W6syjLEuXG0pTpUlJ285jpT8G%2Bj2WUWM9KrepTit6pnPhz1bndOcdEqmeHD0%2FTqASZqvUyUrElLPvDruBSH22So7BRGpIPK%2Fpj561PAOL6DOu0%2Br4VrEjMsq0ONPyTiVJPdsLfEY6ayP4qKRgnBkrgjMCl1Kbbo4LVMnpJKXVGWvdLLqFEeQSoJUDyIuNo2T9WZk2U9elYr0p2A9j0n4hr5R5LB6dJdEK7a5Xe6fG2U1TMTH2RnExntiI1TGeeboXi0uV94NpXVlOTgtVBqwUdVNnk%2BmWWPyRFWG66kajTJ8Dv8AFl%2FNHd31aWRyRpeoWI0ACyQaa3y%2B62j2jjVyJQgdNQMTrv8A93Db%2BVHf416TRH6tnnnstTubD9vxs80b3AqMM4gdUEtUapuk8giTcP4hGV5b5L4%2Fx%2Fium0ak4bqjSFzTK5mcmJRxqXlmA4krcWtQAsE325nsjtJnjWyGVcsULE6UggFQkR2%2BhURXxrZJEKSJLE6Ufu5EkX77ao1r1pLpXb2NVnZ4fwZmMs%2Fwpy%2Bzgx7V7Oxw6mqKqbSZy%2Frws%2BzbzWOVeEZnG1QZqE%2FKy03LySGJWZDbq%2BkVoSRqNtgLkRpQcdGENR6TBOKFW%2BEH2d%2FjMax4jOIqUziZp%2BGcM0p%2Bn4dp7pm1LmgA%2FOzNrBZQCQhCRfSOZJJNo0pJsS65trX10qV1kxq6NfBpcrTD6a8Ysp%2BNmZnLOYmI5InLl5ftXveM2vxmdhVq%2Frwuuvq5sIKNhgnFSR3iYlz%2BWJlcdeE2QVNYHxY6oC1%2FG5dJt6dUczexkn8CVb%2B5jyVGRl2pZwplUJNuaU7x3%2F8AxlgHJZz0qt7V78Xyfnz1bnf9Qmvd3yDmWpCYck2ccYedEumbdK%2FF1PJIQHSPtVpAJEfNzEOXONsJVN2jYkwnVadOy56N1DsqspJGxKFgaVpPMKBsQRHSnDzxPUTLnDhwNmBJT6qbJKW7SahIth1xtC1a1y7rd90hRUUKHK5BHIxtw8ZuRC0lDrdfcSBYBVJURbzXVtHk8GsNINC7xeLtdrpNrZVVTNOWeWXJOcROuYyzifBycvQt7S6X6imq1ryqy%2F8AuHz7VS55vrOSUym3eyofkiQ02cPXMrM6fMyr5o%2BgKuMTh2VvMSNaTb4S6OCBHpa4xOHDowHqfWy2rkoUlIB9UeinS7SLL9WVZ%2Bmew0Zu9xj6aeaN756Kps4pPVlpv7wr5ouFEy%2FxfiyeRRcP4bqs%2FOzY6NlpuVXYqOwuoiyR3k7CPoB9WBw0E6WJSr37B7Djf0WiZjjK4fNOll2vsdIOt%2Bda0i3cbGMVppVpPXRMU4blPhzqnqiiPbC1F3uGec2sz9kR72W1vFD%2BSeUMrUKqqbnEYUpEhIPsyLw1OOICGiGySAQFE%2BoG0am%2BrlwJr3wti5Q%2B2s18vWjXvEhxLUbNOgS2BsDSdQlaMJxE5UJmcaDS5xTYPQtpRclKEm6iTuo27BHOvmjm6NfB3d73c5vGN2cxa1VTMa8py1bYjlmc59DNe8XtYtZiwr1Oz08cWXykArw1i1Kr3I0tc%2Fu4lRxx5fk6nMLYwBTyIUyb%2FwAvaOZhRqclpAcl2gQkE7eYR5n6bT0oV0cs35J%2BDHe%2F8Z6P%2BTnpSw04zfKdtT6IZVZq07NPBjeMaCqqyknNPuywROqs%2B0plely4ST3x818wsrMZ5f4pqtEr1An2wxOPFmaRLqUxNNKcUUPNrAspKgQY3Pw08RlJyjlJ7CmNpWcdoM7M%2ByErOSTXSvSMyoBLgUj4bSwEk23BF%2B0xv1PGLw%2FEaXJqsKSk7J9iHQn025R5TDrljehWJ3izuF0m1sap1ZZzqiZmnXETriJynOM9Wfp27a3uuIWVPx9eUx1eGMnzzcpVQaQlbklNJSu%2BlRYUAq3OxtvFJVNqABUJKbI8zKj%2BSPocOLLhlbbQhZm0NtklCV0ZVkkm5sLbb7x6mOLzhpSCVPz6QRpOmkKG3dyj0MaW6RTtwyrnq7DU7lw%2BPpp5o3vnGKXU1%2BRTptX71lR%2FJFZrC9fmnky8rQqq%2B%2BshIaalHFKJ7rWj6ODi44YwSG%2FH1FIubUlX0YmRxjcOW62KjVmCOWmlupJ%2BIRSvS3SX5uGzz1z%2FAMFoutw5LWZ%2ByN6vk1TcSZT8OdGlsUSM6xM4doszUpqnsrPTIbup3ogLga9O5HeYwdHHNlyE6k0HGHWANlS6bjzHrmMfz84uMJ4swPPYDyvl6i4a0gy9RqM4wqXCJU21ttJJ1KUuwBVsAL98coRztHNAoxaLa%2FaQWcxaWlczERq1cucenZnryZL3i1VNcU3adURk7RPHPl0Rc4fxSfMZRv6UaVz94j1ZvU%2BVwtQ6HOUuhSkyJxzxtaS9OPpBCFEJ2SlIJsnc3N40rEFR7TDtCMGwm8U3qws5mqnZnOeU%2BFz7e%2F3i3p4NdWpJpT2Q0mIad4AKHbHrWkiEmJgLwAvE0AiSJ4kgJ4gQTBO8Rse6AhpgExGEAN%2B6IggG5VaAuTziBA03tAZDS8eY1ouHqnhOhY1rtKo1ZWh2ekZCcUy0%2B6kWDhtuFWABIIvYXvYRvfNrjTxJmnkvh7LNNOrVJrUi9JKrlXRUyBUESjZS30ZQQtKlq0LXq7U9t40BRJdl%2BVcU6lCj0gA83m9cXM0%2BXTzYSPQDAebFmMsW46qaK1jPEtSrk%2BzKtSLMzPPdI43Lt30Ng2Gw1He1zfe8Y%2BecXKrNBmotyjKEXmOjQmw5KWoJv8t%2FRG%2B18EWOktJdRm3lK8pRsUoxKkaT6SneA5yhHRI4JcdFSkKzXynC0mykjFCLj5IlHBFj8atWaGVJ0nSrTitGx7t0wGqsnEJdzgwA0q1lYqpg35fohB%2FJGVcV9zxO5q6uftpm%2FwASY2hl9wgYxwxmBhXEtRzGyvfl6VW5KoPtMYlQpx1pp1K1BIsOtYG2%2B5jUvE5U5CtcR%2BZ1Xpc03MSk3iabWy80oKQ4kWTdJGxFwdxAatiSKi%2FNDRt1tMB53BflFum5Rt9CkL%2BF1VevaLsW4oONQGrZ6jz8lMKYdl1m3JSUkgiKHij%2FAOpOfcGNsIY3uIpPtv8A2%2B0BqvxZ0fAV9zEpacv5CvijZbjZTstIPpAMeKbCUeUhsfwRAYB0Tnd8kTNy77ytLTK3COxKTGTTk0w39p8Ueek1L88FNoXp6VpxtWnbsuPlEBYPFn%2BfRK9cNDo5ojIuk19Ra1aY801LtoI0wFnCFn4J%2BKBbXzKSPjjqvhHmctZjD%2BIqNjj2BTPs1BiYpy6mpKFltbZSsNqPcpKSfTHRJwzlYpsLJw2pAFx%2BbmCgd%2B0B8yikjmbfHEyUXF%2Bz1x9HqtJZDUxBmqscGgjmp15tw%2FEnt80a%2BxXndkHSKPN0ij0ykzhcZdZQmUoyCkFSbatZF7i9wQecBxA42UdkSBJPIGLpN9G2%2BtDYUpGo6SdyRc2JPfaKaFrQ4lxs6VQHiLLwTrLC9PfbaJdKvtT8UZYip1RyTMlNTzzkopSVqZJGgqB2NrRWYdb%2B0T8Q%2BaAw3Sr7U%2FFEQy8ryWln0JjYcuAtPVQ38Q%2BaL5RGULnEIfQlSVJPV0jnAalRKzJ6yZdZSOZCTYemKzUpMLNksLPoSY3qinSdygSoAPMA2CvT3iPNUKdKyMuhbbASrV%2BMQEuQuYOM8lp2brlATJqXVm0MzslOtdIy8yk3TuLKQsHcKHedo3%2FK8dmZEoUhGDMMlKNgC49HN0SQHUP1fOY69zgjDafP0z34oDj1zECf%2BJWGirvK3%2FnjmGGuA6hTx85iDysDYaVv2PPCCuPrMAm6cB4dA7une%2FH%2FAKo5e1%2BaKkv746E2gO0Mp%2BMjGOYmYlKwRPYEo0m3UWZ1an2Zt0qQpmVdeTsraxLdvXGJy%2FhAMfvy7T5y5w8nUnV%2Bin%2BZEc7syLReQUOKaWOS0LKFD0EEERJNyLDcpML6P7EnUn4xAdMU3jfzgqwW7RspKRUUy4SH%2FFhNuhBPaooB038%2FdHsXxrZ4tt2VkhJNL%2B26Cet8WmMR4U3c3USFRXlnNYZZl1V9hKk1YTOvx7xRehV2OTXRa0%2B%2BdUqItvHR6hxiLbuKtliD%2B6VNn8cBouo8budlNbTM1vKelybFwlLkzLzbSLnkLq7TFNjwhOZMs2ekwBhd0XvdUxMJiTiidzxGDak3mNMYRmZJM%2FSm55VKE10pUUuqk1ILvvSkDrhZRdSSQFRp7KDGGHsMTNRlfcn9vWMKqhMnh2XmVBclLOq5qcZ5uEkjlyAgNs1bj3zDqTK%2FEsB4Yk1rHVcS%2B87oV32Nrxzli7FddxpXpvEmJqgudqM6vW%2B8rYE9gA5AAbARuTi2w7hbDuJMLJpdDpVAxLM0RK8U0mkn8xsThKSkti50nyrgcwBeNDL3gJ5FTaanIlYVpE0yVW521pjuWcl3lPuIQSjr6rJ7f%2FzHC8unVPSqe%2BYaH8tMd7ltxm7JbKXGwkKtubefvi9lP4c%2BiFLfXZxPnn3PB0SkBVwpZO6tok0EqSA0sX3NxyEe8TXSJ03TYbG3KIBCb6mirbygo7WjaaSi2w%2BlZWR7ysDUDsdv994rPNvFqzSQra6QeV%2ByPc1LqW2CtQ0WHM9sSvtXaHRX6o2Pmi2ZUsszK65RSFsjUBZYG3xRahIBSXHF6lKVurVvuO6L%2Bph9TOlZNwCLk21f798UXJZwjrjZYNz54ZqxDA6th1pRceliUm%2Bogp2MYdVpNxDaumYAKe0dpEbcmZBSkhItZV7pP44xaq0gLaKnUFJCVaQRzhlmtE5bWn64s%2Bw80vo9WlPNPcVAH8YjHJJKisBI3tcekRsDF1JPsbMuNt%2FA63mNxGK02UGv3zUnfUnT6YrVTrZqJ1NCYuSRXqylXMzLJPywxFf23TX9%2BH81MVsdJKMTVzTzQ82R6Yhik6sXzKu9xB%2FkCNOra2Y2MsphvTX%2FAERiVdSdXxxllK3p74%2FcxjVdQLiISsLJsdVto96FNFrUE7x5Ukg6dMexooLWkJ3gPE%2BE32jzDUVbR65oAHaPM2Fa9oC542%2F5nO29Ma5G%2FwAJQ%2FJFxbb1rTfbqj8UWzHC9b1IG3VpjQ29KouygQlOkgHSLEi4vbtHaID6K8EmXNAyFydrvFBmU2JRdQpy1U5t4BLjNNQdyi%2FJyZXpSnt02744gzazMrObePq1j3ENQbXO1maVMdEV7MotZtlA7EoQEpAHcT2x2nRvCYZbPYbp1KxVkTPqelZNmVmJWWmZR6RKm0BILSHhcI6oIChcX9cRT4Qrh5WdTnDe7fv8TpZ%2FoQHN%2FCHQ8pqvmJOjNPPKq5ZCSpqpimVGl1UU5195awhaDMKBASlNlFoj3wbdkadrzNOla7UZSn12Xq8rLTsw0zUG09GJtpLqgh7T8ErSAojsKjHeLnhAOGl8aZjhmU4kHYKp9JI%2BVMehPH7wwFFzw3KCu406mfNAam8HvxDS2V2ZzmWmIKxLIw5j59tpvxhxPRSdZSkpYcUDsEPouwu%2B1yi8YDxt8PwyGzamZWjybiMKYn6Sq0AkfYEFXv0mT9sy4SB%2B4UiOjn%2BPXhdfA6bhnWdCgtJ9j6XdKhuCDbYg7g9kaj4xeMfBnEXgijYNw7gCo0tVKqS6n4%2FUX21upWWuj6NsN3skp3Vc7kDaA45UmCdrRUWIpwGzcg89sa8PWN1Y7wMxSZmcckXqe%2FL1OXLrDrDunULJIUFdUWIPeN7xvNfhE8xXnOkXlHk8r7bVhcE39JVHIaDaKqVbQHW6vCG5hrQrRkzk86QNRQMLi5SDcgWPOwNvPaN2Z8YkZw%2Fn3gHimpuaddwPgLHOCGJSQxZQ6QiqmTnEN2VIutLQpICgQdxe6CPgm3zkZWE2UDYiN65FcV2NsmKLUcCTFGo2MsBVlalz%2BFK%2B30snrV5TjCrEsqO5IsUkkkAHeA3%2B7xVzFaprFGnuOPMCYcq9GmWJySXlrLOJcn1AIRKgBrVodBUBa9rDcX2u%2BLc0qzwccOmUmT0%2FhbClfxY5IzNYrFJxFIicapjb69SEpTfqOXUR6AqNVSHGLkpl%2B%2BuvZI8IeGMMYlWVqRU6hUFzwlVKHNpBvax3ttHNuP8AMTFeY2Jqhi3GNbmKrVam6XZmZfVdSj2ADklIGwA2AAgOj1eEHxczfosiMmt%2BdsNgXjyzfhCscuUurUqQycywpKa1TZilzcxSqUuVfLDyChQCkEdhvvcXjk0rWVHn8cQUVX7fjgC1aeqjdPLzjzRSieIFJ5wGVZUNJfzLwiyrkvENMH%2FqW43T4RN7peLrHaf1N9pP%2BZRGgMK12YwtiSkYmlJdt9%2BjVCWqLbTpIQ4plxK9CiNwDa1%2By8ZlxCZtHPTNzEOapohpHtgeD%2FiJeDpYshKdOsAavJve3bAa1iINoaYAW7YDenDrxSYu4d5LE9Pw%2FhPC2IZLFrcsifYrrDjqCGArSnSk2UlWo3CgeQjZI8IHiInq8O%2BSrfmGHyR8UcjAkcorIUYDtTLzj1KsfYddxdkXlJTaT7KyqZ2o02iliakmVOBKn21nZJQFar9wMZ1mxX65kFxN5v1Op561DLNGLm5OuYemG8KN1yTxSxoVZIUoHo1tlRR1ed7nkI%2BfDbnlIXpUlWykq5EdxjpPLjjEmpDL6Tyezzy3oubOCaXZNKl6o8WalS0WsEMTQBJSBYAEpUBYaiAAA2RmRm1UM48JYiyjwrxdzWYdSr7UlJ0fDz2WLMkKwt5adaC%2BhILCmiCrV2aR37bA4n%2BJ5rI%2FFFHyfkctsvscO4Yw%2FT6fPTuIpLxp5qZDQC2UKANkpsLgnmY00jjUy%2Fy4pU6xw2cOVGwJV59ksqrU7OmfnGAb7tKVfSRfbe0csVqu1Suz0zVqrOuzk5NOqdffdVqW44o3KiTzJJgOn%2Fq95oAIc4YMknAk22oUWTMDjfrGNsssQZXSeTWA8KUzEbzL845QGFy6luNLCkqKB1Sra1yL2jmbpD2mJFKvARWEr5RRKQmJrmJSL9sBLE1hEQLRMBAQSLmKyU%2BaJEjeKyRAVGUAmPQoWTtFJsWtHoQnXAZTR2tFMQtXakxf8qx%2Bb66rtTQaqfV4qv8A1RZpIBFLbT%2B5VF4yxYemJnETMv8AZV4dqoR6fFlWgNT4XN5yXPmQPxRt%2FhhTfiowD5sa0r%2F71qNdYdw1PyK2ZuoKlWQgIWoLmUhQt2gXjYnC4%2BiZ4pcAzDataXMa0pSVJ8kgzze8B%2Bg2EIQCEIQCEIQCEIQCEIQH5%2BeOA6uJ%2FMtP%2FwC01Q%2F0pjQ6WdVjblpjf3G5Lk8UWY%2F7rEtQV6ulMaTaDSZdKphQShsh0ki5PZYAQGSSCnAlTbKwha0pAWRcI3HWt22527SAI2%2FmPmnQEYbk8nskZWepGAKXMs1KYnpxARUsR1VBC%2FHprn0aEuC7bI5Wue6NP0B2n1F11qkza5mYSx03QqYLbmlJ61r3vYb7dke6%2Fn5c4Da2LeKDOfF%2BJMK4wmK9JU%2Bq4LddmqSqRlA2jxl0BLzzibnWpxAKFC4Gkm1r3j31jNjLQZnYBzowdh2aw%2FVZWqNVTGVJQgGTbmUujpH5RfNSHG1OKIIuki0aYgL3uOfaO%2BA%2BiPG9lRM5tZXS1awYTPTVEWarLBj3zxyRdb5oA8ojqqFr7R8yGKm5SFKlHGdakmykm6VJPcQdwfNHYfDfxhvZX0uVy%2BzAp0zU8LyoKafOSo1zdLQbnoijm6zflbrJvbcRu%2Bp13gazAJxBVKnhBbryg46ZtgNOhXbqTYKv384DizhtyqrueWZtHW1T32sO0KcZqFaqAQehaQyoLQyF8i44tKUgDe1z2R0T4Q3F8u9iHBWWsu8hU1QadM1eqISblh6cUOhbV3KLaCu3YFJ74zPFnGJkrlRh04dyKo0riCoSxPijbUp4rRJFdt3nNgp9XclI3PNQEcO4hxBW8UVuoYjxHVX6lVqtNOTs%2FOPG6331m6leYDYBI2CQANhAWxRtAKJ7YKG8AIBcwuYjpENIgIXMNRiOkQ0iAjHplEzAmGUyjUw5MKcQGES9%2BlU6VAISixvqKiAPORHmG5j0ysxMSczLTsm8pmYlHm5lh1HlIdbUFIUPOFJB9UB2Ng%2FAGJOE7CrmYMzg6q41zixTLGSlJaVZdnGKC15RS%2B8m5UU2TrtcqKQhOwJjjifmJyYm35mffW7NzDzj0y4oWKnVKKlkjsOonbsjZbXFLxEy0y5NsZuVtLzqy4tYLYJVzvskAbxrCZedmpl2cmFlb0w4t51Z5qWpRUpR85UST6YCUEkc4jEBtEYCSI3MT9HECgCAgeW0Q35xNEQICERc2l3B%2B5iMRU2l5BbKCUnmRziM8kO5OIjMfJnAWZOGpzGuTb%2BL8TSOHaZUpGfM4GWGk6LstqTfrFKkkg2NowugZnY2rORub%2BfeE3vFsxK9jWVkK7PSCC7M0ehdGlTLUsCCUoPIrt3nnHO2PcycXZnVqXr%2BNZ1ubn5Sny9LZW20ltKZZgENJ0ja9ibntifL3MnGuVleXiXAtbXTp15gy0wnSHGJpq99DzauqsA8r7jsMSluySxTjPMTg5zUnc2qrO1Wl0Cdpr%2BEa3VE%2Fms1BUwkOSzbhALibEj%2BERfaMv41qxl37bZvCCsratP47XQaW9L4nYfUZeTYt1WlNC%2BshCVA7fC80c85l56ZmZuyspTMdV1qYp0ivppenScsmVlEO8w50aNiodhPKM%2Bl%2BN%2FiHlW2fFq5QQ6whCUvOUVpa1FIsCok9Y2Av3wGTcF2MMspDHdNoM7ghUnjASFYfXi5%2BrhEuJYNFSpfoFEBN2xoue0k98aRzIxJlvimuylTyuy%2BewZTiwlqalXqh42JmZKz7%2BlXwEkKSNPpMYdOrNSmX5udQ267MvrmXboFi4tRUogchuTsOUSA69SH0a0K6qk%2BaLjqLh2pcrkTm5hvAebGQk%2BvGWIqmp%2Bh15663qcy43pGhsXQpIUFKK73Tqja2CMO1eSqvFhgCoYjdxLiR1xmdXUChKH5hmYprhZSUp2Gm3R2HLbvjm7DvF9n%2FhihSuH5LFspMMSTQYln56QbmJptsJCUp6VW5AAFr9wveMJwlm9mNgnG8zmLh7FU2ivz6lGoTT5DvjwUbkPJVssXOw7NrWiIjJExm3jhdxct4NfFs8%2Bh5hVTxCXKR8AqmUz0sWlNg9y2XPuTHStaqVGrcpIcWl2PF6dlJU9CL9czM3pWCD2aVBaPXHBOZWfWZebSJGTxpWpZVOpq%2BllabIyiJWVQ7a3S9GjYrsTueVza0UkZ6ZnIyuOS%2Fs837UC14sZMS6A70HS9L0XTeVo1729XKJMnceRMixmLhfInPqu1EuzuD8JVmm1XpR74%2B8pIbcUpR5KQWVKP7%2BPnpijEL2LsR1fF0wVF2u1GaqatRuQHXVKSPudMZVhvP7NjBeCZ%2FLrDGJWpKgVJc2t9nxNC3R4ykJfCHTulKgL2HIkntjXfkNpbR1UJTpT6IolDSdeoq2iV1xI2BhY253iUpv2QENd%2B2FzEOjMNJHbAR1w1xLYwsYCpGXZS0aYxLmjg%2FDslXjQ5qoV6Rbl6mACZNwOpUl0X2KgU7A7EkA84w8BW28V2V9GpLocWhTa0rQtCilSFA3SoEbgg2II7RAfUmXrNPxXxD5gZXSOXNXwpXnsLsMqzLlZZCHX21JbFgSNKVJUsBNrlRbWDbSmPl1UZNNNnXqa26h0ST70r0zZJS90bhR0gJ56tOq%2FnjZFW4oeIau4cewjU84K%2B9TH2yw4kOpS6tsiykl1KQvcbE3vz3jVoATZCBoCNkjuERMZiKiQbXVbzRDUqxsn44K1FW4v57xT629yYkRLi7xN0irCJOjVE%2FRqsICRTqidA5QCiOZETlB3A5HnEOunYjbe20BMglXOJlXHKJEoWrcRNoWIAlaoipSrxLYxMEkwENcR1xKUkQ0mArN781xNMTs3KU2pqkZyYlVv0%2BYlnFsOFtSmloIW2SNylQABHIjYxQiZfXQptfWS6kpUnvBFiPigOuuM5TNOxbkLOOoQiXlMMU511I8ltLcxKrUfQEgxtXEeGMTTXhIsNYqZpU0ujzGGEzaKihoqZ6ES7yFjpBsOutva%2Fwx3xwrirMXHePG6Q1jXE03V0UGS9j6d4yEXl5bazYsBcdUc7nYRkUtxB51yWDTgGUzMrbNE0dCmXS%2BNSGrEdGly2sJsbWCuVhFpjMeDOOrU%2Bu5uY2rFIcQ5Izdfn3JdxHkrT0pGoeYkE%2BuMLue%2BJ0dHo0I6qUeSmJSLwiMhCETWHdDbzRUSg2iJX54aREqkwE4VftidF4pRW6RfR9mnUPkiM8idbrTAeIMAYd4IcPVXM%2FLhzGVGGPagw3INzXQFmZKlBuYvcXtYpI%2FdReMlc26VnTxE4WpNMwVTaDQ8vMH1heAMPPuBxKquG0lDjnwSrTfSkXta9ybxyk%2FmJi57LtjKhyppOFpWsuV%2BXk0tAKTOLRpUSvmpHNQT2KJPmi1UirVOh1aTr9Hn35KoyDyZiWmWHChxpxPJSSOX5QSImdaHV%2FCbmlxBY84gmMIZi1utV6j1FM2nH1LrcqfFJKXDSiolKgAyUr0pSL2UCefOLphmvZTYU4OMDDHuXM7mBh0Y5xBK0qRknClxlTc1MdFM60kEJ6Pq3%2FdCNI4w4s8%2BcdYemsMV%2FGgRJ1BvoZ5UjJtyr0039o44gaiCOcSZZ8U2bWU2D2sDYQmaIikSbjrso1NUxDq2C4rUtKVE%2BSTvYiIiMkrRlXiHLjB2Jp97NLLScxBJzLkv7HMqnjKrpbwmkqDjl7dIkIKd%2F3F%2B2Nu8cGLMsanmPiTDdOwa3MY1k5ynuzOMGKl0jMyx4uCqXDSSUkhKkJ35WJ80aGzLzMxXm5il3GmM5yWfqbsqxI3lpdLDSWWgQhIQnt3Nybk%2BoRiujo20I%2B0iUTGbaWXeEJvA0pJZ7Y3yOXj3L96Vfkmh0vvS5hxzo0LGm51ocSpGhQ5q37I7Mr0s2zxX5GY5mqvMt0zE%2BF6vSKTQpuXS0aPMCTQ7ZCeYK0HQb7haNPK0cV5WcRubWTNMfomB69LCkvvrml02elkvsdKq2paQd0FRAJsbEi8WjGucmZGY2K5PHGLMTPuVymlBp8zLe8iR0LC09ABsjri5Paed4iYzIjJ15wyyVRkuMXPetVaVXLyMiZoz762yltaHJtDyLqOx96SV%2BiI8NVIpmdXDDScCB5KVYMzGanW9gR4s1UPHmUJHYFNPLSBHOmMeLLPHHmFZrBtdxLJtU%2BoN9FUFSEkiWfnEHml1xO5BGxAtcbcox%2FLHPXMzJpqpsZc1iUkGas40%2FNNvyiHwXWklLa06vJISSNue3dFoS7CYrLPExKcQ2Wz08hZkMwKbO0rpVFTTMmw80DptySXJV6%2FncMc%2BcdWL28TcR9dlJWyZTDklLUlpF90LKS86PunR8Uazy9zgx5lJV6jiDA1Tl5ScrDQani9LpeQ%2BnpelOpKtr9ISq%2FnMYtiXEtbxhX6pivEk4ZurVqbXPTz5SE9K8vyjYbDkBbuAhI8Ou%2B9%2BfZEpKlcolCFK3vtE4BG0QIKCuUSpKuZiZZJFgYlBPOAnhC474XHfAIvGG5mcaq9PRLTkwymYqEmy82y6pHTI8YbIQoA9ZOoA2O20WeKzL7su83MMOFDrLiHW1pNilaVBSSPQQDAds8QlQkqV4QbLScqykNSbKaP0ilkBKFqdmUtk35dcojYPiMjmRxJZi5O5i5E4fdwXJUdM87iWYpVp5c2WmtT6ppQt1gtwICSCgS9zcXjgDG2O8W5lVt7EuO69NVmqzDLTDk3MEBwttkltN0gW0kki29zeMqrPEfntiHCXtGreZ9Ym6OppMu42paUuvMgWDbjoAWpNtiCd%2B2IiMhr6aal2JmYlpWZMyww%2B6y0%2BTcvNoWUoXftukA388UIibBNk2AFrAchEtx3xIHlEtj3RNcd8TADvgJLkRKTFQpB7YgUQFO5iaJggeaJtAgJLmFzE2iGkeaAkJMToueYiBT3EREBQ7oCaK0i9MSk4xNSj7jLzLiXG3WzpW2sG4Uk8wQdwRFMIUReIosF2uEwzzHT2NXlS%2Fg8sCTLylOKXit9x5alFSnff5tRJJ3KiQbxuOiTrOWWTmQlCxdl9N5rLqs9KCQnZeVQsUFKwl1lTagDq6LpAAo2uEKueqI4fmsd4znMEyeXM3iWcfwxTpgzkpS1FPQMvkqVrSLXvdazz%2BEYyPA%2FEBnRllQU4bwVmJU6dSE6uikiUutMatz0YWDoBJvYbX7ILTGbMuNPD83h7iBrYn8UvV16qyctUkOvBIVKsrCkolQEgAJRpOntKVAncxoe5i5VqvVrEtTma3iKrTNSqM650szNzK9Tjq%2BVyfxDkItikm%2BxEREZIySKN4lBsd9oqBN%2BcSlNjEoSnntyiZI7%2BUFt7jTyip0dk9blASXCYi2dTo7hziGi67X2idTZTZQPp88RKHVXCTUMPUnJLPet4sw8qvUKSkqa5VaWl0JM7LpQ6ShJJFiSR2jlElHzlyvzExRltkZhnLKSwRlnM41k6pXWX3wtc%2FNBRLSHDcgNlzRck72SOUaCwxmVjHCmDsWYBoFTbl6NjVphqsMllKluhonToWd0bEg25iMcv73ocR%2BTluCLcjeGREZOqsaZr8VcrxaqozFXxLLVOXxKinyVBZlymmqpanwlIW1bQtss3JdJ2332tG0Ojy1wTL8WSxghOIMGU%2FFtMMxh%2BniyZgqlGy%2By3p2Gl5SjtysY5oluMXiLk8OtYaYzDX0LLHiqJ1cq2ufDfYPGCNVwNgecWXKriBzOyYFYGAarJspr8y3O1AT0oJouzCQodLdRvrUFnUre8WickvI%2FiXLiXzamsVVfKCfGCHJh59OD3ZtbDhZLWlCA%2BednOvse2143zxLY7yVncscAUSVy4cqMzU8CqOGZxmuEe1YLcRZpYST0q0qTcg87WtvcaEzXzyzMzofpYzCrUlNtUUvKkGJSRRLoZLunX5O6r6RzO3ZGBlGhCtCUJStV1JTtc9588WGbZeYKr1YW7mQjKV%2FG%2BFsGTSX6%2Bwi%2FQKbSjWplwpOoXQdXVBIAv3x1VmDUKBjDI7IrN7C8rNYOwVR8dUbp8IvNIRLpQubU2l4GwUotq1KBvpUlZVzF45NyyzazBydrLuIMva%2BqnvzKA1NMOIDstMpBukOtK2JFzZWxFyL2MXHNPPXMjOlMpLZgVaWmJKQK1S0hKS6ZeWbWoaSvQnYq07AnkCbWiJjMdZ47o9ad8JXhVSZSbU2mkszaHg0roSy3KzKHuty2WtIPnUO%2BJsDz9IzTxpxYZJyc2y3L4kmFTctMp8lCnWfEZlYHbpdbbUfVHO1P4xeIORwyjDCMYyzwaZ8WZn3pJtU622AAAHe8AAAkX27TGA5fZn4zywxG9i3BVXEnVX5d%2BTfedbS8H2XlhbgWFXCiVpCr877xGQ7raxVKVLiGxPw6dOn2NXk%2FLUKXb%2BCidbYJdJHLUWn0G3cmNGcZ6pfBeF8ncjpJaFJwnhhD0wW1XSXAhEslR%2FfBp1QJ%2B2MaTl84MwZbNFzOZiuJRi52YdmXJzoUltS3GuiWC0erpKLC3ZYRbMwsx8X5p4kcxfjeotzlTdlmpMuNspaSGWrhCQlOwtc%2FHETCYYssK1G3KJVcu28VkqTyCbxI4pSfgiCFNCL3JVFRSLqABvESE6dyLmDaeZTtASqZIOxhbbQPXqibo19JfpIFpaUlXSavNExOSYnJKFHlGXZWYExjmfjiQwRgSYdlqrONuvKmUTK2USss0NTr7ikEEtoGkkdpKRGIBJMXzCWLcVYErAxDg3EE5R6j0DkqZiVUAtTK7a2zcHqnSm48wiZjNZ1Fn%2FACruQWSM%2FkLlJhGuzMpOlqcxzjF6nrEsekcaCh0ltPW971WNm2wBe6jHQuVMjhXClWwbgjK3G2F6jg7DVDnVztNps6l%2BpViouqbCpxSU3HRpOq6ib6lpFrRwLiHiHzzxbh%2BbwniXM%2BsVGj1Bky05JvFBbfZKtRQoBPIkAm28YvgbHGLctcQDFGXtdfoNWTLrlfGpRCAotLIKk2Uki10pPLYgWiMlclfMfDreEcd17DCK3Ta2KdUX0Co0t7pZWYC1dJdCu0p16FDsUlQ7Ixde0VyuxUdKQVrU4rSLXUpRUo%2Bskn1xTWgr5RXIyUwSo6T2f784gs6dgCo8rxOptdrCwHaOwxKGSvYBV%2B0RKEiQ4ny7WiJIPI7RHoSnybkROhtw8yAICVKU3uYlWATziv0IES9FvcQFHTbsj0SlQnJJSzJvrZLiShZT2p22%2BSIdEpWwtEnQG%2Bom1ouPairVJXlTTh0%2BiKM5OzM0EofeU6lFwkn5YpdfkLWiVaLbiInWJ2iADbtj0yAlPHJdVQRMrk0vtKmkypSl5bGsdIlsq6oWUagknYG0eNFwdzHskEyblQkmqlMuy0i5NMNzj7SdTjMupxIdWkDmoIKiPPaInUmXduQuLMD53V6pYapnD1hzD%2BTVFohYqM%2FVZZBnW521z%2BaRsbNgqKgbpI1E8gbBw74bpctw0zlewNSsvajVJnHNRkqVUscBroE08TCWmg44bHpFICClPwiokR7sYZxcJWJcCyuUFCzarmD8Ey35nmJSkUN1Ls8xq%2FTnVpudVtS9rrPPbaOfMIYc4WMb5dTWE8w8b1vBOKpWsOLbrrjLkzJ1ilh1XRaZYHo2XujKQeSkqTcXBsJic1YhR4maLj6gZoOyOZWBMMYWqgpsumXRhdot02flklYTMt%2FbLJ1JWTY9QXAjUi%2Bcbr4rs6cN5z43o85g5M0aBhqkJpUk9NNFt2ZUV6nHClW4TdKQm%2B53PbGk%2FLgZIE98QYecZWl9hehW%2BlUFNq7IlQN7JimeSXq9k6g2kpRNLI9Vt%2BcU5ipTr7KmpiYW42o3KCLi8U9G0QKL7aVfFEiTUFKB5W25x6EBOkC%2Bq3n5xQLRRY87G3LlFWWBVYHayu7lvAdQ8PmYuFFIwLlHlhkdT6zi2oT6VYwrGI5dt9pyUVdUy40Uk6EJFgkKA2SBuVRtHCXD%2FlP9Upm3WsL4Tk61TsESVOTS8PuOaZFmvTLK3Xm7nZKEaUbKJCC6ofBtGJZFZm8N%2BV%2BURpUpmg%2FhjG%2BJpPXX6ymmLenZN9f6SwSkoSltIGi1wSdR3jGsqMzMmMosYZj5XSOY1bq%2BXmYdGZa9uj0svxiVrC2HEPOOaeuUkO7rtspO%2FfAScU1CxknAOGMVYqymy6lXn5wM%2B3XAlU6aVcvq%2FMsywEgDUfJXc2U2QDvaOW3F9kdGZl46yuwXw24d4Z8qcbKxkmXqiqrU6y3LqYYRZ1TnRoQobFbigQBySCb7gRzmtveLQmFIntiLa3G19I31VJ39HniJQQoDviboj3RVD0rrFS1%2Fo5fxj5opu1Gdc3W%2FrBPLtikWQNiNzEOjtASarmKjabxS02MVW1WgOisk8xsuMPYaw%2FgfA2QoxxmnWqi0xUJityiHZNTC3PfSwQSUoQ2ALqSLXUpRNgIyHiAm8rOHPiSrBwnlXhTEVKqeHZSYnaJUlL8UpU8paipyX030FaUpVoIsNW1gbRdeGTMDh4yuyump85r0%2FDeZuIJZ3x2pTFOcmXqQjWQ000gp0qASAsi9lEi%2BwjTVdw7koc76FS387nMVYJq0wzVcU4pnJVxDheK1uOy60i5Kl6EI1DYdJ3CLQNz8Qz%2BB5Thdw9iGrZNYXwljPMScYmqfK0hkBySk21dL0yl2BBU1oCk2sS4BHHrjnSRuDirzhk85s2p2t0J%2FXhmiMIo%2BHkISUo8WSAXHUiw2Wvlt5KUiNNwgQJI2gCYhpMNJiouSa7UUoSgOeSAkEgXsBYRTXVag55b6viEePQe%2BJyjzwXU7DsJisAdG14oqBHfE%2FTBKO2Cjc2TWNsm8BYZqlRr2W85jzMubm0y%2BH6TNyhVSw2SkI98Ct3FEkkFJ8kAcyY6Dx3klkE3xHZN03FOG6fhRnFtInprEGG2HyJRVRbaQZZB3ukqWpxBAIC%2BjG3ONf8GVa4e8DyFQzDzJxvR6bjZM0qVpUvU0qLclLJRcTDYAIUpZJBVzSE2Fr3i7UjMTKXL7inw1nPizO%2BXzSarsjUJGsVJulFtjDsypTYlHAyL6WAnWgEXUm5UecWgZTm%2FlrQJTJPM2sZr5L4Wy9qlAnlS2CKhRXFB6obp8WKgFEK6U9QhQFwo7DTeOHT5ZjtLEOZGWWDcls2MNVvP2VzbXj6ZnJmg0oBxxdM6fUUJKl%2FYg2opXdNgC0NIBJjip9fcpSlK8pXK57TaKzCYSKBHbFMqI5mIage2GkHtgg1X7YREIicIFoCUDvgReJiLQAvAQhE2iI6DAUjuYiU3G0VQwSLxAN72gKaOcVAL9sFI09kEns0wEizY7QtteJ1p3G0RCdoCDdu1AV64jpB7UjzRFISDuLm%2FZEQD8E9%2B1oD0S9RnZOWMmw630C1a1IKATfvvzit7OVJZ98mG%2FWgRblhcSC%2Fw4CvNTTk250kx5WkJ8m2w9EeVNNpg8mnSo9DSYriy%2BouJigJISICgabSufsdL37%2BiTEUSNPvtJM%2FcCKxbMSbiAmVT5BYOuTllXBFy2kn47QRoQhKEISlLQ0pSlIsAOweaIo%2F31QP8AvaAk%2FwB%2F9URCO3QYj6PiVEUa7wEyLKGkgae0mILZT5PMHke6KmknrD4jEi0lNzc6TzB7ICQIKDYAGKTiNRsRHo6PRrbXq6vxD1iKTnU3gLe8hLYJI7Y1jNOVSpzLxbW4pCHDfSo2QL7CNlTi1k7dxjD6OwWKPNLQ8pC3pxSHE6tiEgFNx6SYDHVU6o9rTh8%2B5j10mVnWapLJUNGpenrecWi%2B63IoLeWiZl3gTcPI5WHMwFwXRJj9TVFBdHnRbU2q3btF7XV19bQy6P3KhEvszMqT0apdah33t64DxUyQcaWrp0dT90nzxdPF5XsZQfSmKUtMPvrVrbskCPQeUB5n0IQ3shKf4IizTi%2Bv5EXic8iLM%2F8AZPfOrAQfoE4XL9AqKLlEmkKF2FD1RljGJXmm0JVIE6UhNyLkgcooO1x1xADkq4spvub2sYDF52Wmm6c%2FdC0hKCb27oxttE%2F%2Blqd%2B6MZ9Uap0so%2B0uVASplYGx7osrD7nQIHV8kfigLKzM15hQUy8%2Bm3nv%2BONj0Kam25eXmXFq6XTqVqFiTyvGMJcWVJAULdlhzjK6YXHpVD7x1qXqJIFr7%2FJAXxuszn2qYlmahMzrYQ90YCVX5WPdHlShXYLROGTuUarnvG0BAnzRKfREwQ52iJg0s8xAUwbRKrnFZTducShHfASdeJ5dbjDnSfamETEXFoD1GuTrOyOj095REF1aYmWHGXCgJdTZVhYR4igkxMBaA2tklM5HS8jPDNmp1mTnF1BFjIT83LBUgGDYo6AFK3Q9a4XYaeRvG11v8CS3LnGOOb%2FAPnNQ%2FHaOUoQG6M53eHpWFlN5S4lrc5Ppn5YyzE7Upx8dAUqEz0jTydAsoIKVpN%2BdxHl4dM5sEZKTlbruIcFTtZrc%2BhqXkZyVebQqSYAPSBOvkpRINx2CNQwsD2QGb5s4nyyxbV2qzl3hfEVHmJovO1hdZqgnlzby1ApcSq3UsLgjlytyjA4n084hAVZFAM%2FJ%2F8AiWf9ImO9lXdm1pQbqUfjjg%2BlKl2qnJTM4pSZaXmWXn1JTqIbQ4FKIHabA7R1G%2FxUZKuzfjDE9VVJV1rmQKbeaxO8ZrGnhVTPmj3sV5q4NER6eTPwNmNoQdWgpT8HZN7GJuijVaOJ7J5skszlUSVne8irn8cTp4oMpSTrqNSAB2tIuXt542uD%2FWbS4XmnmltllvbeK%2FRptzMakRxPZMauvWKqkf8Al64rjigyVSerWKiR56eu8WinUrNXmnmlsx9nkQbd%2BqIFlLiSlKt%2BwA7eqNaDijyUULKrNTBB7Kcs2imOKDJUrUFVepJT2KFOcJ%2BKLxQcLzTzS2L7G7%2B%2BR5KnQ0uJTZF9uX5YwdXFHkgfslbqh%2Fya5Ex4qciy30iq5VDtaxpzl7eiKcHJHCjz80rBjynzcnTJxxCblKFd1iO38sa9pksVqTfsTGxcUZ5ZB4ios5TJPE9Sl5t1s9EtdKd0FQ3AJ7OVr%2BeNRtZtYOkTrNPqTqfthLjcd%2FOK1bWSymeSJ5mkMxkdHiiv8vszfP0xLihNsYPj922f5Aj3Y2lXcQ1KsVuRlXkykytEwjUg6ggna4i2TswajW3KglNkuaVW7hYD8YjQq2uhGxmdDQTLugjmIx7EcsUK6vbGR0RzS2oHlaMexXODxgISOyISx9LJUrckx725ZQTsgx5pF0LcAWk84v7baCgabiAx6al1DsjyBtQc5RkM1LhXZHkEmC5ygLfjI%2B%2FU7zSKR8SlRfn06UJ%2FepirVsC13E7ErUaRJrdaZZ6BZCkAagSbbqHfGZKy0qa2mwqdaTdlBAUgk8uVxzgNeuLUk7GKXTr74ztzKmrHbx%2BX%2BIxS9yStE7VGW%2B5V80BhPTr74dOvvjNxlBWD%2FwA6yvxKif3Hqz%2Bysp9yYDBenX3w6TV5RjOvcerPZVpT7kxEZPVy1%2FZeVv3dGqA1%2BuxMUo2MMna2f%2BcpX7lUTDJqsnc1OUHqMBrlMVEdkbA9xytA%2FwBspT7lUT%2B5BWgP7YSv3JgMERCM59yWs7j2RltufVO0PcjrfbUpf7hUBgp5RTIMZ%2F7kdX7anL%2Fe1RKrKepJGpVWlgO%2FQqA1%2FZXfCy%2B%2BM%2FGU1VPOosD%2FAASoe5LVP2VlvvSoDXwBvE9toz%2F3I6qeVUl%2FvSoj7kVW%2FZOX%2B9KgNfpb3iC0kGNiIygqxH9tGfvCjEVZQVQcqoyfRLrgNbqSecS2jZHuP1C9zVUfg64m9x%2BoWv7Lo%2FBlQGtxziuhO0bB9x%2Bf%2FZlr8HVEDlJUk3tVmiPMwqAwHSImjOvcoqXL2Ubv3dCbxP7k1TP%2FADin8HVAYFFNeq%2BxjYasn6mB%2FbEn0MmKZyfqnP2RR62jAa8sYWMbC9yGo%2Fsk3yv9iVEwygqF%2FwC2jR%2FwKoDXFuyJ9EbG9yKp9k%2B196VA5RVT9kG%2FvJgNc6PPE2jzxsH3I6v%2Bvm%2FvRiojKCrEfo1v70YDXYTaKqY2AcoKmOc8gehoxMMpKgBvPj70YDA20qtHrYT384zRGVrydnJ9w%2BhqJ15cuMgETMwVdlk2gPEwfzuT%2B8MXrLVbbb%2BIFulQQMP1G%2Bnn9hVyixVGnz9MZLCG1uDfSSIyDBMuMO4axDizFra6dJzNKmKbT1vJI8Zm3khISkfCCUkqXbYbDmYDXvvbkov7bof6MZ%2FwjpH1ROWqk%2Fttoh%2F9a1GvZydpb0qWqf4zdaCF9IgICTYjbc3%2BSNncIUmXOIHLpSb%2B94sop5DsnGjAfoHhCEAhCEAhCEAhCEAhCEB8y%2BMjwdua%2BYedlTzGytlZGqUnELhnJlhyabYflJpVukBDhAWlSgVAg3GogjYE8UcR3DDmTw%2FViSw9jGlIQ7NyLc7LqYcS6hxBUUqAUnYqSpJuOYuDyIv%2BguNf5zZGZdZ8YaRhrMKjGabl1l2Tm2V9HNSbhsCppyx03AAIIKTYXBsLB%2BcdhU9ITbU7Iuvyk1LLC2nU3SttQ7QY2vKTaKlKtzVSoNOdfeaStTrQUxrJF9SkpNrm8fRWveCbo8xUnF0PMVwSRV72mcbBcCfPpRYmL9QfBdYXkJJiXqeNH33GklClNiySm%2B1gUwHzQ8Upn7Xmfwlz54eKUwf9Hmvwlz54%2BpP1sjLU88S1EehafoRL9bGy1%2FbPU%2Fu0%2FQgPluGKSk%2F8XUK9M06In6Ol9uFmj6Z1w%2Fkj6gK8GLl98DFU%2BPSofQiZPgxcu%2FhYpqPqUn6EB8v1ppavJwuhP%2BPO%2FNEnQUztw6z%2BGu%2FNH1GT4MbLYeViep%2BpafoRU%2BtjZWnniesD0Op%2BhAfLgMUX4WHkH0TjkR8WoP7X%2FwD1rnzR9Rx4MTKq%2FWxRW7f31H0In%2Bti5R9uJa79%2BR%2FVwHy18WovwaAfwxz5oj4tRe2gH8Lc%2BaPqaPBjZPj%2FAKTYg%2B%2FN%2FQiqnwZOTA8rEWIj%2Fh2%2F6uA%2BV%2Fi9G5%2BwZPpm1%2FNEegon7X7f46v5o%2BqifBl5Ijyq%2FiM%2F4dv6ETjwZuRgG9dxL6n2voQHynEtRLkqoKiOwCcXt8kTeL0L9r6%2FwxfzR9WPrZuRP7OYn%2FCGv6uI%2FWzshv2bxR%2BEtf1cB8pTL0Lsw%2Bv8MX80Q6CinY4eJ%2Fxtz5o%2BrZ8GdkP2VvE%2F4S1%2FVw%2BtnZDXv7N4p%2FCmf6uA%2BUnilBP%2FAEfV%2BFufNAyVG304fUe682vb5I%2Brw8GnkOP%2BesUfhLX9XE%2F1tXIP9lcU%2FhbX9VAfJ9MnR%2FhUA%2FhbnzROmSoduthxZPO4nV8%2Fij6wJ8GvkAPKqWKD%2FjjX9VE58G3w%2FnnP4o%2FDWv6qA%2BTqZCip5UFXrmln8kVFSlBVzw8v8MX9GPrEjwcHD2kdaYxKr0zzf9XE31uHh6%2FVsS%2Fhzf8AVwHyY8RoV9sPL%2FDV%2FNEW6dS%2Byhr9U0sfkj60J8HHw7jmrEp%2Fx9H9XE31uXh17sS%2Fxgj%2BrgPkwaZRk7qoqzt2Tiuf3MU%2FE6PyNDWf8bWP6MfW1Hg6OHRPNvEavTUEf1cTfW6uHT9SxH%2FGCP6uA%2BSKJKjDnQl%2Fhiz%2FAEYiZSj2%2FtCr8MV9GPraPB08On6jiI%2F5QQP%2FAG4j9bp4dP1DEX8Yp%2Fq4D5HiWoyTth5y%2Ff46s%2F0YGUoh8rD8x%2BGLH9GPrl9br4c%2F1piD%2BME%2F1cQPg6%2BHLtlcQfxgn%2BrgPkaZSjcvYF3T3eOLv8dopeKUNPOgPn0zyvox9dleDq4cFc5TEHqqKfoRL9bo4b%2F1piH%2BMR9CA%2BRCmKL2UJwemcWfyQEnRlj%2B0zo9E2v5o%2BvH1ujhv%2FWeIP4xT9CJvrdnDd%2Bx9d%2FjAfQgPkGafR7Eew7u%2Fb40vaJkUykW%2FtM%2Bf8aV80fXr63Zw3fsfXv4wH0IqfW8%2BHH9jq3%2BHj6EB8f10ykX%2FtQ%2BP8YPzQ9jaV8GjEel9Zj6%2Bq8Hdw4K%2FuGvD0VAD%2BhD63dw4frGvfxgn6EB8gvYyl%2FsIv78uJfY2lfsOv78qPr99bt4cf1nX%2F4wT%2FVw%2Bt2cOP6zr%2F8AGCf6uA%2BQPsbSv2HX9%2BVETIU4ixpCtP8AflR9f%2Frd%2FDh%2BsK7%2FABgPoQ%2Bt38ORN1SdfVsB%2FbBI%2FEiA%2BP8A7G0r9h1%2FflRUTTaUka%2FYNYCtgemXzj68%2FW6uG%2F8AWeIP4wH0ImPg7uHI85XEJ9NRH0ID4%2F8AiNMv1aMr78s%2FkifxGmW%2FtMfvqo%2Bvzfg8OHJryJOveufSf%2Fbip9b24c%2F2Prn4ePoQHx7MhTj%2FAMyJ%2B%2BriBpsgeVFT99XH2F%2Bt68OX7H1z8PH0IfW9eHH9jq5%2FGA%2BhAfH9umU%2B29FT99X88RNOkf2GR99XH2C%2Bt98Ol7%2BxtZ%2FDU%2FQiCvB88OatV6bWhq52nxv%2FACID4%2FGnSP7DI%2B%2BLimmnSd%2BtR2x6HFx9gx4PbhzF7SFdF%2B6oD1fAiP1vjh2%2FWlf%2FAIxH0ID4%2FinyR29h2%2Fu1RN7F0%2B1zSE%2Fdrj6%2B%2FW9uHO1vY%2Buenx8fQiJ8Hvw5q50%2BufxgPoQHyB9jqX%2Bw7f3a4lTJU4LsKK192v54%2BwKfB88OiPJp9cH%2BPj6ERX4Prh1cFl06tn%2FHh9CA%2BQokKeRtRWvu1%2FPA0yR5%2BwTX3xXzx9d0%2BD24c0iwkK7bu9kB9CJvrfPDp%2Bx1b%2FjD%2FYgPkIKXIH%2FmZof4RcTex1P2%2FORnb90v54%2BvSPB98OzagtEjXAR%2F9eD%2BNEFeD84elc5av%2BqoJ%2BhAfIbxGnjnRGT6XHB%2BWHilL5ewTP31z54%2BuqvB7cOq%2FKlK%2Bf8AKA%2BhEv1vHhy%2FWVf%2FAIxH0InMfIvxCl%2FsKz99X88PEqby9h2bfvl%2FPH11Pg8uHI%2F3DXv4wH0Ih9bx4c%2ByUr4%2Fx9P9XDMfIrxCl%2FsM398X88REjT%2Fg0Rk%2BlSz%2BWPrn9bx4dP1tiD%2BME%2FQh9bw4dP1tiD%2BME%2F1cQPkd4nI%2FsGx90r54nEtT0j%2B0ct69Z%2FLH1t%2Bt3cOfZK4gHoqIH9CA8Hfw6jkziP8AjIfQgPkkWJL9hZX4lfPEvi8j%2Bwst9yr54%2BuA8Hhw6DnLYhPpqI%2BhA%2BDx4dDylcQD0VEfQgPkf0VOTyw7L37yXPxXiPQyROpVAlrHmAV%2FJvH1t%2Bt3cOh%2FScR%2FxkPoQ%2Bt3cOn6jiP%2BMh9CA%2BR%2Fi9P%2BFQZZXpK%2Fnh0FMtb2uynp98%2BlH1vHg7eHa1inEp%2Fyin%2Brh9bs4dO1rEh%2Fykn%2BrgPkf4vTeygS38v54m8Xkjv7By9z3qXb4rx9bvrdvDp%2BoYj%2FAIyH0IifB2cOSuctiL1VEfQgPkmliQFtWHpM9%2B6x%2BWIBiQJ%2F4uyqf4a%2Fnj61%2FW6uHL9QxJ%2FGY%2BhEw8Hbw5p3EviK%2Ff7JD6EB8legkf2Bk%2Ful%2FPE4RI20rw9IqHZ1nBb5Y%2BtB8Hdw6H%2B58RD%2FACiPoRD63bw6fqOI%2FwCMU%2F1cTE5D5M9DTej0e12T1fba3L%2FjiCmKaR1cPyqT361%2FPH1q%2Bt5cOv62xB%2FGI%2BhA%2BDy4dT%2Fc2If4xH0ITOY%2BSRYlikhNGkQT22WbfyorIbkk8sOSJ9PSfSj6y%2FW7%2BHTn4viL%2BMR9CI%2FW8OHX9QxF%2FGQ%2BhED5LrYk1KKk4dkE37LObfyodBJ3B9rsjt2WXv8Ayo%2BtH1vDh1%2FUMRfxkPoQ%2Bt4cOv63xF%2FGQ%2BhAfJdTMoUEDD0iCrmQF%2FJvtDoJGx%2FsckrkWv19vlj60%2FW8eHT9a4g%2FjEfQiVXg7%2BHNXlS2IT%2FlEfQgPkuGZZI0ihyJT29Vdx8sEtSABScPyJB70r%2BePrMPB2cOYNwziMeipD6ERT4O7h1T%2Bk4jPpqQ%2BhAfJrxen%2FsDI%2FGv54lXLyJ8mhSSfWs%2F0o%2BtP1vHh1%2FW%2BIf4xH0InHg9OHQf3HXz6aiPoQHyTTLyXbQZI%2Fd%2FSiboJD9r8n8a%2Fnj61%2FW9uHT9ZV7%2BMf8AYiP1vjh15eJ17%2BMR9CA%2BSfQSH7X5P41%2FPDxeQP8A0fk%2FjX88fWr63tw6%2FrTEH8Yj6EPre3Dr%2BtMQfxj%2FALEB8lfE6eRb2vyfpu588Q8RkP2BlPjc%2BePrX9b14c738Sr%2FAPGX%2BxEw8Hvw6D%2B4K7%2FGH%2BxAfJVMpTRzw9KH%2BE588R8Wp37XZP7tz54%2Btg8H5w6D%2Fm2tn%2FKH%2BzEw8H%2Fw6jlTKz%2FGH%2BzAfJHxanftdk%2FunPniHQSP7W5D7pz54%2BuP1AHDr%2BxVY%2FD%2FAPZiQ%2BD94dT%2FAM21of4%2BPowHySDEjf8A4t0%2F43fnioGJG3%2FFun%2FG788fWkeD94dRv7GVn8PH0Im%2BoA4drW9i6x%2BHj6EB8lCxI2%2F4t0%2F43fnimWJG%2FwDxbp%2FxufPH1u%2Bt%2FcO37G1n8PH0YDgA4dh%2FzbWfw8fQgPkmG5H9rkh%2FnPniOiQ%2Fa3If5z54%2Btn1APDv%2BxtZ%2FDx9CJT4P7h2P%2FNta%2FDx9CCc3yV0SH7W5D%2FOfPDo5D9rch%2FnPpR9avrf3Dt%2Bxta%2FDx9CH1v7h2%2FY2tfh4%2BhAzfJfoJH9rcl8Tn0oiGKd24YkSf8ACfSj6z%2FW%2FuHb9ja1%2BHj6EPrf3Dr%2Bxta%2FDx9CCHyYDMgP%2BjUkfT0n0odDIftZkfic%2BlH1p%2BoA4c%2F2IrH8YH6MPqAOHP8AYisfxgfowHyV6GR%2Fa5JfEv54dDI%2FtckviX88fWr6gDhz%2FYisfxgfow%2BoA4c%2F2IrH8YH6MB8legkP2tSN%2B%2Bzn0om6CT2%2Fsep%2Bwt5Lm%2F8AKj60fUAcOf7EVj%2BMD9GJhwB8OX7CVY%2F5QV80B8khLSiSkjD8jtzBC7H%2BVEympInbDFPHoDn0o%2Btn1AfDj%2BwdV%2FjBXzRN9QNw4ftfqf8AGC%2FmgPkf4vJXv7XKf6LLt%2FOiHRSY%2FwCjlO5W%2BH9KPrp9QVw3D%2FozP%2Fh64m%2BoO4cQdsNT%2Fo8eXAfIoJkvh4ckFffB%2BIxHoZFXk4YkPunfpR9d%2FqEuHD9qs5%2BHuRH6hThw%2FapN%2FhzkB8iPF5T9rcj%2FAJz6UPF5T9rUj%2FnPpR9efqFuG%2B1vajNfh7nzxMOBnhuH%2FQ6Y%2FD3fngPkN0Mj%2B1iQ%2BNz6UQMvJHlhiQ%2BNz6UfXv6hrhu%2Faa%2F%2BHO%2FPERwO8N4%2F6GPH0zzvzwHyC8XlR%2F0Zp%2FxOfSiPi8p%2B1mR%2BNz6UfX%2F6iDhv%2FaQv8Md%2BeJ%2FqJOG79op%2FDHfpQHx%2FEvIFX%2FFaSt%2B%2Bc%2BeIpkpMbjDckPQXPpR9gPqJuG79oh%2FDXvpRMngp4b08sBD1zj30oD4%2F%2BKS37XZT43PpRDxOV%2Fa3J%2FdOfPH2C%2Bor4cP2hD8Me%2BlE31FvDh%2B0BH4W99KA%2BPfsdKK39rcl92588Q9jpQf9G5T74588fYYcGHDgP%2Fl83%2BFvfSiH1F3Dfv8A8Hze5v8Aot76UB8ezT5IjfDUt9%2BdH5YkEjTgo3wxLEdg6d7aPsT9Rhw3f9XbX4Y%2F9OJ%2FqNuHEHUMu2Qf%2FFv%2FAE4D46Jk5JPLDMp63nvnicSVMHl4Xll%2F4w6n8sfYr6jnh0F%2F%2BD1rc3%2FRb%2F04mVwecOar6su5c3%2F%2Bqf8ApwHx18SoxP8AxWl%2Fv7vzxFUjRSjSnC0uFd%2FTO%2FPH2I%2Bo54cLEe5vLbi36Kf%2BnE44PuHMf%2FLiW%2FCn%2FpwHxzXIUNWnThNlNuf5qd3in7G05XkYdlx6XnD%2BWPsj9SDw6f8AVxLfhUx9OJ1cIvDmryss5M%2F41Mf1kB8a%2FYuSJ99oLKx%2FfnBAUumi18PMmxubPOcu6PssnhG4dE3tllJHULG81M8vvm0QTwicOieWWEl65uZP%2FuQHxpNOkNwnDzQ7vfVn8sQEhJA7UJoehxfzx9mTwj8OpIPuYSII5FM3Mg%2FGHIkPCHw5EWOWEnb%2FAMbNf1sB8aE0yQ%2BFhxn1OuGBptOsR7W2732PSuco%2BzKeEXh0R5OWMmP8cmv6yIfUi8Ol9XuYyd%2B%2Fxya%2FrID4yGmSXNOH2h%2FhHIeISYO1Da%2B%2BrEfZk8IPDib3ywlLHmPHZqx%2FzsS%2FUe8N3%2FVbJfhk1%2FWwWzfGsyMkkWVQUj%2FGHIlVJU0nq0MAeeZcMfZf6j7hu7crJA%2BmbmT%2FAO5E31IXDf8A9VVN%2FCJj%2BsgZvjGafT%2F2GT9%2FXEyJGmjyqChW%2FwCuXB%2BSPs19SFw3%2FwDVVTfwiY%2FrIgeEDhuPPKmm%2FhEx%2FWQM3xl9jqX%2Bwn%2FqV%2FNEfY%2BkfsETtb9FLG%2Ffyj7M%2FUf8Nv8A1UU38ImP6yH1H%2FDb%2FwBVFN%2FCJj%2BsgZvjL7G0m9%2FYIW%2F8SuCqdSiUn2DuBzHjCxf5I%2Bzf1IPDd%2F1U038ImP6yJPqPOGv%2FAKqad%2BEzP9ZBGb4zqkpBRB9r6bDn%2Bal3%2FFFMydN%2FYEfhK%2Fmj7OfUecNf%2FVTTvwmZ%2FrIDg84bByyqkPwuZ%2FrIGb4yeL079r1%2F3s2sfktEUy1LHKguD0Tq%2Fox9mfqOeGu%2Br3K5C5%2F%2Brmf6yCeDzhvSbpyvkh%2Fjkz%2FWQTm%2BM3ilKCSn2DXuLXM0okfJEBJ0cc6Dq9Mwv5o%2Byv1GfDb%2FANWcsfOZyZv%2FAKSJfqMOGz%2Fq1l%2Fw6Z%2FrIGb42GQpKudCH4UofkiJptKSkD2EO3aJlR%2FJH2QTwXcNqeWXDPrnZj6cS%2FUV8NhGn3OW7Xv%2Bjpn6cDN8b%2FEaZ%2BwA%2FCHPmiHsfSNNjh5d%2FtvGlfRj7HfUS8Ne98u0b8%2FzfMfTiRXBDw1KFjl6Pw%2BY%2BnAzfHT2Oo%2F7AOfhavmiQ0%2BiAm2Hlpv3Tix%2BSPsX9Q5w0H%2F5fn%2BMJj6cSfUL8NH7QV%2Fxg%2F8ASgZvjv4hRv2Bf%2FDlfRiCJKhtqJNAmvVPK%2BjH2HPApw0n%2FoM8P8ov%2FSiX6hPhs06faXMW%2FwDMXvpQM3x6NOoq%2FKoT5H%2FjT9GIil4e7cPTPqnlfNH2E%2BoU4bf2mTH4e788PqE%2BG%2BwHtPmdv%2Fr3N%2FlgZvj4aXhxXPDs96p239GHsVhz4NBnR6Z4H%2BjH1%2B%2BoM4bv2pzv8YORD6gvhw%2FatPfxguBm%2BQYpGH9yaFPnutPD6MTIpWH086FPfhgP9GPrv9QRw4%2FtbqH8YL%2BaH1A%2FDl%2B12pfxiv5oGb5Dew%2BHbdehVBX%2BOgf0YpexeHkiyqJUCe8TgH9GPr39QJw5%2FsDVf4xV80DwB8OJFva%2FUwe8VBV%2FxQVfIQSVAQAlNHqIHaPHR9GAlcOjlRqiPRPJ%2BjH12%2Bt%2BcOf7D1j%2BMT9GH1vzhz%2FYesfxifowHyJMph1QKRSKkASL2nEX%2BPTEFUzDyv8Amie9U2Pox9c%2Fre%2FDna3sVWfT7Ib%2FAMyJfrevDp%2Bx1c%2FjEfQgmJyfIw0rD52TSJ8f40D%2FAEYj7D0Mj%2B1c9%2BED6MfXL63pw6fsdXP4xH0IifB7cOpUVGn12x%2BD7IgAfyIJzfIsUWh%2FsbUPwkfRioaXh7a1LqA23vMpO%2F3MfXAeD24dRyp9dHoqX%2BxEfrfHDt%2BsK9%2FGX%2BzAzfIz2Hoh%2FuOc%2B%2FD5oiKTRk8pKZP75%2F8A1R9cvre%2FDr2U6uD0VG39CIHwe%2FDsTfxCuj0VH%2FYgZvkd7F0jtp8x9%2FHzQ9iaJ2yE3%2BED5o%2BuQ8Hxw7gJT4hXCE8r1EbfyIK8Hzw7k3EhXE%2BYVAfQgZvkcKZRgCBJToB%2F7cfNFP2Kpeq4lpv74Pmj64nwefDud%2FFcQA9%2FskPoQ%2Bt5cO97%2BLYg9Hsgn%2BrgZvkeaZTf1rN%2FfR80S%2BxNNII8Um7nl79%2Fqj65%2FW8%2BHf8AWde%2FjBP0IDwenDyEhHi%2BIDbkfZBN%2FwDRwM3yMNEpp3ElM%2FfT80QNFp4%2FuOY%2B%2FH5o%2Buf1vPh5%2FW%2BIP4wT%2FVxH63nw8dsrXz%2Fj6f6uBm%2BRzdLpaQUuU%2BZVtt79ax%2BKIKpFK5iUmU%2F4YfNH1s%2Bt28Pe4tiOx7PH2tv81D63Xw9d2JPw9v8AqoGb5J%2BxNK%2FWs19%2BHzQNHpR3TIzf30H8kfW363dw992I%2FwAPb%2FqoiPB4cPgNwMR7m5%2FN7e%2F%2BagZvkkKVSk7qkpq%2F98HzRN7F0f8AWM399HzR9bPrePD39piL8Pb%2FAKqIHwd3DyQR0WIt%2FwD69H9VAzfJE0ukfrKb%2B%2Bj5ok9jaMD%2BgZz7%2BPmj62K8HRw9H9sg9E%2B3%2FVRA%2BDm4eT%2B2X%2BMG%2FwCqgZvkr7H0b9YTv34fNEvsfSDykZ378n5o%2BtR8HJw%2BdjmJfw9v%2BriX63Fw%2Bfq2Jvw9v%2BqgZvkt7F0nWF%2BKTW3Z043%2BSJjTKMOcjOH0PA%2Fkj6z%2FAFuHh6tbXiS%2Ff483%2FVRL9bf4fv1zib8Na%2FqoGb5NCQpI2TJzI9Lv%2BqHiNL%2FWr%2F37%2FVH1kPg3%2BH4i3jOJvw1r%2BqiT621w%2FwB7%2BOYn%2FDWv6qBm%2BT5k6URbxOYHnDsUzR6O5uqWnN%2B50fNH1kV4NvIE8p7E4%2Fxxn%2BqiQeDYyEHKqYo%2FC2f6qBm%2BSk5S6LISMxUnKW88qTbU%2BEOTJCF6d9KgBex5bGNbSapKcoKnRJOy1Reqb776QfeDLrQkoShJ3SpCwq5JsUqHaI%2B0lc8GRkbV6TN0puvYnY8ab0dKJlkqRvfb3oRgDfgmcEyi3UyeOZ9TalXQXtJUB3bItAzfJXolfqS4rU6TUut0hKmzpNQlzv8A3wc4%2BtX1qnC%2F7eH%2FAL2n6MB4KrDSXG3W8cvBTS0uJu2nmDcfBgZvn85T2ta%2FzIjyj%2BljvMSexyP1sn72I%2BkCvBvtncZglJ7%2FABZH0IgfBv6gArMUne5PijfPzdSCJfNqeokrNtht1hTNjqCm7JN4tftVpnfOn1j5o%2Bnjng2qa4lxLmOVOat06pdHVPqRyimPBqUlPLHLg2v9iHPv8mCHzCcwdSHPKNQ9RTFrq2A5VtlxyVXNEt30Kctta1jH1YHg2aGFH%2BzV3Tfb3lNwPuYg74NTDj7ZaexxOFClajZtFx6DogPnCikAobUZRu62xq6gNjbne0TihM%2FrUR9KR4Omhp8nG0wTa11MNn%2BhE7fg6sPX99xo%2BbG%2B0u3uO7yYD5eY0pMrJ4QrE34k2NEorSdPWCibAiNJNNpQNAvfzgx9qK34M3L%2FABDJtU6oY2rTcsl5LriJfokdIEm4SboO0UT4LPJxZJViWujuCVM2%2FwBHAfGZtHK6gLeaNrUOh0p2hSK3ZZ3plN6i4HdlAnuttH1KR4LLIcbLr%2BJCDzs4x%2FVxdpfwaeSss02w3iXFBQ0gISC7L7AC36lAfK80OjlfUbmwnzrF%2FkiY0WlEJCm5s%2FbWUn5I%2BqZ8G5kv2YhxKP8ACMf1cSK8GxkweWJcTj0Oy%2F8AVQHytcoNHvdpE7a52UU8uyJfYGlfC8eH70pj6rJ8G1kuOeIsTH%2FCsf1cQ%2BtuZPb%2FANkuIt%2FOx%2FVwHyq9gaMQd6hfsOpERGH6JZPXqV%2B37HaPqp9bcye2%2FsnxJsnTbWxb0%2FY%2BcQPg2snVc8TYi9Rl%2FwCrgPlf7X6H%2FwB4fG3EgodHHlInD%2FDRH1PV4NjKP4OKcQevoPoRRV4NXKgHq4sr4H%2BA%2FKiA%2BW4olGJ2anzq8rrI29EQNEpJ3Jn%2FAORH1GV4NXKwnbFNbV%2B%2BDP0IpOeDSy0VYIxdWkJHYnoRcd3kQHy6NFpXwUzh9JTAUSlHm3O%2BpSfmj6h%2FW0st739tlW9FmvoRIfBr4FSB0OLZ9BCbGyGxfznqwHy%2BXQ6epWr83k95UiJhQ6d8Lx0%2Fwkx9OV%2BDWwiq%2FwDZnPG42uhG38mPOrwaGF%2FgY0mvWhH0YD5oLodHPkInuXatHP4opih0oc5eZPpdHzR9LVeDQovwMbuetpP0Yl%2BtoUkcsbX9LKfowHzOnaOzMsiWZSZdv4QSSSr0nti3DCEsf0xP3uPqEPBoUj4WNf8AMp%2BjE%2F1tKjftyH3lP0YD5fjB7A3S8R6AYe1GWPlOOH1R9PvraFG%2FbofvSfoxA%2BDPpGtS%2Fbuq6uZ6FP0YJiZjY%2BYPtRleYW59zEfamz%2BqL%2B5j6fDwaNJFtONjsLbtJO33POIfW0KRb%2Fjuu9v1NP0YJ4VXhfMA4QZJv0iviiYYRZA8r5I%2Bng8GbR73ONlW%2FvQ%2BjER4M%2BkDljhX3lJ%2FowOFPhfML2qNhWzpI%2BKJvao39uqPp39bOo9%2F%2BO67f3pP0Yj9bOon7dnPvafowOFPhfMNWFWPtlje%2B14l9q0te%2FSEH97H0%2B%2BtnUT9urn3tP0Yl%2BtoUtP2PG%2F3TKT%2FAEYIzzfNeSYrVPDaWK8%2BG2hpQ2UJWkJvfTYjlfsizvYCoT80qdLUy04tanFpac6pUeZAVy3j6gq8GjSyOrjex%2FvKfowHg0KT244V6mk%2FRgh815TDmGWG9HilTV%2FjCD%2BSPPMYOwbNLW47LVQqUNOkOo028%2B0fTM%2BDRo1tsbrv%2Fek%2FQiCfBo0axSrG7hB%2F7JP0ID5epyzwe2dTKqwk%2Fv2z8sekYIoSRYPVTb903H07%2BtpUT9urn3tP0YfW0qJ%2B3Vz72n6MB8xfaZRf1ep%2F5uJVYNoF%2Bsupn1tx9PPraNAt%2FwAcnL%2FvB9GIDwaFA%2BFjJfqbH0YD5gzGD6UpAT0CnUdgeSCfkjL8L4wxHhSmpo0szTZ6SauWG56VDqmSTchKr30%2FuTsI%2Bhx8GZh0%2FwDTJ37hP0YkHgycParqxk5p8yBf%2BbAcEDMzExN10jDSvMad%2FtROvM7EdwWKNhtoW3HscTv91Hev1snDX7cXfuR9GH1snDX7cXfuR9GA4KGaGJgd6Rhw%2Bmn%2FAO1EFZmYqWsqNMw1bsHsYL%2FHqvHfH1snDH7cX%2FuU%2FRiZvwZ2Gmzf23uq%2FfJH0YDgf3ScT%2FsTh3%2BLv9qJ%2FdMxRfUKZh3lbanBP5Y78%2Btr4Z%2FbSfuB9GJk%2BDZwwOeKD9wPowHAXum4o%2FYzD%2F4B%2FriZGZ2KUkH2Iw5fttTrX%2BWO%2FfrbWF%2F20K%2B4H0YDwbWF%2FhYoV9z%2FALMBwH7qeK%2F2Hw3%2FABefniRWaOLVK6tKw4kf%2BWg%2F0o7%2B%2BtsYV%2FbSv7kfRiH1tnDN%2FwDjSbfvB9GA4B90jEvM0ugfxf8A64qpzSxUnlTMP%2BunA%2Fljvs%2BDawvtbFCvPdP%2BzA%2BDawt2YnV9z%2FswHAJzQxYXel9i8PX%2FAPLAP6UPdNxJ%2BwGG%2FwCL%2FwDajv3621hj9s5%2B5%2F2Yh9bZwz%2B2hX3P%2BqA4HczRr6zdGGsON7ckySrfzomGa%2BJBzw5hk%2BmQP0o70X4NjDatk4qUkd%2BgX%2FmxH62xhm%2F%2FABpVb94PowHBIzXr6fJwxhkeiUV9KJ%2FdbxF%2B1fDP4Ir6Ud6Hwa%2BFuzE6vuB9GJfrbGGb%2FwDGlVv3o%2BjAcHHN%2FEwFhhzDKf8AElH%2BlFP3X8XJ%2BxULC49Mgr6Ud6q8Gvho%2BTitY%2Fgj6MQ%2Btp4ZPl4scP8ABH0YDgpzNzGCzqFGwuk%2BanH6USLzdxopOg0zDIT3Cl%2F6473Pg08MHb22OAfvR9GJPraGGSeti5wj96PowHBBzYxmr%2B4sPI%2Fe00flMQ91XGX63oP8WJ%2BeO9h4MzDN98YvW8yR9GJD4MnDRH%2FHSYvfuH0YDgheZuNHDcNUIf5MT88U%2FdGxvp0fnJbv9jRf8cd9HwY2F%2F26zXyfRiA8GJhntxvNeq30YDgX3Q8ZW8qkfxcn54kVmDjFXN%2BkD0U9I%2FLHfJ8GBhk%2F9Op3%2BT9GIHwYGHezHc38SfoQHAqcfYxT%2FdVK9UgkfliC8fYxUf0VTPwFMd9fWv8AD37e5v5Pow%2BtfYd%2Fb5O%2FyfoQHAAxzi4EK6emEg33kh88Pb3jLXr6Wj8rW8QFvxx399a%2Bw9f%2FAI%2Bzn8n6ER%2BtfYct%2FwAfZ3%2BT9CA%2Bf4xxjICwnKWO4iQG29%2B%2BHt4xp%2Bv6b%2FFyfnjv7617h79v87%2FJ%2BhD617h79v8AO%2FyfoQHAQxzjIAAzlLIBvvTh9KKSMZ41T5VVpyv8nI%2BePoF9a9w9%2B3%2Bd%2Fk%2FQh9a9w9%2B3%2Bd%2Fk%2FQgPn4rGWNTcCq08A9hpqDb8sRTjLGKb%2Fm2kk%2FBKqU2bfGd4%2BgP1rzD%2FAO36c%2BJP0Ih9a7w%2F%2B36c%2BJP0IDgB%2FHeO2pd12XrVPlVpGrVL0iWBNv3yFRpPE1fxhi6fTP4srNRqrzadLSpm6g0n7VCQAlI8wAj6zzHguKG6ytpGP5ka02uQPoRYqJ4KdctPg1bMNhUnfcS6CHLfwkWgOFeF3hhxfxIY79ptFMtIsoknZ2cnJsL6OXaRZIJCRe6lqSkeknkDHc3Dj4MrGeWeadLxvjTGFHFOodSl6lLy9PLjjr62Va20kqSkJTrSkk8yNrdo7HyN4ect%2BH2iTVJwHT3unqCkLn6hNrDkzNKQLJClAABIubJAAFz2m8bNgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgP%2FZ%22%20vertex%3D%221%22%20parent%3D%225%22%3E%3CmxGeometry%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%227%22%3E%3CmxCell%20style%3D%22vsdxID%3D5%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%2C%5B0%2C0.24%2C0%5D%2C%5B0.86%2C1%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22118.91%22%20y%3D%22179%22%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%228%22%20style%3D%22vsdxID%3D6%3BfillColor%3Dnone%3BgradientColor%3Dnone%3Bimage%3Baspect%3Dfixed%3BstrokeWidth%3D102%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D0%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%3Bimage%3Ddata%3Aimage%2Fjpg%2C%2F9j%2F4AAQSkZJRgABAQAAAQABAAD%2F4gHYSUNDX1BST0ZJTEUAAQEAAAHIAAAAAAQwAABtbnRyUkdCIFhZWiAH4AABAAEAAAAAAABhY3NwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAA9tYAAQAAAADTLQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAlkZXNjAAAA8AAAACRyWFlaAAABFAAAABRnWFlaAAABKAAAABRiWFlaAAABPAAAABR3dHB0AAABUAAAABRyVFJDAAABZAAAAChnVFJDAAABZAAAAChiVFJDAAABZAAAAChjcHJ0AAABjAAAADxtbHVjAAAAAAAAAAEAAAAMZW5VUwAAAAgAAAAcAHMAUgBHAEJYWVogAAAAAAAAb6IAADj1AAADkFhZWiAAAAAAAABimQAAt4UAABjaWFlaIAAAAAAAACSgAAAPhAAAts9YWVogAAAAAAAA9tYAAQAAAADTLXBhcmEAAAAAAAQAAAACZmYAAPKnAAANWQAAE9AAAApbAAAAAAAAAABtbHVjAAAAAAAAAAEAAAAMZW5VUwAAACAAAAAcAEcAbwBvAGcAbABlACAASQBuAGMALgAgADIAMAAxADb%2F2wBDAAMCAgICAgMCAgIDAwMDBAYEBAQEBAgGBgUGCQgKCgkICQkKDA8MCgsOCwkJDRENDg8QEBEQCgwSExIQEw8QEBD%2F2wBDAQMDAwQDBAgEBAgQCwkLEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBD%2FwAARCAGPCigDASIAAhEBAxEB%2F8QAHgABAAAHAQEBAAAAAAAAAAAAAAECAwUGBwgECQr%2FxABzEAABAgQEAgQGCQkQDAwFAQkBAgMABAURBgcSIQgxEyJBUQkUMmFxgRUWFyNCkaHR0hgZM1KSk5SxwSQlNENTVFVWYnKClaKywtMmNURzg4SFo7Ph4vAnNjdFRldjZXR1pMM4R2S08ShmdqW1SFh3hpb%2FxAAbAQEAAgMBAQAAAAAAAAAAAAAAAQIDBAUGB%2F%2FEAFIRAQABAQQEBwoICwgCAgMBAAABAgMEBREGITHREhZBkZKh0hQVUVJTYXGiscEHEzNCQ1SB4SIjJTI0NURicrLwJEVVY3OCwuIXJpPxNrPD0%2F%2FaAAwDAQACEQMRAD8A%2BqcIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgOB%2BN%2Fj%2Fq%2BVuLH8pcn3mWqzS1INWq7iUuIYdKQrxdCFJIWQkjUew9XmDblH65RxOaNQzMp5I8oex8uCPjRGj%2BIqemp%2FOHMCdmnluTDmKaoouLVuT424N40%2BtyA7Sb8JLxOOLA91GmpB33p8tYW5gnTHic8JzxPl9Yax9KabqSm9NlwPTfTHGqzcX7gYpm6uZB9JgO1HfCV8VLTiks48l30fBWaUwm49GjviT65bxXX%2FAOPEv6qUwf6EcqymYOIpCTbk0iVdaYSlCekl0qISBYDzxU91HEf62kPwVMB1R9cy4pxzxox%2FFbH0IHwmHFOtSy3jdm3cKSwbfyI5WOaGIleVKyB9MqmJDmbiXfSiRR3WlE7QHVP1yzis7cct7%2F8AdDH0IfXLuKs8scI%2FiiX%2BhHKwzQxZyDkr5rSyBAZoYt59PKj%2FABdJ%2FJAdVfXLeK0c8bN%2FxQx9CIjwlnFWrljVP8Uy%2FwBCOVjmhi4i3jEv%2BDp%2BaKZzPxeD%2BiGvVLo%2BaA6wHhKeK48sYj1Uhj6ERX4SXiwI6uMFD%2FIzB%2FoRyYczsXE6vG0JNrdWWQPyQOaOMTznQf8AApH5IDq8%2BEn4sxzxgr%2BJmPoRD65VxY9uMF%2FxMx9COU%2FdPxj%2Buh96T80PdRxmP7rT95T80B1inwlnFbpsnFJWf%2FJmfoREeEu4qeRxPv3exDH0I5MOZ%2BMFH9GBJ70tAfkiVWZmMrdaoesMo%2BaA63%2BuWcVx5YiV%2FE7H0ImHhJ%2BLA%2F8ASM%2FxOx9CORRmXjL9lFj%2FAAafmiPukYxP%2FO7gP7xPzQHXY8JPxX%2FtiP8AFDP0InR4Sjiqca6lfuq99QpTPLutojkIZkY1T5NZcHobT80S%2B6Rja9zWHye%2FYfiEB179cl4sf2wf%2FwAJY%2BhEfrknFn2VvV6KUyf6Ecg%2B6Rjf9mH%2FAIk%2FNEpzExornVn%2FAFWH5IDr5fhJeLQ%2BTXFJ%2FwAksfQiX65Nxab%2FAJ%2FHbn%2BdLG38iORRmNjRP%2FOrx%2FfAH8YiT3QcZ9lYd%2BIfNAdfJ8JNxanf2d1D%2FwApY%2BhFRPhLOK5xWhFXUD56Qz9COPTj7Gat1VqZ27rD8kFZg40WnSa3NgeYiA7EHhKeLBStAq6SfPTGR%2FQh9cl4tP2UH8Vs%2FQjjg4%2FxkP8An6c%2BMfNEDj3GR516cPrHzQHZP1yXix%2FZf%2F8AhLP0Ij9ck4sf2W%2F%2FAISz9CON%2Fb9jC1vZ2b%2BT5oj7fsaXCvbBOXHI3G3yQHYx8JLxZfst%2FwDwln6ESK8JLxbDnVrD%2FwApZ%2BhHHwzDxqkaTXptQ7jY%2FkiCMw8ZoBSmuTgB7Li34oDsEeEl4tQbGrgemlMj%2BhE6vCS8WY5VX46Uz9COPfdCxpa3s2%2FbusPmib3RcajnXHztbcA%2FkgOvvrlPFmOdUH8Vs%2FQiqnwkvFqvyZ9J%2FwAmM%2FQjjwZj40ShKDW3ilNrDbs5RJ7o2M%2F2bm%2FjHzQHZP1yLi3%2FAF4j%2BLWfoRBfhJOLZs6VzgSe40xn6Ecb%2B6NjT9m5z4x80TjMLGwSpCK3MpSrmBAdiDwk3Fr%2BvRb%2FAMtZ%2BhD65NxZnlPpP%2BTGvoRxx7fcZjf2dm7%2Br5oj7oONORrs4PQoCA7H%2BuS8Wf6%2BT%2FFjX0IivwkPFs35dQSP8mMn8SI42OP8Y%2Fs5O%2FdxIcwMZ3v7OTP3Q%2BaA7MPhIOLhPlT6R%2Fktn6EPrkfFrfT44fT7FtWPo6kca%2B6Jjb9m5r1EfND3RMbfs3O%2FdD5oDsz65Fxaj%2B6VH%2FJbQ%2FoRFHhIuLa9lPk35fnYz9CONhmJjIA667OEntKr3ikMw8ZXP57zVj2A2vAdp%2FXHuLPQR0x132%2FOtnTb06YkX4SHi0Pkvgf5Ma%2BhHGAzExkOVWmh6FxN7o2M%2BytTg%2FhfPAdmHwj%2FABbpAPToN%2B6ns%2FQiUeEk4tD%2FAHQkemmtD%2BhHGgzFxolWpFdmknzEX%2FFEpzAxiedZmvurfkgOzPrkfFr%2BuUfxc19CIjwkfFqo6UzKSe72OZ%2BjHGSswMZrveuTYubmy%2BZ%2BKI%2B6DjPf8%2Fpvfny3gOzvrkHF2DpLo896az9CA8JDxc9ryBbvp7IP8yOMDmFjEC3szMkdoJiU5hY0P%2FO8zty3F4DtH65LxZfq4%2Fixr6ED4SLi3HkuBf72mtfQji%2F3SMa%2Fs1M%2FJFX3Tsb%2FALOzA9AtAdmnwlXFihSdTaRqPbTm%2FoRMfCW8VX2qP4vR9COLU5l43bXrark0g94tEDmXjg%2BTXp0elQ%2BaA7T%2BuXcVPc3%2FABej6EQPhKuKwdYqSAe6nN%2FQjiwZk452vXZo25XsfyQOZGNCQTWZrbl1rWgO0E%2BEz4pFmyXGie7xBv6EVPrlXFX9qn8Ab%2BhHGHulYyI0GvTiU%2BYxT90nG3L2dm%2FjEB2n9cq4q%2FtU%2FgDf0InX4SbiuRbZBvy0yDZ%2FoRxUMx8ZjlXpwbW8r%2FVEfdIxmdIFdmxp2Fja21u6A7RR4SriuUvTYfxe39CKi%2FCR8WKPKSn%2BL2%2FoRxR7oGMLW9npq172v2xD3QMX%2Fs3NfdQHazfhJuK937GhBH%2FgG%2FoRX%2BuT8VZ%2FudscrfmFve%2F8COIRmBjAbJr06PMF7fiidOYGM0iwrs3b98PmgO2z4SbisHOXa%2FAW%2FoRIrwlfFSlWky7Y9Mi3b%2BZHE5zAxiTc1uav%2B%2Bh7f8Y%2Fs1NfdwHbI8JVxV%2FrZo%2F4k39CI%2FXKeKo8pVv8Cb%2BhHEozAxlf%2B3s593E%2FugYx%2FZ2d%2B7gO1%2FrlHFYOUoj8Cb%2BhD65RxWDlKo%2FAW%2FoRxKcf4zvtXJ375D2%2FYx7K3O%2FfIDtr65PxXnlKI%2FAW%2FoREeEi4sTv4qg%2FvZFq%2F8yOJfb7jD9nZ37uI%2B33GH7Ozv3cB2yfCScWIO8in1yDf0Im%2BuT8Vg%2FuBs%2F4m39COIzj7GnL2dnrf3yJDjzF%2FZXZ37u0B2%2F8AXKuKz9jm%2FwADR9CH1yrir%2FY9v8ER9COJPb7jM%2F8APs790PmgMeYyHk1udH8OA7b%2BuU8Vn7Htj%2FE0fQh9co4q%2FwBaMj%2FE2%2FoRxL7fca%2Fs3N%2Fd%2FwCqIpx5jRPKuTv3yA7aPhKeKlJ0mSQVdwkkH%2BhER4SfirHlU9PrkkD%2BhHEvt%2Fxp%2Bzk592Ie37Gn7OTv3YgO2frlPFV%2BsGvwVv6ED4SripH9wI9Um2f6EcSe3rGNtPs3O27ukiKcd4xT5Ndnh6FwHbH1yzin%2FWSPwFH0Iqjwk%2FFUjy6e0dtW8o2NvuI4l90LHA2GIJ775Epx%2FjVQsquTh3vusfNAdvJ8JfxSLQCmlS%2B5sD4qnc%2FcQPhK%2BKgC5pbHqlEH%2BhHDxxzi9S9aqxOFXO5cionH%2BM0eTWZsefXv8cB279cs4pP2OZH%2BJo%2BhBPhL%2BKFStHsfL388okf0I4iVmBjZaQhVendI7NYh7fMY6NHs9OW7tUB26rwlvFMjyqOj8DR9CIDwmHFErb2Jbv55NH0I4jOPsZjya9PJ9C4icwsbkkmvTpJHMqHx8ucB26PCWcUJ509kemSR9CIJ8JZxSLbLqaU0UJNifE0D5NF44iOYGNVJ0muz33yIDH%2BNQor9nZwqKdNyu5t3XgO3vrlnFJa%2FsZL%2FAIKi%2FwDMiX65fxRlZQilMrI56ZRBt%2FIjij3SMd3v7Pzl%2B%2FUPmiRzMPHTgIXiGeIPZrAgO4FeEy4n0eVQG%2FwRP0Il%2BuccTZOn2AZv%2FwCGT9COH%2Fb9jX9nJz7uJjmFjUo0GuTmnu1wHcJ8JfxPgXNDYHm8WRf%2BZEUeEt4oHPJoTX4In6EcOjMLGoN01ubB7wuAzCxuLWr89t%2F2kB3GfCW8UKfKoLY9Mon6EQPhLuKBI1GhMAXAuZZO1%2B%2FqRw8cxMdKJJxBO78%2FfIl90LHH7PTv3cB3MrwlnFAhQQrD7Goi4Hi6bkfcRI54TDicaQlxdDZ0r8kiVSR%2FMjh8Zh41S30Qrs6E9wXtEfdHxz17V2c65urrjc98B26PCY8Tp5URn1yifoREeEx4nR5VEZP%2BKp%2BhHD%2FuiY3%2FAGdnPu4e6Jjf9nZz7uA7lb8JdxMr%2FwCYZY%2BllI%2FoQR4THiVUSn2Alkkdhl0%2FQjhkZg40tY1ucI7iu8VDmNjUp0GuTtvMofNAdwJ8JnxKrcLaMPsqI7pQfQib65hxLX0%2B15i%2Fd4un6EcPrzHxstOldemyO7Vb8UURmHjhKdCK%2FOpTysF9kB3M54S7iYb8rDzPqlkn%2BhEv1zTiT7MPsH0SyT%2FQjhpvMHG7Ru3XZtJ8yomOYuOVX116cVfndcB3H9c04krXNAa9Hiib%2FwAyH1zTiSt%2FaJgdvWlk8vuI4fOZWOlqCnK5NEgWBuBb5InOZONzb8%2F5oW9HzQHbg8JrxJqGpNCliO8S6foRA%2BE04k%2F2Elh%2FiyfoRxIrMnHayNWIZqw7AAB8giYZkY5AH5%2FzRty6wgO2nPCacSTK9DtElkHzyyR%2FQj0fXNuI61%2Fa%2FK%2Bjok%2FQjhr3R8a9a9ZnDqNzdQNzE3umY5vq9mpm%2FfZPzQHcB8JzxH67DDjB9DA%2BhEfrm%2FEhY%2F2Ns%2Fg4%2BhHD5zLxyRqNdmr%2BqJfdMxxy9nJr4%2F8AVAdwjwm3EgBq9rrB83QD6EPrnfEf%2B1hr7wPoRw97pWOQf7dzfyfNEwzOx1%2BzMz8SfmgO3VeE94jkbqw0yB%2F4cfQiY%2BE74kEmysMtj0y4%2BhHEAzNx2OVbmx6xAZnY7H%2FPc38kB3APCd8RyhdOHGDbn7yPoROPCccR%2FI4bl7nl7yPoRw63mjjpC9Rrcz6CAfyQVmdjlaiVVmZ37gNvkgO3V%2BE84jE7HD7AIO9pcH%2BhFVrwnXESr%2Fo3Kq9LaR%2FRjh5OZuOU8q5NfEn5oJzNxsj%2FAJ4eV%2B%2BSk%2FkgO5keE44il6tOFZbq8%2Fev9iKTvhQ%2BIRlQSvC0tv8A9l%2FsRw8rM3G6yFKrMxcctIAg3mZjZtvok1qZ09xtAdyq8J1xFFGtGE5e3eGwf6Eeb66LxC%2FtXl%2FvP%2BxHEiMz8bo5VZw%2BlCTFNWZ%2BNyb%2BzL9%2F3o%2BaA7hHhQuIcjUMLS1vO1v%2FADIj9dC4hv2qy%2F3n%2FYjh45o476mirPJ0crITv6e%2BInNPHJ3cqzx%2FgJ%2BaA7iPhQeIQc8LsC%2F%2FAGH%2BxEp8KHxCjnhiWAH%2FAGP%2BxHEAzWxt%2ByCt%2BXUERGamNefskrbndsQHbg8KPxAKTqTh2UI8zP8AsRL9dKz%2FAL29rkp96%2F2I4nOa%2BM1c55P3kRJ7qeM73NQB8xZSfyQHcKfCnZ7q3GGZE%2BhP%2BxBzwp2e7SlJcwvKAp5jQNv5EcPLzRxgsAeOoABvswn5onRmxjRsdWdbPpYT80B22fCp55%2FBw3JetH%2BxER4VPPM%2F9GpL1I%2BdEcRnNvG6lX8aaHoYT80FZr40WbmfSB9qGEAfigO3VeFPz0QnUrDUl9yPoRA%2BFSzzSDqw3Jju6nL%2BRHEfup4wtbxpoj%2B8o%2BaIDNfGCb2da35%2B8J3gO2%2FrrGd2rSMNyaje1gkHf7iJk%2BFVzxN74WlBbndHL%2BRHEhzcxkRpLrJHnl0bfJEhzYxjf7K395TAdv8A11TO7sw3JH0Jv%2FQgPCpZ5KBthiUNuZCOX8iOIkZs4wQm3jDB57mWSfjiZGbuL0fp8ufTLJgO3G%2FCpZ5G39jEqq3OzY3%2FAJETHwqWeWr%2FAIrSgHdo%2FwBiOH3M28XOcnZdG%2BrqS6RvD3WsX%2FqrP3kQHb6vCrZ4JAUrCcoBa5JHMfcRBXhU88k2WrC0kEnldP8AsRxB7reLraStkjzsgxA5rYrVzMqfTLiA7gX4VXO9Hl4Yk0%2BlH%2BxEq%2FCs52o54YlOV%2FsZ%2BhHEXus4stpLksRa1jLpO0Dmxi1QIDkuAewS6doDttPhWs7V%2BThqRP8AB%2F2IirwrGdyTpVhqQBtyI%2F2I4lbzcxg35K5T1yiPmiVzNjFyzq1yl%2B8yiT%2BMQHbjnhWM707pw5IlIJBIQfj8iKY8K7ndr0%2B1uRUO%2FQR%2FQjiT3V8Zfrtj8HTEgzTxYnk4xzv9gTAdwjwredqhqThuSIUbAhPb9zE%2F12DOkHScJyRO3f8AQjh0ZvYuSpSguVGrnaWTEHM3cXOk3fZAI8kS6bfigO4x4WHOjyfanI3uO%2B%2F8yIjwr%2BdVwDg%2BUBJsAQQSfuI4bbzbxa2RZyWNr3vKIN9rd0TO5vYrdSlGqWQlIAsmWT2ct%2BcB3EPCvZ1KcUhOE5HUjykgKuP5EB4WDOdZs1hORXvY2uLfGiOGfdYxTb7LL9U7HxdOr44e6xilTZQVyllHf8yoveA7nPhXM7Bf%2BwuVFueoH6ESK8LBnS39lwjIN7fDuN%2FuI4cTmxihABSiTuDe4lkg%2FJEHM3MVuDT%2BZEi1tpZP5YDuP67BnSSVDCcgU9hF%2FoRVR4VjO94ktYSkLW35%2FQjhZObmLbaBMMbCw%2FM4ioc2sUHykSazzBVKpuDAdyHwrWdYKknCkldPlWSo2%2FkQT4WLORKOkVhOQKEmxNyB%2FMjhlGbeK0q1KMqra1%2BhTe1rfigrNvFawUqdllAixCpZJBHxQHdCfCzZvlWkYOkSe7Ur6ETJ8LFnEq2nBkodXLyvoRwoc1sUqIUpUmSFhwEy6eY9XLzRMc28XggpnWE2FrCXRAd2q8K9nE3zwfTz%2FDI%2FoQT4VrOexBwZJE%2BlW38iOFBnBiwgIWqVUkAgDxdHKI%2B7Bim50OSiARY6ZZIv5%2FT54DupHhW86F%2BRgiTV%2B9KvoRD663nJc3wbJfGr6EcLrzexSsqUp6WuvnZlI%2FFETnDiw83pU733YTAdynwrmcV7jCMkfMLn%2BhA%2BFbzoBCfaVK3O42VuPuI4aOceK1eUqR%2FBEmJTnDixWypmXIta3i6bc7wHci%2FCx5whVvahTr9wWT%2FQiZHhX85Fm6cGyRHdc%2FQjhv3XsT6QA3IbcvzEmIrzgxUsWS3JI8yZRIH4oDuZzwsOcLZKfaRT1Ec9LhNv5ED4WPN34OCpE3Fxcq2H3uOGPdbxdcqvK7ix%2FM43ERGbWKU3sJQEixtLJ3gO50%2BFizgPLBEgbqsLKV9CIq8LBnEnngaRH8M%2FQjhj3W8V7XbkzZOkXlwbCHutYq6Po9Mrb%2Fw4gO6keFezgX%2F0IkwbbAFR%2FoRIvwseb7IBcwPIC%2F2zhTf%2BRHC%2FuqYoOx8WBt%2BtxcxH3VsUKASWpVR7NUsFQHcw8LLm924JkD%2FhD9CJleFkzbQ2CrB9NCr%2FAKoq%2FwAWiOGk5uYvR5KJQf4smJPdWxT%2BpyfK36HHzQHcn12bNzY%2B1Cnfdq%2BhAeFnzeKSE4JkCewhav6uOHhm3ilOoiXk7nkfFkm3yRD3YcV7am5M25fmYAfEIDuZvws%2BbSfsmCaaSrld5Q%2F9uJl%2BFozUbIDuCqag2JsXVfQjhQ5u4oUgIMvJkA9suN4nVnBitd7y1O3NyTKpJ%2BWA7mT4WnNdZ6uB6bbu6VX0IiPC1Zq7n2h09XodUf8A244W91jFBIUqXkCAnTbxRNrQ91zFt09WS6vZ4omxgO6R4WbNxQuMAyQHeVL%2FAKuA8LPmuqyW8FU1a%2B1AcVcen3uOGk5u4rupRZk7r5lMuBEnus4sN9Tcmvzqlhf4xaA7pPhac1GiUu4JpgNuReUP%2Fbh9dozWVpCcDU7ft6RRBvy%2FS44XGbmLBfU3JquLEmVTc%2BuIHNrFaiLsyhAN7FgW%2BK0B3WrwsmayEJK8E04XvzcUP%2FbiT67VmkfJwVTVeh4%2FQjhj3W8XHUF%2BKqCuxUsk2iX3V8Sp3TJU4f4omA7vb8LJmslxKl5fySkg3KelULj09HEx8LJmooJtgGnpve3vqjf%2BRHCC83cTLWVrlpE3BSR4sLEHmIkTm1itPZKeqWSIDvJXhZM1UAKXgKmpB5FTyhf%2BREp8LRmgEgjA1MNz2TB%2BhHCQzdxTbrolif3TCVAeoiDebeJUC3i0gfOJRIMB3WvwteZ6ClK8DUxJUdKQX1bn73ER4WbNVZ0owFTie4Or%2Fq44WGbmJbk9BJ7i1vFk%2FND3XMUhICW2E2N7pZTv6doDulfhZ81UHT7Qqbfu6ZQ%2FoRD67Xmh1T7R6Rc3unxlVx%2Fm44VObeJe2Xkzvf8AQ4iPuu1%2F9jqcfOZVJPxwHdf12nNI20YBpir8rTCt%2FwDNwPhas0G9ncC0xBHYp9Vz6Pe44PezYxM5ptKyKLG5tLDn%2BSIqzaxGu2uWk1W5XlUmA7v%2Bu2ZmJFzgqlehUwpP%2FtwT4W7MtzdGBKXbttMLP4m44QOb%2BI3equUkVJ5aTKJ%2BaJhm%2FiW2hEpIITy2lUD8kB3d9duzLJOnAdMOnn7%2Bvb%2FNxD67dmYo%2B94GpSrcwJhf9XHCfuw4sa6rTUhb91LJPqikrNvFKxdTMkjzplUi3yQHeSvC3Zljf2hUy3aS%2BsW%2FzcR%2Bu2ZmgajgKlW7CJlRv%2FIjgv3V8UjqXZIVz1SiDb5IpnNPEgsCmWcCfJSphOn4rQHe%2FwBdqzPJGnAVMt23fWP%2FAG4ivwteZoNxgClgdwmVn%2F244JRmzidNxaUIJuQZZNvRyib3WcR3KixTzfs8TQLQHeX12zM%2Fn7QaZ9%2FX%2FVxE%2BFrzOSpOrANLFud5hdj%2FAJuOChm5iVLQYEvJ6AbgeLJO%2FwAUSe6ziG2lTcoodxlkQHfH12vM8csB0hW2rabVy%2B4idPhbsylISU4DpB1b9WbUT8XRxwErNjEa7FaJI25DxRHKCs2MRBsAtSaQk7FMqgE%2BYQH0A%2Bu3ZkJOn3PKYtR%2B0mlEj1dHED4W%2FMdIurAFKSbFRBm1XH%2BbjgAZu4iBv0MlfvEsgH4wIkXmxiRw6ldFe9yRLo39PVgPoH9duzKDYWrLim2JsCJlZufvcB4W3Mi9l5d09JO4u%2Bu%2F%2BjjgAZu4nA2W2Dtyl02FuW1onGb%2BKDbX0CrG%2FwCh0i8B38rwtWZCEBRy8pgJ7FzS0lPxtxKnwt%2BYxRrOXtLTva3jaz%2F7ccBqzZxCslS5eTVc3sZZJsfiiJzexQSCVSxI23lk7ju5coDvz67ZmSrdGX1LP%2BNr%2Fq4gjwt%2BZClpT7nlN6%2Fk%2Fmpf9XHAfusYjHkpkx6ZZBgvNzE%2BsKQ5LthIHVRKIty9EB38fC2ZjncZe0ob2%2FRav6uIo8LTmSVG%2BXtJ6o3BnFD1%2FY4%2BfKM1cSISGwWCkcgZZFvxRUXmriJxNleKctP6EbuB8UB9BVeFszFbXpOXVKULXBE2sX832OH12vMRRJGXVKSB2GbWf%2Fbj58HNbExQWi60Um23i6ezl2RFOauJ0G4dTzvbxZFvxQH0FPhbcxNQHueUkJ7SZpz%2BriZXha8wwEqGXdKso23m17bdvvcfP4Zu4nvqIlCf%2FCoB%2FFETm9ipSejU3K6L3%2FQqCfxQHf58LZmJzGXVJA%2F8Yv8Aq4k%2Bu35i%2FwDV1SPwxf8AVxwIjN3EaBp8WkyLad5RPL4omGcOKEfY5SnAeeUHzQHfo8LVmJo1nL%2BjbGxAnVkjz7N8oHwtWYadOrLylDVyvNOf1cfP9OcOLEeQ3JJ3v1ZVI%2FJEpzdxUrym5M%2F4smA%2BgZ8LPmINV8vaR1Rc%2Fmxf5W4lT4WrMVSSU5dUo27BNr3%2FAM3Hz8TmxiZKisNygvzAlk2MTqzdxQtJQGpNNze6ZZIt6rWgPoK34WrMNsBT%2BWlMCTtdU4tPxe97wHhb8fKTq9zOlWNtzPLHP%2FBx8%2FRm1ivQlOiUskWHvCfmgc18RptqkpHY6heVQd%2FigPoB9dxx4Tp9zSl37vHV%2FwBXFVPhaMfqF05a0tRAJI8ccFrf4OPn2rNrE6h%2Bh6cNrbSifj5RA5uYtPlCVUf%2FAA6YD6Br8LZmChxKPcypQChe5nnBbzW6OInwtuOxyy3pJN9O08v%2Brj5%2BHN3FahpKJaw5e8J2ij7qWJbqVpl7qNz%2BZkb%2FACQH0KPhbMeC%2FwDwb0nmB%2BjV%2FwBXA%2BFtx2k75cUgecz6xv3fY4%2BfIzbxOLa5eTWB2Kl02MQVmzWySr2Mp4JtezJ3tAfQZPhbMfHY5b0dPbvPL%2Fq4gvwtmP0%2F%2FLejnt2n1%2F1cfPlWbldOy6fIK7N2YgM1a0vcUqRH%2BC%2F1QH0J%2Bu1ZgqsBlxRQSdOk1Fd7%2Fe4m%2Bu3450kjLSjXBIsak5%2FVR89VZoVpeyqZJn%2FBxT90erISfzulBq%2F7OA%2Bh6vC345R0g9zKjK6IAqUKmvSb8rHot4iPC3Y5IAGWdFud96k4Leb7FHzqOY1WPlSMsfS3EnujVT9ZSv3uA%2Bix8LhjhSUrbyyo5CrkD2SXf4uiidPhb8a6QVZaUjc2Nqi5tt%2Feo%2BcSswKko3LDF73HvXKIe6BVP1ux9wYD6Pq8LZjUeTlxRlWNjapLNu4%2FY4lT4XDGilaV5bUdH76ort%2Fo4%2BbjmN59xCkKl2BqASTo3IEeVeKp9flb%2FwAGA%2Blx8LbjNKSs5c0TYXsKku%2Fo%2BxxH67ZjLpA37ndE3F7%2Byarcr8%2Bjj5lLxDOK7O2%2FKKBqz7h66doD6c%2FXb8ZWBOXNEBsSQamser7HE6fC5YvSetlvQ1C1%2FwC2a%2F6uPmH7IudmoeiIGfePa5AfT8eF1xUVIHubUGyxfeqOben3vaJvruOLLqHubUDq%2FwDerm%2Fo97j5dmoTI5FXriHslM9xgPqMPC4YsWoJRlrQCT%2F3qv8Aq4mR4W%2FFS16Pc5w%2Fe5FvZVz%2Brj5b%2Byc1tz9QiKZ2YUTbpCQLm3dAfUf67di61%2Fc2w%2Fe9iPZZdx%2Fm4m%2Bu14tJt7nOH79p9ll2H%2Bbj5aLqbmkJ61xvEzdQfUQTq1c4D6kK8LXi9LXTe5th%2B17WFWXf0%2FY4L8LXisAKRl3h1QJt%2FbZdx%2Fm4%2BXPsi53qicVB3sKjAfUVvwtOLF6bZeYcTfmTVl7d36XEU%2BFqxcVb5cUAC9t6qv4%2FscfLk1B%2F4aFiICfX2BcB9S%2FrteKtake5ph3qgG%2Fsyuxv%2FgomHha8Thzo15a4f9Iq6yPj6OPlp4%2B73Kh4%2B%2F2BUB9SVeFrxQG9fuZ0AkmwT7Lr28597iP12rE%2FX%2F4NsO9QX%2Ftw51vR71vHy0M4%2BTfr%2BqHj7o7FfFAfUseFpxQpGv3NsOeSFWNYWDv2fY%2BcQ%2Bu2Yl0avc1w%2FfVpt7LuX9P2PlHy18fe7lfFD2QdHYr4oD6lq8LViXWoJy2w9pRa5NXX1vR73vD67Via6f8Ag3w7ZQJH57ubW7D71tHy29knuV1fHD2RmO9UB9SV%2BFqxOhOr3N8OEbcqw52%2F4KJh4WnEg6TVlvh89GARarr69%2B73vsj5ZGpvdpPxQ9lHe8%2FFAfU367PiW6U%2B51h26u32XcsD3H3rnEw8LViE2%2F4NsO7kjesuDcf4KPlkmpv9iFGJlVN3TulQ9UB9S%2FrtWIffD7muHuoLj8%2BHLq8w96iP12nEBcS37nGHEhSAvUqsuAAn4J965x8sPZRz7VXxROKmr9TPxwH1LR4WqvrAPub4eF%2BYNXc2%2FwA1ER4WnEBv%2FwAG%2BGxpJSsGtuBQI83Rbx8sjVZj4F4lNVf%2BGi8B9UHPCzYjStaUZbYcXpFwfZlwBXo96h9dlxLpSRlrho3Ok2rbhsfvUfK72Vc%2FU%2Fkh7KufqfyQH1UPhX8VWujLHDa%2BrqFq4vfzfYucSp8LBi1V%2FwDgvw1sbbV1Zt5z71Hyt9k3juG%2Fkib2Ve%2B0PxQH1SPhXsXFtbjeVuHFhCiLezi7m3m6K%2Frib669i0hxQypw4ehSFL%2FsgUNj6Wt4%2BVyaq92oPxxBVUcPePXAfVJrwsOJ3SB7l2GUg9pxCvb%2FADMQHhYMWqQpacpcPHTe4FfXfbzdDHyrNSeJupsKHn3iYVJQ5NesDlAfVL67Bi0uJaTlLh1SlJ1C2IV2%2BPoYnHhWcaFBd9yLDYbC%2BjKvbIeffboeXnj5V%2Byh%2B1v6RERVDfZv4hAfVH669jHe2UWHDY2H9kShf42YijwrmM1nScocOJN7b4lP9VHyxFSctyMU1VJy%2FIwH1UPhWsZJWpJyhw71ef8AZGf6qA8KzjYgH3HaBYi%2F%2FGMjb71HysFSX2oB%2FHE6ai4dw1aA%2BqI8K1jS2r3HKFuQB%2FZEd%2F8ANRBXhWscBKj7jFDHRi674j5D71Hyx9knftDEwrDqO0iA%2Bp%2F11jG2rT7jNC%2F%2FAOjP9VEE%2BFaxobXyVoxv3YiI%2FG1HyzFcmPgqUPSAYrpxC8n4CfuID6gT3hacRU6VMzN5N0xOl7oVJTXiojq3v9i5eePE14XyvutqLeTVMUq402rauXn95j5lT1Wfn220KSkJbJIsgDePCSu%2Bo2H74QH1MT4W3E5Rr9xam27zXCP%2FAGo2VkZ4TjC2Y2OaZgTMDBJwu9WZhEpJ1BmeTMy3TrIDaHNkqQFEhIVYi5F7DePjahSFeVpPoEZBhGZdla5IvSqy043MNqQpHMKCgQR64D9KUIQgEIQgEIQgEIQgEIQgPzu5%2Bf8AKrjf%2FwDeSpq5%2FwD1bsandjaufm2aeOB9riOp%2FwD3bsaqcgPXQ6Y5VZhEuhxtsFY1uubJbRzKr%2Baw27bxkntfkEbBT7g1eWQE3HmHZfnHnw115DpPtfe%2Fii6wHiRQaPyWJjn2LHzQ9rlE%2FS2ppSvOtPzR7eUQ1%2BfTAeH2uU%2F7Rz40xA4ZpZXbQ9b98n8ce%2FX%2B6vEOkMB4fa1TUpult0G%2FMrSYmOH5EHT74R3C0e4dbY374lPO4BHogLecNyF%2F06%2FnKbRFOH5BJsFL%2BNMe1RPK8EuFOxV6oDxOYekV8tZ9Fop%2B12QR5Rc9ZEXLWPPDWO8%2FHAeEUGUt8Mj0iBw1LPHZDqSf3YsI9oNtwSPODeI9JfZKtQ7Cb7QHgOGpZHV64I7dSYm9rkoeaXFehSY9wK%2BwD1fjiKSRcqUogeYnfu23vvAWxeGpY%2BT0qfWkwGGpUc1OH1iN24s4Ys4sD5dPZn4soMpSaSwwy%2B9LTE6gVBtDywhrVLi6klRUDYm4G5tGpO2At5w1LadmXLd%2BoRAYZlVHcuJ7t0xckk32JB7jygpVjyue%2FugPAMLS%2FwBu58aYmOGJZvVrLl%2Fg7iPaHF90XSh0asYkq0nh7D9MmKlVKi6liTk5dGp19w8gB3cySdgBcwGOKwywdwtwesRD2uS%2F26%2FjTG0s48ncU5JYjp%2BFcVVSkzs9UKY1UymnP9KJcLJHROciFApO%2FIixFxGBkKQhala1BHWIHPaAtQw3L%2Fqiie0ak8omXhuWCdnFJ9Yjb2POH%2FHGAMC4azMmXJGq4bxLIsTfj9NdLrcit1N0NPm3VPZqF06ri9xHjyfypnM3cSTeGpbElGorspJGcDtSe0B%2F3xKA00Oa3LqvYdgMBqhWGpU8nV%2FEIqt4WliLl1fyRuDEOQeOqLnH7h9PZlq1iF4sLllSSz0TjLrQc6VSlAaEpTfVq5WjJcyeE7MPLXCE7jdVXoOIKfSV6Ku3R5rp3qeOWtabC6QTuRuOZFoDn32rSdvLc%2B6EUzheT%2FXDo9QjbNQyVxRT8mKVnqtTT1Aqc%2BqSWyyFLflE9IW0PuAC3RrWNIsb3t3xHNbJDGuTkhhmaxmZNp%2FFEk5ONyrDup2TUgp1MvDkFgLSdrjcjmIDUvtXk%2F1y78QiY4Wkh%2FdLo9QjamBcqVY5ewhSG8VUmh1DFPspOrerD3QykpT5RSW0OFXNTjrgdCU9yB3x780MhsW5bZhUzLhxbFeq1blmJiminaiJjpVFKUgKsQbi5v2bwGnBhWR%2BFNPn0BMQOE5E%2BTNvD0pBjpTFPBfmnhfCFQxIuo0GpT1Ia8ZqVHp03001KM2uVEclEC5IHcbXjE8ouHbHGcVNnsR0iepNFw9T3Ogdq9WmOiYce2u20OayLi52AuO2A0ycJUscpqYV6gIiMJ0z9UmfjEbZx1kbjvLzMOlZa16WlzO116WRSp1t28pPNvuhtLiF9gSo2UDuPPcRfn%2BGTMKWz4ayGL0kqdeZ8eRV0lXiIp4Tdc2VWuEJUCgi2rVYW3gNE%2B1Km9r8wR3XTEfarR7eVMfdiM4qGBqlI5oDLB9aXJ1OIW6Atxs9UqU%2BlsuJ8wBKvVGw8EcLONc0qVXcWZd1Wjv0CQq9Rp8h7IVBDc5MtyqiAtTaR1dYAIvYb%2BuA0J7U6P8Aq0x90Pmh7UqP%2BrzH3Q%2BaNj5XZPZg5x1d2j4DoZmlSiQucmnlhqWlEk298cOwJ3sBcmLxm%2Fw%2FY6yTl6VN4um6LMM1hbrUuafPB9QW2AVBabApFiLG1jAaiThGlJN%2BkmSP36fmgrClKPJ2YHrSY2RlDlZXM48atYIok5KSMwuTmJ0zM2FdEhDKQSDp3ubgCKGa%2BWtbyix5PYCrc3LTkzJsMTHjEqSWnEOthabX3BG4II7IDXhwtSB%2BnTHyRJ7VqVqv0kzb98IuR5wvfY7DvgLf7VqR9tNfdj5oicKUwm6VTAHcVJP5I91mx8Mx76DSJzEVcp2H6epAmqpNMyUv0iglHSuLCU6lHZIubk9ggMf9q1L%2B3f8A5MRGGaUnn0x%2FhAR0x9Qpn344ZFpeEH3tam0JarzSisg26ot6PjjnybZdl335V4BLss%2B5LugKBAWhZQoXGx6yTvAWo4aphUVfmgX5WUnb5IlOF6ceTj49JEXCI3PeYC3e1enfqj%2Fxj5oj7VqcnrXfN%2FOPmi5es%2FHELm%2B5PxwFt9q1OP6ZMfdJ%2BaI%2B1GS7H3vjTFx9Z%2BOI%2Bs%2FHAWz2rU89UKmCR3FMS%2B1ST%2B2f%2B6EXX1n44hfz%2FLAWoYTkl8nXU%2FviIj7UpAc3XT6FJi5gk9sTjftgLT7U5Hscd9akw9qcl%2BrOD%2BEmLtb0%2FHENxyUYC1DB0r5RmHLHziI%2B1Cnp3U8%2Br0ERd0qtzXEdY%2B2gLQcIU0%2BS6%2BPSpPzRL7T5D9Xe%2BNMbfytyEzIzekKhV8JSEg3TKYsNTVRqU4mUlUOG1kdIvYq3Gw74seY%2BWeNcp8SKwrjmjKkagGkzDYCwtt5lXJxtYNlpuCLiA18MHU%2B277%2FxpgMI0sE6n5nzWUkWi7rUexUUxzgLanCFN%2BFNTA9C0%2FNEfahTP13M%2FdJi6iJ0oUSbDkLkk2AgLR7Tqb%2BuZn7pMR9p9N%2FVpj7tPzRtw5E5goyYmc9J2TlZHDjU1LsS7c0%2BG5ucbdc6MPtNHdSNXbcEi5AIEa67bQFo9p1O%2FXMz8afmh7T6d%2BuJj40xtnLjInH2a%2BFcT4rwQxJTwwoWhN07p7Tr%2BtJVdlq3XASknsvyFztGBy8q5MTTEqLNmYebYSpw6UoWtYQNZPkgE735WN%2BUBYhg6mjk%2B%2F8AGmAwdTR%2BnzHxpjeecXDVjXJLDknizE9aw9P02dqCqalymThe0OhpThUTYAo6qhcdoi%2B4U4L85sV4Xl8StS9Hp66gx4zT6dPTyWpuabIulQR8G4II1EcxAc4e0%2Bm%2Fq8x8aYe02k9szN%2FGmNt5b5F4%2BzPxLiXCGH5JmWq%2BFJR6ZqEpPOdC50jbnR%2BLoFjd1S9gDYHvjz0XJjG2IcsMU5tyUo0zQ8JudFNiYc6N55aXEoeS0j4Ra1DWLi3LcwGrPadSxymJv7pHzQ9p1M%2FV5v7pHzRllGpUvPU%2FE9YqE4ZSSw1QnqqV9GV9PMl1tmWlv3PSuO%2BV2BJjaWZHC3mFlZl2nMev1XDs5INzEqzMt0yfEwtgTAHRrNgARqIBsdrwGgfabTf1eb%2B6T80TjB1KA6z038afmjoDLnhLzczMwlL4zpLdIpshUNRpoqc4GHJ5INtaE28gnkTzjCqTlDmNXcxHsppLC8wcWSjrjU3T3FJT4uGwFKcUs7BvSpJCuRChbnAa09p9H7Hpv7pHzRH2nUe36Jnr%2BlFo3lmnwwZl5Q0VGKMRN06fohmG5V2oUuZD7cq8s6UpeGxRdXV1WtfY2jH8QZO4yw5lNhzOealW5jDuI3VS7ZllFx6WcK1IaDqLdUOqQpKTvdVhtcQGrPadSe2YnfukfNEfadRv1xPfdo%2BaNnZr5MY6yamqDJ46lpWWfxFTvZJhph8Oql0hYSpl0DyXU3F072vzj14CyQxbmbUsPYewU9Kv1utYZmcWzUvPuiVak5ETKmpfSs36RTiE9JYDa4HngNTe0%2BjE7Pz33SPmiYYOo%2Fwn577tHzRsTF2VuNcE5i%2B5VWaT02JHFSwl5WSWH%2FGvGEami0U%2BVcA%2Bixva0ZvifhFz2wfgup47xFh6Qk6dRpNdQnkLqLZfal021HQDuoXF0g%2FHAaE9qNC%2FVp%2F7tHzQ9qVB%2FVp%2F7tHzRd5dlx99pltIu64hoEmwBUoJF%2FNcxtfO7hsxzkRSKXWsWT9HmZaqzrlPR4jMFxTbyG%2Bk6wKRYFN7eiA0j7UaEf06f%2B7R80Q9p9F2PSz%2FAJ%2FfEfNFwc6h%2B2iHSQHg9qdBH6bUOX26OfxRD2pUP9Xn%2FukfNHuUq8XvB2E8S44r0rhfCFEmqvVp1RSxKSzRWtVhcqPYlI7VGwF4DFvalQzt08%2F90j5oDB1H5l2eP8NA%2FJGyMzcp8e5PzdMp%2BYFDRTpmry6pqUbQ%2Bh0rbS50ZvoJsdW1oztvgt4lHz7xl%2B2vq69qpLctOrlrvy%2BaA599p9H%2FAFSe%2B7R80PafR%2F1Se%2B7R80XJzrub9XmlWrY7GxB9BBiXWYC3nCFFBPvs992j5ol9qVEHN2e8%2FXR80XBS77RAknkBvAeH2p0a32afA%2Ffo%2BaJkYUofY9Pn%2BGj5o9Z5b9nniLagPIFoDxnCFF1X6WoWvy1o5fFEpwhSP1ae%2B7R80XLWo81GIqJ7EA7W3EBbPanSEnd2f37NSNvkgcJ0dVrOT33aPmi46lnYg3PMjuiFljt%2BXnAW84QoyRqLs8P8Ij5ogMJUwA6nJ4nsOtA%2FJFwSu%2F23riJN%2Fh%2FyoC3DCdJH6bOk92tHzRH2o0o8lzv3aPmi49kTXbbb6RxaU9XyoC1HB9PPkPTQ9Kk%2FNETg%2Bn7aXpoWG91p5%2FFG36tw45yYfy6mM1cRYSepVAlWmX3PHHUtTIadWlCF9AevpKlDcgbbxccBcL2dGZuD5THWDqFIzVHn1zDcu47UW2nFKZcLa7oUbgagQL84DSAwhIq6pff9akxBWD5FOwfe%2B6TGyM0spMd5PViQoGP6YzJT1RkjUZZLMwh5KmAstlWpJsDqSRaMJ1ud0Ba%2FafKcxNPfGIDCMoOc06fWmLpdw9ttMRG8BbPalJ%2Fq7vxiJThGXt1Zlz5I29k3kLjnPGZqzeEGpKXkaHLOPT1Sqb%2FQSbTiUFYZLlj1ykE27ALm0a5l3C%2FLtPoOhLqdWlXOAtKcJyva6791%2FqicYTljyecH8IRszKLK%2FEOcuOZXLzDdQpknUZuVmZtp2oPdG0pLKQpSbgElRuLADvPYYx7EmGq7g3EdRwrielzFNq9JeLE3KvCxSexSTyUhQ3SobEQGK%2B1CTO5mHfjES%2B1CU%2FXDvxiN%2By%2FC7jibycezpla3huYpkvSTW3JFmd1zaZYXuCkCyXBY9QkHaPNlBw0Zg5z0SZxRQl0ulURiZ8TbqNVmOhamH9rtt7EqIuLm1gducBo32oyNrdK%2Ffv1D5ogMISf6s98YjcdQyJx7Q83KPknXKexJYhrsw01IuLeBlnmXNVphLg2LdkKv2i1rXi5Yb4Ys0sUZt1rJyRlZGXq9BQqYnJmamOjkxLHZh5LljdLxUkI23JN7WMBotzCciR1XnvjESpwjKW%2BzvfGIzPCOHJnFGM6Ng0lUq%2FU6mmnuqIB6ABZDy%2Be%2BhCHFW7dMbOwDwt48zKyyVmrhav4dcpLzFQnJGUenQiddl5ZawC4gAhtaw2SEqPd3iA0B7UZH9XmPjER9qdP%2FAFeY%2BMRuPJvIDH%2BeEvOVPCTUlKUqnlKJipVR7oJZLik3S0FWOpdiLgcri8eDMrJXMTKrGkrgPFFEC6lUtBpapNzpmqiFrCAWFDyuuQkjYg8xAapVhKR7Jl4ekAxEYTkRzmHj6hHSmIuCvO%2FDuE5vFCpCkz8xTpUzk5R5GeS9UG2kpKlEN8lEJBNgbmxteMCwJkzjPMbLvF2ZeGGpeYpmDWw7NtdIfGHwGg8sMotdZSzdwjbYHtgNUjCcj2uvn%2BEkfkiCsIyR8l54ekpMbWqWTeLqVkxR885zxRugVup%2Bx0o0pwiZUlWro5jRb7EsoVZV99jaxi1YawHP4vkae3R3VOVquYlYwzRZDZCZt5TJcdWp1XVQlsFob3vr7LQGvPabLfrlz7oRH2nSY5zD33QjbeceReYGRc1SmMfSsigVgPiVdkpxMwguMqSlxtRA2V1gQO0GMwwlwW8QmMqTKVeUwlKU9ufCVSrNSn0SzziFbpUUq8m%2B3lW5wHO3tQp%2F6tM%2FdJ%2BaJDg2V7Jl31kRkcwy9KTTsjMNlD0u85LupuDpcbUUqFxsd0ncbGNqz%2FDVj2SyOZz5XOUhVGcprNYMp4wfGkybrvRpXp021XIJTe9t4DQ4wbJ%2FCmnPjETJwfTh9kffI8ykxd3PuYpFfrgLYrCdP5JffHpKYgnBsmrfxl7%2BTFz3UE6%2BV49lLp85VKhK0imST85Pz76JWVlZZBcdfdUbJSlI3Jv8kBYvaXJj%2B6Hv5MSnCMiNuke%2BNMb0xnwqZ8YAwnOY1xHg9KKZTWTM1BEvONvTEiyLEreaSbpABuedhvFPAXDBndmThqWxfhXCIXSZ9JXIvzc03LeOp%2B2ZCyCtJ3seUBov2oyROzr3xpicYNk%2BfTO%2FGmMlxBQa5hetT2HcRUuYptUpr6paclJhOlxh0c0qHrBuNiCCDFsuRvAWxWE5IGwW9t6IlGE5Mqt07o%2BKLqFqO5X6IHTbUT6YC1nCUnyDzvyRKcIyX6s98kXQr7lG3piS55hcBbThKU7HnfkgcIs72dd%2BSLkHF38oxU6ZY%2BGYCznCTHwnnB8USHCTPIOr%2BIReVLJ3KrxDUoch8sBZxhFu32VY9IEPamP1VXxCLzqfcWkG4HpjJMB4AxhmdiiXwZgekOVKrzLbjrcuHUt9RsXUoqUQAADzJgMAVhP%2FALU%2BtIiX2rqT%2Bm%2FyYy%2Bt0mr4dq9Qw3XpJySqdJmnJGelnLa2H21aVoVbbYjmNjFusP1RUBYfanr%2FAE3f96IlOE3E%2Fp9%2FUIvylKG2s%2FHENShyN%2FXAWL2rL%2FVfkEPas4f035BGyctcrcfZvYiOE8vKCqrVZMuubMul1LdmkWuoqUQBupIG%2B5MYvMNTMrMOykyw4y%2FLurYeadSUradQooWhQPIhSSCPNAY6cJun9MT8USnCT%2F6qn4oyAlQ5qPxRIXCPhGAx9WEX7%2FZEfFEycHvKHUIJ8wi%2B9K59sIm1ufbmAx72ozQJBUkemJfafMFX2VHxRkYU4Sev8cQ1uA%2FZIDHvabMj9MSfVBWDXSN1pvseUX9RcvfpFJ27TESpwDyirbvgMcVhGYHII%2BOKZwrNDkG%2FjjJelcPwflgCs%2FAEBjPtVm%2B9ER9qc53D5IyW2%2FWBHoVEyilI2Kh%2FCvAYx7UpoDcARIrCs6Ds2D37iMn6RI%2BER6YmDiexfrtzgMT9qs9%2BoiKiMJTxH2MCMoUq24cvcX2Vy80SiYUjZKgb%2FwC%2FbAYwcHTfPSPiiHtPnSCA2SfRaMpS%2B4o6lKIsexUR6Z0kFDy%2B3nAYecIVMWtL3894ijBtTXuWEp85PKMyS4%2BeTi9%2B%2BJtavhkkwGGHBs8PK0%2FHE6cGTp5afjjLlP220iIdIpXJYHrgMWGEp9vmlB9ce6QwVVp50sS8s444kaihmXW6oDleyATF799%2FVB8cbl4Z65iPDc1m7XcLVqap1XpuVVVnJSbll6XWHUTcqQtJtsbXF%2FPAaSeyyxNLJKn6PUUJACio0mZtY8t9HbD3M8TWSr2GqelR0hXsTMWv3X0RuSn8SnEfNNhx7P3HN2z1QmoNgev3veK6uJDiStpTn7joC1t55v8Aq4DSy8scTo13o1Su2nWoexUxdKdtyNPnEQGWmJbal0ioti4F10t8c%2BXwY3TIcRmfr%2BJKdTa5xJ40olKmZlhucqb06HESTCj13ihLepQSLmw3MbC4jMw88Mm8bUOk4O4nsxKzSsQYYksQys1OzDbLmiYUsAFvQQBpSlQ7etaA5TOW%2BIk21UuoC%2F8A3Y%2Ft%2FJin7Q6tqU2JedK0X1J9jXwU%2BkFO0byHErxHLbDXu9Y2UlKtQ0zzQPx9Fe0PqkuJG9%2Fd4xte1r%2BNs7%2F5reA0YrAdZb2mZWca3A61PeHPl8GIt5e155OpqnzygRqBFOeNx3jq7x15w45n5s5uYkeouKOJHNj2VemZWVk6Zh%2BnNTzyZRZCXqjMOqQG2pZpSkhfwt72sY8OX%2Be%2Bf9K4nsM5cVbiArGJKLKZgSlGdmW1sqlKlKNzOgqSkNghKgmxSDzvAcjpwmtSdZqTVj2hpRiBwms8p5J9LChG3cQZSZwv16tzbeU%2BL20vVWfcuKI%2BRZcy4oEHRa28WwZN5zKbLoyqxsUFOrUKJMWO1%2BeneA1r7Twec%2Bn7wuHtPH6%2FT94XGypbJzOd3V0eUmN7I7RRJi5%2FkxUOT%2BcqRdWVGNRY6T%2BcUwSD5%2BptAaz9p4t%2FbJH4MuIDCH21QT6mFxs73Gs5VBSm8p8aK0p1W9gpkXHm6u8SnKnNtYUXMqcaAJQXCVUOZASkC5JOjsEBrb2pd1Qb%2FB1xVlsDz86sMU9app6yllpiTdcWEJF1K0pSTYDc9wi7MP69Lja%2FK8mO7OAbLtNIwnVM16vh52VxDOVIytEqL6VJWKcGNDpZHItrcKgSQb225QHz3ThBxYQ41UpZxtwBSVoaWpKgeRBAiUYVcKyEzrCkjtDS946R4wcsZTLbOCcXhjDC6HhitycrO00MMrTKKmCk%2BNoaUbgELsooB6urYWjRfSL5%2FwCv13gLOjBzir656XTb%2Fslm%2FwAkUfaqv9eS33tfzRfVvvC6VGxKgo25gQ6T3xf73%2FcgwFl9qBKL%2BPy2ru6FfzRL7UV2UFTsskDt6JfzRfUKWQk3OoAnnziLi1rc%2ByL%2BKAsvtOFv7ZNct%2FzM7sezs3iPtOI%2F5yl%2FvLnzRd0F083DFXpHCoJ6QwFmRg15wpQ1OsLWo6UoDLhUo9wASSY9zuWWIWUrU5T59PREBwKpE2nTfle7fbG7uEtyZa4i8HOsEhbXsg6hQSDoUmQfKVbjYgi4PYYyVOYfEa%2FkBQ888K8SOMKnTWFrpWLZGaebZfpc90mltbSlJPTtKBTyOoXB77ZrKzm0jOJ8PJns%2B1q294ixqiiYjOcts5bZyiNk8rmGZwHVJWXRNTKVNMOqCEPOyT6G1KPIBSkAXMeM4Qd5ePSmrusu%2FwCKOmsIZxZnZoZS53SOO8xqvieQp2D5SaaZnHW1oYe9kmQlxGlIssC%2B%2FPeNFlblvLitdnEUxXTOcT5sl7G2rrqqorpymPPn7oYwcIzg2Q9KqT2m6vmgnB02d%2FGZQ%2Ba5%2BaMjSHlndRV6IBTjaj1V%2FHGNnY8cGzxFuklU%2Bs%2FNEEYOm0nrOyp9Z%2BaMh6aZJ6zpMTKfeSNlGAxxWFXkq3XKenWfmiJwy4N1rlrd%2FSH5oyNMw7putw%2BiKb7yym5WPReAx%2F2tOlOpK5W45guf6omVhxa%2FJblyQd7LHKMlkUpmkO9KogoQCn5jHpbkkISdThsTz0%2F77QGIe1h8HWlMupO%2FwxEDh1aRqUhhI71LAjJ59tco40jWVJdTqTtbTvYxt%2FKafpeFMpKzjRzC2CarU3MaUbDyZ7FsmqZkaZKTLLqluKAI0gLCSpW9gk7Ramma54Mf1lrYre1iws5rmM9mr0zl73PHtfUeSZU%2BhwRFzCs2pHSIZY0eZUdK48zXxzlpi2cwXjTILJ9qdY0vNPtYfUuWnpRwEtTMq6F2cZWncEbjcGxiw5xT9KxDl9lhmHK4Mw9hyq4hlqw1UWKGwqXlXky80lDKy0omy9NwTfeMs2GWf4UdfviGvZXybSqmKrOYidUTqmOXwTPgaEGGphHU8VbWD5JCufnib2pzarapdoX527IyPprHUbgi3bAzKex1QjA3WNKw242vQZRGrVa%2FZvEThV7tlm4yRub66hr%2FAIXKKwnOvpWjWmxO1u6AxRGGnydHiyeQ5Ed8TjDT6OoqUTfvuIyLxsrICAUknf1dkeiXbm56YblZKWempl5WlthhpTji1dyUpuT6oDGPau%2F%2BtEfGIqJws9baWbG1%2FKEZNJydTnq4xhmn0ucmq3NzCZNmmtMqMyuYUQA30flA3O9%2BXbG8cPZX8PWEMbyGD8888EJqbK1IrEjQ5Va5CSe0byz1SF0odSeehKgDte8BzD7AvDypVKfSYgmhvKveSbMZ7jMYWkMXV2VwZWXqnhyWnnk0mdmUhLr0qD1FLAsL27bC4sYsgnNLXSCx1fCTyPcYDHnKE8gp0yjaR6R%2BOJxh%2BbUP0CjnbdQG8ZAmcK9V1BW21x%2BIRWanEqUlAUVAqN1AD1bd%2FfAY4MMzp%2FuBr1uJiU4ZnTqtItDSN7LHOMxaprsw0p5Lii2kgElNggkcvP6IgqRV0Liw99ibUtPV8qxGxJ5bQGGHD0wkALlmtjfdaYnGHlFJuzL3tyCxzi%2FFxRPWTba4N%2B2Jw4kJF0q9IPbAY57XnPtWfR0gh7X3v1Jv7sRkPSa%2BxXzWibpj9pAY97X1kEBhhR86hEEYcd6XQmVbse24i%2Frc3UtAIAG%2B8SqdQEk3JJHmgLSMKvlVugY5X3cA9UVU4RfV5LMof8MiMlVT%2FeEuomDcgGxRyitLUlcwtLTcwu6l2uEXPogMW9qTw5syn31MTowo%2FwBjcmB%2FfUxtrIpzDAxw61jHBdQxLKv0qbZlpaSpjtRLE0dBRMOS7S0LWhICxcKFioE35R0y%2FwDUlL9%2FmOGDH6V77JwfUEg9%2FwCm77wHBq8L2RpKZIK7%2BlH5IkThW%2FlOSo8xXzjtDH7fC47hCqTWGsh8Z0pySpM6C%2B9haoslp1aPeJhUwXdDaW3LFRWlQKbjbnGneHLJaYzxx2nDkzPuSlLp0sJ6sTjFulDJVpShq%2BwWtWwJ5WJgNLDCR5Ayo9Ln%2BqHtSV9vJffP9UfSnG%2FDbwsYGwDO1LFuEXqPS5EobXVWag%2BakX3SENob5h11SiAlAQbm%2B1rxxJnXlZVslsxqjgOpVAVJhlpmcp8%2F0XR%2BNSbydTS1I%2BC4OslaexST2WgNYOYRUyy5NNtS00hoanOgXrKE9qiOdh2kcotiWqWpRSpLNvRGUy07OSk01Ny8wUOsKC2za4BHeO0dhHbG06DwuUbFlEkMU%2B3c08VhkTniiJIlMuVm5QDfcXvbzbdkRMzsiM5T%2BDEcKqcoaCLVJBAShvnblDoJAn7G38UdIK4MpI3DGYRcNtW8kQOV9zfaJGuDWUdsE5jtoURyNPWRfuuDa8MrSPmyjhWfjQ51EvIfqbfxRMJamfCCB6Ex0WeDBaFaPdDl97WPiaiN%2BV99o844Npxywax9LE73Bk17W9fbExFfiyjh2cfOhzyuWpSSQUpO3dBDFGsSU9sdCu8G08xqtmBIEAXv4o5HhXwhzguEY%2BlFEG36EXE8GvxZPjbPxoaKMtRyArqW9V4CUo6ybNpMb2Rwdzrg62YMiFX5GUXE%2FwBRzVE30ZgyAH%2FhVxOVfiyfGWfjQ0KZClq5lHrEPY2kd7XxR0Arg0qDLCpqbzOo8sy2kqW48ytISLX3v6DGJTHD7h9K1Jl88sKrta2rpEhXoOm0IornbTPMr8bZ55cKM2sDTqR1d2uXdEfEaKGQFONDfujbDHC6%2FPAGSzawe%2BFIUtHRTajrSkAqKdtwL793bFJ3hibYmBKTOdeCWnSAQFTptY%2Be1oqu1a1J0IatXR7eaJPFqA6qyENkd5TaNuOcKM61MGVRm5hJ57mlMu668V9nVCEkn1RK3wr1J%2Bbfk280sI%2BMSrpZdYcedQ6hwc0qQUhQI7QRtAan8Qw8nZTLR%2BOIeIYd%2FU2Y23McKFZlh79mlhBBI2CplYv8aYoJ4Vq4pQSM0sE7nmaibD5IDV6afhvtQ3o1G9udrQVI4cWoFXRXKbE%2Bf5o2RN8NVQpxQ1O5r4ERrUQrRUVOFIAvq6qTtFncyQ6Pf3UMKLSeS%2BlfAPrLcBiCKXh4iwLQKd0i2xHbE4kKAnZxDYT36YvL%2BVtNk3G2Xc1MJIW5yBeeG3eD0djHlfwDT2E2VmXhhztsiYdJI%2B9wHk9jsO6tGlm24vta47Yh7H4dK2tCmet8NPwSLbkRM5g%2Bn395x7h1XpmXB%2BNEedeHZJJ0pxvRlb22ccsPjRAexcnh5bi%2BndStWo9Y8jEiaXhvfStobbdljFvNEZVYnFNJNuV3FfRiAoidW2IKYR39Iv6MBdXKdhpTiUhTKd9lH7W3zxUNMwmhCHOqsG5OlN9MWRVMCBdVdp9v36r%2FAM2KXibCCUprElcdylW%2FFAX0UjCKbFpbLjak3CrGx%2BLl64iaPhdRbcdSyhpRspSVX0m217cu6LClhLSrt1aSKhsSsnceoRTLDYJUanLEnmQo7%2FJAZGqj4VQbFTa%2BSgE2spNjqAP2wNtoi3R8HBSEOFkLKesFbb%2FFGOCVGrSibRq32Tft9UehNDq6rILTu24UWldvntAXn2Kwn0l1ltpJOk6Re1uZiZdKwuXOjbDadKtKbbk%2Bfu2izGhVlHwHfW2rf0bRKaNVkbmXmEq%2BDdpY%2FJAX1ukYYDYKuicG5UB2DzRH2MwcqVW60lpSkhSgnTZVgeVuYMY8inT45suavtujVFUUycI3Nj%2B6CgfV3wGQ%2Bw2DQtJs0CUgt6uR7bGHsVhHygWCgm6dPd2xjTshPoO4X6FINjFMSs0CbHSQOWk93ogMpbo2DtXvrjSAsApVbl5rxO1RsJAL6Qsak3CRrvew5xivRPhISXkpJOyjy%2BOIpkXFkkLaChy61ifRAZEqjYWcstxLKAB1wRfQf97RV9hMHO6ve2RYi2ntEYwunziTft7t4Jk5wi4N%2FNv80BlXsBg64DRaJF9QtuDEHKTgtsJLZbVc6VotYp8%2FojFQ2%2BoaFOAWV1Sb2MVW5Z9Z1oWyTsNzuo%2BiAyhVDwU7pLDjbqPhAAg%2BoEfLE4w9g1rWCGNSVbJVzI7PTGJLkp7XdKlAnewBttASdTKSN1cjZQJO3zQGVewmDV9sv5OpNk%2FGIqDDmD19JoeZVoFxtbUe4bc4w9UtOuJGtwbEpCzcc%2FPE6JCdHvfjTf3XZAZR7B4LQla1PttqTptcc79npEVjhvBalLb6RhS0eSQdlRiTlNnNIu8gk8wImTSau6oLQ1MqTtuhpZHp2EBlS8L4JCVIbeaUokKbVoICk25b8jeCcPYELyWkvoCilKkjlv2iMbNGq6k6SxMEd3QOfNEgoVaVfo5KZXfnpYX80BlaaFgIhVn0EqRqKTsUq1W9e1ztFNNDwUpSk9E2CoHQQdQ57evvjGPYSrC%2F5im7jn%2BZ1bfJEF0utKNzJTPqYUPxCAy%2F2BwKhtpWpK9YVqOjZKhyB7bHviX2GwDZRdLJKW7gJ%2BEvu80Yj7G1ZPKUnQfMyqIimVX9j5vnb9Dq5%2FFAZYii4ECC5paACQTffftEVU0bL9bRUp9tJSQkoLe49cYoihVx37FRZ9e9urLrP4hE3tdxPp1CgVG1r38Vc5fFAZQaHl4lSUqeYGq9uqb7R6E4bwF10BTCzpulQSSL35beaMQ9rmLVjScP1Qpve3iq%2BfxRWTg%2FF7XPDVTR%2FiqxAZ4jBeX3izbxDKgp0IISvrpSeatPeOdvNGE40wfQ6dIVR%2BXfQlcsx08mpKwUv6XACO8XQSR5xHkFCxCCCae%2BgE298aXue7viM101LcZGIacmaYdJ1Srq1o6UDs1DrJPngMKpDYdCulGrext2RecKb1ySSP1y0P5QivUJCkSqTP0RwqkXV9GG3nAp5hVr6VWAuO5VhFDBfXxFIJte84yLfwxAfpYhCEAhCEAhCEAhCEAhCEB%2BdziB%2FwCVfHV%2B3EtT%2FwDvHY1K6eqT5jG2%2BIY3zbx0ocjieqH%2FANY9Go3fsN%2FOr8cBl2FWwuklxR%2BFFzvcbRasMk%2BxWkH4Qi5FzQNJgBMSE3iJN4lJMAPLaIp2F4A9W0DsmAFdoilyKSoJgKi94ghAiATeKoSRAS6TDSYmiHOJykQA7LxMGwYhoMTAKEMpEyQRyIFh3RUQtfVBc0qSpJSrkQpJBB9NwIk0KO8RtaGUjqhrE%2BKMYcCmZOIsX4jqFcqdQxg2pybnXy4sgvS3K%2ByQDewAAGrlHKZ8tX76Mwk808b0%2FLKoZPSU9Jt4Vqc6KjNMeJpL7j%2BtC79Ne%2Bm7aOra1hGI9GvnaGUiBF%2BSogUHsMOjcHNMRBUPgwykRF46%2FwCCx7CwwfipvLxume7X4rMiTFbVZkyhA6ES9vgE6uktuVBIPVMchJN%2BcXCj1mqYeq0jiCgVF%2BnVSmuh%2BTm2FWcZWO7vB5FJ2I2MMpG4qurKtvJPGE1mZ7OucQwrDyqgJ1DiZlMwXkpaQlJ97Mt0Grt2VbTtaMlxAvgvGamXfsA3UfaY3JTbmKOu8Wi%2BGU%2BKJfJ6wPSdJ0mjbZMakzfzdxHnTiOQxXiai0mRqMnTWqc45T2ijxsIueldJNysk%2BgAACMH6%2F7pMMpHavDtOSrOJczWcL9CvhkY6ZSFYi1dAy4ptJcblSvrKbK9epJ2HVIss78qT68K%2B6i3PYKbm28Oe2WVdovjYs%2BzLmab0k%2Bje3bpteLvjPPHG2OcD4Yy2qCJKn4awtJNyjVPpyC03OrRyfmPtl7nblffcm8YGzNOy03LT7ASXpaYbmW9SdSdbawtNx2i6ReGUjvyRQG%2FCOYnDhT0r2D3AynTvrMsi59NheNNcJhnGqfxDmoOvusows%2Bmf8YKggzXSPC69XNwp2vztaNV4nz5x%2FijN%2F3cmZiXouKELYUhUglXQoDTXR6ClZJUladQUCd9XZYRkmY%2FFlmPmPhWdwa5QsO4dkqvb2XdpMtoeqIFuqs9gNhfmbbXhlI3lk1mvhvKPhDywruO6NM1ChVOanqdMhlpLymXUrdeZUWj5adTYSe4kHsjCeOPEa8U4YykxmzJuNOV2iTdTaavqXd0tqCPOrcD0mNHVXNbE9YyjoeS83J04UXD1SmKpKTKWleNrdd1dRR5BCda7WG9%2FNF0rmctbxTK5byGLqFJvyGWzbDEiiUCkOzjbSkq98UokaldG2Dba14ZSMczcZkUYlewwlIXLYTp8lh1CSLgql2gp5duxSn3XifOI7KxcqXTxzZGOKKQmYw0yghfaoy7oQoHvjhGdemarMTs9OqPjNQmH5t9Q59I6tS1EfwlGNhY%2BzzxzmFjTDmPp5EnSK1hSQk5GmPU5Kk6DLboeOom61Em%2FZY25RGQ3zw3t1D6sbNF18zXTIka77JLWFaVDpQGOkvtYAdS%2FZe0YPXkyzvg7MI%2B%2BFckjG9SM8QbIdHTvadens1FBA77R5cV8ZmbGK8Kz%2BGhSsO0d%2Bss%2BLVSsU6U0Ts03YgjUfJJBIvc2ubWjFcpeIXGGT1KnsN0amUer4fn3xNOUiqSweYQ%2FYArQD5JISm%2FeQDzhkNzZrOuDCnCVMz6nVvpVT1OB4kvLHSy5uq%2B%2FPTz746DqeeuFJTiMRkg%2Fh2aTiaYqjVPYnFIT0RkHW1TKj0vlCykhPRdpsY4FzBzqxxmhjmnY%2BxI9KomqM5LKpcnLt6ZaTQy6HEoSnmbqSNR5kRcpvP3Fk9nzK8Q0xRqYqvys21OCRGsSgKGi10Y31WKSb73vE5SLriOZFLz4zaxupxClYUNbnpYKFgqcf8AzJKpv2HXMEjtuiMm4CkeK5r1CnNzawynCFQR0RUbOaEIsbcrgX35xpeu45m6%2Bxiqbqcv%2BeuNK2xVai6wkIYQ0z0jgZbTufsy0q9CBF3yWzfreSuLJrFtDpMpUnZmlTdLVLzSilAD6AA5cb3SQDbt3EMpG3sEzxoXAVXatS6jUJBubx221iObpiSZtNNMw2hxQtuCGiNO4uCe%2BLHnxkxldg%2FL%2FBuZ%2BVmNMQ1uiYufdZamKkrWtbKEdJrbCushY0uJKFbaow3JjPjGGST06xRpCRrFGqyAmo0eoAmWmFAW1230qttyII7IuGcnEJM5t0DD%2BF2cA0fC9Lw889MS0tTnFKbCnE6SEggBCQL7AczDKRvTCmE8icp8NYd4o8OM5syNJbmehbQ%2B21qcl3AWwuZaG%2FizihYWO5t2RRx3gvIPH%2BCKxxRYjZzWm6fVppwLW222HGm0J6NDzbagB4slYShKibbm8aXqvE3jGr5MS2R7uGqUiks06Xpjk%2BFuLmHWWXekT1SdAVcAX7uUJXidxlJ5HryKRhyjGmqpS6N7IOqdMwJZTvSHq%2BTqHIHkOcMpGmvfP0xHRfuTYlI5gEjtA2iQkxWc0fqmqJIZSJNGvrridHX977IaP3MTdGtaFeV5JTq5W7NoZSOnclGkZD8NuK%2BIN1K0YmxslWGsGKdWpSmm1akuTKNR5lQWrV9qyO%2BOYOjQ002wlRWGk6dSjuo95PaTzMZxjrOLHeZFEwzhnEr0i3ScISvi1Kk5KWDDSOolGtQB6ytCQAfOrvMYNoiMhBVoAi0FIMQCCIZCJVEhPdE%2BmJtETlIpA98ThUTaIl0nsiBCIEkGIxAi8ATziYq07GIpTbeIKTcxOUhqPZC5gEeaKgbBhlIkvtuYi2QDuIKQAbAxUSkgbARGQ6OwVXstswOEicyAxtmAvLt2SrjtSRWZyReckKiku9L0ZcbFlLAVYt3vdCCLxlPHSqkJw3lFLyk27Mus0V7xaYmLh%2BZkOiYS24tJ6ydSgF2P2xjSeWXEPmNlVQ5vCVJTSKxhudmDNuUWtSQmpVL5tqcQk7pUdIv2bDlGO5l5l4zzYxU9i%2FHNTTN1BxtMu2hpAQxKspvpaaSPJSCSfOYDFiodwimTeJrXhoicpEoJEbH4e5TLGoZv0CSzgdLeG3VrHXXol1zth4s3Mq5hlS9ieV9IJAJjXWiIhtC21Nrb1JUkpUFclA8xDKR25nQ9I1DiSp%2BGOKp00fKhmmOvYNEi%2B4xTX5sBACplxsXS8lHSAIsEpskJ2NzpdqU4YE5YZqKNXnTjKXqVQGBS68sOTEl1fEFIRbSsHr9IV2IAv3Rj1T4gsa17JVWSGK5KSrcqzMyz9Nq08VKnae00q4bQb2UbXQFnraCUm%2B1tYL6Q8ogdQUwYIw9irKmc4KajUKjmRU2g3iGUmJh1cs7IpZbU8KilVksaXte6T1bXTvaPFxt03LmQzQkjhpEtL4snZZUxiyTkiFSjbp09EvuS8rr6hYakhKiASY1zlDnzi%2FJah4rpWDabS%2FHcToZQmrPtXmqfoTYhvsUk3KtJ2CgDvyjXT78zMTD05OTb01NzLinpiYeWVOPOKN1LUo7kk9pgN%2BY3bbb8HzltZtQS1jmdCkqUTsXngRY8wQbRn%2FEnPVOX428tJeVfnWkol6AmmoZfUhAQpwiYDaU7KSRYLFuQjnio5oVerZK0LI%2Bcpkp7D0OtzVZanQpRfeLuqzShyCUlajcbnblbfZuGONHMDD2H6bTarg7DmIq3QJUSlGxDPs2mpVrRosoWOs2AuQRe28MhvPAU4ikcZfElPyMu26un0RuohpDgSXVtaHCkK5JKiALntihX838vs4eGrNteXFEmafTaRR5eZnA%2FLCWCp%2BeKJh9OjtUldwtfJRNxtHLGX%2BeuMsv8S41xmG5Ou1rHVJmabUZqoagULeVcvpSjmU7gIO1rd0WrBOa1bwJl3jvLOlyUlMyOPm5RubmX9XSSnQgJJbSNjqSLG%2FLnE5SPGZg0nKuZl9CdWMcRpJUr4cjTG9Rt3DxuYA%2FwcbapiDL%2BDtx%2BzKI3ON2EoTcqITds3Fzta3LlGlMSVxipyGHKXKSzrMtQaT4rpcA98mnXVvTTwt8Fa1JsOwIi%2FwApmtXJTJSp5GKpMmqkVKvNV1U8Srp0KbCT0AHklJWkKKudiREZDdfFjUJyUXw9ClTE9JMJw9TFyCJR5bWh4uy19GnZSym%2FfsTG%2B5sgcaWbE3TSlM%2BzlLJ9ApqxcS%2BSSk7b6xZPxCOWcvuLvFmCMJUbCVbwFh%2FGCMLH84J2rAmYp1hZIBsdWkbAiyrbXjDaJnzmXRM3Hs8Wa4y%2FiqeW4JwuNAy0ywtISZZSB%2BlpSlITbdJF%2Bd4ZDY%2FDpMO1DhR4iGqhMzD0m3JSThD7inAJpTepxSdRNlFekq89o3FgjNrAmU%2FCdlHOZl0V6dw9WpKaadU2wJlMvPSi3ZyX1Nc1BTqAEqHkrsTtHPeaHE9inMvCTmA6bg%2FD%2BC6BNzHjdSlaMCFVFwEKAdVYWTqGo23UbXNhY4bibM%2Bs4oydwZktUJCWbp2Cn5x6XnmnFF%2BbD%2BsBLgPVToS4R1eexNrQyG8OOyYqmNatlG%2FJyy2J7FOG1vsMrUFKaenZhnSlSu0guC58xjRmJK8w5nJ4%2FQJ19iRolZkKBSXpVxTKkSMk61KISkpN9KujWojkdZ74yLEefNTxvivLjEGKKJIMJy6oppku3K61iddbQeheWlWyDrS0SASOqe%2BNUyL7si5KTTakuzEq7Lv3cGzjjTqXLn98pO%2FpMMh9D5CmSD3hHMVzs0llyZkcAMzVNbUi%2FRuFCW1FI7wgkbdijHPOHcAUHO%2FJPGmadWzuxZO4%2FoEpOVPFGHppavFJKYbcWWmFtkgdGpDR0qAtcAWBBjFMd8ReJ8S8Q6eIzB8ojDlWl0SrbEktZmGi2210bjLp21tuAqJG1ur2iM3rvF9QKxg%2FGFFp%2BR9EoFaxxILkqxUKfMhKJgqSU9IsaQpdgpZAPIm94nKR4uHnIvKTOnCVSVWZ7H7eJKJLzE7UUUmVR4qlkLuw3LrIPSTK0DUlFwdQ2G2%2B3nZjKLjIVTsEM46zOmzgamLm5sTFKQwH5hNmi%2B%2BpQsZpf2MJTsSFbXjn%2FIbiUxDkBK1yUo2GafW2K1Nys6Ezcy430DjDZQLaB1gQQT2i3njzZK8RuIskK9iqu0%2FDchW%2FbY%2BxNTKJl5bXQutvuujRpvcEuqBv2ARGQwDMiVwVIY0qMhl2%2FXHsPyxQywutyolp0PJFnkONfB0ruN7E25Ri8XbElZnMTYhquJZ5lDUxV5%2BZqDraCdKFvOKWUi%2B9gVWi2BtQPKAlsYvWGMcY0y7eqmIMA4gfo1UmaRN0tU0wAV%2BLvpHSJST5JOhNlDcW2tFptEVtNvsuyikE9MktrsbEBQttAdUce0u%2FNYsyvSlxyYXM4TZQhDaSpxxwvtFWkfCWsnYfbGMyGIsjOKrP9OCcR5XZgUDEEzh7oZWrv1NchNSaJcA6PFEmwB1LIWvZRsLdo5jzSzkxlnHMYbnMXIkZaYwvICnSD9NaVLqCApKg4TqJ6QKQkhQIsQSIz5fGpnKZHUZXDK8SKkBTXcVrpwNUcYHLr3tq2uTa197QGlMV0NzC%2BKK3hZydTOGi1Kap4mEm4dDTqkBfrABPnvFrXyEVphRceW4pxTinFKWtazdS1qN1KPnJJJ88UlDflDIU%2B2IpuNonAvEqtoZCRUE98TEQAJ5CJykQ1QC7crxCwMNIiBMHV9kThaztaIJSSeUVktm3KGQoqMSgxVW2e6JAjvicpCJ2y2450b7YWnUFd3L0RLpiZCLwykddM4%2FxtmDwP5q4pxviaaq9VexJLyaJh8JGmW6SUCW0gABKR3Rqjhdy5qOa2dFIwr7I1Bmg07VW602zOOtNmVZULIISoAdI5oBNuQVGLU3ODGFIypq%2BSsu3TThquT6ajNa5W8yHUltSdDl9hdpO1u%2BK2XucuMsrMNYroGEBIMe3KWMnPzy5cmcaZ6MoCWXQodGBqUrkesb9kMpF14ks105x5u1zFUhMaqNKOCk0ZI2SZSXJT0gH7tfSL9BEapXpWbk2tFRAQ2htllsIaaSG20%2FapA2ES6AfXDKRT9ceukqp5qcn7LqmEU%2FxloTq5ZIU%2BiX1jpVNg7FYRqsO%2BKHRRFsFtyIyHcPET4phzLTL6j5bFEhw6VGcllYpq2HyXJxco4%2BgrW6QNWhSblS91FYKVAaQDgEtTeCZHEBPtTlcdRlwMMMLkyiamPF11XplJeSl7T0n2DQtNxYuXHmjWWUHELjDJqlVnDlNp1OxDhyvsPMzVDq6VOSiHHUFKnkJHIm%2FWT5KrA7KF41WGw2hpgKUromw3qUT2QyG8aWrh3lMk6tVKHXa%2FLZySuIZpeDvE1vJn9YnEinhttI0rQZcde9lalKjb%2FFVKMz2ROFK3ntLUuQzrLbbUkilgBx5npB0qZlPINhBKlcwh3ZBIJEczZQZnVTJvHUpj2j4epNampRl5hEtUkq0JLidPSoUndDifgqHeR23i2Y3xriXMHE89jDF9VXUKvUF6nXTshtA8lptPJCEjYAenmSYZDd%2FDY3o4fuJNhjylYeadTvsT0bl9uQNxEmcs2pXATkwyh9Ylpmdm1TJZcUhp52z5bK9NutrFxf4Q741XgvNfEOBMFY8wLRZSUclMxKa3Tp%2BYdB6WTCCoFxoDYlSFqSdWw2IjLcpOJfEeUuFpjALuF6HivC65oz0pTKu1q8SmVEKWppQv1VKAVpI6qrkEXIicpHQeL%2BlVxDcI01UnlqmZijNpmVuAlxS%2BjA61973Ktz23jamAc8sFYpzvqGVcphqYlcYSExPyNYmOjTpVJSCkmWcD4%2ByBfTDS3zRdV44UqnEHjuuZzUTPKuiSnqvh6dbmKfTylSJNmXRq%2FMqbG4SdaiVc77%2BaI4Sz9xTg3Oyo560%2Bj0ybrFWXPqmJJ5S0ywTNAXCSnrXQUIKT2235xGQsmHump01j7GiXAlzDsjPSks4kdZFQqM0qTYUk9ikoVMq9Ubd4HJeXk6lm0thvQU4Be3TyISV8%2FOBbfzRoJdaZGEHsOBpxU7P4h9nJ59adIcDbC2mWrg9YBbzznLYqFoyjKXODEGT72KF0Omyc8jFtBeoE2mZUpJZbcvZ5sp%2BGnUbA7G%2B%2FKGQ2YpxTHg3KAhqdUwzM42dRPFtxSEuoUtQ0uEEbDSnt7BG15QPzk5wSNVl5UzOLdfcW5MqK3VJRKAouVbnYJ9YEc55KcQOKcmKNOYPkaVR8R4Un3Uvv0KtM9Iwl4JALrarEpJ0p1Agg2vsY8mZGe2YGZ2M6LjaoT0tR5rC5bNAl6Y3oZpmhYUC3fcqJSASdiBa1oZDorIqbqX1w%2FHEvN1CdUno6ymZQ68sp8WHQlhJSTp0JudPdc95jw8IeNqdl1kXm9jypyD83TqNi1MxMNMJCnFyq2w0spSdlWQu%2BntAI7YwbEHG%2FmPWKPUZan4QwzRcRVaVEjPYjkZa027L6Sk2B8lVlKsSSBe47Lawwnm1XMG5SY1yeptOkl0nGypZcxMLKumlSyEpIbHIhaUgG%2FLmL3icpHTPEpj7C2Y3CZKYkwVJpk8NS%2BM2qNSQWegCpWVLqEudFb3oGxsg7gAXjlDGyBTaHg7CzTS5OYp1EXWJyzhSvx%2BpOmYBNjdK0S6JVIPMCPfO5n1ifyQk8gZuVlmsOtYhXW3Z5pBM4pK1ErZAJ02BUsg8zcA2Aix40xAMXYvrmJkynizVSnCuXZNrtS6EJaZQbbXS022k22uDDKR1Xi6Vkqz9RZR66tc4xUFMPTZmll0zCkhtXXKt1FSwm5N4uVbwjSs%2B%2BKrMjLnMLOnGmH63I1RmVw3RKUVtIXSxLJW6%2Bk3CVWUTcHcgmxPIc2Y%2FzmqeOcJ5YYUEgmkvZY05cnK1KXmCX33%2BkSpp9I%2FSygNp23uq%2FZG5sN8dM0zUaVi3HeUFFrmMqNKqk5fEUo8Jd95sjrJWCkkBZ3UkEjdWm14jIa5yAyuy8zJx3Ucs8bVbFsvXFzjsnSXKJKoclQywXA%2FMzS1X6JIKU%2BaxHOOgpdzJuu0GW4KE4%2FzSE3J1VUkptyjBt4y7Q1iTdc0afEkn33X2gp62mOXsos4qnlBmBOZiSFEkqlMT8pUJR2TfdW02kTTgcUpKk3PVIsAb7ReGeJPEjXEDOcQ3tdkTU56UckXqYX3BLqZXKpl7ax1rgICr9pv2QyFt4h8F5c5cYybwVgWdxS%2FO0oPS9cTXZZDXvgUCw7LlNtbS0EnVyNgQd9tVxm%2BceaNUznzEn8w6xTJenPzcrKySZWXcUtDbcu3oT1lbkncn0xhRTDIIvWEMSYswliem4lwPOzMpX5N7RTnpRkOvh5wFvS2kggrUFFI27Ys0ZNlzjWr5Z41pOPqAzJvVKiPmYlkTjfSMlehSbqTte2q4sRYgGGQ6mm63M8LuWWMMS5t4qmK7mzm%2FKrbNGmZrpGZJtTSm%2Bket1RoS4suEAAkJbTexMa24ZcRYWpmPMDULPbEmYYnKVPyMtl7LqLqaUhCmig6kmxKFL0AaLp07E2MUsQcaGZuJ6LU6HWMKYGmGKvIPU6aW7Ry44WnG1INlqUVAjWSN9jHkwHxd5k4Jwph%2FC83R8M4sVhCXTKYdqVakiqcpbSUaUpQtPlAAAb2NgBeGQsfFa1jKW4gMXox49Tnaz0zC9VP1GWMoWU%2BLBvUAoWa0ghW9wey0aj1E84vWLMU4gxxiOoYtxVUlVCr1Z4zE3MFOkKVawSkDZKUgBIHYBFmKbdkMhTheBG%2FKFj3ROUiERvE6EX5xKtOkxGQliUk35xNEp5wAExNfe194It2x07mJk1lvSuCXL7NakUFLeLKlNyDk5VEur1zAmXH0OMrTfSUp6NGmwuN%2B%2BA1plZw%2BY2zZwLjDH%2BG5ymtymDUFT0rMrUl6dUGFPKQyQNIIQknrEAmwG8Z1wFuGYz9RMI%2BxO4Wqjiduwhrf4jGxeDQBrhzzxVc2aW%2FdQvYD2IWRfu3jW%2Fg%2FzbO6SHfhGoj%2BSxAYTntT5us8SGO6XJJDk3U8XOSbIUbBTzrjbabnsF1C57otmeGTOJchsbIwLiio0%2BozTlPZqLc1IFRZWhalpUmygCClTahvz2PbGX43s5xj1MGxBzJl0%2Bb9FNCM18IsNOeNNJ8pvCrSj338ZmOfmI5QHLfONl4TyFxjjLJ%2FFmdVLmqc3RsHqWJmVfcKZmbS2lCniyALEoDiTYkatwOUbOz2yYy8wbw05U5gYaozkpXK14p7IzZfWvx4TEot5RWknSClaAE6fgkg3jMMhmNPAfnC4lVys1ZR81peXFoC1eDj2zlxF%2B6w4n5Jxr540TO4XqeYmes9g%2BghlNQxJi2oSEp4w5pQhxU46AVq32ABJ9Eb38HGnVnXXE2VvhtA25foxnnGqsnVJ%2Bq2wm4FdU5hzQBPnmpiAxbOPKavZL4%2Fm8vsSTspOzLEvLTrE5JrJYmZd9GpC06gFJOygUqAItGCOW5Ax0Jx9Lcl%2BIOszJ5tYXpC0DnYCXcI%2BO20X7jLyVyzyvy%2FymxDl%2Fh5ymzeIGHG6i8JhbiJwCRl3wteo2DgW4rybDSfRAcs3N%2BUR1GI7CIah3CAmhEExOOUBKpQuL3v2eiKZuPhbdkVSFckqEQ0C%2BwB3%2BWAp25HURAXGoa725WioQBc6bxTIPVGm1ucBNcxCEICRZPwVE357XibR1NISfit6oitHWCQjYch%2Fv3wuL3CtxASIUlW6RYfliZToTtpN%2Bz0dsU0oWo7C3d27xPcpFnB6LQFRBRbbf0xKbavLt6IkCk37%2FTE50diICfWkAXWYjLMTk9NJlZOVmJl5y5S000pxxVuekJ3PntEg5%2BRfaNy8HS5hniSwtMSbq2piXpeIH2nEc21opMypKh6CAfVAasOHsTJISvCddSTyCqY%2BL%2FyYiMLYnUtTacIV0qSdKh7Gv3B7vJjNaJxOcTb0tK%2BK5%2FY3JfaSuzk%2BlVyU35rSYuzmf8AxTvIRqz4xqlKORFUbHx2Rv64DWjWHsSpsUYWrZvf%2Fm57s5%2FB7I2XkzI1el0HPGZnqPUJLpcp6iyHH2FshQ8elNSQVAb27O2ITHEPxPSLOuaz0xetG6NPsgg3J%2Fep7YynL3NzNrMDLzPOkY5zErmIafLZazUwzLz74cQ26Z%2BVTrAtcG1xe%2FbAaKlp5cskDowsrVq52iquv73MqnV5JIVzjyStLm5xsLb0qA59YD%2FcxXOHp8JS4ppFiLi7g9XqgPDVZhdULp09Cp1kM2ve3VIvGxc7s3U5xVbCVdXRVUteHMJU7DDjZeDnTrlAoF9JHJK9eyTuLbxg0pQaxUKzK4fplLmp6rTzyJaUkpRsuuzDq%2FJQhKdyT8kXrH%2BVuY2VVQk6VmTg2o4emqgyX5UTbdkPoBsrQ4LpUUnmkG4uLiAsrddSjRrlFfvkqv649DVblgVlbRKikgBRPPsigMPzykBaWkEHucESOUKqNFV5W%2BlJWbKHIC5MBsvJLNTLnLaZansVYAr9QrlMqrNXpldw9XTITSW29JMhMIUChyWcUm6ttW9uUXLKvEyce8XeCsXP0eQpasQZgS1SVIyqNLEvreU4UIHYB8pue2NVYYwtiLG1cksMYToU5V6zUFFErIyjet54gXNh5huewRsXhllnpTijyukpxhSHZbF7DL7LgsUON9IFIUOwhSSD5xAYxU8zsxBWqg7L5o42baFRmwyUYhnACgTDgSlI6TYcgBFMZmZxKGpOZWPinzV6dt%2FPjLMhcMUqu4qxFVqlKtzJpM26ZZDidSW1uPvHV5yANrxtCuZw5b4Uqb9ErlRQ3PShQHWG5VSy0SAoAkCwuCDaOJesWtLG8TdrGymuY2vpOCaC3S%2BYTZ4tiV7ixotJmKdUTsmY1zMxrnKdXgaAGY2b2oJVmPmACNx%2Bf88fX5cGsxM2GlKU3mLj9BWdStOIZ8aj3n3yN3HiIyWSnSvEBaVe9jJOD8kVU8RGSt0gYtl7G4UfFnth9xGHvpiHJdp5%2Fub3EvRmNuLU81PaaQOZGcCmwDmRmEUJOpIOIp2wPm68RTmfm%2BhCwMzMelExs4FYgnClwDsI12IjdSeIDJ9XXTX20gAgASzhv%2FJisM%2FcnXblOJGNI59JKuAn0DRCMVv%2FAC3fr%2B44l6Mzsxej1e05rcYfmG1IMsttK0lPUbI280dM5Q8XOPG6rTMLZo5nNYWwpS6StiWn5TDLc2%2BlTDNpdhaeZCrcwBdQF7XvEnu55NuKSBiaWUntIlXNv5EVV5t5TqbEw3XWlJPJSJRa%2FwASdvXE99b99Wnn%2B4p0J0aq2YvRzU9pq3MjiLzezjoMnQcfVaXmpGWnDUpZmXpSJQpeKCgKOkki6DunvPmjWa0Pr6jjLnldUaT2b388dMozjyjBKRiBoWN%2F0Esb%2BpEV1ZuZWNi4rrDn2wEqu6e6%2FViO%2Bt%2B%2BrT17iNCNHJjPvxRzU9py%2FwBA4g6XGVJGrkU2Px%2FkgttxNwJd5Vh2IMdMKzxynbC0Cf1I7SJRZHr6sROfWUTVyK1Lt9cneUdBG3Z1Id9b99Wnn%2B5E6DaOTsxej1e25oB6M9dDl0p2skxWDS%2BkOtOhSbc0kKF46gwzxC5I03E9EqU7Vpd%2BVk59h55JkVkBAUNR0lFjYdkbtc4vOGMOrDNRln0pUSHEUQEG%2Fn6OO3hc29%2FoqqtqYs8p2TO18%2F0tudx0evNFhcbfumKozmqnZE57NUz6XzzWgg7uBXq3iPREfBJ9AvH0Dd4v%2BGEFXSTcoNXPXRgP%2FbiLHFzwsajpq9MbUoWUTSQL%2Bn3uOtGHVzsqjneQnGIj6Orr3OQOHzGWHMEZwYfxFimqJptJbTOykzOrQpSJcvybzKFqCQTp1rTew7YzDDriqLIYIkHeKbKycp2Am3DR6RN0iccky8rWC8%2B10Gl5wBRstW42PZHS6OK3hevqbq1H9IpKf6qKg4reGDbVV6V6qKk%2F%2B3G3Y3Kuyp1zE%2Fa5l%2BvcXuqKspp1ZbM%2FROzVMZuccb40w4jDWZFSquaeAK%2FV8WYVk8NU%2BQwjSn5O7qKgiYDrqC0hBATruq97WHZHPyxvawT6VcvSI%2Bh44reGBtsJbrNISF80ew6R8Y6OPMvil4V0e%2Bqq1ECrX%2FtQCr%2FRxFvdK7xlGcREedfD75RcLOaODVV%2FXofPpetoi6QARfs3ESLWT5CkqH76PoC5xYcKt%2BjcqdJO17Gigj%2FRxBPFlwoNA6atRE2uQBRUi5A%2Fvca04bVHzo52%2FwB%2BafJz%2FX2Pn6S2OZSP4QhrY0X6RH3Qjv4cWPCW8oFdQotyOaqEnbbv6OH1VvCgW7pmqKRa2n2DQPxtxMYbX40c535p8nPXufP1IbKrBaVdpSCL2ik50bcfRuo4ayL4j8DTsrRqRS1NBpxMlUKfKIYmpF8i6HEKSBex5pNwRcGPm3WOlkX35N5YUuVecYWRyKkLUgkekpjXvF0ru8RVMxMS3rnf6L3M0RGVUbYlVZqTMkpwuA2XtZPZERiSXA0LaUSOXnjBKhWplUwoMKKWwdIPf3kx41VScPlPq9W0arcbInsSNTqWAUqSWWyi6u3flG2Mr2J%2FFOR9fw3QaNTq%2FPtY9olZmaLNzyJcTcixLu9JqK1C6FEhB0m4Crxy8KnMj9PX8d4nVNuOJuolXpjJZV00V8KqM419cZMF5sqraz4NM5TqnmnPze12%2FMU%2FMjElbqNfzW4c6Pi0AIYw%2FJtYxZkpOhU9INpKXbbcN06tJ1%2BVtyjWmdUvUcJYPywwZXJNuQq9IkK45N0xM0iZMmh%2BfK2ElxBIUOjIAJNzp3jmkTTg6wsLRH2SmR5Lqh6I2K7xTVTMRE5zy6vNuaVjcLSztKapqjg08kROWyY5apiNuezWzh2oAuWVdO19olE8f1NXxE%2FEO0Rg5qs%2BD%2BiFRAVaoptaaWLcrGNN1Gb%2ByTbcTCpsufCMYMKpPD%2B6D8QiY1eoK5zjnqtAZx7IW8jeNl8PWePuF5lM4%2FXQE1llmSfk32ErDb7aXQB0rC1ApQ4kp5nsJjnv2Vnv1478cVfZyf0hK5pZA74Dr%2BuccGJJjMGpY7wflvgmkzE8dPjc3TOnqbrenSQ5NJUCCpNwVIANjzi%2FM4upeaeEE4iyO4fcq5qtyKCnE2DZqkF6oMqG4npJXSpM1LrB6ybdI2oEEEbxxD7LzKv7oPxRO3WJ1t1D7U4tp1s3Q42ooWg%2BZQsR6oDtisY2zE4dp%2FC2L8xeGvKOXaqvTLp6ZWmWfSUIGttV3FhpQDidSVoO1xHOOLsWSWK8S1DEUrh6kUFM86XfY6kMFmTYPI9G2SdINr2BtcmwHKMYxNm5mTjSmU6jYvxxVazJUm%2FiLU490gl7oCDpJF7lKUgkkk2EYymqTiVHTMKgM08fb74rt1FhKkpQndO4APMiMF9l579cq%2BIRKqqVA%2BTMr9VoDZ6MUNIZMv0bmgm5621%2FRERimU6B%2BXOsKdYLae7USO%2FstGrvZaoHqmZXt3xEVWeH90n1iA2Q3MNuNq31dURL0izyMWDDtUE%2BlTDwSl1sXKhey09%2FmMX0dXlATalw1K7Ykurthc3gJirVtvvEUtovpWuxiQX8pKheCtQ3JEBf2q1KpShGhZUEgEWFto9NPrEvJTDMw2halJUCpJsLg8yPPvFgRKTKkBfi6yk9oBMTdBNJVpMq4D3FBvAbf4b0Y%2BcxvVhl9VKJJzfsDNCfTVJF%2BaRNSZcZC20NS5D5XqLartm4CVE7XjuUUzjn63%2FCflF%2FEtQO4H7%2FAL4%2BemT%2BWFezaxJN0jD9Yl6bNUqmvVQvLD5XoQtCClsMAuFRLovYeTqJ2EdCHgDzr8hGZlIV%2B9n58ens3EBsjOJni1lsJVd3F2Nstp4S%2BHK1NK8SpNSb1SQYSmbZS4SWUvLbUAgO87HTuDHPPCDmdgvLzG1XoeP5kSeHsbUcUOYnVLU2mVd1Etla0nU2hWtaOkHkKKT5xd8c8GWcWCMOVCtVLMGQm2pGlztWflW5moFD7EqhKnEFZHQhZSoaUrI1WNu2NCUHDuI8YVRug4Vw9PVifmAQ3KSbJccUO24HId5O0B9FcMZO4ioGIKbVMzM1ZbFWA8BBT%2BCBUHEB1C1A6Ziou%2BQ%2B4wg9G04Cdusd4444ss1qHmxm%2FPVrDr6ZqkU2WZpUhNgECaS3creF99KlqVbzAGNZ4rw7izBFSdwNjGQqlJnKdoU7SZt5dpcrSFJs3qKRdJB22ixL5iAjfc2jrnLOxy8wuFrNk0pm21rm55n0RyGj9N8qOzMrUsoyzwwpaQU%2Bxbd%2FjMWs5ytIjzT7lLePxE%2BmPeztiSCZVgoAAUjTcgeof64k6EyzulsFISAoK7Fkdnmj04fmmpmWQkt62QglKVp6yjyO0VHrM3ZWdK3bqHba29vX3%2BmN5yZqmJyeFxZbWkr06PJ897bRRccb8fQWfekaRp5C%2FpAi8yuH6lXW2ZWSYDU64sBtDjidBJ71HlGKY3RL4RrD9LrmLaK4ZNLSlNyUwHukDoNyCkEK0kWUAQU3HMGLUxM7FZmMs5e2ozQSHOjcTqUAnq7EA9seZZl3G1L6T33T1VJVzt2ee%2FfFrRW8BzUpMTreP6V0so0FiXnA4y4%2FZNyloqFlHsAJF7i0ebFlPrGDZ4MVLxR9icYbm5abk5pExLPtLvp0uJNtQsbpO%2FLncRMxrylanXGcL2zUJdDSnZpNwls6lX3vyvFgqeOZCmthTaSnUrqrCbG1rEj44xJ%2FEbrij0i7ApBJB3%2F%2FADGITlbemZcMOKDvUVpJA5dhi35rJk9mYeMZirSrjLU2pTOkFSU76U2PP0fljVtFqTrTSUqdSS2dhYEc%2B6Mun1teLOvPNL6FtlxboQkAqNja3p2%2BKNeyyVMNoCjqO17RS1rmZjNlu9MRE%2Bdg2YVSmGcVz7cpMLaS4gAhs6AAoDUAByBI3748FZUyWKb0aEovT2QqwtdQvcxTxy70uKp1Xc2iIV5Jb9jU2IBp8uRc35pvGhP50ujT%2BbD3YdqdapU01MUetT8i82Qpt2WmVtrbINwUqBBHIfFE2K8TYkqE85Wp%2FEFSmanNOrdmJ56bWp95w2utaybqUe0mPJSli6Y89e8kemKyStLlQqMy5qmKjNuq71vrP5YqJdmAmwm5gDuD6%2Fnjwg2N4qhwxCHp8Yfb6yZt5J7w6q%2F44qCqz42FRm7fa9Msj8ceHpYgFEwGc1PMfF89gKiYEqdW8YolNqszU6chbYL0s84gJdQl3yujVsdBNgrcRk2Esx8Z4FlFO4HxyqnCpMtmcS1Jsu6ikkhCumQvySTum3PtjVVTnzL0GSZRLMLWtx%2F31y6lJFx5IvYfFHtlJo%2BIMOW%2FSxAbZmeJPOoEqOZc1cm5IpcgLn1MR5HeJrOtwFKsypyxte1NkU3ty5Mxqh6ZQ4T2GKJWO%2BA2ueJLOm2kZmVEDuErKD%2F2Y9DfFJny0fe82q0kW02S1LAAd32KNPdL6IdL5xAbld4ps9ZhRVMZr1pd7XuzKnst%2BoxR%2BqSzdIVqzMq3WGknxeUvb7zGoOl84h0vogNwscSearYN80Kwm%2FP8zSh%2F9mKrnEzmq6nQvNOrlPd4nKD%2FANmNKlVzuYa%2FNAbmXxKZquK1KzTrZNrX6CV%2FqYmHElm2Qke6zXgE8rty%2FwDVRprX5oa%2FNAbjHERmmtsNOZv1wJBKrFtg7%2Feol%2BqCzMKSheb%2BIFAm9rM%2F1caf1GJ0dYXtAbd93vMVwaV5q4hI9DA%2F9uBz6zIA0jNPEAT5xLn%2FANqNSWhpMBtpefOZDv2TNqvq9IZ%2Fq4irPjMVY0qzXrpH7yX%2FAKuNRnlFI84Db7meGN3EaHMzq%2BpN72tLc%2FvcFZ7Y4XbXmZiI2Fh%2Bhv6qNQDaKgWRAbdGeuO3raszsTG3K5lzb%2FNxM7nfjtRK3M0sQG3VJvLG3mPvcalaLimnbLt72qOv%2BPrDeGaMjJyZouHpCmTM5lzTFTipSWQyX1i%2FXc0ga1%2FujvAaaOdeLlIDTmadeUgG4Fpcb%2FeonXndi1dtWZ2JFW5WVL%2F1UahhAbeczrxU5bVmhio25avFzb%2FNxTfzmxNMqK3808TqURpJ94uR3eRGpYQG22c4cQtJCG82MTISnyQUMED%2BRtB7NWszFy9m5iIgkqI0MgXPmCI1JEQkk2gNonMKYPVVmxiIp86W7%2FzImczIm1gpGb2K7EWNlhII9QjV4YJiRbakmA2gMcKVcrzbxUdXOz1vyRIcWyavKzYxTtsPfze0auiSA2onElAKD0%2Ba%2BKAe7pF7j0iIpq%2BDl6Q5m1iUX5klZA9V41XY84DnAbdFRwkUEpznrWrsBcdH5IjLTuF30KLmddVl1DkHJl0X%2BJMamG1oqBzsgNqsVWkLXpazwqzKftzPvIHyJiv4%2FS79GrPOrqTe101R4j07CNShzaKjRuq8BtcTlNcGk56VkDuVUX9vkirLHDTrw9ls2q1NMWspTNTdJt6DGrEpBG8e5tDfRp6kB0uvAnDM3hyXrdF4m8Tzc4sJD0g7JvoeYUQd9wQQCLE37Y0ziCYR7NtYWGIHMT0iqPIYYfmGNExLPLOlCgoC9wojccwTHnoqGzTFEeVqi3tpLmMMOICgCarKWJ7Pf0QFkelZmnTE9TJxGiYk31yzye5xtRQofGDEcCke2amj%2FwCtY%2F0gjMMV0Wm1DHWIpCjViScm5qrzqm2lTKbqPjDh0XNrEefnGJYMln5THNOk5hoNOt1NhC0A3sekEB%2BlWEIQCEIQCEIQCEIQCEIQH53%2BI9Ns3sdt%2FwD7T1T5Jt6NQu7yyPSVRuHiT2zkx%2Be7FFV%2BWcfjTzn6DSrzqH4oDK8Mf2sv5xFyWm8W7C39qPPqH5YuZHbAUiYgTE%2Bi5IiGjYmAkJgryYHsgeW8BLEUxEERMCICMdB8OnDTTc06C9jXG9TnpSi%2BNLlJGWkCA9NLbt0i1KOyEAkDa5Jv3Rz6ki8d68Psx4nwlylSRqbXKU6suhSTY60hxQI897R4T4QcUvuGYZZ9w1cGq0riiZ5YjKZnLz6svQ6WF2VFpbTVaRnFMTLxfUicP5ASJushRNiDVR1T5xpgjhByHKSkT1XOnmfZVNx%2FJjkfAkth3FGGa%2FO1PEUrh4TVGkaAp6fampl56qFQmXZtotXCTpb0K1fb8oyao0LBVTma23Tc0ZFs1R2lraDdLqKxKplEaVBO3N1XWVf5I5VWimL0zNMYjaz5%2BDVPg%2Fe8%2FU2u%2BdU08L4ujmpzdKDg8yPCivxqs6jyHsmm489tMTfUf5JWsHq7Y8z7Jbfzdo5XxNhDDNXxJUq57uE5LKqE45NeLyNLqCGmdRJ0IHYBe0W6XwLh9b6nVcQNRaSlXVYfk5%2B6we3ntFJ0TxnV%2BUrXP%2BGr3VlOIzyUWfNG510eDzJNRKNNe1DnqqY%2Bj%2BWIJ4QcimwTrqx9NXTt%2FJjmGew3T602yxM8QRSWKYxTEhqQnkFYbOrpNj1nTaxJ53jHJzH0wifnKonM%2BsMzU1WFVRXR0NaB0%2FRdGDo1206eSd0jsivFHGZ1Tidr0a%2B0mcRqjLOzs%2FV3OwBwfZILNgqsKKTpP57JsPMbJidPB7kgo3CKwvVe2mr%2FADCOIma%2FLMsGUZzWxMhlUm5IqSac6SWVudIpPl3uV76vKA2vaJpjEGtDj5zQxM8pxTSyBJPoAU2NKCLObWGxtztveMkaG4tMa8TteartHfKY2WdHq7nbY4QcjiQQmt9Xs9lDb%2BbD6j7I0DnWjbsNWI%2BW0cszmFKRKudBKcTdQfSlQ8mVqCLhW6lEX2323jyu4Vwql51tPEVW3myQC4mnVA6u86SoHntz35xTidi%2BX6ztujV2004jVM6rOz6tzrJPCBkcANaKqdO%2Br2TOw8%2FV3iqOEbJcXCWqvdQ1XFRAsPN1bgeeOSZKh4blZdxv3f6sbr8j2OqG49S9vliR7DuDlalPcQWIJpYOlltEjULqv2C6torGiOL07cStujV21oxGrP5Ozjm7LrccIWTI62qt2PYagFD49MQXwiZJjylVpP8AlAD%2BjHIowjh8rQpGeWJ5QJ2JNLqXVP3UU3cLYcIKpjPqvdItYSQ5TagLjtJJV8kWjRDFp24nbdGrtlWIVeTs%2BrsuvRwiZI9pq59NSH0Yj9SHkdflVf40H0Y5KGX%2BD1klOf8AVlADUUokZ0LIG50gr6xtyHabRgHSUZ1x5SsycWobS6sMpVJv61ov1SqzpCTbmN94mNEMWjbidr0au2icQqmOFwLPqz9jvdHCDkgDdRrNu4VNP0YiOEPI0ndurj%2FKf%2BzHBaPECBpzSxekWNx4rMXI7j75yiT8xISFJzJxi4e1JZeH%2FuRM6IYvOzErXmq7ZTiNVWr4ujq3O%2BTwhZHqbCGpesBQN9Qqe59N0xH6kHJVW5TXDcWSRU%2BXqCY5EVl9hGXWp6W4ia44S2nS4mlziVKUQLp3c7Dcee0SMYBwc7Nty7nETiNpoWHjBpk7oRtc7a789oidEcXjZiVr0au0mMRz%2BZZ9XZdc%2FUdZLatXT16xPL2T2t3eTE%2F1HmSXIKrx%2FwAqp%2BjHIPtHwYhtXR5%2B4t63NKqXNi5HImzkVG8J5dstFRzuxcp8HqBmRm7rWTtp98iOKeMf4ja9Grto7tiZymiz6tzrZzhDyMa5qrd%2F%2FN02%2Fmw%2BpGyL8rxmrW7vZZP0Y4%2FmsAYcS44uZzSxvLKJuUPUWbCr95BXtzjxuYCwclWtzN3FiE%2FbuUd9P43ItGieLTGffG15qu0mb%2FXEfm2fV2XZq%2BEjIoDrGrC%2Fb7Lcv5MUhwkZCA3LtZJ89YH0Y5ElsCYCcTZeemJ1tkdZAkXUHz7FyMMUnCRmHUIxvjpKAs6QZbraATzs9YG1ojiji8%2F3ja5eirtp7sqqjZZerud4J4RshAvUv2X%2FAIVXAH82Iq4RciFKul%2BtDzezN%2F6McIdDg9zysd48T6ZW%2FwD7sQcl8NNAdBjjG7hCxb3rSLX3P2XnEcUcX298rXmq7avdlccll6u53keETIxQsXq0f8r%2FAOzEPqQMi%2BfSVm3%2FAJsPoxyE9gHLxqZcQ3nxi55pJslwU54FQ77dJcRK9hbAEslUtKZy45daULuWklhK%2FNYubQ4pYtEasRtuartIi%2B1TOqLL1ey6%2FwDqQsih%2BmVn%2BN%2F9mIjhEyLKQkPVhQve3sqDb40xxunCWXbmy81ccADsEmq%2F%2Bkj0S%2BEst3U9GvHeNyT5IRKrWpZ7gA5CNE8XjXGIW3NPbZYvdXLFl1dl2AOEjITa6qobdnsqLfFaJfqRchft6n%2FGg%2BjHH68vcFN3TM40zBYA%2BCqmPC3puvaPO7gjLxtelWPsfNJ%2B3ckFpT8ZchxWxXlxC25p7ae7J%2FyursuyvqRMhwQUuVUd49k02Pxp2h9SPkQBbpKtvzPsqnb0dWOPZPA2XUy822vNfGZUT9iSwvURzNj0lr2%2BWMHcVh0uurYxHjfo9aujQXkFSUA7aiHLXtztE06J4tVsxC25p7bFN8q2xFlPN2XfJ4R8iyd5qrn%2FACon6MDwiZGrKdM3WEgc7VJG%2FwAaY4ICKL%2B2bG339H9ZEqmZHSeixFjJZ7CqaSm3%2Bci8aIYxP95WvNPbV74WlO2mz6tzvlXCDkTcgTtYF%2F8AvRG38mJfqP8AIXZK52sq1K1XNTTceYWG8cgrwdlczMKQ%2Fmtj1ZCrEpkVAjv2Lt9opKwllkEJW3mTmCpztBldNh6ekjHxUxbPKcQtuae0yTfap5LLq7LsM8IGQl956rj%2FACmn5olVwicP%2FwAOpVX11VI%2FEmOQfa5lG3svF%2BOHOt5a2t%2FSR0kUvahlQ4slWOseIB7BLXt%2FLi1Oi2Lx%2B323NPbU7sq8FnzR2XX44TeHhpQK6xVRbygurNjV%2FJ2jG8ccGODl4cnKjlxiKoioy7C5hhqbWmYZmNAJ6O6QCkq5BW4jkTMLAlHouGafjHCdWxHUqRM1N6jzMxUk9CGptDSHktpso3JbXqvy2jurgdaffyBkHJl1x1ZFRWhTiyqyEvAJAv3bxz8XsMX0asaL5Z36uueFEZVRq15%2BGZ8GX27WWxrpvVc0WlFExEZ5xHo80OESSTugoPIpPYe0fHGX5T5cVXNfHMhgmlzDcr4ylx%2BamnElSZaWbF3HLDmQLADtJEYtNEKn5kp5eMvW9HSKjoPgdbDmck2k8hh%2BbPr1ItH0PSTELbDcJtr3d9VcU6vNM8v2ORcrGm1t6aKtcZtrMcHuRlOQ3LVOv196YKRqcdnmmQsjtCbbA%2BuKo4RuH42DFeq3SJOo6Kq2o3%2B5jQnF5Q3Mb8TEthuYrfsXLN4dYmHZxSXHGpRltpxxxxSEb7mwuB2iNZjKHCzSA6nPaXCza4akJq9j548JhmB4xidzsr5XiNpE1xE5REzln6Jh0ba%2B1WdpNNNFGXnyz9js1PB1kY8Atmq1pSfhD2TRufQExP8AUZ5JqVfx%2Bu27k1JH0Y44lcv8C08uiZzoEwv4OiWnW%2FkSYg9g3DUxMtN03P5Uo2pO%2BpE95XmuY3OKmL1TwYxG15p7SsX%2FAD202f8AX%2B3J2P8AUY5Lk6BOVxR7hUEE%2FwA2H1F2TSBqXM1%2B3eagj6McfM5eyvTA%2FVMPAjktaZzb0G94x%2FFNNbw9VnaQ9njXpxbQbUp5MtOFtRUAq6Fa9wARvYRE6I41%2FiVp0au0rOJcGfk6OaOy7h%2Bozya5Ccr38YI%2BjEfqMsmVADxuuggW2qKPj8mOCUPS6l3OctfPnEtPX%2FnxV8cDKitjOfEgIF9peeTf%2BXCNEcaj%2B87Toz2jvr%2FlUc0dl3gODTJS%2Bn2SrOru9kUfNEU8GGTWqyZyvLCd7Jnm%2FoxxvQcKKrFIl6wriOm5JL6nEmXfRPhxGk2uRc8%2BY3i5u4KlvF2y5xUP616itu1Q97ty37b%2BaInRLG41xiVp0at5TiNUzqs7Pq7LrU8GOTquU7iIHzTiLfzYingwyfP%2FADjiFPn8bbH9GOP04TaCTq4oXQo%2BSkCoX9J7ory%2BHJSVshziWmXQT9lT7IWR3A7jz9hitWimO5asStOjO9kjEJ5bOz6tzrhXBflGqyUVPEbaO0%2BOtG%2Fr0%2FJD6i7KBH%2FOeIbnkTOtcvRpjj%2Bdo1KffLiOJKbQsiyj0dQVe3be9opGgS6LITxMTbd%2BYU3UN%2FReJp0TxyduJWnRneTf45KLPq7LsccGOT42NUxCRzsZ1r6ESr4McnVeTU8QJP8A49r6Mcgt4NU4duJmaAKbgq8eT1u43O0Y1iZh2g1lVNlM%2BMR1FLLaelmGJac6MuHykoJX1kjbrbXi3FPHM%2F1ladGd6s4lMfR0erudxt8FuT4CkuVTEbhHYJ9q%2FwDNiJ4K8oCoEVTEQT2pE63%2BPTeOCzUJwpCPdqxZZIsB4vOcr3%2B3gmdm%2FhZ0Yr9TE39OJ4p45%2FidpzTvR3xidtnRzRud6HgvyfTzqWJUjtInGzt60xMeCvJ9StRqeJvR4%2B2B%2FMjjSjYTm6nR2KqeIaqyq3SoCWmUTqXUAKtcjVYA8xvFV3B%2BlRC%2BJeeChcaUpniRYc%2BdvlieKmOR%2FeVp0Z3nfCPJ0dXZdjDgsykSQU1fEuwsAqebP9CCOCzKMqK11bEiyb3JnWjf%2BTHHKMJp%2FwD7m5%2Fq%2BTdE7b03vFzZwtRQjoJviWnJkDk4lE8pIPaAAQfXFKtF8cj%2B8bTozvZKb9TPzKOrc61%2Bonygtq9lcRW7%2FHWvoxD6ijJ79lsQ%2FhrX0Y44qVEpfSEy%2FERVGk2soBioaQfNvHkTQ5Rd78SdUCLhILjM%2FY%2FGYtTotjkx%2BsrTozvJxCI%2BbRzR2XaaeCvJ0AE1PEBB5Hx5ux9emJjwZZMq8qdxF%2BGN%2FRjjprAi3wGlcSM02NN7HxzSPN5UWGtyqKDU1Uw5%2FYjeUykB51EpPdH0nchQV1k2%2BFYRbirjfLiVp0Z3qziPgs6Orsu4RwY5MAk%2ByeIkg9njjZt%2FJiH1F%2BToOpNTxEBz%2FRjXx%2BTHBxmkqGg554oPVP8Acc9b0eXEPe7WTnRiNItawkp36UOKmN8mJWnRnepOJz5Kjmjsu9E8GOTqb3quI13OreebFh6kw%2BowycNrVXEBJ5fmtv6McXU%2FB87NSMjVGuIKosonGek6N7x1DjBClJ0rTfY9W%2B1xYiKwwrOynRu%2FVITyFNqukNePKKD2EWNh6YjitjcTrxK06M7ycSnZFnRzR2XZA4LMohfRVsR%2Ba842bfyYqDgryd0jXVcRKNzf82oH9GOMva1MoKmU8SU%2FpJ5ATwSfTvePTLYcpqW7Tef8%2B4onrnRPnc8yOuLxE6K43t75WnRntL04hHLZ0dXZdhp4L8mwetVsQq%2Fxxv6MQXwY5McjU8Q%2Fhrf0Y4wmaBSVuAyefs82yUiyujn76u0W1GPK7huWCgo8QU1dI5lM%2Fse7cwjRPG5%2FvK06M9onEPBRZ80dl2yeDHJIiyajXgQDzqCN%2FwCRtBPBhkp0elFTr1yb6hPt%2FRjjFGAG1tKfb4g5hCkpubCc1E9o8rl54tNfpicMVOcovu8V1apQI1LlpWe6NaynVZPW3FiOtaxieKGM8uJ2nRntHfCrkos%2Brc7kTwW5MpN1VnEJ57Gdb7f4EDwZ5LlIKa1XjbkBOtb%2Bm6Y4HWFu3LmdOInAVAlSpWdsT38%2FlgqXaslK85awsIN0hcvO9XfsuraMlOieMcuJ2nRntKTiFXk7Pq3O91cGWShWNdYxEO782tc%2B89WJzwa5J6LKq9fuRYkz7Yue%2FwAmOJpLAyKhTJeojiB8W8ZZU4ph9M6h9lWsjQ4nkCQAoWJBChEzuBGChDT3EKh5CUnSlaZyyfNaE6KYv%2FiVp0Z7SvfCfJ2fVudo%2FUb5FH%2Fnqsp%2Fe1Jv8dt4kVwb5Dg6vbBWU6%2Bw1Jq3q2jjOVy%2FwfKnQvN5p1XlKUGJwWPxx5pnLXDjzi1yuc0s0g2snoJsj8cRToti2eU4ha809pab7OWfAs%2Brc7T%2BpC4edwvE9UQT8H2UauPURFCa4MsmZ%2BUcTh%2FFNdS%2BdSW30zTL6G1gbFSQNx3i42jiHEGVTcphusYoo%2BYMvW3KC0xNTUs0l9L3QOvBkuJKuYSop1dwUI354OZM8vFeNE%2BNPKl2paSc6Iuko1qeKSqx7Sm4vHOxjCsVwa42l9oxC0maNeUx54jlmfD4GS72sW9rTRVRTlPgiNzUGO8FVfLrGVVwVXFtOTdJe6FTrQIbeSQFIcSDvZSSDFolJSZn5uXkJJlTszNPIl2W081uLUEpHrJEbl4yG0t8Q2IGkIADUrIN3A52ZIBPqt8UYJlchv3TMFhwXQcRU%2FUO%2FwB%2BTHvbriVvOCUX%2B1j8Z8XFU%2BDhcHOetzosqZvXxXJm6jw%2FwT5eUejNnMTFdWfqRSgTbkq%2B3KyjLvMtoKgSqx21G17G0e0cIvDsvqpxzVU9v9t2Pi5RZPCOTj8vl1QZFkuqM5iFYLbZPvqky5UlJAO%2FWUPXHJ1SySoFLqDkjO5wUcTMsotvgS0z724B1k8huDsbx880dueM6Q3KL%2FbX%2B0pmqZ1Uxq1TyZbPQ6t6tbOytZos6KYiPDludpHg%2FwAgXFdInFlXWFfqdWa0n5IDg1yGuL4irhPbeqN%2FRjiqUy%2BwFJrCZ7N5l5vQSUsSs0NK%2BzYRVmMIYJeTeSzYXKOk6gpxE4L9lr32jr1aNYvH5uIWvR%2F7MUXuPBZ80bnaY4OchBe1crJJ2%2Fti380FcGWRStVq9XRvfq1Jof0Y4sVlhQLKKM8mVkC4CWJvfl3n0%2FFE1by%2FoNBpclUZjOuoTPjsw42PFJGadS0G0AqKzrFiVKSEje4udrRWdGsZjX3xtOjVvRN7%2Fcs%2Brc7QHBxkYEa0V6vBQN7GoN7ebyYqDg2yPULprVe3uSBUmrjccrp5RwailUNQcBzPrigshX9r5o3I5E%2B%2BRFFHoiVBac06%2BhQSUgpkJoEA8x9k5GFOjWMzr75WvRneib74aKOaNzvEcGmSF%2BvXa4U9mmpM%2FjCYK4MMkh5Nbr38Ytn8kcQ0HBGHaoZxCc5qhTlSwQfzRIzSA9qNuqQre3M3tFyOWOHGWnnns%2FnkrQkFoIlJtQcPaAQrY%2BmLcWsZq%2FvG16M70xe8%2FmWfVudnJ4MsltIBq9eJB3V4%2B3y%2B5iC%2BDHJZVv7IK8m3O88yb%2BnqxxecCYdQXEIz9qxQo72kpvrDzjVFaTwbgZl94TedNQnUp%2BxpckpxvVbtF1c4idGcajX3wtejO8i9TVOXBs%2Brc7KVwX5KNhLYruIVX3JE%2B0D%2FADYfUZZI9uIMQcrb1Bnn9zHHU9gnA7xApWbFYBT9kW1T50gH7XyyO6PKnANCUm6c38Q6rXI9i57Yd560RGjeMTrnEbWP9s71arxEfNo%2Fr%2Fa7UPBvkoG1tez1eAXz%2FPBr6MS%2FUa5Jk2VWK8fRUGh%2FRji5eX%2BGJhZ6TPGpG6gklcjNg7CwNiu8efE%2BCsNYblZJ2XzexHUn5110K8WkJgNtNoAtdZd3UVHZI7NzaJjRrGZ%2FvG06M70xe55KbPq3O2l8GWSKkpJqmIBp3uKi0L%2FyYHg1yUKQBWK%2BPOKg1v8AyY4EMlTynScx8VHa28o9a3o6WJm5aSZIDeYmLAAbgplnk2P32InRjGuTErTozvRF8qz%2FADbPq3O%2BBwaZKqSEisYgJ%2B29kGrn%2BTE31GGTHSBz2XxDYC2jx9qx9em4jiPDOG6NiFE27N5tYqp7UoW20Ovy7yg6pdzoSEubWAvv3xeF4Gws0ga898TadiNElMKNxz26TaK8WsejZiNp0fvW7qz202fVudhq4KsmVA2reJGiTe6ai2fj6kRHBVksqxVWMSKF%2Bfsg19GOMl4RwinSk52YwWL3NpB5O33zePXJYZwKgL6TNzF6tth4q8AT6Okis6O47H94Ws%2F7Z3rReafFs%2BeNzsFfBTkqNjWcRJ%2Fx9r6MRHBVksNxWMQD%2FKDX0Y5C9pOGqi0FUzH%2BYD6WwOlVLUuYdsT2XC7R5jl7ShdDuN8yDqt1TSpi59PXisaOY5O3ELTo%2FwDZE3nwU2fVudkngqyZXzreIgfNPNA%2Fzd4h9RXkzyFbxL%2BGtfRjjP2oYN1hQzkxelaBb3yVeQpJ7t3LxQxHh%2FCFBkKZNyGauPKiqol%2B70syeiR0RAUglT19dzfla3bFo0bx3kxC06M9paLaJ202fPG52mOC7JkCxqeIT%2B6M83%2BLTFP6ivJkn%2B3eI%2Fw1v6McJh3Dyx1sdZiKT5%2Br8nTRFpzDlhrxxmQgk2ISUmw7%2Fs0J0ax3%2FEbTo%2F8AZE23gps%2BeNzus8FGTpFhXcRj90Jxr8WmIo4JsoCAEV7ERAN7eNtG%2FwDJjimi0vC9Wl5p5%2FNDH8kWXEIa6bk6CCTuHTYjbbzxcjQMIMrujN%2FH9reUnVe%2F3yJ4uY%2FlnGIWnQ%2F7Ji8URtps%2BeNzsL6iTKLVc17EZ3vYTLXL7mIjghyjBv7M4kV3hU00PxJjjk0fBgJIzazHVvcDrA3%2B%2BxUZkMEJUrpsysxnBbmpw3Hp98hGj2Pf4hadH%2Fsnuiz8Sz543OwBwRZQNps5WsRk95nGx%2FRiVXBPk1%2BzmIx%2FjrX0Y5HXhvDVTbSul4pzUnmULKFOMIWpu%2FcLLNjFNvBkg9pBxDmsSokW6JZPq60Txcx6dffG06P%2FAGVm8UclNn1dl2CeCvJrpFlNVxGCo6gPHG7D%2BTEv1FGUJUT7O4j0nkPG2tv5MccpoODQoJms0swJMoBC0vFQKCAerbXcdnPvijian4VoErSDI47zDnnagy9MOuonUoaQEuFCUJ691K2uTyFwIRo3jvLiNr0f%2ByO6afFs%2Brsuy18EOUmyPZzEiVDvmmrn%2BTEVcEmUKhb2bxGFd4mmvxaY4abqcgg3GKsx0m1rpqqN%2FN9kiCqvLoVqbxXmKbdnsqkE%2BvXFo0cx3PKcQtOj%2FwBlIvUT8yz6tzuT6h7KjSlXtjxJYdvjDW%2Fp6kTfUP5UKTpOIcTAE%2FBmmuX3Ecc4XlqPWJOamq1mFmPJBLiUSwRUQ6HE26xPX2sdovjdDwWlSbZoZm6QLkpnbH%2BfDi7j0f3hadH71otqJ%2BbZ8%2F8A1dT%2FAFDOVA54ixV65pr6ERTwOZTH%2FpDigemYa%2BhHK4puBQ4tcxjXM6aO6klyoJvc8%2Fh84kmKbgOb6zeLc0GDptp9kkG57N9cRGjuP568QtOjHaJtrPwUf1%2FtdWq4IcnGhZ6vYkBUOqTMtC3o6seab4JMoHEFEvifEqXLbAPsL37yNO8cy0XL3DuLKkzhfDuOMx1VefamEU3xidSWVTKWHHG0KCV30qUgAkd8ScEuMcVVnPGnUqZr0%2FOSD9NnH5tiYmlqSktt3StNzsQr47mNe%2BYLjVyu1pepxG0zoiZymmNeUZ%2BFawtabW0pspoo1zyZbluzgyrrOT2NXcIVeZRONuy6Z6nzzbZQmZllqUkEp%2BCtKklKk9hFxsYweOouP5pLOP8ABBTbU7hdTqj3kzMcuntj3GjN%2Bt8SwmwvV5%2FPqjX58pmM%2Ftycq9WcWdtVTRGqEoNovcxjfF85heQwPOYmqb%2BHaW8uYkaU5MFUtLOLvqUhHYSVKPmubWvFiPOJ08o7rXXqj4uxXQKbVqNQsRVGQp1eZEvVZOXfKGZ5oCwS6nkoW29BtGwOGzN6kZL5sSuOMQUaaqFMFOm6fMNSih06A9os4gGwUQUAEXGyj3RsrIPhDoeNcvms282cVu0PDk2y5MyjLKksqXKpOkTLrq9m0KIOkcyN%2B0Rg3Edl3ktgWj4arWSmOfbExUvH01EGfbmAwpkI0HqAKRfUq4I7Nj2QGu8d4o9uOOcQY1aYXKKrdYmaqhtLnWY6R0rQAoW3SLbjtEeTEmKsTYxqasQYvxBUK3VXGW2Fzk88XXVNtiyEXPwUgmw85743Xn5w8YMypyky%2FwAf4aqtXmJ%2FFS2kT7M6ptTKdch05LWkBQIXcWJPVjJcuOGnKKUyZpudWfWM6jSadW0tPSjcgrQ1LNOrKWulWELUpSilRsBYC2%2FOA5wnsZYvq9BpeFaxiipz9FoRUaZT5h8rYk7ixDaezYkeYGwhIYtxVTKDUcKUzEtTk6JWXEO1KmsTBRLzi0W0KcRyJFh3XsL3tGQ5p4cwBI5kOUPJSuTOKcOzyJFNKfUrW87MvpAUwSEpuQ4bchsRHS7HB1kxlvhWWqHEDmYKfU5tYbKWpxuUlmnbdZltRBW6UnZSrAXEBpnhXz4ofD5mJUMWYjoVSqtPqNJEj0cgUdK26l9DqFWWQCk6NJ32vfeNUTNVmX629iKUdekZtypTFUZXLulK5Z1cwp5BQsbhSCobjtEbCxXlBIzWfU3k%2FlBVBiKSm6izL0SeU%2BhwOS7jKHVPLcR1SlsFd1D7XvjopfBpw54Zfp2Fcd5uzjeKKgAhkCfl5QvuK5dFLrBNvtdZGqA4zxNiPEmMqxM4ixhX56t1acCUzE9POdI86lI0pCjsLAbAAAeaJK9jLGOKKfSKLiXFlWq0hh6VMnSJecmC4iQY2HRtX5CyUje5skC9gI2RxFZA1vILEclTJ2pirUWspfco9UDPRLd6IpDrDze%2Bh5AUkkA2UCFDtA1AuApnmYlA3vEV9sTIG3OAAWiMIQAm0AbxKqIpgJiFeqJCRE9ydrxLpEBEcokiflEkBPaJCnzRPEdt7wFHQ4T1TYRA6%2B%2B5MVFJJHOKZHPSecBKj8fxemI9IUedX23ZDdHOIc%2BvAVEuGxN%2ByNzcIWn3dZZ4%2BUxhLFTyDbbUKPMCx9RPxRpVHkxsnh3x3hXLXNiRxdjf2R9hBSavS5lVOZDsy345JOy6XEoJAVpLlyLwGucMuJak6W4vyUy7ZP3IjJ26nL9Vvp%2FgjrbW5c9uYjNWMPcIcihthvM7NTom2kttq9q8v1bJtvZ7fkIyXBWV3C1jhFfk6PmZmf4xhvDk9ieccew3LNgycqEl0IBd6y%2Bumw7e%2BA1BUnG36U6UODpUvNWR9sk31H1bRnGSVm8E59uKSSPcycRYG3lVOU%2BaJm6TwoPoQt3MnNphZB1A4VliVDstZ6wMZThaucK2CaVjWiU%2FH%2BZ0%2B1jjDntbmXXcMMp8VR4y1MB9IDvWILWjTtssm%2B0BpOkzbDbDofVpV5SVJUL37LiPT7IS%2FX%2FNSezyT57%2FAI4zpmkcJ6ylL2Z%2BazbZBUE%2B1GXJbWbblXTdYbcolFI4T1IQBmfmmhRVZwqwjLmw70gPfjvAWrL9jEdVzgw1I4Bxo1hauT003KydfcfSwinBbSulcK1bA9H0iQPhFQT2xuTjLpxwZhrLvKjDbkvP4GwxMT65CrTFbbn6lVqm6kKmJl9KFEsNkKUUpPNRPKwjWM1hzhGfbDZzXzLW24LKZXg5ohHr6axEX7AOUPDFjiszNDw9m9jhE7K0mdq7y3cHobvKSbKnn7HpDuEJNh32HbAapE%2Bn9X%2BWJhMbrLrgOptQF1d42jM0UPhSdbaU3nJmE1r3Ut3BibAeYB3eKsxR%2BElCymXzgzLUE263tMRZXou8OUBt7gVxXlRgiqyc1O47kKLmLiLEUtTWW6hJuKbTRmx0jjDT32Nt2ZWAgrURpCbdsYNlQzSJfjmwsxhupN1GnDMiZXLzTaVJQ4hSn1kDVv1dSk3PPTcbERi%2Fte4T30kPZ34%2BOxAQME3PmNuk7YyfKur8LeWWZWE8yGs2sbzy8KVVupIkXMHKbEwEoUnRrDh031c7H0QEnDGy0qdxuhRsjxnc%2BYLmDGl8XUerY34h5%2FClLZmXHqviBqU6OWWkOlFk6ykqISCEJUesQNt43PwvEOKxrNpHVecS6lKj5IWp5QHxKtGtsMtr%2BrEb6NIUoVqd2Ive0qvaPPXWPytbzy5R7n1vGpmjQK4T%2B%2F8A%2FwCjKJWi5Z4ZkXaBKYGbryEz82%2BmrVaZWJt9hSgGG1IQejQEJTc6b6lLVvYCPNPUzLOdnKfMTeWEuw3IzfjK2pCqvNJnW9Niw7e5Sm9lBSdxuO3aabjL8CZS1TGmH5%2FGU7ibDuFsNU2YTJv1ivz4lJYzKk6gyhRBK123sBttHfyjlfJomZ5WJKomViyCcq5ZLi7cqzMad%2FNz%2BKL4jK7C8thuvVt7Juak%2FY%2BkzUyl%2BZdnNDDiUjQ4QpICgCb2JANxGbU3LXLuiByvfVFZXTQpjL8yEytYK3VuIaUpKUp0bqKgkJ85Ecu13NHMBFKZk8Q5gYuqErOIs5LTdZmH0KBsSlxClaVdmxFtojKPAnOfCtE7W5JtKGl0GlsqPWKmUuC%2FqK7RbpiqyTrxmGpiclVK5olrIQPVcxZ6pUm55xDsqFAEWNxyMeYrIHOJjgwrwpZUjFk4htLbU2%2F1fhdE2FH1gxnmVuLapVcSSNOmqVRas3O1KVl1t1GQU6tYKko6JKm1pUkKCrG29yLRomb6QmMmwriyTodKVKKQ%2BJlbxc1geTa1rEbg%2BfsiZiDOXT2I8P0eiTU27U8kZ2nSrU6ttap5U40gFKyNOspAHmvvyixD3L3VHxrK5pSCCCGKy6hQv2glJsR2Racoce4nxrjaiULFuclVplArPjEjMu4irEy5T1NqaV9l6RSkBJKQASOemxBjcL3DfIOdG1SeI3KGoOunQ0gYgDWtR8lAK9rk7CLcCFs58LVlMayzpVKkKacunKjMSaCH6hOVVzpZpwrUoqKUgJSLKSkAfaXvvFd73OF1OQqrWCJphiXlXpaapTFTUliacJu0%2BVkFaCi51JGyrDlvebG2CsUZc4oqGDMZ0lym1imLSl9hZBBSoXQ4hQ2WhQ3SobERk%2BXeSGM8yKHUMUUh2j06jU19Mo7UazUWpGWMwRfokrcPWWBYkDlcRHApkznwsafGU02UF%2FLGddWT1h7OuC%2FmFkx6ZzC2XKcOYjqtOybrjD1Mpbs0h2dq73i7B1oSlaylIJHWIttuRGdryExJg9p%2FGE3mLlx4tRpZ%2BfKpTFMs9MBTTalI6NvfUvUE6R9taNBYtz9zcq9FVh%2FHGaOKKrS59CVuyM7Olxl8AhQ6RAAvY22PbDgRBnLH367QEPpb9rbcskHrJTU3lhQv3lNxHhmaml2adekZ1MpLKWFNsKBdKR2jXYX%2BKMVqM2xNv3YXqRHm1uNwzVzZuirttoSlyZDxF7qCim%2FqsYzjLr2hYnnqZh3EOCq1OOVKpJbeqVMrgZmG2CN0NMONFta%2BZupQ5WjQkxNTTatSH1p9BjPcA47XhD2Jr1GrCpWu0x8Tcs8gdeXfSTpWL7E79oI3iKpOE2qnBOTLjoZdrGNlqCykkKlNx2EAE7%2BaKdRy1yoekZhui4oxdJT6myZZ6elWHWEujklxKFatCuRUm5FwbHcRlmXWYWcHEDW05dPN0XEIqcnNPsSzdFkJWZU%2B0nWHG320IUlQIud7EXBEZLMcLXEazsrJuvqUeQZDLt%2FuVmI4MJ2bGtZPK7Jt6TljPY5xgxMlpHjKW6c0tvpdI19H1rlOq9r2NucYtmJl3J4Zp0%2FijBuMGqpRZES%2BuXqMuqWqCVuOlsgIF0LSOqoqChsrlcRkr7E7T5yYptSk5iTnJR1TExLTDRbdZcSbFK0K3SRHvKl%2B0fHyQm7RwpN9MhR6qvfmCkkd4UAR5xFuDEKTr2uk%2FB5L15Yo6T%2B7KtPuKHcUtEbebaOE8RvdJUJ92%2Flzswv43lmO1%2FB41BZy4RKunqMT8%2BU%2Fw2T%2BURw%2FXAEuzCUkkB98XJ5%2B%2BKjo1T%2BTaI%2Fen3uPdYnvlbT5o9rCZhXXUPOR8sVpGWk3gVTz7w36rbCQpdrXJ32AEeVw9eCHOjWlfbHOdrJcbYYH6bVvuEfPFNZoHwH6l62UfPF2oFCkKtR5mbdf0Ll1gPONklyTQdkvLR8Nkk2UU7oI35i9jqdNnaPOrkZ9oIdQArqm6VpO6VpUNlJI3BECYVUChKVZUzUR2CzCT%2BWJqjJSsktKWJxTt7pW240W3WlDmFpO24IIIMW7WIip1SlFSiSVG5JO5MEIkiJbnviETwEtz3xCJieyJCowEYRLc98LnvgKtx3wuO%2BJIQE1xDUO%2BJYQFRJvFTsik11lhMXGdl5MScvN09xxST7zMpXbqvDclNvgkWt27GA8JPbEt7mIXMSkmAyDCiwmdcSRfW2QPNvGYIcjC8K71IJ%2B2QRGXo5b%2Bf8AHAV0uEqtbaCSb2vziQKsnSRzh5W6eyAqC97E29EVEqTa%2Bm8UxqsBa3fAqBNyrlAZnLz%2FAOZ2m3EBKkI6253tve3ZFeUnC1NDpHU%2BQqxIve4MY1QGVVStUiiF9bfslUJWRLiU6lIS66lBUB2kBWw7bCLrmRhFWX%2BZGKsB%2ByZqLeHKzNUtubLegvoacKQ4U3OkkWuLne8BkWScxl3K4nmZnMt2styjdLdVT1Utc2gicK0J9%2BXKJLyW9Bc3A06tGraOjG65wGPe9uYyzPQ5ur80VCtg9xN9Fr2sI5tyczcrOTeJZ%2Bv0aQZn0VKmmmTLLk47KLCOlQ6FtvNdZCgptIIsQpJIMb%2BT4RzMLWtS8rsNWUOrpn3wU%2BvSbjzQFuzGnuD9GD6ujCGMMeKXN0ibRLJmajWFJ9krJMndDrYacaUdYX0igALEXjUeRWPcZYEzHpLWC685SVYkqNMpNTWy2hTj8p422tTQUoHQFEWURuRtGzMe8dmNcd4YqeGZ3LqkSyKtTZqlPKZqcwplLMwkBayyUhLjiQnqFXk3No5yo9Vn6FUpGt0yZMtO02ZampV8AKLTzSgtCrHY2IBsYDdvHYQjiixZKJTpEu3JtgX5DoE7RocEW3MXzMHMHE%2BZ2K5zHGM51qdrVT0GbmG2EtJcUlISCEp2HVSIx25gPQjReO0cuaW8%2FlphhLBbK00trpErJG5BPPvjir9LUuO08v6ghnAmG2i6tK%2FYuX2tzOmJsYzt49E%2B5jvE%2FiZjzx72e06SclXWuncc1NWXZQ6qB5rdkbEeyvqGMW5Vinl6V8al1vJdZZC1qUke96Qojq67aj9rfnFiy9bYnq9JS9Sel0tHSSt1Q06SQAfPueUddZb1Gk1cO1Nro0NsJMnT0kBNpZCrFY861DUfVGxbV2lM5Uc7UsLOztZzrc04tyamadSvz0RNzcwiXbU%2BwwpXRBKR74oDt07kX5iOZMxKPTqN9hb6JtLii1dARrbJ6pA7NvTH0YzvrFLkaQ5MTE2hlDTZbcdvYNlXaT5u6OAsfdBiZt2q0WbpVclGjpnfEZnpF00gH3p5vymyQLgkad9iY690omqx4VXK5d5yotpijYx%2FKfJh3NWbm512pGWlJJ0MuhPWWFc02B7xfcxvWQ4YcOUFhaKUqeDbgPTS10%2BLPX8rU0BpJJ3uLEdhjAcmcYUjLXAGP8w9Mu43SZJgykoqZDbk68tVmkgnmgX6ygDblG0p7icYxTkbP4xwBRZmdclvFpLESzpbmsOF0C7rjJPvjSwFht1skdptY206LG0rtZmdmeUdW9uza2cUcGNuWc%2BHbO5xtmtN4awliyeotDqM243ITHQTaHEhbKQRsW3b3IBulQVy2sTGKBxb%2FUfN1NtjT%2FC5emNqcUWKcj8XuUCpZJ4dmpSamJYS9VYUlVn3VEABIJJWsm4JHPq9sc80CszNGnVyM8l1yUQtbSUvJIcasbaTfe4IsQdxFr1T8VXGrLOM8vB6fOy2NHCoyic8tWezNsi7D1Jf6fR700VHriy7DYWPPb8sa0W4G27xsFh6UnKfOOIWFLclVKFk9QGx29Nrxq2pzjbDH2x%2B1jXqnOM2azjLU13jBWrFE8e9tB%2BSK%2BKZN%2BRFG6Zp1vxikSkynpE21pWFWWnvSbbegxbcSzBnK1MuKWd5dtFxzFgRGws98ylZjLy8aVT5KV9qOAKNhkKlwQqY6BLiukX%2B698t6o0%2BWW3E5RDDaTeyT5opV8kISb9sV6QQUD97FDEJ96RFRYAbRNFIExNATE2iZBinEyTAerEH9oKOjuVNK%2BNSY9UmR7CSyu1SVD5THkxHcUmip7FIfP8AL%2F1R6pc2o8mgfaavxwHkWlV72EEhS9lRMEq5kGKraVOdVJEBIGe4RIpsDsjrngb4V6Tnbi2oV7H8k89grDrSfGW23S0qfnHBduXDg3SAAVKI3tbvjxcb3CrSchcZSFYwJLzgwbiltTkg3MLLqpCbbA6aTU4d1C1nEE7lCje%2Bm8BycrqmClbRXmG9PKPORAS33iaIAG8R88BUAvFQIFoybLDL3FGauN6Pl7guVZmK3XZnxWTbeeS0hS9JUbrVskWBjotfg0%2BLFKCpGDKEuxtZNfl7n5YDlJDYMbHyayKzHz0xOMJ5bYecqc4gJXMuEhEvKNn4bzh6qB8vcI3OfBt8WEqjWvANJd8zddlifxxvDF2Acx8jcgctOGHK%2BizEhmZmrOTExiFcgtKXnVI3WwqYB6rSE7qUDbSk25wGsE%2BDUx%2FMqVTKVnRlVUMQpH9omqwpMwVb9UK0kX9ItHMmZGV2N8qcWzuBswsMzdDrcgAXpWYA6yDfS42sXS42bbLSSDHRk94PDicpldpkvSML0OsGemQlFbotXQtuTfBvqfe6rrRB%2BEL79sbUnsCZkcX%2FAAxP4arMgzXs5cmMVvYaZqC5xoKqUnb31pyY8h2ybEKvuWwrmo3D53uN2iipABjqZXg6uLlQ3yvY%2FjqU%2BnEG%2FBucXL6ujbyxly52J9mpSx9euA5YhHvq9KnqJUpuj1RhUtOyLzkvMMqtdDiFFK09xspJG0eEi0BWY8hz%2B9qjs%2Fwhiy4zkotXM5c0wn1hXzRxgx5Dn97VHY%2FhClgzOTKPtctaT%2FTgON3D1ohfeIOHrRCAnhGb5Q5M5iZ5Yncwhlnh41iqNSy5xxnpkNBLKCApRUsgc1D443CrwdfFum5GU2q3dVJX6cBzW23eNsZI8NObHEDUHpHLnDhmGJM2nqlNLDElKX3Gt5W1%2FMLmM8Pg%2FeLaXl1FOTcy44dkhNSleff5cdHZ0YNzJTM4K4G%2BGxiYk5Sj4YareJX23zKoU64m6picmBuEElQt2qI5wGoKt4NLPBinzUxhPEOB8XT0k2XH6XSK0PG025hKVpCVHzaheOU67h%2Bq0GoTdIrVNmZGdkHlS01LTLRbel3U%2BUhaFbpI88dQyHBfxl5d4uNVwphSapVWpco5V5XEdLrbQllBqytpnUErUbbtODrC99jG1M98oMa8aGV2WPEjlhl%2F47jav0xdOxfKSzjUsl12XJQiZOsgHrJWjmTpUkckiA%2BeBa57%2FLEnR2PP5Y6YX4Pji33tktPbd1RlPyuRbq1wF8V1Co87Xqjk1Um5Onyy5uYWmclHFJaQnUpWlLhUbAE2AvAc8HYRIVb3j0ON2jzqTvARConCopjsgSYCsFAxVbVaPKlW8VNVu2AuDblxHvYcBRaLOyvePdKuEqtAZrQP7WOE%2FbRbpYFWN8NoHbV5Mcv%2B3RFxoRtSHfOoiPFSrnMPC6E81VqRA9PTogMfrTi%2FdJrK%2Fta5Oecfohz5IuuHwDmdThtdVUlOQ%2Fdoiz1r3vMSt%2FC%2FPic%2F%2B4XF4w0k%2B6xTEdnstKD%2BWiA%2FSNCEIBCEIBCEIBCEIBCEID88%2FFCnRnXmGnuxTVf%2FALt35400reUR%2FC%2BO8br4rUaM9sxkd2Kar8sy6Y0mf0IPNr%2BO8Bl2GU2pXpt%2BMxepGQn6pPStLpck9OT08%2B3KysswgrcfecUEobQkc1EkACLThkfnZ60%2Fijf3Bw3hd%2FOlljFNCpc2linzFTp9TqdS8UYo07LDpGpkjUkOkr0o0k7AkjlAYrlnkxXsYZiYcwpiaSqlApdXxE5hx%2Bov050tpn2UKcdkgQPsxSkpB8lJ3OwMXfPPKnC%2BBaBgvGGFqXiygy%2BLHKpLOUPFbSU1JlyUcF5i6Bo6FSVoSkc9QVzG8bsrEnnMjI3Mt%2Fiok6Pi2cpuitYUkHa23Kvsuua2nqnK9AUlbKNaChIBKrKF%2Bcch1qu13EM0mp4lxDUq1P8ARNsrmp%2BaW84pKEhKRdRNgABsIDyyVNdqD%2FQS5SFkX6xttFx9p1W7HGPjMeajVBmn1JqZf1dGkK1aRc2tGRnGFHGwL5HfpN4DG6tQZ2jIQ5NKaUhatIUg3sfPFsJ7iDGR4mr8jVZFhiUK7hzUu4t2bRjVx2QFS9o7syRdbl%2BDIvPlJbTTMQFZVytpc%2FEY4RB7DHdGTaUzXBe%2BysJCVUqutj0gOH5Y%2BbfCbOVxuv8ArR%2FJW62EfKV%2Bhx3gNv8A4KXm3NQ6PEjKut3mQVv6bGMyy2l3K%2Fjb2vPVGqMSApMzNKZp810CnHQpIQpSrHUE77RiuAk9JlLNTB5%2B2WXCh6ZAxdaJO1DD9ebr9FfXLTqJdxkPtpClJaI1KASdje3Ix9Es9VLmVznk277nCEJK%2FZrEQA%2BD48pRjB82qBJYexbS6LS5qdcTMshxT0y5qc67oFirt7T5ot8%2FxNzLIbQ%2Fi%2FEyekGoKXRZS%2FqsuMaXm1lvVsQS2IcXVrHFVcl3G1qbalZVrUlCtQQkqUQkEjfYxlhR4qhm3K4PqTrbOWlBmplLL7LEy7MTClNFYW2HAkq0lSQSoXFgqxttGq5vEKX5tbjMoWkq%2BCV6j6z2x68W1WVrFRXNSd%2Bit1Qq9xdSlW33NtVr9toxlbehy8Fl%2FZq4t1pcn0ER7RV23W1NrSpGsWuCLjzjzxjbavNFVLunsgiW3nc3pavzDMlM5aYbbemlttLmpV%2BbbWFEBPSJR0hQk9trWuTyi4zDfRrUj7RWmNO0aotyFXkZ99txxmXmWnXUNqCVLbSoFSUk7AkXsTsDG553MjJB11wyUvmElsuKLaX2pIlKCdgSle5A7drxVLwOd0SOTM3IMmakJp2VmWtJafaNltqvbUnuO8V3Mb5QLYWRJ44BIJSejk9IPZfrXt8sV5ukt9I7KzS1mVRcuqQgqWUAaiUp77RZSYzdJTWG5ibDTgbqmlTLZ%2FRj6k6tAuoaj8I7n07Ri%2BZ2DJGXwDUZl5meQ%2B080rpXppxXVUoC2hW23O%2FONMDOuhSaW0jEWN2UONhQF0EaTsCCly%2FZEqc4cvZ19o16vY5nZRDiVuy6W2E9IB2alrVb02iMiYzeOpZrs4RqD0kzgShTDrCClmccQ8tYJ2Dukr06hzG1r9kaum8RS6ptSpNt1aXAFKLwGrX28oq4qqrVbqLk5LI0IcPVBN9rm3zeqMYcBRMCE61oZRL11xbdvFkpj1%2ByZW1pUgjULAhVoxxhywj0pduPRDJDbKs3%2FZt9iXmcv8MsLcLcut2TadlyT1U6wAsgK7eVrk7RdH%2Bo4pv90U%2FEY07ITqJOek5xxsuIYfQ6tANitKVAlN%2BwkAgHvIjbk3mPku%2FNvuMUrHrcut0qabLkkVto%2B1J5KPn2iUwlci11WYmZKQenJSYdYeZF0ONqKVoNxuCOR35x7049ynW2oJpeNkr30EuyduW1%2FX3R7PEEPO%2BJPhRlnFe%2BBIBV0YGokA7E2giJdDOYQdqiZeYXJ1MkyrKVuCafUXVaR1jdXMxYsf4NprOX9Wbeps0mbbW0pD7s06SlGsApCVG1vPzjUEzndl3KJbZapWOUK0IUjpJqWto7DseZES%2B7flFOlCapQsfOtpUhTiGp%2BXQV6TfTck2B7TYwFhq2bbmE6g9T5LAGFHtLK0NPTEm44tGtJTq3XYrTe4JHPe0avXiFC5hXQNqCVfbKF4rYsqUtW6s9OyQIZVcpBO4BJNvVyjGwND4tETrM4llUvWSv4EVhUVuoKRdPnTsR6IsDbmiK7cxEjbjucDuJKtLpncvcIsvTjjMs47JSS5dW9kFYAXYKNrk25xVmEIbWtA%2BCop%2BWNYUKps06t06pTTBmGJOcZmHWQrSXW0rBUgHsJFwD2Xja8%2FmBkPMTMy7J4VzCaaceUthpdSkldG2SSEE6etblfblETrFuK97CFYedlaFMzMpMOszKAgtONLKVouoAkEbg2POKq8bZK2szhvH6VaCEqVUpJXW7yNHLzD449b9JtVF0p9a1sJUpKyEbqQlJWQBy1ED44RA6TmsIGtqYqLsgUqVKsNuKbmFpS4UtgBagXDdRtcntNz2xh%2BbGEqdTMup8Kpuid8aZW1MKfUV6CpIUhIKiLWN%2BV7xpGYzbwHIuJWuj4tSpaekT%2BbJYjT2fB5xQRm3ly7MsLnaTjB6XS6HH2UTcq0XkjcI1aTYE2v5olaYzUp3N2q4IqzzNNwfhNxTaHG2X3qcpbyAtJSVAlzSVgE2Vp2O9o1i1iF3XpQ2kAcgSdo9OKaq3WKg5OMoKELNwg%2FB80Y4z%2BiVXgqylqurUOshPqisKyhXlAj0GMeSrzRMFHugNsrzXn8UzaKbMYJwk09PrQy7My9PU2%2BRsNST0lgs9qrb77RK5724pHSK6iikee0a9w1VmKRXpCrTUuZhiUmEOushVi4gHrJB7CRcX7I2RN46yimZtx6Ww9jFppSiUtrnZYlI7tWkXi48uvzRMjnETi%2FLJfVTQ8WIBOy%2FHJY27ri24vz80V%2FF1tudGvrKT1fyxTLNaYXrG4twxyh78ylH%2FAPhgjsPgWdW7w8yGr9KTVWwe8dMD%2BW3qjkHHTKU8MUkNRsrMle3d%2BdgjsPgYP%2F6c6anRYoTVQT9t7%2Fe%2Fyx85%2BEXVcaI%2FzKfZLtYT%2BdV%2FDPthwdMJ0zrw%2FwC3eP8AnFR0HwM392mcv%2B1%2Bb%2FnIjnyZCkzzyV8w%2B8D98VHQnA5YZzztxf8Asem7eY6kR2tNJ%2FIFvP7u5qYdqvVPpT59noOKDEKCNJXlq%2BSvV2KYt%2BIWjTclOT0g0ZmnzypWaVNyLTb6La2wqYSlRTcEA2JF7RufP5oHilrwF%2Bvle6Tfv6E8vijSTiUFnQ7cthbbxSDa5bVqHyiNjRGM8Eu0%2FuR7GvfdVtV6W%2BalhObmqk%2FMIquJUNFzqJXOKWpA7r6Bf4oxPNfDMvRcGtzztSqs1M%2BMttlE68HEouu%2BpsWBSbbHfeLK9mpMyQKa1mnXpOZaDfStpkwtpClDUlKVqWCbAje1rxYqzjvDOKAhmuZqVSdaSQvQuUbtqHLbX2R6SNbWW16u4awpTmH61hZmrl5hp9x12cfbUelKrICWiAAAnne%2FOMDx5mFSMVVuYqspTkySpherxaWQpLLCAlKUIRqJUQAnmSSTvF6zNquEqiz0OF5%2BZflG5WSlWxNqb6dbjSVlxwpbulKSV7C5IAFzcxqOaQph8Enc9sWyRMMjbq0moD3xYMekTjSyPfFERi6XSkC5BMetp9W1yQIqltfCmYOFqNhyWotcwPTqpMSbzriJxc1MsurbWQoNqDagkhJvY2BsYus1NSk70U%2FIy%2Fi7M2ymYQxrKuiSrkm53IFuZjTHSdI2rrxuyiV7KGewzQzU8T1%2BRqsrTmpafZRJMOtF1BIu2ouJOkp0%2BUL3v5oSngwtjjljEEalutpB8pQHxxkCJnJ3bp8b14d%2FR0pk3%2BN2LTUhS25kTuHai9OU59BdYdfYDTmxKSFJBI5jmCbxGRk27glrEOIcC02aXi6tsq8Zm29EutpLCWW1hLTaUhu4IsSTc3uIv7GEp%2BZZfYn8dYpAEu4plLTrJQVgbBwLQbt2vcDfujWVGzFbwDRzQWcb1SmutPFbzLUi2tgOrSFqSkqVfkoX29Ee1zPSUqTCGKlmdVnWlGzjbVNl2wU9o1Fd%2BUMjJgc1iagYdkG3qzheWnxNFQS6qcfb0q3JTpb2tb1xhWL8dUbEVefq9PkkU9l8JKZKWQpLEsALBCNZKiLAbkkk3MXPNOZwvNysozhSfemJZgIQDMFHTLUlB1uLSglKdSlWABOwjVtih%2B0SrEZMmXWpBxvZx%2F7iKaazIJ%2FTH%2FuP9cWMLNt4lWu8I1JbcoWamDpXD1PolYwlJz0xJ6z44t6ZbecSpRVoXoVpUBewNgbRdHSy6pMzLsdA0%2BhLyWQoqDYVvpBO5A8%2B8aOBvHQbdSypmaRSnXsTVuVqIkmUT7QblnGA8lIB6IhQUEmw2ULg3gLVqT%2FuIoFXWGvlfui7uTmVoWFDF9bSntHibKvxLjwVBMk2BMUicVNSjjXStLeaCFncgggEi%2B3YYDatJbrT%2BHKMZTEVck1ty9ngzNXZeJWohQQUdSwITYG214lrEtWkUCpT05jHETjzAaLCFvoVLrTrHSJdSpFzcWAt23vFgYxvhfCci1T5zHeKZSfaSnp0y8uymVSspCihOtepQGoC9olns0MJVpjxWfzCxJMtgg9GZeU0kW5EahfeAx2cxfgrBYabrGCJWrPzJW4XX52aRayr6dLRCQLWHfGvMXY4pWJcS1Cuy0giQanXekRKyqVpYlk2sG2wslWkADckk7kxc84JzDFRdl14VmJp6SZASlU2W%2FGFL0JC1rDV0pClhWkXJAtfeNYQTDJU1qSRzee%2B5is3XpD9Wd%2B5jFSYIXaCI1N10jNPArWHqbR6vgKSqs5TkOIE%2BqZnJd15CllaUOJaXoJRcgKABIsDyiep%2BKmfWuSllSzDqEPNsFwudEFJvpCiLkDfc7xpuXc98R%2B%2BEdAPzWU9QlpJ6cxRXJOe8RZZm22JaWfYTMITpUWldIlSkKFj1gCDcQRLFlKIMQbUlb6EKUbKIEZME5LBY6THWIrWGpKaYwVA9v6bYxbK1I06Rnm3MOVJ2fpr7QflnphgMu2JIKHEXICgR2EiBDaUsuuu0emNsV2tsluWu4W3kltSys2KE6OqkJATa55XvvaKGIG621hucfexZXVPNOsKSl11tTDjesBaFpKN7g7WPOMbk8f0fD0o3TajmTXZCZSmy25aVSGkqvdQTqXuATztEJvMjC1SATN5n1adQiy0szMiytC1DcXTrAIv5%2ByCfzmK1DEOCcMmVYxDg9VRU814ytxM8%2ByVoKjdsBs2SNrX5xg2McZSWKcVVTEUrIokUVGZL7cqwFBqXb0hKWkBRKtKUpA3JJ5x7s3JjDc3U5NGEZ9%2BckGJUNJXM6Q%2BpQJ1KWlJKU3UVEAHlaNfI2iJ1phkzNaZ%2BE4qDtWklc1rjHA4EnnEFvRKG4KZmJl67S6fS6hhCYqVRYStrxtupTEst7UeolbYui6b6dQ5gbi8UZgNh5xSULQ2pV0IUsq0Duv2xq2jTCWKxIvOOBtKX0KUTySL9sbveeyonWpea9u081NFpPjLBkkrQh34WhYX1k91wD3wGPdXvV8UTItq5q%2BKL%2BG8qv8ArEqBv%2F3Pcn1BceKfkZWXmiKfNqm5NwFTDxa6NS03t1kG%2Bk%2Ba8BluA%2Fe8vs6XOv8A8nq2%2FMdVSlOfmjP%2FAAbyl%2BzGYVkXR4pSrqtyPjKrfljAcFIBy3zpJJA9oguR3ioSxA%2FHGf8Ag3SVTeYbffLUk%2F8AqVCPG6bxngt49HvpdXCo%2FtNP9ckrFxjm%2FEXisdyZMf5gRgWWBJzKwanur9P%2BPp0xn3GSsK4icUWQke9yRJB3VdntjA8pQDmfg7UL2r8hb78I2aZy0apmPI%2F8WKn9K8%2FCh094Q9IFAwC7vdOOm7WNti0n5o5xzGctnHizxn321fm9aFb398Vz7zyvHSXhC0n2pYEUNFhjZjUD5V%2Bi2t8t%2FVHNObF2s3cZqZVuivTZSr0LNjHN%2BDj9RUR%2B9V7U4pGV5qbmwbhyoYowJhyrTOLK2uampIKmEJU0GkkEhAbsjYBIG3eIv3ua0xVOqTNQqVffQuUeUlCn0FoqCCR0idN1J25CNLYSzhxFl%2FhaUlncUzcnTWEuNyTbFKTOKTospZUVKT1RqHeYlqvEzJ11h6SqOY%2BKQw%2BlSFdBQmWzYi23vm0e7c5hNIcpVMw5M4hqtAYrXiy22kyr8y6wg6m1KJ1t9a9wLdkWLEOaNHxRTKfSKXgCnYcZpnTOK8Umnn3JxxwpJU6t0k9UJASEgAAnvi74ixVlv7SXqFhOdxFNz780X3HJ%2BUaYZ6MMlCEJCVKUV6lElRNrCwF408hZbXAjUysVhkN9WXVft3gK6keTLqt6Yx1TxDdwN%2B3eKJm1A2A29MBsXCmYVPw4mptVDBNKxBL1JltstVB55oy6kL1pcaW0pKgrmCDcEHcRf14ipeLJJVXp2DpLDobmPFizJTTzzLvUCgr30lQVc72Nt%2BUaeQ6Vb3jZuXGLcsadhWdoOPJfFQnV1BE1ITNFal3G0t9GUuIdS6pJ1XAKVJNrXBhnmmHr0%2Fux8UEp98HXEXFzFmQ%2BtIRNZlWv17SMiNv3J6T8cSTM9gSrSpnMCzGJiJMpROIrkuw2pQWeq4gsqULdhBtAltXJqRmqjRq3JN1asSrTamuiTIzhYQlxVyVrSB75dIsBcWO%2FmjYNMwW%2BioMKmcU4rUgrSHUt1JSVFNxfe3dHP%2BHswBl6w9VpmtV6RM7dsClssuApRa5cDpG11C1t4vTPFBLWSZjHGMzp5hqmygv8avxwQtWP5mTwhiSvT83RGMRMSUyWEt1V5xSw2Vq0FSmyCpYAAuY19iXMuXxZJUuRkcHUjD0tSi8UNU%2FpFF9bpBU46txSipXVAHIAbWi742xngGt0KaYoT2J5yq1CaVMTk1Vww2jo%2FgNtoaJudRJUpR7rDnGqZRxWgbwGRCqqCtQHyxM5WFrFujv%2FAAosod2sYmDgHf8AHAbAwZmWnCEtVJN7CFBrstVEs6mqoytfi62iSlbKkqSUKNyDzuDF3XiWVxPLprUthanUQdMqW6Gn6w0dKQdRC1KOrfcg%2BqNU9Knz%2FHGw8DYxyzkcLv0PHNNxOZ1E%2BZqTm6M6xo6JSAlbbrbvM3SClST2kEcomZRMZvWXT54qNnULm8VVYyyOF9EhmKd9vfJEbQXVcG1ZvpcHy9fZDBHT%2BzCmFageWjoeVvPELRDaGV%2BG5GvYWnZqaqNYYmhOpQ0uUqDrDSWwDrC0IICibiyuYtGZU7LKivVBhqexBiZcstwBxLNXeQux7lFVhv5o1JhLNKSyspPjlSmcWoM884Uoo65RDAbSoJusTCFalk38nYCLw7xcU94Fv2Qx5bsURSrj1BqBkxnENZawQ9WK6cOUivuS80xJaayhbwSNK%2BsAlSbq2FybxgeKsyn8bmnrcw1QqG1TWVsNS9HlDLtrK1aluOXUoqWSLXvsABFxzGx9l%2FXsNO07CNLxO3OTM6ucnpqtTbLnSqsA2ltDSQEpHWJJJJJHK0a1lXCEC8EL2mpFHZExqmr4MWhTlx5UQDtvhQGfYTzOmsJUup0dOG8PVmRqrjDzrVXp4mC060SUrZWCFNkglKrHcRc5yvJxVIy%2BJFYeo9FccfflyzSmFMS60pIIVoKlWULkXB37o1f0w%2B2jYmC8dZaUzCrNBxthnEc%2FMy08%2FNNTNJqDcuC04gDolocQoEhY1BQI5kWgI38xiYcuRj2e6JkikpPtExssA7gV2WTcfeoru1PB2Iac5VsGUet0puTdRLvy1TnWZsu67lLiFtoTptaxBB5ixgNqZO0YVTDtRllyRmdUy3p1LWFtWHNFlAC97E23jYlNwFSpSfYmJzCweaQsFSHnXSgi%2FI2WNvXHOCMZ0fBNMlJuvU6tzqp8OOIVIzrcuhltKygIGpKiokgnew80Su58YUIUlik4uSFXuFVhk3Hcfe94jIS4yri8GTFRqdOpNJqN6s5KoFUYM4kMhHVA1KG4v5Rudh3RhOJMx6njBVPfqVLpMiilyniMrLUyUEsy23rKydIJupSlElRO8enHmOMKYioMpTMOUWoyJamHJqbdnplLyn3FWA06QAlKQOW9yYwPpNovkmF79nT%2Bt0%2FHEHKyVJ%2BxJHrMWXX5oa%2FNFUM7w5mfVsLU6YpdPplFm2JxxLq%2FZGQTMKaWkWCmlEgo22IGx7RGW0%2Btz2IpZNTqEpIS7zvNEjLBhq3ZZAJAMaX6SNnYPzKwbScPt0uu4SnJycac1%2BNMz3Q6mrC7RTpUOYuFbHc3iMjavkwHUp0na%2FIxQbQ6Fdp%2BOKb%2Ba%2BX7qjbAVV0k9tYFx6OpHtkMR0TEbSpiiUSbpzDBCFImJsTBVcXvqASfkiRn2QzP%2FDVgtZNrz7puTsPzK8d4wfgHS%2BriDpfi5vakVMuJuOs30R1fkjYOQLpRnRg%2FqJP5tmAUKFwQZN8H4hv6owDgE6nEBSFlCVaqTVBc8k3aPW9Vo4OkerDLfPxZ9kt3Do%2FtNE%2Bdurj%2BN8xsDjuwiB%2F6oxy9HUXH4L5kYKvzGERYf4zHLsa%2Bhn6ju8fuz7ZUvlX4%2Bv0pDEHG3HG1Nt%2BUtJSn0kWicjtgnnHpmpOp9Aq%2Fhqa4keC%2FCVMyxnZVM3TWKa3M091YbadfkUlt%2BScI2Qq9lo1dU9XvjjfNnJrMbJ6iy8zmLQJakGvszYkW25tt9xYZSnWV6CQny023337ot%2BBMzcwcsKg%2FVMvsWz9EmJpITMBhQU0%2BBy6RpQKFEW2JFx3xWzDzZzFzbclHMxsTrq4kEuplGyy222x0ltelKUi2qwv6IJdVcZC1M8OGTTqyEkOyfVPafYgcvR%2BWK%2FDHjDiIw5hLC2A8RZHrxVl5UGmk0iqIU2FydPfWV3dQvU28yglSgFBKgBYHlHJeJc08xca0ClYVxfi6eq1IoJSaZKTGjRK6WuhBTZIJPRgJ3J2EZJh%2FiYzzwlh%2BUwjh3MGelqVIsplpRpTTS1S7Sb6UIWUagBc2uTaA3BxC0fLPIXixy9xJh%2BRlKXSekkq9iCnyyT0EkoTKmg%2Bhs3LaFt2d0ch0aiAIz3jH4fcz8y8cULHGXMmxiWTboopnQInkILV3lOCYZCyELbdSpBK0m%2FVHZHE1YxJXcQ1SZrmIqtM1SpTqtUzOTjhdddNrdYnsA2A5AcozHA3EHnJlpSUYfwdjicl6QzsxIzCUzDMuCblLYcB0Jv8ABGw7AIDZXDXKqyK4tpLBuYiqfS5pLEzh9xaHUrYlp2al21sp6QbDUVBBPIKVaMw4kuETOXMPO3EeI8OU2TqNKxZMMON1Gam0tqpQ6NCOiebV1wlkoJSUXvcW3vHK2KcTV3HNcn8S4xqK6rU6msOTT7wSC4oAJGyQALAAC3KwjYFC4qOIHDtFTQKdmZUlyrTfRsKmkomH2Baw0OrSV7Dlcm0B0N4QqrU%2Bl4Ey5yxfnjP1%2BTe9lHZhabOGWalBKl5QO4LzguAdyEkxw8d4udbrtbxJUZitYirE5VKjNHU%2FNzbynXXD51H8Q2i1HnAS%2FCiZPOJU84mTzgJoGEDAIQhAIQhAIQhAQPPly7Yavl7Yh%2BXsiI58%2BXZAR5xIRaJxziRyAprVbyhe24iCVavJ7NoLUCLc%2FwAcShQUbjYQE9tuQidAFuQin67xOgHvEBXQWUMqU4uyUqHZe5vskDtJ5WHMxstOU%2BIcC41omEs18Xs5WtYvoD06KhOKLoTIO9XxeZZZJWgu6bdGq3YTFiygx5K5W5l4dzDnsJSWJZaiTYecps2BZwEEdI0Tsl5F9SCoFOob946vx3m7Rc0M3ZaTyRyTyrzXmcbUn2ZROVdpxmqyxQno5hif1qCUvN2FrEWSU274DS1b4dcJO5c4zzEy34g8L44GBpNifqkhJU%2BYl3Aw66GwQpfVvuSB26TGjo6mwtkrmlkvwz8QhzIwo7Q26xRqIxIB%2BcaecfDU%2BOkA0KUbJC7AnmO%2FeOVlqKG7oX1km9rXt5wO2w7IDfvDzwm4nz1otSxa%2FV2aBhxhEzKSE6qzjk3VG0jS0W%2BYYBUNbnMchcxpvHODMSZc4vqmCMXSiJasUZ8y06024HGw4ADdCxspJBBB7QRH0LyIzh4Wcusv5DLjA2arlV9jW3alOKcp007MFbgDkw84lDZ6NsK9SQOccwcZlcySxrjSn5h5R5gMYiqGIEODEMqyFFmXW0hCGXm1KSCOkTcKTuLpBFrmA54jMML4TzH9qVVzVwkmel8O0qY9ga7Vae8C5INTSAlfToSekEupC7KVaxvbnFmwfXmcK4ppmJZnD9NrrVNfD66ZUwoys2LEaHNO9rkHbtA5jaOuck%2BKrK3BmG8V48m8qsBYbqM4W6HJ4Tw248Z3ETzliBMNu%2B9CUHSKBcIJvqG19w1LP8MOHpjB%2BK8TYD4iMD4xewXQ1Vyfp1LYfSvxZK0p6q1DSPKHP0RomOrsvcj81coMreIev5j5fzGGZCr4CXLSHSOIcaCzPJUWUEKJ6qVgC%2FMJjlBS13gJPhCJz5MSb33ifshA37wvG0jipdr7yqLfwVn%2FAF%2BqMEwdgHD%2BOOJvETGI56rSsvI1V%2BabVTX0svdIgEp6ygbbgct7XjPOFvam4ov2OS57e1tcWbJ%2F%2FwCJHFribr0Tc2rle%2FvRt%2Fv5o83dv1tb%2FZ7n2DHqYnQW4R%2B9n1Wi1zMwqZfcfcS2FuLK1BsWSCT2eaJs7ZxpnKXKykzb7yJBcziCoqYQNSVzJdYb6VSfttACQewXiUtAuBCRzJHyx5uJtbMtl7lV0ZSbMVskAWJPjDV%2FxR6PJ8fiWq2JrDOnUqad6vfJm4iy4xm5GfTL%2BIvl1LaiCSgpPxGLU3UkI5ao80xNBxeuGS6n0YRC4MUlP6okLtjvEqKjiAsgW5xRcQtIBHaoCKqHkgg90SuuXAA7FAwGyZFVAFHkGHKmw24hizrZaUbHnYx5p2Xw6%2BhSET8np0lNnWTuPijDV1NC9XlR5lz%2BtpzyvJMB1Pi2v1jEOHMvZuuzip2bYwXTZQTKzqWtpsupbClcyQmw33iz5vzSpnLHLLD89PpZprLlfn%2FFXEqLK5hUwygvlIFisIASCeQ5dsemtq0ULAbSQBfB9MJFuRKVn8sWPPpa2MF5V6zdPsfWinSrvnk3vEwuwOTp%2BHEEKZn5BBG4KWynf7mLPjXxeYn2ES8w26htkJK2%2BSo8aKmyR13FpPouItr04hbiik6t%2B0RCiCWEpiYpRHnXNiJfGgYCdUsnUV2vcR5wwEOJCUaiTyismYCuZtBh1AmULUuwBgNjyEm4xJyr0tUWJdaUbFMyGltq5dUggiJ3qzi%2BjrE7S8c1CWm2RrZfarjra2ljdKknXYEERrxybl7q99HPtTHlfmG3Jd3r%2FBPwfNBaJzdd5y4vq2YGMKPjnEBlzWK5hSizVSWykJS9M%2BLBK3dvhL0gnzxjblMrNZwVjOnUKpS0pMuUJ1bqZhkrQ%2FLIcQt1sKH2NZCQUqItdNri4Me3HzbbVUw8w3ybwnRUn0%2BKgn5THsw1K68MY0nAsp6HDU6T3G%2BhNvl%2BSJlMNreD%2FJTlxMrvYCam7dW%2FJlR5euOLastK%2BnWNgp54gd11q2jtTgDGnLSaV3zM6f8AMkRxNVdkK%2Fvjn89UbueeHWf8UuTd4%2FKNt9jDXvKikrmIqu7ri5yVFlJijezczUWtLEz0EzKNH81IQpF0PJQdlovdJsbg8%2BYjRdNGgTM3TnkVaWeW1MtlbcuEbFd0kLB7CkAm4iecqDtSoshRG2GnWqU48pqdNw4UuaT0O5t0aSkqSOYKld8eN16W8XEkmozC5dpa3G0Fu1lKACiO64AvEqKktmRepjMw8ZR9xLzjKkDSXEghKu8EAkbd8BSfkJphvpVMgp1adSVAi9r227bR57fzo9LDjfRqZcU6hhxSVOJbRfdN7G3rPxmJH%2BjK1KbTYKXdNxa4t2j0wFI84miU84mgJTziQ84nPbEh5wCEIQCEIQE0eiTkJ6ouKakJN%2BZcQnUpDLZWoDvsI88XKjJqo8aeo1WMlMIbGoNzRYcdb31BJuNVrXIvAGqeqnzZlq6zM09amzpDssSoE8iUmxtz3hKuSsrTZ6XE30vTugNoS0bkoN0u6j5IIvtzijVJmqzTrblYqL84%2BEFIW%2B8XVpT2AqN9u4R40a4CY8oliY8jEsBfcJ%2Fo9X97MZeLrPWjDsKL0VEq7m1Rmd4CoEp07xIFFJ35ROCLb84lAJVc8oCom6k6r9vKBRcXAtvFVtsKHSXtY8oXK1d28BkOWnRDMnB3SJUT7Y6VpA5H81t3v6ov3EA90%2BfOZDtrasV1Pbu%2FNC4sOXgWjMTCC9O6cSUoi%2B23jbcXrPLR7umY3lafbVVdOnf%2B6V9sBg2pKuuhAAAsrfmYmLqkgEW1W33iVtu%2FX1iwPdziRZIN0EHfc2vAVNR0aybaja1%2BcQKwRYp2UO%2FkYlKQdwb3FuXKI7qRcC59HZAU%2Bv5onAPMiGje5ioAO0QEtz0ajfbTe1xHYeCVoThXD6i4Qr2Ll%2Bpbl1OccdzCkhpSU91o61wJ0qMPUN5WnanshP73T%2F8AmL2Py0eifcxXj5L7Y97bstiduiU9FckqRKTbtPYce6CdTqZdUU6NwLEWKgoWOxAjdWHsaoocjJSaWXilmWbbbFzcAJFt%2FwDe8c8yMg7Wqa9SmhdU0wpCSBug87m%2FZdMdRYdwfQ6hh6SVNNB9brCFlxJsbkDlG5XVwao4MOfZUTXFUTLW2fmNlYpwY7RRMuMqm9Wra6uVgrnbY72POOAqhh%2FH2XOLJHFMpV5ulT7jKn6dW6a7cTsuFdGpQtz0qBStpwbHsIIMfSHHOQtGxbKIlZeqzMgpJKSbagtJN7Ht5xxpxEU%2FCuWOP5DCMpX1Ygfk5BTtZcZsluSeUfe2jc89ABUOY2vHQs7SbeiKac44PN9rXmz7nr%2FCmJ4XP9iyZoNvVjBtBxvjfGr1dxtVJoUyWlnGGmZVqQDepTiUtpTpVrO%2B29zFqzXm5bLDKTCWVkhLzkvXsXSLGKMXz5fSpM22VLTJSTJbNvF20hSyk365Fze4GG4jouNarSpqdGE59Mgzadedbac1MtDyX9C%2BskEG10ixHxxuLJbIXFfELlkcCYkqMs1K4cl5qq4Xr8z1H6IySVOy0yo7OyLy7lKPLbVdSercRgtLamyqpmjz888vuhmosJmnKvw5zGWyI5N%2FhcuLxHMyj7b0o6tp5hxLzTqFWWhaVBSVJI5EEAg94EKPPz1ZnJ2cn5x6adU8p51bqypS3XCVLWSeZUq5J7TFR%2FDyujW5rT1b%2BSbhXoPcYjgmXSlM%2FMKRqQp1CEk8hpG%2F440bSKonKp0LPKY4VLJ6bWXKLLvuNr6rrC2%2FK2FxY27ja4%2BOMEnnPGPfIy6rIb9jJhxtxv7Geqn8fpjEej6unviszOWS0RG1rqtHRU3yewD8UVqy5eblx3SrKfiERxMyG63MtD7RJ%2BSI1hq1QaH%2FANO0fjEa7Ku1G8kfvY8%2BIfsCYr0f7Gk94ijiIWaSPNAY8OcTjkYkHOKggJYRP1fth8cLJPJQ%2BOA9mKRalUQX3DDm38K%2F5YqsC1Olgf1ERNji4kaCC1o%2FMHx9Y7xKk2kJW36kmApg3OmMkwJhStYvxBTsNYekVTdUqk23JyjKRcrecISkeje58wMWCXYU86EI8pRsI%2Bh3g9smKPgzDFZ4qMxkJkaZT5SZaozj3JqWQn81ToB%2BFt0bZ7ybQGzcxqHO5F5LYS4Qsl0MzWYWYTMxIB5p%2FoNKSi9RqLjvwAbFtCuwA25R7MJ4dqfERkRi%2FhVzemqc3mflyJKmvzrMwmYR4yloLpdSS4nmFJvLvee%2BrcxrPIjNP2z45zk47cxmw1SMKUoUPDUq8QEtrc%2BxS7d%2FhaOiSbblTqo52ybzozByizaHEjVqTXKjQqjUHJXFc4ZR0S09KzjhU630ltJcSffG973bAEBoTEmHath%2Brz1Fr1PVJVKQmXZScllixYfbWULbPoIMY86jSoiPoT4R%2FJCSmpyk8SOA%2Bjm6HidDEvWZqWA6NcwtsGTn9uSX2gEKP26B2mPn7OMKSTcWINj6YDwlVja0Er%2BDaIrAFj2wAAVeA3lwZYpwzgfiZy7xRjGtSdIpMjWEuTE7NuhtpkdGsAqUdgN7b98ebPjHkzP5045qmFsWT8xTJ3EE%2FMyb0tVJjonGVvKKFo0rAKSNxbsjP%2BATL%2Bg5l4zzCw%2FXcIy%2BJQMvas%2FJST0qH1CbCQGVtDmHNRSEkb3ItHP2KMH4twJUG8PY3w1VqDVWpdtxclVJNyWfSkjZRSsAlJsbHltAehvG2KlKs5imtAeaqTP9ZHbWW84OMnITC%2BXWHscGiZ75OqeeoDkxPrlna5TVAgFqYCtXSBNkqNzpUgauqu8cBdJHsp9WnaXNsT9PnZiUmZZYdYfl3VNOsrHJSFpIUkjvBEB1RhTIXjnoNdncIYbwhmLQXqw6fZINVBbMo8Sestx0LLe9z1k7mMzz0q2H%2BF3Iam8MeGcVoqONqtVvbJjKpUyYUlMu8B73LBxBCtXkg78knvjnx%2Fi54jp2kKoU5njjJ2SW2GloVP8AWUnlYrCQs%2Bm941PN1KZmnXHnnluOOKKlLWoqWsnmSTuTAZR7p%2BPraTjOv27vZib%2FAKyN88DGbaqHxRYOquYuZz9NoLSJ3xh6s1l3xUqMurQlXSLKblVrX7Y5UDytVjHZ%2FBtltk9mPw%2F5rSObFMkZcTdXpVEpVfeZu7Rp2cSpuVdSvmhHjBbC%2BwggHaA5ZzRmmJ%2FMDENQlX0PMzNUnHG3GyFJUkzDhCgRzBBB9cYnHTfH3lthzK7OWm4Xw%2FQafRlS2FaQJ%2BWkGQ0w5N9DZ10JGwKlC5PbtHMkBWlRqWU2vcEW747C8IagoquUDINyjLSj7dvJyOPpU6XL%2BYiOv%2FCIq%2Fsjymb%2B0y0o4%2F0kBxw9zERREHucRQbQHWHg5MYYTwXnVWpzF2I6dR2J3CFUYYdnplLDbjtk2bClEAqOxAvfY90aSms1czpZ95kZi4pFnDcCvTZF%2B4e%2BWsOyNw8OWUtFzH4V8%2BaoMCIxHiiimk%2BwDjUut6blnFuErDIRvcgG4sb2jnGsSE9R556mVKTmJSblllt6XmGlNOtLHNK0KAKT5iIDKGc280lLTbM3FjSwoFtaa3NdRYNwTde4BHKO2ce0zGvFvgKh8SPDpWJ1vMGk0JGFswsL0yo%2BLT7gQNnEJCgHmlDUoJPlJIKTqSRHzxQ5F%2FwljzFmX9cYxPgvEtToVVlwUNzlOmlMOhJIJQSNlpNh1VAjzQHSGX2UnG3jGWcyhoUnmJSMPTi%2Bjn2Ks%2B9LUuWbUTqW4XTqKRz0JNjGTcVebFMyvoeC%2BHXJjG9QTJ5cyJYqlWpU6uXE9UXLKcAU2oakJN%2B0i6vNGj8U8ZHEnjOjroGI85MSTUg6nS6yhxtnpB3KU2hKj8cafcnnHNlm8Bnfu55wjyM2cYj01qZP9OOpOCTOmsvyucMrmZmrNzCHMCTDVLl65WVKS6%2BoObMh1W6%2Byyd944dQ4DH0I4Z%2BG7IvOHh%2Bywmq7Q6e3jqpYump2TfeBPs3K0%2BYC5unuX6pQqW1EWsq6Lg84D5%2FVTSqYKkLKklKbKPb1RvFtNibxtzilwxhnBvEDj%2FDODqainUSn16bYkpRu%2FRy7QXshF7kJHdftMagUbHaAHaJSbxFR6sS80XgJkc4qRTRFSAqtG0e6U2Vcx4Guce9nqiAzmgpKqOsn7c%2FijzULScy8J3%2FAGdkP9OiPVh9QNBWe0rP4o8NHJTmNhRY%2FZ2Q%2FwBOiAxuq7ZgVe9%2F7cTfPn%2BiVxf8JAKzdpI76zJj%2FOIjwVinSrOOa0%2FPzKmwmqzl9CdZuJhfZePVl9MNT2a1CmJfUW3K1J6dSbG3SoHKA%2FSNCEIBCEIBCEIBCEIBCEID8%2BnF0nRxAZkIT%2B2mo%2FH4w5Gj1foEW5lKifjMb14xE6OInMxKezFVRt6fGHI0U6LSLduZbN%2FujAZhhr%2B1V%2F3v5Y9brTTyFNPNJWhXNKhcH0jtjyYa%2Ftb0f7kKi4pBUbJBJJAAHMkmwAHaSdgID2V3EFdxO%2FITOI6vNVN6lSDVLkXJpzpFS0o1fo2UE7hCbmw88WyMukctcQ1DAGKcx0uykrTsI1SRpE9LTSlNzSpmaCihKUEbaQnrBVjvsIxqep1Qpk05I1KRmJSZaIDjL7ZQ4gkXF0ncbEc4DzNMTEy50EsgqUb7J3Meo0KsJ8qnuj0oivh55MtWWnXFaEhCgTGcpqlMJSVzaNR6wuodlr3gNcTdPm5QDxuWcZvyKkWv8cZPlnk7mFnDVJmkZeYdcqTkg2l2dfUtLTEohRslTriiAnUbgDmbGw2iOOqhL1Bpro30r648lV%2ByMp4Y8Q16nZ24FwtTq7PSVJr2KaealKS7xQ3NlsOdGHQPKAuoWO28BrnF2Fa1gXFVVwXiNhDNUosyqUm20LC0pcABIChsRYg3Eds5JH%2F9Ga3EJB00quqJ7L2djl%2FiVbUjiFzGLibL9sUzdPaOqiOocjf%2FAIN16%2Fg06vX%2FAHVg7vHzT4UP1fdp8FtH8lbrYR8pX%2FDPucjZcMqcyXrK7CzWIpFRPbdUmR%2BSPdIp1O6e9twf5tURyqpdZRlHXqg%2FVcPM0F6ZklKkZh9Sao%2FOBo9G7LISCktJBsvWRyNuQv51zCZVh95V7Blwbc90KH5Y%2BkWcZ0uVO1pvFoSlmlgJ0kyYWRfcEqPPzxjIeUFWvGa5o4FrOWeNqpgHEU5JTdQopZbefknC4wvWyh1BQpQBI0rT2De8YKrquRaEPWiZvsYLUFG948oVEdR74kekOgC20A6D3R5rmFzAexKx3xVDiYt%2BpXfEekV2mAuKZhzo9IF97x0IdLS3F3trQvfuBb3%2FABxpbLHB6sw8eUTA%2Fs1L0lNZmgwuemELWiXbCSpThSgFSrJSbAC5Jjbzk7LFkzGouMaHEpUlJTrTpKQrSd032NjuL2gNJV4IApxSpJCpFBsDuOsoWPn2iyl06iIzXNzLqo5T5g1bLur1KTqE5SEy%2BqblAoNPJdl23kEawFX0uAG45gxgp5wHrS92Xim9ZTyTFDURfeHSXse6A94WByIicObc4toWftonCyPhQFyDtoj01ot%2FSkdsA6b84C5iYjoAFaXG3kjfogef7jeNL5YYPOYuYFAwEKu3SxXp1EoqecbU4mWSblSylO6rAHYc43M7MtS6VrukoaaW1cDZWlJTqseV7Xt2XtAaMxMEJclCkpNpJpJ094vFh6cXteM3zay5m8qcfVPL%2BfqUtUHaciWX41KoUlpxL0u28CkLAULBwA37QYwK%2B94D1pe0nnFEL1PXine8B1dxAe1Lhiql098W%2FpVQ6ZcBcg%2BRyibxg98W5LpPMmJw4k%2FCMB70TKlLSm%2FNST6rx0E5qXiJOtVipa9%2B4Fk2%2BSNMZYYOTmJmBQ8Brqqaa3XJnxZycUyp7xdASVKWG07rICTZI5m0bafqbBqjs5crZQhbYV0ekqT0RbCtG9jbfTfntAaTxUWiuW6NaFfmNGrRyBuraLI24e%2BM8zyy2eyfzKreWz9al6qui%2BLJE4wyppDqXZdt5J0K3SQHbEd4Ma91kbQXe1LvYYpJI6a8Uel88Aontgo93SfuodJ%2B6jxeuH8KA9yXNvKiolw6djFvSdvKMTpUexUBdJN7W60nXzWj5VARuOcsibWO24P8kRrfKvBbWYePqNgt%2BtJpLVSLvSzpYL3QobbU6ohsEFZsggC43IjYU883MPOOyxWUEnoy4nSoptYEjsO24gnNkWOk24X5A2vqzJcN%2B61LG35Y6%2B4HlBXDnSrHk3VQfN%2BaDHN1KyfxnnBkfiGq0jHOHqZh%2FBVYbqKqC9JupmH3nGEtmZL4SQpRSFJCb2AHIbR0pwTBaOHamNuJAKG6qNuR%2FNZF%2Fkj5p8JFUdx2cf5lPsqdvCNtU%2BafbDgqbFqhMDumHx%2FnFR0DwOW92id539r85%2FObjn2b%2FthMf%2BIf%2FwBIqOguBz%2Flonf%2FAN35z%2Bc3Hb00n8gW%2FwDDuamH%2FpNPpXLPCVMzxX1Rgc3ssXgPvKo0PP8A6EeQna7RIPqMdBZy0rE1a4yJGRwxPYap7ysGNtzkziSYUzT0yXQul7UtHWSsgWSQDv2RoOqolXJ2aFL1eKFaugCiSQgnbc7nzHtEbOhs54Fdv4YYb5H4%2Br0sZzHShftlca20OyCEDuJYQSI1Qlelwxt3OLBtZpNKpGYrs%2Bwuj46mJsyDDT5LzZkC0w4H27WTcrBQQTcX5Rp1Z0uGPTtR7fGFWHmjzTLiXnRfsimZkpOkxTKwpWqAmUTrFuyPUlfVEePzxUQvbnAevXZOwg28QdwYoBza2q0QK7Hy4C7tzqlEAnsMbLoadWEaQ6BbXLvkecF0gERqBqbQklS7kIuqw7duUb9r2CJjLkSOB5muyNXmpCSQ4%2FMSSXAy25MJD%2FQAuAEqQHACQLXO17XgnNhmaCAsVKYWB0rdYQwsgbbSqD6%2ByNctzFo2hnPgGqYbpuHceu1OWmKRjvx%2BcpjDbyi%2Bx4o8Jd0PoICUqKxdOm90kdsamuO%2BCYnN7kzagCm20eNa%2FfSq0SF5INokURe8FVfpBECsGKF%2FPE19oCqhW8ehKwOceJKiDFTpPPAXVudWrYqMbWoTa%2Fa5TG1fqS%2BztKrxplMylkB1XIR0LV8GzOXhksGT9alqrPU%2BWbcnJmWCw0HXkId6JJWAVaA4ElVrEg2uN4DX2bCCJyamAk9SqutX7Cnxdo7esxr9Dlo2pnjgasYbZoWOJqoyUxRseNzlUpjDLylOyxYdEs8h5JA0q1IBFrggjfsGptQgK5dOkiPKXLKJgp8cook3MBOt5SuyJmiTziloSfhRMEW5LgPUFEDsiq28Wt9MeVJ28uIhzV1dUBc25y%2FKNsyqCijU0H9bG3o1qEaZlFqTMNhKdRWsICb8yTa0b7xPhR%2FAk8nBM5iKWrVRokqiXqExLNuJZbmlXcWwhSwC50YWlJWBYm4HK8BrzNJkNzjXUsUTc4i%2FeLoP5YwlDlhGy86MAVzCzdAxhOVKVm6RjmTmKvSQ26ouMNtTBl3G3UKHUXrRewuCCN41b0loJh6jMnSRaPLrN%2BUQLo74lPPyoIT6rdhiVSz3GIWv2xDR5zAQS6Qu8e5iasY8BSAqJ0KsqAv0nOLW4hOrtA%2BWNpygKafKBQIIQoEH9%2BY1DS23ZqflpNlQS5MPNst35a1KATfzXMburGGZ3Bc87g6qVOUqE%2FRVrlJuYk3CthToWSoIUQCq17E23IgMnwWEe5VnhqPWGCWikf5Ql4z3wbCB7IZgrK7WlKQNPfeaVv6rfLGLZXZeZiZp0nFWWuVcph12pYmoC2amKvUhLPGXZmm3dMqkmxV1ElRN7AnlGc%2BD%2Bo85h7GOZGHqpKhE3KNUptwhwKCVpmVgp22PPn5o8Xp1OWCW%2FniP5qXWwn9Jp%2FrkYZxiA%2FVEYrUrmfFAPR0O0YTlQP8AhRwZ%2FwDvDIf6ZMZrxhf%2FABD4qv8Aayn%2BhjC8p21O5qYKQjma%2FIn4nkxs0z%2F61Tn5H%2FgwU%2Fpf%2B6Pa6f8ACGD%2Bw%2FBB%2B1xux%2FoY5uzfa6LNzGaO6uTR%2BNUdM%2BECkqjUcF4SkKQ0wudexww3Ll0dVLvQEoub7Jv5XmEc%2BZ30iapeYc8xXKlhudxCffKy7hycXM05c0o6joUsakrAIC0bgECx325nwbTngVP8VS%2BJx%2FaamBYqWFYBkkLdVoQ5VDpPIKIYtb0xpdt%2BN3YgwbV8WZYVmvUaZlUMZfNqqlWZecKHX2JuZZYb6AAELKVDUsG1gRa8aNdIaPKPfOdk9KJogmKJcuu5MeZUykGwIiHSX5EwQ9hf2tFMrvHnv54jqMB6kOWHOJ0zCgdlx49ZiBXY3gLmH9oz7LcKXRa%2B6FJAS5KoIPb1zGr%2FABgxu7BmEZWg5YyONTiRiYmcWTEzKilJlnAuWblHgOmU6eorWSRpG42vAW7HDF8Lyy9SbFM4qx57OND%2FAH9Eaw6SNzYnwG7inKit5hSdUlmBl89LonpR5K9c01UJoNoU0QNN0KSNQURsra9jGkFuW5wHqE44OqTsImYJSiPB4wiIF1R8lxQ9EBc%2BlibpQYtQcN%2FLVE3Sn7dUBci7blaHjJA7ItvTfujEqnyPPAXEzar842FlwA5T6me5TA%2BImNXNOlagPPG6sGYYlMPZeUnFq60qYnMXF9YkRKrSJNmVfLYUp09VanFEkJHIJ3gPNmihKMJ0kXF0pfCfOfGN41QHiO2N34%2BwOjFOUczmVKVdplzA03K0udp7jCgqYbn33FNPNuDYlKmyCk22ta8aJ5bwTmqPPqUg7xWYmAGgCY8pWkgiKPSEEAQQufjKe%2BHjCItvSGHSGAunTAi4IikuZWDYGPB0p74j0o7TAezxqNmZdBCsKVJ1RTqE5Lpt27hX4o1OlYKgO8xvCgYPksJ5fUCutVt2cncay3so%2FK%2BJ9G1JNNPuspSl0n3xZKbkWASO%2BAs%2BaSEJw3SApSUnxMKACt1fmpfMfljWHSKjdOYOBJet5RO5sNVhCHsOVSSws9TXGDdxMyH5hMwh0HaxRpKSPPfsjSGvzwHoL6gm14p9OQecUCs6rQJ9PxwHrQ8TziqHCe744t1%2FTEbjvV8cB7Fum%2FK8Q8YIHMiPGT%2B6V8cS67dpMB7kzij2xtTLoJXR3HkKSrpCi9uw7gg%2FJGn0OWJMdCUnBNNwNhihOylamqhM4pocjXpkOyyWUS3SlxKWUWUSsJ0C6ja9%2BUBsjh6CTnng4%2FDTNTKk91xJvxgXAK443n5Sg2UkOUWpoWrTeyS2bkd3p88ZZlDSqriDHtFw7hvGbmEK7U6giWka43TfHlSwW04gpS32FRXbVvYX9Me7hey2msp%2BLuoYBdq8tPuUaj1WV8bZCm0vANAFSUqF7m3I8t44Ok05YXbT%2B7Psb%2BHZd0UR52W8foPul4NVfb2ooH%2FqFRzAR2iOnuPsE5m4RUBYDCLYt3Hp1XjmKMGhs%2FkO7%2Bif5pYr5rvFfplTVEEgxExMlIO0elaqER0HvMdBnIPBQ4XcF5yJnqp7PYgxTJUaZb6VHiwZdnlsL0i2oLCE3Bva%2FwAUZ9m9klwYZJY09o%2BYWNcfyc%2B5KioN%2BLIS8gSxeW2DqSm2q6Dtz5GA5ACILFov1RpMjUMaTFAwImanpKfrJkKCZoBD8wy49ply4BslRSpOru3jppXCRkczjmX4fapnXWWM2n6WKhdNPSaUl0oLgaHwldVKjp1ailJI32gORInsY3NgPKfK2jt4wqHEfmc3hBWDqi5SXMP03Q7VKg%2B2E63mkq3LN1p0EC6t%2BVov%2BanDDTML17LNeCcedNhjNNVqfOYhaRJPU0BpDxW%2FyBQWXNQJAOoFJFyDAc9RAjtEde07hIyMxvWcRZa5XZ21Kr48w3TUz7ilyra6W8V7ISFoJ6uohJ0qJSVC4NjGA4AyPy1lMlJTPrP%2FABVXaBQa3UPY2lU%2BjyyHponpFtl9ZNwUXadUAkeSi%2FaBAc%2FRTcT2iNu8SmRMzw%2F44l8ON1v2do1Yp6arRan0QaW8xq0rbdSLgOJJTuDZQWki24GoSQoXBgJIQhATwhCAjYd8LDviWx74WPfARhC474QA8oDlA8oDlAQVEE84iqIJ5wE0UnIqxTcgKNj3RBI7LRUA2iAAvAInREp5xMiAnQu3U16kxUQ4HSSVKChuFIWpCvugQY88TDqmA9C33ynovHJlTX2jky4tPxKJEUriIa%2FN1Yp3PSW7IDMMus0sf5UT9VqmX2I10l6uUxyj1IBlDiZiTWblHWB0KBNwpNiN4xFGhttKG%2FJbSEJT3AbRCEBPcwuYkuYXMB7XaxWH5YyUzXKo9Lq2Uy7PvLQoXvYpKiDuBzjxrXeIRJAThUVAoGKIG8VByhA6D4XbexeKlJvqSpnke5pZH441tgKqVuS4sJ6Wo9cRS5ddSm36g85KCaSZZplanU9ESNRIFhuLEg3jZXCuUGl4qKuanGr%2FAHtVo1DhyqyVD4pKg7VFvNszk5Uab0jbRc0OPMltBUBvp1qSCewEnsjzVznPF7f7Pc%2BwaQfg6DXD%2BKPZWzJlspfR1NItcJJvYHcCLXxPsdNlplRPJWrSBXpcp7LomGlX%2FlRe2wrpR0idKgLEdxG0WniYV0WVOVUsE%2BUrELxPmMwyB8dvkj0r49DmbpREOkEea5hcwSrKcimpZPbEhV3xLzgKnS27Ym6UmPOpVjC574Cqpy%2FbFWUR07b%2FAEjmlKU%2Fa3jxEk849UrqLTxTyKDeA6wxnKqkJjDNNWrUqVwrR06uV7ywVf5YxviJk1sZcZR1HpLtPyFeQnzqRPJ1fzx8UZdmOwr2x0l4m4OG6OB5h4m3%2BW8WDiWaSzlHkw0m%2BoUzELir8rGooAt6xAc4pfA7YldfBjyFRG0SlR74Csp%2BJC6YpkiJS4BAehLpEFOXjzFwDsgHQRAVVuXidhqYmJZ51CkgNoOoFXZHlKyYuchtKP8A7pJT8kEw6pzDR0WI6ZLK%2BysYcozbu3whKI%2FJaIPYhVhbKPGVWYo5qjj0oinPpEwG%2FE2ZlYR4woHdaQpCU2HIuAnaPdm4gIzCmUJ5Jp9NA%2FBGosFeek5TJTMBx6YaacmJORl0BawlS1GbQdKAdybC5A7BfsgiG9%2BAQg5WzZF%2Bq7Pk2%2FvJMcSVYpU0pTYsklZT5xrVHbfAWkIygnXVEi66gbjmCGTHEdQ%2BwncHde47euY3pjLDrP8AilyrCfyjbeiGGKVBKoKTBKY0XVTBOqIhsje0ZLh3B1YxI4pmlSbswpATqDTZWQVbJACQSSTsAASTyjpTJzgkncZUWZm8xKzM4TqU8lHtbp82yEJmlgkq8bv12EK8lBte9yRtYhyUgXO28VgxrHnjpWawmnLqfqWCp7BtLkZiQeXLzLE5IoemUdwLqrk7EEKHMEER0jlJw0ZH5y4HZreIsGMys7NulCpqlumWU2UNBtIAF0lOwWRbdRvAfNQsWNrGJVN27I7P4h%2FB742ylo0xmDg6cXinB7G8zMBnRO09Nrlcw0m6ejvt0iTbvA5xyVVqS5KOKS4nT2wGPLBESR6HUARQsICEIQgEIRBXKAXHfHpk5d6cm2ZSWKQ6%2BsNN6lWGo7AX852jxXMVUHvMB76nTpylzJl5xlTaxcEKFrEbEekG4ieiU56r1aWp8tJPzjjqtpaX%2ByvWFylPebAxkuF3JPG8zK4Wrk7Ly06%2BoMys7NPdG26bdVDjh2Qu%2BwWdjyUeRjE20TUnNhTK3mJiXeISpKihba0HncHYg90Be6q7SazRV1Wk4Nco7ci%2B3LuzTTq3mHFKCilDhV5DpCSRbYhKttox6LlW6lWJ5emqvO63SH13ASHSdwtQFgo87Ei%2B574tUBfsKJvPrP7iMwDZTtFy4X8pXc5MxV4VNXRTJZmRdnJqYKdS%2BjQUjShPaolQtHYkzwO5YSyrPY5xChXPdxhJ9NiIDiuIgG4jtWncEGUUysXx3iPRfclyX3PpEXxvgSydUlKVY%2Fr6iTt75Lgj4hvAcLN3DfriKRzNu2O%2BpTgFydmB0ace4mUpXkhJYOg9%2FLeLovwfeSr5unGmLEiwulHQEX7bC0Bw3lK0mZzcwGy%2FqLa8U0kK02vbxpHfHsznV43nLmDO3v0mKaqb25%2FmpwR3DQ%2BA7KPDOIaPiemY4xcJyiVKWqculxMupta2XQ4lCwEg6SRY2N7RJX%2BBHKCv1%2BsYifxzixt6sVGYqS2tLKkMrecU4tCdt0hSja%2B9oD53obXaJVN2v3x36fB75RabpzFxcFA6r9DL209oItyiQeD6yiAVfMTFaSfJIaYNvjG8BwEltSz1TFQAtjc%2FLHfqPB85U2%2F5RsUuemXl03i3zfg%2BMsVq0S%2BZWKWTfcFiWXtAcIE37YlU4Ux3mPB85WLTpTmRinVbmJaXMcsZ%2FwCRVcyIxXL0Oo1Buq02py5m6TVGmy2JlsK0rbcbN%2BjdQq1xcghQINjAapmHS4y5q7B2R11hKcWjDNF6tkpkJdFz%2Fex%2BWOQX%2FsS%2FQY6xws637AUfX%2BspfqlVyD0YG3mjJYx%2BMifNPuYrx8l9se9tnC1UTKT0o64pOggpWm2yr%2BeN%2FwCU2MnHCvCVSWkqlQTT3Rt00v8ABSe9Sb29QjlaVn3WwwttHkJ0qT3RluFsbs06dbM5MOMusrC5V9N%2Fe1DkFebsjbn8LW59nPBl2I5MRzxVeC7Kuu5jnF9SW8mgvP8Aj01Q2h73Ov8Aa24snUEKV1lG5Jtp5GNkYNzIp%2BIkGSfmJdudbSNQQ4Clzzp7fVGWmbShsOrNkcr9kKuFVTNnnqna2KK4oqi05Yaz4ipTBkngOuYmqeD6TP1yalkyErOPsXeZSeqlLahYoSlN7Aco4srWd%2BZ4y5qeUjtbYTSqs82uoTzUqlqoTcs2gJRKOuosFN2SAVaQpQuCTc37C4k6xSzlxNMCdl1vCZaAQVgqub8hzjgCqsVquVBVHwpS5iq1BXSLDTQJCEJF1qUR8FI5neOhRTRd7vTVMZTm1oibza1Z641MKxNMLEomQkUDp5shloJHI%2FNFeRpyZCRZpzW6GwSpR21LPlGLhT6Iin3nKi8JicIuCB72336RFRxbfSRzbXOqc29TVERwYWyo38QmNCPIbOrl1trfJGKNnqjqXjNpssKkZxve6W1G9ue0YUyglI3jFK8MFxIpn2yTy3GwoIKBYns0gxccbSDdPxC3Kod6QKk5Z3V%2B%2FbSq3qixYmUTiCpj%2FtLfEBGRZgL6TEMu7%2F3dJI%2B5ZAjBLLDN8kmsIIxjSTjLDSsR0oKV4zTEzhlC%2BChQFnkgqSUqsrlva214t2YErQ0VOafw%2FSXKfKPPKU3KPPiYLKCo2RrKQVWFhcjsjzZbOaMQU8%2Fu7fIYhjRw%2BMK%2Ffn8ZiBjKXLAIUxLJSBayWE3PrtHmmnGWykIabPf1BEXndI5xbpiYgLlL1GXC0Jmukbav1jLttlVv4Qj2rqGE0NoMqzXw8AdSy7LhJPZZIRt8cYx0ioh0kBkM3UaJNLCpiluzzoGlD04%2BSUJtYJCUaUxb3nG1qs0AlACQEjkLRb%2BkMV2XE2BPwdzAbW4e8naznbmdRMvaOpbJqTuucmgNpOSR1n3yeQskWH7pQjsrwgObtFwNhih8LmWwbkqbTJSXXV2mrWYlkJ%2FM0kbcyd3nPOU35xsvgNyPmcqckHM1WaVKVTGGPpAT0i2uYS20iSTcyrBcIsgLWNaz3AAjaOecX8A%2FFrjbEtTxXiWWwnO1Krzj09NPe2NsFbjirnmNgNgB3AQFk4bM7M3MQUKjcMOU2EsvkTU09O1NqfxBJqmzNTSQXtam1%2B9JdShOlCiD5I5GM58JLmrjBzEOHMmn2JuToFEkWZ9SlJSy3V5tbYSuYDSLBLaDcIBHNSiOwxSyh4KeLPJ7Mih5m4foGCJieoDrjzMtNYiQWnitpbZSrSAbde9vMIs%2BM%2BBDjEzAxJUMX4uThmpVeqPqmJqZexI0SpSjySLWSkCwSkbAACA2TwG5k4bzlyixLwkZoqTMMy9MeNKCzdb1HWq7jaCdy5KPFLqLbhB7hHCucuV%2BIMo8d1zL7FKAalRJtcu46gWRMt82phH7hxspWD5yOyOocCcD3GHljjWg5h4RpOFmazhydbn5VftiZsvTstlQ2uhxBW2odyjG4PCMZKoxvljTs%2BqfRPYyuYXZl5OuSqnAsqp75shGsbOKl31FKVdra9uUB8tHUkKimeceiZAC4oAb3gLxhvHOK8CT4rODsRVah1AILXjdNnXJV7QfKRqbIJSdrg7bCPTinH2K8xJ5Fcxjiis12oNMplzM1WdcmnggXISFrJOnc2HfeMXebUTcnaKsojynDpT8HT2mA9IVflBJOoxKAb90X3B%2BFatjTFFJwhQWG36nW5xmQk23F6EredUEpBUdki55mAtMSLuT6I3XTeE%2FOSq1CvUmVoMg3N4XxPL4Qq6Hqi0hMtUX1lDQ1XsppSk26QGwuI1NW6LPUCqTtEqzAZnadMOSsw2HErSlxtZQoBSbpULg2UDYwFrHOLlJ42rtJpVQw7T6tPs0qrBoVGRamlol5zolami62NlFCt0nmDyjwI%2BybiLe%2BwttxcBleJMb4lxzNiu4qxJU65OhpEt41UplUw%2FoQLJSVq3sBsIsZcudooSnvcur91E45wHsk917R2B4RgacYZYJ%2B1y3pA%2F0kcgSF9Yt3%2FljsDwj6wccZcJTyTl3R7eg9LAccL5wUbbwXziVwXTAZRgnOjMnKxycGXeOa9hxFQ0eOClTypfxgpvpKwLgkXNjz3MeDE2MMQ42qz2KMV1qdrNUnCFPTs650j71gEgrV8IgJA9AEYspsuO6CLR7m2i3KhPM3gK3SEmJr3iinsjNMrcq8aZx4rZwPl5RxU62%2FLvzLUsXktam2UFbnWWQLhI2BO52gMRiW5jbOGeGrN7GeFKbjTDOF0zlJq7NTek3TOMtqc9jxeaTpWoEKSLkA%2BVY2vGqX29BgJUvJa6yztGQ0jOrH1AlKRTKFi6tyMjh6fXVKOyzNFIp82u%2Bt5gAdRSrqvzB1EEbxjLiOkbUi0WzxdfeIDLcU4mrmMKvOYrxBVpiq1KquqmZucfILrzqvKUsiw1eqLDe6o9DbK2ZFvUrZKTceeKI5wESkkREJ2tE45RAnsgJeUTxJE8BUbFjePc1ciPI2No90snvgM2w%2FwD2kA71R56DpOY%2BEwRe9ckBbzl9EemhjTRT5lfNHjw6q%2BZOEx%2F37If6dMBbcd0qpUPGOIKVV5VcvNNVKbWUKNwpCnllKknkpJB2I2MRyjKVZlYYT31qSH%2BfTGwao%2FQMQzFTwfjNbctItz84KRWSCXqMtT6zpWRu5KKUesk7oJKk7XEYngLCtdwfnRhigYikFy8y3XZAJXsW3kl5BS42sXC0KBBCgSCCDAfo3hCEAhCEAhCEAhCEAhCEB%2Bf7jTTo4k80E92Jp%2F8A0640G8bSTQPNTZP8qN%2FcaybcSWaB%2B2xTUP8ATORoJ5OmnNX5hs29Sv8AXAZdhi4lBc%2FpQ%2FHG8%2BEWSpk%2FxFYVlajJSs3MJaqEzR2poAtLq7Uo4uSCknZXvoBA%2B2AjRuHNpMH%2FALNH5YvclOTtNnpaqUydfk56ReRMysywvQ6w6g3StChyUDygM4XmcBktmZgDH79UmMbYpxlTa7OTDzZ0pdlul8bU8s%2BS70irBNt%2ByMv4qZuq1ZzKzEmMG1N47rOX8hNYr6QaH3nwtaZd59O2l1bAQTte1o8r3FBWajOMYmxNlBl3iHGMrZbeI5%2BQUl5bwtpfeYQQ084LA3UOe8arxTirEuOsSVLGGMa1MVat1d4zE9OPm6nV2sAByShIACUiwAAAgLKoOKWQm5vEpZf7Wl%2FFF5wxYVxm58kE%2FJGf6gvmr5B6oDUxaUk3II9Ii%2F4HpmN6hiiROXElV5rEUisT0maS0pyZl1oOzo0g6bHtO0XfG6L02VWCnUh%2F4PPcRnXDhO54YiNayayYq0vQJXEym5nEWIW5cpmaXKJsNZmgQW02BCWxupSjbtIDVGKmcUS%2BIZ842aqaK888p6f9kgoTK3Vblbmrck98drZFgO8Ha0nZXsdX0%2BmwdjSHF%2FmRg3MPHdIouDp96tDBVLFCnsQvIAXVZhBGpZI8sJ0nrciVKttG8sjEKPB4AyNalU6vbep6%2FwCWPm3wm67hdo%2FzY%2FkrdbCYzrr%2FAIZci5d1%2Bjz%2BW%2FtR9kUprLb8tPMShSq7rLbKtZCraQRvsTfYwfYcm5Z%2BWZAK1trtflYJJPyAx6spqi9I5C4r8VUllc%2FXKVLPPJbT0hZDCl9FrI1BBVuQCL7XvaPKy4daiCRqbcGxI%2BAruj6PZ7HKnawviNxjhvH%2Bc2JsX4PqLlQo1QXJ%2BKTK2FsqdS3KMtqOhYCk9ZChuOy8anc8uMnxHKy8uZNUs2UJek2nSnVexN9h5oxlwdeJhCkVb84avPApF4hpESJ9Xphq9MSaRDSICpr80NfmilYwsYDPslcUUfBuaeGsUYhmnJam0%2BbK5l5touKbQptadQSNzYqHKNluyr0y2uTlk%2B%2BKQsNJOwPvZI9Vt456RdSgg8iQI6XIWxUHEsLspu6dXobIP5YDAOJDGmHcxc6sR4zwnU3qjSZ5unol5p6WVLqdLciy0s9GrdIC21AX5jftjVLhN7xkuIJdhkyqpcEB2VQtV1X61yPyCMad2O8BT1w1xLCAnDkTa4pQgK%2BoQCt4pX88Rue%2BAzjJ%2FFNEwfmlhjE%2BI3HkUynT4dmlst61pRpUCQntteNtvS79QPi0uQVzAVoJ5EaSq9vQL2jm1Bu4hJ7VAfLaOoUKZbmEp1dG22gpGncgdEoAene0BrXiNxzh3MjN%2BuYzwk%2FMO0meZp7Uut9ksrV0MkyyolB3A1tqt5rHtjVKzYxf69KNyjkuhlvQlcq04E3va4O1%2FVGPuc4CGvzw1%2BeJdJhpMBOHO8xHXFPSYWMBW1jvh0nnilDlAbAyOxfQ8C5t4Wxdid99ml0ydLk06w2XFtoU2pGoJG5sVA2EbHl5Kanp005ACnXA6StA6pAQpZUP4IvaOfWOu%2B0PtnE%2FjEdMuMMe2J9HR%2B9dI4hSf3JaIgNfcTePMO5oZ2Yox7hF2Zdo1UclUybkywWXHEMybLJWUEkpuptRtfkRGpHNoyTEEozKNSYaB98lEKNzffcfkEYwvnBdEKiYLikBaJgIKKmuGuJdJhpMBV1%2BaAcIilYwsYDPMmMZUXA2ZtGxPiMzIpkoJluZVLIC3EpdYcbCgDzsVgkd14zz7Br179EnSrTvtbsjSNLbbfn5Rp0XQ5MNIV6CsAxviZQgT00kDq9IoeoQG5cCZ6ZX5Q5MZiZdYnnapN4kxT4j4qzT6etbDDiUFZQt5RCSQlaCdN%2B6N%2FcFbvjHDnSX97Klqpa%2FP9Fq%2FLeOQMyVuI4XaEwD%2FwDMJxz1mnAerYD4o684JSpXDZSVKttK1FIt3eNq%2BePmnwkRHcVlOW20pjqqdvCdXD9HvhwK7%2BinP787%2FpFR0TwMp1Z0T%2Fmw%2FNfKtu0c7O%2Fopz%2B%2FO%2F6RUdFcC9xnROH4KqBMA%2BnWi0dzTP8AUNvH7se2Grh%2F6TT6Vxz4xFh3C%2FFqiexHWWKZLTeCpeTS88lRQh9xLiUA6QSBbtt2xomc%2FMTz6XVC7NypSTdJG5uD3WtHQ2b6TK8YExURLsOOSuWTs5KKdaS70T6GVaXEpUCAtKhdJI2IBjnJ196cemX5uYemXXlrW668rUt1aiSpSj2kkkn0xm0LiIwO7ZeLDBfZ%2FHVT55Vc%2Bq9QTlvlrgNifK8RYbdrz1ZktCwZITTzC5dKiQAVKQkqsm9u2OfHlHpFRtjMhpL81iKefKn5sVKXa6daipekMJuCe3%2FUI1I8TrVHqWqplzfeIdJEpBvEICoHInS5vFCJgbdsB6NdyRflEhWCCb8op67Em8S6jYjvgKqz1FD9zHT%2BZmLKFjDGMxibDc%2BJ2mz7Mstl%2FQpAPRyrSFpIULgpWkpPojl3stG66SwJXCdAQ2kJQ5Si5YfbqcJUfXAXziAxZhmrZdZWYKpdQcermEpCtorksphxBknJmodIy2SoBKiWxq6txvHPy1ERs3MptEw%2FVaw6FKm3qsWHHFKJuhLCCE%2Bok%2FHGrlkd8Ewa4a4pWhYwQr3ENXnincwue%2BAq6vPDV54pajDUYCo4Spopv2GOn8f4uw9jbF1UxhhucXM0upBgy7ym1NmzUu22oFKtxZSVD1Ry30kb1pTctK0OlSrDIQ2ZFKtN7jUoXUfWYC5cReK8P1HBmW2B5KfL1XwdTapLVpnoVoEq%2FMz5eba1KAC1dHYnTcC9r3jQBdvteNlZqtodfmqiVqXMO1J9t51ayoq0staQb90auuYCcqJMNXmilq80NXmgK4X54mC7R5tUTajAV%2BkEOkijc90LnugPXLvllxp0n7E6lw%2BgEGOkszcQ0TFuYNexThqppn6RWpoTkjMJSUlbRQlJ1JUAQoLSsEEcxHMXSRvoykpIsU6WkWAyymWuEA3AJcJPy7wFfiCxfhms4PyywtS59UxV8IYen6bXGOjWkSk05UnHUN6lABatBBOm4F7XjQnSeiNhZvMspqr9QZv0s1UJrpVkkldiixPoBtGuIJhPrERDlop%2BuHrghWDsTBwR54mF4CqpdzeJNagb3MSk2iUmAu1CqDEhWqdPTbhSzLzrDzirE2QlxJJsOewMdF5g1WlYgxzX8Q0GpMVCmVaovzsnNMk6XWluKINjuk94O4jmenBC6jKIcRqQuYbSoX5grFxG%2BW5ViSl2WJVoNMpC%2BjQDska1bCA31wl4%2By9ynx7MY6zNxvSsPU12g1GRlzMLUqYdcWEoBbbSCSLgi%2B3IiL5wOVGUr%2BZOa1apV3pF5VK6J09XZU06oGx7wI07SJKQqGRWcjs9S5Wacp%2BHpFySddYStyTX7JMkqaUd0E3IJB3BIN42B4NZDnstjtWk9GWqQm%2FZq6Z3aPF6fU54HbTy%2Fg%2Fz0uvhH6RH9cjEuLsn6oXF6TvZ2WN73%2FSE7RiGUes5tYHKdW%2BIZAbf30RlfFt%2F8RGMd%2F0yV2%2FwAjG8lxqzcwQi1wrEEkD9389o2NmjNOfkf%2BDBT%2Bl%2F7o9rqnjtrknQ8OYInKgro5VOPGpl52x6jTUuoqO2%2FJXZ3RytmFNSNTxhVq5SKmxUadVZx2alJthRKXEXsR1gCCCLEER0v4QxH9hOBmJhAKZvGsuqxOy0dBZQI8940Jn1UX6lnFilTgDbMtUHZaXlkIS21LtpVshtCAEpFyTYDmSY5vwcU8DA6ZnbwqvatidczeKoWSWxBQcNZOZpSFdnxJzeM6NJ0ygsqbWoz0xL1Fh19KSkEJ0N73UQDyjmqed1r2jdGOmG38Fy3jAVrk1zTzHXICSotBW3LcRpBy%2FbHvmgkiKTaKcIKKwcibXFEAxEAmAqlyJS5EhFolPOAqa79sdAYUxJh%2BtZO4Xw7Izuus4YcqYqMsppSClExMpW04lRGlYIBBANxYRz1G2MsGm0YSqM2lkdK7OtNLcN76QRYei5MBsWexLh7DuQuYGEapNONVfHDtJRRGG2FKS%2BiTni5NKWsDSgJBTa562rblHNkw4T5O0bizAaS5hKmvuJKlSzc%2BWzq8i7zQO3n%2FJGl1qJgIA9sVErtFCI3MBX6QbQ6QbxQuYiDuYCr0hiVTnbEsSkQFZt0ggiN64dxZR67ldhXDck%2B97I4WZnmJ5txrSi0xOKdZKFfC6pNx2GNBg2jbmWMs17UZmbS0kOKmEBxdt1ALIFz3C3ywGe4ixVRMP5D4twhUXJr2UxnPUp%2BkoQxdssU994zLi3Ser1lhKUi5JHZtHObj%2Bk2Bv642rmew0cNUyaLYLjbT4C7%2BUC%2FbcdnKNQQFXpzDpjFKIX8xgK3SCHSCKUICdS4gHCBEsSq5wFZDqgoHzxvqj4ro%2BKst8I06nrmUT2E5F2mVBp1uyCXJl11tbarm40qAINiD3845%2Bjc2XjTScBJU2yhC3JhJcWB1lm7lrn1QGXY7xnRqFkFUctX5acVWsWV%2Bm4jlHUNgy6JGUbmWXNa731l1dgkDsuTyjnRbsbZzRZZcw5Ivqa99lJbogf3Kn1Ej1neNQQFQOkdph0x74pwgJ%2BlXDpVxJdULqgJy4qJS4q3OJOtEpCu2ArocjoSl4wpeNKDh009E2y9h%2BgSNBnGX2wAtxkuHpm1JJughSedlXHLkY51vaN54BQw3hqU6BtCSqWaU4UpsVKJVcnv2tAbWyexJS8A46o2YlclqzOSOHqmw8uUpMn41NPqAWsJSgqTpTZtRKybC1u2Mg4esw6Pmjxp1DGWHZKaYp1SpVYfZanFJLqEqRffTtffsjycNrz7GdmHHpV1TTl5tClpWU2SqUeSbkdm8YT4PNNs9h1b6cM1Xf7XqJ3jzmlk5YPbz%2B7V7G9cMovNFXgltzj8GnNLCqf%2FwBk2h8TyuXxxzGeUdNcfS9WbmHG9%2BphFj5XlRzKuKaHfqO7fw%2B%2BVL7qt6%2FSp3uYrNbuRQsRE6FlLgj0zUdnNtPv8AWVRQlSgvMGkgrCdik1d4fjt8Ubl4iqvxAyGaYZyq4ecNY6paZcOqn6tR0zDrM6p9wFkKJHVCQkhPYSY%2BdjGJ8YT9LksGs12szFNbmW1SFKZmHFNImNZWgtNDYL1kqBAve5EZ9iCtcTeDJFNaxVWsyaLJuOBpM3PTEy22XDyGtWwUew3veAwcpxDhTHTK0NsUjEtGr4WlucAQ1I1JuauG3QdktpcOg3Ngnt2j6IYZl5jEvEXS8TY54X6%2FhXHZoKxUsTPVRiZo0pJpQoa2XWiULdJUW0k2UGzv3x85pWmV7GVZckpSSqFdqtUU464022qZmJpR3WpQ3KyeZO%2FnjPaKviQxBTqllbQZ7HlRlKGgS1RoLT7yvE2%2FJDbqCdQTyTpJ80BsZig5pYqx1j%2Fiyydwhh3G0hIYnqsu3SJxpM888hQSylZkgNSurpcQb3sbgG0Zjxc4AxHmFP5LNCmuSWY%2BP2vYebwvMTZXIyjgZQ6XENnZkIcJQuw6wT3pjnxFBz3yVmHcUtUbGWB1OISw7PNNuyzS0jyUrI6h82r1RaZCvZk41xrKVaUq%2BIq7jBbuuTmWn3HZ0KSk3U2U7psCb6bDvgOz5zKjHfDvlA9l7w6Zd1XFuN8VS626%2FiuXl0oblEaCFdCFEEWSVhpsct1q3sI1djfDlazk8H5lLIZX0ecr87h%2BeTRZ6VkW9b0tMaZmXPSo5psVtqJPILvyN41Czj%2FiPmsRKwfIY0zAerodLKqUzMvGaQ4BYpKPKTsRf0x6Rg%2FicyBkprEkvRsa4Dp8%2BlCZ2bllKbl3L7J6a2pIVvbUoA7gX7IDaPhCKrLM4jy6wChxt2oYfwx0lR0qCiytfRNoQbcr9CtVu6xjke1oulWqdSq1SmqlV56YnZ6ccL0zMzDpcdeWfhKUdzFvUkQFCETWHdCwgIwhCAlKjEuoxPpEQ0wEIRNsO2IwCER0%2BeGnzwEpIEQBtExES6TACbxAi8IiBeAp22tENO0Vbb2hbe0BTtDlExTvzhp88BCETWHdCw7oCA5GJRzMTDkYlHOAjCJrCFhASwhCAimIRMjkYWEBLE0LCJgLQgdA8K6QaPid3kTMNI%2BJs%2FPFvyKnZiXzrx%2FOyJSJluYnwF2BIHRrGxO4i68LTixQMRBVtAmUhN%2BWotG%2F5IxvIyo0lvOLMCUfqcszOzK6mZRhxwJVNKSlZ0N38pR3sOZjzFzj8rW8%2Bj3PsuPzloTcI%2FrZVveaV8hH72Mc4p3HBhHKixIQaNVFAemeIJ%2BMfJGQyod03WLXSDbuJ5xcuJLK%2BuYkyGyvzQw2hVUkKYuqYZrLEugrXT5ozBeZUsDcJcQVb8gQPthHp3xmHHUQMZB7RMWqF2sOVFY70SqyPxQGBMZLWkDC1UHVN7ybm%2FyQSxsje8QjJRl7jIocUcNVMaQo%2FoRfzRfsV4InZldJXQcP1G6ZFCJxPia7JdA33A7bmA14ReEbAouAak3Tay1VsNVRMw7LBVPUZNwguA7iwF7mLD7QMYWv7Wqp%2BCLv8AigMbA80V23FobXo6vVMXk4Ixajnhiq%2FgjnzRdsLZV44xfXJLC9Hw5PLqVWmmZGTZWwpHSvOuBCRcgAC6rknYCA6MxiD4%2FQgo3V7WKKVnvV4mi%2F4hGGcUMw6xQMqKYmZDrCcLTcwmxuEl2oPFQ9N0CNoZz4WmMDZkzWBpuclpuZwzTafR5l6Wc1srfZlWwsoPO1zyO4NxGHcUuXeI3MuMm80ZeW8ZoVTw3MUNT0ugqErPS068tbLttkqUhYUm%2FlaV%2FamA5Zha4Me72EqxWS3S5xSRuSGVEWiApc%2FqIEk%2BAdhdtQsYC3G94li5t0uZ97DzDoT0idZ0Hyb7%2FJF7xlh2nSNfDOG1uTFPdYQ6FgE6Fm90k94%2FLAYirlEtrRlUnh6SewpVpyZ1pqku%2B14uwpJClN3Gqw9ZPqixGnzKPsjCh6oDxWPOPWzOvyzCm2wjS53pubxAyzgP2NXxRdsMYUreMK9T8LYepz89VarMtSUjKso1OPzDiwlCEjzk%2FEDBMOpszSVY3eUvyzTqdq9PijUW2ao9MreWOMmatIsTCJKSYnJdaxZcvMB0JS4hQ5bKUCORBjJM8KNOYdzZr9AqLaUTVLWxIvpSoEBxqXbQoAjYgEHeLElxTeW%2BNUi9lyUsD9%2FEEQ3XwPFDWSc8oJ1pUaiu17agGj80cPzitcuF%2FbBR%2BUx2%2FwADHvmR05%2B5bqnxlpVjHD031ZJPmQfxmN6qfydZemXKu0Z4hb%2FYxBw2UQPPE8vcuJOjX%2B574pObuGPVTf0Y0j90I0Z1Oo%2Bm3g3WKW3Xqil6UkZ3DuEpZmcanXKelp%2BarLxPRrUpQ1EMtl1KDe1l3IuARsjiAxMH80l4UVMMTL9QYeqdHmVHS90iR0kxJFXJYHWdaVzHXT3Ro7gwfrFGypm6vTQSKjWXGHCpVwA02kW8w3iy5z1TG1SzcoLeHGp53FEjUZaZo6GWulW06hwK1FNtOgEde%2BxSVXsIJU8dYny2zuxKzP03EKKBiRqm%2BIms1NH5y1lTarJl5tQuWjp%2BxvjYK2V1TcZ5lNnKxkjQTQMcy2HJtUogJl04arCJqYXqc8p9lF2%2Bon4YWlShbYxozG1YRU6%2FVFyVBpdGlajUJicVIU9oJlQtbhK%2BjG4CCrUU22sRba0eKls0KYxBS6fWZWoNUajS7lSqxoqW252altJ95aKgUDSpIUSocgodsB9hsosa4Zx1hByYlHpacpz6QjSpOpLza07hSVCxSQbW3B3j5BcemStLyUzyq%2BHKLKdBQ6jLorNITawTLPKVqaHmacC0J%2FchPdHV%2FCjnZUabgOkZeuopzb9OqLjUtOs6g%2FOSpbLiuqOqpKSpN1eoRpbwo1QTVcW5f1BVvGF0SebUssKSpaEzQtqWSQ4BqNgLabkHnAcETTdo8auceuZcBjyKgJNJhpMRhAQI29ESHnFUjlEhAgJIXtCEBPF3YnGJShKdX0a5p99xCN7rttcnbqj8ceOnU5yoOOfmhplhhJdfec2S2i9r%2BcnsA3MeiWw%2B%2FPUKYr0k8283Jr0zUuFWeZQbaHSntQSbFQ5HY2uLhblKLp6Um6u1Rh1Qi%2FPzRKQEDa6knkIIUUqset3CA6h8H1PU%2Bm521maqCgEownOqbB7XA43Yfj%2BKKM0qi4xczFzUzMxXixxmkYgcpzEtTZpRUUqc0MNoTqSlI6qrqOwAAsSYxbhEfLGZs%2B5%2F3O6n43EW%2BWLohOvJvNRggan8XU9YCttzPP8A0TAW1NSyMQpwjFOarYUoFssBKVAHmF3dNyOwiPU1WchUuJ14zzaCAnrXKblQB2Fndgdt%2ByNUmVdU10zSRYzokU9a13b8opLkZxDbzqykBidFPXvyePZ6PPAb2wpJZLYwreHsNYezXzIlK5XJlqRbYmW3ujMy5ZKG9aHe1ZABjxTk3k3TqhNSExnjmKw6w8thxpclOBTbiFaVJ2d5hQIse6NS0aoYhwXX5bFtDnEyFXwrU5WalpjSlZl5xDgU0oJUCFWUAbEER5ayiov1Gr1GrzSHJpqZMxPuafKdeUVE2HeVE7d8BvBiqZDLl0maz4zNDwulQErO6TY7KHvnIjs7DEzdRyFU24hzP3MpCvgnxKeKVb9o6TbaNFTcnOSS5tD60JVJtIeXuTdKu0d8SOtTjDr7DxSlUux4wsE%2FAPaIDdk5W8jOj%2FOvOXM3UooSETKJkayRYp6rn2x2v2RUxhJ5b4KxTUMKV3OPMBqp0WZXKTzHQTK0B1HYlYe8%2FdGiil3X0QUUqMv42Ck8kg3BB7wRHurtfr%2BNsQTWJsT1V6pVmtlU%2FNzj1tcws2BWqwAvsOQ7IDbaMYZCoSjXmTmy8rfUEqW2PNYl4xGoYoyTnTKewuaGYdNSlvTN%2ByaZmZKl3NlNll4WFrXBBNxsY0fN0qbk2HJ5ZQUDrW1dkTNsL74Drjhzq8sxmHJVXAmcOIqmilzEq1VZOeYmW2n5OYX0RUA84oagsoAFgbXIPMRtPwhswy5SsuHGnQVPCoqdCTfrAtg37jyjnjhAR%2FZpVVgAq6OkDfu8fTeNtcdSnBUMHILhKCioK0k7A9IiA5Tf%2BxL9BjrClM9DQqQ2ppKVok5YEjuKAR8kcouqSGlXHYY6to2sUKnTS3Eq%2FMkv8HknQm%2Fr5Rlsfz%2Fs98KW0Z2eX9crL0rTKtodZGt%2FR121cimFPptTxRXJWiYclelqE0SQNVm5dAHWccVyCEjck8rRUuwFpff09VkW53HafQCI9uH6gvDWXVSqNPmSzVcaPuU59AHWRSUBKjZXKzjmlJtY2BjZqmdlO2WhERGuUMTYjo1IQcNYCdW%2FLMKQZivLTZ%2BemUE6nGe1tkHZIO6gLnY2izYizyzTlsKzWHfZ0u0xV3iytsW6QDywRuD6DbzR4mA004EoNy2m4uLxZMXKb9iJ2clwAVNlOnV2kDcRkpr%2BLj8BTgRaT%2BMjNZ6%2FWfZKSlHpxBJmJNpaytSlFLh3URcmMNnPHaa%2BxUqDUH6fNML1sPyjhQtsjuIjZuaFA8XZw%2B9T0t6jh2RdUlItclKib%2BfzxrEvuaFtOIitVdVcRNU5y2dVMzFMZQv1WqrGYtCm68pDMtiujthVYlmmwhupS5%2FuxCU2CXUkgOgdUghYsbxg%2FwBkHSR7qRWHMLYqpuJWWUvBh0MzLKh1XpZwFLiCO26FEem3dFSoyMrTatO02WFpeVeU2zc3u3zTv6CIpnmvTEU7Fkn0hMvMqTz6Bd97dkYnLI6ojM6w2humzLn2zakxikkgKSm4itca2ajXDVmJf%2BMdSH%2Fbn8UXTEz5eqTRUvcSrA0%2FwOcW3Eab4mqo7n1R6cQkCsN6eXi7NvRpEas7V2ZZbJC8T01CiAlTyQbmw598VMwktoqTyW7W6VfI7c48uAlFNakFJNiHRY3j0Y%2FJVPFR5lxRPxxAwmZO0W1zyouMxyi3OeVASHaJCbRMTFJRMBVSbxVaUAY86OUTpNjAbfwTxOZ85fYcl8I4MzbxLSKNKFRlpKXmx0TGo3UEBSSUpuSdINrk2G8X0cZHE9qv7u%2BL7%2F8Aim%2F6uNFAm3OKiHSnZW4gN7jjJ4oP%2BvfF34S3%2FVxP9WXxRAaU57YsAvfeYaP%2FALcaJD6B2mIl9J7YDfH1a3FOk6hnrib0a2P6qMax5xPZ9ZmUT2tY7zTrdZpPSB5Um%2B4hLa1jySoISNVjuL8o1UXvN8sUi4rvgD5ubxTAvESdV7xBPMQG4eFfI2jZ%2FZv0rL7EGL5CgSU0sF0vzSWZmaSduilAoEOP9uj7UKPZGMZt5dJysx3VsFoxFR8QNyDyktVOkzaZiXmE6iBunyXBay0HyVAxmfCLlzTc2eITBuX1Xq1UpcpVJ0qVO0qY6CcYU22paVsu2PRrBSOsB3xhmZOF2cM44xJh6TmXppil1qekm3nQOkdS0%2B42Frt8IgAnvNzAYchuNh5JYjpWB81sHY1ryH1Uyg16RqM6JdGt0MNuguFCdtRCbm3baMNlaY87sAY7DynyqyiyLyVkOJHP%2FD4xPO4heU3gzChe6Nia0XvMzJPwL3IBuLdhgNlU7j4y%2BrGI8TP4zfK6YMxqViCgGToCWn5iiS7xUvxgoF3HQCLBd1bRwrmnWJDEeYGKMRUlJ8Qqlanp2VJa6O7Tr61o6nweqobdnKOp1celMq7vsZjjhkygqeFnCG10uXk0y82GuVm3yny7ctk%2BkRhnE7w%2F4Cw9hXDGfOQNRmZ%2FK7HWtqXlptRVM0OoJuVyTqjclPVWElW4KSkk7KIcsKSoG4SfijP8qMmqpm69UWKdjfBVAep3R60YjrTVPL%2BvVYs6%2FsgGk6rcri%2FMRhzshNNneXd%2BIxuzhDyKwrn7nPKZa43m6jJU%2BYps9PdNIpb6cKYb1JCekSU2JIvtuBAafx5hCdwFiifwfUahSp%2BYpzgQZulTiJuTfBSFBTTyOqoWNj2ggg7iMf5Rda7IpptWnae3p6OWfcaQUpCdQBtqsNhfnFtO0B66bvMI7ibfLHXXhHNsxMAtdjWXdFHyORyLSt5hsd6vyx114R%2F%2FAJUsGs%2Fa5f0UD7lyA49ULmIKFxFRQuYgYDffCvwvv8SCsTsLxtSKCxh%2BkTc20qYm2g%2BJpCEqbU4yohfipJst4bJjTeLMNVDCeIKlheqLk1zdNfUw6uTmUTDDhHw23UEpWg8woHeN%2BcFeUSc3MQ47ZbxrW8LzNAwbPVFqbpKkhT6SkpXLPBWy2Vi%2BpB2Mc%2BOSTpQkobCU6QrSgWG4vsOweaA8KGRG%2FwDgyzNwnkznhT8fY6qL1PpEtS6jLF9qUVMWedYKWgUJBJGq3m740lL059wApYUtRWLJ%2B2J5CO4JHAuSPBll5h3EecuBpXHmauK5NNQk6FOuhNPpTB3QXQdirvuDvsBteAyHBfGhlRXcu8PN5jppdNxHJyOK5Go0%2Bj4dLUj0s41ok3A02FIusAalAnrXvaPn1VGUpmCRyISnfvCbE%2BjaO0ZLjCyYzBmm8PcQPDDgIYYmfeXKnhFJl6hS0qNg8kAJUvRcklKr2BOk8jqHir4dnciceN0ql1f2cwvXpFFZwzWAQTO09ZsNdtulbJCVEABQKFbXsA596PujbGVfDjjjN7DruIsK17BMs21MLlTK1XEktJTRWkA%2FYnCFAG%2FVJ2Ma1XJupNkpJEbtyE4eMPZy4EzYxLXqxMUyby%2Fw6KxIhiWbdE051%2Bo5q3CbpSLpIIuTvygNF1enzdIqczSZ5CETEk%2B5LvJQ4lxAWhRSrStJKVpuDZQNiLER47GPXOMBg6Or1fe%2Bry22280ULWEBShETzgmAmsYWPdEw5RGAqtx75cWIjwNc7RcGBygM1o%2F9ph%2B%2BP44tlIWpvH2HHUeU3VZZz7lYP5IudF3o4v8AbGLC270OKKc7v73MBe3PlAXt%2Bc6SpTjn20y8r7pwk%2FHeM4y9xTQGazhqj42dLVHpVVlZmn1AIK10vQ8lZbI5lg2O3NBJttcDVbcw50i1%2FbKKvlj3iaSRp1G3faA%2FRhRq1SsQ0uWrdDn2J6QnGkvMTDCwpDiDyIIj3R8eeCbjfqWRFWlcC48nHp%2FAU86GyvdblJUeTiRzU39skb23FyLH69UirUyvUyVrNFn2J2QnmUTEtMMLC23W1C6VJUNiCDzhnmPZCEIBCEIBCEIBCEID4H8c3iR4jsxvFW3UrGJ53pdZ2Kitdyn1gxzq9vT2b%2FaW%2BXeOgON91Z4mMyUlRKUYnngnzXcVcfHHPz5%2FMDSe5u%2FymAzHDoHsYe%2FQ1b4zFzT5Qjw4bSBS%2BktyQ0PxmN08NOTVNzozEVR8QOPt0CiyvslVgwrS5Mo1hLUslXwekXso%2FapV2wGn0vMnWQ6g2523ibo77iPpzjOfyRydws0qt4UoEhKzikyNNolOpLb07VHz1US8uzYrcUokAqJsL3JjlDiuySkMu28MY4o2G04bZxN0kvVKCiY6dFLqKUdKEIWNtKkXBA2C0m20BqfBmS2amYFIVibBWBqrVqeh9coqZlUjSl1NtSbkjkFC%2Fpi%2Fo4Z%2BItbnRjLHEIPeSkD49Vo3RlDXsRYT4IsRYiwxWJimVKWxWppiaYtrbC32ErtcEbjaMKPEFnSo3OZ1Xv5g39GAwlzhj4ikBTjuVlfWhCFOLKgkpSlIuSet3An1R5cquILMDJym1aj4LTRlydbmG5ubRPyXTFTiEFCbHUOrYnqm%2B5jqzhVzEzBx5XMaS2MMVztVap%2BHlTMsl%2FRZpZUoEjSkcxtvHBdhtt3%2FAI4DNsys2cRZsztKnsSUugyK6NLOSbCKPTUSTa0LWFkrSjZSrjY9gjrXIffg%2FwD3tNr2n4nbRwpy5R3fkMgHhFaHZ7F1wH06Hrx82%2BE79X3f%2FVj%2BWp18I%2BUq9EuO8uNQySxA2nyU4jphP4KoQl3AF23HVUOduaSPyxLlkou5HYlUOXtgpm%2F%2BLqinH0ajY5M7WCz2CMaVRiRcbwvNgMyqGSrUjrEX35%2BeLd7kOPX9TicPvJ%2FfKR9KNmdTzREdGDewi6Gr1ZQY7T5VHI%2FwqPniLWUmL1LAep6kJ7SFJP5Y2lqbt5CYk1J%2F3EBrJWUmKU85VY9Q%2BeINZVV12yEodLvakNbfHeNnak%2F7iGpH%2B4gNYvZTYoaOlUsoHuOn6UUU5W4oWbCVI85sPyxtUFMVbJX1NlQGqk5S4t8YaQmWRdS0glbiUhO%2FMkmNvqmG1VQqbdRoU8oFy907JIvftF48Tov54gG7iA11P4QxRUZeWW3SXSWmQhWpaU33J7%2FPFsOWOLnTqMiEA9hWk%2FljbqGtoj0cBqZjJ7GDx%2BwMAed9H0oqIybxevlLsja%2B77Y%2FGqNqBtAN7RFXKA1a5kzi5tGstSqhe3VmGyfi1QTk5ipQSeiZGrld1v542ffzD4hEynbJ5D4hAakdyrxQ2dPioJ8ykn5QbRKnK3FpXoMkAfOtPzxtvpImL6gLXgNUsZR4temGkJalkkuJF3H0ISN%2BZJOwEbjmAluYeQHUKCSpIWk3SqwsCPMbbemPC24SeuiKql7bCA1XUMHYtqCmVewTyFNNBohS0X2J8%2Fnjxe5ZixzcyjbXpdEbfSo3ic8oDT4yoxV%2BotffE%2FPEE5WYlLoa6JFz26xb8cbdKF84ouAwGsPckxJbfovvqfnin7leIwT72nb92n542hCA1d7luJL%2BSi3pF%2FxxFeVOIrXT0Sj3FaR%2BWNnFdolLt9rwGtJLKzEZmWQsyjILrYK3JhASm6hdRN9gOZjcXslJqxC7NlwKlhMODWOSwAUgjzHa3mMWNwExBAIRpgMLq%2BCMV1BqVb9j2VKZl0tEiZRzBJva%2Fn%2BSLT7lWKlWLkvLt%2Bl9J%2FEY2TohotBdroZTYl7DLn%2FDI%2FLEwyoxD8JLPqeR88bFt%2B5T8ULfuU%2FFBWWvvcorRbcSFNhZILay%2B3pA7QRe9%2B60TOZWz4EvoS7e1pgl1o3Ormjrfa9h7Yz%2FAPgp%2BKH8FPxQQwBeV84ZiYLQe8XUlYlgtaA4FfA172t32jxLy0ryEadKVL%2B2DibRs3X5oipVhcQGs5DL6vtT0qpSGkhLza7qcSAAFAm5vtG0ZxwGbmtG6ekPKKF9rxLrINhAZPmH%2FwDDBRf%2FAPIKv%2F5cY7A4JFlXDXStXwWagPV42qOQcw0W4XaGv7bMJX%2F8tMdg8FobRwz0UIvfxKfUr98Zxd4%2BZ%2FCTquVj%2FqU%2Byp2MKnXV6PfDgNz9Euf397%2FSKjovgY3zjnvNh%2BaP8tEc6PC02%2BPtX3f9IqOi%2BBX%2FAJZZ4f8AcEwP84iO7ptlOA22Xix7Ya%2BHz%2FaafSvWdJUniyqenmnKp8j7yoxzox8KOjc41LPF1PJUbj3LXUpHmLKvykmOcmO2M%2BhtPBwS7fwwxX6Px8ws%2BLKXWKjNV0S1OfmETM20%2BhxpN0KsykH1jt9EYCvLbGK3DejvI%2Ff2H5Y250ixEpcMeoauTU6MrsXLCiaepJSCogjsETnKjGKUhaqaoJPIkc42kXFd5%2F39cUiq57fjghrFOVmKlc5Ep9KYnOVeJAm%2FQp1d2kxsjVbv%2BOJStfwSfjgNbLytxKPIYSfVaKT2WOKG06vFAfQY2Stb1%2BZ%2BOKep3vPxwGtk5bYsJIMiAANV9Q5RtSYpi6JQ6NSZh9l%2BYlqW2pZYcS4LLClBNwbarEXTzB2MeZPSfbxLZKNhp%2B2%2BOAt2M6XP1MVGWprInA9U%2FG2nGVAoW2phAvc25KBBHeIwJeAcUfCpik%2BlQjaF78omQbGCYaxTl1iI82W0%2Bsn8QioMtMSfaNfdRssqVe4cIiBWu27ioGTXCMscSLOkJaB8%2B0ToysxKXEtLDKVL8ne942Elz%2FtFROl8BXlqgZNcO5YYja5hs7kesRS9zfEitPRNIVq5b2jZ%2FjCidlm3niJc2gZNWOZcYoZOl2WaSe7WD%2BKNpGXVTabISzzjbjjEkgHolar7cj3HblFNXXv5ooq2NoGS243olTq%2FjsnIS5mFmqOvNqaIKFNrZb6wV6QR6Qe6MHRl5ipZt4gEjvLgjZMToRcQMmuxlhiopuiWaUT2awIj7lWMCvR4gNX74RshG0VQ5blAya39yLGO4MkAR3qAHx3iHuVYmShJdQ0kk6SNV7GNk9O52LiYLUrcm5ghrT3LcSdgb%2BWKCstcTp5stj0rEbT6Vz7b5YpPqcUPKgNXoy1xIpxIUGEAkAqLnk%2BeNtzLYlUyiFuIeLcshd2lBXVKiQNuSrc08xcXi3emJ%2B7T%2B%2B6vb6YCwZi0aoVWffap7XjKUTsy6hxvdCm1qSpBB77bW7LRhntDxKvf2OWn07Rs8LPdFRHSKNypVvTBMNZDLnEvwpdKN7bq7YqDLXEausENlI5m52jZe94n68FmtRlliJSAUlkqPZc7RTOW2IU%2BUpselKo2dpP25iax%2B3V%2Fv64KNWry8riXNJLZ2%2B1VFJeAK8D1Uo%2BIxtjSftzE%2FwDDMBrCl5f11uqSL0z0aGEzLSnHLE6EhQJNu2wvG0%2Bv0DTaz1kpOrt2KyR6NrfHEoWoCwWbRJe0BnFGOjILOxwK0%2FnDTkHzg1KX2%2BSNl%2BDTebPt8lRMWcM1SXCzp5pCnRqv6TaNZ0waeHzOlz%2FuWnJ%2F%2FiTEbD8Gekpq%2BPXyleyaSgG3V%2BzOEi%2FfsI8Xp7%2BpLX%2Fb%2FNS6uET%2BPz%2FrlYZxagjiHxjdQILkqRb%2B8JjG8lf%2BV%2FA21%2F7IZH%2FSRkPFgdXEHjI%2FazEuj4mExYsj1aM4sCq%2F%2FaCT%2Fnxnmf8A1imf8n%2FgxWH4V8iP3o9rpfwgkw1LYOwGVtJWfbsyLqANkhkFVu4naOfc62ynOLGSVI0%2Fnw%2Ft5rxvnwiN%2FaXgDu9urf8A9um8aHzrN84MXn%2FvV38caPwefqSif3qvajE%2F0mpgGM2XZrDLcrJyzsw6vp2tDSSpQUS0UkgdhsRfzRqp3AOKVuKCaJN%2BtNo3Drhr80e7abTyMusXqPWpLqB3qt88elGWGJlC%2FiTpPmbv%2BWNsa%2FNENd4DVQyzxEb3lHxbn7wdvlib3L8QJ%2ByNvJ%2Fxcn8sbT37z8cUnFkG1z8cFGr1ZaVxPlIcH%2BCt%2BWKRy5r9r9Ht6N%2FxxtBRvEsBq85eVodiz6ERnWBqRO0LDdQkZ1JHjE4ypsFQCttyQkG9trXi7QCLHUkJB79oDyYyYmanh2VlZNCnnF%2BMy620DrNqKm1pWruSoagD3pMa3VgLEANjJqA7yR88bW8tzpF9b7aJNHngNYoy2xAu56NPxw9zHEyj70ylX8ID8sbO0eeGi0BrI5Y4oSjUZdHoCkk%2FjiojLKvqFi2lKu4lP47xsuEBrJzLWvI5Fs%2BkgfliX3N8Qfqbf3YjZ5So8jEujzwGs28tq4r7JZPoWg%2FljO8G0uYoeHnqfOOtBxTos3qGoi5VrHZbs9MXMN23ETnVa20BbMaSExXaDT6dSAH3kpfS8i%2Bkte%2FpUgkq2UFJ1WtysQeyNenL3ERXpWwlJ860n8sbOWN94BAgNajLevfatfdj54qjLatrFg43cd6h88bHhAa39zKufqjP3Y%2BeJhljWTzmWR5tQ%2BeNkDlCA1uvLGsD%2B6Wvuh88UlZaVn9WaP8ADEbKWDeIWMBrQZZ1s8i199QI2FhanO0PCgpU2814yZpI6IL1HSlKiXbjbSSvSN73B7I9aEbXgdoDyYypUxiKiyMpTX0OOeLFuYQ4ro%2BhcS%2BpQsT5QUkg3HnEYD7mOItdvzN9%2FT88bF%2FTLxWgNeIyqryt%2BmlEnzviPQMpK2Eh1x%2BWKCbdV9BPxRn0Ttc4DBEZPVk3vMyh1eT%2BaUC3pioMnKgpoKM7LoWk2UPGEnV6I2COUIDXL%2BUFQSQhmaQu%2FL31OxjyLyjruvSh1j0lwWjZyfK7OR5fkioEgG4Q4k95O0Bq0ZO4iI1dNL27y6BGf4Uos3RKGmXnnmy8ghoIQbnSkeV3WJNh6IvAWv4bioprXvsTAbL4bwF5z4fSsXQozOvzDxZ4xh3g9GC7ny278FnD1TUre2xSkflEZjw1ArzloVrkjxo2Bte0q7tGGeD1CznkhQJAGHakVWF7iyPy2jzWl9UU4NeKv3Z9joYfGd4o9LbfHsB7r2H%2B%2FwBqcvf0dMqOZ3BvHS%2FHstXu0Uhk8m8KSvPnqL67%2FijmpYBMV0P%2FAFHdv4ffLHfPl6vSoQtc3iKx3QQO%2BPTtNmuUWaNVyZxk1j%2BhUej1GoybDjMsipyynkNqcsCtsJIKXbApSRc9Y25x2ArEmPsEcLuYWK%2BKDEbs8%2FmIlxFBw3O2W5KF5lQbbSg%2BR1ih3TzbDYJIJjlHILHeCctMzZHGeP8ADb9dptOYfcl5ZlCFqbnbDoHtKzpIQdR37SD2RuHOnPvhrzsp1ZqWIsB42msUvUaYkKLOPz4TL059SeotLSV6QNfWUbFSrWPZAbF4TsvpTImXwdWcayzrmYObk0il0mWbSQqk0pDKnnHVqt1VrCUqVyNlJT3xkeQSZ0cU%2FEv0yFNTL7ksphJunpCtS9DiSewqA37wY0Jl%2FwAb%2BbVExHh1OYNYTWsM01DcvUZOVp7CJmYbQz0aFIcO4WFBBO4uLiMhwfxlUWm5u5i5g4ro9an5DE1Hl6HQG5NllqYkJRhby20PWUAohTpOsEqPqgNn4GlM08rshsyWuLzG0pPU6fp7jchLzdUbnHzqlloWi6R1gp0tKQnchSb7RjfCRgmm5N0PBWN8dST%2FALes2ptqi4fkyghdOphRqemln4GsJCjex0qQBzMcTPF6clEMVaZfnVhsJUt%2BYcdIJ8ojWTa5jobLrjZzew5VaBLYuqcrWMNUstS05LNU1lM49JoRpCEOnkoAJ6219O8Bs7Deb2A8n%2BN7NmezJnvYqVxFaTlKvMIVoYcSllZ1qAKg24ApHSC4CkC%2B0X2by5zvw3g3FlXyL4gafmthmtyTpqNFxIE1B99goUXQwtK9Gst%2FA6urSCBqEaoY4vKZMZ34lx3i7A8riTBNfp7WHmqXNSTKpyRpjKlqaUlSrgu3de12IulQsbpEenBfEBw3ZAUrEMxw94KxaK7iCXEtrrUwDLS4TctG1%2BtoJvyubWJtAcqthoMshgqLYbSEFRudNtr33vbviRyK7jmq5JClrupagLXUoklXmubm3nigsXgKcIjYxCAgTaIXMTRDSIADeAJJiIHdEUp60BccPYfq%2BJ67TMM4fpzs9VKxNtSUnLNi6nXXFWAHx3PmBjNa1kDmVIY%2FxXlzQaC7iupYOdQ3Un8PIVOSydaEqFlgDrAqKSki4Uki0ZBwhYnw5g7iWwDXcVvtS9OTPOSnjThsmUffaU0y8SdhpcUnc7bx1rwl16m5eSWNMgsbTQpeZGF8Q1StVkurIXVZFwh5FQQ6PLQhtQuL3Skg23MBwzKZSYuqGWVfzVpzDb9LwpWE0WvSh1Inqc6pKdLrrCgClrUoIKuw32sCRiJlFlJUllZCfLKUqIHp7BHa%2BIcb4SxTNcTmelFWlWBMQYVkcEyc4tPRtYjrwSkF1rtWpIHlWuRuecY74P3HVcGPJrJl6nUaaw7WJWfrc2uYkUuTXTNSyW9AcNwW1AglJBsRtzMByOWrqCAVXI2CRcxBxkpKhdSVJAugpII89jHXPDpISWWeQrmclBwLTMU48xhjc4Iw%2FLVFSQzKnpi2hAKtkgkElXOwAuBGD8XC88ncV4Zaz3wrhaiTyJKYZpC6ClAYfZVMISsOuBRJUhekb2ABJ7TAaQwpg%2FEmOMQSeFcJ0p%2Bp1eoKUmVlGACt0pSVEC%2B2wST6ouWPsrcf5WVGUpWYWF52hzU%2FLeOSjcyke%2Fs30laSCQbHY9ojqLJXhSzvykzQw3mS2%2FgipMUmcDc3Lpr6NLsu%2B2pt1KHALdIEr1Ab3KbdsZrxU8PGaOemYErXsMTeE26Dh6lGnSL71ZAdmStzpVOPIsUskKJQN9wAbwHz%2FWLRLGR47wbVsvsX1XBNedkXahSHgw%2B5IzAmJdSihKrocTsoWUPQbjsjH4CiVHVaJ4gpPbBJ7ICMIQgJYQhABziaJQDE0BLY90LHuiaIgXgIAWhE9okgETiJbbXhcwJdDcLyVJw1iFZISDOI3I%2F7MCNT5SyFLm%2BI3E79Wp0tOGkS1an5dEwjWhEygFLblu0pKtSe5QB7I25wtkLwpiBKlm4qKQTe1rtp%2BeNO5b1GjYd4jMTyWK65L0hmqirUZufmyUsMvumzSnVfAbJG6zsOZ2EeauMxOKXiZ83ufYdKM%2BJuG0Rr2fyy2Q2iVY5N6ur8Lt9MXySxFWpOTcYoc1MSSnvswYdLYXYWBIGxNu%2BLr7TcLIUEPZz5VkqBt%2FZWxzHP1eeIyeEMPt7pzpyrIVqSAnFjFwRvzO0ei%2BMpnlfI%2Fia%2FBPMscjV8YlCm2cTVNrR1j7%2BQCe4jtiZvEGYTn2TFFX6v%2FbEARneXCMmqhiisYKxvnXhSl1anS7cy2ZWbEzLTDarH3uaSOiUsBQ1N3uPUY2ezhrhnSUpez4w0ogb2m2xq%2BWJ4UKcGWgma5jdQ6%2BLKt6pgx6UVvFQ6rmKajY8x0%2Bx9IAjYubLnDphun0in4ezvw6%2FV67NeKyrKntTKOQLjzyAUsNgm2pexPoMYs3hPDYGp%2FPXKdJ2uBipk%2Bns3ic4OBV4FubruMlm7eM6x3WD9tviip7I45uFDGdbSRyImOXyRcZap5WYCrlImMc51YEcos7Otykw%2FRqkKlMMFQJBLLQKg3t1nDsnbneN8zcrwoua2%2FdkwytCOrrFVbtvyNwdxDhR4TgVeBzA%2FirMmSWeixxWLBX6qDbuHkxY5%2FMbMpOpK8Y1FQOxVdIUPQoAEeqOm8UUHhTlqDPVZ3PTDcmzKS63ypM4l8kAXsltF1rJtYBIJJMc%2FyWXLeLacxXMPZk5cO0ydR0so5M4pl5Z5SCTstl0pW2ocilQBBBhwoRwavA1o6p%2BYdXMPuqddcUVrWs3UpR5kk7kxdqXi3GdEpUxQaPiWoSlLm30zL0ih0mXW8OTnRqunV5wLxnRyHxE4QWsdZcOJT2oxdJberXvFRnILGrW%2FthwS%2FwBW%2FUxZIn0fDhnEqVVU0TlVOSy0vHOPW29LeIZnSpOhaQy11knmD1YuIrWL5pZUKmlBOm%2F5kZO45HdHONkZOZfZZ1qdr%2BGMb5p4apmIcPOoE3TEz7bikoULhfSA9GvnuEKUQTY2jbcrlBkhLj%2FlQoi0JIJHjzFvT5USjh057XNyKlic6PGanLuaBZI9jZewH3EexrENZlEKYaFNQUiylKpksSR9xG1M1MH5c0mao9AwHjigVfE1XUtUnRTVWGnpllIJWtClKCDYJOylAmxteMMGUmY76Er9rssu56oRWZMm3n982gtnmxCZq1ZdUktKpYCQdnKTLq%2Fo7RZJ6t4gQoKXScMP6RbUuhMEk9523MbTw%2FlymnYppVFzVq9KwbK1p8ytOmKjUZfTOTG1mWylZGo6gLG3MDntG0KlwyYOmVluWzDpKSobJW6i4I9BgapcmP43n5TV0mE8HuBXPVQGrj0ERLJZo1KjzzFaoeE8IUmrSrgelqjIUkMzEu6PJcbVqISoXNjbtMb9xrwsyFBw3UsSIzKw2GKayX3TMzrcui3IDWs6QTyF40VMZK5uTVpqUysxO%2FLODW261IdIlaDuFpUg2UgjcKFwRyhnEbZMp5IYPVqlUq9Vput1mednJ6feXMTMw8oqW64o3UpRPMkmLPmGHk5RVubk6pNyjkrUpBDzTSrNzbK%2Bk97cHPqqCVDe3O47s%2FVk3m6hYQrK7FQvexFLcI%2BSMQzjw3ivCGUdXlMVYYqdG9kqnT0y5qMoqXLqkBwqCNXlaQbm3K4is1U8krZTG1v7gdQljJKaU4oJStmouKUewdAsXjiCoEGRQpPIpuI7a4LZkJyOnEi3Vlaiybf3gxxJO%2F2ua%2FeR0Ko%2FJ9l6Zcm6T%2Fb7efQw9zZwmPRIupZmmZg80rBI80eVw2XEULjRdV9QfBt4spNWwzjHLSaQ0ubk32sRSSF2PTSrqQ28Ug79RaU38yo6QzPwAavhGrqwc8qi14yLwZm5GTQ49NWTfxRwnrdC7YIXpIVY7doPyDyTzfr%2BVWMqLjHDs94tVKJMdLLKcJ6F5tQ0uyr4HlMupJSR2Gx7I%2BvmS%2BemXufOHvZrA070NRYSFVKgzDg8dp6%2B24%2FTWvtXUXSRa9jtAcUZiZCZz0GvsNO5b1Co4fZZamG5vD6fGmmkLbStbDaiAorbUSnSpIG1r2Memi5Y4vyjzMw9iqpLencNz8uH5Gel5JTa5uXeB1Sz0u91mn0qFltrG1jYkG8fQwuutnUlZEW%2BuYbpmMqe5R600t1Dx1JcHWcbX2LSe8XgLRlZgvL2j4XkE4Tw9T2GUNrQ10SNYQhStRS2TuEEm%2Bns5dgj5u%2BEczAp%2BLeIGaoVJUhUtgyms0NxaL28cuXJgdx0qUlNx9qe6N8ZtcTMrwoyGJcE4RrrFZxxNOuystIpPSylGHLx1xQOzikm6WUnytzYDf5r1aszVTmXJuamnn3nFqcdceUVLcWo3UpRPMkkkmAt7uyucUlG5g4u6rxId4CaES3PfC574CY7CJecQ1eeIwCEIQF9ouEqliGgVar0h%2BWddoamXpin9KBNPMLJSXmm%2BbiUGwXa5SFAna5EMJUd%2BpvVR9it06nGmUuYnlibmwwZxtOkLl2b7OOqCiQ38IJPdFmYfflZhE1LPuMvNG6HG1FKk%2BgiIa4CWHngd4QG7eFD%2FlEnf%2FK1f6RMe6oTipXJLMlSSQV4ipKwQd9pucVHi4Utsf1JX2tKJ%2FziYuWJqb0WUOK5ZtJJnK7h4bm1itM64T8ZgOfl1KYGpKXHAnpw8LHk5c9b0784leqk2sODplkPOB5dzzc%2B285i5ChTLqPGUtp6JyeTJCx5OEm3q25xFeHnlIfWW0pDU%2BmnrBPkrPJXoMBa3apNvF4OPuKD6gtwFV9Sh8I%2BfzxB6ozb5WuYmHHVPABwqUevblfvtt8UXGbw49LJnXlFBTKTaZVWlXae0eaJZrDsxKio9IttZp60IVoVfUV2tb44C3qqU0vpNb7h6VOhd1X1J7AfREy6lNuKW4t5awtvo1AqvdPdHrm6BMyi59CnEKMghta9JvqCuVvjiD1AmJYzKHSgiXYTMEhXMK5AeeA8QqMylWsOKv0fRX1E9T7X0RDx2a979%2BV70jQjrbpT3DzR7HKI82t1JWg9FLeNKIVtpva3piKKFMuPIYTpKlywmR1ttN7W9MBUknnVyM7qecV7wDYruOfnil0623Oj1q7PhR710edp1Nm3Xi2lDkuEghVyTrG0eUyTy3tZA0m0B0lwXqQvFdcK1ErLNK0edXjyb%2FJG1uOhwmpYST2aagR92kRqjgxZLWMKooclO0ZCvQZzf8UbQ459q1hMc9TM8r0e%2BpEBy4%2Bo9Er0GOspRzxeRkUrIKPEpcqty%2Bxp2Hnjk1wXZdT2gGOu6SwhctTFv2WrxJhVtPP3tIO3dGWx%2FPY7b8xks6pz2JmCBpsyoIIF%2Fg7R7JlL6cOYaSmXS42qUQtQdcKEKsSFC4BI5dgMeCWqCW20ScwgKbuOfLTa1j5oucgy5V8Ky7KwoO4anHG3kAXvLOHZf71KrX8xjaj86JaW2mfseOfVRENqWxTZZheoKSlM04SRY3uSm17xj1cm6HP0t%2BQXRmU9IypAUxMrUpCu8AjeMh6NcpN%2BMNTTgSlJb0BptYNze%2FX5R4%2FZSfbbdDEs270l9ww0Cmx3F7X7Ysjhed58S1yTdZpbU0KfMqkaczLjoZnWC0LlIUUjZYuQR2Rg9TfwxNOhcph5guAEqQZxwBZ7N7bdsZPNKq63Qy3TnluHcJZlmySLXNgLk7R5JjEdKmcOVSnTtKRNz0%2BmX9jJ5IQ2KepDmpxSkgXcK0XRa4te8DhZRnm1FidNPW025JUd6lqWkh5lb%2FTILgVspCiAQCOzsipX1KVWXFqBBWhtRB7D0YjOaLgh%2FHuL6JgyUeQ2JyZ6aaeULiVlUdZ1237lAUfVGJV%2BSdm8Q1SbkUuPSipt5UspQsfFwopaJ8%2BgJjBP505cjPTXHBjPlY9UVr9jJjW55Tald%2B%2Ff5oxSVcIUlKVW88ZTU2XGZGaU4SCW1DSewRjEhLuOdRH2sROtkolrqry3S1Wsvn9LmCCO3cRDEw01kAdkuyP5Aj21RHQVSuhwW0vEqHqBjz4sSRV21XuFyrC0nvBQN4152s8MkwKfz2kj9q4FeqKmM3Okmf4So8uCwlE%2FLqcXYahE%2BK%2F0SrR9sYgYnMKMeBXlGPW%2BuPGpW8BTVEsTKiWAinnE6ecSJ5xNAVRyhEtzC574CfXDXEljCxgJriFx3xLCAmuIXHfEsIDaXDrnC9kPm9hzNZmhtVk0J5bi5Fb5Z6dKkKQQFgHSoFQIuLbW7Y6HqXF7ws1yozlXq%2FAlQJmfn31zMy%2BrEKgp51aipa1WA3JN9h2xxOlaknYx6ETCxzMB2Qvie4R3mVAcBFH1aT1U4kcA%2BTnG5896lTK6rhbzfwV7UsPYCm6c9T5D20sGcoVHmtCiJacAPWFgttJJB1IueRj5stTihyJjorh04rDldhurZSZm4MlcwMqsRL6adw9NrCVycyTcvyi1bIJNlFNx1hqSUkm4dQDMeUmp2XZfxFwVOJm56bkJhxyjO6ZdLQVZxZPwHNICTy66dzFpwTWsFZQ8FCns68upDF%2BH8X5hT87RsPtTa5SXeZQpX5qllqsvoBoKkX8pK035xraVxr4NbDE2cT0fLfM7EM4kpcZoFXmUpkWlDcIKj5SQeQJVGmOIjiUxfxCYqarlbZZptMprPilGo8oAmWp0tfyUDtUQBc9tuwQG3lcR3BU2TbgWYItt%2FZK4Tf7qL7gTjX4WcrcQt4xy%2B4PnqBXpeXfl2JyXxBrKUOoKVJIWSCCD3RxC68pZuSTFPpD3%2FLAeyvzzdSqU5PstqbTMOqcAVz3N94tkTOOd8U9UBcKSm84wkfqiR8ojrrwlFkZ14YZHkt4Eoyf5CvnjkeiG1Qlge11P84D8sdceEvGjPikNfqOCqKn%2FADSoDj8kX5xC474kUbGIajAb%2FwCEfiOoPDji7EdYxHgl%2FE1OxJQnKK%2FLMTiZdaEqUCo3VsQU6kkbHe4jZLefvAwyhKGeCuaATyvia5%2BMuG8ccg%2BeKgc7oDseXz84GnpmWTM8HE3KMJmmFuTScSkmXAcB6SwXuE8yO21o3dntJz1O41KjV5tzLCbpeIsCSk%2FQ3sxg4KRNyzYSCiVWkFKZgW%2B4UT54%2BabD2k32O1iDyIjq7Kviry1xNlbT8g%2BLTAM3jLC9DV%2FY7XqcsJrFGb7Gkk2LiU2ABBPVACkqsCA2viyYo9ZwRW2F4T4QdE3hd6raadOvNzoKmz%2BZ2SEXE2k20i4GojeLrmHiTKXKjh8yIwPxG5OTWOq3KYU8clmBVBJzFLbcVshfWSVEpKRbs0co1nQMa%2BDyyemTizCOF8cZjYhlHvGaZLYjYTLysu6N0lY0IC9JANyCdo50zrzqxdnZjifxzjCdDs7Nq0IbRs3Lsp8hpsdiEjYD0ntgN7DPDgVQLHg6rAFrdXE5JP8AnIuMnxYcMGDMDY7wzlTw84jwvP44oi6NMTSqwiZbCbkoKkqWTZKj2b2JjjBx1SjubxDplQFWdcS86VAdXUT8ZjxnnFRa7xTgIW3vEwHbAc4mAvACLRMlJhFRA2gJm0EEbCLlLoJA2EW5POLlKHaAy%2BjbUb1mLG0hCsUU%2FWjUA8CU2vfzReqSvTSCP3RjyUGWVOY4o8qhGpbk6wlIHMnWIiqcomUxGc5NwZVcOjs3My9azKZnZemrQXUU%2BUKUzT6T5JKldVsec3PmjfchR8AUBoYfpGV9CTT0gqWZ5C5lV%2BxLiyoXJ25AbxkDsoKmuY8XxC2iWDAeenpmZQw3IEKDZU8tY0tjX1Qk877dpijS8vceTdaEgujzMtNOKDU1OaChlyVHN9K0ktugp5WJBNo6FnY2dnTnXrnzufaW9pXVNNOqPBHt8PWxOrZX5OYn6ROIMuV0ptwECbw1Mlh9i%2FwugcKm3Ld103747r4GqHQ8G5GyuBqLj2XxQ1SJ%2Ba6J5IU28wy44VobdZX1mVi5BTyvcgkERxbVZzAFVRMMyTVew%2FPyU0WkSFTWXfGkJJSXEKACmV%2FCLbg025Kj3ZS5qT%2BUuO5LFlCUqZZJDM8wkKHjUre6kX5FQ5pvyIi15unA%2BblPgRdr3FrrirONX9a31LhHmp1QlKtT5aqSDwdlpxlD7KxyUhSQUn1giPTHOdAhCEAhCEAhCEB8B%2BOYFHEzmXsdsSTahv23Pzxz48L09gb7IIG%2FZf8A%2FMdCcdAB4m8y7gW9sc0R6jvHPTw009jYX0C3qJv%2BSAzrD6wmnKQPJKWvjsY25kFnXNZG4sqdfRQfZmUrFNFPmpQP9CQpDmtp1KrEXSbgi24UY09h5V5ED%2Fs2zG28icG5XYvxkpWcOP6NhzDlMaRNLk6hOiVXWXC5YSzbh5IFruEG%2BkgDneA287xk5dVnF9FzDq%2BRkxM4gw8w7LUupeyyVKlErvq0IsE3upVlHcX2tGD5%2FcS7meNFomHJfCa6LKUqfcqDqnZkPLmHCjQjcAaQAVbdpIjKs0ct8vMx8eVPGMvxH5KYdkH0MytPplMm0oQxKso0N60g26QjyiOZjVOYWWWE8E0iSquHc8sFY1mZmcTLO06jvlcwygpJLxT2tiwBPeRAbXwhNOS%2FABjUteWjFWsfhLAjm%2F2w1bXbxj%2BTHSmCZRmc4EsYSj7hQhzFRaWRz2fYUPxRon2pUvpblyZV5wsW%2BK0B0BwEVyanMc5gSU84lbSsIly2mxuHiPyxyf3ev8cdgcDmG5GnYxx1NSq1FftV6M6lX2Lqj%2BSOP%2B71%2FjgIR3ZkLdXCEAL3NPrvLu0OxwnHdmQqgeEMJv0einV1JPfZLv44%2Bb%2FCbrw%2B7x%2Fmx%2FLU6%2BEfKV%2Bhx%2FlgjRkXiZP%2FAH%2FTD%2F6cx5dZj3ZaAnJLE7d9k1qmKt3kS5jxpRfnH0WjY5M7UmqJoqCXQUkqcQn0mKnii09o%2FwB%2BXxxdCiBcjaGmw9ERWtCL9dN7wQpC79ZO3KAQhqa%2FVUfvr7efeIgtXv0ggIgC%2B8V1t2CSna8Uullx%2Bnt%2FJFRMzLu6dLyF7X2N9oCCW7xUQjeIFbLeu7yP4JB27OUVWxvATWAHKJdogtaV6ih5AT278okStvtcBB2Ft4CJtEhBvFRK2vK6RF087c7RQcmGkLstwb9bTeAqaPPFJznaCJlgm%2FTJ52t54jdrV9kTv64CQRFaSOW0RPR32dRFRZlggEPC%2FpgKSEKVpIPM2j0lG14otvskhIdTsbc%2B2PUsdSAopAvFWKetlvy3h5Xnv54j4ywOcwkekQEx3ii4gRVL7IOkzCL91opLfl7q9%2FTdHlbcvTAUVoiWxifxmVOrU%2BgW88UzNSX65HxwEhHYYl0b3iXx2UuodOjaJi7LpTqU8ACL7jsgI2ES6REPGZcjaYQRyv2fHFRaUgJINyTaAlA23HyxKoHu39MTpKB2n4jEqlI5XPxGAglCu%2F8ALE4R2m8SpWyOax6wRFQOsDbUm48xgFmxzh73ENuzUr%2BCeXfyiazaE6tSwOy6O2AkLaVHa0SONkdu0VyoEXKFE%2BZBiiXkk23H8EwEh5cxEiBvFcoWoGyVEc%2FIMU27KNxvCBlOYgA4WsOgjf3QVG%2FmNOP%2B%2FwAcdf8ABmFDhooZKbapGfI848dXvHIOZmscMGHEnmnHqwr0%2Bx5%2FJHX3Bm4V8NNDB5NyE6geqcVHzL4Sv0Ox%2FwBSn2VO1hUa6vR74cCOfoyY%2FwDEvf6RUdHcCiAc4Kmfhe19%2B3qcbvHOB%2FRLv9%2Bd%2FwBIqOj%2BBf8A5Y6h%2FwDu%2FM%2F6REd3TX9QW3oj2w1MP%2FSafSvWcQWri9mgpCbHK10JI7uhXv8AHcRzgx2x0lm6NXFxNjWd8rnxpItp97VyPbfnHNrHbG3odrwS7z%2B7DHf%2FAJer0qhMSLB7IiXmkmyiIlW80Rs4kesR6VqJIliVyblD5U0ym2ygpQA%2BOJenl7lPjbVwQkWWm1%2BzaAiRC1uyJVPsKSSHm%2Brz64HKJRNSqlAGZaHmKwICZSL7xJaJula6nv6Osnq9cG%2FzxL0sta%2FjbH3Y%2BOAWPdEjo6h2idEzLFRT4y16QsRUt0mlbelRG2xuIDyoippMT2aQtSFlCVemIOOs8ukR91ygmEvVBtsb%2BeIOJ7OXbzvEuu5uHm7J7iIn1sp3W6BbbdUEJACYlHMxVLzB2DqD64i2lnUVXuOzeCFMDUbd0VU3O0QWptJuSIlDjI63SpglUSmxNwCPTEq7KuEpt6oih1kmwWm9%2BRMRQkOq5JPoMBRS3vFUaUjlALYQtSFPNgp5gmxgHGCAS8LWPM7QXTBJWbpN4m0KHMesc4mbUwRtMII9MFPMJ5uo9JO0FEmjeKg2iXxmW1%2FZEfJEVvMIHXcTvuDcQEqygm3yXiVTaTuFn0XiXp2SdnE%2BmJytBTspJ894CkpFoijlaIlxm%2F2ZPk98VENoDaXOqpKoCmlsXvb%2BVFVOw2iXWzbrOo1dwPL0jsiOtrsdR61QTCbkLxOTbSL8%2FNFNC2LX6Vr1KidTrIt76jfziCEdhfmbQTpty5RJ0jVjZ1G%2F7qCXm9P2dG%2B%2FlCAqX1dkR3HOJm9ITzHrIiZsIUTZQ%2BMQEg3PUPqhocWuwTtFQp6NQItcx6G203uvtgMtk29PDjnQ6oWKaZS0j11Jj5o2T4NOdeUccUoIa6HxulzZVp6%2Bu7iAL%2Fa2vt33jAEqA4as50gdY0%2Bk39Hsiz%2BURnPgzLip46JbVpU5Sk6rbX1Om1%2B%2B19o8Vp7qwS1nz0%2Fz0uphHy%2BX9crBeK6%2F1QWM7%2Frli33hMWLJS5zhwEkduIJTf0LvF84phr4gsZDumWEfEyiLTkmkozmwEG0g6MQydz%2FD5xmqnLReP9H%2FAIMVhqvcT%2B9Hth0P4RFBOFMvFjkMaJSr1sot%2BIxobOg2zexcEbpFUese8XjfPhEFqGEcvkAXBxsg277MIt%2BONEZ3NlvNrFBULFVRdUdrdpjS%2BDnXgVE%2FvVe0xL9Jq%2FrkYXEkRcKUKBW4EBQtvBJZO5mEajsATYmPeNNCIp5xIotnYzDYvsLrHP44ioJZTdxxKB3k8vP5oCeKahcxBuYZdHvcy0r0KvEXC00TrdSD2jz3sYMZ0XmiUt2PKKqSgjSp9KV7kpPaBv8AJEpflQnUZhNu%2FVBKTRaIaEwM3KBzolTKUrvbSSLxOgtuglt1CrdxvaAp6PPEbRFam2k3dIbA56jYekxTDrA64fQQfPtAVAIjFJU1LItd0b8rdsFPtDSpSyEqBUICrCKfTtbWWN%2BXPeHTtj4XyGAqRLqSOyCHgtKlautcDSBva3dziVTjajr6RIA5g7fHAT6x3RC5vE7aml%2FBP3JiLakuuWuLjstuRyvvAUVo66rRCxj0OIsCpOpQB65SkmwiRtrpN0BxWruSTv3QEiU3ifo4qplnyNKGJknv6JW3yRP4vMH%2B5Jg%2BboF%2FNAefR54WMenxWZuUJkJ0r0lekSyzdPeLCIGSn%2F2NnvwZz5oDzLR2xJccrR7RJTihqVTpzbbeXX3eiKS5Cd1WTTJ25vYeLOG%2Fo2gKSPtBFM849aZCoakp9jZ4lQuD4uvcd3KJH5WYl3QmblXpcrTdKXmlIUR2EBXZAea294mBj1MU2cmQsysq%2B%2F0fldE0pdr8uQip7CVUE%2FnVP6U81eKrsPkgPLFaXRqVfsj0ewta1dH7DT9xz%2FMy9vTtFaXodeClJTRp8kcx4ssfkgKWnzxDT54uTWG8TPKKWsPVJZHMJlVnn6oqowli1zZOF6pzt%2BhHOfxQFn0XP%2BqKlrI%2F1R7zhzEaVqQrD9UBRfV%2BZF9W3ftEU4fr60gpolSN%2BVpZe%2FyQFrJX3xLFzOHcRaiE4eqirG20m4d%2FijxPyM%2FKLDU7IzEq4eSH2lNqt32UBAbK4Z0g5xUdRF9KJq3m%2FMzsYd4PRIVnas33Thmom3fugfljMeGfSM46Vvb3ibudN%2F7nctt6Yw%2FweWkZ1Om11DDVR9Q97H5Y8tpl%2BpLzH7sujh36RT6W1uPpV86qX5sMyo%2Fzq45pWo3jpPj5srOqmJ7WcNyoPoLq45rXzjLohTlgl2jze%2BWC%2BT%2BPq9KWEIznL7JTNDM%2BWeqOCsJTE5T5ZzonZ1xaWWdQ5pQpZGtQ7QLx275fLvh9n8deq4op8NU5RzyxWVjaW9XBs4zlg0I3P9SLnvsPackE%2FwD17BHx6oqI4OeIVZUBgprq9vsgzv8ALHInSrA423uz6cNiMNvc7KJaZRE8bmHB5xCbXwQhFzbedZFvl5RAcIHEGLasCoVq5aagzt6d4RpXgc7L3Z9ON6e9l88nLTCucQjdieDvP8DUrBCCbG4TUmOfpvFH6kDP7V0ftF3%2FAPHM%2FSi3GnBJ%2Fa7PpRvO9t68SWl4kjdZ4O8%2FgbDA9%2F8AHmfpRBfB5xAhIWMCHfa3jrJI39MJ0owX63Z9KN53tvXiS0rC143KrhHz%2FTe2A1nlb80s9v8ACiZXCHxBC9sBE27pxjf%2BVE8Z8F%2BtWfShHe29eJLTHRiJFIAMboHCLxBC2vL9wE33E6yRsL%2FbRD6kbiBWFrRgN7Skm35pZJUO%2B2qK8asD%2Bt2fTjeiMPvU%2FRzzNL6BDQI3W7wiZ%2FN6Ve0OYsQCU%2BMskg23HlWiT6kXiDUpKU4Beuq9rzbA%2FpbQ41YH9bs%2BnG9bvbevJy0vpETBAHKNyr4RuIZGq2Xcyu3LTNsb%2FwAqIDhJ4gyE3y2mhqF%2F0Uzt6etDjTgk7L3Z9KN6O9t68nLUMmmRVPSqKuqYFNW%2B2idVLJCnky5UA4ptKtlLCbkAkAm28ddZEVrhAwpjaoV%2BXzZx1MVaaw5P05TuMJbxdtyWfQGnkIWkKK3%2BiACQTyAtyjUC%2BEjiBBTpy6nbr8kdO1t6ettE31JPEJpB9zqcsQDfp2drm1vKieNGCct7s%2BlG9Pe29%2BTlb8cUzhxkcIqlcqMyMyp%2Bdl51l2So9cpqGpAtg6FrKkmwWG90qtqNrHmYvPCdmnhDJ3OVvGWOJiYlqT7D1CUMwwwXih5aU9GlSU76VFJTcciR2R4%2FqUOIU2SvLubCvPMsEeohW8So4UuIFQP%2FAAdTqSBcAvsi%2FwDKieNGC5Z912fSjejvdeo22cshyXzbyxXljXcgs%2FJKpe1GpVV2u0esUsK8apc845q1WTuNJstKwDbUtJFiIn4qcycAY1Tl1h%2FLjEc9X5DBeH3KY%2FPTrK0uPLK0aFLUvdaylu6j3mMe%2BpP4gbXVl3Op3sSXmbW776oivhO4ggE6Mu5w3ulSfGGQoH0auXnisaV4F9cs%2BnTvIw69TsoluqjY2yBlOBz2iorlA9siaA5U1UgOLTOIxB0pKHEDmHUm2kg6beaIcIOLOHOiZJYkwpmbiDD0nVMTTU%2FLYhkanNLbdqEkhAMt28tyUlFjqG%2B8aUHCjxC%2FCy6nRpG132fi8qJXOFniCUAF5aT6urfdxo2819UJ0rwL65Z9Onet3svfk5agbQUNpb0aEIT1b87dlz2m0S2PdG4XOFDiB0dJ7mtR%2FgutH%2BlFIcKefqjYZaVYeno7fzojjXgcbb3Z9Onejvbeo20S1EUbRIUG%2B0bfXwqcQIX0acs6qv8AdJ0afj1RD6lTiCBscsKpe1%2FgfF5UTxrwOdl7s%2BnTvVnD71H0ctQ6TDSY26OFfP0lSTllVApKQq129%2FMOtziZXCln%2BkJJyyqnW87e38qHGrA%2Frdn043q9w3ryctP9GYBs3jb44Vc%2Fjzywq4sbHdr5OtEU8K2ffWDmWlUQQLi%2Bg3Pd5UONWB%2FW7PpxvO4b15OWow2Ijo88bZXwsZ9IUEjLiqHzgIsP5USDhaz%2FACTbLSqHu0lFz%2FK2hxqwT63Z9ON60XG9eJLVPRw0eeNrHhcz97MrayPU39KI%2FUu59aSfcwrdx2aG%2FpRPGnBPrdn06d53DevJzzNUQ0eeNsK4Wc%2BkaNeWVYGskeSg6fTZUBws5%2Fk29zGrAbbkI7f4UONOCZ5Te7PpxvTGH3qrVFnLU%2Bjzw0eeNrI4WuIFdwnK6r6htp6lz%2FKtEr3C%2Fn4yR%2FwYVdY7dAQf6UTxpwP65Z9OnemcNvcbbOVHJXMWjYG9kKNXnugkamtDomtJUG3h1euB8EjTuORHnja0ziPIesTi6hV6th5%2BafsXFuMtLUoja5JTe%2B0amPDbn0Lf8FFe3%2F7EfPGG4nwTirB1QTSMZYYqFFnXGumQxOsFtS0XsVJPJQvtsTzjn1WeE4tbzXdrxTNVW2KaonqfQcG0%2BxXArhTcrWwiuijZNUTnEeCeSdupvSoy%2FDq4SqXmsNFwdjiEpT8Yi2CmZCKJUHcKkj90r540H0fR%2FpcOr8JuNqMAs42WlXO6EfCza5fhXKzn7Pub59gsgnVkpdwspR5gukfJflE6aPw%2BtuJ2wog9gK1KB%2BMxoPQyrYtpPpETEhSdBQCnz2i0YBT5WrnYqvhWqq%2FYLLm%2B5vv2t8PWtCDN4XSVmws4T%2BWCKNw9JISiawupROkalkXPojQQShPJtIh1O20T3hp8rVzlPwqVR%2BbcbLmjc32aZkAQFIfwlv8AbOERVRR8hrhSXcJm9yOZuL2vzjQA0J5JT6xExcChpKU2vfZMT3ho8pVzrf8AlWv6jZc33Ogjh%2FIB5KWw9hVGvdJ12uPSYirD%2FD8whIXN4V1E2F3hb1xz4SyRZQJHdbaIXY7vkEO8FHlaudWPhUrpnPuGy%2Fr7HTOAsI8N1RxpSpTEKMJvUt5%2Fo5kuvaEJFiQVKJASLi179sbeRltwNDqNy2AFfvqh8644KDmvqL0qT9r2fEdomsyeqploju0pjuYZdrth1nVRaUzXnOecz9z5xpji1vpXfaL3TTTY8GnLKmNU65nPVMa9bvJeX3A81q%2FO%2FAA08%2FzWD%2FSgjAHBA%2BjaUy909%2FjaR%2FTjg8pZ%2FUE%2FJEdLKur0DfrSI6fdNy8j1%2Fc8lOG3qfp%2FVntO8xl1wRLCkJl8ujr61vG0kn0db8UUH8tOCFA6TxXLsi1v0bb%2BnHCIQwm1mGxbl1BtEvRS17%2BLsX79A%2BaL03u6Rssev7le9l48v1T2ndTWCeChtHRtU3L9aQCQFTiVWtztde0Tv4V4NXXNKzgVC736tS07%2BpyOE%2Bhlzv0LP3A%2BaI9GwkWEuwf4A%2BaJ7tuvkeuNyYwy9eX6p7TuxeCOESaliyZrBDrCz1mlVUqQSDtdJct8cVG8OcLzEuiWk8VUBhlrqNtS2KJhpCB2JSlLwCR3AAARwYtDP6g0PQkfNFMolu1lv7kfNExfbrH0PX9ys4VeJnXeJ5p7TvZL%2FDyws9DjqVQo%2FCRiyZ%2FrrRbsSNcNmJW5cYjrVCrKJAKEuKpWlzQY1W1aOkcVa9he3OwjhfoWeyXbt%2B9HzRDoGP1u39wPmiJv138l1%2FcmMItonP4%2FqntOxcTZw5TZX4OqNMwJM0Zx5yVfZp1NpVlI6ZxOnW5p5Jsdz5o4dqqQzLdCg6tCLfJF90IRuhCU%2FvRaLFV%2FJc%2Fexr3q9xeIpoop4NNPI3bhh%2FcfCqqq4VVW2fR5s59rCnTEqDBwxKgmNNvvU25ojIcOYzr%2BGahLVSg1udps7KKC2JiVfU062q9%2BqtJBHLlex7YxiPbTZB6oOltt5lpKE6luPOBCEJ7yTAdLULwgfE9RZYSxzAYqiQlSddUprMw4bm9yvSCSOwmLJjnjc4jsc012k1bMmakZOYSpDrNHZRIhxChYoUpsBRT640TUJKYpk0ZOaLZXpC0LbWFtuIPJSVDYgiPIT54CvN1BUwsqUpR1EklRJKieZJO5PnO8eIudkSuLtFLXvAVokhfa8XCjUV%2BuOraZnZKVCbDXNzCWklR5JBPMmAtxJBiGr0RGalpiUmXZWZT0brSihSSb7g27IpwE%2Br0REEGKcTA3gJ%2BUTXEUwbRNAR1GGow0mGkwE0RAvEImTAbt4Ukk48qquwUog%2Fdj5ovmYAdlslqrOJQq0xiShNJcSPJLcnNKKb9%2FWB9EWjhMt7fapq5exwv6NcXisYcr%2BMOG%2BnGjS6X3JnGDjiwp5LYV4vJOnQLkBSwkk2G9oDQYqQCdPTqI1a7E%2FC7%2FAE%2BeILqIXr1OX6RQWvrHrKHInz%2BeMj9xDMNNulpPR3t5TqfniHuI5gltLqaclSVHT1XASD57QFSm4LqFXprNSXV5VtE5dfRuElRF%2BZt6IhP4Jqssw%2B6avJujRrWmx69twIulNylzILbMql%2BaYI6vRqWEpT5rnaITuVWYjKltKmZ1ZGxT2H4tjAa8FRf6wW%2BolxOhfW5gG4B7xeI%2BPi19atWkpPWJuD2G%2FMRszAeUWK6LjfDlXruEvHaYxU5Z2cYmEBTDsuHB0gWAb6Sm9%2FNeLXWcisdNz00%2FKUXTJOTLnii2lamnGislJSruta14DAPHn%2F1dXklHldh7PR5op%2ByM63p0PudVNk9bs7vR5ozIZKY%2FUFFFFcVoKQTew35GItZI5huqsmiK9bibQGFOT86%2BkodmHClXNJVsfVFeWmnk2uskRmasjMxAtCRQwdfI9MLRFWS%2BYTCuj9h21qF7hD6Da3rgN28GN1Y3m2Fc1zNHWn%2BDNk%2FFGyuOcD2bwgO3xWdP%2BeTGI8HWFKxS8avPz7AQkGmBYSoKKFCaJAUB5INjYnnYxl%2FHKE%2B2XCW2%2FiM5b7%2BIDlxYOhyOwZJ51inSLLJKlJl2Lq097aeR7BHIy2itNk9pjspumsLkJDxdtRUmXZ6pNrWbTz74vZTlX9m5jtvzHilw5N7HVr%2BEntPpi7Yfn5miTbdUlW0OhsFqYYWeo%2BwoWW2odxG3mj0syDzSFuNyy1LULNI5XV3XjZlIyPrUzSGazPJabbm3PekLNr2B1JCh2%2BbmY2Jtaaaopqna0%2Fi5mM4a7xNIssSjE9hx1yYprySrolC78t%2B4cHcOQX2i0a7rDlYl1rmJWSZWvddiiyifPG2MaYcxnl9U2Omkw%2BlBD6Gio6bH9JCk9p2uL%2BaNWY3zSxTNFqZknxSHphClPNU2WS0004nZIW3uodgNzvzjas4pmnOZalrTXnEUwx6RzKxRQalLVOmuol5yTc6Rh5tsEoVYi9jseZizMV%2FpnGKXSZGZqNSmXNEvIsJK3nnVHkAO8xi2P6PjyYwy3mFNU5iSpNXmRLialWujS86BupIv3g3I2vGHYXxxjjAc07OUZ51tM4gsrmG0hLxSfKCHrakEja4IMYqrSJj8XLYosKqYzq5s3TbiWcsqXN0NVVam8cVtjoq1MSjt2qRLK5yAUNi6RYOW2A2vuYxHpG9HQIcSlWnTGGYdxJJ1KVbMqSkHZaF%2BWhXbq7z54yuX1uN9f4SdKorZRFFEU55%2BGfDJacLhZ1LdWaOVYfnJhQQXEBd033023jBqewG1IX8FMbSnktooFTY6ZatUoogkDcptt8R3jWDWgJT75EWkZTDNYzMw1FjN1bNWrSknZyYUPkAixYela5XanK0Ojyzs%2FOP%2B9y0skalrVuQhA7SewRfsYtdNP1hf2syr5D%2FriyYUquIMNV2VxThebflKlRXUT0tNMeXLuIUClY9BtGpVtbkbFyksVzVIcamJaXbcUzspDoKVJWDuDHsaxNO4omzLinyzThQ44PfSNRCSbb%2BiLPSaTXcZVj2Oo1OcnqlNqW70bY67qt1KsO08zaKDlKqNNm1ysy09KzLRstJFik25fEYqlRcrSVn3yVKf4Y%2BaKfso12ML%2B7HzR5X5ZTbikBJVp%2BFpMUuid%2FU1wHu9kG%2F1BX3UPZBv9QV91Hj6NX2ivih0avtFQHs8fl%2FhMK%2B6idNRkwLGWcP8MR4OjV9or4odGr7RXxQHt9kW%2FwBRV8cPZFv9RV8ceLoXf1NXxQ6F39SV8UB7PZM%2FqHyx6pd9EynqXSpO6knu7xFp6F39SV8UXGnSzjetxwWUsaUp7SID0mIEd0ehuXJiZUqR2QHkse6EexMoSNx8kDKemA8cVExVMuR3wDB7jAQSSN4qJfUNoplpQiUgjnAenxiJVPg9seY8olgK6nQYNkqMUFXiqwbdsAeFopgRWesYpJgLnQh%2BecqDyMy0n43Ex1z4TYlHEPJtnswnR0fEyb%2FjjkjD6dVUkU%2F%2FAFjH%2BlTHWvhOTq4lUt%2FqWGaUn45dJtAcduc4kJ74nc5xIReAazFRtUUtMVGxAehCrREuW7YlAFoprgKwfV3%2FACxKXD3xQiIFzATlxUS6ld8TBtRiYNKMBTGpXbDSe8xWSyvuicS6z2QFEJPdE6QYnDKhEwZXAU9JiYG20VAyoxHod%2BUBBF%2BcXCTO0eJKbbR7ZaAzClf2q9Z%2FHFwyolhNZx4ZSpVktTgeJtfyElX5It1LJ9i%2FWfxxfskJ1Elnfhtxx0tJcmFMlxPlI1oUnUPOLxWdkrU65dq4IxFgqaqwwpjEP072Xn25lFQKQ5IuPJQUoYnW%2FKDd90uJuEqvqBEZhMY%2Flsv5GdQ5RV0%2BXS8WVMSt1yilJ2JSAShKdr3AAMYHhSnUqpYkp8tWHES8qqaKA9MkIadcBOgKc5ISpQAJOwvHqzWxDiCvVxWGcQYInMIGTl7zVP6riXCDbWHBsppQHVKbg77x37KmiLWZqjVt%2FwDqP6yeevM1V0U007dn2Rltnw%2BDwsIkZpOOsS1Wal52Vdqkw6XJaXU9ZU8i%2B4bUqyS4lNj0d7kXtflFwQJmXYdpjkipL8qoKIUAg35ELHZ6R3bxRnMH4Ipsl4%2FQp6oMzqQD7EzzSXW3yf0yXfRbSRz0OJBsNjFyobFdr87TcMyEi9NVWqzAlGBsslSvhKNyQANyeztjDeLSJztZbF1ommmLONfJD6I8N83OTuR2D5ie%2By%2Bx4Ryt1ErUlH8kJjZMWfB%2BHZbCWFaThiU%2BxUuTalUn7bQkAn1m59cXiORHndfYQhCAQhCAQhCA%2BA3HWdPEvmVtbViOc%2FHvHPUwbyksnT8AEj0x0Hx1b8TOZdri2I5z8Y%2F%2FADHPEyQJVmwO6UwGc4d%2FQtv%2ByR%2BONh5a5lO5aVCpTyMBYSxUmpMts9BiKQEymWKFFQWyfgKN7HbcW7o19h9P5mPmbQI2NlLlJjDOXF8vhbCcqtLSVJXUqmtsqlqdL8y44RzJAISgdZarAQGy6TxJzddq9OoUvkbkpSVVSbZk%2FHp%2BjDxeV1qt0rpCQQhIuTFTinzVy3xNUGMvMrML4cEhQp4PVDEdNpzUsZyZQgoLEsUAEy4KiSo31EADleMeqmL%2BGHDVTew3J5M4rxNSpN0y81X6jXjI1B5SSUuONSqU9G2kEGyVm%2FfGP5l5TVvB2vFlEw%2FXxl%2FUHGvYSsVWS8WddbcQFJS63clB5hKiAFgXEBtzBM4iT4DsbTZR0hYxVdIvzPTS4t%2BOOel4vnW3F%2FmZryvtyY6DwVJrnOArG8o04lJdxYm6zySC%2BwbmOf3MFzHSL%2FPCX%2B5MB0rwF4hdqOOscSz8qhKPaopwrCuVnTt67%2FJHI3d6%2FwAcda8CuHXqXjXHcwubbdS5hXodKRbfpib%2FACGOSiLW9f44CCI7tyDSE8IqW%2FKJpld59%2Bh68cKJ5x3PkAtDnCSdfwZOu39SHY%2BbfCfOWHXf%2FVj%2BSt18I%2BUq9DkrK8JXklipXaisU4f5gxPRmiueaUlDalNnWkL3SSBcXHaLjlE%2BTzcu%2FkljSW1tma8dp0yy0FjpChDYDi9N76Rfc2ttvFOnfZxYX6i%2F5pj6NZ7HJnaxGp545j0wolnajJuqS0hVzTZVNrjkLN8o8COI%2FMdryZqT9clL%2FwBXGH4tqElUJxC5BwrQ0w20V6bAlI3jHIuhtJfEjmWt0veOygUQRtJS4AB5%2FpUTN8SmZzYAFQljbleSltv8zGq4QG2DxO5rKUVKq7JJtzk5Xs5fpMR%2BqazW2%2FPpAsb7S0qP%2FZjUcIDb31TmaXW%2FPpHWNyPE5X%2Bp88Sp4m80kW0VsptytLSot%2FmY1NY90LHugNqu8SOZ7zaml1hBSo3UPFZXrd9%2Feo2U2lSJkThbQpRT02ki41FOrl2i5jmC1o6rYbClgK6g8XNx2gdDzgNW1HO3Mqnsyq3MQuPF1oOp1MMjTe4sOptyi2jP3MQFSvZQlSgQSUt335%2FAjFq9OsTbEi20SVMSgbcuLdfUSfxiLDAbJHEHmQnZFV0jTpsEN2ta32kTDiGzLSq4rSh3gJb3%2FkRrM8okN77QG0xxHZo20%2BzzlrW8lr%2BriRPEPmWm2msrFiVbBvmefwI1dv3xMLkQGzVcQmZC%2FKqyyO4hv6EDxB5jqSEGqqsBYDqbfyI1npV9qYaVfan4oDZf1QOZTgDBrSwhRA06W7c%2F3kbZ6BDetbelS20lxOqxGoJuDbkbHeOXWkqDouDtY%2FLHVUqNT2kNld2VDQPhe9q%2F%2FPqgNa1fP7N6nGW6TGtQe8Yl0TAKksAAm45BrzRahxHZrJ8jE00n0dF%2FVxh%2BIJlid8RTKq1IlpNtkqtbURck%2FL8kWMpF94DZieI7NhFujxdOIsLC3Rf1cVfqlM4NZWMZzgUTckBkX%2FzUashAbUPElnAV9J7dJ8Kve46H%2BqgriTzgWDfGc%2Bb87hn%2BqjVe8N4Dah4lM4VbnGM0T3lti%2F8Ao4lPEhnAopJxnOkoN0khnY%2Fe41dv54b9t4DaSeInOKZdbQ9jWdWkqSmykMkWKhcEdHuI2G%2BBJ1Wael0JZVLrfeRYAhtYQpQIHLZW9vNHOMslTUy3qOkIWkm%2F74R085INzVWqCQdIW2%2BsX7PeFKgNb1rOvNqiCVYTjiqLDks3MgrU2T1tx8CLQeIXNoqClYxnioG9zov%2FADYxnEtQlqomQclVqUGKewwslNuslO%2F44x4bmA2T9UPmxtqxdOq08rlGx7%2FJiP1RObvTLmBjWohxwAKVrSb2N%2B1Ma3KD2RCxgNnDiUznBSTj2qkoN03dTt%2FJiT6o7OLUVe3ipb7n3xP0Y1nY90TdGojYQGyk8R2b6FBxOM5%2FWBbXrGr47RT%2BqHzd09H7bpvR3ah8141v0DkTdA53wGy2eIPOCZfaZXjaohpxaW1oDo0qQTYpII5EbRnNRaQzPvttJCUhZsAOV97fLGh6ewfG2taeqlxBWe4ahHQlTZ1T8wrUnyh%2BIQgXjM9J%2Bpcw8oeSMfuX9PsefyR1rwXo08NNHP28rPq%2BOcUY5IzgnqZI5AYYwdMVqnprhxYqpO0pMyhc03LqkrJdW2kkoSSbC9jvHXnBs4h3hsoimkFOmQnGzc3usTS7n8UfLvhMme5LCI8pT%2FLW7eExnNXo98OAlkKmXSnl0zoHn98VvHRvAoB7sNYX2jD7gHreQI5uBPSq%2Fvrv%2BkVHSPAqUpzdq1ydSsPvEegOtk%2Fkj0Om36gt%2FRHthp4f%2Bk0%2Bles1EKXxjVJDikhHuZOc%2B7oT%2BWOcV9RtwnbnHR%2BZ6JVvjSqCJ2cYbE1l2G0hbiUalqaAS2m5F1nsSNyeUc6zEs%2Bx00rNMraebWttxtaSFIUCQQQeRuI29D9WCXb%2BCFL98vV6VXFeb2McDzc7ScPtUBuRpkwzKNNu0WXfOnoErupa0lS1EqJKifRaMR%2BqWzG7ZHCx9NAlj%2FRilmxNyXstX5AOWfTVm1oQfKKBLJBJ9caxWLR6hptovcS%2BYrtryWFk23snD8sB%2FNgjifzHaGlFPwsB%2FwCQSp%2FoRqggX5RJYwG3TxTZmk38Xw2B3ChStvi0RBPFBmSk7SOFj%2B%2FoEor%2BhGo7G9on6FR7IrI22nihzKF7yuGFXN%2F7RSu3o6m0RPFHmMposmn4Y0E3sKJKjtv9pGo%2BgV3fJAsKCgLc4gbf%2BqjzOc%2FScNfxFKf1cX52szmK5KQxTPsSUvO1OXLkz4owllta9RGvQmyQSAL2AjRUizqdKVJje2F5fxjCGHngm6FSjqAe8pdWDAePE2a2L8Mrm5WSapHisrPKlWGV0thVm0oHNRTqUSdySYxk8QWOCrWZShX7xTWR%2FRiGa8zKeyNap%2FTJ8ZYrj6ujHwUFpPyXEa00%2BaA2ajiDxs0NpOiE2tdVPZJ%2FmxN9UjmBqBMtRTZQUPzuZ5jlzQY1aU27IlAvAbaTxNZjJWpwNUcFV72psv2m%2FwCpwPEtj4jeXpN7abinsXI9OiNT6IiGlHlAbV%2BqUx7%2Bt6T%2FABfL%2FwBXEv1SuYYGlDNHCe402XP%2FALcatMu6hCVlBUCYilhSlW0keaA2s3xJ5jW6rVEH%2BTJf6EZKqbma5LtV2eSyH59jpXAy0ltN76dkpsBy7BGjaa3rcjfOG2Eu4XpjtwpLsr72q1ttZSR6biAnxLn7mZgx1%2BmUubpCZKUmFykswqiyag002lKQNSmytR3NyokkmMXHFDmfr166Lf8A8plrfF0dotWakwwudnpH%2B6ZSrTiXgdiL9Hbb1GNdpRaC7bf1UWZwJUPYZNzc2pcqLn73FZfFlmqoaS5RwPNSpT%2BqjTjibxT6IHsgNyq4r81VpKTNU0g8702U3%2FzMSniozPUQpa6WogabmnSvL71GnOiHdFUo0pvaA279VLmZv1aVuLf2ulu%2B%2FwCpRI7xQZlu26tHFjcfnZLc%2FvcalDKlKAF94Fi3YYDb7fFBmgtSCpdEIA0kijSilW8124yWbml19MtVp1phMzUZdDkwphpLSFuEkawhNkpuALgAC940RT0IVsRHQFJlw5RcPvtgKC5FkoPO%2FvihAY3iLOPGGFHlU2TlqOZZDrzTLTlJYV0aW16QnUU6lHtJJO5izDiKxyk6hT8PX%2F8AKmPoxa81XGHK7MSqHgt6Vn6g28LeSrxg%2FjG8YUW0pTciA2MeInHF1fnZh%2B6jcn2KZ3%2FkxUHEjj1N9NMw4LjT%2FaeX5fcxq9YvyiHRmCuTag4mcxE7IkMOJG1gKNL2H8iKh4n8xVApNLwvYi39o5fl9zGqAwpXIw8WX9tAybTHEtj%2FAH10rDS7m%2B9GY2P3MTI4mcwEIWj2Jw0UrIJBozHZ%2FBjVXiyx8KIFu0DJuml8TeYaXkIErhlAUoXAw%2FLG2%2FnTGRGemKtoqs0hlL84gPOBlsNo1Em%2BlI2SNuQjRVNQhDrClKTuofjEb7pLKV0SlrStDgMokhaRsRqURY9vOCGUF23DZnK1oIvIUg6%2Bz%2B2LOx%2BKNkeDMdfUMbSqXSZfx2lPKb7A4OlAV9zceuNf1FtElwu5tPTT7THjiaW1LoWsJU%2BUz7RIQOarWJNuVjGeeDMSgTeNySoL6elAC2xTd25v33jw%2Bn85YJaemj%2Bel1MI%2FSIa%2FwCKJerP7GY26s0wn%2FMpP5YtORe%2BdOBEfb1%2BVH4z%2BSLjxQqJz8xr5p9kf5hEW%2FIsas5sBaVaSK%2FK%2Bvc7RtWtP%2Fqsf6H%2FAAY7H9Kj%2BKPa6E8IdpOEMAX8oY2at6Cwn8ojRmeYJzaxJ%2F41Ubs8IjMMNYZy8DkwGwMZJcIvYBCWUXV6riNQ58Mf8KdZn2yh2Wnl9PLzDagtt5F1DUlQ2ULg8o0vg5pywGj%2BKr2oxL9JqYTOY5xDl5hBNXww5JNvTE443NKmKezMqUgJTpSC4lWlIJJsBuTzjETxM5hqv0jVJ3JJApksBvz5Nx78x5tmTy%2FlZN0qDk9OzBa22IbS3c%2FGfxRpYpj3bTbXd4mcwkIshFJT%2B8psqP8A2opDidzOCy6JiT1K5nxKWN%2FT71GqltgxL0UBt1vipzZZGlmoyrY7kSEqP%2FZiJ4rM3lc6w16RKSwP%2BhjUQl7xMJXY7QVltj6qjN9RJVXrk8yZaW7rfqMTN8UmbbSNDNaaR6JWW%2FKzGpxK%2BaJQxpVyghtv6qXOPR0Xs%2Bkt%2FaGVlSP9DGRYYzKxTmXIzzeMJ9ubVT%2BjEqtMs0hTVybgFtCbg33BvyjRLCPPG1coAAzWwkm7aJe%2B3YpVufqgMoxPi%2FEuX2H5acw1PNy3jQeemSllClPFC0oAUVpNgm5sB3xgyuIrMgoKfZFO51boatf1Nxk2cM4zK4fpVOdU6pU9KzZZGgFKSmYRcX9Aub%2BaNGhs3gNko4icz279HVkJv3JR9CKv1SWa%2FwC2Fzlp%2BBsPN1I1ipvaKaGVazcm0BtT6pjODSEpxZNJAtaykdn8CJVcS%2BcavKxhOK3vutPP7mNbIlwREHZXqwGxlcR%2BbijdWKHie%2B6QfjCYo%2FVDZp3v7Y3799x9GNeiV27YkcY0tOLB8m3ywGzE8RObq1BwYumARyusbfyYyXDWNsU45p6nMTVfxsyqgGFOEEN3NiL2vvtty2jTVMB6ONm5XuNuMVFhF9bCm1L9Cjt%2BKAyzEeYePcusNyqcFYmnKSwrpJmZbliEJmHS7oCl7EqKRsN7CMId4l863r9JjyodYWNnbX%2BIRec3JxiWoFJp5adS%2FNS76780rSmZFiO63KNQlsDYwGwvqkM59ISMfVYWFhaaULRIOJDOpKShOYNaSkjSQmdWAR6o1041dUSdD19MBspPEnnWkaRmFXALk%2Fo9ztFoHiPznUSVZhVwk99Qd%2BeNcCXuk7ROZbyduyA2IOI3OUHUnMOuA31bTznO1r84gjiMznSnQjMWupT3CfdH5dvVGvBLXUodwvFFxhQRqEBsw8Qecak2GYldT501B0W%2BXaMvw1izFuP6A6%2FizEc%2FV1MzDTjSp%2BYU%2B40SFBQbUq5CSALp5bXtGmZOwRG28pFy01Rqs0khTkpNy6VC3LUlZ2PxwHqzBxfjDA9FpPtXxDUaYz4qjpG5SYU0hxxbqyXFBJ6yrJABPIC0YGrPTNRSQg42qpSOQM69b%2BdGS54T7LUvTqK4k9O5TmJpFiLdGHnE39N%2ByNTaNoDL1Z4Zpm98a1cX2P5vf3%2FlRROdmZ2kN%2B3asaRyHsg%2Ft%2FKjD3WLnYxT8W8reAzRvOvM9tQKMdVsEbA%2ByUx9OKnu05oklXt6rVyLK%2FPGZ3%2FlxhCZU2iu1Le%2BC5gMv92jM3QF%2B3GrG3YahME%2Fz4g3nZme2QWsY1VBSNIKZ6YFh93GG%2BLuaF7xL0CkpBJEBnbWdWZd0qcxrWbpNxoqEwLHv8uM9wvXq9iemiertXnqg62AW1Tcyt5SArewUskgbcrxpFtADdjG5MsJliZwzMpTs4w%2B2yr0hBJA%2FwBcBufhsl3HM4ae22jrNMzLno94d2jD%2FB3FoZvVLUn35WGJwNG%2ByR0jev1kAD1xmGSGJsKYBxo3jDG9dk6NTJND7Spp8m63HGFhLSQkEqUQCQAOyMR8HqypOdE5rFiMMzpt3Aqbt8keV00iO8l4n910sN%2FSKfS2Tx7m%2Bd0md%2F8Ai5LDn3OrjmxcdIceZSc72AOacPSoPrdcjm9e8bOiX6lu3o98ta%2BfL1elK5cSzrvJSEKI9Qj6QSlUl8ruGSnV6iSjQRh3B4qjLJ2Q48mWS6oqt2rWrc84%2BcD%2FAOg3usPsSh8kfQTMRt1fCFUm0WSRl24bHtCJZBPyR5H4RqYtbxcbGvXTNc5x0Y9kzzujhczTY21VO2Ihzy1xZ8W88tuoSmTXTyryUrSJelTCkEHlYgnv74uMlxWcXDkuXF5HMFKdi4uRmU2PnF9vRGiM4MRYjkcw6tK0nElakZIS9OdbYlak%2B00NchLkkISsAXNz6411J4gr0zL9JMYkrK9Sjq1VF86vP5ceostFMEtbOKqrtTnMckZe9zbS3tYrnKZj7Xck%2FnxxXIp0zUqDgmh1puUmGpdSZSnzQUpSxfqgnewBJA3FjFhRxMcaxFxkBMKFr3FImo5BFZqSVJWmv1UKQrWk%2BPv3SrvHX5%2BeKjeMcTLaL4xZiDmT%2FbWZ7OZ8uLcT8D5bvSjuq28Z2PI8TfGI9OMS09kZ4i26oBb79MnAhCSd1Gw7LfKI9Vb4j%2BK%2BltsO0%2FKyn1Vb3SdIJemTw6IItsbgbm%2Bw7Y4tp%2BLMWz7HSoxTWUJ%2B1VVZr49lxBGLMbPTDifbXWrpN7mrTXPze%2BRXibgeecXeOved1W3jOu2uLHjBT9kyCW5vYWps2m59Y7YudO4rOKyaUU1DJNmmtDUPGJmQnSnWBfR1U%2BUeyOMXMT43v%2FxurX8bzP04mOLsZadJxliG3Owq01z%2B%2BQnQ3A5%2FZ4553ndVt4zsqd4qeLCUcDDOSbE%2F1dRdlpGbCUn7U6h8sTM8UvFoGw7NZCONpVzBk5gK8wvaOK3MT4rcGl3FleUO5VVmD%2FTjz%2B2nEyqhKNO4mrSkLX1gak%2BQbch5cTGhuB%2FV4553ndVt4zuhzih4rFJAZyBdC7i92H7bjbsigOKfixl3EpneH5aQpOoDoXwSL2vuI5hzgxlimbwflc1OYgniqSwZLSyFtzDjalteOzagFlKuuRqI33A2jWIxHiC%2F%2FGCrfxg99KJ4m4F9Xp553p7qtvGd5u8TnFEtsvMZR0pdm9YZLM4XL28nybXi3L4sOLlBsrhwedF7EiUmvmjiI4hr7SA4rENWAHK1Qe%2BlHoqGI8SSMuJg4jrCgbWvU5gf0opxLwKf2eOed6Zvlvl%2Bc7bb4uOKpZSF8Nz6ArtLc19GPZPcU3E3JNdMzkfIz6iQA1LibCwD8LdFrRwt7PYvWx0pr9T02vY1V%2F6UeeTxDiRcuFt1ipBKxcAVF8W9WqHEnAuS7xz1b0xfbePnO3kcYvFKAQ5w2vL7jpmAR%2FJi40zjG4g5pn808PjrCnbdE6t19LY33J6hJFu6OEUVbECfLrlSP%2BUXvpRN7M1kbGt1Tnfafe%2BlEToTgXLd456t63d1v4zumd4xc%2BJbWVZHtTL32sq%2FMnQkfCILdzfzRBjjNz4m0ak8PsySnnZ9255Wt1OV44WRXKw1fo65VkX56ag8L%2Fyo9dBrFZm1z%2FSV2re9JSn9Hvct%2FwB1EToVgWeq7xzzvRN%2Bt5%2Bc7qd4wc%2BUMFxnh7qLpQCXF3cShNue%2BiPKONfO5Cx0vD3UClQukoddUFDzEI3jl%2BoY1xU1w2UmktVyfRKJzAqa2VCadDyPztlkrR0gVfQeqdN7XHnMa2bxRihq3RYorSNIsNNSfFh93FeJWAztu8c87zuy38Z3u7xiZ2rLSkZBoKVC%2Bhc48HB6uitFvmuNzPeWWtpvhtqroRYqI6cpA79m%2FljiJvF2L1uhlGMcQalJ1f21mPpxKvG%2BNm5vxQYvxCQpI2VWJgAfy4tGhWBx9BHPO8m%2FXidXCdtS3G7n9Mqu3wxVdxF%2BaRMcvT0cXn6rzPxGh1zhqqa0FAeUhp98r0HlzateOFJrHWYEnpR7c8QpSSLaa5M%2FTiRzGuP3EFJxhX0AixtWpk3%2BNcJ0LwL6v11byL9eI%2BdLugcY3ELMFXinCriYj4OpuYV8fvUe6Q4s%2BIydGtfDFVW7A2C0zCTf1tco4GTjfHabhWNsQ78%2Fz4mfpxTcxdip23TYsrzlhYaqpMH%2BnCNCsC8h11b098Lx40voCOKjicT0mvhnnuqLjo3nSQfQWvXFM8WPEyFtJmuF2uAKPvaktvKuPvcfPOYxHXgFFrENVSobgife2P3cXd3EWJJSiy0zL4orjZcCVLCKm%2BNR37NcW4k4FP0HXVvR3wvHjO9Zni74gmdCE8M9fU5YhxK2nE6Fdn6Wb3jyTvGrnjT0dHNcN9aQ6eXvrgSkXsb2b5jzRyVQsZYtTkRixCMR1RWjFdEIdXUZgPMkys5shQXsFb6huDpT2gGMI9t2K%2BXtur3Mn%2B20xzPM%2BXFJ0JwL6vHPVvO%2BF48Z3NN8bOdMuppJyDnx0gvZT7o%2BQt3jyzfHXnHKOFo8PdXKkGy9JcWPUejjiZrHWM3AX2sc4kJBKNQrMzfbs8uIyWYuYc2rTL43xPz%2BHXpkf04tGheBx%2Bzxz1bzu%2B8T852w3x8ZoBR6Th1rygOdg5cfyI9j%2FHNmm02h1HD9VCksCYPvqydJ7LdHz7CO%2BOHkZkZl%2BNqa9vOKUqDQ1J9n5nlfv19%2B8TTGP8zXyL47xXsLDViCZVYfdxPEzAuW7xz1bzu28eNLtZjjvzcfdDSOHTEFzySEuX%2BVEe2W4186pzV0HDZiM6QCbrUnY8juiOHvbrjuZv49jvEq789VamVX%2BNceZ6uVx8aX8SVh0adNl1J89Xu3XyieJmBfV4553qzfbx48u9HuL7Ppp9m%2BQDjLUyjpWg%2FVWgSg%2BkWivIcX%2Bf8AVpoy0lkVLvrISpLTNYlivSTYbW3j5v1Lrvy9utqV2kqv6bmKCJcLeb94TcK5pFomNDcCiMu5qevev3ZeJ%2BfL6dVTiyz2whTpuuY44asRU%2BmU1Cnp2ZQ62roWULQlx22ndCS4i6hsNQ3i%2FcW0pI4x4cZ3E0%2FLpW9R5mRqFOdWj3xnpinUlJ5gLbXuOVwO6PnvhN6psYRxyvp51LScOKYSsTDhASqaZ1IuTyIAukcxzBj6AcQM%2BuW4S5%2BnvjWZqSoNlX5rCWgB8UeBxrCrng2MYf3FRwZqtMpyz5Joy5Z8aYn2Opd7W1tLvazaTnlTHXn5o8D5%2FuRSIUTtFVR0nrRRUVE7R9kefnWjCEIBCEIBEw09sSxAhR8kwE4sSR8UNFwDblADlFQEbnugJG9I57en%2FfaJllMOqOX%2B4iU6fR6O6ALKygbAejtiYLuoFJO%2FI%2F6opkG4IBSQerEydR5kWt6xAVFLJ20iIJF%2FgCJCNr3iKTbtMBEnSlSkC5ES36qVHyj2RMmwvtzMXfBuFqrjjGFDwXQksmo12oM0%2BWLy9CA44rSCo9gHMwFGTolcqlMqFWptBnpuQpDImKhNsS61syrdwNTiwLJFyOcSuYdra8OLxe1Rp1dDamvEnakhhSpZt%2BwPRqcHVSdxsT2x23gyRxjwh0iUyDVP4ZxTi3NGsTU3TGpkus0iSkWpctTL08SnWtCghYCAD5J5Xix4Zx%2FT82cB1Pg%2FoE5l9R5zEdLD9CquFWps0dxxl8PvyU0y%2BkOpfUhvUlwakqHbtAcWREHvjOs5MqcR5M4%2BmcA4odk5icZlJeeRMyaiph5h5JUhSbgEHYgpIBBEYPo88BRc5Rj9YNm1%2BiMhcFhGO1r7EswGFwEemninmZK6q663LJBUSykKWT2AA7XMV6q3SRMNuUWYeclnWwsofSEutKvYoVbY99x2QFYYdqBpqql0sp1Wg%2BZczCen6Im2sIvciLYtfUiZz7Prv1%2F9XzbRTVAEu2Qm6yQkWAPZ6BF7mcNVGWpqqmp6TdQ2hDjrLMwlTzSFGyVKRe9r%2FF22iyJiZKlIUVoUUkgpJBtseYgJXEExSKSOyLrT00W7rlbVOFtKRobldOtRJ71bAARQqDEkzOut02aXMylwpl1aNClJPYodhHIwHoncOTtPkRPrmJJ1CVBDyGZhK1sKPILA5X3%2BKLUuI%2FY3IE3gIIDi3Et%2BUpVkp%2FIIutZw1UaJLom5hyUfZUvolKlphLvROWvoXbdJt3xaoh0nlfuvK89uUBCEXGkt4bW2v2am59pa%2Bq34u0lYRtspVyLi%2FYN7R5JthUrMOSxA1Nm1%2BwjsI8xG8BSBvsYvrVUwuhpDa8IKdWkWW4aioFR77adosMTQGQCrYTAscDqPnNUX9CKiKpgx4FiYwfMSqXLJ8ZZqCnFs%2FuggpAVbuuLxj1iTZKSpR5AczF4xBhxVCEu61VJSoy740l%2BW1aW3glJWyoKAIWnVY7WO9rwFGs0d2kPtWdTMSk0kuSky35D6O8dyhyKTuDHg5RdKRVpeWYcpNZZXMUuYOpSUHry7nY81%2B6HaOShsewxQq1JfpL6ELdQ%2Bw%2BnpJWab%2BxzDf2w7j2FJ3B2MBuXhQQpWPKn0fP2KV%2FOjY2W2ImMMZL4KxvhyWkvbDhzHVY98mGRMNlLkuUBt1lZKFdRxRSrTcHkdo1vwpkJxnWFKvYUy5tztqjaWTqKVjPKbCmBaolynUqVxFVxXK6mUW%2Bqk9MyZiUmA21dTjeptaFlXVTqG4gLqjiZzQQAHFUBZtZR9hZe6v5MTq4m8yVm5Zw8fMaKxb8UZO%2Fw%2FZFMWS7xVUxBIvdeHZoD8UUk5F5ELRccWmHEDXYF2jzKN%2FWIDHPqk8yhYolMLAAEWNCYI357WgniZzKTfVJ4TN7cqAyOXoEZJ7hGSCyA3xeYMBUbALp0wN4pJyMyROonjDwEEpUUHVKPg3HPa0Bj6eJfMMXtTMIpvz%2FOJqJmOJLHV9DkhhdCUpCkg0VBTt2WHKL57hOSqiot8YeXJSB5SmH9j80QXkFlA2E9JxhZYpJF7kPi8BYF8SWPrWcouDVbFN%2FYNu5B9EUVcRWMFgJXhrBikjsNBaMZEvIbKAIStzjByu0r8kqMwAfjiAyCyeUerxg5WcuYU%2Fa%2FxQGOucQeK3Bc4TwWdrdagNH8kedWfdfLZaOCcD7m%2B2HmrDv2jLRw%2B5SjoSeL7K49P5HXfGr0bRWb4dcp5q6WOLjLG6RYnpHrau7ydoDwZM4tl8b50UCpz1JpVMqEo0ZVr2OkBLIfa1lfvmjZSk6iBcHY%2BaHHIonEuEk32TIzn%2BnEZZlTg3D2VubsvS6XjGg48lK3ItyiazRHdTNLmlOlaWXW1jUFrSyopWOwkERhvHA4VYwwu32JpcwfjmDAc1o1XAv2%2FljtqUW6qWlktNFCuibvtsk6Bt6LxxOhJLiE2vdYFvXHccgroktvqXqSEJC23Lg2CRt6RF7P5T7GG8TlZxLMMDilM1EVzFqVopdNR0kwltJWp3kAhIAJKiTsO02Ed3ZcytDrlFla3KyikyaAUyLDzekoRtdakHyXCbg9w9cfPoVh2Qw5UnKes6wpkyjRvbxnWNJHcbx0hgvM00WVZoqpx11Ek0lpSiTY6QLnz73PrjJaWEWlcTHga9leZs4q8H3QyLiepmGhh6cdnXzKI0nSW5dK9ToGpBtcbJUB6ATHzXm6PRsS1Ss4kxbiaXoNHpbrLE1NS8q5NOThc2ShhpFiVkJUQpVhtY846t4sM3VvUWn0%2BmMGbOptxbKLrdUlS%2BsQBvfTeOapvAlfw3S5tdWYclKFi%2BpIS2%2FUGiy4tppRdZUllXvig2FFKlpGm6gLx16bOzizpsc889sQ0vja86rWfsefNGqU48MVOwjljWariTC2H66%2FNVacqlG8Um6ep1SUtIWApQSysr2IPlAgxgPDNmBg3CGNhI5o0Bmu4IqyTLVaQdTdTeojTMNquClaCdWxFxcd0ZVgusyuXT%2BMME5h%2BzdPw9iuWak0YgkpRc1KJAXqQXmBs%2By6OqtKSHEEAp3BjFMEZIUXMPMZOE8GZrUOSXVZ1yUpKpuSmtEyoIKkIJKAUhZSUo1b3sDuY1re7TFnwKafwad%2BftXut6oornhVa6p8Hmy9EaohfeJLKKjZK5guy2Eqx7IYar8oisYYqySFdJLr3DayPK0nqk2FxY84smD8QS2IZYsjSxOoSLoJ2Nu1PfGu04rqjstJ%2ByqXHFUtTjLUtMqKksoBUlTOknYBV9u8RPgty8v07DnWacKdSfN%2FqIjBaTTFWdP8AXhbVnRVVTlXt%2FrLqybgq7YaodRWtSAtcotoA7k3I2v6o1h0awjo%2FQqM1drrVSw9OImZoMzTTJVotsoAbW8%2FbGuJmoA9Qk2IuTe28K5iYzTZUzEzEsBqcwhyp1hvX9lmXUxdc15XC1NxlL%2B0KlexEmik04LSh1a1LmfFkdO6SskjpF3VpHVF9gBGJ1F8irVA35zKz8Zi54qdU9V9S%2FKDLCfibA%2FJGpLZiMl%2Fw2joXGHmSG3NuugaSCO24j01pBdUpxaytSt1FXMmGGmwtxlJtskGKtVTtygyMQn0EAxZX07xkdUbskm0WF1POKDyEWiWwJvaKhFolItAQHOJ4kHOJ4CaB80IQBOuPfIsCYcICU7C%2B8eCLlSgoOab7rBAgO68qvBtUfMHKvC2ZVTzvFDGJKY1UTLO0hKkS2skBBcLgB5c9owziE4AcY5HYZGPKNimSxphxDzLE49KMKYmZIvLCGnFNEkLaUtSU60KNiRcW3jsSnUbKOtcC%2BAKJnjiFdFwfNUKlh%2BeRMGXUl7WVMpCwlRF1C1rG8alzRz2yOkcj5DhS4YK9O4mqdaXL0alOrUtbMn0kyl0KVMPBIWvpLAIACQO4CAx3Dng0KFTqRTE5u57U3C1eq6UdDTUS7ailxVvegp1aelWCQCE9ptGucUcBWKsH8QWEslcR4nlUUnHDj6aPieWk1FDnQoUXW3JdR1IeRZJKNRBCwQdjbqXNfOLKGpytCwBx%2B5IzOFK%2FMy%2FjMpO6TPyCnNQbedlJyUUXZdRUhKltKB03Te%2Bxj0YkykrODeJPIDE8rmzifFeE5%2BszcpJU7EVQE49T5kyK3G3WXtKVONuNdUhY1gpBJNzAcG8Q%2FDQchc3pfK5vFiMQNTrMk%2BxPiV8XUBMK06Vt3Nik9t9wRyjPuJDgLrmSNUwfRMG4mmMf1LFzs3LtSEnS1MzKHWEpWdCdRDiSFHuItGacf1PqM5xV0VmWkZhxdRkKCmRCWyfGFB4pX0f2xSdiBy7Y3P4RrH2KctMRZTYywLiF2jYhpUxV3pObabQ4pCVttNKuhYKVJIJBuIDmLHXADibL3hymc7cV4tbptck%2BgW%2Fhd6SJW2l14NhKngqyXLHVaxG1rxyM%2B3Yx9VsxsaYkzD8GvL4%2BxjP%2ByFbrUrJPTsyWUtB5fsgpIUUJsBskcrR8r5vy4DwqiUX7YqORTgERSoiIQgJyrUII23iA5RFPMwF5w2Pz0kyOZmpf%2FTIjq7wnwtxSzo7sP0kH1S6fnjlPCgvXaag8lT8on430R1X4T4%2F%2FAKqaog9lGpif%2FTIgOPnOcQJBEQc2VEDygIxFJtFO574XPfAV%2BkiUrvFK574ngJriJ0RRBuYrN8oC94WobuJMQ0ygsupZXUp1iTS4oXCC64EBR8wKrx3C54KbHrK%2FFV5x4NEzfSGlsTCSo%2Bba5%2BKONsrEBePsNN99akP%2FALhEfU7jFy24c8cY4oNUzvzxnsA1CmSrop0vKPhpyaZ6cKU4DYkELTYEQHBGMeD%2FADhwTmzScm5%2FDiJms4hUVUWblHekkqgyk2ccQ7YWDfNxKgFJFttxG7R4MHEb7TtJk8%2BMCrxS1Ll9dDPSEgAX3Wm6kp%2Fd6NI58oz3MLiafzO4istPqZcKz2Ys5l2iemJlsJLQqUs80hmZQlS9wA2EqDhHl2NrRdJWtcH2e2dqalKTeOMos9ETJliu66fUBPNpCFNEK1yzy9ICCm6NaTa28Byzk7wRZkZs5gYxyynatScI1%2FA4QKkxVkuOILi1lKUoU1e6SLKC%2BRSoGMDykyGrWbGcMvk1K1mnUmpvOzjSpx%2FU5Lo8XCisjT1lA6Tawj6F8LGEsdYG4ss4aBmZjI4srz1Fo821XVNBpVSkFOEMOrbGzawLoUnsKeZFo5b4SWX18ccilTDnSsz1cU%2Bkp3ZAQ4Dr7tyOfmgMDb4PcyJrP2pcPtEmKVVatSdLs3U2XFpkWJYoSsvLKhqSAFgabXJ2EbFzR8HBjXBeB6jjXA%2BY1BxwaG0t6qU2RbW1NNpQNThbuSFlKQVFs6VWuRflGTZpV%2FPin8a2PKDw81ealK7iEy0rNoYl2nUOMNMtG7i1ghpKSb6rj1xmZqmA%2BBPKTFeFK3j2XxPmnmElyYm5aWfHQsPLbU3rIvsAFq3PWWfNAfORxvo12j0S3ZEZ5RXMKOgJT8FPaPNEWPIgMspn9qx5yY8uFpuZkcwKVNyJSJpiYDrGtGpOtIKhqHaNt%2FNePVTAfYseYmLVTlvs4qlJiVVZ1kqWk%2FwFX%2BSImIqjKTOYnOHcuE8T0fNCley%2BHpZiXeUgImqM2LusKI66mzezzRNyCBqF7EdsXYvOqp65OpvOLRJNeKtoUpatDd79GEE3SkHsG28cLYLx5jLANTlq3g7EU1TJ2WUlxp1uygFAdqVApO224jerHHVn5MttKrMrgasTbI6k5O4bbLw9aFJB%2BKN%2Bzvc5cGr3%2B6JadpdqZ1059U%2B2YbxksBztcdC6JTZmamVke8yjBASL7EHmAO25jrDhOySw3SVP5kuz0lUaih12SaTLu9MiRcSdLrerlqB2NuXLsjjPIaR4pON7ETlHrWNXsOZfyK0itzNDkkU9laefi6CganHFDs1WSNz2A%2FUjL7L7CWVuEKdgbA9HaptHpbXRsMt7kkm6lrUd1rUSVKUdySSYxXmuLWIias9fJs3zzQvdaa7OZmactXLOc7o55ZFCEI1myQhCAQhCAQhCA%2BA3HSB9U3mXewviOc%2FFHPM8LNSw72EK39MdCcdKv%2F1NZljffEk3y9No57nTdqVVttLp5d9zAZ3h%2FwDQ7l%2F1NEbiybzokctqbO4axJhP2ao09XKXXmlN1RdPVJ1CUUUtPOuoBK5cBfXRbYDUN409Q9mVfvURtrJrAOWOORURmHmGrDT7U9LSso14zLMI6BxC1Oza1PEFaUKQlGhHWu4DygL9mFw5Z%2F4uxvWKw1ghjEvtpqD9SFYoUy0qkzCphZcLiHdQDbY1fCtYC5i%2F5%2F5uSHsbUMtKGaZVMQ1uRo8tmFiSReW7Jzk1TkaGZOTQT0aUNAJC3UCylBVuZjJ2%2BHvhelJM0uT4rFSsjMXvKt1mWbaVfndCVhJv298a7zTyuyLwdhWdnMu84GsQT8kuSEuw3Nyrjc30q1peaQ02S4gtJSlZWRpOqwgMywHMy8pwIY8cdWQGsUtLA7fs0uLes2jRTmMZTplp6F7nbyY3ngtiYm%2BArH0tKo1PLxShCATYX6aXO%2FqBjnQ4TrynVq8Wa5k%2FZBAdTcCuIpSq46x1JtIeQ77VOlF7W0h4g%2BveORFiyj5ir8ZjqjgKotVp2ZGNVzEqltlWEtGq4vr8YuB6OccsOrU486tRuVOLJPf1jAQRzjuHIMK%2BpHd0JurxSu7fwHY4eRzjuDIMqHCK6vUCVSle027Oq6I%2Ba%2FCfEd7bvn5WP5K3UwvVVX%2FDLkzLOlYabyln6%2F7WZV6u%2BOybLdXded6aTYDKgpppAUEaXLnUVAnutHnmpxyQlJqYlyQpLSwkjmAQfyR7crpSpu5Q4im2naSKPIzUlLzAdUrx1yZXLlTZYAGnQnfWVHtAEeZuTlp9xUnOuLRLuJUHCgb20Hb1mwj6PRscydrFeJXBmF8C5z4hwzg2nKkqRKtU91hhT6nynppFh1fvitzda1HzXt2RqNznGbZn45ruZuNKljjEMrJy07UEsIUzJIUhlCGWUMtgBRJvobTck7m5jB3DYxdAN4mAtFPUYmC4D0tspUN4rIYQOwR4enUnlFZmZJ2MB7Ogbh0DcShQIvEbjvgM0yUoFCxLm3hChYgpqKhITtVbbmpRbikJfbAUooUpJBANhexjcC55Eu%2B68y2ENNlaEoSNkosU6QOwBJtHP%2BFMVVLBOJ6XjCiiXVP0WaROMJmW9bSlJ7FJuLg37434ltE4XFrSUCYQp4pQeRWkqsD3XNoDAeJ3C2FMH50YgoGDKKKVSWJWmOMSaHVuIbU5IsuLIUslR1KUVc%2BajaNOORnGZWOcSZmYunscYoEkmo1NqXbcRJsdCyhDDKGEJQkkkWS2Lm%2B5uYwVarqIgAAO14qJaSecUtxDpCmA9aWG%2BUVmpZq%2FKPCibMeliaPdAepEq3qJ%2B2gZRsJKQYlQ9uTfnygXbC14DOMiaPRKxnRg2l12ksVOSeqaTMykzqLUwhKVK0KSCCUkpFxfeNpzVScb8ZmmkJbXZxWlGyUgg3SO4WJHojQ2E8XVfAuKadjHD%2FQeyVJeExLdO3rb1WKesna4soxveUYlVzaXJsaZYJW45pudujJt3kXt8sBg%2FFVhvDeEs%2BsU0LCNDYo9JZ8RdlpFgqLTAdkmHFBJUSbFa1nc9sadVzMZnmfjnEeZuL6lmDixUqatWuiW%2BJSX6FhIbaQ0hKEdgCG0j1RhB5wE1h3RUbQk84pAxEulHKA9rbTZ2MVxKsjfaLYiYINzHsamNYgPSmWaF7fCgqWb2%2FcxKlfLflBS%2Be%2FOA2Nw7SFInM7MMMViiSNYlQqZfckZ5suSz6mpd1xCXUAgqRrSklN97Rni5%2BYfbdnFFPTTKC4dIskFSbFI7huRbujSGEMYVnAeK6fjDDxZ9kaYtSmA%2B30jataC2pKk9oKVKHrje6qZKImX5TodUshp4hu5NilpSki4sSAoD4oDAuKiiUDDufONKNheiy1IpUvOMmWkpZCkNMBUqytSUhRJA1KUbX7Y04OcZhmPjfEmY2LKjjfFrzDtWrKkTEythgMtkhtKAEoAskBKEj1XjD4Cskg7GKqUIMeXV3QLihteAuCGEEdkVUMARbmphQNt49zbxIEB6AwiJVsoHKIB0d8SrdEBsTh4ptJqOcuHZSr0qSqUmoTjjkpOtdIw6pEq8tGtNxqAUlJtfmBGb9I48svOkFTiQtVthewOwEaYwZjSuYGxXTsWYZWymqU5xRl%2BmZDraitJbUlSDsoFK1C3njdMxKOMOLYb6qdkhO9htyF%2BwcoDfmS%2BX%2BXuKsgc5KriDL%2Bh1Kq04SE5J1N9gmbYdWChRS7e6R1B1Rte%2FONqcGyAnhrpLSjYGXqRJ7rzi%2FmjlTFONc3MDZKP1TCeKKRRsI4trLeHJylyVPQJ2aSyx0yXZh9SST1tVrG%2FqjqTgrW%2Bvhqpq1udbxap6VembXb5bx8w%2BEynhXWwn%2FMp%2FlrdvCasuFHm98OCFHVMOK733T%2FLVHR%2FAogHN%2BrKPNOHX9P3xF45xQPfV%2F353%2BeY6Q4Fbe6%2FVesP%2BLsxt%2FhW47%2Bm%2FwCoLefNHthqYfH9qpjzrlm3SMHV7i7qycZ4TksSSdMwKw%2BzITrzrbCpjoDoWstKCzp1bWMaQqRcmZt96YcK3XFK1KNySfWbn1m8bczk9uU5xgVprBM5h1maYwQw7NezSXPFnJREuOkQNHW6U6k6SO2NSzbzMzPTTsr%2Bh1PLLPPyb7c97d197c42dDY%2FId2%2Fgp9kMV8j8dV6Xj4isIYYkMDZbY5plIdl67i1NdXW5kvKWiaVLzDKWFBJ2b0oUU2HO1455f2jdGe2O6pWxR8uVSMvL0fAInJSnON61PvmbWh51b6z1T1gAlKQAADz5xpV8kKIj1TVySExXZbQrnHmvcRMFqRyMUQujMowrnHtbkZa2wixNzTqbWMepFSdTzgLsqSlvJsrfuMSPSTBQkC4095i2mqk2JSdj3xK5U3dwlGxgPY8wlpQ8X2UopT6ybR1ZmVRsP4VxlPYVwpRJej0ilpZal5Fh5x1DaiygrWVOEqKlqJUd7XOwAjkPx5xV9fVVdJCu60dKO4tquYjctjysyEtKVKuNJdmW5VKksno7MpWlKrlOpKASLkXvaAtXEphfCtJw1lriej0bxWsYqoM%2FO114OLUmbmmqgttD1lbIPR9UhNhsNrxz3sOyNt5y45xDiJ2lYRn5WVRTMDtTtHpbzbaw6607MrmFqdUSQpWpdhawAAG%2FONRFUBA9Y2j0MyyDzIjy6x2REPLTyMBeZenMrF1HfsAj1ppUqnrJKhuL2%2FFFiRPOISOsY9CatMBIAWPWIC6qpbGlSUhdjumKExINtt9JZWr1R4vZl%2FvTEjlTdXzVAV5aXaTNspClXW%2B2g2VyuoDaOrc1JSh0TH1ZoOGqHJ0ak0yZMtJyMmVlllISnVp1qUq6l6lEk7knlyjkluassLKt0kK%2BLeOhDievZgKTjLEMsxLVGsnxmaSw2UN6r6dSUnlcJCrd5MB4%2BJ7C%2BGqU1lviei0MU6cxjhBVVrGl1a0Tc6memGvGQFE6CpCE3CbJ25c45%2F125RtfO%2FG9ZxhU6RRpuVl2qZgqnqw1RltNLQXZRt5x3pHdROp1S3VEkWHIAbRqTtvBdOCVHePU1LNLHWMePUeyKiHVAc4KLqzIyyrc%2FPYx6kUuVI2DlvTFlROuN%2BSRaPU3VXgNgLemAuRpUsR8O%2FmtFF%2BRl2htr89yIoGrOgeSgnzx5pipKdFth32MBc8MyjE5iWjyD6VLZmqlLS7iQqxUhbqUqAPZcE7x09iml0%2Bi40qtEolPYptJo9RdlqdJsFSkMMNunSm6yVKPaSeZJjk2Qq01TJ%2BUqciUpmJKYbmWVKFwHELCkkjt3AjqGnVmfxs6xi2tSKJGbrzvjk4w2TobW64dWkHcA87E7XgmGA8S%2BF8O0Cp4LquHqaqTXifCTVdqg6ZTgmJ5ycmUOPi%2Fka0obugbAp25xpZKtaNzGys68ZVfF1el5apScrLS%2BFpE4ZpSJZtaQqTYmHlpW4VE6nCpxVyLDkANo1glZBI7L7QM1ZLaTzXHoal2iN3I8ZcUO6CX3B2iCF6ZkZa1lKJvFZNNl%2FhBXmi0NT7qBzj1N1d1PwbwHudpsvcbK9ced2QYZSUlHUWer33jyO1aYUdiBHneqL7idJWfVBMTkyHB9Okp%2FFeH6XUUFyUnarKSswhKikqaW8hKwCNxdJIv2R0PiWmSFGr9VotHlBKU%2Bmz8zJycslxSwww28tLaNSt1WTYXO57Y5joVYnKTV6dWpAJVN0%2BbZm5cLTqSXW1haAQOYKgNo6QVW5jFilYsnKainzFdKp9%2BVbUooZdcWStKdXWA1XIB5XghtPhoyayszqx%2FU6LmphVValpPDM47KLTPPMKlXGjrSpAbIBJKiDquN%2BUZPwDU6nUrE%2BYlMprS20S1VpgbC1XIbCXha%2Ffff1RrHDeZeamS%2BE8RZo5XUTCxlaLIokq1PVcLfmfzc8GEpYZC0p0pIQSd%2FKN4zvwdNVm61Vsf1OcUFTU5OUt11SU2BVZ7s7N48F8IlM95q5jw0f%2FALKHUwj5eI%2FrY1ZxRJKc%2BsaXt%2FbFu1u7oUW%2BS0W7IOxzswHqO3tglvXuY9%2FE6AM%2Bcbaf2UR%2FoG48WQH%2FAC24D%2F8AP5f%2BlG%2FbT%2F6rn%2Fkf8GOx%2FS4j96Pa6T43qJT8QzGVdErEsX5OcxbMsTCErKS6gyjQKPNfcbb9Y2jnjMMUaVxfVaXhzC8phykyM%2FMNylIlX3XWJTrAK0F0lVllOsjldRsBG7%2FCDVWq0eUy0qFEWhFRbxNNGUK03SHTLspQVDuuRfzRozMiRxNTcYT9OxgKL7YGXnBUF0VThknFazpU3rJO45729HKNP4O5mMDoz8NX80q4jOd4r9Puh5ZvDWHMSZMZlVCt0xUxUMH0uUqlEmm3lIMm8%2FPsMv3SOqtK0WSQeVriOZHhp5Rv7GeNarg3LSq4apUrLOt5gNex1VceCi40xKvsvthm2wKljrE322Fucc%2FzDl4901EE7xVS0DHmS5aKqZjSd4KPa3Lo7or9CjujzMzQO1o9aXQRygJCyi0UHG2wY9K1C20W99zciAn6nmjpLB8nRZTIbBs5KUSQl6pVqjWHZ6ooQfGZttmYQhttar20I5gADeOYS5vG6crsZVSvYS9o083LeJYaccnKc422UvXmnAXkLVeyk3QCNgRvvvAZ%2Fiek0GtcPOYdSqtIlpmqYcmqE%2FRp9RUHpMzE4puYQixsUrSBcEHdIIjlx4aHNMb5zNxfXKFgGYwhRUMmmY06N%2BtBxjU4n2PmQpjol36gKnDq2ubCNCPLuq4gJ06Tsox6W2EWuCIt51EXBtE8rMrB0kwF3aZbtuIn8Xb7opS0wkjePV0ybXtAUVy7fdHhnm0tJUvotSCoXTqteLgp1J5xbag5dBR2QFOSfS0CkoO%2FIA3jpqnrp0jkllzLydCpbD81KVOZmag1LJTOzR8fUAiYdG7oTp6gPkjaOWELIjdWXeK8R4nwy3h%2Bruh%2BRw8laaUsspSpAfd6R5JUPLBUAR3QGwsV0%2BkVnhnxdWahSJR6o4exHQm6bPlFpiXamPGA%2B0FDfo12BKTcX32jmR8jpNuUbkzLxjX6HgQZe01baKLX5hFWq6ehBdemZVa25ezh3ShIWeqOZue2NKlZPOAiN17x7WZdtZBIEW8qIF49EtNHVa8Bc0yjVuyCpVA3im26e0xV6UQFNbLY61vKjyTCGEIUj7aPW4uLVNOlS1eaArNO25R1LKeJS2XeX0pJU2nMB%2FC7E8%2B5KyyW3ZmYU%2B%2BlTj6wLurtsCeQAEcmtuqSrc7RvLLDEuIcQYRaplaUh6Ww90crR3yyEOIllFxSmSofZEBRuNW6TfextAZrmlIUub4eqpOP0qTfqMji%2BlMy9QUyPGWGHJWZK2Euc%2BiUUglB2uL7GOZFkGNw5v4qxDLYck8CsTCm6JOoarM6z0CbPVBtTjbbvS%2BUbNLICLgC5Nje8aW6WA9CAg84qttNqjx69I3iqw9vzgPWJZHdFRMukbgRK24CIj0ouBAQW0kBXnjyOpRyEemYeSlIi1uzI1Gx5QFfURtHV1VYl04KwO1T6bLMKRhCkzL%2FAIuwlsPOlLgU64Uga1nYFRuTYDsjkZM1pOpXKOisr8Q4sq%2BFmGMRuqeYo7bEjTi6wlLiZIJKm29QAK2xdWm%2B433gNtZCsSc1mvhBE1TqdUZSdqrLD8tUJVuaaSVBSdRbcBSbBRF7dsXjIqmyFM4z8cSFLpsrT5dqjVMol5VoNNNp6RqyUoGwF7xiuVNDxZWcXKoOCMcu4KrDy3J2XrDckmZWlttlxwspSryNS9B1psRbui18CNermK8%2BKtiWvzs1UZ%2Bcw1OOTc2%2BvUsqU61uo9tzHlNNYjvJb5%2BLLo4b%2Bk0Mz491JVnm0Uu6lLw%2FKHRY%2B9pDrgG%2FI35%2Ba0c29u8dIcd51Z5sg%2FBw7Jp%2Fzrp%2FLHOShvt2RtaJa8Fu0%2Fu%2B%2BWve5zt6vSg8keJzHmZWfkj6CZlTLQ4VJlSypTbmBQyq3PS5LtI%2FKY%2BfM3qElMkfqDn4o%2BgmcoZleFioyyChKUYBI6%2FL9Dsgeu%2FLz2jyfwgxwr5cIjxp9tG90MN1Xe2nzR73CufrLUrmJPSbN9MvIUxsE8zaTaAJPabARqeVaelpYJdCU2vzMbBzzl%2FG8ZIcVVX2n3MNUEoCm79ITT2iSo9l%2B%2BNblbjckGn3gopuoqV3R9EuufxFGfgj2OXbfKT6XvYDBsp2ZaFtzdQ29USyjLIkVNuTjCV9I6qxWLWKjbeMZfmF9IreKfTufbxs5sTLaMpmmyimH5lgq30qS8kpO%2Ff2XEStPdDMvul1mzigRpeSSIxPpD%2B5%2BIRLAZi5PNk7vtffBHncnGb7PtffBGLQgMkL6FfDbP8ADETsyU07OS8wlKAhskqUVDYW5xjzC7G0ZZTHGy31%2FtT%2BKAz3OeQW9RsuJRlLKVN4KpriQCACC9ME37ySbkxq%2FwAWUl0pUttPpUI2fmtMeMS%2BXbyAOj9oNMQkg31aXpkH0biNU1dfvkUHrnZdIkill5tThIA64233j119DU3IdFLzMspwKSbFYFwOdoxMueeIdJAZU46n2NRLtqQp3o%2BWoc%2FTePPKKS3KJb1BOn90IxyH3EXGROPJ%2B3Sf4Q%2BeKKn0jtHxiLCdPaB6oh1b7QF9Ci6PeQpZ7k84veGJCck%2FHlzrJaDum1yDe178oxemOdGtDnwtUZwiYb6Py%2FLT8sBnuYVEVSuHDL%2BVaKSXcUVmadUkWK9bDOnUO0hItfutGn5SWWo63XEJHnVG28b1Z2qcPGCEzDSkLkcV1mUQon7IhMrLnUfureqNHzjqhcJPbAZA1Lo9l230uoDQlChR1C2vVyinUJcN1diZbcQpsJsVJWOV4xZb7n28Uy4s81GAy2tlUyUmWRr0qCtWobfLEjhP%2B6oxS57zEbjvMBkKyQq%2B3xxSWtXd8sWTUAL3MEuC%2FlfJAXgyszMp6NhgqUe0WjIPFNdNk5RzqrQ2NQ1cjFloMx7%2FANH9smL3NODQFa7aUmA2XUKGmj8Ks2tyVZ8cmccSTvjA%2ByKZMo8EoUe0ApUQOzUY1Kw2PNGy5nE0zVeG6uUh9tCW6PiyjhtZO7ynJeaJt3FIHxGNJzM45c6SQIRqGRU5tDdNV0y0tlMw5sVC9idjFCjESa3%2BnI8o6dwe3aMdM44ee8SlwmAybxhPsgp240KZ03894reyDQ5n5YxDWu8R6SAyhyqMnkReKBqAPIiMdKlA7KMTIeWO2AvzMjO1CZYUywtaUrC1EHkI9jslMSzza2kdIlBIWi4BV%2FveLVLTFSUlAkpgNG9r3EVVvVlLvSzVREwgKAUUq3IIgOu8S4cwhTeCukz2F2jUq7jBTlQnXmkuEsvJeLSpNtA2UpCEXcNjubjYRvzidUlHCynolakqaoYv5iGvyxzLwS19j3QKdR8S45Vh7C9FqMviNybdmeiTJFvWHktuK6rQfbu0tNjrBtztHTPFEuXd4ZJpyTa6OWXM0pTCPtWlOhSAPME2EfN9L7OznEsMqojLK1iMuWZmqmZnqjX58nZudUxd7amdecRPojXEQ4T584lIN4C5POJo%2BkS4yTlziYemCxvuIlRc8xARtvE0IlJN4CMTC0U4ngJrCFoE2gDeARJE8S2PdAQ0iAFom0%2BeGnzwAC43iA5xEiI91oBEyXSwDMJdW0Wuulba1IWgg%2BUFJ3SRzuNxaJRy39B9MTNnQu8B9AcVZT4klqtkXmRQcbs5l40wjS3m5uTTVGGqhiGnutrdExIKcOl1yXDyrahdaUJJuQYt%2BTGRtccz2puN8e4mr9GqFMw87L0OQxRU5FzELr60rZ8cabZOkSzIdKk67nVe%2B1o4qwTiurYAxlQsd4cUyirYdm0Tcg48jpEtlNxosT5BBUCkWG8ZDm5mfinOXGqsf4tZk5OoGVakmGqchTTcsyhJAS2okrGq5Kt97wFjx4isM42rspiDFpxTUZSozEq%2FWvGS%2BmfLaykPJWeaVAXA5C9uyMbWFX2iuUIR1EaU6bJSlKdhbsHdFIg9sB53oxuuH3lz0XjI3%2B7vEY3XPsTvmRAYvItyD4mETs4ZZQZUphXR60rdFrIVbkCL79htEsy1JNsyypCacfW7LhyYStrR0LupQKBudQsEnVtztbaPLE6IC6TMjRmni6xVnXWlySXWj4vZYmbC7KxfYA6hr3BFj27W1SVFBUEmybXNuUR0oOw5%2BYx7qdW56mStQp8rMJMtU2BLzbK2wpLiQoKTz3BCgCCLGAt5QpKNRSQUi9jF2q0hh%2BVmZtNMxA7PS4YacknFShbLrh0623Ek%2B9lN177g6R33jzVKr1CsOtTFTmVTDrEu1KNrUACGmk6W07AX0pAF%2BffHkgPdJytMfpVQefqSpeoy5aVJy6mromkk2cGu%2FUUnYi4soX7RvLPM0uVny3Izz03I6kHpiz0bhSQNfUJ5g3A3sbX7Y8moclbX74jAe6p0%2BiSsxPokq45OttOpEg4JYtiZaN9Slgm7SgNPVsbknfaLapAtqAVY8iREVKSDuoCPY3Vp5FIeoiXUqkn30TRbUgHS6lJSFpPMHSSDvYjmNhAeKUbllTjDc6%2BtmWW6hLzqG9am2ybKUE%2FCIFzbttCcZYYm3mpWY8YYQ4oNO6dPSIubK0ncXFjY8rweUXXFLUsFa%2B4RKkXGntEB61y1KVQm51qpr9kUzK2npNbRA6KwKHUL5HcqBTsRYHcHbxQ7bQgJYmiWJoCvT3peXnEPTjTrjKb3DSglYNtiCdtjaPR7JJ9jJinL6RwzDyHrqWNKSm%2B%2FfqINrxboQFXXePW1OzJp%2FsWp1SpVL3jDbZ36NdrEjuuOY8wjwxVZ5KgN68KSL4vrSzayaYLg8iNfKPfSalPUbh6q8%2FQqpP02cOKKK05MSkythwlcrNlxAUgg6SLAjkbco83COjVizEA06r0m3o6xN%2FkjzylVMrw51yfV10tY2ovV7DaTmwR5u%2BAxpOYOOm%2FJx%2FiI2O%2F56vK38%2FWiVWZeYo3bzBxARe3XqK1fjvGHyOLVU%2BWp7Lck0tUhUDNgnm9fV1D5t4kRitfRNS6pRromquqq6COd%2FwBLNvgwGyJTOnNGWl0S6sazrqUXGp97UVG%2Fabbx6Xc880UsrQjGr7QWkoJQpNwDzG4jVTuKnltTCEss3cqfsiPSbe9j9ztyiaZxY%2FMmeUuXl0CcnGptSQjYFB3SnuBtAbhwFnji2m48w5UccY7r03h2VqjC6vLshp5bkok9dKWykBRsdkn5osk1nNmk2%2B%2B2xmPWnGelXo6QtE6NR0agUGx02uO%2BNbTuJ1TkvV0Klm2%2FZF1p4W5tlJHk%2BmIT2K3p56qOKlZdHsg235N%2BoUgC6fOe2Az9%2FOvNhXWGYlWUbclKZ2%2FkbR45vP3OslLDeYVZU22kFv7Hbz2siMIexEp8ToUygeMyqGgQPI07gjzm0VPbXM%2BN%2BNdE3fxZLFuzbe%2FpgMsXn7nKG1BWYNaKVEKPXQPX5Me%2BjZ05sTU%2Bwy%2FmDWlI1adPTJHYb7aYw5%2BtuT1EnmXQ2lTYbCCNyoFQHOK0pVyirNI6FPld4%2B1MB1RwhYmxDifFbE%2FiKsTdTeRXaZKNuTKgpSGwxMuWBsLC%2FwCOL1xvJPtwwwdVx7FPqG3L80EW%2FL64xTgjcEzV5J7SlKk4ykU6yfK%2FMU0rT5xYcoyjjeKjjrDSSSLUVZA77zCjAc6IKUzCCRca0i3f1hHc7KAtBbfW2pVkAKt3Adg587RwqBqeaSRcF1AI7xqF47aaZSFpaQSiyBYpvcEJ2BPyRksddpPoYr1qs6Y%2FrkZFKONOIflXXpZtpuYam3CobEMONrCEfu1AqHqjqp%2FK6gTrSphgvNqdST0jfLSrfly5RyzhRMu6t6nzCEkTSFNlahYb7H4%2BUdZZd1J17B0jKTAWmZprfsfMoUblK29hv2gpsQe0GNiqmOFEtSmvKmYj0uauJnDmZOUtMaxTltiqqyya1pp1QXIMtmZAbuprSspUtHb5Nr73jj9M1i%2BsV52u4xm8SVJ%2BXSnxmeqDrr7suxfZRK76Wwo7gWEfXFbrD46J5ttQ1X0qSCLjt37Ys%2BKcAYFx5LysvivDkrN%2BJr6Rh1pIZdRfyk6kAakKGykKukjmI26LeujKKcsmrVY2dUTVP53s9D5nTmKKpjWep%2BT8rien0Cm1gMS8zNvLvLLmVKu044dw2gK0qKhGKUXEE3khj2Uq8t0OIsQYXqwfaHSpTTlvsLISoOJBLzSiAtKk2uI2hl5kjWZDiao9BbpUm%2BzhnFKJqeRZLcgumB8uKAKzp0BpWnQSbWKe6MFzlwrL0rNfGzdOTLuUmXxJOy8iuXsGhLlZU0lAHwQghItt1Yz29dcWlcTOfBiI82vNisLCiqimNnCzq9OWTUeIi7U5%2Bp12ZZl2X6pPTE%2B81LtlDLbjzhcUltJJISFKNgSbC0TYBknjQPGgbB591Q9F7fkj2YnlnHUM0%2BTbWp%2BYV0aEp53PMiMikKT7E0qWkEJA8XQE37D3n445tUzXOcurRlTGTxVJHRyD%2FwBt0JjFSwTpt2xl1QbPicwF%2BSGlJH5IxpgdI5y%2F3MVWanqY%2FPeoD%2F6hf4zF0xKgory2%2B5tr%2BYIt1Wt7NVMd0wv%2BdF%2Bxq2W8ZTjShYpSyD97TGvM62bkZZguVQ%2B%2BjU3ezR%2FEYkqqByi7ZcAJnEhWmxlnL6uXkGLbW0aHLRVZitTTds7RYHE2EZJPgFJiwPpsq0BbiIlj1rbigpvfaApwHOJw35omCBASRAm0TKFjEyW7wEkemUf6NYCvUYp9Cq%2B0TJQU7wHT2MuNet424c6Bw8zeBKbIs0FFOS1V5aecU46JQkpJaKdIKr72Vsfk0GxXJtuabmmpt5mYacS8082spW24kgpWk9igQCD3iMf6QgxP0sB3phzwn9ddw7K07NTJjDuMarJFJTUS6lkPuBIBeUy42tLbirdYoIBN9hyjUOd3GdmZnPiyg4n6ZGGU4Umkz9ClaYo2kppJBD5WrdxewSbi2kkWsY5rD6hayj8cTeML%2B2MB9BKN4VWsCkyqcXZHUKp1qUSdM7KT%2FQtFw%2BU4ltxClMlXaErI88cw8QHEtjXiCxgnFOLES0oiVaErI0%2BVv0MmwCToTfckqOpSjuTblYCNM9Oq3lGJOkJ7YDpud40Z%2Be4W6fwwv4EkG5WRbYYTWW55ZdWhqYLybslGkEk2NlWjmaaVdfOKXSRKteo374Cm5FOKi%2BUSWMBCEIiOcBOlO0RSneCDtaJkmxgL1hFOrEVJT31OSH%2BfRHU3hOjfitriftKTTE%2F%2BmRHMGB06sVUNPfVpIf8AqER054TFXScWWJ0%2FqdPpnxGWRAchOiy4kJid03X6Ik0kmAhCJwiBRaAkhAi0ICZI3isk2ikOcTg2gL%2FhOvTGG69TMQyjLTr1LnGJ1tt2%2BhxTSwsJVbcAlNiRvvG6uKHionuJzFlLxXO4NlsNu0ym%2BxxYl51Uyl330uFepSUkbki1o58aWQIrIUbQGwcqs18W5P46pWYeCJxqXq9JcWpAfQVsTDa0lLjDyQRqbWklJF78iNwI6xe8I5gKaqIxvN8KGGVY7CBetKm0LJcSnSFlZb6Q7bXPWtteOD%2BmKYeMGA6KoXGNmtQs9pziAQ%2FJzlaqTapOfp7yVJkpmRIAEtZJ1ICNKVIUCSlQvvciN5zfhLsJyZncQ4N4a6PR8XVNoJmas9MsrK1nmXFNtpW6PTa%2FbHAgmFdpiYTR7YDqDI7jMquUeNMcZgVrAchi6tY4caVMzkzPLlXZYJUpS0J0pUClV07bW0jnGbYt4%2FsG4opdYkqlwl4BmJisyrks%2FOzLqHnyVIKQsrUzqJTcEHUDcDcRxX0%2Bruh0vmEBWffS88XEIKE%2FBTz2G28eiXspMeEKubiPSw5ogMwp6tNLT5yY8mGpZU3jeSlkp1FYdAHeeiXHpp29LR649WXEr43mrRJfeynXdx2WZcP5IDF5YBTSVd6R%2BKM4ygwcxmHmjhHAs48%2BzKV6tyNMmXmQCtpp59DalJvtcBRIv2xh8nJuTTigkIQyynUty%2FVQPPGwuGqtJneJXK6Sp3UkUYxo2%2FJUwoTjXWPm7hAfePL3L7COV2EafgfA9HZplIpjYbZZbG6j8Ja1c1LUdyo7kxkcIQCEIQCEIQCEIQCEIQHwD46bDifzIA2%2FsinTc8tlCOeZokhoHkGkAR0Hx1f%2FABP5k73%2FALIp%2FwBXWEc%2BTHktfvW4DP6J9hV%2B9RG%2FOGtJWutJRkgrMAIn5Bx5aZeUdLKAl20n%2BaDZIeKgslHXPQ9140PRrCTGyb2Rc9sbPy%2BqueeA6W%2FiXANAqqKVNOt1FUyui%2BMy5cZStKJhClJISUpWtIWDyUqA6pVMSDJI%2Bt8zJ1G50yNPV%2BKNWZ%2FdCnA9ULHC8vAqXvY1IqCpKRaFOJfUel1tXdPTj3qxAR1dt4wM8WvEAtCULzDQjULjo5FgX%2BSI1TEPEZnVQH1TlJrOIaZUVMMPzcjQU%2FmjxVZW0yp9tOoobWpSgi9go3gNjZcLaZ4GsfzLirJRilK1K7E2XLi%2FxGNIJxBSdavzajyj2xuPATi18BmZ7YTdxrEQQlHbqDstcHz845lMnOBarSb%2FAJR%2FSzAdi8D1UkJzHWM2ZaabWs4aSvSDvYPEX9G4jjZwhS1qTyK12%2B6MdPcATc2zmli0uSziELwmsFSkkDaYRYfKY5jf5uH%2FALZz%2BeYCVHOO3uH8X4Q3AFXvK4h59nUc2jh9BjuHIFV%2BER0faSuIU%2FEhyPm3wnRM4fd4jysfy1OrhNM1Wlf8MuU8pf8AkLxj%2FwCe0v8A%2B3MSSDRU6E%2FCNx%2FJMMrF6cjcVp%2B2r9L%2FAPtjHtoMoqbqktItVGmy03NlXirU5MdGZhSRulAsSoi8fRrPY5c7WlMXdGp2TdZbQkOSLalhCbDXc%2FNzjEHRZRA7436vKKjP9A3PYskHlMIDHvdSaCbJvzuL33jzKyYwo9NSqX5qdEvNPJQZmXWh4aNYSpSQLarAkgdtrRdDQ0IyrGVApFHqb0tRXnXpRpS0tuvJ0rdSHFJSsp%2BASkAlNzY3FzGLrbPZAUiqJkKiUoiZCYD1tOEiK179sRocvKTdYp8nPl%2FxZ%2Baaae6C3SaFLAVpvtq03tfa%2FON4VrK%2FLP2dnvYCn4iapCZhzxJuem2VzCWdR6PpVIASV6bXttflAaHmSrQux%2BCfxR1LJaQmXe1DQqVTdVrG3Qi0YSMqsFqtdqpBN%2BsC4jcdvZGb9MwgFwuMy8sy2Qtby%2Bo20E2uo9yRzPmgOf8AEX6FpZ06byZPputW8YisWcUI6RfyjwG9LyqJvH1HV0MqhCPzWrrNnrJXcN7gg3EeR3I7AvRJdl8TU2oHUgqak58qfCCRqVoUgAhINzvAc8RKrnGYYuolIpc6uXpYcU2gK6yzuuyykHzXABtGIrBvygKR2idtyxiUgk8omQ3Aext28VNRMVMNSspPYipUjUEvKk5idYamEMqCXFNKcAWEE7BWkmxO143nUspsAJqU6qnSFQap7jrhk2n5kOOtN6joC1pAClBOnUQAL3tAaHFy80f3aR8ojqCYb0KmVfbNLP8AmzGKyGVGBWzqmpGbeUlQUjTMaBt2HY%2FJGX1GZlZWXmJidfSxKNtLQ84dw22U6SfUDAc84l%2FQkg30enVIMufGDGJx0TN5YYLeblUTWKVuKTJMhnUw8gLZ09RW7e9xCn5KYLmn2UNThmEh1szIaSoLDAWOk0a0gFejUUi%2B5AB2gOd9J5xIfPGYYyotHptTmmqMHfEw%2B4JdT4AWWgshGoDYK02uBsCTbaMRWDeAkJAio27aKRF4ilJMB7mnSRFXVfti4YDptNq2M6FTKyzMPU%2BZqDDc41LuBt1xjWOkShRBCVFNwCQQCQY3hV8j8EipzUzT5WdlpR99xcrLuzHSuMMlai22pYAC1JTpBVYXIvYQHPssnXPS%2B%2F8AdDf84R1bOMt%2ByNSUU7dDOEW5mzCyLRhstk7gth1Ew8xNudGoKCQ6U7g99oy%2BfnWJdtybnZpiVkktLbfedBIaQtJQo2AJJsrsF4DnrG60TD8rMeTqkJX%2FAEQjDtBjpZ%2FJ7AzzDDc3jUOfmdJbS5JTLZcaA6igejtuImo2QmAqjNMiVqvjjRUStKGnm1LSgp6RKFOICSpKTe1%2FVAcy2iRZtGWY4o0jSqzNStKbWmXbWpKNRuQATsT2%2BeMTWLmAghW8elD1hHl0xG5EB70PE9sRKzbePfgOnyNXxpQ6XVmHHpKZnmW5hptehbjRUNSUq30ki4CrGxIMbsmsscv%2FAByYbRSX22S6ospExqUhvUbAqI6xtbewvAaNoAvXJAf%2FAFTZ%2BWOj6i3eoujTpsv8QG0Y63llgmXmGZlmVfJYdSsBT5BUAeRIG1%2B8Rkjy1POrddF1OOE7bgeb0DYeqA9mbyT9THhVRR%2F03cSD3gSSjb4yfjjqvgr6NPDRStPNcnUVn8LVeOXc4Ej6lvDJtbTj5Y5f93qvHUPBS4tXDVTUq%2BBJVRI9HjKz%2BWPmHwlTwrrYT4LWn%2BWt28Jj870e%2BHBSPL9Ljv8APVHSXAgArN2uE%2FBw84R63kRzajmn985%2FPMdJcCNzm7W0jl7XHifU6mPQacx%2F6%2Fb%2Bin2w1sP%2FAEun0vVjdvXxkYxcv9iy71bdnvLO%2FqjScs2AwmN2YyB%2BrAzFWnUCcvQLns1MMCw828adpUoZ1xLKpqVlEXCS%2FNOhtpJJsLqO25ja0O1YHdY%2Fcp9kNe%2BT%2BOqYTmq5%2BeeJWPgqrDKfUGAR%2BMxp2YbjpzEmVLlZxLWJ%2BoV%2Bks%2BPTaX1SKaigpbWlAABJF%2BQJ9cW17JOltoU901MnECwWZWYS6UX5XANwDyj1DWzc3xFxITpKTckXMbhzbwDhnB0wKfRHRNqEvJOvPFgtFp55jpHWLEnUEHYLGyr3jTrl4LJdRhqMSWWeRMNK%2FPFFFQGJ%2BYilHTcxkrgR6hYcqVKkZtoVCh06ZmvGVIWVTa2dT62tO4ZKiNAV1tjfsgOZygnnHUOD5fpMAYTf%2BEunhtPqeVb1Wi1O5M4YAIS05faxCQfTGdUSkP06kU6hyiHHxIAS8sgJF1FS9hblzMBpnNXpPH8QS%2FwEYjmU%2FE1Go1t2jq%2Bp5IYaxHP1KszGdmEmUzs%2B5OuypniSy8TpcT5G5FrWBiVHDXgqYQkS%2BbeBJlxRCUNJnF6lrUbJSDptcmw3I5wHJ%2BiKS9o3Fm9l7SsCz0zQ2G0rmJRxtLzgRpOpTKVKTa5tYkj1RqBxuAphUTBXdEoTaJtO0AuInimlMdRTeRuCnkyszRpV5iVmJSVWETaUrdS8plJe3TtoLhVoBuQm1zeA5iT2%2BgmOnqIhC6BRVE6lCQa6U9x1WHyRa3MlMNpQrUhP3u35Yzmn0ZbFNlaXLN6zJNNoBIAuq3LzCA0jmq2tybn5e%2FWl61UGVeYpWkWjV5YjoSuYAotdqM1XGce0BEtUZp6oIlTOKUW1ukFaQdH2yT2xRYygoM66iXpuI8NOzb6g1LsGcVqddOyU3KQBc2Fz3wWc%2BlpXdA7RtfPDBVCwTiM0Oglx5mSYaL7rzfRu%2BMLZaW62pIJFkOKWlJB6yQCbE2jVSwTyEEqWqxiYLAiBREpBEFFXXftiBRfmYmlEa5hpvq%2BUPLvbn227I6nrPD9g6beTOUNh2SkHJeWebl6ghKplKlMIL2pTfV0l3WUDmEFOreA5YaQVOpT3rSPlEddUSWJplImVk6ZltpYVe5t0mm%2F44xN3IOnNEqbmWUFvtDR9UbMpNMcpshIyEspbi5FttKFOWBWpJ1XPYAST6oDm7NhHSVKY%2Fcz8%2BlPo8ZVGt9EdJT%2BV%2BG67NPzk1mdhu78y%2FMhnxhSujLrilqQDosQCSPVEsvkThOYmWJGVxphyZm5xxLEsymZUFPOq8lAJSACfOYDnEtmxiidjGz868F0rA%2BKpjD1HeceakwlJeWkIUslKSSUjYG5I2PIAxrHozzgGuGsxKRbaEBFSrxGLjhuTZnK7JS8yyl5txyym1KKQrY2BI3te0b3ncmcHIeQulF16VcZZWjxhAS6lRaSpwKCTbZZUE96Qkne8BovDA%2FsjpZ7pxo%2FyhHSMmR7DSDurV0jF%2FR1jGMM5WUOSmmpyUCWnmVBxpYQTZSTsbExlLzctKy8tKSqV6WWw3ddrqt27bcyYDIK24F8LubyejB0GipCu0XqDZ%2FJGd%2BDRLfR44Ac9%2BM9TOr3JCH7H7o2jXta%2FwDhczXXf9PoibemeRGwfBotWONZm24nqY1fzEPG3x7x4j4QI4WCWkeej%2Bel1cJ%2BXiWt%2BJ%2Byc%2BsbI%2F7ySr42W48vDwAc88BBSrD2caPK9zoXYfHaPTxRG%2Bf2M%2BuVfngnstb3pvaPNw8hK89MAIN7KrzA2%2Feqi81TxSpmfIf%2FAM2Kw%2FS4nzx7W8fCHqUhOVYQoavbWspHnCZf%2FVGrc80qTnBiVCgkFMyAQOQO5%2FLGzvCFkCp5TJsCTidZtfnvL9ka0zxC3M3cSqPlrnP9UU%2BDyn8hWfpq%2FmlXEYyvNfp9zW%2BY0u25gKVUoAq6Z8puNxu3yjQb8vHT9ewU9iGhStMXijDLCGHXXFEVIdIsLCOooabApKOzvMYmrIumqBSjEVNfdPktsVBC1uHuAta%2Frj28tLNoYNEdsUnCQuN24uynwxh3AE1iIVOdNZangwzJ9ADLrli2VKcLt7hwLCRotYpJNwRGknAdfKCFZh4gx6w%2BSOcWsa0m8TB5Y7YC5iYtzMed1es3jy9OvvjcmV%2BW%2BDcZZfztUqDdVTXGax0LLyZhsSSpMS5Km1N21l3pLKCgdOkEHeA024FXNo3FkWpQoWIEXFvGGDawudrc4uj%2BTOFUcg%2F93GQYXwxTcJSE7IyLCiZxxtanFL2CUg7W7723gLPmirpKJKp63vknNcvO%2Bj8oMaJ6MnaOrZzA2H8YU6Vbr%2BNaNh4MpeCEzRdU6604sbhLaFBKQpNrm199os1P4f8AKt2Y6FWb2H1OOdUJCZsqJ9TP4oDmpSNo852O0b4zJytwJhbCy6hSKyqqzTjv5lm5NRVJPM9HckFQSvWF3SQQLWjRMB6mXrAAGPWmZ6tri8WdRUk7KiW7nPXAXgzG%2FMR4plalqvePLqc%2FVI3fljl%2FgvFOXqJ%2BpUh9VWM%2B6FTgmLtqlghIS10VtlhYUrXfcbW7YDSPLnG8clUNnDqukKQoiyL8zd43%2BQCLj7kmCtGoSri%2Bt2qtF4otCpmHZFynU6QTd1SVF4rJUixvpSOVrkwGO5vlfsE0xdOnoOr6enJMaUKCOcdM1nCVFxNTW2azVjIqkUKW70dOmH7NuudQurbSUo66SEg77mLAzkvgl9aWJbEbr7yzZKGKTOOqJ8yQm5gNCKSdMUW1lK%2B3443dmNlzgvCuAZCZpa35iszU4qYTPtTAVJTVOW0nowlsgLbeS4HNWrYggbERpNbdt4D0ImSntip4554tqypMSBxfaYC5OzStOxMeUlaopHpFDa8dCYNwHgDEWXVIW9hYNVlqZdVNVFEyq04wppAbZU1yQpCtSisG6r25QHPpaUe%2BOgMo0tu4OSrfS222m57D75tFf3JsGpvop61fbWcItF8pNIl8PSJp9Nl0ttFYWpRJKlAJISg9lhcnvuYDFM67e16nNhzV7y33fqixt8UaRU0AbWjpur4ZwvielygxLWZyWXKjxZKZakuvp0lRcAW4khOrdVrchcRa5fKPK97rs1yrPFsFxz84ZhVkJFz1Qfl7IDnV1tWm8UW3LGN25yZf4NwjhShzeHD4zNT0xOKdnUuK0TMt70pizZHvSkArSoXN7jlaNIuNkE6RaA9iJiw5xEzF%2B2LerpB2wSXD2wHpeeKto8x3vESF9sdEYWy7wDVsHUuYmqChFQa6VL8yl9ZM0F6CjUg9VBbsoAp5hW%2FIQHOZQTzjpHLicWmguypspLjEkkG5NtDf%2B4iZOVuAnho9i3lK%2B1LlhF9pdHpFFkRL02UWjSbOqUsknsHq2gNlcOy1e6vJMOIuFSM46e%2B6ZdY2jXfg7SyM16mHEXX7WX%2BjPd763f5I2Vw8oadzSkl9IsPMyM%2F1EjygZdYMa58HwA3nFMoSkEOYYeUrzDW3HlNNYzwO8fwulhn6TSzrjtAGfBIIN8PyHpHXdjnVHbeOiOPABOfZFueH6eb2%2FdOxzwOe8bein6lu38Pvlq3r5er0pXxeRmR%2F2Sx8kd954laeFuetpLjuAUMpChzUoS6QB5%2BttHAcyU%2BKTKVKsno1G47rR3vn2lxXCtMtob1uPYPk5ZtFr6nHFyqUj448xpzOWIXH01e2hvXHPua2y83vcE8SMhP07M1qnTYAmJXD9DZmQP1VEihK%2FlTGrap%2Bg%2FufxxuXiR6NeakwuZGlbdHo6LHstKI%2FLeNSVdDTkslts%2FCEfQbD5GiPNHsc21nOufTLHSFKOqJSLRdJeVbDzPjCdTXTNhwd6NYBHxRWqMtSWpOpLl0OqdRUdMoq%2FVEuOk2P7q4T6rxlY1lse4xPF%2BqVPosvM1luVS6WmmmVSZWryFKWjVq79iq0TCRoiS4fzQkIoiX0p1C%2FjehJJN%2Fg3KokY%2FCMglJCjqm6Wh9D3Rrk1qmutzeHS6Sk92ze3p74kp8lSnE0IzLbylTM08md0qFlNhaAnSOw2KoCxt3Cx%2B%2BEZXJpWmRmEt6ukLCw0QPhW2jGej98%2FhFXqBi8y8y6lslJcICbgi4AFriA2rmlIPSdAyrbfS2lTmX8k8NBv1VTk2Rfz2I%2BSNPV0lDibdt43LnTPh%2BlZUJbZW2Gct6Y0SoEalCYmbkX9IjTNU9%2BcRfzxQWobwi6yElJjxkzwWUiTfWzo5h0JugnzX5x7ZKRork3QRNpfKH23TPhP2wW5p0%2BawTf0GAsESkDsi8yErTX2KSH0uF16fWicKeRYBbsE9x6yvkiR6Tphkpl1pDnTpqfRNm9h0GlRI9Owi4tEQIvuIv9Sp9IaNe8XS8DLPoTTzruCguKBC%2B86besRCbkqGmZqSGPGEstyKFy2o9YPkNFV%2B9PWXb1QFqpdjNttrvYmMsqcu%2BGJJbWsATSEOaL7A3Fz67Ri0q2ph9LqOaFRfBU55ehLy1kFxJANhc9hgNsYnkJuS4ZsKuzBAbmcwa%2BWbp6y0pkpUage6%2B3pjQ84TrO8b%2BxtOqmuF%2FLIKaPXxTiR4ub2JKJcW7uz5Y0O%2BxrUTeA8Bv2xCLouVk0Up19WszSJhtKBfqFsoUVX8%2BoJt6THrqVOo7LlfTLqmEmVLapEG3IuAKC%2FQk7QFghGQLp9F8YfQFuhtNKbfaJPKZKEEg%2FublXyRTap1GLlP8AGFTAbmKa%2B68pJTcTCel02H2vVRtzsTAWOJRF%2FkKfRn%2FYQTPTIE0%2B4mdKSLhAWkJ0X7bE8%2FNHhcYkfYhLzanfHPG1ottp6EIBH8K94CtQEqXMrseSfyxdmmlzVc8UW4sI6C4HebxY6ct6XdU42TuI9CKi%2BJ5MwlwhxKQB8fKA2q3TX5Lh9x06tnSyvGlAbbcINlKTKTpUlJ5XGtJI84jSrlzG%2BUzyp3hQxNNE2EzmHTAW7nqqRT3QpXrMaO8Wc7oDxxNF5ZkaR43INvdOlt2UcW%2BUnfpgHLWv2bI%2BWIyclR1%2BwS3w4C%2FMLTP2PwAtNin1EwFliBF9xF3l5GmGnS00%2Bp7pjUCw8lPIsaUnbz31fGITklTW5aruyqnSqXnUtypUbXZJc3UO%2FqpgLPEtzGQTtPo4fqyJQPhLTbfimog9fUgLCtu4qtHgqcpKNOt%2BI9Jo6Bkr1nfpFIBX6tV7ea0BPJrc6C6TuSSbdsSMLmCs6iSnVexirJocVLpQlNiFEbRVQpMq6hei5QsKIPbAbIwlQ6p7jmYVbLQTJzMnIS7JUoe%2Bqbnm1OWHckdvp88d9cUzaGuGV1IAA6SiJHdslEcI4bmlTHDvjRp1y6ZByTZbAvdJcnQvT6CPxx3pxahCeG5XRC6fGKMfVpRfaPl%2Bl8Z47hcR5Sr%2Baxdy6ZRdbafNT%2FycDgRKoEcomTEyhH1CXDUd%2FPCx7onhAQHKJYniSAmHKJ4kGwieAgqCecFQTzgJucNJgnnFVKYCS3k%2Be%2FqiGkWiupCNIJJ22O%2B94goJSyHnFoQ3puF3uD57wHnI7IAbRVKBfb0xTUbG14CU3idIvEsVUCAtVZqi6a8httYSgjVeJaLi5yam1SU690suUda4F0WNgr0xcqrIylZkEyEwhPSNqLjDvItX8oedJsNuwiPbgmcm8DyGJKbSm6VMMYqpZpM85NyKX32mSsKK5dxX2Fza2sA7efeApufwbfBUO2KKwe6K7i%2BkiQ6bdfqjv5wHieHVPVvGNV1PvLm%2FwFRk0x5HOMcrw%2FM7htfqKgMHj3UmUYmpkmdf6GVZSXX3ALkIHYPOdgPOY8bce6XlZmak5tEqwt0MoS%2B8Ei%2BltKhdSv3IJFz2bQF5bxnVJQhGEpFmlyrd0IUiXS88sfu3FpNz6LR5q9VavVkSr9dk2Q8kLSmYRKIZU8Odl6AAq3YbXEeykUer4gwyulUKcDzspOOTcxTumSgkaQlMwgHyxbqkA7d294tVYolUobjDNUbbSt4EpSH0uFPffSTp9cB6X8XTM1ILpb9MpPQLQlF0SCEuoKeSkrG9%2FP2xTpNYk6NLCYTTJeeqK72M23rZZR%2B85LUfPsIszZ98Hr%2FFGY4cp8lXcOqptQpL7RZmtUpWZdsuFlRHXZfQN1t8iFDdBJ5g7BTGJcX1GmpXUmpGYpj3SsIU7IMhpKtPWCSlIKVAcjeLNSJalNsLqVaLi5RnZDCFaVzDp5Iv8FI5qPdHpYq8%2Fhp%2BZpbMxLVGnuLtMyurXLTI709qT3KFiDHgqUk6llUxLsvGTbmFMoUoXCVEBQSo%2FbEfHaAvgxzW0ttytNo1GkWSAUMopjbhWOabqcBKz577xb3dddqqHJtmVp2tsOTKmWejQ2hI6y9APOw5DmT2RcVYfrmI5WnTdKnEVJpqVblQlb6Urkyi92lBRFkgklJ5WMWmYpdUlZl6RUEvOpYUtYl3A6FNJ6yrFN7gWufRAXRGLJ2lptg%2BhS0lLlPVmJiVS%2FMODlrK1gpTfuA288V5irJrL4omOaVLyM44lJYqUvKiVdZWsAoU6lICXGjtvYEA3BPKPLQJWo1zDz9Bp1VutudE37GreS2h1IQQHUEkAqTuCL8jePHiX2RdVJ0ycqBnn5JgMJQhfSCXQVkhpKhzAKibDYajaAskxLTElNvSc2nS8wtTbgveygbfFtEsV6mp12ccW%2BT0wsly%2FwBsAB%2BSPNAImiWEBdaPhus11SE02UDgccDSVKcSgFZ5JBJ5mKErSZycmHJVpizjRIWFqCNJBsb3tbeL7LSbLNPo7FWwvMTPS%2B%2Fyk1JLsp9tSt0r84IO43EWepyryZ%2Bd8XafcZbmFJBcGtabnYKI7YCNVoFUorMrM1GXShqdC%2BgWhxKwooICgbHYi4594jwNmKsxLTkuw307bjbayVISq4HcSB%2BWPOiA6D4RU%2F2UYiV2ClpB9HWvFmZZUvhirbNiSvHFIT%2F6Oa3%2BWL%2FwgIJr2LFDmmkot8ao8dPmG5PhhmaglGpQx3TrBRsCUSUze%2FqMBoTxJ0t6wDu5pTt5USeKvFJWEqsFaL6dtXd6YyWUrnijUi0202VSMy5MMrP2yhuD3iJfZYsNtsNoSlLU57IJT9q52j0X7IDHDKP9yvK0cvhd3pgqRmEgqUhQSlQQTbkT2emMiXWC4HNSG7vTyZ%2Fq%2FqoHZ5ohNVpTpmveUpM4%2Bmac08g4LEWHdcX9cBjjkupHSpKT1CAYj4o4gqSpKgW%2FKBT5Ppi%2FzFWVNCoLKUpNSU2pxKR5JQbix89opTk%2BZt%2BcddQlJnkhLgCjYFI2tAWVcu4gr1A3QBqHcDyiTojysfJBi%2BPVFTzkw4pNzMS6GVfweRiRFdDE30%2FiSFL6IM%2BUOSeRt3wFGXH53ToIN9DZH3QH5YryrZXVW0pG5cNvuIlncQKnpNcv4ro6QJ6wI2AIPIeiPXTamXJ9tQYa0rXc%2BpJHOA6f4HE6p6TT1b%2B3GRVuewU%2BZ5fJGU8ba%2F8AhDw%2ByCCE0dxZ7wTML%2FIIsnA10jk4x1ElDWL5RzzgmnTO%2Fo3i78byv%2BEihDvol%2F8APrgOeGP0ZLjsL6AfMCsXMduMOPSEwlkpbdb0pKXLEKBHb%2FqjiWSBVPyoFrl9sC%2FK%2BsR224S8klSEo0Cy0pNxcDv9UZbD5SfQxXjXZwuEnPql3UdAnUVXICN9PabmNt5YZlNUYolZhLjjallDyFLvqb7LfukHkTzG0aXlVMy6S4lxVykgA%2BbfeAm1Je6Rp7SVHY957o3fS5su2ZWpSVQlkzkhMJeaXuFJP44riYWpISi49EcnYWx9XKClLcpOuoUl3UpAPVcH2pvtaMvTxIzFOFqvQQtSdrsPDl32MZaYpmNqJrmJyiM2%2FVyci80pmapss8herWFsIOu%2FO%2B294%2BePEJgT2m45rdOYl%2Bjk2VomZQJ7WHPJA845eqOhK3xUqTJuv0SgoDibdEqbdITz3uB%2BKNE47xvWMdVNVZxG8y%2FNOI6JPRtBIba7EDzDzxmimizonOdvgRTaWldpE8HVG3NpqhUZtpa63Nt%2FmtxOmTQrbokfb%2BdR5RVm9HRrQ436NPfF%2Bn2PfOk6RKv3PcBytFhfccXqbWUq1RoS3onNZKppNOmgFX0pJG1iDcbfjjHpJrrpv9sIy6rEuUx7pW0p6p06duUYvLtrOnT3iKVbWWnXDTVZTpr1WHdNOD%2BVGTZi290aq6fJ1s6fvSIs9ek%2BjrlWcdXLhLj6136S17m%2Fxxc8Wl6axpPPLT1lLbN77HqJ3Eas7WXbDYuV7CHKgttZsEyT5uewhs2%2BW0WWudZ0emMqyll3U1QhCNanZN5ABFxcoNox%2FEjDjboLzZSruAiEsRnE3HkiLRMMEnkIv7zSV%2BSq%2FqigunuK3CR8UBjy5ckbCKBZWk8jGS%2Bx7g2U38kQXTL%2FAKWfigMa6M9oiUptyjInqOdNwgj1RZZtgsKI7RAeQpBVFaXStLg0xTQCTeLzh%2BlTVWqDElJS65iZfdS0yygXU64TZKAO0kkAemA2bkHwz5i8RNZnqLgRqnNGlywmp2cqL5YlmEqJDaSsAnUsg2AHYSbARr7HGBcTZe4oquDsW0h6m1iiTa5KelXbamnUnsI2UkiykqGykqBHOPp6mo0PwffDNSkzNKarOMq5NNTM9JhzQZybISp9Gob6GGjoT3rNu2MA8IFlTQc0Mv8ADnFplqfZGRep0rL1h5lO71McP5lnFgfDZWSw72gEX5QHzdWi24iS5EXGdlegdKSLb2i3uItASoO8VNJVFHlFRCyICk5PnVoYYTpTsCon1xWZfbfT1UhC0eWn8ojzOSi0OdGOv9qpPyfJHplpcMoK1KutexHcICO%2F%2B6Ybnt%2FkxU0xs%2FJXI2sZ0S%2BNn6NWqfT1YIwzMYnmETgXaaZZ2U02pIOlZ7CrbvgNWFvzRIRba0bIwjkXm1mFQJ7FGBst6%2FXKVS0lU5NSMqp1DNk6iNvKUE7kJubCNfvMEAKG4UNV7Wv80B5NG9483j5%2FS0J0%2Fuuce%2FQQQ2oWC%2BZ7o8k3TXWH7BJIULhadx8cB6W%2FzRLom0I0JVdPrHOIIFonYR0Eolj90VKT3GFj2CAyHAn%2FABsoP%2Fm8j%2F8AcNx0p4S2x4uMUHukaen%2FANK2fyxzfl%2BlRxfQNHlCsSBH4S3HRXhJV6uLfFY7peR%2F%2B1bgOT3EHUfPEvkILh%2BDFdzyok0a0Fv7aAkS866ApRTYdgFrxNueyJRLPJcCENLUPMLxXDW0BSDYPMRMGU90VQi0bIw1kniLFOT%2BK85KXPSApWDqlI0yflXXFJmXFzXkKaFtKgDa4JBtuL2gNZdHbtiXT5xGdHKDM1WB3MyW8A15eFWl9GusinuGTQQbXLgFgm%2B2rl54w1yWWhelSbH0QFHpG22%2BkWfJ7I8bddmW3AVNMLbJsUBNjbzHvj2Ot9Ijo%2BceNFMXrvoVvAXSYCG9C23elbcQFoI7j2HzxSid9OkNtnfQm1xyvFIkwFTpB3w6TzxSiI5wFZK7RPrudooDnFRIgPQ2TFdJPdFFoR6AkWvAZlTP7VNegxecpmk%2B6lSppZASwH3FE8gAyu%2FyRZaafzqa%2FemMhyobQ5j1oOLCUGVnNSj2ASzhJgMAn6miekV0%2BTcU3KtS9ysb9MvRcX7h3RmnCR%2F8SOV%2F%2FwC91G%2F%2B8ajXzkqGJc%2BLvlQ6EDyCbXTyNo2BwlahxI5XhQsr230a47j441AfodhCEAhCEAhCEAhCEAhCEB%2Bf7jpN%2BKLMpJJuMRTv84Rz68dRZuBbQ38d46B469uJ%2FMoi5%2Fshnd%2FPrEc%2BOW1skWPvSQR%2BWA2DSvsW32ifxx2hLZ04fycwBktiusVnHkxUpbAS3pDDFNWPYWqJS6%2B2BOBRsLrUb2B6oEcXUfyf4Ii8z1arNVl5CUqtWm5yXpMqmRp7T7hUiTlgpSgy0Pgo1KUbd5gOmMNYblcNz%2BUGXlH4faVjah5j06nVXENceYdXMzD82tRmWpR9B0yjcok2sftN49mI2ncM8PWGKNgjFeYfj1Kr2LJDDzuF1OGWnmUVBSNc%2Bps%2BQW0nSU3%2BFtHO1EzNzEwzh1%2FCWHcc1um0aYCwuRlZxbbVl%2BUEgHqg9um149WFM5c2cCUNrDWC8xa5RKUyVluUk5jQ2jXfVYEG17m%2FpMBvbKJlZ4JMdsyMm6847ixCQyyhS1qVrYuQBvsOcaxRRsR9b%2Bx%2BreUf7hd%2BaPRk9xL43yVw3MYWwpRaPOy03UHKm%2BueSsuF1baUGxBtbq3NxzMb%2FwArOL%2FMbGOCM08S1uk4fTNYHw61WKc1LoWEurU7oUHgTfTyNwRAeTg0plQksc4uRP0ydldWHAEKfYWgKPTcgVDc232ji18DW6n%2FALZz%2BeY6cmvCB5ulOhvCuE9YChrSh4jcEctXnv6o5g56v3xV8ZuYCSO4cg2w7whzSDyMtiK%2FxORxASI7k4YjL1PhraoiXQlb8xWJFwncIU5dP9MGPmvwoTFGGWFdWyLWP5K3VwifxtUeGmXJ%2BVzY9w%2Bup%2BG7Xaef31pbf4rxbC49J46w%2FPtOOMCVYmT4w2FamlEpAIKdwefKNq5bZKZ3ZdS1VoddydpuNqVNlnoWBiQSbbT7N09Mko3VqTYWNrWjL28H45SVW4MaUANwDjpZsbW9cejp0uwPL8G9Wc%2F76Y97DOG3vP5Kr7IajcqGGUkpcxXJ3O5HRuH%2BjHonqvJzZp7svOqmww2EBwoKQUpV1QL72tG004Txupdl8GVEHSb3dxq5b44oe1bHNtP1G1F37fbk7cHzb7RPHDBZ%2FarP%2FwCSnenvXe%2FJV9FzZUct53ElRaTKVGnS4mlr0CZdLYbutR65tZPpPmjWeIaD7DzaGEzAeS40lwK0lJBI3SR3gx3CrCOPXJdxlvg6oqXFIWlKxjdYUgqSRqso2Nr33vGr5zhlzImpjpJrImYdCEBCdWLWhYDtJCdzFZ0xwaP2mz%2F%2BSjtLU4Ve6vo6o9MS5WMuL%2BV8kVW5RKgpdj1UkgfbHujqVrhZxu6NRyBSj99jJIP82DvCpj0AJRkMxco16k4wSfVy5%2BaKcdMFjbeKP%2Fks%2B0mcIvcfMnmnc1kMlJOh4gl1S%2BYFKqbEq%2FLveMyLDy2VnQlxQSVJSeqolskgdZJtcbxn7zgdcUu466tUbZ9pWZCGktnhIwsopQhGr21vXNhYk9fmYq%2B0bMhXlcJmFB%2F%2FALa9%2BRcZI0wwaf2mz6dO9Heu8%2BSq5vvaiuO2PHihp2YwxVmGEFbi5J5KUDmrqHYRuhzBGaTnRkcKmExvbUrFby7j75tF1Tl9mEro2n%2BGnBBUu3LE0zt6SFRWdMsGjZeKJ9FdO9NOFXqrPOzqj7Pvack6pSXaTTnZ%2FFDEstEmy30L7bhU0AgAI5W27or%2BztGS0qSpddTUC4oKUhplaUelRUAB3eeNjzGAM0W5lxljhYwa82FWStOJn7EelTm%2FxCKQwPmwhehHCtg3SOdsTu79vMOw444Py3iz6dO9WcMvMfRVc33ucp7LGaxFPBaazTpMOuFsdMpQS2nUSCtVrAW%2FJGqq7RPYyf8AFUvFxPRpXqItzF47lRgXNdSVpTwrYPaDgUm%2Ftqd1AqBFwekNrXuL7XjXx4U8xakQZnJymFTSQ030uLwCUp2sLAb%2BcxMaY4N9Yo%2ByujetThN6qjPgVR6Yn73Jglh2i8VEyqTsU33AsnmY6ua4S8edIllWQ9LJUAdSsYiw9JG0JXhUx84FNjISkMOFJQlbuLjsfthva%2FdCdMsEj9po6dHaJwm9Rtpnmnc1ojJSi0bEEjMUvF4n5eTdZdL6JRxAcKdKjpSrcAk6d%2B1JPKM76UOazcJ59Xu3jbwwLm8ykSf1KeBHOhCWyo4kdXrskDXs7ve19u0mHtLzcWoD6kvAYSRZYRiRwfGeluImNMcFn9ps%2BnTvR3qvXkq%2Bi1GwodJzEWzGLTs7g2sS0uy4uYdlVpbaSkkqV3C0bvXg%2FN9pBU1wm4EUW0hQ04jeUTc2sPfdzF1RgPMvxKXXN8MOCxMPoCy2nEEwro9%2BSj0lgfNDjhg07LzZz%2Fvp3p703rb8VVzNPs1mjpkpE1OvLlnDLNAtrlXnSkhIuAUgiwj2UrEFEdfLVOmpmc0AuqJllNoT3XKrd8bHfwxnezMJZlOFfBLzKLpaIxE55Pdu6LH1RSFDzySkhXCjgdSAkpI9n17%2Bvpd4Tpfg8ftVl06d6ney9%2BRr6P3uZZ%2FKmo4grLbNQq9OpUq%2B84FzU0tQaYHWUFuFIJCTYC4B3IjUNao5ptSekQ6VhogBSha%2B147yNEzmMs7LnhIwT760por9sLuoBSSLi7pFxfbaNXDhczNn3%2BlfyFktW%2B8xiwG1uQvfeHHHBfrNn9lpRvO9d8mM4squZyeZbvidqVKiW0pBXewubAnujrZjhEzMUoKdyOoNu0O4oO%2FxGK54UMyUFKGch8OtKBFle2pRvvfa6opx0wWNt4o6dO9k7z3zLP4urma5kMmqdhTHTE3RMT%2By8hSptp2Xn%2FFFs%2BNAJSokNK6yLKKk789N%2B2No7T%2FNenrFXPvMbHVSuIFNul4YMstrCwqTlja29um80QFP4iwoKHDbloCOX55LsP8APRbjlgf1uy6cInCb35Krmje1x4qGbpCblXfvf0RZMdU6aewVV25GXLs04yOjZQnrLspJ29QMbqDPEgj%2FAPpxyz%2FjJfW9Hv0eqSYz%2FccT45w9ZepBSTdqfcI1Gx3982iKtM8DpjPuuz6cLRhF65bOrm%2B9pNWIsPJZaM9UayhaWUJLYprjgTYcgb8hHsomM6S%2FUZaTpDlUm22EvTCw%2B0ppCSpISLJJtckbnuja83K8RTK0hXDjlq%2BlQUklFRc1AE8ieljxFjP1N0jhXy9NxYkVV0Aj79e8RGmeCzsvVn06d6s4VeY%2Bjq5vvcyTeTlTxNWHXZitScky%2BXXFOupUUoA1qBOkE9gHLtEaarVINMqL0gTcskC9rXuAfyx9AOgz9XKvyZ4X8u2UPMOS5KKo4lQStJSdJ6U2Nu3nGpJjhdzQn5gvzOSdKWrqpBcxMomwFgL3hxzwWI13ij7K6N6Jwq8%2BTqj0w5LLAG3bFeXlA4ttJudS0psnzm0daDhJzJ%2F6jsO9U3P9lC9x3eXFSX4Us0mJhqZkMkMNsPMnUFLxMpQN%2FMV2%2BOK8d8D%2BsUdOjtHeu8%2BLPM1jScoqXhvFspVpTEipmVpswh9DniqkqcsPtCbp622%2FdeM0DnSOK1xuxWGs%2BNOp3hcy2ULAG1XcHK2%2Bz23KKKsP53J0oHCxlqQBsfZd3bzfZufyRPHPBp2Xiz6dO9Peq9cllXzfe04EMn4QiC2SDqB6npEbcmcI53P9ZHCll%2BFH7StO7%2Bf7NFeSwvnoy8HEcLmXqHB8JVYcKTbzF0iM0aY4Hl%2Bl2cT%2FAB071Zwq%2B8ljVzNW5xqCuFzDKUG4RjxSVWG1%2FY9R%2FEofHHUfBjMS7%2FDPTBLEnoJCpIdJ5lYmHCv0jcD1Rz5m1khxAZlv0alyeWmFsMyFHDivE6XV1Ll3XXCFdIsOLPXSBpuOwkR07w44BquUWS%2FtRxJNyj05LSM%2B%2FMLllFTSelKnCm5AvYXv2R4LTnGcPxO7WNndbamurh0zlE56sqterzzDpXG7Wt2oqm2py1T7nzqZVq0K79R%2FlGOleBBQTmxiFV9xht0j78iOZ2PIT3WVb0XMdI8C7qEZr19snruYZet6A83f8Yj2Wm%2F%2FAOP28z4Kf5oc3D5%2FtNM%2BefY9uLHSOMDNH4Rl8ENt28%2FRy%2B3yxo2sTAkJKTm%2BjKm5aqyy3rC9k9aOn8wsls0GOI2fzowVR6TiGkVmlJkqlR5yqCQW6CwG1p12OwUhK0qG%2B0eF7BOMmFgs8IuF12Frox07b02I5xytG9K8HuuFXewrvFEVU0UxMTVETExERMTn52zeMOvFtaTXTRMx5tfvaWcxTgNxfTO4kmlLI1EmmuqVfuv3x76HW6DV1T8nR5%2BYebQ0yErdZU2Ee%2B6iN%2F8Ae0bTVhDG4NxwdUBtX26cdr%2BYxE4VxqwvqcIdJXq8pTeO12%2BIixjvccsG%2Bs2fTp3sHeq8eTq5vvc9Zg0Cp4qrK5htAeaEsxqWhW4LLOgpA7TtGpMx8CjBFafoTz7T81KudE%2BpmYS81r0hXUWnZQsobjkbjsjuBGFcVpcC1cHVINjewx24AfNsI17ivhtxvizEMxV3cifEm5p1b%2FiftxQW2So7oQro7lIsLX3iOOeC%2FWKJ9FdO8pwy81fMmPTH%2FwBuMSyE7aYiiXK1WAjsJjhBxWtVzkfIJKtkh7Gm4PfcNiK8vwf4vbWSclaGVA3urGC%2FyJiOO2CRtt6elTvZIwe9Tsp9rRFHyWlavg2jYnkq9KTLtXl3npiUbKg5T1ImHGktu3FipSUBwaSQErT2xv2mzKW6VS5Bx5LhpdPlZHUPJJbTp%2FJvGwcKZbZm4Nw3IUBnhpy7qSKaFoafnMRvLeIWsrOrSpIVYk22va0XJqiZotElPCXlxc%2FCGIpkX%2BJcU48YJyXmjp07ycIvUfR1c0b2u%2BhDnvd9f21ouVIp96lJ6krQ30qSVnbtjOUyubTRCm%2BFLLoaftcRvg%2FKu8e%2BTns3mEXc4XcDIdB6hRiF7SfSCT%2BOL06a4JV%2B1WfTjerOFXnls6uaN7k6g4toUpICn1uen5Ocl3n0uNmTWogdKreLkrF%2BGyhtEhN1GacfcbQlPiK0BR1jt5R1BVKnnRPrUn6mDAbwIBLiq%2BoEqtuOV4tjshm0%2BW1zPCzgdQRchIxU4mxPPlDjlg%2F1qy6cMc4XeI%2Bjq5o3ucc2sJVvGmM6rPy7CFSkw%2B24khYChZtKCkg8rFPyxpLMrBSMF4jfojc03MrllrZecadDjSlpO5QsAak7jf0x30ijZj69TnCbggnUFX9uDwv6bRq%2FFHDbmBi3Es%2FiOfyRpTS6g%2BuYVLIxeRLslR8ltOi4TbaxJiJ03wOnbebPp070xhd4n5lUemHFXQHuh0B7o7Jb4PcXlKVe4nh%2FUAb68Yr37uSeyJ0cHOL06ArJnDSiD1j7bnbW7vJjHOnWA%2FWaOlTvT3pvPizzS0NTMk5aqYVotfp9WRNO1eRM040m48VdDq0dCq4FyQgKuNrLA5gx0AxNtty8qyp0EsS7MuknYHSkC%2FyRsPCuWOZ2FMMyGHU8M2XlRapzamW35rFD5eUkrUrraVAG2ogbcgIuTeGMz2wlA4UctdKbmwxRMbnznXCNN8Cn9qs%2BnBGE3rLXZ1c0b2swhb%2Bpz7ePdT5TUFhG5N0aR2nsjZCKNm2gJSjhby5ATy%2Fspe2%2FlRcZSUzVQhJmOGTALbgNk9HiV4keve0WjTXAp%2FarPpwnvTefJ1c0b3JWEqjSZXDsjS6vPTFOnZQOMuy7kk4dKws7AgWi9M1mipfl2ZeqvTTi5pj3hEosA2cSbkkAWFr%2BqOnZgZ0OzSlI4bMvVNkgpKsQuagR3m2%2FxRQXQ80pgHpuGLL5VuY9tbyQfVpis6bYLH7TZ9OCcJvEbaKuaN7lfNfBtWx7jio1mSlQmSfcSSvXdwq0pC7J7hbnGlMxMItYMxXUsNtTjM4mnTK5bxhhwOMvFJtrbUPKQew9sfQ9vDeYrakFPC5l%2FZBGxxhMb2N7HaNTYg4Usb4krtQrU3k9QG%2FH5pc0JZrGC9DBUokoQejvoF7AXNgO2I484H9Zo6Ub0xhV4n5kx6Y3ZuIjL3idqUClWjthPBTidbWlOU2G0uKNwtWNHDb1dEIgeCbFW%2FR5W4bSSbg%2B3J07d32OLcd8CjbeKeeExhF55acvslolrI%2BnuUShVSj1OWqblWpbNReLDix7HvLKgqWeCkj3xIRqOm4ssbx0AKsqalWkKFlNyzTSj%2B6baCPxJBjZVGy4zGwvhql4cb4csAT6KYwJdD7%2BLphbzoBuCspABO9tgB5o9CcMZlt6izwzZetKURfTiqZsB2gAg2vEceMD5bzR0oW70XnydXNG9rNtvpP33wvni6KpDymOkCFKSUrsACSq6TytzjYKKRm22FBvhyy6TtsVYmmFfk3i7y7%2BcqEgP5B4BJRYtaK%2FMEC38DaInTnAo23mjpQjvRevJz1b3IVOrFLVIywnqs%2FJvNNBtxgybpKFDmLAWEe72epLk3TJGRqE3NKFUlHFI8WcQhOhwHVc%2Bbtjq2fczqmtb73D%2Fl48VHUfz%2BdSsnv%2Bxc4sD9KzRmD0kzwwYOWoix6PFq0X%2BJuLRprgtWy82fSVqwq25aaub73K2a%2BBq5mFmJVKlKtMdBOuIKFreCOxKeR7Bz%2BONIYvwuvDGJalh4zLUwadMuSxfaXqbd0KKdaFdqTa4PaLR9FpekZitOpeXwnYPcUhaFJvjFfwTe32ONM1%2FhQxniKvzdZmcn1Nmefcfdb9uLagFKUVGxLfk3Jt22ieO2CfWaJ9FdO9TvXbzspnmcZLl0g22MQblgXAm0djngvxMFdInJyXKPtTjVF%2F9FFN7gvxOo6ZfKUMpJuScZNEjzD3qKzpxgnl6elT2icLvEfNnmnc01KZQt0l6l1in1ZqdS7LMzuptd0tKWDdld7aXEW6w3AuNzeNpOTHRo6NtxtXRJCer8PSkC4jdVFyrxjSaJTKHUeGqmVV6QlGpVU%2BrHqG1zOi%2FXcAZslRuAbbbROvLPEDrRbd4WZMXOq6MwEhQ82ror2jJGmeDTri8WeX8dO9Xvdb%2BJVzNGuTaHHN9P2wSE8vNHkmFBauVo3wvK%2BrrcUpXCiyQre%2Fuj7j0e82if3KaujS43wvyqiCbh3H4ULH%2FAxWNNcFmcpvFHTp3p72XjxKuZp%2BruKTwqZqIKrJXOUUAd5E6nn5rRnng03D4zjdq5t4zTHLW2Bu6L%2FLHrzHyUzTxlgNzAmDMrafg2Wn6gzOVVxeJxOCcaaB6NnR0YsA4UrvfmkRsDg7yGxZkgiuP4tqFPdfrkzKFuXlHCsNJZ1lSlKIA31AADujymmGlGEYhh1pd7teKa65mnVE57KqZ5PNEy6NwuNvYVxaWlOUR4XN3FQb8QGND3TyB%2FmUR5%2BG5AXn1l6pXwa40f5C4hxMTDE1n3jx2XVqSKsUE%2FuktICh6iCIk4dHQznzl8pS0pBrzCTqNgbpUAL9lzaPR1xMaIxTlssP%2BDmWE%2F2yn0x7m5vCEOE4nyhl%2B32ddX6%2Bmlkxr7OporzVxCFarmYJue3dW4jfHF7kRjLO8YWn8FVCRk57Dr8ysibeLVy50akLSbEEpW2CQRyi0VfCOPKlN%2BP17hXwpVqm622man%2Fb08kzDqUBKndASANagVW7NVo8%2FofpThVwwqzu9vbU01xNWcTMRl%2BFMxt8zdvuHW9tbVVUUzMTPJzNE0Sq0SYosmqpYhZknGEFKmnWlnTc94Fo9fs%2FRGG3JSQxC3OPPqbBlW2VhLllXuSRYabX3jb6MHYvS22TwcYTO1ikY3fFviESO4MxelzUODjCq%2BkAV%2Fx4fsi3ZyEeo47YNH7TZ9One1Iwq8Z66Kub72gcbNOVvCU1SJFoB52oImUFxWwRoUhQv2c0xqLEuU0%2Fh7DMpiqZq0k8mdmnZUSjK9T7BRoJU4nmlCtY0K3CtKu6O2ThXGqnC4vg0wgokWucavf%2FAI%2BSMax9lLmNjWnScjJcNNDoTUsXQ54jjRZLwWoE6gtJ6w0gBQtteHHXBPrNn06d6%2Feq8eJVzbnCrsghJtsYpGSR9rHYctwoYymEdI7kDSNQJ1F3Gqk3HZsAIqHhIxidJTkJh5AG6gcZuEnzX7IidOMDj9oo6dO9MYPep1RTPNO5zbgHLOTxdSq5UJjEMpIzVKEmZWnOtrL1RDzhQ50SgNCehSOkVqIunlcxtrL6gHCdCmKSuYK1OzqXrEW0p0W7I29l5kXmZl%2FMTzspwyYOq7c%2BgIUioYsccQ2Um4KQFA39N%2BcZQuh5p69R4OstrdwxE%2F8AkciOO%2BCz%2BbebPp07096LzG2zqn0Rq65hphxCFrIJBtEipdSthcjsKd7emN1N0PNcABHB9logA7asQTHLt%2FTY99Po2bLIcbc4U8sZZAR1LVh9wkg7D7J3dsROm2DR%2B0WfTp3kYReZ%2Bjq5o3tCMTshJ1F9iqz7slLzMq0A8hhTgKkrXsQncc%2Fli5S2IMI0l9ioSmM3mpiVUlxpxqQe1JWDcKHV53jeE%2FR80Ura8R4UsrH7j3xT9UfRv326T5bx4hQc4Ta%2FCTlMLnSfz8f6o7%2Fsv4ocdsGn9ps%2BnCveq8Z5fF1c0b3OmK5ZzFmG2JOXeDa%2FGXXmy4CNTbpUST287%2FHGpcY5XqwtRqXV1VqTml1B6ZaclWgrpJTolhKSu4sQ4CVJtfZJvaO41YezYacCjwh5QPFA0pV7MvcvW7GHZg5O5t5guyBmOHXA1HTIoWhKKZiNxttwKN7rSVquocgdrDaJjTbBuW82fTgnCrzyWVfNG9wu%2FIoQq20UvFEHYWjsdjhKzCUkBWSeDVK0ndzEz3PvPW%2F1RWb4S8xyA6nI3AoUtekoViN46QO09e1j5orx6wTy9HTp3rRhFvPzZ5nOWAstKDi3DdSqU3UlS0%2FTnWWkS5ST4wlwqupKuQKQkbHc6tuRjamEaSxhqiexctMghCybEc0kRujAOSueOXDdUNIyMyqmW57ogpmpVNyY1FskhbXvg0Hexvz2jIV0LiFupSuGrJK7g6xDit%2B69nt7Qp03wWrZebOPTXHuzTGEXidUWdU%2FZG9ovU11W9Q7Ep7%2FAFQcYN%2BRA74301h3iJ06jw7ZGIV9qvpCfkdi4ydD4gwFeNZEZIISAChKG3tjffk4ey%2FriJ04wWnberPpfcnvNefJ1c0b3O0jPSsvPzias%2FOS0vMtNNNrlWVOhZSolQUB2ciIu8liDDNHm0T8niKroeZOtBbkHGzcfuuyN51CjcQbYaNIyKyZVcnpA606Ld1vfBHibonEk8NLuQGRjYPYtDv9bExpxgk%2FtVn0vuRGD3ifmVc0b3NeMqcrFGG5GipU009K6HFG48ldyQe49YRrHHeWEnhKj0GpsVtqdeq7cyqblktqSqnuNOFCULURpXrTZxJSTYXB3EdxpoXEba5yByKUVC4CkOmxvy%2ByxiGYGTOe2P3pKYq2TmVEo5JNqZaTTpt9hvSpWolSOkIUq99%2BdtomdOMEp%2FarOfRVviEVYReI%2Bjq5o3uDH5BOrYiKHiSE7EiO3pLhJzSW2p1eWGViDbSETFQmln0iy7CIr4Rs2%2Bk0IywynKd%2Bv43M2%2Fn3jHx8wTPL4%2BnpQvGC28xnlPM5pwHlrhvEuDZqtTdcmWavLVBEuiT6D8zuyqm1lTvTX6riFpSkNkdYKJBFo2jhRhihUSXojc1q6ArWtRtYk6Qm3bayd79sbuwXktxHZeszUph7LLJaYZnFNrcRPMuzIQUX06NSxp5m%2FOL2vDHFYVKT7kWQjaSd7UglJ9QcvDj3gmWc3mzj%2Fd9ys4PeOSmere0YHmCCpLqR6%2BcQWtvtjeasKcVYToGV2QJ8%2FsMu%2FwDPi6UzC3FAoKXUcuMiQdggN0ZwkenrHaJnTvA4jPuqzn0TO5TvTevJz1b3O8vM09Kn2pwToSpaVNqZa1oI02IO43iq5XKJJoc8UVV3HFIUlIMqEXJTbnqjoafwdxNuLT4hl7kWlHwg7Q3jc%2BgKsBHgm8IcUzSlpTl1kK%2Bhv7G4aK4i%2FoGvb0mKxp7geWc3miPTM7lu895iNdE9W9zDi2hHGOHKTR3nVSjtJdcIWG9aHUraQNJtulQUlW%2FKNZY9y8kMMexTtPrCZ1ufkVTD6eiLZlX0urQWiTsu6UoWFD7e1to7mcw5xaMFCmcuMiVlQsSilqGnzHUuMLxxklxHZgTkvVMR5eZSqmWGPFx4olbCAgElIKErsSLnfnF%2BPWB5Z91WfS3wr3pvHiVdW9wu5JNA8x8d4omVTfqkR2e3wm50OS6nFZdZThwKsG1re1Ed99dvyxBXChni6hxPuZZSt2AFwpd1X7vfIpGnuCTnleKOlC0YPePFnmc%2BYLymoeKsMorDtbmmKimYU27LdBdgS4RcLDl7lZXtoty3v2RtKiyjdFkJWRZmiUtbFSwDdXLa3mtG4cI5OcUmXlKnKXhrBuT65WcdTMutTLfTHpEApGgrXcDT2DYx7XMP8X6lhSsrskVEC21Mat6bdJzjJTp1gVUfpVn0lasJvNOqLOqebe1JKKLrD7ss42pxKDoT2r3sqw8w39EeVy5l2pxsJS06ryr3G3ON0N4e4u2AHW8s8kOk5XTSkBQv59cU00jjEQnoUZYZMpbvqsKc2AD3gdJGSnTXA6v2qz6Sveq9zssquresvD3LTDOZ1OnFtlTD8jPoCwANNpdzc%2FjjWng%2B7jOaY%2FdYYfT6tbdrDs743BVcNcYuIsPVbD0xgbKmlM1SReknJiTl0MzCEOJKVFpaFkocsdlW2ipwscNWYGVGOKji3FrtMZl3KOZBhqXf6Z1TqlDuAsLC5Mef0q0rwe%2BYXbXewvFFVdUZRETnm3bhcLxY20V2tM0xHhY3x5gjPdI%2BD7ASBH%2Bcv8sc4nmY6K465hMxn1dKknRh2nJNjyPX2PnjnePW6KRlgt2z8X3y496121XpSzdvY%2Ba0c%2Bgc%2Fmx3fxOOmX4SX31XunDVKII5hZXLBJHoIvHB83vTpxP2zDieV%2BaTH0KzuwXV81uHFnBmDUSztRncPUsyyJh4NoWlHQOKSFHYKKEK0k7A2748hp%2Fb2V2xDD7S2nKmKpzmdkRwrPPP2%2FY6eGUzVY20R5nz54j6PNLzNmUEaegpFGY6199NOYudvOoxrBmjzbLYVdKk322j6HZi8OmB8R1ybxHN4azNnXZnoWm2qbTZMlplqXaabQOkmADYN3JtuSeyMXmuHjLKZTvklnhLql0pQOhbpdnFb3WdTxAPm5eaPU3fSjCYs6Ym8WeeUfSUdpq1XC3qmZopmfsnc4gaknQWVKFx0zd997axEkzTZl2nTbLDDiyuoqCCATqA17XHdcR1lmPhLJ7LGTptVxFw55mMB11mVlRVa3JycvOKbcS4%2BFloKVrU0FpBTyKgRyjWmH8xcF0yWqFLewZi%2BSkU1SbmaYzRcSMMlMm6u7bUz0rKw68hICelTpChzF9z3rveLG9WcW13riqmdkxMTE%2FbDStLOuyq4NcZT52o5umVGZmasWaa%2B4p3oi2lKTchKklQHn2ioKJUVLcR7GTBS5TUoQejVYL0jblG9FZn5WpQdGEc0yo2G%2BMJJIHedpaKgzcy2SAkYWzSAtuBjGS5%2Fg0Z1GhGpCcTN04PSL5Bk1BRS2RZVnfnTHjp6OrR1W8h90n7tNo35Us4cBsSDicP4OzCE2llYlhP4tlVy6XSghKlpRLhSk3O6QRcbXEY3hRzK%2BsKoNFXlfiucrzzbbC2KfPsONzFQU6oksII1pQpAbsgkkEK3taK1102dM11TlEa5TTTNdUUxtlpXoz1TFyYl5r7IhxKG3WA2pspvyHMdxvHR0zknhcoM5O5M5syi7rKpVima0NnsSFX3vcxWp%2BVGCJxozb2TmalNaaISvpKa46F3G2yL6fMY5dOOYdVstqelG9tzcLzG2ieaWr82JmsVWhZYF11tIYwHKyragjcoTNTNjt272%2FgxreYk%2FsWsdYNpSv0gbn1x1FiWg0XEMrQ6c9k%2FmazLYboqKNKOtUPrvpS864Fukr7ndOwv1YtcvlphmqMyUlOZP5kUoSTKkuzoo63nJ1al367YVZOkGwKbctwbxknFbh5anpRvYu5bfxJ5pc5NNKQmZATcCTfJ82wiq0gMPUh5TS1NMtkPFPMKUXCBflvG9sS4WwDhqmyzlUytx9Jsy7apWaqjtNLDcytzVoWQ6oBKgSlIAtcA9pjy4Zx9ldhbEtXYolCx7L4WmJSTbkFpdppqZdQgF8THSoW0pPSqcLakBKgnSFE9m3Y21leKeHZVRVHhic2Kuiqzng1xlLSMjKzDSaYhyXILM2VP9YeQVN2PyGILkZoSak%2BLqK%2FHwsjc3TpIP446TXm7lMCjoafmwkAnVeaolyOyx6D5IkazYyh6RYdpmbZSVEhSKhR0m3YLdBaM6rnWcp08U1UolHCh2bSpvqndIcVc%2FLFCbYs9UgRYty6APModECI6P8AdXypbU24ij5tPFC9Skrq9ITqF72BEudJ89jGI4Sr%2BSdUen5%2FNnL7Fj8%2FUpubU4qhT8v0aGFJQqXIQ4UlTiXA50nJKgUkWO0RM5DS3i6%2ByJxJ1NSGG1PoPRq1JWUkq53EdTqy54c5iyahlpnxQ3EMJb0CjsOdJts4bqNiYoSmCuGqbaLU1gPPWTVYAPN0eXUOzcAL58%2BztjSjErrOy0p6VO9s9yWmWc0z0atzWVVnKrM8O2CpCcUkyUjjSvBkBIBQXJaVUpN%2BZFwT%2FCjVfikdeVJeRE3hejZfDAOca6ZRajNVGWeTQmTMTT77KGlIWSsdUBu4tvdRi0M4L4fZ7VTXMsM62SyvUX0URlTjd1XCVDpNxYW5dsTOI3WIz%2BMp543qU3e1qnKKZ5p3OW3JR40x5IbuozLZB83RritPtLcdrriWVFK9Gi3MXdTz9UdJV7C3DzRJFSKnl9nS1LgF5c8qkyzWlF9wrW4EgAG17dsYecRZJyeLZKcwxRcf0ykuyE0irTq%2FEnZ9ybU6S0W2VLDXQhsNpUFHVcqIOwvsWNvZ29PCs6omPNOfsVrsqrOcq4ylpsy7q6lMSjLKy4ac00lJ7V6W9h39sU2dQMkFIICZF0K25KPSj8ZEdA%2B3LJ5H2PEmZ6FefD1MVb0Hpop%2B3TKwr6%2BMsxCgbDpcJ01fxgPfiMZVMmgJVpQ9iroI0rd19YbDWDeKIbIpjaiCD404Lf4NMdBPYtyldSbYvx3c2uV4Lpqth2fZosrFYyPrmIqxP4%2Fw7jZ2TSmURSH6UZNl58toKHnJtoqCEKWnQUhskJtY35wMmkUS8weuwfJVqip4vNuTa3ClpKtPJPL1R00xgDh%2BqsvLzEnlznpJy77CVNPJpsu94wFbh0EKIsfNsRBrAnDuXAlWXud6ei6QOPqprBS4fggJBuO%2FsjSnEbpEzHxlOcfvRvZfiK4jPgz0Z3NcYcdmXeG%2FHlJceu3LYroM%2FwBHp8kuImmisK7b6bW80ay8TX3x1o1JZESGD6nhD3NM310%2BpuSTj06ukN9My5LuOrQlrraRqLxSrUDsNrGLBT8D5IFh2kuZTZzPrmnEOtz6qU100ulANw2kL0qSrmdSb7C0O%2BN0jbaU9KN6KLC1tNlM807nNzEosvyiXOaZV71Ks4RE0hLKW7RkNtdIoOuKWlBv1QQo%2FEI6cm8G5D0qlOSnuV5x1B9J6VqfFJbZXL3J1NEKVYp3vy9cYVPVvJGlOUCYwFhHGyn5GquTFSfqc%2FKS7ypItpQluVU0FBtwK1q1LBBFge2M1jebK8ZzZVROXgmJ9iLSzqs%2Fzoy%2ByY9rTMpS55UlLMiQfW8md6RYCFHqWTv8kTzlDqbkpUCmmzYSub97IYUQpN3De%2FrjoT3Ssq%2BjSFUrNxSua7YnpyQT3j3i4iRnNHK9tpxp2l5vEKASm2K5AADzjoN4zsbQ01Rak5M1Qpp04rpEpLSiwqyt0X7PMYtlUps1KvpYmZZ1hamGHNLiCk2087HsveOjRm3lUndygZuPGwFlYykkgDuFpfaMUqOOsuq3jJmpYpy8r9bw5IU5ctKyk3iJJqKpguBwOPTKWwlbQstAbSkEBVwbwGl26XMOi6X9PrMehigTLmsqn0pIGwuSDG%2F8D4Wy5xB4rUxkjmLNUNt9xS3qW340Hxc%2B867AEC4Gob7bxNOZSSCkt0%2BTyPzTdU2VBE0KfpW4k%2FbJvp2jn2mK3GxrmzrtqYmPDVEe9sU3W2qjOKJ5pYBhHppXJnNaUmXUBSkUF0IPlEpnSnb1G%2Frjv%2Fi6UXuGx16wF6jSNhyHVjmVnKLFc%2Fl7jfB%2BGsg8eyVRxX7EtST88wgS8r4vNdI4p5alahqRsCkbduxuOleL8mW4c5iRKgVN1aktEjkSkEH5RHzTSK%2FXe%2FY%2Fh0WFpTVlaTnwaonbNllnlOrZPM613s67O621NcTGqnbq8O9wegWteC1cxEurlA7x9blwSIEG8QFwYmgEImsO6Fh3QCETWECBaApjnE0QtvtEYCdI5RXSk3FiI8%2FLsishQ1Wtz2gOpeFnKbE%2BXeIKHxLZmYZkpDLGQpc9U36xUltLDLYQUsvtsG61rU5pDdk3JIsNwY27g3HWROCs1Hc58V8OlYwbSccLk2VVmpvyUxIyyZz%2B6HKclRXKtzQKekVpIGoEhIJMYNldhfPniJ4K8eYBVVJWfkpEycrgdpxKUTcwuQcDszIOOCwUyElKW9YB1WBJTvGIZm4EqnEPO0XCOXGF6ecSTEjRaTPMzeFZ%2BnVuk%2BLSbcvNmdnHAJZTaFJVt5SkhASdoDX2eXD5mflDP1HEuL8CM0Cg1SuzktTDKTbT8slJWtxltvQolKS1YpBtsLdkaise6OuuP2t5lUnFFByrrE7K%2B0VmlSNQoKWGkhybel2RLPPTJPWLiFpUANgErHO8ck2HdAUtNt4XtE8S6YDIMuqbJVfMDC9GqjXSyNTrUjJTSLkamXH0pWLjvSTGXcSeCsOZcZ947wRg2VXK0Oj1Yy8lLuOKcUwjom1FGtV1EBRVa5JAIF9osuTehGbuAlOJulOKKYSO%2FwDNCLfLaMu4vnQ9xR5qKSq%2BnEbyPQQhAtAafKrRKV98RKdheJSmAoPAqSbRjNcVZh0fuFRk6tiQYxvEKLyzu1uofxQGDtm0XjDWJ6rhSsM1yivIRNMhaClxAW0%2B0tJS4y4g7LbWklKknmDFkvaJkqIMBeK45h6dmUTlFln5JDibuSizrTLrvultfNSO7V1hyN%2BZ8ahINyjSJcOmYDilOnYIKdtGntB53vtyt2x5dZEOkgPW5L0sLeLczMqToJYSUAHVtYLN7d%2FLuiZMw2zLNKlZuaamAVpeSlWlCkHydJG%2FfcH1Rb%2BkMRC4C94crjmGqzKV2WkpCdek3OkQxPyyZiXWbEWcaV1Vjfke0A9kVsO4omsOonJQy7c9TKm2lmfkX90TCEm6DfmhaTcpWNxcjcEg4%2F0hibX5oD2VBNNXNrcpaXvFl7oRM2Ljf7lRGyvSLX7hHpka3NUGqyNaw%2FMOSs1IFDrazY%2B%2BAda45FJBIKTsQSDzi06zELnvgL3X57D9acFSp8gaXNOkmZk0gqltRPlMnmhJ%2B0N7cgSIqYTxfXsB4gkcWYUnhI1WmLU5KTHRIc6JZSUkhKwUnZR5gxj8Rv3mAK6O20Sq5i3KInRaIK5i3KAhCEID2ylarEjLqlJKqTTDKr3bbcITvzIHYfREJOq1OnIU3I1GZYCzqUG3CkKPee%2BPHCA9E1NTk%2B7084%2B4%2B5y1uLKjbu37Ipt%2BXEgJvFQdkB0pwYShmK3jNwI1FujN2HpUr8gMYo6VK4TpptKgSvMdgJGr4Psc8fxxtTwfUq1N1nHbcwSGVyEiy5bnZTix%2BWNg4V4Osy8OUKsZfzNFwbjXCdRnkVGTM5Un5Cal5hAWlt5K0JOlQQ4tJTuki3dAcBrafSb2%2BWIjphzSfiMd9q4HsUNlK2cm8GFKR5KsZzRv8bcRd4KcTvtpSMj8F6hfUr27TW4PYAGhYQHF2WWW1VzMxazhGm1qkUubmZaZmZd2qzBYYdWy0pwMhdiA4sJKUg2BVYXEYl0Uw575oV14%2BimGOEnM7CU3NT2Hsq8B06ZnqfM0p55zEz0z%2BZphGh0JS42QlenZK02Ukm4i0L4HcZgJCcqcCq6MANn22zOxAtc3a3gOAEszAX5CoqeLvq%2BCr44%2BiMvwYzzaUKf4esMLeLaUurazBcQlSgLFQSZclNzva5iq5wZ1EhDslkDhmWmW0ktqXjtx5tLgFkKUgy41i%2B5SSL27IDgbL7Cb%2BNccULBSKnKU1zEFSl6Y3OTeroJZTqwgOOaQToBIJsDtFnq1NeplWm6c88y85KzDsup1lWptZQooKkntSSkkHuj6D0DhBzRwtWqXiShZYYDkqtRpxufk5lOJ3SETCFBSVBBaIsFC%2Bk7W2ihM8FmMKnUJ6p1TJfBMxMz80ubcW3jJ9pIWslS9KQzYAkk27Oy0B89PF3IudIaWkuOHkwkuH0R3wvgvxO0lIVkTgZSgnSCrGb5BA5XBa5gXF4gngoxWG3rZIYRaW6nQNONpjSAedwGfywGHcA8uvxlx9OwXiWWB84Eg8bfHaPXxwI0ZlUVJSRahDn2%2B%2FrjfGR2QuM8usRS03WaFhjDlEp6Xn2ZGlVB2oTE5NrQGw4864lOlKEXAAG%2BoxozjmfaczSpUuhd1y9DbC09xU8tQ%2BS0BzpI%2F2wk%2F%2FEtfzxHcCggBxBOrUFJsFXJ80cQSf9sJT%2FxLP%2BkTHc7jYeddDLSgdQ1WtpJ7xGWx%2BUn0KW%2F5kR55eIKFgEMgi2m3yWiCVNlPQhFlNqsTfnftj2LZSHShxCkqZcsTfnccxHn0I6f7H1v9%2B3tjbc%2BaXpl2Q6ndRNje4PKKFRkZd4lEw2lQV8ICxB7xHqlNAUo9Gobbq7xHrcZbcZ6RDm4HVKu%2FzxOas05NbV2nzEopJA6hN0m1wfmixPoUgddA1KFtjGyp%2BVL5KHFpKUjrpPfGHV2huSi0Kl29aFG5R3Ht9UM1qZYbMNhBWtG9xfzDvi2OMMha0uGyT1hYi0XeYIuoC6Ekk2KeUWacZUpajbZQIJtt6ooyvBiJq0g4u1ve%2BXfGLNhKQnUrTvGTVZavYl1txfkNCx7rEbfLGNNjpLN26lx%2FqitW1monU1LiF0JrE%2BlSUkJn2lG%2FphXwE4lmmgNI6dSdyb%2Bj4o8uKyRWaue6Ybj04nKfbVMBPLptviEak7WeNjYWDKjTaMpupzFCFVUwyUKlZmfmGmXLjmS0tKgR2WMY3XsWtpeU5IM1ZpCyVFhdXW623y2SVJ1W9JvHvpiiKa6vttaMRrqQFnTtEJToxWVOlT7E7oI8lE8Qb999PyRKvEa3gpJNRQFcgJ0m3xpixNhSl2j2NpSBvAXFdeVp066iTa288rn9zEZfEBlz0jqaoux5IqRAI7iCneLQ%2Bq55RBDkBkuNsQVWg1FmWotUmFS8zKNvFEwUPadYvYK0gxa5sF%2Fr81KTqVFHG6iubpiuw05o%2BvcfkEevoxf%2BCPxQHiYYKjaO7PB0cP8AKVvEcxnrjBltrD%2BENaacqYT709PhOpb5vsUMIBUTy1Ed0cn5U5bV%2FNLHNHwNhdjpKnV5gSzF%2BSL7rcV%2B5QgKUfRHfXGTjzD3Dtkfh7hfy2cCHZ6QQifWk2WKdclSln9UmXQVHt0JPfAWfDlKw14QniGxhO4tr1Zp%2BC8FUxlmgylPcQh%2BZQ6%2BWy%2BpSwQm6h0p23ukdkXrg8xXRsLY9zH4G8cVEYioTM9U2cNuzCAjx9gXTPyWnkFLQemSBsFpXp7I114LWpE5%2BYjpTiz0U5hR1zR9sWZppRPq1RzRizHtdl836lmHh2oGQrUpiV6sU%2BbbuOhmETK1oV5wRsodoJEBS4iMmalkbmlW8t59Tz7EgpL9LnHB%2Bjqc71pZ8HtOnqK7lIUI1O4g%2BsR9QeJfDdH4x%2BFnD%2FERgOlBWJ8NSj01MyTB1OdCk%2FnnT7DcqZWOnbHam9ucfMmfYCVFTZulW4I7QeRgLWsEHlE7aAecRUgg79kTtgCA6D4P8scl8zsez9CzhxcaWymjzr0hIdE6lU8tMs4ouNPINg6xpDgbO7guADyjS2KKZRKViCep2GMRt4ho7DxTI1ZEq5LCda7HCy4AtsntSrtEb54GcrMv85c3JnB%2BZlCNWozOHqjPpYEw4yUzDTWptYWgggje3ZfmDGgXEsDYz6HPOpQv6%2FPAeRtsHnG9OGDOGiZL1jFSMTYPqeI6VjbDEzhmZlqVOJl5xDbrgUtTZUCD1QRtuCQReNMNplEMrddmGSEC%2BkKuo%2BYAc47smZygcC2BMMSOEcHyOKM7MaUxNYm5%2BekjNJoUotIKEtNJBOrfblyJJgLXgPihy%2FyToNDoklkpmpSKBhWtu4mws5PVREup6fdYLbrE%2BvQlD8sSdSdN1AbHlvxtjGpv17E9Tr81LNMP1ObenXW2U6UJW64pagkdguo2EdV07j24mKdOOO5iNy%2BOsPTYV7J4cruG9MrMs%2FDQlzo%2FezpJsVBSb8xGJ8W%2BTeXmF2MGZ25MuOM5a5pSK56mSj5N6POIsXZPUSTpuTpBPV0qTcgAwHMa2rHnGw8r8C5RYppM1NZg58SWA51qZ6FmSmqBOTomGSkHpUuMApG90lJsRbziMILUur%2B62Pux88dC8H2UOXGbS81ZTHdPVUPa5geYrFJXLzi2TLzqNXvgKT1rADZVxvuIDnCry0nJVSbk6dU2KjKsPuNMzjCFobmWwohLqUrAUAoWVZQBF7HlHlAFuUVltxT0iAyLLwIVjfDqF%2BSqtU4H8KaMdA%2BEcVfi5xiD8FuUT8Us3Gg8s0g5gYXTqAvXqaLq5fopuN8eEdVfi4xmfPLj4pduA5eXEADExiKQIDpHhzyNyUzPyqzIxNj7NhjDdaw5Tm5iWZXKvk00dOhKZpwIBEyy5ctlKLqRqCiI55nJMSk29LJmGphLbikpdZuUOJB2Wm%2B9iLEA7i%2B8dFcOuUuAcd5GZ3Y3xXJTa61gOjS85RJqXnFMeLrcJC9QGywbJuFbWB7458WlB%2FTm%2FuhAedtq8dF5C5t5aYZypxxkpmlgjGVdpuN6nT6kHMLzDLU20ZZNkpAdve6t7gHujSWGcPTWJq9S8N0paHJ%2BszjMhKoG93HVhIPoF7nzCO4cw8x8McD003ktkThukVDHkpLNqxTjCoSJnH0zBAPRNJtZISDfcgeYmAsp4v8ABmDMBjCMtl3mDKVqnYRncAUeVq8y23SZumTDhUibm5bbVNoSSklKSFG9jY7cSz7HRuLbR5KfJT5hyjsTDPHbXcTzzWDuK6h4ezIy%2FrT6JOpOTVJErP05txQT07LqQB1L3IGldh1VXEak4qsipLIHNicwZJVn2Roc3Ls1WgTzyx0j1PfBLYWdtS02KSq3WsDzMBoco80bUwvldlLiHBTVdqXEfhfDtdcYcW5QqpSZ7pWHklQS2p5tBQoKASQpNxZQjXKpdsrv4w1p%2FfiOgsrMoMAYy4Qs2M1qvLTRxNhGuSMlSJlmaUhtDbiWytC2%2FJWFEqG%2B4vsdoDmlzpP0zqq%2BFvfftF%2B2IRUcBEU4CSx7oWMTwsYAOcVUiJQBeKqUwFVrsj1ge9iPM2I9drIEBlFNVemNj9yYyHK1WnFE04SQEUypKURzAEo5GPUgaqegfuTGQ5U%2F8YKu5f7HQaqv%2FwBK5AawwTOTkpUJZclNOS7im0o1oNjYpsY2nwxj%2FwDVRl6PtccUoeTb%2B7Go1NhI6J%2BVXa%2BkINu%2BNucMn%2FxU5f8A%2FwC%2B9KP%2FAK1qA%2FQdCEIBCEIBCEIBCEIBCEID8%2F8Ax2rJ4ncyUEjq4ineX7%2BOe1eU2vziN%2FcchB4nczSP2yz4Pp6SNAH4HqgNgUfyf4KY9hjw0tSm0rUlou6EpJQOagFbgee3LzxtvNvKCn4Po1MzFy8xCrFmAK4ENydXaYKXWJogBUpMtC%2FRvBVwB29kBrDUb2iYHvjNsX5I5sYFqtDw9iXAlSZq%2BJVBukSTOl5c29cAsp0EgOJuCpJsUjc8jGRz%2BTeG6dmdgfJpvGLdcxTVagzJYrTT7KkKS6p1J8TaeH2Z5KAvpFDqg7CA2Tw4cIysxqFL5iZkzc1TMNzY6SmyDBDczUGwd3VrIPRNEiwsNStyLDeN4v4w4PsnZaoYPYlsOyKKpL%2BI1RlhCphc21cHQ%2Bu5K033sY8XHNmdN5V5Zy2H8IuGQeqbhp8spnq%2BLyzaQLI7urZIj51UyanZ9pazPltSlfBbSST3kne8B3xX%2BGnILPCgP13JSq0%2BkVJIu0ZF7XKLXbZDrRJLd%2B8cu6OKsTYcrOEMQVHDGIZFySqdKmFS0ywsbpUO0d4IsQe0GLtkxmjiHKTNCg1iQqC1y01UGJKpsaAlMxLurCCDbYlJUCDa%2B3njpPwhuEZKXreDMwpRhttyuyszTZpSRYuuS9lIUrzhKikeYCA4%2Bub2vGyspM9sVZPJmpKmycrVaPPO%2BMPyE0pSdDtrFxpad0KIABG4NhGt4Rp3%2FD7rilhVdr5RFdE7YleztKrKrhUTlLqdvjtqSEhPuby9u3833%2FGiH1eNX19bLSTKf3M4L%2FKmOWIR53iJgHkPWq7TZ7uvMRrrnq3OplceVa%2FS8spH%2BFOA%2FwBGK6ePCq6d8sZMnvE2n6McpRPDiJgPJYetVvR3dePHnq3Oqk8dtUAF8spEW7PGh9GIHjtqoPUyykwL9k0mx%2FkxytFaSk5upT8pS6fLOTE3PTDcrLMti6nXXFBKEjzlRAiJ0EwDlu%2FrVbzu68ePPVudTfV41T%2Fqzl%2FwxP0YlPHhVb9bLCXI%2FwDGJ%2BjFkHBRitqpuYLdzNwecdtyJqCsNIeWp8NA28sC3Pa9rEkdm8c9z0rMSUzMSE02W35V1bDqDzStKilQ9RBhxF0f%2Brx0qu0d3Xjx56tzqAcedU%2F6tpdPom0H8aIh9XlVEEacuGV2F7rmkAk%2BgItaOVtB74heJjQXAPIetV2ju68ePPVudWfV5VLSLZasBXaTOJ%2FFoiRHHpWwbKy4lj%2FjSfoRyuD3xG474idBcAj6D1q%2B0t3defHnqdWnjyrJG2WsoPTNI%2BhEw48anbrZbsg9wmkfQjlCFx3xMaC4B9X9avtK933jx56nVSePOqBV15bs2tyE2nn9zyic8etS19XLZnT55tF%2F5kcpQHVSXe6HEXAPq%2FrV9pMX%2B8%2BPPVudX%2FV51T%2Fq1b%2FDUfQiKOPOrAdbLVgHuE4m3yoi2VThQy4w5WKLhHFXEhSKTiWuybE1KU%2Bapy0dIHkjotJvyUq4FyCY0tiTKzGmHMy6plM7R5moYjpT6mVS9PZU90yQkKDqAAeoUkG%2FqhGguAclh61faJv945a56tzfv1eNVP8A8tZb1zifoRD6vCqj%2FwCWksf8cR9COa8RYMxfg6ZakcYYYqlDmnwFNtz8uprWD2pJFleqN%2FYo4XsnMAVhvDePuJ2l0SrKlGJ12UfpDpUll0XQpNibgi%2Fn25RHEXAvIetVvV7tvE%2FPnq3Lorj0rCwUqy0l7Hn%2BbUn%2BhEiePGqjyss5M%2F48PoRzlRsJ1rF2JHsNYGp83X5krmlyaJZk9JMyzOol4I5pBbTrIO4BtFjBujpBqKYvOguA5fIetX2kxfrx489W51aePGpkp05XydvhEzgP9CJ1ceFRLdkZYSaV95nRb%2BbGPYZ4RpBw4foGPc68N0DGGLJVU5SaCygzay2E30LcQrT0ljulPnAvYxi%2BDuF3GmKMz8WZcVGsU6jt4ER0tfqzwUuXZQU6mwgc1KWghQG1hcnlEcRsBnV8R61W8m%2F3iPnz1bmyBx4VEc8r5Q%2BifH0Yl%2Br1qF7e5XKfxgPoxhNd4badTKHgzH%2BFcx5LFGBMUV2VoM3XJWTU2aa6%2B70SHFtE3KNfVO4sbX5iPRiPhXm6DxLULIFrE3TStalE1JNZXJ6VNSqW3FPqLV%2BaFN6ee5UIjiHgMa%2FiPWq3o7vvHjz1bmXfV5VH%2Fqslf4xP0Imc48qjazWWMtfvVPC382MKxXwvv4Y4gcE5Mt4jdmpHGaGphqpmV0uMMALMwot3sS30fK%2B%2Boco1znHgmnZa5mV7ANKrq6wzQ5hMqucUyGit3o0qWnSCQNJVp59kRxGwHyHrVb093Xjx56tzfQ49KsE2VljJ6u8Tu38yIDj5qvJWWMl%2BGD6EcmknXzgom%2FOJ4i4D5D1qt53dePHnq3Oszx81XV1MspBKfPO7%2FIiIL4%2Fat8DLKWHpqA%2BhHJeo98CrbnEcRcB8h61XaO7rx489W51qnj%2Bq1iDlnLA22Pj4O%2F3EE8flX6S6stZMoty8bF%2F5kcjEm8RBNocRMA8h61faO7rx489W51y5x%2BVMoHRZXygV265wW%2BRMS%2FV%2BVf4GWUnfzz1h%2FNjkm5i5YfolSxJWqfh2jSvjNSq00zIybOoJDj7qglCSTyFzuewRPEXAfIetV2ju68ePPVudTtcfeIgLu5aU7%2BDPfOiIDj%2BroXvlpJFJN%2F0eAQO7yIsx4KHn8T1TLekZ6YTqWP6RTfZGYw03LTCFpQQkgdMRosdSbH92m9rxzMT19BQppSVFLiDzQpJKVJ%2BMGIjQfAY%2Bg9artHd148eerc60HH7WSbjLGVA7lVAG%2FwASNoj9XzWFc8rJE%2F5SH5URyVrHcqHSDzxfiTgPkPWq3p7vvHjz1bnW31fFU039y2Tv3ePj6ESfV%2BVYK%2F5L5DT%2FAOO3%2FmRyZ0g88QKxfkqHEfAZ%2Bg9arerN%2BvGf589W51dMcfVSW4Fs5YS6VjsXPix9FkRiOZfGVjbHmGJ3CtJw9JYcl6myqWnJpmYU7MrZVspts2AbuNirc2Jjn1RiF79sZ7PQ%2FBbG0ptYsIzp2ZzM7PNM5Im920xlVVOUn7zqpT5PmHdF%2BwbjTEGAsRSWLcLTvitTkFHQojUhxs7LacTyU2sbEeg8xFgVEI9BbWFneLObK1piaZjKYnZMMFNU0znDq6U49sQtS6EPZayXT2GtbVSUlBPbZJSbD1x6jx%2BV5SrqyzlCP%2FHf7MclJMTR5aNBcAzzi7xH%2B6rtNmL9eI%2BfPVudZnj7rJP%2FACYSlv8Axw%2FIiJXOPqsHZrLOUT%2B%2Bn%2F8AYjk6EOI2A%2BQ9artJ7vvHjz1bnWSuPirnUU5ZyKexP5vJ27%2FIiDfHzVwqyss5QDvTPf7EcoDlGWZXZc4lzaxpKYCwmiV9kJpp2aU5NzAZZYYaTrddWs8glIvDiNgPkPWq3nd948eerc6GRx9YhSon3OZPT2Wn1A%2FzYnVx%2FV47Jy5lEnvVP%2FMi8agz2yNn8hZ%2BhyNTxPI1%2FwBnpFc6wuRYWjSEuBsIsrdRUSNJHMGM9Z4LMROVCVwdM5nYUlcwJ%2Bjity2EHulTNrZIPVLltAUCFJO%2FNJ7BeL8RsBj9njpVb1e7bfx56tzIT4QCvEXOWsoVdxqG38yJUcfVeH2TLqSV%2B9nrfjRHLE9KTNPmX5GelXJaZlXVsPMuCym3EKKVoI7wQRHnuIjiLgFW27%2BtV2ju238eerc6uPH7W%2BzLWX%2FjAf1cR%2Br8rX%2FVrL%2FxgPoRydrhriOIuARssPWr7R3bb%2BPPVudY%2FV%2BVrsy1l%2F4wH0ImVx91xX2PLZlP76fB%2FEiOTAveKoXDiNgP1f1q%2B0d23jkrnq3OrHOPXEIPUy8kyO8Txv6PIgOPivX%2FAOTlr8P%2FANmOU9cNd4mNBsA%2Br%2BtVvO7bz489W51enj5xB25dyx7vzwI%2FoQPHxiNPWGXEofTUyP6EYDl7kFget5QSucuY%2BcUpgylTlXmaOwH5BTqOlaNgCsHyldYgAckneLBnfkkvKQ4ZrFJxdJ4rwtjKTVNUSsyTRSJlaSNbWi5uqyklJTfUL8iLRSdBMA8h61XaO7bx489W5t%2F6vzEOnfLmVv8A%2BZH6MSnj7xD%2FANXEp%2FGR%2BjHPlcyozMwvRG8S4ly7xHS6S6hLgnJuQW22Eq8kqJHVv57Rs7BHD7gCsZMUPOHMHOaWwbI12pTlOl0v08ut9IwpSQjUDcrUEKVa1rCJjQfAY2Xf1qt53bePHnq3M2c4%2FK6kNhnLZhRsekK6kQL9lrJgjj6rejr5ctavNUtv5kc8ZmYdwfhTFRo2X2PWsa0oSzC%2FZNmVUwC%2Bu%2BpkJJ3KeqLjYkxbcWYVxJgTEc3hDGNGmKVWZEIMzJTCdLjWtAWm486VA%2BuJnQbAZ%2Bg9areib7eI%2BfPVudLDj7xIk3Tl5LhPcKkb%2FwAyJ%2Fq%2FcQrQUqy8Zv2E1I7fyI1hlVkZQMYZf1HNjH2a1FwNheQmlSCFzSemmJh1JSkqDQOpKNSgkGxJN9rC8XHMnhexjgrMTBmAMPVSQxH7oKVKoU80OibXpAUvpOekJbIcKhcFPLfaEaD4DH0HrVdpMX28T872bmwG%2BPrESR%2FyeS485qZ%2FFoiK%2BPivHTpy9aT9sPZNR%2BI6Yslc4P5F2SxlSsvM3qRinGeBJTxqsYfTKLYWkdHr0oWfhEAgXFrixsTaMLzLyFk8G5HYBzqwpiSZxAxjZUsyqWclAz4s9MNqLTYUCb%2B%2BoW2Se0Xi8aEYF5D1qt53bePG9m5s76vyvczl0j0mqkD5ERBPH5Wv0zLxs%2Bipq%2BjGI8R%2FCo5kJlzTsdy%2BKJiurVUWqdVZYynRIlXHGVKSUKBOodKlTe%2FeD5ox3iEyHp%2BRftRkTil2qVXEVOdqM3LGW6NEohHRgBJuSq6nCne3kkxjq0EwDb8R61W87uvHJXPVubNXx%2BV3VZGW7Wm%2FM1ZV7fcRMOPusaFasu0avg2qZt%2FNjlEpA7YlinETAJ%2Bg9artHd158pPVudWL4%2BK0Ui2XaCrt%2FPVQH82CuPmtXARlui1hcmrK9fwY5RJtBDm8TGgmAeQ9artJm%2B3nyk9W51cjj1rnNeXSfVVFfRiJ4%2Bq6Fq05dthPwb1RRPr6scp9JEIvxGwD6v61W9Tuy8ROfDnq3Orjx%2FYhKrJy6YCe9VUVf%2BbEyuPmt8xl20fRVT9COT4z%2FJvJrE%2Bd2IpugYXXJSqabK%2BP1Cdnnw0zKy%2BsICjfdRKiAEgXieI2AfV%2FWq7S0X68%2BPPVub3HH1iHQEt4AaRpI8upkgj7iIp4%2FK8FXcy7SU2%2BDUt%2FlRGlc4slK9lHj2nZbOz0tXqlUJWVmJUyLax0q5hxTaGQlW%2BoKTbu3jPaxwiqoi38Mz2eOAmMeSMi3OzWF5qc8XWnWm4aD6yEldiLbcyL2BBikaDYDnqsPWq7R3defHnq3MoPH%2FXuRy1T%2FGn%2BzEx4%2BaspR05daQRtqqm9%2FueUcm7tuLbWFJWlRSoHmCNiIli1WguA8th61W9WL7efKT1bnWX1fNbH%2FwAu2z%2FlM%2FQiP1ftcH%2Fy4Qf8pn6EcmA2iYKHeYidBsBq%2Bg9arev3defHnq3OsHOPqtpQHF5coAPYKqdXxaYtlc48MZT1MelsPYLkqbPOJUlubmZozCWCRssN2AUodgJtHMKzqMQue%2BLUaDYBZ1RX3PE5eGqqff1K1X68TE0zXOv0e6HoqE3NVKefnp6bdmpiZdW8%2B86bqdcUSVKJ7ySTEJKZmpGbZm5KZclpiXcS8w82qy23EkKSoHvBAMeeJgoiPVVUUVU8CY1bMmvE5TnDqKicdWKZSVQ3iHAUnUJ1P2WalJxTAe23UUWIBJuTY23i5Hj8rR3GWjY%2Fymb%2FAMyOTekMOkMeVr0GwCrX3PEZ%2BCao9ktju28x8%2BXWP1f1ettlq1%2FGZ%2BhEfq%2Fa3o3y0aKrdtTJF%2FuI5L1mI6zE8SMBpj5D1qu0nu68%2BPPVudZjj%2BrhV1ssZfT5qhv%2FADIgrj8rWrq5ZNW%2F8xt%2FQjk3WY9VJkpysVWSotOZ6adqUy1JyreoDW84sIQm55XUQPXFZ0HwCdth61XaO7rz489W51Ynj7rIBtlq3e2355DY%2FcQT4QCvA75bM281T%2F2I1zm5wq4wybwAxjbFGKaJNPqqjVKmKdT1qeDDikr1EveSrSpBSbdsejCPDG1UMEYXxrmFmvQMCt44mxK4dk5%2BWdfdngogNqujySsnYHkLEncRXiNgH1f1qu0nu28xtr9m5n54%2FwCuKO%2BWbBHcakPoRBfH9WvgZZsj01AfQjn3NjLHEeTmPapl7ioMmoU5LTyH5dWpqZl3U6m3UnnYi4sdwQRGIXHfFo0IwLksPWq3o7tt%2FGnq3OrleEBrgFvc1YJ7%2FZIfQiX64BX%2FAPq1l%2F4xH0Y5MV5cIniPgXkPWq3ndtv409W51oOP6vnnlzLDe29TP0Iivj%2Brp02y5lT9t%2BeJH9COSge2JtcOI%2BBeQ9ared23jkrnmjc62%2BuA1UNn%2Fg2Z19n547fzIlT4QGu%2F9W0uP3tT3%2BVEcmBd%2ByJVC5hxIwLyHrVb0923jlrnq3OuV%2BEAxAbdBls2Nt%2BkqYN%2FiRFVHH%2FWutry4b%2Fc2qX4%2BrGpsjMj6BmjhnGuLMV5gN4TpeCkya5maclOmR0T4US4rcaUp0gdvlRXzc4f6ZgbL6SzXy%2BzOpmO8HvVA0eenZVHRLkZzfSCL2UkkaewgkXFiDEcScC8h61W9WL5b%2BNPVubP%2BuAYjF%2F%2BDmXPd%2BeZH9CKQ8IBijV1suZYC3ZVDz%2B4jnxnKbNCYwycaS2WmKXqElBdVPoprhbSgblR2vptve1ozPJLJHDGZ2CcX5h4zzMawhQcITEpLzE2Zbp0e%2FpJC1m%2FVF9KRzuTDiPgc%2FQetVvJvtv409W5tH6vzEahvlwj%2BNdv5kTfV%2FYk%2FwCrlH8bK%2BjGk83cE5VYNNHVlrnDL46E4l81FDEmpjxEIt0aio7ELuRbmLeeMRrmFcR4ZapT%2BIsPztParsgiqUxx9uyZuUUSEvNnkU3B847RuIcRsC5bD1qt6Yvtv409W50seP8AxOT1cuGCPPVV%2FRionj8r1vfMtW794q6voRpjJfJp7N%2BYrE1M4zo2E6Bh1pDtTqlScHVKgpQbabuFOK0oUo22AHnjIc2%2BHVGBcB4fzTwDjqTxzhPEc%2BzTpWak5dTbwdeKks9Q%2BUFuIUjbcKABG94cR8Cj6D1q%2B0nu238b2bmxRx%2B4gTsMu2B6Kor6MTL4%2Fa7oT0eXCdXwr1M29XUvHglOCuT9nqflzV86aDTsxqnSjVpfDrko4pPRAG6VOja9wQbcglRsQIw1HD0FcPOJs4pqvvSuIcGVWapVcw6phKkybstMpafu8DvZC0uAgWIMTxHwGdth61XaR3deI2Vezcz9HH5X%2Fh5dI9VVV9CJzx%2BV6%2Br3PEX7%2FZVV%2FwCbGLzfCe%2FLcNXu6qxLNCrN0VvED1G8VBbTJl4BQC76tYaIc5W5jzxiWI8jZDDvDhhnPGfxQ6aliicaYlKR4sNBaWp33zpb9iGwq1vhCK8SMB8h61XaO7LxPz%2BqNzaqvCBVw88vBf8A81I%2FoxSHH%2FX%2BRy8Sf8rKH9GOUIk5Q4j4F5D1q%2B0juu3n53VG51kePzEShYZdhJ7zVln%2BjEyOPqufDy7Xy7Kurn9zHJ3SQhxIwLyPrV9o7rt%2FHnq3OsU8feICbDLgW89ZXf8AmxUXx9VpAsnLtSV%2F%2BcKKf5scmXA7Yj0htfsiY0GwGdtjPSr7RF8t5%2Bd1RudX%2FV%2FV2%2F8Ayc3%2FAMsK%2BhEfq%2FK9r%2F5OFaf%2FADff%2BZHKPV037YzDKbKvFGc%2BNJXAeD5dpU%2B%2BlUw688rS1KyyCOkdWR2C425kkCE6CYB5D1q%2B0mb7eJ%2Bf1Rub%2B%2Br%2FAMQ%2FpeXnq9lv9iKieP8AxF8LLsH%2FACp%2FsRr7H3C%2B5hjAVczDwJmfh7HlOwnPKkcRN0rUhynLSQFGyvK0kjUOdjcX3i15B8N2LM%2FXKw7Sq1LUOmUlbMuKjNy63Wn5pZuWEhO90o6xPZsO2JjQfAo%2Bg9areim%2FXiPn%2Bzc2qOP6vg3OXNh3Cq3%2FABoiRfhBMQAe95ai97daqA7d%2Fkc45WnGVyk0%2FKLUFKl33WFFJ2JQspJHrEeZSiDEcScD8h61W8m%2B3ifnex1r9cErdlD3OF3PI%2Byg2%2FkbxKfCCVwW6PLxPcdVSB%2FoRyVEpA74mNB8Bj6D1qu0mL5ePG6o3OvFeEBnylH%2FAAZm%2B%2BvTUE%2FJdEW%2Brcf%2BI3JdxNMy7ZbmVCzTkxUNSEecpSkFXZ298cqRBW9iYtToTgVE8L4j1qt53beeWvqjcvGKMT17GVcncT4mqCp2qVF0vTLx8m%2FYlA%2BChI2AizRN0%2FwLRTWY9RRRTZ0xTTGUQ1dqa%2FnjoPKbi7qmAsLSeEcX4dmsRNUpvoKdPSswhqZRLjyWXteywjcJUN7bHleOeLnvi6URouPOKDIcCGypV%2BQFx88c3F8DuGO2UWN%2Bs%2BFETnG2JifNMZSzWNvaWEzNnOWbrR%2Fjrwg%2B0UTOXGI7KNxpnpW9%2FTEMNcYOH8RYoouG5XAFbYXWKixTkzD9Ql9DJdWEpUQBvYnl2xzQiWlinWZVkpV%2B4vYxQrqGJWnU56RU5L1FqeXM%2BMIAToKQlTSk23ulQv8AFHlbz8HOCzZVRY0TFWU5TNVWqeSdutvWeKW9MxFVWr7HXvF1lXiLM%2FAlN9qzKpuoYeqSpzxBOy5tlbRbcDd9taTZWntF7Rw3M5d4zkH1S09hOuS7qSQUuU9wbjn2R15hnjRwrOUplWNqDWGKyEJTNinspelnnAAFOpKiCnUbq09hJi9fVnZW6iBRMVEWvcSiOfd5ceRwW86WaN3ebjTcuHTEzl9u3KYziYz1x6fsjfvE3C91%2FG1V5S4kVgfFKbg4aq5PcJJy%2FwCKKC8D4sSd8L1oX5fmB3f%2BTHcY42cpUlKVUfEqnD2CTbv8i49SON%2FJ1sWmcNYnK%2FtvFwL%2FAMuO1TpTpXl%2Bro553Naq74d5Sepwd7TcVHlhisn0SLp%2Foxt%2FhdyXx3Vs26Diebw7U6ZScNTaarNTk5LLZbUW0q0NIKralqUoWA88dLJ44Mml7jC%2BJrHlaWSfxLinMcbWT6mtSaFixxSfJZ8USL%2FwiuwjXxHG9KsRudpdJuHB4cTTnGc5ROqeSI2L3anD7tbU20VzOWvLz%2FYu2dXEBJ5OVOjSFRolSqblXlnZpKpWZQ30SULCLKCt9ydrd0a5TxyUJHk4FxGf8fZEaJzjzRqOb2NH8VT1PFPl0IEnT5IL1GXlUklIUobFaiVKURtc%2BaMOp0qhyeaR5STcKjawn4M8K7ispxKyztsvwsqpjXty1TlqjU17fFLeq0mbOqYh1Snjjw6Qn%2BwLEYJ5%2Fm5iwiZ3jow0yFOe59iZ3T8BE8xuPNHOhkJXbSyk6ee0W6syjLEuXG0pTpUlJ285jpT8G%2Bj2WUWM9KrepTit6pnPhz1bndOcdEqmeHD0%2FTqASZqvUyUrElLPvDruBSH22So7BRGpIPK%2Fpj561PAOL6DOu0%2Br4VrEjMsq0ONPyTiVJPdsLfEY6ayP4qKRgnBkrgjMCl1Kbbo4LVMnpJKXVGWvdLLqFEeQSoJUDyIuNo2T9WZk2U9elYr0p2A9j0n4hr5R5LB6dJdEK7a5Xe6fG2U1TMTH2RnExntiI1TGeeboXi0uV94NpXVlOTgtVBqwUdVNnk%2BmWWPyRFWG66kajTJ8Dv8AFl%2FNHd31aWRyRpeoWI0ACyQaa3y%2B62j2jjVyJQgdNQMTrv8A93Db%2BVHf416TRH6tnnnstTubD9vxs80b3AqMM4gdUEtUapuk8giTcP4hGV5b5L4%2Fx%2Fium0ak4bqjSFzTK5mcmJRxqXlmA4krcWtQAsE325nsjtJnjWyGVcsULE6UggFQkR2%2BhURXxrZJEKSJLE6Ufu5EkX77ao1r1pLpXb2NVnZ4fwZmMs%2Fwpy%2Bzgx7V7Oxw6mqKqbSZy%2Frws%2BzbzWOVeEZnG1QZqE%2FKy03LySGJWZDbq%2BkVoSRqNtgLkRpQcdGENR6TBOKFW%2BEH2d%2FjMax4jOIqUziZp%2BGcM0p%2Bn4dp7pm1LmgA%2FOzNrBZQCQhCRfSOZJJNo0pJsS65trX10qV1kxq6NfBpcrTD6a8Ysp%2BNmZnLOYmI5InLl5ftXveM2vxmdhVq%2Frwuuvq5sIKNhgnFSR3iYlz%2BWJlcdeE2QVNYHxY6oC1%2FG5dJt6dUczexkn8CVb%2B5jyVGRl2pZwplUJNuaU7x3%2F8AxlgHJZz0qt7V78Xyfnz1bnf9Qmvd3yDmWpCYck2ccYedEumbdK%2FF1PJIQHSPtVpAJEfNzEOXONsJVN2jYkwnVadOy56N1DsqspJGxKFgaVpPMKBsQRHSnDzxPUTLnDhwNmBJT6qbJKW7SahIth1xtC1a1y7rd90hRUUKHK5BHIxtw8ZuRC0lDrdfcSBYBVJURbzXVtHk8GsNINC7xeLtdrpNrZVVTNOWeWXJOcROuYyzifBycvQt7S6X6imq1ryqy%2F8AuHz7VS55vrOSUym3eyofkiQ02cPXMrM6fMyr5o%2BgKuMTh2VvMSNaTb4S6OCBHpa4xOHDowHqfWy2rkoUlIB9UeinS7SLL9WVZ%2Bmew0Zu9xj6aeaN756Kps4pPVlpv7wr5ouFEy%2FxfiyeRRcP4bqs%2FOzY6NlpuVXYqOwuoiyR3k7CPoB9WBw0E6WJSr37B7Djf0WiZjjK4fNOll2vsdIOt%2Bda0i3cbGMVppVpPXRMU4blPhzqnqiiPbC1F3uGec2sz9kR72W1vFD%2BSeUMrUKqqbnEYUpEhIPsyLw1OOICGiGySAQFE%2BoG0am%2BrlwJr3wti5Q%2B2s18vWjXvEhxLUbNOgS2BsDSdQlaMJxE5UJmcaDS5xTYPQtpRclKEm6iTuo27BHOvmjm6NfB3d73c5vGN2cxa1VTMa8py1bYjlmc59DNe8XtYtZiwr1Oz08cWXykArw1i1Kr3I0tc%2Fu4lRxx5fk6nMLYwBTyIUyb%2FwAvaOZhRqclpAcl2gQkE7eYR5n6bT0oV0cs35J%2BDHe%2F8Z6P%2BTnpSw04zfKdtT6IZVZq07NPBjeMaCqqyknNPuywROqs%2B0plely4ST3x818wsrMZ5f4pqtEr1An2wxOPFmaRLqUxNNKcUUPNrAspKgQY3Pw08RlJyjlJ7CmNpWcdoM7M%2ByErOSTXSvSMyoBLgUj4bSwEk23BF%2B0xv1PGLw%2FEaXJqsKSk7J9iHQn025R5TDrljehWJ3izuF0m1sap1ZZzqiZmnXETriJynOM9Wfp27a3uuIWVPx9eUx1eGMnzzcpVQaQlbklNJSu%2BlRYUAq3OxtvFJVNqABUJKbI8zKj%2BSPocOLLhlbbQhZm0NtklCV0ZVkkm5sLbb7x6mOLzhpSCVPz6QRpOmkKG3dyj0MaW6RTtwyrnq7DU7lw%2BPpp5o3vnGKXU1%2BRTptX71lR%2FJFZrC9fmnky8rQqq%2B%2BshIaalHFKJ7rWj6ODi44YwSG%2FH1FIubUlX0YmRxjcOW62KjVmCOWmlupJ%2BIRSvS3SX5uGzz1z%2FAMFoutw5LWZ%2ByN6vk1TcSZT8OdGlsUSM6xM4doszUpqnsrPTIbup3ogLga9O5HeYwdHHNlyE6k0HGHWANlS6bjzHrmMfz84uMJ4swPPYDyvl6i4a0gy9RqM4wqXCJU21ttJJ1KUuwBVsAL98coRztHNAoxaLa%2FaQWcxaWlczERq1cucenZnryZL3i1VNcU3adURk7RPHPl0Rc4fxSfMZRv6UaVz94j1ZvU%2BVwtQ6HOUuhSkyJxzxtaS9OPpBCFEJ2SlIJsnc3N40rEFR7TDtCMGwm8U3qws5mqnZnOeU%2BFz7e%2F3i3p4NdWpJpT2Q0mIad4AKHbHrWkiEmJgLwAvE0AiSJ4kgJ4gQTBO8Rse6AhpgExGEAN%2B6IggG5VaAuTziBA03tAZDS8eY1ouHqnhOhY1rtKo1ZWh2ekZCcUy0%2B6kWDhtuFWABIIvYXvYRvfNrjTxJmnkvh7LNNOrVJrUi9JKrlXRUyBUESjZS30ZQQtKlq0LXq7U9t40BRJdl%2BVcU6lCj0gA83m9cXM0%2BXTzYSPQDAebFmMsW46qaK1jPEtSrk%2BzKtSLMzPPdI43Lt30Ng2Gw1He1zfe8Y%2BecXKrNBmotyjKEXmOjQmw5KWoJv8t%2FRG%2B18EWOktJdRm3lK8pRsUoxKkaT6SneA5yhHRI4JcdFSkKzXynC0mykjFCLj5IlHBFj8atWaGVJ0nSrTitGx7t0wGqsnEJdzgwA0q1lYqpg35fohB%2FJGVcV9zxO5q6uftpm%2FwASY2hl9wgYxwxmBhXEtRzGyvfl6VW5KoPtMYlQpx1pp1K1BIsOtYG2%2B5jUvE5U5CtcR%2BZ1Xpc03MSk3iabWy80oKQ4kWTdJGxFwdxAatiSKi%2FNDRt1tMB53BflFum5Rt9CkL%2BF1VevaLsW4oONQGrZ6jz8lMKYdl1m3JSUkgiKHij%2FAOpOfcGNsIY3uIpPtv8A2%2B0BqvxZ0fAV9zEpacv5CvijZbjZTstIPpAMeKbCUeUhsfwRAYB0Tnd8kTNy77ytLTK3COxKTGTTk0w39p8Ueek1L88FNoXp6VpxtWnbsuPlEBYPFn%2BfRK9cNDo5ojIuk19Ra1aY801LtoI0wFnCFn4J%2BKBbXzKSPjjqvhHmctZjD%2BIqNjj2BTPs1BiYpy6mpKFltbZSsNqPcpKSfTHRJwzlYpsLJw2pAFx%2BbmCgd%2B0B8yikjmbfHEyUXF%2Bz1x9HqtJZDUxBmqscGgjmp15tw%2FEnt80a%2BxXndkHSKPN0ij0ykzhcZdZQmUoyCkFSbatZF7i9wQecBxA42UdkSBJPIGLpN9G2%2BtDYUpGo6SdyRc2JPfaKaFrQ4lxs6VQHiLLwTrLC9PfbaJdKvtT8UZYip1RyTMlNTzzkopSVqZJGgqB2NrRWYdb%2B0T8Q%2BaAw3Sr7U%2FFEQy8ryWln0JjYcuAtPVQ38Q%2BaL5RGULnEIfQlSVJPV0jnAalRKzJ6yZdZSOZCTYemKzUpMLNksLPoSY3qinSdygSoAPMA2CvT3iPNUKdKyMuhbbASrV%2BMQEuQuYOM8lp2brlATJqXVm0MzslOtdIy8yk3TuLKQsHcKHedo3%2FK8dmZEoUhGDMMlKNgC49HN0SQHUP1fOY69zgjDafP0z34oDj1zECf%2BJWGirvK3%2FnjmGGuA6hTx85iDysDYaVv2PPCCuPrMAm6cB4dA7une%2FH%2FAKo5e1%2BaKkv746E2gO0Mp%2BMjGOYmYlKwRPYEo0m3UWZ1an2Zt0qQpmVdeTsraxLdvXGJy%2FhAMfvy7T5y5w8nUnV%2Bin%2BZEc7syLReQUOKaWOS0LKFD0EEERJNyLDcpML6P7EnUn4xAdMU3jfzgqwW7RspKRUUy4SH%2FFhNuhBPaooB038%2FdHsXxrZ4tt2VkhJNL%2B26Cet8WmMR4U3c3USFRXlnNYZZl1V9hKk1YTOvx7xRehV2OTXRa0%2B%2BdUqItvHR6hxiLbuKtliD%2B6VNn8cBouo8budlNbTM1vKelybFwlLkzLzbSLnkLq7TFNjwhOZMs2ekwBhd0XvdUxMJiTiidzxGDak3mNMYRmZJM%2FSm55VKE10pUUuqk1ILvvSkDrhZRdSSQFRp7KDGGHsMTNRlfcn9vWMKqhMnh2XmVBclLOq5qcZ5uEkjlyAgNs1bj3zDqTK%2FEsB4Yk1rHVcS%2B87oV32Nrxzli7FddxpXpvEmJqgudqM6vW%2B8rYE9gA5AAbARuTi2w7hbDuJMLJpdDpVAxLM0RK8U0mkn8xsThKSkti50nyrgcwBeNDL3gJ5FTaanIlYVpE0yVW521pjuWcl3lPuIQSjr6rJ7f%2FzHC8unVPSqe%2BYaH8tMd7ltxm7JbKXGwkKtubefvi9lP4c%2BiFLfXZxPnn3PB0SkBVwpZO6tok0EqSA0sX3NxyEe8TXSJ03TYbG3KIBCb6mirbygo7WjaaSi2w%2BlZWR7ysDUDsdv994rPNvFqzSQra6QeV%2ByPc1LqW2CtQ0WHM9sSvtXaHRX6o2Pmi2ZUsszK65RSFsjUBZYG3xRahIBSXHF6lKVurVvuO6L%2Bph9TOlZNwCLk21f798UXJZwjrjZYNz54ZqxDA6th1pRceliUm%2Bogp2MYdVpNxDaumYAKe0dpEbcmZBSkhItZV7pP44xaq0gLaKnUFJCVaQRzhlmtE5bWn64s%2Bw80vo9WlPNPcVAH8YjHJJKisBI3tcekRsDF1JPsbMuNt%2FA63mNxGK02UGv3zUnfUnT6YrVTrZqJ1NCYuSRXqylXMzLJPywxFf23TX9%2BH81MVsdJKMTVzTzQ82R6Yhik6sXzKu9xB%2FkCNOra2Y2MsphvTX%2FAERiVdSdXxxllK3p74%2FcxjVdQLiISsLJsdVto96FNFrUE7x5Ukg6dMexooLWkJ3gPE%2BE32jzDUVbR65oAHaPM2Fa9oC542%2F5nO29Ma5G%2FwAJQ%2FJFxbb1rTfbqj8UWzHC9b1IG3VpjQ29KouygQlOkgHSLEi4vbtHaID6K8EmXNAyFydrvFBmU2JRdQpy1U5t4BLjNNQdyi%2FJyZXpSnt02744gzazMrObePq1j3ENQbXO1maVMdEV7MotZtlA7EoQEpAHcT2x2nRvCYZbPYbp1KxVkTPqelZNmVmJWWmZR6RKm0BILSHhcI6oIChcX9cRT4Qrh5WdTnDe7fv8TpZ%2FoQHN%2FCHQ8pqvmJOjNPPKq5ZCSpqpimVGl1UU5195awhaDMKBASlNlFoj3wbdkadrzNOla7UZSn12Xq8rLTsw0zUG09GJtpLqgh7T8ErSAojsKjHeLnhAOGl8aZjhmU4kHYKp9JI%2BVMehPH7wwFFzw3KCu406mfNAam8HvxDS2V2ZzmWmIKxLIw5j59tpvxhxPRSdZSkpYcUDsEPouwu%2B1yi8YDxt8PwyGzamZWjybiMKYn6Sq0AkfYEFXv0mT9sy4SB%2B4UiOjn%2BPXhdfA6bhnWdCgtJ9j6XdKhuCDbYg7g9kaj4xeMfBnEXgijYNw7gCo0tVKqS6n4%2FUX21upWWuj6NsN3skp3Vc7kDaA45UmCdrRUWIpwGzcg89sa8PWN1Y7wMxSZmcckXqe%2FL1OXLrDrDunULJIUFdUWIPeN7xvNfhE8xXnOkXlHk8r7bVhcE39JVHIaDaKqVbQHW6vCG5hrQrRkzk86QNRQMLi5SDcgWPOwNvPaN2Z8YkZw%2Fn3gHimpuaddwPgLHOCGJSQxZQ6QiqmTnEN2VIutLQpICgQdxe6CPgm3zkZWE2UDYiN65FcV2NsmKLUcCTFGo2MsBVlalz%2BFK%2B30snrV5TjCrEsqO5IsUkkkAHeA3%2B7xVzFaprFGnuOPMCYcq9GmWJySXlrLOJcn1AIRKgBrVodBUBa9rDcX2u%2BLc0qzwccOmUmT0%2FhbClfxY5IzNYrFJxFIicapjb69SEpTfqOXUR6AqNVSHGLkpl%2B%2BuvZI8IeGMMYlWVqRU6hUFzwlVKHNpBvax3ttHNuP8AMTFeY2Jqhi3GNbmKrVam6XZmZfVdSj2ADklIGwA2AAgOj1eEHxczfosiMmt%2BdsNgXjyzfhCscuUurUqQycywpKa1TZilzcxSqUuVfLDyChQCkEdhvvcXjk0rWVHn8cQUVX7fjgC1aeqjdPLzjzRSieIFJ5wGVZUNJfzLwiyrkvENMH%2FqW43T4RN7peLrHaf1N9pP%2BZRGgMK12YwtiSkYmlJdt9%2BjVCWqLbTpIQ4plxK9CiNwDa1%2By8ZlxCZtHPTNzEOapohpHtgeD%2FiJeDpYshKdOsAavJve3bAa1iINoaYAW7YDenDrxSYu4d5LE9Pw%2FhPC2IZLFrcsifYrrDjqCGArSnSk2UlWo3CgeQjZI8IHiInq8O%2BSrfmGHyR8UcjAkcorIUYDtTLzj1KsfYddxdkXlJTaT7KyqZ2o02iliakmVOBKn21nZJQFar9wMZ1mxX65kFxN5v1Op561DLNGLm5OuYemG8KN1yTxSxoVZIUoHo1tlRR1ed7nkI%2BfDbnlIXpUlWykq5EdxjpPLjjEmpDL6Tyezzy3oubOCaXZNKl6o8WalS0WsEMTQBJSBYAEpUBYaiAAA2RmRm1UM48JYiyjwrxdzWYdSr7UlJ0fDz2WLMkKwt5adaC%2BhILCmiCrV2aR37bA4n%2BJ5rI%2FFFHyfkctsvscO4Yw%2FT6fPTuIpLxp5qZDQC2UKANkpsLgnmY00jjUy%2Fy4pU6xw2cOVGwJV59ksqrU7OmfnGAb7tKVfSRfbe0csVqu1Suz0zVqrOuzk5NOqdffdVqW44o3KiTzJJgOn%2Fq95oAIc4YMknAk22oUWTMDjfrGNsssQZXSeTWA8KUzEbzL845QGFy6luNLCkqKB1Sra1yL2jmbpD2mJFKvARWEr5RRKQmJrmJSL9sBLE1hEQLRMBAQSLmKyU%2BaJEjeKyRAVGUAmPQoWTtFJsWtHoQnXAZTR2tFMQtXakxf8qx%2Bb66rtTQaqfV4qv8A1RZpIBFLbT%2B5VF4yxYemJnETMv8AZV4dqoR6fFlWgNT4XN5yXPmQPxRt%2FhhTfiowD5sa0r%2F71qNdYdw1PyK2ZuoKlWQgIWoLmUhQt2gXjYnC4%2BiZ4pcAzDataXMa0pSVJ8kgzze8B%2Bg2EIQCEIQCEIQCEIQCEIQH5%2BeOA6uJ%2FMtP%2FwC01Q%2F0pjQ6WdVjblpjf3G5Lk8UWY%2F7rEtQV6ulMaTaDSZdKphQShsh0ki5PZYAQGSSCnAlTbKwha0pAWRcI3HWt22527SAI2%2FmPmnQEYbk8nskZWepGAKXMs1KYnpxARUsR1VBC%2FHprn0aEuC7bI5Wue6NP0B2n1F11qkza5mYSx03QqYLbmlJ61r3vYb7dke6%2Fn5c4Da2LeKDOfF%2BJMK4wmK9JU%2Bq4LddmqSqRlA2jxl0BLzzibnWpxAKFC4Gkm1r3j31jNjLQZnYBzowdh2aw%2FVZWqNVTGVJQgGTbmUujpH5RfNSHG1OKIIuki0aYgL3uOfaO%2BA%2BiPG9lRM5tZXS1awYTPTVEWarLBj3zxyRdb5oA8ojqqFr7R8yGKm5SFKlHGdakmykm6VJPcQdwfNHYfDfxhvZX0uVy%2BzAp0zU8LyoKafOSo1zdLQbnoijm6zflbrJvbcRu%2Bp13gazAJxBVKnhBbryg46ZtgNOhXbqTYKv384DizhtyqrueWZtHW1T32sO0KcZqFaqAQehaQyoLQyF8i44tKUgDe1z2R0T4Q3F8u9iHBWWsu8hU1QadM1eqISblh6cUOhbV3KLaCu3YFJ74zPFnGJkrlRh04dyKo0riCoSxPijbUp4rRJFdt3nNgp9XclI3PNQEcO4hxBW8UVuoYjxHVX6lVqtNOTs%2FOPG6331m6leYDYBI2CQANhAWxRtAKJ7YKG8AIBcwuYjpENIgIXMNRiOkQ0iAjHplEzAmGUyjUw5MKcQGES9%2BlU6VAISixvqKiAPORHmG5j0ysxMSczLTsm8pmYlHm5lh1HlIdbUFIUPOFJB9UB2Ng%2FAGJOE7CrmYMzg6q41zixTLGSlJaVZdnGKC15RS%2B8m5UU2TrtcqKQhOwJjjifmJyYm35mffW7NzDzj0y4oWKnVKKlkjsOonbsjZbXFLxEy0y5NsZuVtLzqy4tYLYJVzvskAbxrCZedmpl2cmFlb0w4t51Z5qWpRUpR85UST6YCUEkc4jEBtEYCSI3MT9HECgCAgeW0Q35xNEQICERc2l3B%2B5iMRU2l5BbKCUnmRziM8kO5OIjMfJnAWZOGpzGuTb%2BL8TSOHaZUpGfM4GWGk6LstqTfrFKkkg2NowugZnY2rORub%2BfeE3vFsxK9jWVkK7PSCC7M0ehdGlTLUsCCUoPIrt3nnHO2PcycXZnVqXr%2BNZ1ubn5Sny9LZW20ltKZZgENJ0ja9ibntifL3MnGuVleXiXAtbXTp15gy0wnSHGJpq99DzauqsA8r7jsMSluySxTjPMTg5zUnc2qrO1Wl0Cdpr%2BEa3VE%2Fms1BUwkOSzbhALibEj%2BERfaMv41qxl37bZvCCsratP47XQaW9L4nYfUZeTYt1WlNC%2BshCVA7fC80c85l56ZmZuyspTMdV1qYp0ivppenScsmVlEO8w50aNiodhPKM%2Bl%2BN%2FiHlW2fFq5QQ6whCUvOUVpa1FIsCok9Y2Av3wGTcF2MMspDHdNoM7ghUnjASFYfXi5%2BrhEuJYNFSpfoFEBN2xoue0k98aRzIxJlvimuylTyuy%2BewZTiwlqalXqh42JmZKz7%2BlXwEkKSNPpMYdOrNSmX5udQ267MvrmXboFi4tRUogchuTsOUSA69SH0a0K6qk%2BaLjqLh2pcrkTm5hvAebGQk%2BvGWIqmp%2Bh15663qcy43pGhsXQpIUFKK73Tqja2CMO1eSqvFhgCoYjdxLiR1xmdXUChKH5hmYprhZSUp2Gm3R2HLbvjm7DvF9n%2FhihSuH5LFspMMSTQYln56QbmJptsJCUp6VW5AAFr9wveMJwlm9mNgnG8zmLh7FU2ivz6lGoTT5DvjwUbkPJVssXOw7NrWiIjJExm3jhdxct4NfFs8%2Bh5hVTxCXKR8AqmUz0sWlNg9y2XPuTHStaqVGrcpIcWl2PF6dlJU9CL9czM3pWCD2aVBaPXHBOZWfWZebSJGTxpWpZVOpq%2BllabIyiJWVQ7a3S9GjYrsTueVza0UkZ6ZnIyuOS%2Fs837UC14sZMS6A70HS9L0XTeVo1729XKJMnceRMixmLhfInPqu1EuzuD8JVmm1XpR74%2B8pIbcUpR5KQWVKP7%2BPnpijEL2LsR1fF0wVF2u1GaqatRuQHXVKSPudMZVhvP7NjBeCZ%2FLrDGJWpKgVJc2t9nxNC3R4ykJfCHTulKgL2HIkntjXfkNpbR1UJTpT6IolDSdeoq2iV1xI2BhY253iUpv2QENd%2B2FzEOjMNJHbAR1w1xLYwsYCpGXZS0aYxLmjg%2FDslXjQ5qoV6Rbl6mACZNwOpUl0X2KgU7A7EkA84w8BW28V2V9GpLocWhTa0rQtCilSFA3SoEbgg2II7RAfUmXrNPxXxD5gZXSOXNXwpXnsLsMqzLlZZCHX21JbFgSNKVJUsBNrlRbWDbSmPl1UZNNNnXqa26h0ST70r0zZJS90bhR0gJ56tOq%2FnjZFW4oeIau4cewjU84K%2B9TH2yw4kOpS6tsiykl1KQvcbE3vz3jVoATZCBoCNkjuERMZiKiQbXVbzRDUqxsn44K1FW4v57xT629yYkRLi7xN0irCJOjVE%2FRqsICRTqidA5QCiOZETlB3A5HnEOunYjbe20BMglXOJlXHKJEoWrcRNoWIAlaoipSrxLYxMEkwENcR1xKUkQ0mArN781xNMTs3KU2pqkZyYlVv0%2BYlnFsOFtSmloIW2SNylQABHIjYxQiZfXQptfWS6kpUnvBFiPigOuuM5TNOxbkLOOoQiXlMMU511I8ltLcxKrUfQEgxtXEeGMTTXhIsNYqZpU0ujzGGEzaKihoqZ6ES7yFjpBsOutva%2Fwx3xwrirMXHePG6Q1jXE03V0UGS9j6d4yEXl5bazYsBcdUc7nYRkUtxB51yWDTgGUzMrbNE0dCmXS%2BNSGrEdGly2sJsbWCuVhFpjMeDOOrU%2Bu5uY2rFIcQ5Izdfn3JdxHkrT0pGoeYkE%2BuMLue%2BJ0dHo0I6qUeSmJSLwiMhCETWHdDbzRUSg2iJX54aREqkwE4VftidF4pRW6RfR9mnUPkiM8idbrTAeIMAYd4IcPVXM%2FLhzGVGGPagw3INzXQFmZKlBuYvcXtYpI%2FdReMlc26VnTxE4WpNMwVTaDQ8vMH1heAMPPuBxKquG0lDjnwSrTfSkXta9ybxyk%2FmJi57LtjKhyppOFpWsuV%2BXk0tAKTOLRpUSvmpHNQT2KJPmi1UirVOh1aTr9Hn35KoyDyZiWmWHChxpxPJSSOX5QSImdaHV%2FCbmlxBY84gmMIZi1utV6j1FM2nH1LrcqfFJKXDSiolKgAyUr0pSL2UCefOLphmvZTYU4OMDDHuXM7mBh0Y5xBK0qRknClxlTc1MdFM60kEJ6Pq3%2FdCNI4w4s8%2BcdYemsMV%2FGgRJ1BvoZ5UjJtyr0039o44gaiCOcSZZ8U2bWU2D2sDYQmaIikSbjrso1NUxDq2C4rUtKVE%2BSTvYiIiMkrRlXiHLjB2Jp97NLLScxBJzLkv7HMqnjKrpbwmkqDjl7dIkIKd%2F3F%2B2Nu8cGLMsanmPiTDdOwa3MY1k5ynuzOMGKl0jMyx4uCqXDSSUkhKkJ35WJ80aGzLzMxXm5il3GmM5yWfqbsqxI3lpdLDSWWgQhIQnt3Nybk%2BoRiujo20I%2B0iUTGbaWXeEJvA0pJZ7Y3yOXj3L96Vfkmh0vvS5hxzo0LGm51ocSpGhQ5q37I7Mr0s2zxX5GY5mqvMt0zE%2BF6vSKTQpuXS0aPMCTQ7ZCeYK0HQb7haNPK0cV5WcRubWTNMfomB69LCkvvrml02elkvsdKq2paQd0FRAJsbEi8WjGucmZGY2K5PHGLMTPuVymlBp8zLe8iR0LC09ABsjri5Paed4iYzIjJ15wyyVRkuMXPetVaVXLyMiZoz762yltaHJtDyLqOx96SV%2BiI8NVIpmdXDDScCB5KVYMzGanW9gR4s1UPHmUJHYFNPLSBHOmMeLLPHHmFZrBtdxLJtU%2BoN9FUFSEkiWfnEHml1xO5BGxAtcbcox%2FLHPXMzJpqpsZc1iUkGas40%2FNNvyiHwXWklLa06vJISSNue3dFoS7CYrLPExKcQ2Wz08hZkMwKbO0rpVFTTMmw80DptySXJV6%2FncMc%2BcdWL28TcR9dlJWyZTDklLUlpF90LKS86PunR8Uazy9zgx5lJV6jiDA1Tl5ScrDQani9LpeQ%2BnpelOpKtr9ISq%2FnMYtiXEtbxhX6pivEk4ZurVqbXPTz5SE9K8vyjYbDkBbuAhI8Ou%2B9%2BfZEpKlcolCFK3vtE4BG0QIKCuUSpKuZiZZJFgYlBPOAnhC474XHfAIvGG5mcaq9PRLTkwymYqEmy82y6pHTI8YbIQoA9ZOoA2O20WeKzL7su83MMOFDrLiHW1pNilaVBSSPQQDAds8QlQkqV4QbLScqykNSbKaP0ilkBKFqdmUtk35dcojYPiMjmRxJZi5O5i5E4fdwXJUdM87iWYpVp5c2WmtT6ppQt1gtwICSCgS9zcXjgDG2O8W5lVt7EuO69NVmqzDLTDk3MEBwttkltN0gW0kki29zeMqrPEfntiHCXtGreZ9Ym6OppMu42paUuvMgWDbjoAWpNtiCd%2B2IiMhr6aal2JmYlpWZMyww%2B6y0%2BTcvNoWUoXftukA388UIibBNk2AFrAchEtx3xIHlEtj3RNcd8TADvgJLkRKTFQpB7YgUQFO5iaJggeaJtAgJLmFzE2iGkeaAkJMToueYiBT3EREBQ7oCaK0i9MSk4xNSj7jLzLiXG3WzpW2sG4Uk8wQdwRFMIUReIosF2uEwzzHT2NXlS%2Fg8sCTLylOKXit9x5alFSnff5tRJJ3KiQbxuOiTrOWWTmQlCxdl9N5rLqs9KCQnZeVQsUFKwl1lTagDq6LpAAo2uEKueqI4fmsd4znMEyeXM3iWcfwxTpgzkpS1FPQMvkqVrSLXvdazz%2BEYyPA%2FEBnRllQU4bwVmJU6dSE6uikiUutMatz0YWDoBJvYbX7ILTGbMuNPD83h7iBrYn8UvV16qyctUkOvBIVKsrCkolQEgAJRpOntKVAncxoe5i5VqvVrEtTma3iKrTNSqM650szNzK9Tjq%2BVyfxDkItikm%2BxEREZIySKN4lBsd9oqBN%2BcSlNjEoSnntyiZI7%2BUFt7jTyip0dk9blASXCYi2dTo7hziGi67X2idTZTZQPp88RKHVXCTUMPUnJLPet4sw8qvUKSkqa5VaWl0JM7LpQ6ShJJFiSR2jlElHzlyvzExRltkZhnLKSwRlnM41k6pXWX3wtc%2FNBRLSHDcgNlzRck72SOUaCwxmVjHCmDsWYBoFTbl6NjVphqsMllKluhonToWd0bEg25iMcv73ocR%2BTluCLcjeGREZOqsaZr8VcrxaqozFXxLLVOXxKinyVBZlymmqpanwlIW1bQtss3JdJ2332tG0Ojy1wTL8WSxghOIMGU%2FFtMMxh%2BniyZgqlGy%2By3p2Gl5SjtysY5oluMXiLk8OtYaYzDX0LLHiqJ1cq2ufDfYPGCNVwNgecWXKriBzOyYFYGAarJspr8y3O1AT0oJouzCQodLdRvrUFnUre8WickvI%2FiXLiXzamsVVfKCfGCHJh59OD3ZtbDhZLWlCA%2BednOvse2143zxLY7yVncscAUSVy4cqMzU8CqOGZxmuEe1YLcRZpYST0q0qTcg87WtvcaEzXzyzMzofpYzCrUlNtUUvKkGJSRRLoZLunX5O6r6RzO3ZGBlGhCtCUJStV1JTtc9588WGbZeYKr1YW7mQjKV%2FG%2BFsGTSX6%2Bwi%2FQKbSjWplwpOoXQdXVBIAv3x1VmDUKBjDI7IrN7C8rNYOwVR8dUbp8IvNIRLpQubU2l4GwUotq1KBvpUlZVzF45NyyzazBydrLuIMva%2BqnvzKA1NMOIDstMpBukOtK2JFzZWxFyL2MXHNPPXMjOlMpLZgVaWmJKQK1S0hKS6ZeWbWoaSvQnYq07AnkCbWiJjMdZ47o9ad8JXhVSZSbU2mkszaHg0roSy3KzKHuty2WtIPnUO%2BJsDz9IzTxpxYZJyc2y3L4kmFTctMp8lCnWfEZlYHbpdbbUfVHO1P4xeIORwyjDCMYyzwaZ8WZn3pJtU622AAAHe8AAAkX27TGA5fZn4zywxG9i3BVXEnVX5d%2BTfedbS8H2XlhbgWFXCiVpCr877xGQ7raxVKVLiGxPw6dOn2NXk%2FLUKXb%2BCidbYJdJHLUWn0G3cmNGcZ6pfBeF8ncjpJaFJwnhhD0wW1XSXAhEslR%2FfBp1QJ%2B2MaTl84MwZbNFzOZiuJRi52YdmXJzoUltS3GuiWC0erpKLC3ZYRbMwsx8X5p4kcxfjeotzlTdlmpMuNspaSGWrhCQlOwtc%2FHETCYYssK1G3KJVcu28VkqTyCbxI4pSfgiCFNCL3JVFRSLqABvESE6dyLmDaeZTtASqZIOxhbbQPXqibo19JfpIFpaUlXSavNExOSYnJKFHlGXZWYExjmfjiQwRgSYdlqrONuvKmUTK2USss0NTr7ikEEtoGkkdpKRGIBJMXzCWLcVYErAxDg3EE5R6j0DkqZiVUAtTK7a2zcHqnSm48wiZjNZ1Fn%2FACruQWSM%2FkLlJhGuzMpOlqcxzjF6nrEsekcaCh0ltPW971WNm2wBe6jHQuVMjhXClWwbgjK3G2F6jg7DVDnVztNps6l%2BpViouqbCpxSU3HRpOq6ib6lpFrRwLiHiHzzxbh%2BbwniXM%2BsVGj1Bky05JvFBbfZKtRQoBPIkAm28YvgbHGLctcQDFGXtdfoNWTLrlfGpRCAotLIKk2Uki10pPLYgWiMlclfMfDreEcd17DCK3Ta2KdUX0Co0t7pZWYC1dJdCu0p16FDsUlQ7Ixde0VyuxUdKQVrU4rSLXUpRUo%2Bskn1xTWgr5RXIyUwSo6T2f784gs6dgCo8rxOptdrCwHaOwxKGSvYBV%2B0RKEiQ4ny7WiJIPI7RHoSnybkROhtw8yAICVKU3uYlWATziv0IES9FvcQFHTbsj0SlQnJJSzJvrZLiShZT2p22%2BSIdEpWwtEnQG%2Bom1ouPairVJXlTTh0%2BiKM5OzM0EofeU6lFwkn5YpdfkLWiVaLbiInWJ2iADbtj0yAlPHJdVQRMrk0vtKmkypSl5bGsdIlsq6oWUagknYG0eNFwdzHskEyblQkmqlMuy0i5NMNzj7SdTjMupxIdWkDmoIKiPPaInUmXduQuLMD53V6pYapnD1hzD%2BTVFohYqM%2FVZZBnW521z%2BaRsbNgqKgbpI1E8gbBw74bpctw0zlewNSsvajVJnHNRkqVUscBroE08TCWmg44bHpFICClPwiokR7sYZxcJWJcCyuUFCzarmD8Ey35nmJSkUN1Ls8xq%2FTnVpudVtS9rrPPbaOfMIYc4WMb5dTWE8w8b1vBOKpWsOLbrrjLkzJ1ilh1XRaZYHo2XujKQeSkqTcXBsJic1YhR4maLj6gZoOyOZWBMMYWqgpsumXRhdot02flklYTMt%2FbLJ1JWTY9QXAjUi%2Bcbr4rs6cN5z43o85g5M0aBhqkJpUk9NNFt2ZUV6nHClW4TdKQm%2B53PbGk%2FLgZIE98QYecZWl9hehW%2BlUFNq7IlQN7JimeSXq9k6g2kpRNLI9Vt%2BcU5ipTr7KmpiYW42o3KCLi8U9G0QKL7aVfFEiTUFKB5W25x6EBOkC%2Bq3n5xQLRRY87G3LlFWWBVYHayu7lvAdQ8PmYuFFIwLlHlhkdT6zi2oT6VYwrGI5dt9pyUVdUy40Uk6EJFgkKA2SBuVRtHCXD%2FlP9Upm3WsL4Tk61TsESVOTS8PuOaZFmvTLK3Xm7nZKEaUbKJCC6ofBtGJZFZm8N%2BV%2BURpUpmg%2FhjG%2BJpPXX6ymmLenZN9f6SwSkoSltIGi1wSdR3jGsqMzMmMosYZj5XSOY1bq%2BXmYdGZa9uj0svxiVrC2HEPOOaeuUkO7rtspO%2FfAScU1CxknAOGMVYqymy6lXn5wM%2B3XAlU6aVcvq%2FMsywEgDUfJXc2U2QDvaOW3F9kdGZl46yuwXw24d4Z8qcbKxkmXqiqrU6y3LqYYRZ1TnRoQobFbigQBySCb7gRzmtveLQmFIntiLa3G19I31VJ39HniJQQoDviboj3RVD0rrFS1%2Fo5fxj5opu1Gdc3W%2FrBPLtikWQNiNzEOjtASarmKjabxS02MVW1WgOisk8xsuMPYaw%2FgfA2QoxxmnWqi0xUJityiHZNTC3PfSwQSUoQ2ALqSLXUpRNgIyHiAm8rOHPiSrBwnlXhTEVKqeHZSYnaJUlL8UpU8paipyX030FaUpVoIsNW1gbRdeGTMDh4yuyump85r0%2FDeZuIJZ3x2pTFOcmXqQjWQ000gp0qASAsi9lEi%2BwjTVdw7koc76FS387nMVYJq0wzVcU4pnJVxDheK1uOy60i5Kl6EI1DYdJ3CLQNz8Qz%2BB5Thdw9iGrZNYXwljPMScYmqfK0hkBySk21dL0yl2BBU1oCk2sS4BHHrjnSRuDirzhk85s2p2t0J%2FXhmiMIo%2BHkISUo8WSAXHUiw2Wvlt5KUiNNwgQJI2gCYhpMNJiouSa7UUoSgOeSAkEgXsBYRTXVag55b6viEePQe%2BJyjzwXU7DsJisAdG14oqBHfE%2FTBKO2Cjc2TWNsm8BYZqlRr2W85jzMubm0y%2BH6TNyhVSw2SkI98Ct3FEkkFJ8kAcyY6Dx3klkE3xHZN03FOG6fhRnFtInprEGG2HyJRVRbaQZZB3ukqWpxBAIC%2BjG3ONf8GVa4e8DyFQzDzJxvR6bjZM0qVpUvU0qLclLJRcTDYAIUpZJBVzSE2Fr3i7UjMTKXL7inw1nPizO%2BXzSarsjUJGsVJulFtjDsypTYlHAyL6WAnWgEXUm5UecWgZTm%2FlrQJTJPM2sZr5L4Wy9qlAnlS2CKhRXFB6obp8WKgFEK6U9QhQFwo7DTeOHT5ZjtLEOZGWWDcls2MNVvP2VzbXj6ZnJmg0oBxxdM6fUUJKl%2FYg2opXdNgC0NIBJjip9fcpSlK8pXK57TaKzCYSKBHbFMqI5mIage2GkHtgg1X7YREIicIFoCUDvgReJiLQAvAQhE2iI6DAUjuYiU3G0VQwSLxAN72gKaOcVAL9sFI09kEns0wEizY7QtteJ1p3G0RCdoCDdu1AV64jpB7UjzRFISDuLm%2FZEQD8E9%2B1oD0S9RnZOWMmw630C1a1IKATfvvzit7OVJZ98mG%2FWgRblhcSC%2Fw4CvNTTk250kx5WkJ8m2w9EeVNNpg8mnSo9DSYriy%2BouJigJISICgabSufsdL37%2BiTEUSNPvtJM%2FcCKxbMSbiAmVT5BYOuTllXBFy2kn47QRoQhKEISlLQ0pSlIsAOweaIo%2F31QP8AvaAk%2FwB%2F9URCO3QYj6PiVEUa7wEyLKGkgae0mILZT5PMHke6KmknrD4jEi0lNzc6TzB7ICQIKDYAGKTiNRsRHo6PRrbXq6vxD1iKTnU3gLe8hLYJI7Y1jNOVSpzLxbW4pCHDfSo2QL7CNlTi1k7dxjD6OwWKPNLQ8pC3pxSHE6tiEgFNx6SYDHVU6o9rTh8%2B5j10mVnWapLJUNGpenrecWi%2B63IoLeWiZl3gTcPI5WHMwFwXRJj9TVFBdHnRbU2q3btF7XV19bQy6P3KhEvszMqT0apdah33t64DxUyQcaWrp0dT90nzxdPF5XsZQfSmKUtMPvrVrbskCPQeUB5n0IQ3shKf4IizTi%2Bv5EXic8iLM%2F8AZPfOrAQfoE4XL9AqKLlEmkKF2FD1RljGJXmm0JVIE6UhNyLkgcooO1x1xADkq4spvub2sYDF52Wmm6c%2FdC0hKCb27oxttE%2F%2Blqd%2B6MZ9Uap0so%2B0uVASplYGx7osrD7nQIHV8kfigLKzM15hQUy8%2Bm3nv%2BONj0Kam25eXmXFq6XTqVqFiTyvGMJcWVJAULdlhzjK6YXHpVD7x1qXqJIFr7%2FJAXxuszn2qYlmahMzrYQ90YCVX5WPdHlShXYLROGTuUarnvG0BAnzRKfREwQ52iJg0s8xAUwbRKrnFZTducShHfASdeJ5dbjDnSfamETEXFoD1GuTrOyOj095REF1aYmWHGXCgJdTZVhYR4igkxMBaA2tklM5HS8jPDNmp1mTnF1BFjIT83LBUgGDYo6AFK3Q9a4XYaeRvG11v8CS3LnGOOb%2FAPnNQ%2FHaOUoQG6M53eHpWFlN5S4lrc5Ppn5YyzE7Upx8dAUqEz0jTydAsoIKVpN%2BdxHl4dM5sEZKTlbruIcFTtZrc%2BhqXkZyVebQqSYAPSBOvkpRINx2CNQwsD2QGb5s4nyyxbV2qzl3hfEVHmJovO1hdZqgnlzby1ApcSq3UsLgjlytyjA4n084hAVZFAM%2FJ%2F8AiWf9ImO9lXdm1pQbqUfjjg%2BlKl2qnJTM4pSZaXmWXn1JTqIbQ4FKIHabA7R1G%2FxUZKuzfjDE9VVJV1rmQKbeaxO8ZrGnhVTPmj3sV5q4NER6eTPwNmNoQdWgpT8HZN7GJuijVaOJ7J5skszlUSVne8irn8cTp4oMpSTrqNSAB2tIuXt542uD%2FWbS4XmnmltllvbeK%2FRptzMakRxPZMauvWKqkf8Al64rjigyVSerWKiR56eu8WinUrNXmnmlsx9nkQbd%2BqIFlLiSlKt%2BwA7eqNaDijyUULKrNTBB7Kcs2imOKDJUrUFVepJT2KFOcJ%2BKLxQcLzTzS2L7G7%2B%2BR5KnQ0uJTZF9uX5YwdXFHkgfslbqh%2Fya5Ex4qciy30iq5VDtaxpzl7eiKcHJHCjz80rBjynzcnTJxxCblKFd1iO38sa9pksVqTfsTGxcUZ5ZB4ios5TJPE9Sl5t1s9EtdKd0FQ3AJ7OVr%2BeNRtZtYOkTrNPqTqfthLjcd%2FOK1bWSymeSJ5mkMxkdHiiv8vszfP0xLihNsYPj922f5Aj3Y2lXcQ1KsVuRlXkykytEwjUg6ggna4i2TswajW3KglNkuaVW7hYD8YjQq2uhGxmdDQTLugjmIx7EcsUK6vbGR0RzS2oHlaMexXODxgISOyISx9LJUrckx725ZQTsgx5pF0LcAWk84v7baCgabiAx6al1DsjyBtQc5RkM1LhXZHkEmC5ygLfjI%2B%2FU7zSKR8SlRfn06UJ%2FepirVsC13E7ErUaRJrdaZZ6BZCkAagSbbqHfGZKy0qa2mwqdaTdlBAUgk8uVxzgNeuLUk7GKXTr74ztzKmrHbx%2BX%2BIxS9yStE7VGW%2B5V80BhPTr74dOvvjNxlBWD%2FwA6yvxKif3Hqz%2Bysp9yYDBenX3w6TV5RjOvcerPZVpT7kxEZPVy1%2FZeVv3dGqA1%2BuxMUo2MMna2f%2BcpX7lUTDJqsnc1OUHqMBrlMVEdkbA9xytA%2FwBspT7lUT%2B5BWgP7YSv3JgMERCM59yWs7j2RltufVO0PcjrfbUpf7hUBgp5RTIMZ%2F7kdX7anL%2Fe1RKrKepJGpVWlgO%2FQqA1%2FZXfCy%2B%2BM%2FGU1VPOosD%2FAASoe5LVP2VlvvSoDXwBvE9toz%2F3I6qeVUl%2FvSoj7kVW%2FZOX%2B9KgNfpb3iC0kGNiIygqxH9tGfvCjEVZQVQcqoyfRLrgNbqSecS2jZHuP1C9zVUfg64m9x%2BoWv7Lo%2FBlQGtxziuhO0bB9x%2Bf%2FZlr8HVEDlJUk3tVmiPMwqAwHSImjOvcoqXL2Ubv3dCbxP7k1TP%2FADin8HVAYFFNeq%2BxjYasn6mB%2FbEn0MmKZyfqnP2RR62jAa8sYWMbC9yGo%2Fsk3yv9iVEwygqF%2FwC2jR%2FwKoDXFuyJ9EbG9yKp9k%2B196VA5RVT9kG%2FvJgNc6PPE2jzxsH3I6v%2Bvm%2FvRiojKCrEfo1v70YDXYTaKqY2AcoKmOc8gehoxMMpKgBvPj70YDA20qtHrYT384zRGVrydnJ9w%2BhqJ15cuMgETMwVdlk2gPEwfzuT%2B8MXrLVbbb%2BIFulQQMP1G%2Bnn9hVyixVGnz9MZLCG1uDfSSIyDBMuMO4axDizFra6dJzNKmKbT1vJI8Zm3khISkfCCUkqXbYbDmYDXvvbkov7bof6MZ%2FwjpH1ROWqk%2Fttoh%2F9a1GvZydpb0qWqf4zdaCF9IgICTYjbc3%2BSNncIUmXOIHLpSb%2B94sop5DsnGjAfoHhCEAhCEAhCEAhCEAhCEB8y%2BMjwdua%2BYedlTzGytlZGqUnELhnJlhyabYflJpVukBDhAWlSgVAg3GogjYE8UcR3DDmTw%2FViSw9jGlIQ7NyLc7LqYcS6hxBUUqAUnYqSpJuOYuDyIv%2BguNf5zZGZdZ8YaRhrMKjGabl1l2Tm2V9HNSbhsCppyx03AAIIKTYXBsLB%2BcdhU9ITbU7Iuvyk1LLC2nU3SttQ7QY2vKTaKlKtzVSoNOdfeaStTrQUxrJF9SkpNrm8fRWveCbo8xUnF0PMVwSRV72mcbBcCfPpRYmL9QfBdYXkJJiXqeNH33GklClNiySm%2B1gUwHzQ8Upn7Xmfwlz54eKUwf9Hmvwlz54%2BpP1sjLU88S1EehafoRL9bGy1%2FbPU%2Fu0%2FQgPluGKSk%2F8XUK9M06In6Ol9uFmj6Z1w%2Fkj6gK8GLl98DFU%2BPSofQiZPgxcu%2FhYpqPqUn6EB8v1ppavJwuhP%2BPO%2FNEnQUztw6z%2BGu%2FNH1GT4MbLYeViep%2BpafoRU%2BtjZWnniesD0Op%2BhAfLgMUX4WHkH0TjkR8WoP7X%2FwD1rnzR9Rx4MTKq%2FWxRW7f31H0In%2Bti5R9uJa79%2BR%2FVwHy18WovwaAfwxz5oj4tRe2gH8Lc%2BaPqaPBjZPj%2FAKTYg%2B%2FN%2FQiqnwZOTA8rEWIj%2Fh2%2F6uA%2BV%2Fi9G5%2BwZPpm1%2FNEegon7X7f46v5o%2BqifBl5Ijyq%2FiM%2F4dv6ETjwZuRgG9dxL6n2voQHynEtRLkqoKiOwCcXt8kTeL0L9r6%2FwxfzR9WPrZuRP7OYn%2FCGv6uI%2FWzshv2bxR%2BEtf1cB8pTL0Lsw%2Bv8MX80Q6CinY4eJ%2Fxtz5o%2BrZ8GdkP2VvE%2F4S1%2FVw%2BtnZDXv7N4p%2FCmf6uA%2BUnilBP%2FAEfV%2BFufNAyVG304fUe682vb5I%2Brw8GnkOP%2BesUfhLX9XE%2F1tXIP9lcU%2FhbX9VAfJ9MnR%2FhUA%2FhbnzROmSoduthxZPO4nV8%2Fij6wJ8GvkAPKqWKD%2FjjX9VE58G3w%2FnnP4o%2FDWv6qA%2BTqZCip5UFXrmln8kVFSlBVzw8v8MX9GPrEjwcHD2kdaYxKr0zzf9XE31uHh6%2FVsS%2Fhzf8AVwHyY8RoV9sPL%2FDV%2FNEW6dS%2Byhr9U0sfkj60J8HHw7jmrEp%2Fx9H9XE31uXh17sS%2Fxgj%2BrgPkwaZRk7qoqzt2Tiuf3MU%2FE6PyNDWf8bWP6MfW1Hg6OHRPNvEavTUEf1cTfW6uHT9SxH%2FGCP6uA%2BSKJKjDnQl%2Fhiz%2FAEYiZSj2%2FtCr8MV9GPraPB08On6jiI%2F5QQP%2FAG4j9bp4dP1DEX8Yp%2Fq4D5HiWoyTth5y%2Ff46s%2F0YGUoh8rD8x%2BGLH9GPrl9br4c%2F1piD%2BME%2F1cQPg6%2BHLtlcQfxgn%2BrgPkaZSjcvYF3T3eOLv8dopeKUNPOgPn0zyvox9dleDq4cFc5TEHqqKfoRL9bo4b%2F1piH%2BMR9CA%2BRCmKL2UJwemcWfyQEnRlj%2B0zo9E2v5o%2BvH1ujhv%2FWeIP4xT9CJvrdnDd%2Bx9d%2FjAfQgPkGafR7Eew7u%2Fb40vaJkUykW%2FtM%2Bf8aV80fXr63Zw3fsfXv4wH0IqfW8%2BHH9jq3%2BHj6EB8f10ykX%2FtQ%2BP8YPzQ9jaV8GjEel9Zj6%2Bq8Hdw4K%2FuGvD0VAD%2BhD63dw4frGvfxgn6EB8gvYyl%2FsIv78uJfY2lfsOv78qPr99bt4cf1nX%2F4wT%2FVw%2Bt2cOP6zr%2F8AGCf6uA%2BQPsbSv2HX9%2BVETIU4ixpCtP8AflR9f%2Frd%2FDh%2BsK7%2FABgPoQ%2Bt38ORN1SdfVsB%2FbBI%2FEiA%2BP8A7G0r9h1%2FflRUTTaUka%2FYNYCtgemXzj68%2FW6uG%2F8AWeIP4wH0ImPg7uHI85XEJ9NRH0ID4%2F8AiNMv1aMr78s%2FkifxGmW%2FtMfvqo%2Bvzfg8OHJryJOveufSf%2Fbip9b24c%2F2Prn4ePoQHx7MhTj%2FAMyJ%2B%2BriBpsgeVFT99XH2F%2Bt68OX7H1z8PH0IfW9eHH9jq5%2FGA%2BhAfH9umU%2B29FT99X88RNOkf2GR99XH2C%2Bt98Ol7%2BxtZ%2FDU%2FQiCvB88OatV6bWhq52nxv%2FACID4%2FGnSP7DI%2B%2BLimmnSd%2BtR2x6HFx9gx4PbhzF7SFdF%2B6oD1fAiP1vjh2%2FWlf%2FAIxH0ID4%2FinyR29h2%2Fu1RN7F0%2B1zSE%2Fdrj6%2B%2FW9uHO1vY%2Buenx8fQiJ8Hvw5q50%2BufxgPoQHyB9jqX%2Bw7f3a4lTJU4LsKK192v54%2BwKfB88OiPJp9cH%2BPj6ERX4Prh1cFl06tn%2FHh9CA%2BQokKeRtRWvu1%2FPA0yR5%2BwTX3xXzx9d0%2BD24c0iwkK7bu9kB9CJvrfPDp%2Bx1b%2FjD%2FYgPkIKXIH%2FmZof4RcTex1P2%2FORnb90v54%2BvSPB98OzagtEjXAR%2F9eD%2BNEFeD84elc5av%2BqoJ%2BhAfIbxGnjnRGT6XHB%2BWHilL5ewTP31z54%2BuqvB7cOq%2FKlK%2Bf8AKA%2BhEv1vHhy%2FWVf%2FAIxH0InMfIvxCl%2FsKz99X88PEqby9h2bfvl%2FPH11Pg8uHI%2F3DXv4wH0Ih9bx4c%2ByUr4%2Fx9P9XDMfIrxCl%2FsM398X88REjT%2Fg0Rk%2BlSz%2BWPrn9bx4dP1tiD%2BME%2FQh9bw4dP1tiD%2BME%2F1cQPkd4nI%2FsGx90r54nEtT0j%2B0ct69Z%2FLH1t%2Bt3cOfZK4gHoqIH9CA8Hfw6jkziP8AjIfQgPkkWJL9hZX4lfPEvi8j%2Bwst9yr54%2BuA8Hhw6DnLYhPpqI%2BhA%2BDx4dDylcQD0VEfQgPkf0VOTyw7L37yXPxXiPQyROpVAlrHmAV%2FJvH1t%2Bt3cOh%2FScR%2FxkPoQ%2Bt3cOn6jiP%2BMh9CA%2BR%2Fi9P%2BFQZZXpK%2Fnh0FMtb2uynp98%2BlH1vHg7eHa1inEp%2Fyin%2Brh9bs4dO1rEh%2Fykn%2BrgPkf4vTeygS38v54m8Xkjv7By9z3qXb4rx9bvrdvDp%2BoYj%2FAIyH0IifB2cOSuctiL1VEfQgPkmliQFtWHpM9%2B6x%2BWIBiQJ%2F4uyqf4a%2Fnj61%2FW6uHL9QxJ%2FGY%2BhEw8Hbw5p3EviK%2Ff7JD6EB8legkf2Bk%2Ful%2FPE4RI20rw9IqHZ1nBb5Y%2BtB8Hdw6H%2B58RD%2FACiPoRD63bw6fqOI%2FwCMU%2F1cTE5D5M9DTej0e12T1fba3L%2FjiCmKaR1cPyqT361%2FPH1q%2Bt5cOv62xB%2FGI%2BhA%2BDy4dT%2Fc2If4xH0ITOY%2BSRYlikhNGkQT22WbfyorIbkk8sOSJ9PSfSj6y%2FW7%2BHTn4viL%2BMR9CI%2FW8OHX9QxF%2FGQ%2BhED5LrYk1KKk4dkE37LObfyodBJ3B9rsjt2WXv8Ayo%2BtH1vDh1%2FUMRfxkPoQ%2Bt4cOv63xF%2FGQ%2BhAfJdTMoUEDD0iCrmQF%2FJvtDoJGx%2FsckrkWv19vlj60%2FW8eHT9a4g%2FjEfQiVXg7%2BHNXlS2IT%2FlEfQgPkuGZZI0ihyJT29Vdx8sEtSABScPyJB70r%2BePrMPB2cOYNwziMeipD6ERT4O7h1T%2Bk4jPpqQ%2BhAfJrxen%2FsDI%2FGv54lXLyJ8mhSSfWs%2F0o%2BtP1vHh1%2FW%2BIf4xH0InHg9OHQf3HXz6aiPoQHyTTLyXbQZI%2Fd%2FSiboJD9r8n8a%2Fnj61%2FW9uHT9ZV7%2BMf8AYiP1vjh15eJ17%2BMR9CA%2BSfQSH7X5P41%2FPDxeQP8A0fk%2FjX88fWr63tw6%2FrTEH8Yj6EPre3Dr%2BtMQfxj%2FALEB8lfE6eRb2vyfpu588Q8RkP2BlPjc%2BePrX9b14c738Sr%2FAPGX%2BxEw8Hvw6D%2B4K7%2FGH%2BxAfJVMpTRzw9KH%2BE588R8Wp37XZP7tz54%2Btg8H5w6D%2Fm2tn%2FKH%2BzEw8H%2Fw6jlTKz%2FGH%2BzAfJHxanftdk%2FunPniHQSP7W5D7pz54%2BuP1AHDr%2BxVY%2FD%2FAPZiQ%2BD94dT%2FAM21of4%2BPowHySDEjf8A4t0%2F43fnioGJG3%2FFun%2FG788fWkeD94dRv7GVn8PH0Im%2BoA4drW9i6x%2BHj6EB8lCxI2%2F4t0%2F43fnimWJG%2FwDxbp%2FxufPH1u%2Bt%2FcO37G1n8PH0YDgA4dh%2FzbWfw8fQgPkmG5H9rkh%2FnPniOiQ%2Fa3If5z54%2Btn1APDv%2BxtZ%2FDx9CJT4P7h2P%2FNta%2FDx9CCc3yV0SH7W5D%2FOfPDo5D9rch%2FnPpR9avrf3Dt%2Bxta%2FDx9CH1v7h2%2FY2tfh4%2BhAzfJfoJH9rcl8Tn0oiGKd24YkSf8ACfSj6z%2FW%2FuHb9ja1%2BHj6EPrf3Dr%2Bxta%2FDx9CCHyYDMgP%2BjUkfT0n0odDIftZkfic%2BlH1p%2BoA4c%2F2IrH8YH6MPqAOHP8AYisfxgfowHyV6GR%2Fa5JfEv54dDI%2FtckviX88fWr6gDhz%2FYisfxgfow%2BoA4c%2F2IrH8YH6MB8legkP2tSN%2B%2Bzn0om6CT2%2Fsep%2Bwt5Lm%2F8AKj60fUAcOf7EVj%2BMD9GJhwB8OX7CVY%2F5QV80B8khLSiSkjD8jtzBC7H%2BVEympInbDFPHoDn0o%2Btn1AfDj%2BwdV%2FjBXzRN9QNw4ftfqf8AGC%2FmgPkf4vJXv7XKf6LLt%2FOiHRSY%2FwCjlO5W%2BH9KPrp9QVw3D%2FozP%2Fh64m%2BoO4cQdsNT%2Fo8eXAfIoJkvh4ckFffB%2BIxHoZFXk4YkPunfpR9d%2FqEuHD9qs5%2BHuRH6hThw%2FapN%2FhzkB8iPF5T9rcj%2FAJz6UPF5T9rUj%2FnPpR9efqFuG%2B1vajNfh7nzxMOBnhuH%2FQ6Y%2FD3fngPkN0Mj%2B1iQ%2BNz6UQMvJHlhiQ%2BNz6UfXv6hrhu%2Faa%2F%2BHO%2FPERwO8N4%2F6GPH0zzvzwHyC8XlR%2F0Zp%2FxOfSiPi8p%2B1mR%2BNz6UfX%2F6iDhv%2FaQv8Md%2BeJ%2FqJOG79op%2FDHfpQHx%2FEvIFX%2FFaSt%2B%2Bc%2BeIpkpMbjDckPQXPpR9gPqJuG79oh%2FDXvpRMngp4b08sBD1zj30oD4%2F%2BKS37XZT43PpRDxOV%2Fa3J%2FdOfPH2C%2Bor4cP2hD8Me%2BlE31FvDh%2B0BH4W99KA%2BPfsdKK39rcl92588Q9jpQf9G5T74588fYYcGHDgP%2Fl83%2BFvfSiH1F3Dfv8A8Hze5v8Aot76UB8ezT5IjfDUt9%2BdH5YkEjTgo3wxLEdg6d7aPsT9Rhw3f9XbX4Y%2F9OJ%2FqNuHEHUMu2Qf%2FFv%2FAE4D46Jk5JPLDMp63nvnicSVMHl4Xll%2F4w6n8sfYr6jnh0F%2F%2BD1rc3%2FRb%2F04mVwecOar6su5c3%2F%2Bqf8ApwHx18SoxP8AxWl%2Fv7vzxFUjRSjSnC0uFd%2FTO%2FPH2I%2Bo54cLEe5vLbi36Kf%2BnE44PuHMf%2FLiW%2FCn%2FpwHxzXIUNWnThNlNuf5qd3in7G05XkYdlx6XnD%2BWPsj9SDw6f8AVxLfhUx9OJ1cIvDmryss5M%2F41Mf1kB8a%2FYuSJ99oLKx%2FfnBAUumi18PMmxubPOcu6PssnhG4dE3tllJHULG81M8vvm0QTwicOieWWEl65uZP%2FuQHxpNOkNwnDzQ7vfVn8sQEhJA7UJoehxfzx9mTwj8OpIPuYSII5FM3Mg%2FGHIkPCHw5EWOWEnb%2FAMbNf1sB8aE0yQ%2BFhxn1OuGBptOsR7W2732PSuco%2BzKeEXh0R5OWMmP8cmv6yIfUi8Ol9XuYyd%2B%2Fxya%2FrID4yGmSXNOH2h%2FhHIeISYO1Da%2B%2BrEfZk8IPDib3ywlLHmPHZqx%2FzsS%2FUe8N3%2FVbJfhk1%2FWwWzfGsyMkkWVQUj%2FGHIlVJU0nq0MAeeZcMfZf6j7hu7crJA%2BmbmT%2FAO5E31IXDf8A9VVN%2FCJj%2BsgZvjGafT%2F2GT9%2FXEyJGmjyqChW%2FwCuXB%2BSPs19SFw3%2FwDVVTfwiY%2FrIgeEDhuPPKmm%2FhEx%2FWQM3xl9jqX%2Bwn%2FqV%2FNEfY%2BkfsETtb9FLG%2Ffyj7M%2FUf8Nv8A1UU38ImP6yH1H%2FDb%2FwBVFN%2FCJj%2BsgZvjL7G0m9%2FYIW%2F8SuCqdSiUn2DuBzHjCxf5I%2Bzf1IPDd%2F1U038ImP6yJPqPOGv%2FAKqad%2BEzP9ZBGb4zqkpBRB9r6bDn%2Bal3%2FFFMydN%2FYEfhK%2Fmj7OfUecNf%2FVTTvwmZ%2FrIDg84bByyqkPwuZ%2FrIGb4yeL079r1%2F3s2sfktEUy1LHKguD0Tq%2Fox9mfqOeGu%2Br3K5C5%2F%2Brmf6yCeDzhvSbpyvkh%2Fjkz%2FWQTm%2BM3ilKCSn2DXuLXM0okfJEBJ0cc6Dq9Mwv5o%2Byv1GfDb%2FANWcsfOZyZv%2FAKSJfqMOGz%2Fq1l%2Fw6Z%2FrIGb42GQpKudCH4UofkiJptKSkD2EO3aJlR%2FJH2QTwXcNqeWXDPrnZj6cS%2FUV8NhGn3OW7Xv%2Bjpn6cDN8b%2FEaZ%2BwA%2FCHPmiHsfSNNjh5d%2FtvGlfRj7HfUS8Ne98u0b8%2FzfMfTiRXBDw1KFjl6Pw%2BY%2BnAzfHT2Oo%2F7AOfhavmiQ0%2BiAm2Hlpv3Tix%2BSPsX9Q5w0H%2F5fn%2BMJj6cSfUL8NH7QV%2Fxg%2F8ASgZvjv4hRv2Bf%2FDlfRiCJKhtqJNAmvVPK%2BjH2HPApw0n%2FoM8P8ov%2FSiX6hPhs06faXMW%2FwDMXvpQM3x6NOoq%2FKoT5H%2FjT9GIil4e7cPTPqnlfNH2E%2BoU4bf2mTH4e788PqE%2BG%2BwHtPmdv%2Fr3N%2FlgZvj4aXhxXPDs96p239GHsVhz4NBnR6Z4H%2BjH1%2B%2BoM4bv2pzv8YORD6gvhw%2FatPfxguBm%2BQYpGH9yaFPnutPD6MTIpWH086FPfhgP9GPrv9QRw4%2FtbqH8YL%2BaH1A%2FDl%2B12pfxiv5oGb5Dew%2BHbdehVBX%2BOgf0YpexeHkiyqJUCe8TgH9GPr39QJw5%2FsDVf4xV80DwB8OJFva%2FUwe8VBV%2FxQVfIQSVAQAlNHqIHaPHR9GAlcOjlRqiPRPJ%2BjH12%2Bt%2BcOf7D1j%2BMT9GH1vzhz%2FYesfxifowHyJMph1QKRSKkASL2nEX%2BPTEFUzDyv8Amie9U2Pox9c%2Fre%2FDna3sVWfT7Ib%2FAMyJfrevDp%2Bx1c%2FjEfQgmJyfIw0rD52TSJ8f40D%2FAEYj7D0Mj%2B1c9%2BED6MfXL63pw6fsdXP4xH0IifB7cOpUVGn12x%2BD7IgAfyIJzfIsUWh%2FsbUPwkfRioaXh7a1LqA23vMpO%2F3MfXAeD24dRyp9dHoqX%2BxEfrfHDt%2BsK9%2FGX%2BzAzfIz2Hoh%2FuOc%2B%2FD5oiKTRk8pKZP75%2F8A1R9cvre%2FDr2U6uD0VG39CIHwe%2FDsTfxCuj0VH%2FYgZvkd7F0jtp8x9%2FHzQ9iaJ2yE3%2BED5o%2BuQ8Hxw7gJT4hXCE8r1EbfyIK8Hzw7k3EhXE%2BYVAfQgZvkcKZRgCBJToB%2F7cfNFP2Kpeq4lpv74Pmj64nwefDud%2FFcQA9%2FskPoQ%2Bt5cO97%2BLYg9Hsgn%2BrgZvkeaZTf1rN%2FfR80S%2BxNNII8Um7nl79%2Fqj65%2FW8%2BHf8AWde%2FjBP0IDwenDyEhHi%2BIDbkfZBN%2FwDRwM3yMNEpp3ElM%2FfT80QNFp4%2FuOY%2B%2FH5o%2Buf1vPh5%2FW%2BIP4wT%2FVxH63nw8dsrXz%2Fj6f6uBm%2BRzdLpaQUuU%2BZVtt79ax%2BKIKpFK5iUmU%2F4YfNH1s%2Bt28Pe4tiOx7PH2tv81D63Xw9d2JPw9v8AqoGb5J%2BxNK%2FWs19%2BHzQNHpR3TIzf30H8kfW363dw992I%2FwAPb%2FqoiPB4cPgNwMR7m5%2FN7e%2F%2BagZvkkKVSk7qkpq%2F98HzRN7F0f8AWM399HzR9bPrePD39piL8Pb%2FAKqIHwd3DyQR0WIt%2FwD69H9VAzfJE0ukfrKb%2B%2Bj5ok9jaMD%2BgZz7%2BPmj62K8HRw9H9sg9E%2B3%2FVRA%2BDm4eT%2B2X%2BMG%2FwCqgZvkr7H0b9YTv34fNEvsfSDykZ378n5o%2BtR8HJw%2BdjmJfw9v%2BriX63Fw%2Bfq2Jvw9v%2BqgZvkt7F0nWF%2BKTW3Z043%2BSJjTKMOcjOH0PA%2Fkj6z%2FAFuHh6tbXiS%2Ff483%2FVRL9bf4fv1zib8Na%2FqoGb5NCQpI2TJzI9Lv%2BqHiNL%2FWr%2F37%2FVH1kPg3%2BH4i3jOJvw1r%2BqiT621w%2FwB7%2BOYn%2FDWv6qBm%2BT5k6URbxOYHnDsUzR6O5uqWnN%2B50fNH1kV4NvIE8p7E4%2Fxxn%2BqiQeDYyEHKqYo%2FC2f6qBm%2BSk5S6LISMxUnKW88qTbU%2BEOTJCF6d9KgBex5bGNbSapKcoKnRJOy1Reqb776QfeDLrQkoShJ3SpCwq5JsUqHaI%2B0lc8GRkbV6TN0puvYnY8ab0dKJlkqRvfb3oRgDfgmcEyi3UyeOZ9TalXQXtJUB3bItAzfJXolfqS4rU6TUut0hKmzpNQlzv8A3wc4%2BtX1qnC%2F7eH%2FAL2n6MB4KrDSXG3W8cvBTS0uJu2nmDcfBgZvn85T2ta%2FzIjyj%2BljvMSexyP1sn72I%2BkCvBvtncZglJ7%2FABZH0IgfBv6gArMUne5PijfPzdSCJfNqeokrNtht1hTNjqCm7JN4tftVpnfOn1j5o%2Bnjng2qa4lxLmOVOat06pdHVPqRyimPBqUlPLHLg2v9iHPv8mCHzCcwdSHPKNQ9RTFrq2A5VtlxyVXNEt30Kctta1jH1YHg2aGFH%2BzV3Tfb3lNwPuYg74NTDj7ZaexxOFClajZtFx6DogPnCikAobUZRu62xq6gNjbne0TihM%2FrUR9KR4Omhp8nG0wTa11MNn%2BhE7fg6sPX99xo%2BbG%2B0u3uO7yYD5eY0pMrJ4QrE34k2NEorSdPWCibAiNJNNpQNAvfzgx9qK34M3L%2FABDJtU6oY2rTcsl5LriJfokdIEm4SboO0UT4LPJxZJViWujuCVM2%2FwBHAfGZtHK6gLeaNrUOh0p2hSK3ZZ3plN6i4HdlAnuttH1KR4LLIcbLr%2BJCDzs4x%2FVxdpfwaeSss02w3iXFBQ0gISC7L7AC36lAfK80OjlfUbmwnzrF%2FkiY0WlEJCm5s%2FbWUn5I%2BqZ8G5kv2YhxKP8ACMf1cSK8GxkweWJcTj0Oy%2F8AVQHytcoNHvdpE7a52UU8uyJfYGlfC8eH70pj6rJ8G1kuOeIsTH%2FCsf1cQ%2BtuZPb%2FANkuIt%2FOx%2FVwHyq9gaMQd6hfsOpERGH6JZPXqV%2B37HaPqp9bcye2%2FsnxJsnTbWxb0%2FY%2BcQPg2snVc8TYi9Rl%2FwCrgPlf7X6H%2FwB4fG3EgodHHlInD%2FDRH1PV4NjKP4OKcQevoPoRRV4NXKgHq4sr4H%2BA%2FKiA%2BW4olGJ2anzq8rrI29EQNEpJ3Jn%2FAORH1GV4NXKwnbFNbV%2B%2BDP0IpOeDSy0VYIxdWkJHYnoRcd3kQHy6NFpXwUzh9JTAUSlHm3O%2BpSfmj6h%2FW0st739tlW9FmvoRIfBr4FSB0OLZ9BCbGyGxfznqwHy%2BXQ6epWr83k95UiJhQ6d8Lx0%2Fwkx9OV%2BDWwiq%2FwDZnPG42uhG38mPOrwaGF%2FgY0mvWhH0YD5oLodHPkInuXatHP4opih0oc5eZPpdHzR9LVeDQovwMbuetpP0Yl%2BtoUkcsbX9LKfowHzOnaOzMsiWZSZdv4QSSSr0nti3DCEsf0xP3uPqEPBoUj4WNf8AMp%2BjE%2F1tKjftyH3lP0YD5fjB7A3S8R6AYe1GWPlOOH1R9PvraFG%2FbofvSfoxA%2BDPpGtS%2Fbuq6uZ6FP0YJiZjY%2BYPtRleYW59zEfamz%2BqL%2B5j6fDwaNJFtONjsLbtJO33POIfW0KRb%2Fjuu9v1NP0YJ4VXhfMA4QZJv0iviiYYRZA8r5I%2Bng8GbR73ONlW%2FvQ%2BjER4M%2BkDljhX3lJ%2FowOFPhfML2qNhWzpI%2BKJvao39uqPp39bOo9%2F%2BO67f3pP0Yj9bOon7dnPvafowOFPhfMNWFWPtlje%2B14l9q0te%2FSEH97H0%2B%2BtnUT9urn3tP0Yl%2BtoUtP2PG%2F3TKT%2FAEYIzzfNeSYrVPDaWK8%2BG2hpQ2UJWkJvfTYjlfsizvYCoT80qdLUy04tanFpac6pUeZAVy3j6gq8GjSyOrjex%2FvKfowHg0KT244V6mk%2FRgh815TDmGWG9HilTV%2FjCD%2BSPPMYOwbNLW47LVQqUNOkOo028%2B0fTM%2BDRo1tsbrv%2Fek%2FQiCfBo0axSrG7hB%2F7JP0ID5epyzwe2dTKqwk%2Fv2z8sekYIoSRYPVTb903H07%2BtpUT9urn3tP0YfW0qJ%2B3Vz72n6MB8xfaZRf1ep%2F5uJVYNoF%2Bsupn1tx9PPraNAt%2FwAcnL%2FvB9GIDwaFA%2BFjJfqbH0YD5gzGD6UpAT0CnUdgeSCfkjL8L4wxHhSmpo0szTZ6SauWG56VDqmSTchKr30%2FuTsI%2Bhx8GZh0%2FwDTJ37hP0YkHgycParqxk5p8yBf%2BbAcEDMzExN10jDSvMad%2FtROvM7EdwWKNhtoW3HscTv91Hev1snDX7cXfuR9GH1snDX7cXfuR9GA4KGaGJgd6Rhw%2Bmn%2FAO1EFZmYqWsqNMw1bsHsYL%2FHqvHfH1snDH7cX%2FuU%2FRiZvwZ2Gmzf23uq%2FfJH0YDgf3ScT%2FsTh3%2BLv9qJ%2FdMxRfUKZh3lbanBP5Y78%2Btr4Z%2FbSfuB9GJk%2BDZwwOeKD9wPowHAXum4o%2FYzD%2F4B%2FriZGZ2KUkH2Iw5fttTrX%2BWO%2FfrbWF%2F20K%2B4H0YDwbWF%2FhYoV9z%2FALMBwH7qeK%2F2Hw3%2FABefniRWaOLVK6tKw4kf%2BWg%2F0o7%2B%2BtsYV%2FbSv7kfRiH1tnDN%2FwDjSbfvB9GA4B90jEvM0ugfxf8A64qpzSxUnlTMP%2BunA%2Fljvs%2BDawvtbFCvPdP%2BzA%2BDawt2YnV9z%2FswHAJzQxYXel9i8PX%2FAPLAP6UPdNxJ%2BwGG%2FwCL%2FwDajv3621hj9s5%2B5%2F2Yh9bZwz%2B2hX3P%2BqA4HczRr6zdGGsON7ckySrfzomGa%2BJBzw5hk%2BmQP0o70X4NjDatk4qUkd%2BgX%2FmxH62xhm%2F%2FABpVb94PowHBIzXr6fJwxhkeiUV9KJ%2FdbxF%2B1fDP4Ir6Ud6Hwa%2BFuzE6vuB9GJfrbGGb%2FwDGlVv3o%2BjAcHHN%2FEwFhhzDKf8AElH%2BlFP3X8XJ%2BxULC49Mgr6Ud6q8Gvho%2BTitY%2Fgj6MQ%2Btp4ZPl4scP8ABH0YDgpzNzGCzqFGwuk%2BanH6USLzdxopOg0zDIT3Cl%2F6473Pg08MHb22OAfvR9GJPraGGSeti5wj96PowHBBzYxmr%2B4sPI%2Fe00flMQ91XGX63oP8WJ%2BeO9h4MzDN98YvW8yR9GJD4MnDRH%2FHSYvfuH0YDgheZuNHDcNUIf5MT88U%2FdGxvp0fnJbv9jRf8cd9HwY2F%2F26zXyfRiA8GJhntxvNeq30YDgX3Q8ZW8qkfxcn54kVmDjFXN%2BkD0U9I%2FLHfJ8GBhk%2F9Op3%2BT9GIHwYGHezHc38SfoQHAqcfYxT%2FdVK9UgkfliC8fYxUf0VTPwFMd9fWv8AD37e5v5Pow%2BtfYd%2Fb5O%2FyfoQHAAxzi4EK6emEg33kh88Pb3jLXr6Wj8rW8QFvxx399a%2Bw9f%2FAI%2Bzn8n6ER%2BtfYct%2FwAfZ3%2BT9CA%2Bf4xxjICwnKWO4iQG29%2B%2BHt4xp%2Bv6b%2FFyfnjv7617h79v87%2FJ%2BhD617h79v8AO%2FyfoQHAQxzjIAAzlLIBvvTh9KKSMZ41T5VVpyv8nI%2BePoF9a9w9%2B3%2Bd%2Fk%2FQh9a9w9%2B3%2Bd%2Fk%2FQgPn4rGWNTcCq08A9hpqDb8sRTjLGKb%2Fm2kk%2FBKqU2bfGd4%2BgP1rzD%2FAO36c%2BJP0Ih9a7w%2F%2B36c%2BJP0IDgB%2FHeO2pd12XrVPlVpGrVL0iWBNv3yFRpPE1fxhi6fTP4srNRqrzadLSpm6g0n7VCQAlI8wAj6zzHguKG6ytpGP5ka02uQPoRYqJ4KdctPg1bMNhUnfcS6CHLfwkWgOFeF3hhxfxIY79ptFMtIsoknZ2cnJsL6OXaRZIJCRe6lqSkeknkDHc3Dj4MrGeWeadLxvjTGFHFOodSl6lLy9PLjjr62Va20kqSkJTrSkk8yNrdo7HyN4ect%2BH2iTVJwHT3unqCkLn6hNrDkzNKQLJClAABIubJAAFz2m8bNgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgP%2FZ%22%20vertex%3D%221%22%20parent%3D%227%22%3E%3CmxGeometry%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%229%22%3E%3CmxCell%20style%3D%22vsdxID%3D7%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%2C%5B0%2C0.24%2C0%5D%2C%5B0.83%2C1%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22414.91%22%20y%3D%22179%22%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%2210%22%20style%3D%22vsdxID%3D8%3BfillColor%3Dnone%3BgradientColor%3Dnone%3Bimage%3Baspect%3Dfixed%3BstrokeWidth%3D102%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D0%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%3Bimage%3Ddata%3Aimage%2Fjpg%2C%2F9j%2F4AAQSkZJRgABAQAAAQABAAD%2F4gHYSUNDX1BST0ZJTEUAAQEAAAHIAAAAAAQwAABtbnRyUkdCIFhZWiAH4AABAAEAAAAAAABhY3NwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAA9tYAAQAAAADTLQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAlkZXNjAAAA8AAAACRyWFlaAAABFAAAABRnWFlaAAABKAAAABRiWFlaAAABPAAAABR3dHB0AAABUAAAABRyVFJDAAABZAAAAChnVFJDAAABZAAAAChiVFJDAAABZAAAAChjcHJ0AAABjAAAADxtbHVjAAAAAAAAAAEAAAAMZW5VUwAAAAgAAAAcAHMAUgBHAEJYWVogAAAAAAAAb6IAADj1AAADkFhZWiAAAAAAAABimQAAt4UAABjaWFlaIAAAAAAAACSgAAAPhAAAts9YWVogAAAAAAAA9tYAAQAAAADTLXBhcmEAAAAAAAQAAAACZmYAAPKnAAANWQAAE9AAAApbAAAAAAAAAABtbHVjAAAAAAAAAAEAAAAMZW5VUwAAACAAAAAcAEcAbwBvAGcAbABlACAASQBuAGMALgAgADIAMAAxADb%2F2wBDAAMCAgICAgMCAgIDAwMDBAYEBAQEBAgGBgUGCQgKCgkICQkKDA8MCgsOCwkJDRENDg8QEBEQCgwSExIQEw8QEBD%2F2wBDAQMDAwQDBAgEBAgQCwkLEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBD%2FwAARCAGPCigDASIAAhEBAxEB%2F8QAHgABAAAHAQEBAAAAAAAAAAAAAAECAwUGBwgECQr%2FxABzEAABAgQEAgQGCQkQDAwFAQkBAgMABAURBgcSIQgxEyJBUQkUMmFxgRUWFyNCkaHR0hgZM1KSk5SxwSQlNENTVFVWYnKClaKywtMmNURzg4SFo7Ph4vAnNjdFRldjZXR1pMM4R2S08ShmdqW1SFh3hpb%2FxAAbAQEAAgMBAQAAAAAAAAAAAAAAAQIDBAUGB%2F%2FEAFIRAQABAQQEBwoICwgCAgMBAAABAgMEBREGITHREhZBkZKh0hQVUVJTYXGiscEHEzNCQ1SB4SIjJTI0NURicrLwJEVVY3OCwuIXJpPxNrPD0%2F%2FaAAwDAQACEQMRAD8A%2BqcIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgOB%2BN%2Fj%2Fq%2BVuLH8pcn3mWqzS1INWq7iUuIYdKQrxdCFJIWQkjUew9XmDblH65RxOaNQzMp5I8oex8uCPjRGj%2BIqemp%2FOHMCdmnluTDmKaoouLVuT424N40%2BtyA7Sb8JLxOOLA91GmpB33p8tYW5gnTHic8JzxPl9Yax9KabqSm9NlwPTfTHGqzcX7gYpm6uZB9JgO1HfCV8VLTiks48l30fBWaUwm49GjviT65bxXX%2FAOPEv6qUwf6EcqymYOIpCTbk0iVdaYSlCekl0qISBYDzxU91HEf62kPwVMB1R9cy4pxzxox%2FFbH0IHwmHFOtSy3jdm3cKSwbfyI5WOaGIleVKyB9MqmJDmbiXfSiRR3WlE7QHVP1yzis7cct7%2F8AdDH0IfXLuKs8scI%2FiiX%2BhHKwzQxZyDkr5rSyBAZoYt59PKj%2FABdJ%2FJAdVfXLeK0c8bN%2FxQx9CIjwlnFWrljVP8Uy%2FwBCOVjmhi4i3jEv%2BDp%2BaKZzPxeD%2BiGvVLo%2BaA6wHhKeK48sYj1Uhj6ERX4SXiwI6uMFD%2FIzB%2FoRyYczsXE6vG0JNrdWWQPyQOaOMTznQf8AApH5IDq8%2BEn4sxzxgr%2BJmPoRD65VxY9uMF%2FxMx9COU%2FdPxj%2Buh96T80PdRxmP7rT95T80B1inwlnFbpsnFJWf%2FJmfoREeEu4qeRxPv3exDH0I5MOZ%2BMFH9GBJ70tAfkiVWZmMrdaoesMo%2BaA63%2BuWcVx5YiV%2FE7H0ImHhJ%2BLA%2F8ASM%2FxOx9CORRmXjL9lFj%2FAAafmiPukYxP%2FO7gP7xPzQHXY8JPxX%2FtiP8AFDP0InR4Sjiqca6lfuq99QpTPLutojkIZkY1T5NZcHobT80S%2B6Rja9zWHye%2FYfiEB179cl4sf2wf%2FwAJY%2BhEfrknFn2VvV6KUyf6Ecg%2B6Rjf9mH%2FAIk%2FNEpzExornVn%2FAFWH5IDr5fhJeLQ%2BTXFJ%2FwAksfQiX65Nxab%2FAJ%2FHbn%2BdLG38iORRmNjRP%2FOrx%2FfAH8YiT3QcZ9lYd%2BIfNAdfJ8JNxanf2d1D%2FwApY%2BhFRPhLOK5xWhFXUD56Qz9COPTj7Gat1VqZ27rD8kFZg40WnSa3NgeYiA7EHhKeLBStAq6SfPTGR%2FQh9cl4tP2UH8Vs%2FQjjg4%2FxkP8An6c%2BMfNEDj3GR516cPrHzQHZP1yXix%2FZf%2F8AhLP0Ij9ck4sf2W%2F%2FAISz9CON%2Fb9jC1vZ2b%2BT5oj7fsaXCvbBOXHI3G3yQHYx8JLxZfst%2FwDwln6ESK8JLxbDnVrD%2FwApZ%2BhHHwzDxqkaTXptQ7jY%2FkiCMw8ZoBSmuTgB7Li34oDsEeEl4tQbGrgemlMj%2BhE6vCS8WY5VX46Uz9COPfdCxpa3s2%2FbusPmib3RcajnXHztbcA%2FkgOvvrlPFmOdUH8Vs%2FQiqnwkvFqvyZ9J%2FwAmM%2FQjjwZj40ShKDW3ilNrDbs5RJ7o2M%2F2bm%2FjHzQHZP1yLi3%2FAF4j%2BLWfoRBfhJOLZs6VzgSe40xn6Ecb%2B6NjT9m5z4x80TjMLGwSpCK3MpSrmBAdiDwk3Fr%2BvRb%2FAMtZ%2BhD65NxZnlPpP%2BTGvoRxx7fcZjf2dm7%2Br5oj7oONORrs4PQoCA7H%2BuS8Wf6%2BT%2FFjX0IivwkPFs35dQSP8mMn8SI42OP8Y%2Fs5O%2FdxIcwMZ3v7OTP3Q%2BaA7MPhIOLhPlT6R%2Fktn6EPrkfFrfT44fT7FtWPo6kca%2B6Jjb9m5r1EfND3RMbfs3O%2FdD5oDsz65Fxaj%2B6VH%2FJbQ%2FoRFHhIuLa9lPk35fnYz9CONhmJjIA667OEntKr3ikMw8ZXP57zVj2A2vAdp%2FXHuLPQR0x132%2FOtnTb06YkX4SHi0Pkvgf5Ma%2BhHGAzExkOVWmh6FxN7o2M%2BytTg%2FhfPAdmHwj%2FABbpAPToN%2B6ns%2FQiUeEk4tD%2FAHQkemmtD%2BhHGgzFxolWpFdmknzEX%2FFEpzAxiedZmvurfkgOzPrkfFr%2BuUfxc19CIjwkfFqo6UzKSe72OZ%2BjHGSswMZrveuTYubmy%2BZ%2BKI%2B6DjPf8%2Fpvfny3gOzvrkHF2DpLo896az9CA8JDxc9ryBbvp7IP8yOMDmFjEC3szMkdoJiU5hY0P%2FO8zty3F4DtH65LxZfq4%2Fixr6ED4SLi3HkuBf72mtfQji%2F3SMa%2Fs1M%2FJFX3Tsb%2FALOzA9AtAdmnwlXFihSdTaRqPbTm%2FoRMfCW8VX2qP4vR9COLU5l43bXrark0g94tEDmXjg%2BTXp0elQ%2BaA7T%2BuXcVPc3%2FABej6EQPhKuKwdYqSAe6nN%2FQjiwZk452vXZo25XsfyQOZGNCQTWZrbl1rWgO0E%2BEz4pFmyXGie7xBv6EVPrlXFX9qn8Ab%2BhHGHulYyI0GvTiU%2BYxT90nG3L2dm%2FjEB2n9cq4q%2FtU%2FgDf0InX4SbiuRbZBvy0yDZ%2FoRxUMx8ZjlXpwbW8r%2FVEfdIxmdIFdmxp2Fja21u6A7RR4SriuUvTYfxe39CKi%2FCR8WKPKSn%2BL2%2FoRxR7oGMLW9npq172v2xD3QMX%2Fs3NfdQHazfhJuK937GhBH%2FgG%2FoRX%2BuT8VZ%2FudscrfmFve%2F8COIRmBjAbJr06PMF7fiidOYGM0iwrs3b98PmgO2z4SbisHOXa%2FAW%2FoRIrwlfFSlWky7Y9Mi3b%2BZHE5zAxiTc1uav%2B%2Bh7f8Y%2Fs1NfdwHbI8JVxV%2FrZo%2F4k39CI%2FXKeKo8pVv8Cb%2BhHEozAxlf%2B3s593E%2FugYx%2FZ2d%2B7gO1%2FrlHFYOUoj8Cb%2BhD65RxWDlKo%2FAW%2FoRxKcf4zvtXJ375D2%2FYx7K3O%2FfIDtr65PxXnlKI%2FAW%2FoREeEi4sTv4qg%2FvZFq%2F8yOJfb7jD9nZ37uI%2B33GH7Ozv3cB2yfCScWIO8in1yDf0Im%2BuT8Vg%2FuBs%2F4m39COIzj7GnL2dnrf3yJDjzF%2FZXZ37u0B2%2F8AXKuKz9jm%2FwADR9CH1yrir%2FY9v8ER9COJPb7jM%2F8APs790PmgMeYyHk1udH8OA7b%2BuU8Vn7Htj%2FE0fQh9co4q%2FwBaMj%2FE2%2FoRxL7fca%2Fs3N%2Fd%2FwCqIpx5jRPKuTv3yA7aPhKeKlJ0mSQVdwkkH%2BhER4SfirHlU9PrkkD%2BhHEvt%2Fxp%2Bzk592Ie37Gn7OTv3YgO2frlPFV%2BsGvwVv6ED4SripH9wI9Um2f6EcSe3rGNtPs3O27ukiKcd4xT5Ndnh6FwHbH1yzin%2FWSPwFH0Iqjwk%2FFUjy6e0dtW8o2NvuI4l90LHA2GIJ775Epx%2FjVQsquTh3vusfNAdvJ8JfxSLQCmlS%2B5sD4qnc%2FcQPhK%2BKgC5pbHqlEH%2BhHDxxzi9S9aqxOFXO5cionH%2BM0eTWZsefXv8cB279cs4pP2OZH%2BJo%2BhBPhL%2BKFStHsfL388okf0I4iVmBjZaQhVendI7NYh7fMY6NHs9OW7tUB26rwlvFMjyqOj8DR9CIDwmHFErb2Jbv55NH0I4jOPsZjya9PJ9C4icwsbkkmvTpJHMqHx8ucB26PCWcUJ509kemSR9CIJ8JZxSLbLqaU0UJNifE0D5NF44iOYGNVJ0muz33yIDH%2BNQor9nZwqKdNyu5t3XgO3vrlnFJa%2FsZL%2FAIKi%2FwDMiX65fxRlZQilMrI56ZRBt%2FIjij3SMd3v7Pzl%2B%2FUPmiRzMPHTgIXiGeIPZrAgO4FeEy4n0eVQG%2FwRP0Il%2BuccTZOn2AZv%2FwCGT9COH%2Fb9jX9nJz7uJjmFjUo0GuTmnu1wHcJ8JfxPgXNDYHm8WRf%2BZEUeEt4oHPJoTX4In6EcOjMLGoN01ubB7wuAzCxuLWr89t%2F2kB3GfCW8UKfKoLY9Mon6EQPhLuKBI1GhMAXAuZZO1%2B%2FqRw8cxMdKJJxBO78%2FfIl90LHH7PTv3cB3MrwlnFAhQQrD7Goi4Hi6bkfcRI54TDicaQlxdDZ0r8kiVSR%2FMjh8Zh41S30Qrs6E9wXtEfdHxz17V2c65urrjc98B26PCY8Tp5URn1yifoREeEx4nR5VEZP%2BKp%2BhHD%2FuiY3%2FAGdnPu4e6Jjf9nZz7uA7lb8JdxMr%2FwCYZY%2BllI%2FoQR4THiVUSn2Alkkdhl0%2FQjhkZg40tY1ucI7iu8VDmNjUp0GuTtvMofNAdwJ8JnxKrcLaMPsqI7pQfQib65hxLX0%2B15i%2Fd4un6EcPrzHxstOldemyO7Vb8UURmHjhKdCK%2FOpTysF9kB3M54S7iYb8rDzPqlkn%2BhEv1zTiT7MPsH0SyT%2FQjhpvMHG7Ru3XZtJ8yomOYuOVX116cVfndcB3H9c04krXNAa9Hiib%2FwAyH1zTiSt%2FaJgdvWlk8vuI4fOZWOlqCnK5NEgWBuBb5InOZONzb8%2F5oW9HzQHbg8JrxJqGpNCliO8S6foRA%2BE04k%2F2Elh%2FiyfoRxIrMnHayNWIZqw7AAB8giYZkY5AH5%2FzRty6wgO2nPCacSTK9DtElkHzyyR%2FQj0fXNuI61%2Fa%2FK%2Bjok%2FQjhr3R8a9a9ZnDqNzdQNzE3umY5vq9mpm%2FfZPzQHcB8JzxH67DDjB9DA%2BhEfrm%2FEhY%2F2Ns%2Fg4%2BhHD5zLxyRqNdmr%2BqJfdMxxy9nJr4%2F8AVAdwjwm3EgBq9rrB83QD6EPrnfEf%2B1hr7wPoRw97pWOQf7dzfyfNEwzOx1%2BzMz8SfmgO3VeE94jkbqw0yB%2F4cfQiY%2BE74kEmysMtj0y4%2BhHEAzNx2OVbmx6xAZnY7H%2FPc38kB3APCd8RyhdOHGDbn7yPoROPCccR%2FI4bl7nl7yPoRw63mjjpC9Rrcz6CAfyQVmdjlaiVVmZ37gNvkgO3V%2BE84jE7HD7AIO9pcH%2BhFVrwnXESr%2Fo3Kq9LaR%2FRjh5OZuOU8q5NfEn5oJzNxsj%2FAJ4eV%2B%2BSk%2FkgO5keE44il6tOFZbq8%2Fev9iKTvhQ%2BIRlQSvC0tv8A9l%2FsRw8rM3G6yFKrMxcctIAg3mZjZtvok1qZ09xtAdyq8J1xFFGtGE5e3eGwf6Eeb66LxC%2FtXl%2FvP%2BxHEiMz8bo5VZw%2BlCTFNWZ%2BNyb%2BzL9%2F3o%2BaA7hHhQuIcjUMLS1vO1v%2FADIj9dC4hv2qy%2F3n%2FYjh45o476mirPJ0crITv6e%2BInNPHJ3cqzx%2FgJ%2BaA7iPhQeIQc8LsC%2F%2FAGH%2BxEp8KHxCjnhiWAH%2FAGP%2BxHEAzWxt%2ByCt%2BXUERGamNefskrbndsQHbg8KPxAKTqTh2UI8zP8AsRL9dKz%2FAL29rkp96%2F2I4nOa%2BM1c55P3kRJ7qeM73NQB8xZSfyQHcKfCnZ7q3GGZE%2BhP%2BxBzwp2e7SlJcwvKAp5jQNv5EcPLzRxgsAeOoABvswn5onRmxjRsdWdbPpYT80B22fCp55%2FBw3JetH%2BxER4VPPM%2F9GpL1I%2BdEcRnNvG6lX8aaHoYT80FZr40WbmfSB9qGEAfigO3VeFPz0QnUrDUl9yPoRA%2BFSzzSDqw3Jju6nL%2BRHEfup4wtbxpoj%2B8o%2BaIDNfGCb2da35%2B8J3gO2%2FrrGd2rSMNyaje1gkHf7iJk%2BFVzxN74WlBbndHL%2BRHEhzcxkRpLrJHnl0bfJEhzYxjf7K395TAdv8A11TO7sw3JH0Jv%2FQgPCpZ5KBthiUNuZCOX8iOIkZs4wQm3jDB57mWSfjiZGbuL0fp8ufTLJgO3G%2FCpZ5G39jEqq3OzY3%2FAJETHwqWeWr%2FAIrSgHdo%2FwBiOH3M28XOcnZdG%2BrqS6RvD3WsX%2FqrP3kQHb6vCrZ4JAUrCcoBa5JHMfcRBXhU88k2WrC0kEnldP8AsRxB7reLraStkjzsgxA5rYrVzMqfTLiA7gX4VXO9Hl4Yk0%2BlH%2BxEq%2FCs52o54YlOV%2FsZ%2BhHEXus4stpLksRa1jLpO0Dmxi1QIDkuAewS6doDttPhWs7V%2BThqRP8AB%2F2IirwrGdyTpVhqQBtyI%2F2I4lbzcxg35K5T1yiPmiVzNjFyzq1yl%2B8yiT%2BMQHbjnhWM707pw5IlIJBIQfj8iKY8K7ndr0%2B1uRUO%2FQR%2FQjiT3V8Zfrtj8HTEgzTxYnk4xzv9gTAdwjwredqhqThuSIUbAhPb9zE%2F12DOkHScJyRO3f8AQjh0ZvYuSpSguVGrnaWTEHM3cXOk3fZAI8kS6bfigO4x4WHOjyfanI3uO%2B%2F8yIjwr%2BdVwDg%2BUBJsAQQSfuI4bbzbxa2RZyWNr3vKIN9rd0TO5vYrdSlGqWQlIAsmWT2ct%2BcB3EPCvZ1KcUhOE5HUjykgKuP5EB4WDOdZs1hORXvY2uLfGiOGfdYxTb7LL9U7HxdOr44e6xilTZQVyllHf8yoveA7nPhXM7Bf%2BwuVFueoH6ESK8LBnS39lwjIN7fDuN%2FuI4cTmxihABSiTuDe4lkg%2FJEHM3MVuDT%2BZEi1tpZP5YDuP67BnSSVDCcgU9hF%2FoRVR4VjO94ktYSkLW35%2FQjhZObmLbaBMMbCw%2FM4ioc2sUHykSazzBVKpuDAdyHwrWdYKknCkldPlWSo2%2FkQT4WLORKOkVhOQKEmxNyB%2FMjhlGbeK0q1KMqra1%2BhTe1rfigrNvFawUqdllAixCpZJBHxQHdCfCzZvlWkYOkSe7Ur6ETJ8LFnEq2nBkodXLyvoRwoc1sUqIUpUmSFhwEy6eY9XLzRMc28XggpnWE2FrCXRAd2q8K9nE3zwfTz%2FDI%2FoQT4VrOexBwZJE%2BlW38iOFBnBiwgIWqVUkAgDxdHKI%2B7Bim50OSiARY6ZZIv5%2FT54DupHhW86F%2BRgiTV%2B9KvoRD663nJc3wbJfGr6EcLrzexSsqUp6WuvnZlI%2FFETnDiw83pU733YTAdynwrmcV7jCMkfMLn%2BhA%2BFbzoBCfaVK3O42VuPuI4aOceK1eUqR%2FBEmJTnDixWypmXIta3i6bc7wHci%2FCx5whVvahTr9wWT%2FQiZHhX85Fm6cGyRHdc%2FQjhv3XsT6QA3IbcvzEmIrzgxUsWS3JI8yZRIH4oDuZzwsOcLZKfaRT1Ec9LhNv5ED4WPN34OCpE3Fxcq2H3uOGPdbxdcqvK7ix%2FM43ERGbWKU3sJQEixtLJ3gO50%2BFizgPLBEgbqsLKV9CIq8LBnEnngaRH8M%2FQjhj3W8V7XbkzZOkXlwbCHutYq6Po9Mrb%2Fw4gO6keFezgX%2F0IkwbbAFR%2FoRIvwseb7IBcwPIC%2F2zhTf%2BRHC%2FuqYoOx8WBt%2BtxcxH3VsUKASWpVR7NUsFQHcw8LLm924JkD%2FhD9CJleFkzbQ2CrB9NCr%2FAKoq%2FwAWiOGk5uYvR5KJQf4smJPdWxT%2BpyfK36HHzQHcn12bNzY%2B1Cnfdq%2BhAeFnzeKSE4JkCewhav6uOHhm3ilOoiXk7nkfFkm3yRD3YcV7am5M25fmYAfEIDuZvws%2BbSfsmCaaSrld5Q%2F9uJl%2BFozUbIDuCqag2JsXVfQjhQ5u4oUgIMvJkA9suN4nVnBitd7y1O3NyTKpJ%2BWA7mT4WnNdZ6uB6bbu6VX0IiPC1Zq7n2h09XodUf8A244W91jFBIUqXkCAnTbxRNrQ91zFt09WS6vZ4omxgO6R4WbNxQuMAyQHeVL%2FAKuA8LPmuqyW8FU1a%2B1AcVcen3uOGk5u4rupRZk7r5lMuBEnus4sN9Tcmvzqlhf4xaA7pPhac1GiUu4JpgNuReUP%2Fbh9dozWVpCcDU7ft6RRBvy%2FS44XGbmLBfU3JquLEmVTc%2BuIHNrFaiLsyhAN7FgW%2BK0B3WrwsmayEJK8E04XvzcUP%2FbiT67VmkfJwVTVeh4%2FQjhj3W8XHUF%2BKqCuxUsk2iX3V8Sp3TJU4f4omA7vb8LJmslxKl5fySkg3KelULj09HEx8LJmooJtgGnpve3vqjf%2BRHCC83cTLWVrlpE3BSR4sLEHmIkTm1itPZKeqWSIDvJXhZM1UAKXgKmpB5FTyhf%2BREp8LRmgEgjA1MNz2TB%2BhHCQzdxTbrolif3TCVAeoiDebeJUC3i0gfOJRIMB3WvwteZ6ClK8DUxJUdKQX1bn73ER4WbNVZ0owFTie4Or%2Fq44WGbmJbk9BJ7i1vFk%2FND3XMUhICW2E2N7pZTv6doDulfhZ81UHT7Qqbfu6ZQ%2FoRD67Xmh1T7R6Rc3unxlVx%2Fm44VObeJe2Xkzvf8AQ4iPuu1%2F9jqcfOZVJPxwHdf12nNI20YBpir8rTCt%2FwDNwPhas0G9ncC0xBHYp9Vz6Pe44PezYxM5ptKyKLG5tLDn%2BSIqzaxGu2uWk1W5XlUmA7v%2Bu2ZmJFzgqlehUwpP%2FtwT4W7MtzdGBKXbttMLP4m44QOb%2BI3equUkVJ5aTKJ%2BaJhm%2FiW2hEpIITy2lUD8kB3d9duzLJOnAdMOnn7%2Bvb%2FNxD67dmYo%2B94GpSrcwJhf9XHCfuw4sa6rTUhb91LJPqikrNvFKxdTMkjzplUi3yQHeSvC3Zljf2hUy3aS%2BsW%2FzcR%2Bu2ZmgajgKlW7CJlRv%2FIjgv3V8UjqXZIVz1SiDb5IpnNPEgsCmWcCfJSphOn4rQHe%2FwBdqzPJGnAVMt23fWP%2FAG4ivwteZoNxgClgdwmVn%2F244JRmzidNxaUIJuQZZNvRyib3WcR3KixTzfs8TQLQHeX12zM%2Fn7QaZ9%2FX%2FVxE%2BFrzOSpOrANLFud5hdj%2FAJuOChm5iVLQYEvJ6AbgeLJO%2FwAUSe6ziG2lTcoodxlkQHfH12vM8csB0hW2rabVy%2B4idPhbsylISU4DpB1b9WbUT8XRxwErNjEa7FaJI25DxRHKCs2MRBsAtSaQk7FMqgE%2BYQH0A%2Bu3ZkJOn3PKYtR%2B0mlEj1dHED4W%2FMdIurAFKSbFRBm1XH%2BbjgAZu4iBv0MlfvEsgH4wIkXmxiRw6ldFe9yRLo39PVgPoH9duzKDYWrLim2JsCJlZufvcB4W3Mi9l5d09JO4u%2Bu%2F%2BjjgAZu4nA2W2Dtyl02FuW1onGb%2BKDbX0CrG%2FwCh0i8B38rwtWZCEBRy8pgJ7FzS0lPxtxKnwt%2BYxRrOXtLTva3jaz%2F7ccBqzZxCslS5eTVc3sZZJsfiiJzexQSCVSxI23lk7ju5coDvz67ZmSrdGX1LP%2BNr%2Fq4gjwt%2BZClpT7nlN6%2Fk%2Fmpf9XHAfusYjHkpkx6ZZBgvNzE%2BsKQ5LthIHVRKIty9EB38fC2ZjncZe0ob2%2FRav6uIo8LTmSVG%2BXtJ6o3BnFD1%2FY4%2BfKM1cSISGwWCkcgZZFvxRUXmriJxNleKctP6EbuB8UB9BVeFszFbXpOXVKULXBE2sX832OH12vMRRJGXVKSB2GbWf%2Fbj58HNbExQWi60Um23i6ezl2RFOauJ0G4dTzvbxZFvxQH0FPhbcxNQHueUkJ7SZpz%2BriZXha8wwEqGXdKso23m17bdvvcfP4Zu4nvqIlCf%2FCoB%2FFETm9ipSejU3K6L3%2FQqCfxQHf58LZmJzGXVJA%2F8Yv8Aq4k%2Bu35i%2FwDV1SPwxf8AVxwIjN3EaBp8WkyLad5RPL4omGcOKEfY5SnAeeUHzQHfo8LVmJo1nL%2BjbGxAnVkjz7N8oHwtWYadOrLylDVyvNOf1cfP9OcOLEeQ3JJ3v1ZVI%2FJEpzdxUrym5M%2F4smA%2BgZ8LPmINV8vaR1Rc%2Fmxf5W4lT4WrMVSSU5dUo27BNr3%2FAM3Hz8TmxiZKisNygvzAlk2MTqzdxQtJQGpNNze6ZZIt6rWgPoK34WrMNsBT%2BWlMCTtdU4tPxe97wHhb8fKTq9zOlWNtzPLHP%2FBx8%2FRm1ivQlOiUskWHvCfmgc18RptqkpHY6heVQd%2FigPoB9dxx4Tp9zSl37vHV%2FwBXFVPhaMfqF05a0tRAJI8ccFrf4OPn2rNrE6h%2Bh6cNrbSifj5RA5uYtPlCVUf%2FAA6YD6Br8LZmChxKPcypQChe5nnBbzW6OInwtuOxyy3pJN9O08v%2Brj5%2BHN3FahpKJaw5e8J2ij7qWJbqVpl7qNz%2BZkb%2FACQH0KPhbMeC%2FwDwb0nmB%2BjV%2FwBXA%2BFtx2k75cUgecz6xv3fY4%2BfIzbxOLa5eTWB2Kl02MQVmzWySr2Mp4JtezJ3tAfQZPhbMfHY5b0dPbvPL%2Fq4gvwtmP0%2F%2FLejnt2n1%2F1cfPlWbldOy6fIK7N2YgM1a0vcUqRH%2BC%2F1QH0J%2Bu1ZgqsBlxRQSdOk1Fd7%2Fe4m%2Bu3450kjLSjXBIsak5%2FVR89VZoVpeyqZJn%2FBxT90erISfzulBq%2F7OA%2Bh6vC345R0g9zKjK6IAqUKmvSb8rHot4iPC3Y5IAGWdFud96k4Leb7FHzqOY1WPlSMsfS3EnujVT9ZSv3uA%2Bix8LhjhSUrbyyo5CrkD2SXf4uiidPhb8a6QVZaUjc2Nqi5tt%2Feo%2BcSswKko3LDF73HvXKIe6BVP1ux9wYD6Pq8LZjUeTlxRlWNjapLNu4%2FY4lT4XDGilaV5bUdH76ort%2Fo4%2BbjmN59xCkKl2BqASTo3IEeVeKp9flb%2FwAGA%2Blx8LbjNKSs5c0TYXsKku%2Fo%2BxxH67ZjLpA37ndE3F7%2Byarcr8%2Bjj5lLxDOK7O2%2FKKBqz7h66doD6c%2FXb8ZWBOXNEBsSQamser7HE6fC5YvSetlvQ1C1%2FwC2a%2F6uPmH7IudmoeiIGfePa5AfT8eF1xUVIHubUGyxfeqOben3vaJvruOLLqHubUDq%2FwDerm%2Fo97j5dmoTI5FXriHslM9xgPqMPC4YsWoJRlrQCT%2F3qv8Aq4mR4W%2FFS16Pc5w%2Fe5FvZVz%2Brj5b%2Byc1tz9QiKZ2YUTbpCQLm3dAfUf67di61%2Fc2w%2Fe9iPZZdx%2Fm4m%2Bu14tJt7nOH79p9ll2H%2Bbj5aLqbmkJ61xvEzdQfUQTq1c4D6kK8LXi9LXTe5th%2B17WFWXf0%2FY4L8LXisAKRl3h1QJt%2FbZdx%2Fm4%2BXPsi53qicVB3sKjAfUVvwtOLF6bZeYcTfmTVl7d36XEU%2BFqxcVb5cUAC9t6qv4%2FscfLk1B%2F4aFiICfX2BcB9S%2FrteKtake5ph3qgG%2Fsyuxv%2FgomHha8Thzo15a4f9Iq6yPj6OPlp4%2B73Kh4%2B%2F2BUB9SVeFrxQG9fuZ0AkmwT7Lr28597iP12rE%2FX%2F4NsO9QX%2Ftw51vR71vHy0M4%2BTfr%2BqHj7o7FfFAfUseFpxQpGv3NsOeSFWNYWDv2fY%2BcQ%2Bu2Yl0avc1w%2FfVpt7LuX9P2PlHy18fe7lfFD2QdHYr4oD6lq8LViXWoJy2w9pRa5NXX1vR73vD67Via6f8Ag3w7ZQJH57ubW7D71tHy29knuV1fHD2RmO9UB9SV%2BFqxOhOr3N8OEbcqw52%2F4KJh4WnEg6TVlvh89GARarr69%2B73vsj5ZGpvdpPxQ9lHe8%2FFAfU367PiW6U%2B51h26u32XcsD3H3rnEw8LViE2%2F4NsO7kjesuDcf4KPlkmpv9iFGJlVN3TulQ9UB9S%2FrtWIffD7muHuoLj8%2BHLq8w96iP12nEBcS37nGHEhSAvUqsuAAn4J965x8sPZRz7VXxROKmr9TPxwH1LR4WqvrAPub4eF%2BYNXc2%2FwA1ER4WnEBv%2FwAG%2BGxpJSsGtuBQI83Rbx8sjVZj4F4lNVf%2BGi8B9UHPCzYjStaUZbYcXpFwfZlwBXo96h9dlxLpSRlrho3Ok2rbhsfvUfK72Vc%2FU%2Fkh7KufqfyQH1UPhX8VWujLHDa%2BrqFq4vfzfYucSp8LBi1V%2FwDgvw1sbbV1Zt5z71Hyt9k3juG%2Fkib2Ve%2B0PxQH1SPhXsXFtbjeVuHFhCiLezi7m3m6K%2Frib669i0hxQypw4ehSFL%2FsgUNj6Wt4%2BVyaq92oPxxBVUcPePXAfVJrwsOJ3SB7l2GUg9pxCvb%2FADMQHhYMWqQpacpcPHTe4FfXfbzdDHyrNSeJupsKHn3iYVJQ5NesDlAfVL67Bi0uJaTlLh1SlJ1C2IV2%2BPoYnHhWcaFBd9yLDYbC%2BjKvbIeffboeXnj5V%2Byh%2B1v6RERVDfZv4hAfVH669jHe2UWHDY2H9kShf42YijwrmM1nScocOJN7b4lP9VHyxFSctyMU1VJy%2FIwH1UPhWsZJWpJyhw71ef8AZGf6qA8KzjYgH3HaBYi%2F%2FGMjb71HysFSX2oB%2FHE6ai4dw1aA%2BqI8K1jS2r3HKFuQB%2FZEd%2F8ANRBXhWscBKj7jFDHRi674j5D71Hyx9knftDEwrDqO0iA%2Bp%2F11jG2rT7jNC%2F%2FAOjP9VEE%2BFaxobXyVoxv3YiI%2FG1HyzFcmPgqUPSAYrpxC8n4CfuID6gT3hacRU6VMzN5N0xOl7oVJTXiojq3v9i5eePE14XyvutqLeTVMUq402rauXn95j5lT1Wfn220KSkJbJIsgDePCSu%2Bo2H74QH1MT4W3E5Rr9xam27zXCP%2FAGo2VkZ4TjC2Y2OaZgTMDBJwu9WZhEpJ1BmeTMy3TrIDaHNkqQFEhIVYi5F7DePjahSFeVpPoEZBhGZdla5IvSqy043MNqQpHMKCgQR64D9KUIQgEIQgEIQgEIQgEIQgPzu5%2Bf8AKrjf%2FwDeSpq5%2FwD1bsandjaufm2aeOB9riOp%2FwD3bsaqcgPXQ6Y5VZhEuhxtsFY1uubJbRzKr%2Baw27bxkntfkEbBT7g1eWQE3HmHZfnHnw115DpPtfe%2Fii6wHiRQaPyWJjn2LHzQ9rlE%2FS2ppSvOtPzR7eUQ1%2BfTAeH2uU%2F7Rz40xA4ZpZXbQ9b98n8ce%2FX%2B6vEOkMB4fa1TUpult0G%2FMrSYmOH5EHT74R3C0e4dbY374lPO4BHogLecNyF%2F06%2FnKbRFOH5BJsFL%2BNMe1RPK8EuFOxV6oDxOYekV8tZ9Fop%2B12QR5Rc9ZEXLWPPDWO8%2FHAeEUGUt8Mj0iBw1LPHZDqSf3YsI9oNtwSPODeI9JfZKtQ7Cb7QHgOGpZHV64I7dSYm9rkoeaXFehSY9wK%2BwD1fjiKSRcqUogeYnfu23vvAWxeGpY%2BT0qfWkwGGpUc1OH1iN24s4Ys4sD5dPZn4soMpSaSwwy%2B9LTE6gVBtDywhrVLi6klRUDYm4G5tGpO2At5w1LadmXLd%2BoRAYZlVHcuJ7t0xckk32JB7jygpVjyue%2FugPAMLS%2FwBu58aYmOGJZvVrLl%2Fg7iPaHF90XSh0asYkq0nh7D9MmKlVKi6liTk5dGp19w8gB3cySdgBcwGOKwywdwtwesRD2uS%2F26%2FjTG0s48ncU5JYjp%2BFcVVSkzs9UKY1UymnP9KJcLJHROciFApO%2FIixFxGBkKQhala1BHWIHPaAtQw3L%2Fqiie0ak8omXhuWCdnFJ9Yjb2POH%2FHGAMC4azMmXJGq4bxLIsTfj9NdLrcit1N0NPm3VPZqF06ri9xHjyfypnM3cSTeGpbElGorspJGcDtSe0B%2F3xKA00Oa3LqvYdgMBqhWGpU8nV%2FEIqt4WliLl1fyRuDEOQeOqLnH7h9PZlq1iF4sLllSSz0TjLrQc6VSlAaEpTfVq5WjJcyeE7MPLXCE7jdVXoOIKfSV6Ku3R5rp3qeOWtabC6QTuRuOZFoDn32rSdvLc%2B6EUzheT%2FXDo9QjbNQyVxRT8mKVnqtTT1Aqc%2BqSWyyFLflE9IW0PuAC3RrWNIsb3t3xHNbJDGuTkhhmaxmZNp%2FFEk5ONyrDup2TUgp1MvDkFgLSdrjcjmIDUvtXk%2F1y78QiY4Wkh%2FdLo9QjamBcqVY5ewhSG8VUmh1DFPspOrerD3QykpT5RSW0OFXNTjrgdCU9yB3x780MhsW5bZhUzLhxbFeq1blmJiminaiJjpVFKUgKsQbi5v2bwGnBhWR%2BFNPn0BMQOE5E%2BTNvD0pBjpTFPBfmnhfCFQxIuo0GpT1Ia8ZqVHp03001KM2uVEclEC5IHcbXjE8ouHbHGcVNnsR0iepNFw9T3Ogdq9WmOiYce2u20OayLi52AuO2A0ycJUscpqYV6gIiMJ0z9UmfjEbZx1kbjvLzMOlZa16WlzO116WRSp1t28pPNvuhtLiF9gSo2UDuPPcRfn%2BGTMKWz4ayGL0kqdeZ8eRV0lXiIp4Tdc2VWuEJUCgi2rVYW3gNE%2B1Km9r8wR3XTEfarR7eVMfdiM4qGBqlI5oDLB9aXJ1OIW6Atxs9UqU%2BlsuJ8wBKvVGw8EcLONc0qVXcWZd1Wjv0CQq9Rp8h7IVBDc5MtyqiAtTaR1dYAIvYb%2BuA0J7U6P8Aq0x90Pmh7UqP%2BrzH3Q%2BaNj5XZPZg5x1d2j4DoZmlSiQucmnlhqWlEk298cOwJ3sBcmLxm%2Fw%2FY6yTl6VN4um6LMM1hbrUuafPB9QW2AVBabApFiLG1jAaiThGlJN%2BkmSP36fmgrClKPJ2YHrSY2RlDlZXM48atYIok5KSMwuTmJ0zM2FdEhDKQSDp3ubgCKGa%2BWtbyix5PYCrc3LTkzJsMTHjEqSWnEOthabX3BG4II7IDXhwtSB%2BnTHyRJ7VqVqv0kzb98IuR5wvfY7DvgLf7VqR9tNfdj5oicKUwm6VTAHcVJP5I91mx8Mx76DSJzEVcp2H6epAmqpNMyUv0iglHSuLCU6lHZIubk9ggMf9q1L%2B3f8A5MRGGaUnn0x%2FhAR0x9Qpn344ZFpeEH3tam0JarzSisg26ot6PjjnybZdl335V4BLss%2B5LugKBAWhZQoXGx6yTvAWo4aphUVfmgX5WUnb5IlOF6ceTj49JEXCI3PeYC3e1enfqj%2Fxj5oj7VqcnrXfN%2FOPmi5es%2FHELm%2B5PxwFt9q1OP6ZMfdJ%2BaI%2B1GS7H3vjTFx9Z%2BOI%2Bs%2FHAWz2rU89UKmCR3FMS%2B1ST%2B2f%2B6EXX1n44hfz%2FLAWoYTkl8nXU%2FviIj7UpAc3XT6FJi5gk9sTjftgLT7U5Hscd9akw9qcl%2BrOD%2BEmLtb0%2FHENxyUYC1DB0r5RmHLHziI%2B1Cnp3U8%2Br0ERd0qtzXEdY%2B2gLQcIU0%2BS6%2BPSpPzRL7T5D9Xe%2BNMbfytyEzIzekKhV8JSEg3TKYsNTVRqU4mUlUOG1kdIvYq3Gw74seY%2BWeNcp8SKwrjmjKkagGkzDYCwtt5lXJxtYNlpuCLiA18MHU%2B277%2FxpgMI0sE6n5nzWUkWi7rUexUUxzgLanCFN%2BFNTA9C0%2FNEfahTP13M%2FdJi6iJ0oUSbDkLkk2AgLR7Tqb%2BuZn7pMR9p9N%2FVpj7tPzRtw5E5goyYmc9J2TlZHDjU1LsS7c0%2BG5ucbdc6MPtNHdSNXbcEi5AIEa67bQFo9p1O%2FXMz8afmh7T6d%2BuJj40xtnLjInH2a%2BFcT4rwQxJTwwoWhN07p7Tr%2BtJVdlq3XASknsvyFztGBy8q5MTTEqLNmYebYSpw6UoWtYQNZPkgE735WN%2BUBYhg6mjk%2B%2F8AGmAwdTR%2BnzHxpjeecXDVjXJLDknizE9aw9P02dqCqalymThe0OhpThUTYAo6qhcdoi%2B4U4L85sV4Xl8StS9Hp66gx4zT6dPTyWpuabIulQR8G4II1EcxAc4e0%2Bm%2Fq8x8aYe02k9szN%2FGmNt5b5F4%2BzPxLiXCGH5JmWq%2BFJR6ZqEpPOdC50jbnR%2BLoFjd1S9gDYHvjz0XJjG2IcsMU5tyUo0zQ8JudFNiYc6N55aXEoeS0j4Ra1DWLi3LcwGrPadSxymJv7pHzQ9p1M%2FV5v7pHzRllGpUvPU%2FE9YqE4ZSSw1QnqqV9GV9PMl1tmWlv3PSuO%2BV2BJjaWZHC3mFlZl2nMev1XDs5INzEqzMt0yfEwtgTAHRrNgARqIBsdrwGgfabTf1eb%2B6T80TjB1KA6z038afmjoDLnhLzczMwlL4zpLdIpshUNRpoqc4GHJ5INtaE28gnkTzjCqTlDmNXcxHsppLC8wcWSjrjU3T3FJT4uGwFKcUs7BvSpJCuRChbnAa09p9H7Hpv7pHzRH2nUe36Jnr%2BlFo3lmnwwZl5Q0VGKMRN06fohmG5V2oUuZD7cq8s6UpeGxRdXV1WtfY2jH8QZO4yw5lNhzOealW5jDuI3VS7ZllFx6WcK1IaDqLdUOqQpKTvdVhtcQGrPadSe2YnfukfNEfadRv1xPfdo%2BaNnZr5MY6yamqDJ46lpWWfxFTvZJhph8Oql0hYSpl0DyXU3F072vzj14CyQxbmbUsPYewU9Kv1utYZmcWzUvPuiVak5ETKmpfSs36RTiE9JYDa4HngNTe0%2BjE7Pz33SPmiYYOo%2Fwn577tHzRsTF2VuNcE5i%2B5VWaT02JHFSwl5WSWH%2FGvGEami0U%2BVcA%2Bixva0ZvifhFz2wfgup47xFh6Qk6dRpNdQnkLqLZfal021HQDuoXF0g%2FHAaE9qNC%2FVp%2F7tHzQ9qVB%2FVp%2F7tHzRd5dlx99pltIu64hoEmwBUoJF%2FNcxtfO7hsxzkRSKXWsWT9HmZaqzrlPR4jMFxTbyG%2Bk6wKRYFN7eiA0j7UaEf06f%2B7R80Q9p9F2PSz%2FAJ%2FfEfNFwc6h%2B2iHSQHg9qdBH6bUOX26OfxRD2pUP9Xn%2FukfNHuUq8XvB2E8S44r0rhfCFEmqvVp1RSxKSzRWtVhcqPYlI7VGwF4DFvalQzt08%2F90j5oDB1H5l2eP8NA%2FJGyMzcp8e5PzdMp%2BYFDRTpmry6pqUbQ%2Bh0rbS50ZvoJsdW1oztvgt4lHz7xl%2B2vq69qpLctOrlrvy%2BaA599p9H%2FAFSe%2B7R80PafR%2F1Se%2B7R80XJzrub9XmlWrY7GxB9BBiXWYC3nCFFBPvs992j5ol9qVEHN2e8%2FXR80XBS77RAknkBvAeH2p0a32afA%2Ffo%2BaJkYUofY9Pn%2BGj5o9Z5b9nniLagPIFoDxnCFF1X6WoWvy1o5fFEpwhSP1ae%2B7R80XLWo81GIqJ7EA7W3EBbPanSEnd2f37NSNvkgcJ0dVrOT33aPmi46lnYg3PMjuiFljt%2BXnAW84QoyRqLs8P8Ij5ogMJUwA6nJ4nsOtA%2FJFwSu%2F23riJN%2Fh%2FyoC3DCdJH6bOk92tHzRH2o0o8lzv3aPmi49kTXbbb6RxaU9XyoC1HB9PPkPTQ9Kk%2FNETg%2Bn7aXpoWG91p5%2FFG36tw45yYfy6mM1cRYSepVAlWmX3PHHUtTIadWlCF9AevpKlDcgbbxccBcL2dGZuD5THWDqFIzVHn1zDcu47UW2nFKZcLa7oUbgagQL84DSAwhIq6pff9akxBWD5FOwfe%2B6TGyM0spMd5PViQoGP6YzJT1RkjUZZLMwh5KmAstlWpJsDqSRaMJ1ud0Ba%2FafKcxNPfGIDCMoOc06fWmLpdw9ttMRG8BbPalJ%2Fq7vxiJThGXt1Zlz5I29k3kLjnPGZqzeEGpKXkaHLOPT1Sqb%2FQSbTiUFYZLlj1ykE27ALm0a5l3C%2FLtPoOhLqdWlXOAtKcJyva6791%2FqicYTljyecH8IRszKLK%2FEOcuOZXLzDdQpknUZuVmZtp2oPdG0pLKQpSbgElRuLADvPYYx7EmGq7g3EdRwrielzFNq9JeLE3KvCxSexSTyUhQ3SobEQGK%2B1CTO5mHfjES%2B1CU%2FXDvxiN%2By%2FC7jibycezpla3huYpkvSTW3JFmd1zaZYXuCkCyXBY9QkHaPNlBw0Zg5z0SZxRQl0ulURiZ8TbqNVmOhamH9rtt7EqIuLm1gducBo32oyNrdK%2Ffv1D5ogMISf6s98YjcdQyJx7Q83KPknXKexJYhrsw01IuLeBlnmXNVphLg2LdkKv2i1rXi5Yb4Ys0sUZt1rJyRlZGXq9BQqYnJmamOjkxLHZh5LljdLxUkI23JN7WMBotzCciR1XnvjESpwjKW%2BzvfGIzPCOHJnFGM6Ng0lUq%2FU6mmnuqIB6ABZDy%2Be%2BhCHFW7dMbOwDwt48zKyyVmrhav4dcpLzFQnJGUenQiddl5ZawC4gAhtaw2SEqPd3iA0B7UZH9XmPjER9qdP%2FAFeY%2BMRuPJvIDH%2BeEvOVPCTUlKUqnlKJipVR7oJZLik3S0FWOpdiLgcri8eDMrJXMTKrGkrgPFFEC6lUtBpapNzpmqiFrCAWFDyuuQkjYg8xAapVhKR7Jl4ekAxEYTkRzmHj6hHSmIuCvO%2FDuE5vFCpCkz8xTpUzk5R5GeS9UG2kpKlEN8lEJBNgbmxteMCwJkzjPMbLvF2ZeGGpeYpmDWw7NtdIfGHwGg8sMotdZSzdwjbYHtgNUjCcj2uvn%2BEkfkiCsIyR8l54ekpMbWqWTeLqVkxR885zxRugVup%2Bx0o0pwiZUlWro5jRb7EsoVZV99jaxi1YawHP4vkae3R3VOVquYlYwzRZDZCZt5TJcdWp1XVQlsFob3vr7LQGvPabLfrlz7oRH2nSY5zD33QjbeceReYGRc1SmMfSsigVgPiVdkpxMwguMqSlxtRA2V1gQO0GMwwlwW8QmMqTKVeUwlKU9ufCVSrNSn0SzziFbpUUq8m%2B3lW5wHO3tQp%2F6tM%2FdJ%2BaJDg2V7Jl31kRkcwy9KTTsjMNlD0u85LupuDpcbUUqFxsd0ncbGNqz%2FDVj2SyOZz5XOUhVGcprNYMp4wfGkybrvRpXp021XIJTe9t4DQ4wbJ%2FCmnPjETJwfTh9kffI8ykxd3PuYpFfrgLYrCdP5JffHpKYgnBsmrfxl7%2BTFz3UE6%2BV49lLp85VKhK0imST85Pz76JWVlZZBcdfdUbJSlI3Jv8kBYvaXJj%2B6Hv5MSnCMiNuke%2BNMb0xnwqZ8YAwnOY1xHg9KKZTWTM1BEvONvTEiyLEreaSbpABuedhvFPAXDBndmThqWxfhXCIXSZ9JXIvzc03LeOp%2B2ZCyCtJ3seUBov2oyROzr3xpicYNk%2BfTO%2FGmMlxBQa5hetT2HcRUuYptUpr6paclJhOlxh0c0qHrBuNiCCDFsuRvAWxWE5IGwW9t6IlGE5Mqt07o%2BKLqFqO5X6IHTbUT6YC1nCUnyDzvyRKcIyX6s98kXQr7lG3piS55hcBbThKU7HnfkgcIs72dd%2BSLkHF38oxU6ZY%2BGYCznCTHwnnB8USHCTPIOr%2BIReVLJ3KrxDUoch8sBZxhFu32VY9IEPamP1VXxCLzqfcWkG4HpjJMB4AxhmdiiXwZgekOVKrzLbjrcuHUt9RsXUoqUQAADzJgMAVhP%2FALU%2BtIiX2rqT%2Bm%2FyYy%2Bt0mr4dq9Qw3XpJySqdJmnJGelnLa2H21aVoVbbYjmNjFusP1RUBYfanr%2FAE3f96IlOE3E%2Fp9%2FUIvylKG2s%2FHENShyN%2FXAWL2rL%2FVfkEPas4f035BGyctcrcfZvYiOE8vKCqrVZMuubMul1LdmkWuoqUQBupIG%2B5MYvMNTMrMOykyw4y%2FLurYeadSUradQooWhQPIhSSCPNAY6cJun9MT8USnCT%2F6qn4oyAlQ5qPxRIXCPhGAx9WEX7%2FZEfFEycHvKHUIJ8wi%2B9K59sIm1ufbmAx72ozQJBUkemJfafMFX2VHxRkYU4Sev8cQ1uA%2FZIDHvabMj9MSfVBWDXSN1pvseUX9RcvfpFJ27TESpwDyirbvgMcVhGYHII%2BOKZwrNDkG%2FjjJelcPwflgCs%2FAEBjPtVm%2B9ER9qc53D5IyW2%2FWBHoVEyilI2Kh%2FCvAYx7UpoDcARIrCs6Ds2D37iMn6RI%2BER6YmDiexfrtzgMT9qs9%2BoiKiMJTxH2MCMoUq24cvcX2Vy80SiYUjZKgb%2FwC%2FbAYwcHTfPSPiiHtPnSCA2SfRaMpS%2B4o6lKIsexUR6Z0kFDy%2B3nAYecIVMWtL3894ijBtTXuWEp85PKMyS4%2BeTi9%2B%2BJtavhkkwGGHBs8PK0%2FHE6cGTp5afjjLlP220iIdIpXJYHrgMWGEp9vmlB9ce6QwVVp50sS8s444kaihmXW6oDleyATF799%2FVB8cbl4Z65iPDc1m7XcLVqap1XpuVVVnJSbll6XWHUTcqQtJtsbXF%2FPAaSeyyxNLJKn6PUUJACio0mZtY8t9HbD3M8TWSr2GqelR0hXsTMWv3X0RuSn8SnEfNNhx7P3HN2z1QmoNgev3veK6uJDiStpTn7joC1t55v8Aq4DSy8scTo13o1Su2nWoexUxdKdtyNPnEQGWmJbal0ioti4F10t8c%2BXwY3TIcRmfr%2BJKdTa5xJ40olKmZlhucqb06HESTCj13ihLepQSLmw3MbC4jMw88Mm8bUOk4O4nsxKzSsQYYksQys1OzDbLmiYUsAFvQQBpSlQ7etaA5TOW%2BIk21UuoC%2F8A3Y%2Ft%2FJin7Q6tqU2JedK0X1J9jXwU%2BkFO0byHErxHLbDXu9Y2UlKtQ0zzQPx9Fe0PqkuJG9%2Fd4xte1r%2BNs7%2F5reA0YrAdZb2mZWca3A61PeHPl8GIt5e155OpqnzygRqBFOeNx3jq7x15w45n5s5uYkeouKOJHNj2VemZWVk6Zh%2BnNTzyZRZCXqjMOqQG2pZpSkhfwt72sY8OX%2Be%2Bf9K4nsM5cVbiArGJKLKZgSlGdmW1sqlKlKNzOgqSkNghKgmxSDzvAcjpwmtSdZqTVj2hpRiBwms8p5J9LChG3cQZSZwv16tzbeU%2BL20vVWfcuKI%2BRZcy4oEHRa28WwZN5zKbLoyqxsUFOrUKJMWO1%2BeneA1r7Twec%2Bn7wuHtPH6%2FT94XGypbJzOd3V0eUmN7I7RRJi5%2FkxUOT%2BcqRdWVGNRY6T%2BcUwSD5%2BptAaz9p4t%2FbJH4MuIDCH21QT6mFxs73Gs5VBSm8p8aK0p1W9gpkXHm6u8SnKnNtYUXMqcaAJQXCVUOZASkC5JOjsEBrb2pd1Qb%2FB1xVlsDz86sMU9app6yllpiTdcWEJF1K0pSTYDc9wi7MP69Lja%2FK8mO7OAbLtNIwnVM16vh52VxDOVIytEqL6VJWKcGNDpZHItrcKgSQb225QHz3ThBxYQ41UpZxtwBSVoaWpKgeRBAiUYVcKyEzrCkjtDS946R4wcsZTLbOCcXhjDC6HhitycrO00MMrTKKmCk%2BNoaUbgELsooB6urYWjRfSL5%2FwCv13gLOjBzir656XTb%2Fslm%2FwAkUfaqv9eS33tfzRfVvvC6VGxKgo25gQ6T3xf73%2FcgwFl9qBKL%2BPy2ru6FfzRL7UV2UFTsskDt6JfzRfUKWQk3OoAnnziLi1rc%2ByL%2BKAsvtOFv7ZNct%2FzM7sezs3iPtOI%2F5yl%2FvLnzRd0F083DFXpHCoJ6QwFmRg15wpQ1OsLWo6UoDLhUo9wASSY9zuWWIWUrU5T59PREBwKpE2nTfle7fbG7uEtyZa4i8HOsEhbXsg6hQSDoUmQfKVbjYgi4PYYyVOYfEa%2FkBQ888K8SOMKnTWFrpWLZGaebZfpc90mltbSlJPTtKBTyOoXB77ZrKzm0jOJ8PJns%2B1q294ixqiiYjOcts5bZyiNk8rmGZwHVJWXRNTKVNMOqCEPOyT6G1KPIBSkAXMeM4Qd5ePSmrusu%2FwCKOmsIZxZnZoZS53SOO8xqvieQp2D5SaaZnHW1oYe9kmQlxGlIssC%2B%2FPeNFlblvLitdnEUxXTOcT5sl7G2rrqqorpymPPn7oYwcIzg2Q9KqT2m6vmgnB02d%2FGZQ%2Ba5%2BaMjSHlndRV6IBTjaj1V%2FHGNnY8cGzxFuklU%2Bs%2FNEEYOm0nrOyp9Z%2BaMh6aZJ6zpMTKfeSNlGAxxWFXkq3XKenWfmiJwy4N1rlrd%2FSH5oyNMw7putw%2BiKb7yym5WPReAx%2F2tOlOpK5W45guf6omVhxa%2FJblyQd7LHKMlkUpmkO9KogoQCn5jHpbkkISdThsTz0%2F77QGIe1h8HWlMupO%2FwxEDh1aRqUhhI71LAjJ59tco40jWVJdTqTtbTvYxt%2FKafpeFMpKzjRzC2CarU3MaUbDyZ7FsmqZkaZKTLLqluKAI0gLCSpW9gk7Ramma54Mf1lrYre1iws5rmM9mr0zl73PHtfUeSZU%2BhwRFzCs2pHSIZY0eZUdK48zXxzlpi2cwXjTILJ9qdY0vNPtYfUuWnpRwEtTMq6F2cZWncEbjcGxiw5xT9KxDl9lhmHK4Mw9hyq4hlqw1UWKGwqXlXky80lDKy0omy9NwTfeMs2GWf4UdfviGvZXybSqmKrOYidUTqmOXwTPgaEGGphHU8VbWD5JCufnib2pzarapdoX527IyPprHUbgi3bAzKex1QjA3WNKw242vQZRGrVa%2FZvEThV7tlm4yRub66hr%2FAIXKKwnOvpWjWmxO1u6AxRGGnydHiyeQ5Ed8TjDT6OoqUTfvuIyLxsrICAUknf1dkeiXbm56YblZKWempl5WlthhpTji1dyUpuT6oDGPau%2F%2BtEfGIqJws9baWbG1%2FKEZNJydTnq4xhmn0ucmq3NzCZNmmtMqMyuYUQA30flA3O9%2BXbG8cPZX8PWEMbyGD8888EJqbK1IrEjQ5Va5CSe0byz1SF0odSeehKgDte8BzD7AvDypVKfSYgmhvKveSbMZ7jMYWkMXV2VwZWXqnhyWnnk0mdmUhLr0qD1FLAsL27bC4sYsgnNLXSCx1fCTyPcYDHnKE8gp0yjaR6R%2BOJxh%2BbUP0CjnbdQG8ZAmcK9V1BW21x%2BIRWanEqUlAUVAqN1AD1bd%2FfAY4MMzp%2FuBr1uJiU4ZnTqtItDSN7LHOMxaprsw0p5Lii2kgElNggkcvP6IgqRV0Liw99ibUtPV8qxGxJ5bQGGHD0wkALlmtjfdaYnGHlFJuzL3tyCxzi%2FFxRPWTba4N%2B2Jw4kJF0q9IPbAY57XnPtWfR0gh7X3v1Jv7sRkPSa%2BxXzWibpj9pAY97X1kEBhhR86hEEYcd6XQmVbse24i%2Frc3UtAIAG%2B8SqdQEk3JJHmgLSMKvlVugY5X3cA9UVU4RfV5LMof8MiMlVT%2FeEuomDcgGxRyitLUlcwtLTcwu6l2uEXPogMW9qTw5syn31MTowo%2FwBjcmB%2FfUxtrIpzDAxw61jHBdQxLKv0qbZlpaSpjtRLE0dBRMOS7S0LWhICxcKFioE35R0y%2FwDUlL9%2FmOGDH6V77JwfUEg9%2FwCm77wHBq8L2RpKZIK7%2BlH5IkThW%2FlOSo8xXzjtDH7fC47hCqTWGsh8Z0pySpM6C%2B9haoslp1aPeJhUwXdDaW3LFRWlQKbjbnGneHLJaYzxx2nDkzPuSlLp0sJ6sTjFulDJVpShq%2BwWtWwJ5WJgNLDCR5Ayo9Ln%2BqHtSV9vJffP9UfSnG%2FDbwsYGwDO1LFuEXqPS5EobXVWag%2BakX3SENob5h11SiAlAQbm%2B1rxxJnXlZVslsxqjgOpVAVJhlpmcp8%2F0XR%2BNSbydTS1I%2BC4OslaexST2WgNYOYRUyy5NNtS00hoanOgXrKE9qiOdh2kcotiWqWpRSpLNvRGUy07OSk01Ny8wUOsKC2za4BHeO0dhHbG06DwuUbFlEkMU%2B3c08VhkTniiJIlMuVm5QDfcXvbzbdkRMzsiM5T%2BDEcKqcoaCLVJBAShvnblDoJAn7G38UdIK4MpI3DGYRcNtW8kQOV9zfaJGuDWUdsE5jtoURyNPWRfuuDa8MrSPmyjhWfjQ51EvIfqbfxRMJamfCCB6Ex0WeDBaFaPdDl97WPiaiN%2BV99o844Npxywax9LE73Bk17W9fbExFfiyjh2cfOhzyuWpSSQUpO3dBDFGsSU9sdCu8G08xqtmBIEAXv4o5HhXwhzguEY%2BlFEG36EXE8GvxZPjbPxoaKMtRyArqW9V4CUo6ybNpMb2Rwdzrg62YMiFX5GUXE%2FwBRzVE30ZgyAH%2FhVxOVfiyfGWfjQ0KZClq5lHrEPY2kd7XxR0Arg0qDLCpqbzOo8sy2kqW48ytISLX3v6DGJTHD7h9K1Jl88sKrta2rpEhXoOm0IornbTPMr8bZ55cKM2sDTqR1d2uXdEfEaKGQFONDfujbDHC6%2FPAGSzawe%2BFIUtHRTajrSkAqKdtwL793bFJ3hibYmBKTOdeCWnSAQFTptY%2Be1oqu1a1J0IatXR7eaJPFqA6qyENkd5TaNuOcKM61MGVRm5hJ57mlMu668V9nVCEkn1RK3wr1J%2Bbfk280sI%2BMSrpZdYcedQ6hwc0qQUhQI7QRtAan8Qw8nZTLR%2BOIeIYd%2FU2Y23McKFZlh79mlhBBI2CplYv8aYoJ4Vq4pQSM0sE7nmaibD5IDV6afhvtQ3o1G9udrQVI4cWoFXRXKbE%2Bf5o2RN8NVQpxQ1O5r4ERrUQrRUVOFIAvq6qTtFncyQ6Pf3UMKLSeS%2BlfAPrLcBiCKXh4iwLQKd0i2xHbE4kKAnZxDYT36YvL%2BVtNk3G2Xc1MJIW5yBeeG3eD0djHlfwDT2E2VmXhhztsiYdJI%2B9wHk9jsO6tGlm24vta47Yh7H4dK2tCmet8NPwSLbkRM5g%2Bn395x7h1XpmXB%2BNEedeHZJJ0pxvRlb22ccsPjRAexcnh5bi%2BndStWo9Y8jEiaXhvfStobbdljFvNEZVYnFNJNuV3FfRiAoidW2IKYR39Iv6MBdXKdhpTiUhTKd9lH7W3zxUNMwmhCHOqsG5OlN9MWRVMCBdVdp9v36r%2FAM2KXibCCUprElcdylW%2FFAX0UjCKbFpbLjak3CrGx%2BLl64iaPhdRbcdSyhpRspSVX0m217cu6LClhLSrt1aSKhsSsnceoRTLDYJUanLEnmQo7%2FJAZGqj4VQbFTa%2BSgE2spNjqAP2wNtoi3R8HBSEOFkLKesFbb%2FFGOCVGrSibRq32Tft9UehNDq6rILTu24UWldvntAXn2Kwn0l1ltpJOk6Re1uZiZdKwuXOjbDadKtKbbk%2Bfu2izGhVlHwHfW2rf0bRKaNVkbmXmEq%2BDdpY%2FJAX1ukYYDYKuicG5UB2DzRH2MwcqVW60lpSkhSgnTZVgeVuYMY8inT45suavtujVFUUycI3Nj%2B6CgfV3wGQ%2Bw2DQtJs0CUgt6uR7bGHsVhHygWCgm6dPd2xjTshPoO4X6FINjFMSs0CbHSQOWk93ogMpbo2DtXvrjSAsApVbl5rxO1RsJAL6Qsak3CRrvew5xivRPhISXkpJOyjy%2BOIpkXFkkLaChy61ifRAZEqjYWcstxLKAB1wRfQf97RV9hMHO6ve2RYi2ntEYwunziTft7t4Jk5wi4N%2FNv80BlXsBg64DRaJF9QtuDEHKTgtsJLZbVc6VotYp8%2FojFQ2%2BoaFOAWV1Sb2MVW5Z9Z1oWyTsNzuo%2BiAyhVDwU7pLDjbqPhAAg%2BoEfLE4w9g1rWCGNSVbJVzI7PTGJLkp7XdKlAnewBttASdTKSN1cjZQJO3zQGVewmDV9sv5OpNk%2FGIqDDmD19JoeZVoFxtbUe4bc4w9UtOuJGtwbEpCzcc%2FPE6JCdHvfjTf3XZAZR7B4LQla1PttqTptcc79npEVjhvBalLb6RhS0eSQdlRiTlNnNIu8gk8wImTSau6oLQ1MqTtuhpZHp2EBlS8L4JCVIbeaUokKbVoICk25b8jeCcPYELyWkvoCilKkjlv2iMbNGq6k6SxMEd3QOfNEgoVaVfo5KZXfnpYX80BlaaFgIhVn0EqRqKTsUq1W9e1ztFNNDwUpSk9E2CoHQQdQ57evvjGPYSrC%2F5im7jn%2BZ1bfJEF0utKNzJTPqYUPxCAy%2F2BwKhtpWpK9YVqOjZKhyB7bHviX2GwDZRdLJKW7gJ%2BEvu80Yj7G1ZPKUnQfMyqIimVX9j5vnb9Dq5%2FFAZYii4ECC5paACQTffftEVU0bL9bRUp9tJSQkoLe49cYoihVx37FRZ9e9urLrP4hE3tdxPp1CgVG1r38Vc5fFAZQaHl4lSUqeYGq9uqb7R6E4bwF10BTCzpulQSSL35beaMQ9rmLVjScP1Qpve3iq%2BfxRWTg%2FF7XPDVTR%2FiqxAZ4jBeX3izbxDKgp0IISvrpSeatPeOdvNGE40wfQ6dIVR%2BXfQlcsx08mpKwUv6XACO8XQSR5xHkFCxCCCae%2BgE298aXue7viM101LcZGIacmaYdJ1Srq1o6UDs1DrJPngMKpDYdCulGrext2RecKb1ySSP1y0P5QivUJCkSqTP0RwqkXV9GG3nAp5hVr6VWAuO5VhFDBfXxFIJte84yLfwxAfpYhCEAhCEAhCEAhCEAhCEB%2BdziB%2FwCVfHV%2B3EtT%2FwDvHY1K6eqT5jG2%2BIY3zbx0ocjieqH%2FANY9Go3fsN%2FOr8cBl2FWwuklxR%2BFFzvcbRasMk%2BxWkH4Qi5FzQNJgBMSE3iJN4lJMAPLaIp2F4A9W0DsmAFdoilyKSoJgKi94ghAiATeKoSRAS6TDSYmiHOJykQA7LxMGwYhoMTAKEMpEyQRyIFh3RUQtfVBc0qSpJSrkQpJBB9NwIk0KO8RtaGUjqhrE%2BKMYcCmZOIsX4jqFcqdQxg2pybnXy4sgvS3K%2ByQDewAAGrlHKZ8tX76Mwk808b0%2FLKoZPSU9Jt4Vqc6KjNMeJpL7j%2BtC79Ne%2Bm7aOra1hGI9GvnaGUiBF%2BSogUHsMOjcHNMRBUPgwykRF46%2FwCCx7CwwfipvLxume7X4rMiTFbVZkyhA6ES9vgE6uktuVBIPVMchJN%2BcXCj1mqYeq0jiCgVF%2BnVSmuh%2BTm2FWcZWO7vB5FJ2I2MMpG4qurKtvJPGE1mZ7OucQwrDyqgJ1DiZlMwXkpaQlJ97Mt0Grt2VbTtaMlxAvgvGamXfsA3UfaY3JTbmKOu8Wi%2BGU%2BKJfJ6wPSdJ0mjbZMakzfzdxHnTiOQxXiai0mRqMnTWqc45T2ijxsIueldJNysk%2BgAACMH6%2F7pMMpHavDtOSrOJczWcL9CvhkY6ZSFYi1dAy4ptJcblSvrKbK9epJ2HVIss78qT68K%2B6i3PYKbm28Oe2WVdovjYs%2BzLmab0k%2Bje3bpteLvjPPHG2OcD4Yy2qCJKn4awtJNyjVPpyC03OrRyfmPtl7nblffcm8YGzNOy03LT7ASXpaYbmW9SdSdbawtNx2i6ReGUjvyRQG%2FCOYnDhT0r2D3AynTvrMsi59NheNNcJhnGqfxDmoOvusows%2Bmf8YKggzXSPC69XNwp2vztaNV4nz5x%2FijN%2F3cmZiXouKELYUhUglXQoDTXR6ClZJUladQUCd9XZYRkmY%2FFlmPmPhWdwa5QsO4dkqvb2XdpMtoeqIFuqs9gNhfmbbXhlI3lk1mvhvKPhDywruO6NM1ChVOanqdMhlpLymXUrdeZUWj5adTYSe4kHsjCeOPEa8U4YykxmzJuNOV2iTdTaavqXd0tqCPOrcD0mNHVXNbE9YyjoeS83J04UXD1SmKpKTKWleNrdd1dRR5BCda7WG9%2FNF0rmctbxTK5byGLqFJvyGWzbDEiiUCkOzjbSkq98UokaldG2Dba14ZSMczcZkUYlewwlIXLYTp8lh1CSLgql2gp5duxSn3XifOI7KxcqXTxzZGOKKQmYw0yghfaoy7oQoHvjhGdemarMTs9OqPjNQmH5t9Q59I6tS1EfwlGNhY%2BzzxzmFjTDmPp5EnSK1hSQk5GmPU5Kk6DLboeOom61Em%2FZY25RGQ3zw3t1D6sbNF18zXTIka77JLWFaVDpQGOkvtYAdS%2FZe0YPXkyzvg7MI%2B%2BFckjG9SM8QbIdHTvadens1FBA77R5cV8ZmbGK8Kz%2BGhSsO0d%2Bss%2BLVSsU6U0Ts03YgjUfJJBIvc2ubWjFcpeIXGGT1KnsN0amUer4fn3xNOUiqSweYQ%2FYArQD5JISm%2FeQDzhkNzZrOuDCnCVMz6nVvpVT1OB4kvLHSy5uq%2B%2FPTz746DqeeuFJTiMRkg%2Fh2aTiaYqjVPYnFIT0RkHW1TKj0vlCykhPRdpsY4FzBzqxxmhjmnY%2BxI9KomqM5LKpcnLt6ZaTQy6HEoSnmbqSNR5kRcpvP3Fk9nzK8Q0xRqYqvys21OCRGsSgKGi10Y31WKSb73vE5SLriOZFLz4zaxupxClYUNbnpYKFgqcf8AzJKpv2HXMEjtuiMm4CkeK5r1CnNzawynCFQR0RUbOaEIsbcrgX35xpeu45m6%2Bxiqbqcv%2BeuNK2xVai6wkIYQ0z0jgZbTufsy0q9CBF3yWzfreSuLJrFtDpMpUnZmlTdLVLzSilAD6AA5cb3SQDbt3EMpG3sEzxoXAVXatS6jUJBubx221iObpiSZtNNMw2hxQtuCGiNO4uCe%2BLHnxkxldg%2FL%2FBuZ%2BVmNMQ1uiYufdZamKkrWtbKEdJrbCushY0uJKFbaow3JjPjGGST06xRpCRrFGqyAmo0eoAmWmFAW1230qttyII7IuGcnEJM5t0DD%2BF2cA0fC9Lw889MS0tTnFKbCnE6SEggBCQL7AczDKRvTCmE8icp8NYd4o8OM5syNJbmehbQ%2B21qcl3AWwuZaG%2FizihYWO5t2RRx3gvIPH%2BCKxxRYjZzWm6fVppwLW222HGm0J6NDzbagB4slYShKibbm8aXqvE3jGr5MS2R7uGqUiks06Xpjk%2BFuLmHWWXekT1SdAVcAX7uUJXidxlJ5HryKRhyjGmqpS6N7IOqdMwJZTvSHq%2BTqHIHkOcMpGmvfP0xHRfuTYlI5gEjtA2iQkxWc0fqmqJIZSJNGvrridHX977IaP3MTdGtaFeV5JTq5W7NoZSOnclGkZD8NuK%2BIN1K0YmxslWGsGKdWpSmm1akuTKNR5lQWrV9qyO%2BOYOjQ002wlRWGk6dSjuo95PaTzMZxjrOLHeZFEwzhnEr0i3ScISvi1Kk5KWDDSOolGtQB6ytCQAfOrvMYNoiMhBVoAi0FIMQCCIZCJVEhPdE%2BmJtETlIpA98ThUTaIl0nsiBCIEkGIxAi8ATziYq07GIpTbeIKTcxOUhqPZC5gEeaKgbBhlIkvtuYi2QDuIKQAbAxUSkgbARGQ6OwVXstswOEicyAxtmAvLt2SrjtSRWZyReckKiku9L0ZcbFlLAVYt3vdCCLxlPHSqkJw3lFLyk27Mus0V7xaYmLh%2BZkOiYS24tJ6ydSgF2P2xjSeWXEPmNlVQ5vCVJTSKxhudmDNuUWtSQmpVL5tqcQk7pUdIv2bDlGO5l5l4zzYxU9i%2FHNTTN1BxtMu2hpAQxKspvpaaSPJSCSfOYDFiodwimTeJrXhoicpEoJEbH4e5TLGoZv0CSzgdLeG3VrHXXol1zth4s3Mq5hlS9ieV9IJAJjXWiIhtC21Nrb1JUkpUFclA8xDKR25nQ9I1DiSp%2BGOKp00fKhmmOvYNEi%2B4xTX5sBACplxsXS8lHSAIsEpskJ2NzpdqU4YE5YZqKNXnTjKXqVQGBS68sOTEl1fEFIRbSsHr9IV2IAv3Rj1T4gsa17JVWSGK5KSrcqzMyz9Nq08VKnae00q4bQb2UbXQFnraCUm%2B1tYL6Q8ogdQUwYIw9irKmc4KajUKjmRU2g3iGUmJh1cs7IpZbU8KilVksaXte6T1bXTvaPFxt03LmQzQkjhpEtL4snZZUxiyTkiFSjbp09EvuS8rr6hYakhKiASY1zlDnzi%2FJah4rpWDabS%2FHcToZQmrPtXmqfoTYhvsUk3KtJ2CgDvyjXT78zMTD05OTb01NzLinpiYeWVOPOKN1LUo7kk9pgN%2BY3bbb8HzltZtQS1jmdCkqUTsXngRY8wQbRn%2FEnPVOX428tJeVfnWkol6AmmoZfUhAQpwiYDaU7KSRYLFuQjnio5oVerZK0LI%2Bcpkp7D0OtzVZanQpRfeLuqzShyCUlajcbnblbfZuGONHMDD2H6bTarg7DmIq3QJUSlGxDPs2mpVrRosoWOs2AuQRe28MhvPAU4ikcZfElPyMu26un0RuohpDgSXVtaHCkK5JKiALntihX838vs4eGrNteXFEmafTaRR5eZnA%2FLCWCp%2BeKJh9OjtUldwtfJRNxtHLGX%2BeuMsv8S41xmG5Ou1rHVJmabUZqoagULeVcvpSjmU7gIO1rd0WrBOa1bwJl3jvLOlyUlMyOPm5RubmX9XSSnQgJJbSNjqSLG%2FLnE5SPGZg0nKuZl9CdWMcRpJUr4cjTG9Rt3DxuYA%2FwcbapiDL%2BDtx%2BzKI3ON2EoTcqITds3Fzta3LlGlMSVxipyGHKXKSzrMtQaT4rpcA98mnXVvTTwt8Fa1JsOwIi%2FwApmtXJTJSp5GKpMmqkVKvNV1U8Srp0KbCT0AHklJWkKKudiREZDdfFjUJyUXw9ClTE9JMJw9TFyCJR5bWh4uy19GnZSym%2FfsTG%2B5sgcaWbE3TSlM%2BzlLJ9ApqxcS%2BSSk7b6xZPxCOWcvuLvFmCMJUbCVbwFh%2FGCMLH84J2rAmYp1hZIBsdWkbAiyrbXjDaJnzmXRM3Hs8Wa4y%2FiqeW4JwuNAy0ywtISZZSB%2BlpSlITbdJF%2Bd4ZDY%2FDpMO1DhR4iGqhMzD0m3JSThD7inAJpTepxSdRNlFekq89o3FgjNrAmU%2FCdlHOZl0V6dw9WpKaadU2wJlMvPSi3ZyX1Nc1BTqAEqHkrsTtHPeaHE9inMvCTmA6bg%2FD%2BC6BNzHjdSlaMCFVFwEKAdVYWTqGo23UbXNhY4bibM%2Bs4oydwZktUJCWbp2Cn5x6XnmnFF%2BbD%2BsBLgPVToS4R1eexNrQyG8OOyYqmNatlG%2FJyy2J7FOG1vsMrUFKaenZhnSlSu0guC58xjRmJK8w5nJ4%2FQJ19iRolZkKBSXpVxTKkSMk61KISkpN9KujWojkdZ74yLEefNTxvivLjEGKKJIMJy6oppku3K61iddbQeheWlWyDrS0SASOqe%2BNUyL7si5KTTakuzEq7Lv3cGzjjTqXLn98pO%2FpMMh9D5CmSD3hHMVzs0llyZkcAMzVNbUi%2FRuFCW1FI7wgkbdijHPOHcAUHO%2FJPGmadWzuxZO4%2FoEpOVPFGHppavFJKYbcWWmFtkgdGpDR0qAtcAWBBjFMd8ReJ8S8Q6eIzB8ojDlWl0SrbEktZmGi2210bjLp21tuAqJG1ur2iM3rvF9QKxg%2FGFFp%2BR9EoFaxxILkqxUKfMhKJgqSU9IsaQpdgpZAPIm94nKR4uHnIvKTOnCVSVWZ7H7eJKJLzE7UUUmVR4qlkLuw3LrIPSTK0DUlFwdQ2G2%2B3nZjKLjIVTsEM46zOmzgamLm5sTFKQwH5hNmi%2B%2BpQsZpf2MJTsSFbXjn%2FIbiUxDkBK1yUo2GafW2K1Nys6Ezcy430DjDZQLaB1gQQT2i3njzZK8RuIskK9iqu0%2FDchW%2FbY%2BxNTKJl5bXQutvuujRpvcEuqBv2ARGQwDMiVwVIY0qMhl2%2FXHsPyxQywutyolp0PJFnkONfB0ruN7E25Ri8XbElZnMTYhquJZ5lDUxV5%2BZqDraCdKFvOKWUi%2B9gVWi2BtQPKAlsYvWGMcY0y7eqmIMA4gfo1UmaRN0tU0wAV%2BLvpHSJST5JOhNlDcW2tFptEVtNvsuyikE9MktrsbEBQttAdUce0u%2FNYsyvSlxyYXM4TZQhDaSpxxwvtFWkfCWsnYfbGMyGIsjOKrP9OCcR5XZgUDEEzh7oZWrv1NchNSaJcA6PFEmwB1LIWvZRsLdo5jzSzkxlnHMYbnMXIkZaYwvICnSD9NaVLqCApKg4TqJ6QKQkhQIsQSIz5fGpnKZHUZXDK8SKkBTXcVrpwNUcYHLr3tq2uTa197QGlMV0NzC%2BKK3hZydTOGi1Kap4mEm4dDTqkBfrABPnvFrXyEVphRceW4pxTinFKWtazdS1qN1KPnJJJ88UlDflDIU%2B2IpuNonAvEqtoZCRUE98TEQAJ5CJykQ1QC7crxCwMNIiBMHV9kThaztaIJSSeUVktm3KGQoqMSgxVW2e6JAjvicpCJ2y2450b7YWnUFd3L0RLpiZCLwykddM4%2FxtmDwP5q4pxviaaq9VexJLyaJh8JGmW6SUCW0gABKR3Rqjhdy5qOa2dFIwr7I1Bmg07VW602zOOtNmVZULIISoAdI5oBNuQVGLU3ODGFIypq%2BSsu3TThquT6ajNa5W8yHUltSdDl9hdpO1u%2BK2XucuMsrMNYroGEBIMe3KWMnPzy5cmcaZ6MoCWXQodGBqUrkesb9kMpF14ks105x5u1zFUhMaqNKOCk0ZI2SZSXJT0gH7tfSL9BEapXpWbk2tFRAQ2htllsIaaSG20%2FapA2ES6AfXDKRT9ceukqp5qcn7LqmEU%2FxloTq5ZIU%2BiX1jpVNg7FYRqsO%2BKHRRFsFtyIyHcPET4phzLTL6j5bFEhw6VGcllYpq2HyXJxco4%2BgrW6QNWhSblS91FYKVAaQDgEtTeCZHEBPtTlcdRlwMMMLkyiamPF11XplJeSl7T0n2DQtNxYuXHmjWWUHELjDJqlVnDlNp1OxDhyvsPMzVDq6VOSiHHUFKnkJHIm%2FWT5KrA7KF41WGw2hpgKUromw3qUT2QyG8aWrh3lMk6tVKHXa%2FLZySuIZpeDvE1vJn9YnEinhttI0rQZcde9lalKjb%2FFVKMz2ROFK3ntLUuQzrLbbUkilgBx5npB0qZlPINhBKlcwh3ZBIJEczZQZnVTJvHUpj2j4epNampRl5hEtUkq0JLidPSoUndDifgqHeR23i2Y3xriXMHE89jDF9VXUKvUF6nXTshtA8lptPJCEjYAenmSYZDd%2FDY3o4fuJNhjylYeadTvsT0bl9uQNxEmcs2pXATkwyh9Ylpmdm1TJZcUhp52z5bK9NutrFxf4Q741XgvNfEOBMFY8wLRZSUclMxKa3Tp%2BYdB6WTCCoFxoDYlSFqSdWw2IjLcpOJfEeUuFpjALuF6HivC65oz0pTKu1q8SmVEKWppQv1VKAVpI6qrkEXIicpHQeL%2BlVxDcI01UnlqmZijNpmVuAlxS%2BjA61973Ktz23jamAc8sFYpzvqGVcphqYlcYSExPyNYmOjTpVJSCkmWcD4%2ByBfTDS3zRdV44UqnEHjuuZzUTPKuiSnqvh6dbmKfTylSJNmXRq%2FMqbG4SdaiVc77%2BaI4Sz9xTg3Oyo560%2Bj0ybrFWXPqmJJ5S0ywTNAXCSnrXQUIKT2235xGQsmHump01j7GiXAlzDsjPSks4kdZFQqM0qTYUk9ikoVMq9Ubd4HJeXk6lm0thvQU4Be3TyISV8%2FOBbfzRoJdaZGEHsOBpxU7P4h9nJ59adIcDbC2mWrg9YBbzznLYqFoyjKXODEGT72KF0Omyc8jFtBeoE2mZUpJZbcvZ5sp%2BGnUbA7G%2B%2FKGQ2YpxTHg3KAhqdUwzM42dRPFtxSEuoUtQ0uEEbDSnt7BG15QPzk5wSNVl5UzOLdfcW5MqK3VJRKAouVbnYJ9YEc55KcQOKcmKNOYPkaVR8R4Un3Uvv0KtM9Iwl4JALrarEpJ0p1Agg2vsY8mZGe2YGZ2M6LjaoT0tR5rC5bNAl6Y3oZpmhYUC3fcqJSASdiBa1oZDorIqbqX1w%2FHEvN1CdUno6ymZQ68sp8WHQlhJSTp0JudPdc95jw8IeNqdl1kXm9jypyD83TqNi1MxMNMJCnFyq2w0spSdlWQu%2BntAI7YwbEHG%2FmPWKPUZan4QwzRcRVaVEjPYjkZa027L6Sk2B8lVlKsSSBe47Lawwnm1XMG5SY1yeptOkl0nGypZcxMLKumlSyEpIbHIhaUgG%2FLmL3icpHTPEpj7C2Y3CZKYkwVJpk8NS%2BM2qNSQWegCpWVLqEudFb3oGxsg7gAXjlDGyBTaHg7CzTS5OYp1EXWJyzhSvx%2BpOmYBNjdK0S6JVIPMCPfO5n1ifyQk8gZuVlmsOtYhXW3Z5pBM4pK1ErZAJ02BUsg8zcA2Aix40xAMXYvrmJkynizVSnCuXZNrtS6EJaZQbbXS022k22uDDKR1Xi6Vkqz9RZR66tc4xUFMPTZmll0zCkhtXXKt1FSwm5N4uVbwjSs%2B%2BKrMjLnMLOnGmH63I1RmVw3RKUVtIXSxLJW6%2Bk3CVWUTcHcgmxPIc2Y%2FzmqeOcJ5YYUEgmkvZY05cnK1KXmCX33%2BkSpp9I%2FSygNp23uq%2FZG5sN8dM0zUaVi3HeUFFrmMqNKqk5fEUo8Jd95sjrJWCkkBZ3UkEjdWm14jIa5yAyuy8zJx3Ucs8bVbFsvXFzjsnSXKJKoclQywXA%2FMzS1X6JIKU%2BaxHOOgpdzJuu0GW4KE4%2FzSE3J1VUkptyjBt4y7Q1iTdc0afEkn33X2gp62mOXsos4qnlBmBOZiSFEkqlMT8pUJR2TfdW02kTTgcUpKk3PVIsAb7ReGeJPEjXEDOcQ3tdkTU56UckXqYX3BLqZXKpl7ax1rgICr9pv2QyFt4h8F5c5cYybwVgWdxS%2FO0oPS9cTXZZDXvgUCw7LlNtbS0EnVyNgQd9tVxm%2BceaNUznzEn8w6xTJenPzcrKySZWXcUtDbcu3oT1lbkncn0xhRTDIIvWEMSYswliem4lwPOzMpX5N7RTnpRkOvh5wFvS2kggrUFFI27Ys0ZNlzjWr5Z41pOPqAzJvVKiPmYlkTjfSMlehSbqTte2q4sRYgGGQ6mm63M8LuWWMMS5t4qmK7mzm%2FKrbNGmZrpGZJtTSm%2Bket1RoS4suEAAkJbTexMa24ZcRYWpmPMDULPbEmYYnKVPyMtl7LqLqaUhCmig6kmxKFL0AaLp07E2MUsQcaGZuJ6LU6HWMKYGmGKvIPU6aW7Ry44WnG1INlqUVAjWSN9jHkwHxd5k4Jwph%2FC83R8M4sVhCXTKYdqVakiqcpbSUaUpQtPlAAAb2NgBeGQsfFa1jKW4gMXox49Tnaz0zC9VP1GWMoWU%2BLBvUAoWa0ghW9wey0aj1E84vWLMU4gxxiOoYtxVUlVCr1Z4zE3MFOkKVawSkDZKUgBIHYBFmKbdkMhTheBG%2FKFj3ROUiERvE6EX5xKtOkxGQliUk35xNEp5wAExNfe194It2x07mJk1lvSuCXL7NakUFLeLKlNyDk5VEur1zAmXH0OMrTfSUp6NGmwuN%2B%2BA1plZw%2BY2zZwLjDH%2BG5ymtymDUFT0rMrUl6dUGFPKQyQNIIQknrEAmwG8Z1wFuGYz9RMI%2BxO4Wqjiduwhrf4jGxeDQBrhzzxVc2aW%2FdQvYD2IWRfu3jW%2Fg%2FzbO6SHfhGoj%2BSxAYTntT5us8SGO6XJJDk3U8XOSbIUbBTzrjbabnsF1C57otmeGTOJchsbIwLiio0%2BozTlPZqLc1IFRZWhalpUmygCClTahvz2PbGX43s5xj1MGxBzJl0%2Bb9FNCM18IsNOeNNJ8pvCrSj338ZmOfmI5QHLfONl4TyFxjjLJ%2FFmdVLmqc3RsHqWJmVfcKZmbS2lCniyALEoDiTYkatwOUbOz2yYy8wbw05U5gYaozkpXK14p7IzZfWvx4TEot5RWknSClaAE6fgkg3jMMhmNPAfnC4lVys1ZR81peXFoC1eDj2zlxF%2B6w4n5Jxr540TO4XqeYmes9g%2BghlNQxJi2oSEp4w5pQhxU46AVq32ABJ9Eb38HGnVnXXE2VvhtA25foxnnGqsnVJ%2Bq2wm4FdU5hzQBPnmpiAxbOPKavZL4%2Fm8vsSTspOzLEvLTrE5JrJYmZd9GpC06gFJOygUqAItGCOW5Ax0Jx9Lcl%2BIOszJ5tYXpC0DnYCXcI%2BO20X7jLyVyzyvy%2FymxDl%2Fh5ymzeIGHG6i8JhbiJwCRl3wteo2DgW4rybDSfRAcs3N%2BUR1GI7CIah3CAmhEExOOUBKpQuL3v2eiKZuPhbdkVSFckqEQ0C%2BwB3%2BWAp25HURAXGoa725WioQBc6bxTIPVGm1ucBNcxCEICRZPwVE357XibR1NISfit6oitHWCQjYch%2Fv3wuL3CtxASIUlW6RYfliZToTtpN%2Bz0dsU0oWo7C3d27xPcpFnB6LQFRBRbbf0xKbavLt6IkCk37%2FTE50diICfWkAXWYjLMTk9NJlZOVmJl5y5S000pxxVuekJ3PntEg5%2BRfaNy8HS5hniSwtMSbq2piXpeIH2nEc21opMypKh6CAfVAasOHsTJISvCddSTyCqY%2BL%2FyYiMLYnUtTacIV0qSdKh7Gv3B7vJjNaJxOcTb0tK%2BK5%2FY3JfaSuzk%2BlVyU35rSYuzmf8AxTvIRqz4xqlKORFUbHx2Rv64DWjWHsSpsUYWrZvf%2Fm57s5%2FB7I2XkzI1el0HPGZnqPUJLpcp6iyHH2FshQ8elNSQVAb27O2ITHEPxPSLOuaz0xetG6NPsgg3J%2Fep7YynL3NzNrMDLzPOkY5zErmIafLZazUwzLz74cQ26Z%2BVTrAtcG1xe%2FbAaKlp5cskDowsrVq52iquv73MqnV5JIVzjyStLm5xsLb0qA59YD%2FcxXOHp8JS4ppFiLi7g9XqgPDVZhdULp09Cp1kM2ve3VIvGxc7s3U5xVbCVdXRVUteHMJU7DDjZeDnTrlAoF9JHJK9eyTuLbxg0pQaxUKzK4fplLmp6rTzyJaUkpRsuuzDq%2FJQhKdyT8kXrH%2BVuY2VVQk6VmTg2o4emqgyX5UTbdkPoBsrQ4LpUUnmkG4uLiAsrddSjRrlFfvkqv649DVblgVlbRKikgBRPPsigMPzykBaWkEHucESOUKqNFV5W%2BlJWbKHIC5MBsvJLNTLnLaZansVYAr9QrlMqrNXpldw9XTITSW29JMhMIUChyWcUm6ttW9uUXLKvEyce8XeCsXP0eQpasQZgS1SVIyqNLEvreU4UIHYB8pue2NVYYwtiLG1cksMYToU5V6zUFFErIyjet54gXNh5huewRsXhllnpTijyukpxhSHZbF7DL7LgsUON9IFIUOwhSSD5xAYxU8zsxBWqg7L5o42baFRmwyUYhnACgTDgSlI6TYcgBFMZmZxKGpOZWPinzV6dt%2FPjLMhcMUqu4qxFVqlKtzJpM26ZZDidSW1uPvHV5yANrxtCuZw5b4Uqb9ErlRQ3PShQHWG5VSy0SAoAkCwuCDaOJesWtLG8TdrGymuY2vpOCaC3S%2BYTZ4tiV7ixotJmKdUTsmY1zMxrnKdXgaAGY2b2oJVmPmACNx%2Bf88fX5cGsxM2GlKU3mLj9BWdStOIZ8aj3n3yN3HiIyWSnSvEBaVe9jJOD8kVU8RGSt0gYtl7G4UfFnth9xGHvpiHJdp5%2Fub3EvRmNuLU81PaaQOZGcCmwDmRmEUJOpIOIp2wPm68RTmfm%2BhCwMzMelExs4FYgnClwDsI12IjdSeIDJ9XXTX20gAgASzhv%2FJisM%2FcnXblOJGNI59JKuAn0DRCMVv%2FAC3fr%2B44l6Mzsxej1e05rcYfmG1IMsttK0lPUbI280dM5Q8XOPG6rTMLZo5nNYWwpS6StiWn5TDLc2%2BlTDNpdhaeZCrcwBdQF7XvEnu55NuKSBiaWUntIlXNv5EVV5t5TqbEw3XWlJPJSJRa%2FwASdvXE99b99Wnn%2B4p0J0aq2YvRzU9pq3MjiLzezjoMnQcfVaXmpGWnDUpZmXpSJQpeKCgKOkki6DunvPmjWa0Pr6jjLnldUaT2b388dMozjyjBKRiBoWN%2F0Esb%2BpEV1ZuZWNi4rrDn2wEqu6e6%2FViO%2Bt%2B%2BrT17iNCNHJjPvxRzU9py%2FwBA4g6XGVJGrkU2Px%2FkgttxNwJd5Vh2IMdMKzxynbC0Cf1I7SJRZHr6sROfWUTVyK1Lt9cneUdBG3Z1Id9b99Wnn%2B5E6DaOTsxej1e25oB6M9dDl0p2skxWDS%2BkOtOhSbc0kKF46gwzxC5I03E9EqU7Vpd%2BVk59h55JkVkBAUNR0lFjYdkbtc4vOGMOrDNRln0pUSHEUQEG%2Fn6OO3hc29%2FoqqtqYs8p2TO18%2F0tudx0evNFhcbfumKozmqnZE57NUz6XzzWgg7uBXq3iPREfBJ9AvH0Dd4v%2BGEFXSTcoNXPXRgP%2FbiLHFzwsajpq9MbUoWUTSQL%2Bn3uOtGHVzsqjneQnGIj6Orr3OQOHzGWHMEZwYfxFimqJptJbTOykzOrQpSJcvybzKFqCQTp1rTew7YzDDriqLIYIkHeKbKycp2Am3DR6RN0iccky8rWC8%2B10Gl5wBRstW42PZHS6OK3hevqbq1H9IpKf6qKg4reGDbVV6V6qKk%2F%2B3G3Y3Kuyp1zE%2Fa5l%2BvcXuqKspp1ZbM%2FROzVMZuccb40w4jDWZFSquaeAK%2FV8WYVk8NU%2BQwjSn5O7qKgiYDrqC0hBATruq97WHZHPyxvawT6VcvSI%2Bh44reGBtsJbrNISF80ew6R8Y6OPMvil4V0e%2Bqq1ECrX%2FtQCr%2FRxFvdK7xlGcREedfD75RcLOaODVV%2FXofPpetoi6QARfs3ESLWT5CkqH76PoC5xYcKt%2BjcqdJO17Gigj%2FRxBPFlwoNA6atRE2uQBRUi5A%2Fvca04bVHzo52%2FwB%2BafJz%2FX2Pn6S2OZSP4QhrY0X6RH3Qjv4cWPCW8oFdQotyOaqEnbbv6OH1VvCgW7pmqKRa2n2DQPxtxMYbX40c535p8nPXufP1IbKrBaVdpSCL2ik50bcfRuo4ayL4j8DTsrRqRS1NBpxMlUKfKIYmpF8i6HEKSBex5pNwRcGPm3WOlkX35N5YUuVecYWRyKkLUgkekpjXvF0ru8RVMxMS3rnf6L3M0RGVUbYlVZqTMkpwuA2XtZPZERiSXA0LaUSOXnjBKhWplUwoMKKWwdIPf3kx41VScPlPq9W0arcbInsSNTqWAUqSWWyi6u3flG2Mr2J%2FFOR9fw3QaNTq%2FPtY9olZmaLNzyJcTcixLu9JqK1C6FEhB0m4Crxy8KnMj9PX8d4nVNuOJuolXpjJZV00V8KqM419cZMF5sqraz4NM5TqnmnPze12%2FMU%2FMjElbqNfzW4c6Pi0AIYw%2FJtYxZkpOhU9INpKXbbcN06tJ1%2BVtyjWmdUvUcJYPywwZXJNuQq9IkK45N0xM0iZMmh%2BfK2ElxBIUOjIAJNzp3jmkTTg6wsLRH2SmR5Lqh6I2K7xTVTMRE5zy6vNuaVjcLSztKapqjg08kROWyY5apiNuezWzh2oAuWVdO19olE8f1NXxE%2FEO0Rg5qs%2BD%2BiFRAVaoptaaWLcrGNN1Gb%2ByTbcTCpsufCMYMKpPD%2B6D8QiY1eoK5zjnqtAZx7IW8jeNl8PWePuF5lM4%2FXQE1llmSfk32ErDb7aXQB0rC1ApQ4kp5nsJjnv2Vnv1478cVfZyf0hK5pZA74Dr%2BuccGJJjMGpY7wflvgmkzE8dPjc3TOnqbrenSQ5NJUCCpNwVIANjzi%2FM4upeaeEE4iyO4fcq5qtyKCnE2DZqkF6oMqG4npJXSpM1LrB6ybdI2oEEEbxxD7LzKv7oPxRO3WJ1t1D7U4tp1s3Q42ooWg%2BZQsR6oDtisY2zE4dp%2FC2L8xeGvKOXaqvTLp6ZWmWfSUIGttV3FhpQDidSVoO1xHOOLsWSWK8S1DEUrh6kUFM86XfY6kMFmTYPI9G2SdINr2BtcmwHKMYxNm5mTjSmU6jYvxxVazJUm%2FiLU490gl7oCDpJF7lKUgkkk2EYymqTiVHTMKgM08fb74rt1FhKkpQndO4APMiMF9l579cq%2BIRKqqVA%2BTMr9VoDZ6MUNIZMv0bmgm5621%2FRERimU6B%2BXOsKdYLae7USO%2FstGrvZaoHqmZXt3xEVWeH90n1iA2Q3MNuNq31dURL0izyMWDDtUE%2BlTDwSl1sXKhey09%2FmMX0dXlATalw1K7Ykurthc3gJirVtvvEUtovpWuxiQX8pKheCtQ3JEBf2q1KpShGhZUEgEWFto9NPrEvJTDMw2halJUCpJsLg8yPPvFgRKTKkBfi6yk9oBMTdBNJVpMq4D3FBvAbf4b0Y%2BcxvVhl9VKJJzfsDNCfTVJF%2BaRNSZcZC20NS5D5XqLartm4CVE7XjuUUzjn63%2FCflF%2FEtQO4H7%2FAL4%2BemT%2BWFezaxJN0jD9Yl6bNUqmvVQvLD5XoQtCClsMAuFRLovYeTqJ2EdCHgDzr8hGZlIV%2B9n58ens3EBsjOJni1lsJVd3F2Nstp4S%2BHK1NK8SpNSb1SQYSmbZS4SWUvLbUAgO87HTuDHPPCDmdgvLzG1XoeP5kSeHsbUcUOYnVLU2mVd1Etla0nU2hWtaOkHkKKT5xd8c8GWcWCMOVCtVLMGQm2pGlztWflW5moFD7EqhKnEFZHQhZSoaUrI1WNu2NCUHDuI8YVRug4Vw9PVifmAQ3KSbJccUO24HId5O0B9FcMZO4ioGIKbVMzM1ZbFWA8BBT%2BCBUHEB1C1A6Ziou%2BQ%2B4wg9G04Cdusd4444ss1qHmxm%2FPVrDr6ZqkU2WZpUhNgECaS3creF99KlqVbzAGNZ4rw7izBFSdwNjGQqlJnKdoU7SZt5dpcrSFJs3qKRdJB22ixL5iAjfc2jrnLOxy8wuFrNk0pm21rm55n0RyGj9N8qOzMrUsoyzwwpaQU%2Bxbd%2FjMWs5ytIjzT7lLePxE%2BmPeztiSCZVgoAAUjTcgeof64k6EyzulsFISAoK7Fkdnmj04fmmpmWQkt62QglKVp6yjyO0VHrM3ZWdK3bqHba29vX3%2BmN5yZqmJyeFxZbWkr06PJ897bRRccb8fQWfekaRp5C%2FpAi8yuH6lXW2ZWSYDU64sBtDjidBJ71HlGKY3RL4RrD9LrmLaK4ZNLSlNyUwHukDoNyCkEK0kWUAQU3HMGLUxM7FZmMs5e2ozQSHOjcTqUAnq7EA9seZZl3G1L6T33T1VJVzt2ee%2FfFrRW8BzUpMTreP6V0so0FiXnA4y4%2FZNyloqFlHsAJF7i0ebFlPrGDZ4MVLxR9icYbm5abk5pExLPtLvp0uJNtQsbpO%2FLncRMxrylanXGcL2zUJdDSnZpNwls6lX3vyvFgqeOZCmthTaSnUrqrCbG1rEj44xJ%2FEbrij0i7ApBJB3%2F%2FADGITlbemZcMOKDvUVpJA5dhi35rJk9mYeMZirSrjLU2pTOkFSU76U2PP0fljVtFqTrTSUqdSS2dhYEc%2B6Mun1teLOvPNL6FtlxboQkAqNja3p2%2BKNeyyVMNoCjqO17RS1rmZjNlu9MRE%2Bdg2YVSmGcVz7cpMLaS4gAhs6AAoDUAByBI3748FZUyWKb0aEovT2QqwtdQvcxTxy70uKp1Xc2iIV5Jb9jU2IBp8uRc35pvGhP50ujT%2BbD3YdqdapU01MUetT8i82Qpt2WmVtrbINwUqBBHIfFE2K8TYkqE85Wp%2FEFSmanNOrdmJ56bWp95w2utaybqUe0mPJSli6Y89e8kemKyStLlQqMy5qmKjNuq71vrP5YqJdmAmwm5gDuD6%2Fnjwg2N4qhwxCHp8Yfb6yZt5J7w6q%2F44qCqz42FRm7fa9Msj8ceHpYgFEwGc1PMfF89gKiYEqdW8YolNqszU6chbYL0s84gJdQl3yujVsdBNgrcRk2Esx8Z4FlFO4HxyqnCpMtmcS1Jsu6ikkhCumQvySTum3PtjVVTnzL0GSZRLMLWtx%2F31y6lJFx5IvYfFHtlJo%2BIMOW%2FSxAbZmeJPOoEqOZc1cm5IpcgLn1MR5HeJrOtwFKsypyxte1NkU3ty5Mxqh6ZQ4T2GKJWO%2BA2ueJLOm2kZmVEDuErKD%2F2Y9DfFJny0fe82q0kW02S1LAAd32KNPdL6IdL5xAbld4ps9ZhRVMZr1pd7XuzKnst%2BoxR%2BqSzdIVqzMq3WGknxeUvb7zGoOl84h0vogNwscSearYN80Kwm%2FP8zSh%2F9mKrnEzmq6nQvNOrlPd4nKD%2FANmNKlVzuYa%2FNAbmXxKZquK1KzTrZNrX6CV%2FqYmHElm2Qke6zXgE8rty%2FwDVRprX5oa%2FNAbjHERmmtsNOZv1wJBKrFtg7%2Feol%2BqCzMKSheb%2BIFAm9rM%2F1caf1GJ0dYXtAbd93vMVwaV5q4hI9DA%2F9uBz6zIA0jNPEAT5xLn%2FANqNSWhpMBtpefOZDv2TNqvq9IZ%2Fq4irPjMVY0qzXrpH7yX%2FAKuNRnlFI84Db7meGN3EaHMzq%2BpN72tLc%2FvcFZ7Y4XbXmZiI2Fh%2Bhv6qNQDaKgWRAbdGeuO3raszsTG3K5lzb%2FNxM7nfjtRK3M0sQG3VJvLG3mPvcalaLimnbLt72qOv%2BPrDeGaMjJyZouHpCmTM5lzTFTipSWQyX1i%2FXc0ga1%2FujvAaaOdeLlIDTmadeUgG4Fpcb%2FeonXndi1dtWZ2JFW5WVL%2F1UahhAbeczrxU5bVmhio25avFzb%2FNxTfzmxNMqK3808TqURpJ94uR3eRGpYQG22c4cQtJCG82MTISnyQUMED%2BRtB7NWszFy9m5iIgkqI0MgXPmCI1JEQkk2gNonMKYPVVmxiIp86W7%2FzImczIm1gpGb2K7EWNlhII9QjV4YJiRbakmA2gMcKVcrzbxUdXOz1vyRIcWyavKzYxTtsPfze0auiSA2onElAKD0%2Ba%2BKAe7pF7j0iIpq%2BDl6Q5m1iUX5klZA9V41XY84DnAbdFRwkUEpznrWrsBcdH5IjLTuF30KLmddVl1DkHJl0X%2BJMamG1oqBzsgNqsVWkLXpazwqzKftzPvIHyJiv4%2FS79GrPOrqTe101R4j07CNShzaKjRuq8BtcTlNcGk56VkDuVUX9vkirLHDTrw9ls2q1NMWspTNTdJt6DGrEpBG8e5tDfRp6kB0uvAnDM3hyXrdF4m8Tzc4sJD0g7JvoeYUQd9wQQCLE37Y0ziCYR7NtYWGIHMT0iqPIYYfmGNExLPLOlCgoC9wojccwTHnoqGzTFEeVqi3tpLmMMOICgCarKWJ7Pf0QFkelZmnTE9TJxGiYk31yzye5xtRQofGDEcCke2amj%2FwCtY%2F0gjMMV0Wm1DHWIpCjViScm5qrzqm2lTKbqPjDh0XNrEefnGJYMln5THNOk5hoNOt1NhC0A3sekEB%2BlWEIQCEIQCEIQCEIQCEIQH53%2BI9Ns3sdt%2FwD7T1T5Jt6NQu7yyPSVRuHiT2zkx%2Be7FFV%2BWcfjTzn6DSrzqH4oDK8Mf2sv5xFyWm8W7C39qPPqH5YuZHbAUiYgTE%2Bi5IiGjYmAkJgryYHsgeW8BLEUxEERMCICMdB8OnDTTc06C9jXG9TnpSi%2BNLlJGWkCA9NLbt0i1KOyEAkDa5Jv3Rz6ki8d68Psx4nwlylSRqbXKU6suhSTY60hxQI897R4T4QcUvuGYZZ9w1cGq0riiZ5YjKZnLz6svQ6WF2VFpbTVaRnFMTLxfUicP5ASJushRNiDVR1T5xpgjhByHKSkT1XOnmfZVNx%2FJjkfAkth3FGGa%2FO1PEUrh4TVGkaAp6fampl56qFQmXZtotXCTpb0K1fb8oyao0LBVTma23Tc0ZFs1R2lraDdLqKxKplEaVBO3N1XWVf5I5VWimL0zNMYjaz5%2BDVPg%2Fe8%2FU2u%2BdU08L4ujmpzdKDg8yPCivxqs6jyHsmm489tMTfUf5JWsHq7Y8z7Jbfzdo5XxNhDDNXxJUq57uE5LKqE45NeLyNLqCGmdRJ0IHYBe0W6XwLh9b6nVcQNRaSlXVYfk5%2B6we3ntFJ0TxnV%2BUrXP%2BGr3VlOIzyUWfNG510eDzJNRKNNe1DnqqY%2Bj%2BWIJ4QcimwTrqx9NXTt%2FJjmGew3T602yxM8QRSWKYxTEhqQnkFYbOrpNj1nTaxJ53jHJzH0wifnKonM%2BsMzU1WFVRXR0NaB0%2FRdGDo1206eSd0jsivFHGZ1Tidr0a%2B0mcRqjLOzs%2FV3OwBwfZILNgqsKKTpP57JsPMbJidPB7kgo3CKwvVe2mr%2FADCOIma%2FLMsGUZzWxMhlUm5IqSac6SWVudIpPl3uV76vKA2vaJpjEGtDj5zQxM8pxTSyBJPoAU2NKCLObWGxtztveMkaG4tMa8TteartHfKY2WdHq7nbY4QcjiQQmt9Xs9lDb%2BbD6j7I0DnWjbsNWI%2BW0cszmFKRKudBKcTdQfSlQ8mVqCLhW6lEX2323jyu4Vwql51tPEVW3myQC4mnVA6u86SoHntz35xTidi%2BX6ztujV2004jVM6rOz6tzrJPCBkcANaKqdO%2Br2TOw8%2FV3iqOEbJcXCWqvdQ1XFRAsPN1bgeeOSZKh4blZdxv3f6sbr8j2OqG49S9vliR7DuDlalPcQWIJpYOlltEjULqv2C6torGiOL07cStujV21oxGrP5Ozjm7LrccIWTI62qt2PYagFD49MQXwiZJjylVpP8AlAD%2BjHIowjh8rQpGeWJ5QJ2JNLqXVP3UU3cLYcIKpjPqvdItYSQ5TagLjtJJV8kWjRDFp24nbdGrtlWIVeTs%2BrsuvRwiZI9pq59NSH0Yj9SHkdflVf40H0Y5KGX%2BD1klOf8AVlADUUokZ0LIG50gr6xtyHabRgHSUZ1x5SsycWobS6sMpVJv61ov1SqzpCTbmN94mNEMWjbidr0au2icQqmOFwLPqz9jvdHCDkgDdRrNu4VNP0YiOEPI0ndurj%2FKf%2BzHBaPECBpzSxekWNx4rMXI7j75yiT8xISFJzJxi4e1JZeH%2FuRM6IYvOzErXmq7ZTiNVWr4ujq3O%2BTwhZHqbCGpesBQN9Qqe59N0xH6kHJVW5TXDcWSRU%2BXqCY5EVl9hGXWp6W4ia44S2nS4mlziVKUQLp3c7Dcee0SMYBwc7Nty7nETiNpoWHjBpk7oRtc7a789oidEcXjZiVr0au0mMRz%2BZZ9XZdc%2FUdZLatXT16xPL2T2t3eTE%2F1HmSXIKrx%2FwAqp%2BjHIPtHwYhtXR5%2B4t63NKqXNi5HImzkVG8J5dstFRzuxcp8HqBmRm7rWTtp98iOKeMf4ja9Grto7tiZymiz6tzrZzhDyMa5qrd%2F%2FN02%2Fmw%2BpGyL8rxmrW7vZZP0Y4%2FmsAYcS44uZzSxvLKJuUPUWbCr95BXtzjxuYCwclWtzN3FiE%2FbuUd9P43ItGieLTGffG15qu0mb%2FXEfm2fV2XZq%2BEjIoDrGrC%2Fb7Lcv5MUhwkZCA3LtZJ89YH0Y5ElsCYCcTZeemJ1tkdZAkXUHz7FyMMUnCRmHUIxvjpKAs6QZbraATzs9YG1ojiji8%2F3ja5eirtp7sqqjZZerud4J4RshAvUv2X%2FAIVXAH82Iq4RciFKul%2BtDzezN%2F6McIdDg9zysd48T6ZW%2FwD7sQcl8NNAdBjjG7hCxb3rSLX3P2XnEcUcX298rXmq7avdlccll6u53keETIxQsXq0f8r%2FAOzEPqQMi%2BfSVm3%2FAJsPoxyE9gHLxqZcQ3nxi55pJslwU54FQ77dJcRK9hbAEslUtKZy45daULuWklhK%2FNYubQ4pYtEasRtuartIi%2B1TOqLL1ey6%2FwDqQsih%2BmVn%2BN%2F9mIjhEyLKQkPVhQve3sqDb40xxunCWXbmy81ccADsEmq%2F%2Bkj0S%2BEst3U9GvHeNyT5IRKrWpZ7gA5CNE8XjXGIW3NPbZYvdXLFl1dl2AOEjITa6qobdnsqLfFaJfqRchft6n%2FGg%2BjHH68vcFN3TM40zBYA%2BCqmPC3puvaPO7gjLxtelWPsfNJ%2B3ckFpT8ZchxWxXlxC25p7ae7J%2FyursuyvqRMhwQUuVUd49k02Pxp2h9SPkQBbpKtvzPsqnb0dWOPZPA2XUy822vNfGZUT9iSwvURzNj0lr2%2BWMHcVh0uurYxHjfo9aujQXkFSUA7aiHLXtztE06J4tVsxC25p7bFN8q2xFlPN2XfJ4R8iyd5qrn%2FACon6MDwiZGrKdM3WEgc7VJG%2FwAaY4ICKL%2B2bG339H9ZEqmZHSeixFjJZ7CqaSm3%2Bci8aIYxP95WvNPbV74WlO2mz6tzvlXCDkTcgTtYF%2F8AvRG38mJfqP8AIXZK52sq1K1XNTTceYWG8cgrwdlczMKQ%2Fmtj1ZCrEpkVAjv2Lt9opKwllkEJW3mTmCpztBldNh6ekjHxUxbPKcQtuae0yTfap5LLq7LsM8IGQl956rj%2FACmn5olVwicP%2FwAOpVX11VI%2FEmOQfa5lG3svF%2BOHOt5a2t%2FSR0kUvahlQ4slWOseIB7BLXt%2FLi1Oi2Lx%2B323NPbU7sq8FnzR2XX44TeHhpQK6xVRbygurNjV%2FJ2jG8ccGODl4cnKjlxiKoioy7C5hhqbWmYZmNAJ6O6QCkq5BW4jkTMLAlHouGafjHCdWxHUqRM1N6jzMxUk9CGptDSHktpso3JbXqvy2jurgdaffyBkHJl1x1ZFRWhTiyqyEvAJAv3bxz8XsMX0asaL5Z36uueFEZVRq15%2BGZ8GX27WWxrpvVc0WlFExEZ5xHo80OESSTugoPIpPYe0fHGX5T5cVXNfHMhgmlzDcr4ylx%2BamnElSZaWbF3HLDmQLADtJEYtNEKn5kp5eMvW9HSKjoPgdbDmck2k8hh%2BbPr1ItH0PSTELbDcJtr3d9VcU6vNM8v2ORcrGm1t6aKtcZtrMcHuRlOQ3LVOv196YKRqcdnmmQsjtCbbA%2BuKo4RuH42DFeq3SJOo6Kq2o3%2B5jQnF5Q3Mb8TEthuYrfsXLN4dYmHZxSXHGpRltpxxxxSEb7mwuB2iNZjKHCzSA6nPaXCza4akJq9j548JhmB4xidzsr5XiNpE1xE5REzln6Jh0ba%2B1WdpNNNFGXnyz9js1PB1kY8Atmq1pSfhD2TRufQExP8AUZ5JqVfx%2Bu27k1JH0Y44lcv8C08uiZzoEwv4OiWnW%2FkSYg9g3DUxMtN03P5Uo2pO%2BpE95XmuY3OKmL1TwYxG15p7SsX%2FAD202f8AX%2B3J2P8AUY5Lk6BOVxR7hUEE%2FwA2H1F2TSBqXM1%2B3eagj6McfM5eyvTA%2FVMPAjktaZzb0G94x%2FFNNbw9VnaQ9njXpxbQbUp5MtOFtRUAq6Fa9wARvYRE6I41%2FiVp0au0rOJcGfk6OaOy7h%2Bozya5Ccr38YI%2BjEfqMsmVADxuuggW2qKPj8mOCUPS6l3OctfPnEtPX%2FnxV8cDKitjOfEgIF9peeTf%2BXCNEcaj%2B87Toz2jvr%2FlUc0dl3gODTJS%2Bn2SrOru9kUfNEU8GGTWqyZyvLCd7Jnm%2FoxxvQcKKrFIl6wriOm5JL6nEmXfRPhxGk2uRc8%2BY3i5u4KlvF2y5xUP616itu1Q97ty37b%2BaInRLG41xiVp0at5TiNUzqs7Pq7LrU8GOTquU7iIHzTiLfzYingwyfP%2FADjiFPn8bbH9GOP04TaCTq4oXQo%2BSkCoX9J7ory%2BHJSVshziWmXQT9lT7IWR3A7jz9hitWimO5asStOjO9kjEJ5bOz6tzrhXBflGqyUVPEbaO0%2BOtG%2Fr0%2FJD6i7KBH%2FOeIbnkTOtcvRpjj%2Bdo1KffLiOJKbQsiyj0dQVe3be9opGgS6LITxMTbd%2BYU3UN%2FReJp0TxyduJWnRneTf45KLPq7LsccGOT42NUxCRzsZ1r6ESr4McnVeTU8QJP8A49r6Mcgt4NU4duJmaAKbgq8eT1u43O0Y1iZh2g1lVNlM%2BMR1FLLaelmGJac6MuHykoJX1kjbrbXi3FPHM%2F1ladGd6s4lMfR0erudxt8FuT4CkuVTEbhHYJ9q%2FwDNiJ4K8oCoEVTEQT2pE63%2BPTeOCzUJwpCPdqxZZIsB4vOcr3%2B3gmdm%2FhZ0Yr9TE39OJ4p45%2FidpzTvR3xidtnRzRud6HgvyfTzqWJUjtInGzt60xMeCvJ9StRqeJvR4%2B2B%2FMjjSjYTm6nR2KqeIaqyq3SoCWmUTqXUAKtcjVYA8xvFV3B%2BlRC%2BJeeChcaUpniRYc%2BdvlieKmOR%2FeVp0Z3nfCPJ0dXZdjDgsykSQU1fEuwsAqebP9CCOCzKMqK11bEiyb3JnWjf%2BTHHKMJp%2FwD7m5%2Fq%2BTdE7b03vFzZwtRQjoJviWnJkDk4lE8pIPaAAQfXFKtF8cj%2B8bTozvZKb9TPzKOrc61%2Bonygtq9lcRW7%2FHWvoxD6ijJ79lsQ%2FhrX0Y44qVEpfSEy%2FERVGk2soBioaQfNvHkTQ5Rd78SdUCLhILjM%2FY%2FGYtTotjkx%2BsrTozvJxCI%2BbRzR2XaaeCvJ0AE1PEBB5Hx5ux9emJjwZZMq8qdxF%2BGN%2FRjjprAi3wGlcSM02NN7HxzSPN5UWGtyqKDU1Uw5%2FYjeUykB51EpPdH0nchQV1k2%2BFYRbirjfLiVp0Z3qziPgs6Orsu4RwY5MAk%2ByeIkg9njjZt%2FJiH1F%2BToOpNTxEBz%2FRjXx%2BTHBxmkqGg554oPVP8Acc9b0eXEPe7WTnRiNItawkp36UOKmN8mJWnRnepOJz5Kjmjsu9E8GOTqb3quI13OreebFh6kw%2BowycNrVXEBJ5fmtv6McXU%2FB87NSMjVGuIKosonGek6N7x1DjBClJ0rTfY9W%2B1xYiKwwrOynRu%2FVITyFNqukNePKKD2EWNh6YjitjcTrxK06M7ycSnZFnRzR2XZA4LMohfRVsR%2Ba842bfyYqDgryd0jXVcRKNzf82oH9GOMva1MoKmU8SU%2FpJ5ATwSfTvePTLYcpqW7Tef8%2B4onrnRPnc8yOuLxE6K43t75WnRntL04hHLZ0dXZdhp4L8mwetVsQq%2Fxxv6MQXwY5McjU8Q%2Fhrf0Y4wmaBSVuAyefs82yUiyujn76u0W1GPK7huWCgo8QU1dI5lM%2Fse7cwjRPG5%2FvK06M9onEPBRZ80dl2yeDHJIiyajXgQDzqCN%2FwCRtBPBhkp0elFTr1yb6hPt%2FRjjFGAG1tKfb4g5hCkpubCc1E9o8rl54tNfpicMVOcovu8V1apQI1LlpWe6NaynVZPW3FiOtaxieKGM8uJ2nRntHfCrkos%2Brc7kTwW5MpN1VnEJ57Gdb7f4EDwZ5LlIKa1XjbkBOtb%2Bm6Y4HWFu3LmdOInAVAlSpWdsT38%2FlgqXaslK85awsIN0hcvO9XfsuraMlOieMcuJ2nRntKTiFXk7Pq3O91cGWShWNdYxEO782tc%2B89WJzwa5J6LKq9fuRYkz7Yue%2FwAmOJpLAyKhTJeojiB8W8ZZU4ph9M6h9lWsjQ4nkCQAoWJBChEzuBGChDT3EKh5CUnSlaZyyfNaE6KYv%2FiVp0Z7SvfCfJ2fVudo%2FUb5FH%2Fnqsp%2Fe1Jv8dt4kVwb5Dg6vbBWU6%2Bw1Jq3q2jjOVy%2FwfKnQvN5p1XlKUGJwWPxx5pnLXDjzi1yuc0s0g2snoJsj8cRToti2eU4ha809pab7OWfAs%2Brc7T%2BpC4edwvE9UQT8H2UauPURFCa4MsmZ%2BUcTh%2FFNdS%2BdSW30zTL6G1gbFSQNx3i42jiHEGVTcphusYoo%2BYMvW3KC0xNTUs0l9L3QOvBkuJKuYSop1dwUI354OZM8vFeNE%2BNPKl2paSc6Iuko1qeKSqx7Sm4vHOxjCsVwa42l9oxC0maNeUx54jlmfD4GS72sW9rTRVRTlPgiNzUGO8FVfLrGVVwVXFtOTdJe6FTrQIbeSQFIcSDvZSSDFolJSZn5uXkJJlTszNPIl2W081uLUEpHrJEbl4yG0t8Q2IGkIADUrIN3A52ZIBPqt8UYJlchv3TMFhwXQcRU%2FUO%2FwB%2BTHvbriVvOCUX%2B1j8Z8XFU%2BDhcHOetzosqZvXxXJm6jw%2FwT5eUejNnMTFdWfqRSgTbkq%2B3KyjLvMtoKgSqx21G17G0e0cIvDsvqpxzVU9v9t2Pi5RZPCOTj8vl1QZFkuqM5iFYLbZPvqky5UlJAO%2FWUPXHJ1SySoFLqDkjO5wUcTMsotvgS0z724B1k8huDsbx880dueM6Q3KL%2FbX%2B0pmqZ1Uxq1TyZbPQ6t6tbOytZos6KYiPDludpHg%2FwAgXFdInFlXWFfqdWa0n5IDg1yGuL4irhPbeqN%2FRjiqUy%2BwFJrCZ7N5l5vQSUsSs0NK%2BzYRVmMIYJeTeSzYXKOk6gpxE4L9lr32jr1aNYvH5uIWvR%2F7MUXuPBZ80bnaY4OchBe1crJJ2%2Fti380FcGWRStVq9XRvfq1Jof0Y4sVlhQLKKM8mVkC4CWJvfl3n0%2FFE1by%2FoNBpclUZjOuoTPjsw42PFJGadS0G0AqKzrFiVKSEje4udrRWdGsZjX3xtOjVvRN7%2Fcs%2Brc7QHBxkYEa0V6vBQN7GoN7ebyYqDg2yPULprVe3uSBUmrjccrp5RwailUNQcBzPrigshX9r5o3I5E%2B%2BRFFHoiVBac06%2BhQSUgpkJoEA8x9k5GFOjWMzr75WvRneib74aKOaNzvEcGmSF%2BvXa4U9mmpM%2FjCYK4MMkh5Nbr38Ytn8kcQ0HBGHaoZxCc5qhTlSwQfzRIzSA9qNuqQre3M3tFyOWOHGWnnns%2FnkrQkFoIlJtQcPaAQrY%2BmLcWsZq%2FvG16M70xe8%2FmWfVudnJ4MsltIBq9eJB3V4%2B3y%2B5iC%2BDHJZVv7IK8m3O88yb%2BnqxxecCYdQXEIz9qxQo72kpvrDzjVFaTwbgZl94TedNQnUp%2BxpckpxvVbtF1c4idGcajX3wtejO8i9TVOXBs%2Brc7KVwX5KNhLYruIVX3JE%2B0D%2FADYfUZZI9uIMQcrb1Bnn9zHHU9gnA7xApWbFYBT9kW1T50gH7XyyO6PKnANCUm6c38Q6rXI9i57Yd560RGjeMTrnEbWP9s71arxEfNo%2Fr%2Fa7UPBvkoG1tez1eAXz%2FPBr6MS%2FUa5Jk2VWK8fRUGh%2FRji5eX%2BGJhZ6TPGpG6gklcjNg7CwNiu8efE%2BCsNYblZJ2XzexHUn5110K8WkJgNtNoAtdZd3UVHZI7NzaJjRrGZ%2FvG06M70xe55KbPq3O2l8GWSKkpJqmIBp3uKi0L%2FyYHg1yUKQBWK%2BPOKg1v8AyY4EMlTynScx8VHa28o9a3o6WJm5aSZIDeYmLAAbgplnk2P32InRjGuTErTozvRF8qz%2FADbPq3O%2BBwaZKqSEisYgJ%2B29kGrn%2BTE31GGTHSBz2XxDYC2jx9qx9em4jiPDOG6NiFE27N5tYqp7UoW20Ovy7yg6pdzoSEubWAvv3xeF4Gws0ga898TadiNElMKNxz26TaK8WsejZiNp0fvW7qz202fVudhq4KsmVA2reJGiTe6ai2fj6kRHBVksqxVWMSKF%2Bfsg19GOMl4RwinSk52YwWL3NpB5O33zePXJYZwKgL6TNzF6tth4q8AT6Okis6O47H94Ws%2F7Z3rReafFs%2BeNzsFfBTkqNjWcRJ%2Fx9r6MRHBVksNxWMQD%2FKDX0Y5C9pOGqi0FUzH%2BYD6WwOlVLUuYdsT2XC7R5jl7ShdDuN8yDqt1TSpi59PXisaOY5O3ELTo%2FwDZE3nwU2fVudkngqyZXzreIgfNPNA%2Fzd4h9RXkzyFbxL%2BGtfRjjP2oYN1hQzkxelaBb3yVeQpJ7t3LxQxHh%2FCFBkKZNyGauPKiqol%2B70syeiR0RAUglT19dzfla3bFo0bx3kxC06M9paLaJ202fPG52mOC7JkCxqeIT%2B6M83%2BLTFP6ivJkn%2B3eI%2Fw1v6McJh3Dyx1sdZiKT5%2Br8nTRFpzDlhrxxmQgk2ISUmw7%2Fs0J0ax3%2FEbTo%2F8AZE23gps%2BeNzus8FGTpFhXcRj90Jxr8WmIo4JsoCAEV7ERAN7eNtG%2FwDJjimi0vC9Wl5p5%2FNDH8kWXEIa6bk6CCTuHTYjbbzxcjQMIMrujN%2FH9reUnVe%2F3yJ4uY%2FlnGIWnQ%2F7Ji8URtps%2BeNzsL6iTKLVc17EZ3vYTLXL7mIjghyjBv7M4kV3hU00PxJjjk0fBgJIzazHVvcDrA3%2B%2BxUZkMEJUrpsysxnBbmpw3Hp98hGj2Pf4hadH%2Fsnuiz8Sz543OwBwRZQNps5WsRk95nGx%2FRiVXBPk1%2BzmIx%2FjrX0Y5HXhvDVTbSul4pzUnmULKFOMIWpu%2FcLLNjFNvBkg9pBxDmsSokW6JZPq60Txcx6dffG06P%2FAGVm8UclNn1dl2CeCvJrpFlNVxGCo6gPHG7D%2BTEv1FGUJUT7O4j0nkPG2tv5MccpoODQoJms0swJMoBC0vFQKCAerbXcdnPvijian4VoErSDI47zDnnagy9MOuonUoaQEuFCUJ691K2uTyFwIRo3jvLiNr0f%2ByO6afFs%2Brsuy18EOUmyPZzEiVDvmmrn%2BTEVcEmUKhb2bxGFd4mmvxaY4abqcgg3GKsx0m1rpqqN%2FN9kiCqvLoVqbxXmKbdnsqkE%2BvXFo0cx3PKcQtOj%2FwBlIvUT8yz6tzuT6h7KjSlXtjxJYdvjDW%2Fp6kTfUP5UKTpOIcTAE%2FBmmuX3Ecc4XlqPWJOamq1mFmPJBLiUSwRUQ6HE26xPX2sdovjdDwWlSbZoZm6QLkpnbH%2BfDi7j0f3hadH71otqJ%2BbZ8%2F8A1dT%2FAFDOVA54ixV65pr6ERTwOZTH%2FpDigemYa%2BhHK4puBQ4tcxjXM6aO6klyoJvc8%2Fh84kmKbgOb6zeLc0GDptp9kkG57N9cRGjuP568QtOjHaJtrPwUf1%2FtdWq4IcnGhZ6vYkBUOqTMtC3o6seab4JMoHEFEvifEqXLbAPsL37yNO8cy0XL3DuLKkzhfDuOMx1VefamEU3xidSWVTKWHHG0KCV30qUgAkd8ScEuMcVVnPGnUqZr0%2FOSD9NnH5tiYmlqSktt3StNzsQr47mNe%2BYLjVyu1pepxG0zoiZymmNeUZ%2BFawtabW0pspoo1zyZbluzgyrrOT2NXcIVeZRONuy6Z6nzzbZQmZllqUkEp%2BCtKklKk9hFxsYweOouP5pLOP8ABBTbU7hdTqj3kzMcuntj3GjN%2Bt8SwmwvV5%2FPqjX58pmM%2Ftycq9WcWdtVTRGqEoNovcxjfF85heQwPOYmqb%2BHaW8uYkaU5MFUtLOLvqUhHYSVKPmubWvFiPOJ08o7rXXqj4uxXQKbVqNQsRVGQp1eZEvVZOXfKGZ5oCwS6nkoW29BtGwOGzN6kZL5sSuOMQUaaqFMFOm6fMNSih06A9os4gGwUQUAEXGyj3RsrIPhDoeNcvms282cVu0PDk2y5MyjLKksqXKpOkTLrq9m0KIOkcyN%2B0Rg3Edl3ktgWj4arWSmOfbExUvH01EGfbmAwpkI0HqAKRfUq4I7Nj2QGu8d4o9uOOcQY1aYXKKrdYmaqhtLnWY6R0rQAoW3SLbjtEeTEmKsTYxqasQYvxBUK3VXGW2Fzk88XXVNtiyEXPwUgmw85743Xn5w8YMypyky%2FwAf4aqtXmJ%2FFS2kT7M6ptTKdch05LWkBQIXcWJPVjJcuOGnKKUyZpudWfWM6jSadW0tPSjcgrQ1LNOrKWulWELUpSilRsBYC2%2FOA5wnsZYvq9BpeFaxiipz9FoRUaZT5h8rYk7ixDaezYkeYGwhIYtxVTKDUcKUzEtTk6JWXEO1KmsTBRLzi0W0KcRyJFh3XsL3tGQ5p4cwBI5kOUPJSuTOKcOzyJFNKfUrW87MvpAUwSEpuQ4bchsRHS7HB1kxlvhWWqHEDmYKfU5tYbKWpxuUlmnbdZltRBW6UnZSrAXEBpnhXz4ofD5mJUMWYjoVSqtPqNJEj0cgUdK26l9DqFWWQCk6NJ32vfeNUTNVmX629iKUdekZtypTFUZXLulK5Z1cwp5BQsbhSCobjtEbCxXlBIzWfU3k%2FlBVBiKSm6izL0SeU%2BhwOS7jKHVPLcR1SlsFd1D7XvjopfBpw54Zfp2Fcd5uzjeKKgAhkCfl5QvuK5dFLrBNvtdZGqA4zxNiPEmMqxM4ixhX56t1acCUzE9POdI86lI0pCjsLAbAAAeaJK9jLGOKKfSKLiXFlWq0hh6VMnSJecmC4iQY2HRtX5CyUje5skC9gI2RxFZA1vILEclTJ2pirUWspfco9UDPRLd6IpDrDze%2Bh5AUkkA2UCFDtA1AuApnmYlA3vEV9sTIG3OAAWiMIQAm0AbxKqIpgJiFeqJCRE9ydrxLpEBEcokiflEkBPaJCnzRPEdt7wFHQ4T1TYRA6%2B%2B5MVFJJHOKZHPSecBKj8fxemI9IUedX23ZDdHOIc%2BvAVEuGxN%2ByNzcIWn3dZZ4%2BUxhLFTyDbbUKPMCx9RPxRpVHkxsnh3x3hXLXNiRxdjf2R9hBSavS5lVOZDsy345JOy6XEoJAVpLlyLwGucMuJak6W4vyUy7ZP3IjJ26nL9Vvp%2FgjrbW5c9uYjNWMPcIcihthvM7NTom2kttq9q8v1bJtvZ7fkIyXBWV3C1jhFfk6PmZmf4xhvDk9ieccew3LNgycqEl0IBd6y%2Bumw7e%2BA1BUnG36U6UODpUvNWR9sk31H1bRnGSVm8E59uKSSPcycRYG3lVOU%2BaJm6TwoPoQt3MnNphZB1A4VliVDstZ6wMZThaucK2CaVjWiU%2FH%2BZ0%2B1jjDntbmXXcMMp8VR4y1MB9IDvWILWjTtssm%2B0BpOkzbDbDofVpV5SVJUL37LiPT7IS%2FX%2FNSezyT57%2FAI4zpmkcJ6ylL2Z%2BazbZBUE%2B1GXJbWbblXTdYbcolFI4T1IQBmfmmhRVZwqwjLmw70gPfjvAWrL9jEdVzgw1I4Bxo1hauT003KydfcfSwinBbSulcK1bA9H0iQPhFQT2xuTjLpxwZhrLvKjDbkvP4GwxMT65CrTFbbn6lVqm6kKmJl9KFEsNkKUUpPNRPKwjWM1hzhGfbDZzXzLW24LKZXg5ohHr6axEX7AOUPDFjiszNDw9m9jhE7K0mdq7y3cHobvKSbKnn7HpDuEJNh32HbAapE%2Bn9X%2BWJhMbrLrgOptQF1d42jM0UPhSdbaU3nJmE1r3Ut3BibAeYB3eKsxR%2BElCymXzgzLUE263tMRZXou8OUBt7gVxXlRgiqyc1O47kKLmLiLEUtTWW6hJuKbTRmx0jjDT32Nt2ZWAgrURpCbdsYNlQzSJfjmwsxhupN1GnDMiZXLzTaVJQ4hSn1kDVv1dSk3PPTcbERi%2Fte4T30kPZ34%2BOxAQME3PmNuk7YyfKur8LeWWZWE8yGs2sbzy8KVVupIkXMHKbEwEoUnRrDh031c7H0QEnDGy0qdxuhRsjxnc%2BYLmDGl8XUerY34h5%2FClLZmXHqviBqU6OWWkOlFk6ykqISCEJUesQNt43PwvEOKxrNpHVecS6lKj5IWp5QHxKtGtsMtr%2BrEb6NIUoVqd2Ive0qvaPPXWPytbzy5R7n1vGpmjQK4T%2B%2F8A%2FwCjKJWi5Z4ZkXaBKYGbryEz82%2BmrVaZWJt9hSgGG1IQejQEJTc6b6lLVvYCPNPUzLOdnKfMTeWEuw3IzfjK2pCqvNJnW9Niw7e5Sm9lBSdxuO3aabjL8CZS1TGmH5%2FGU7ibDuFsNU2YTJv1ivz4lJYzKk6gyhRBK123sBttHfyjlfJomZ5WJKomViyCcq5ZLi7cqzMad%2FNz%2BKL4jK7C8thuvVt7Juak%2FY%2BkzUyl%2BZdnNDDiUjQ4QpICgCb2JANxGbU3LXLuiByvfVFZXTQpjL8yEytYK3VuIaUpKUp0bqKgkJ85Ecu13NHMBFKZk8Q5gYuqErOIs5LTdZmH0KBsSlxClaVdmxFtojKPAnOfCtE7W5JtKGl0GlsqPWKmUuC%2FqK7RbpiqyTrxmGpiclVK5olrIQPVcxZ6pUm55xDsqFAEWNxyMeYrIHOJjgwrwpZUjFk4htLbU2%2F1fhdE2FH1gxnmVuLapVcSSNOmqVRas3O1KVl1t1GQU6tYKko6JKm1pUkKCrG29yLRomb6QmMmwriyTodKVKKQ%2BJlbxc1geTa1rEbg%2BfsiZiDOXT2I8P0eiTU27U8kZ2nSrU6ttap5U40gFKyNOspAHmvvyixD3L3VHxrK5pSCCCGKy6hQv2glJsR2Racoce4nxrjaiULFuclVplArPjEjMu4irEy5T1NqaV9l6RSkBJKQASOemxBjcL3DfIOdG1SeI3KGoOunQ0gYgDWtR8lAK9rk7CLcCFs58LVlMayzpVKkKacunKjMSaCH6hOVVzpZpwrUoqKUgJSLKSkAfaXvvFd73OF1OQqrWCJphiXlXpaapTFTUliacJu0%2BVkFaCi51JGyrDlvebG2CsUZc4oqGDMZ0lym1imLSl9hZBBSoXQ4hQ2WhQ3SobERk%2BXeSGM8yKHUMUUh2j06jU19Mo7UazUWpGWMwRfokrcPWWBYkDlcRHApkznwsafGU02UF%2FLGddWT1h7OuC%2FmFkx6ZzC2XKcOYjqtOybrjD1Mpbs0h2dq73i7B1oSlaylIJHWIttuRGdryExJg9p%2FGE3mLlx4tRpZ%2BfKpTFMs9MBTTalI6NvfUvUE6R9taNBYtz9zcq9FVh%2FHGaOKKrS59CVuyM7Olxl8AhQ6RAAvY22PbDgRBnLH367QEPpb9rbcskHrJTU3lhQv3lNxHhmaml2adekZ1MpLKWFNsKBdKR2jXYX%2BKMVqM2xNv3YXqRHm1uNwzVzZuirttoSlyZDxF7qCim%2FqsYzjLr2hYnnqZh3EOCq1OOVKpJbeqVMrgZmG2CN0NMONFta%2BZupQ5WjQkxNTTatSH1p9BjPcA47XhD2Jr1GrCpWu0x8Tcs8gdeXfSTpWL7E79oI3iKpOE2qnBOTLjoZdrGNlqCykkKlNx2EAE7%2BaKdRy1yoekZhui4oxdJT6myZZ6elWHWEujklxKFatCuRUm5FwbHcRlmXWYWcHEDW05dPN0XEIqcnNPsSzdFkJWZU%2B0nWHG320IUlQIud7EXBEZLMcLXEazsrJuvqUeQZDLt%2FuVmI4MJ2bGtZPK7Jt6TljPY5xgxMlpHjKW6c0tvpdI19H1rlOq9r2NucYtmJl3J4Zp0%2FijBuMGqpRZES%2BuXqMuqWqCVuOlsgIF0LSOqoqChsrlcRkr7E7T5yYptSk5iTnJR1TExLTDRbdZcSbFK0K3SRHvKl%2B0fHyQm7RwpN9MhR6qvfmCkkd4UAR5xFuDEKTr2uk%2FB5L15Yo6T%2B7KtPuKHcUtEbebaOE8RvdJUJ92%2Flzswv43lmO1%2FB41BZy4RKunqMT8%2BU%2Fw2T%2BURw%2FXAEuzCUkkB98XJ5%2B%2BKjo1T%2BTaI%2Fen3uPdYnvlbT5o9rCZhXXUPOR8sVpGWk3gVTz7w36rbCQpdrXJ32AEeVw9eCHOjWlfbHOdrJcbYYH6bVvuEfPFNZoHwH6l62UfPF2oFCkKtR5mbdf0Ll1gPONklyTQdkvLR8Nkk2UU7oI35i9jqdNnaPOrkZ9oIdQArqm6VpO6VpUNlJI3BECYVUChKVZUzUR2CzCT%2BWJqjJSsktKWJxTt7pW240W3WlDmFpO24IIIMW7WIip1SlFSiSVG5JO5MEIkiJbnviETwEtz3xCJieyJCowEYRLc98LnvgKtx3wuO%2BJIQE1xDUO%2BJYQFRJvFTsik11lhMXGdl5MScvN09xxST7zMpXbqvDclNvgkWt27GA8JPbEt7mIXMSkmAyDCiwmdcSRfW2QPNvGYIcjC8K71IJ%2B2QRGXo5b%2Bf8AHAV0uEqtbaCSb2vziQKsnSRzh5W6eyAqC97E29EVEqTa%2Bm8UxqsBa3fAqBNyrlAZnLz%2FAOZ2m3EBKkI6253tve3ZFeUnC1NDpHU%2BQqxIve4MY1QGVVStUiiF9bfslUJWRLiU6lIS66lBUB2kBWw7bCLrmRhFWX%2BZGKsB%2ByZqLeHKzNUtubLegvoacKQ4U3OkkWuLne8BkWScxl3K4nmZnMt2styjdLdVT1Utc2gicK0J9%2BXKJLyW9Bc3A06tGraOjG65wGPe9uYyzPQ5ur80VCtg9xN9Fr2sI5tyczcrOTeJZ%2Bv0aQZn0VKmmmTLLk47KLCOlQ6FtvNdZCgptIIsQpJIMb%2BT4RzMLWtS8rsNWUOrpn3wU%2BvSbjzQFuzGnuD9GD6ujCGMMeKXN0ibRLJmajWFJ9krJMndDrYacaUdYX0igALEXjUeRWPcZYEzHpLWC685SVYkqNMpNTWy2hTj8p422tTQUoHQFEWURuRtGzMe8dmNcd4YqeGZ3LqkSyKtTZqlPKZqcwplLMwkBayyUhLjiQnqFXk3No5yo9Vn6FUpGt0yZMtO02ZampV8AKLTzSgtCrHY2IBsYDdvHYQjiixZKJTpEu3JtgX5DoE7RocEW3MXzMHMHE%2BZ2K5zHGM51qdrVT0GbmG2EtJcUlISCEp2HVSIx25gPQjReO0cuaW8%2FlphhLBbK00trpErJG5BPPvjir9LUuO08v6ghnAmG2i6tK%2FYuX2tzOmJsYzt49E%2B5jvE%2FiZjzx72e06SclXWuncc1NWXZQ6qB5rdkbEeyvqGMW5Vinl6V8al1vJdZZC1qUke96Qojq67aj9rfnFiy9bYnq9JS9Sel0tHSSt1Q06SQAfPueUddZb1Gk1cO1Nro0NsJMnT0kBNpZCrFY861DUfVGxbV2lM5Uc7UsLOztZzrc04tyamadSvz0RNzcwiXbU%2BwwpXRBKR74oDt07kX5iOZMxKPTqN9hb6JtLii1dARrbJ6pA7NvTH0YzvrFLkaQ5MTE2hlDTZbcdvYNlXaT5u6OAsfdBiZt2q0WbpVclGjpnfEZnpF00gH3p5vymyQLgkad9iY690omqx4VXK5d5yotpijYx%2FKfJh3NWbm512pGWlJJ0MuhPWWFc02B7xfcxvWQ4YcOUFhaKUqeDbgPTS10%2BLPX8rU0BpJJ3uLEdhjAcmcYUjLXAGP8w9Mu43SZJgykoqZDbk68tVmkgnmgX6ygDblG0p7icYxTkbP4xwBRZmdclvFpLESzpbmsOF0C7rjJPvjSwFht1skdptY206LG0rtZmdmeUdW9uza2cUcGNuWc%2BHbO5xtmtN4awliyeotDqM243ITHQTaHEhbKQRsW3b3IBulQVy2sTGKBxb%2FUfN1NtjT%2FC5emNqcUWKcj8XuUCpZJ4dmpSamJYS9VYUlVn3VEABIJJWsm4JHPq9sc80CszNGnVyM8l1yUQtbSUvJIcasbaTfe4IsQdxFr1T8VXGrLOM8vB6fOy2NHCoyic8tWezNsi7D1Jf6fR700VHriy7DYWPPb8sa0W4G27xsFh6UnKfOOIWFLclVKFk9QGx29Nrxq2pzjbDH2x%2B1jXqnOM2azjLU13jBWrFE8e9tB%2BSK%2BKZN%2BRFG6Zp1vxikSkynpE21pWFWWnvSbbegxbcSzBnK1MuKWd5dtFxzFgRGws98ylZjLy8aVT5KV9qOAKNhkKlwQqY6BLiukX%2B698t6o0%2BWW3E5RDDaTeyT5opV8kISb9sV6QQUD97FDEJ96RFRYAbRNFIExNATE2iZBinEyTAerEH9oKOjuVNK%2BNSY9UmR7CSyu1SVD5THkxHcUmip7FIfP8AL%2F1R6pc2o8mgfaavxwHkWlV72EEhS9lRMEq5kGKraVOdVJEBIGe4RIpsDsjrngb4V6Tnbi2oV7H8k89grDrSfGW23S0qfnHBduXDg3SAAVKI3tbvjxcb3CrSchcZSFYwJLzgwbiltTkg3MLLqpCbbA6aTU4d1C1nEE7lCje%2Bm8BycrqmClbRXmG9PKPORAS33iaIAG8R88BUAvFQIFoybLDL3FGauN6Pl7guVZmK3XZnxWTbeeS0hS9JUbrVskWBjotfg0%2BLFKCpGDKEuxtZNfl7n5YDlJDYMbHyayKzHz0xOMJ5bYecqc4gJXMuEhEvKNn4bzh6qB8vcI3OfBt8WEqjWvANJd8zddlifxxvDF2Acx8jcgctOGHK%2BizEhmZmrOTExiFcgtKXnVI3WwqYB6rSE7qUDbSk25wGsE%2BDUx%2FMqVTKVnRlVUMQpH9omqwpMwVb9UK0kX9ItHMmZGV2N8qcWzuBswsMzdDrcgAXpWYA6yDfS42sXS42bbLSSDHRk94PDicpldpkvSML0OsGemQlFbotXQtuTfBvqfe6rrRB%2BEL79sbUnsCZkcX%2FAAxP4arMgzXs5cmMVvYaZqC5xoKqUnb31pyY8h2ybEKvuWwrmo3D53uN2iipABjqZXg6uLlQ3yvY%2FjqU%2BnEG%2FBucXL6ujbyxly52J9mpSx9euA5YhHvq9KnqJUpuj1RhUtOyLzkvMMqtdDiFFK09xspJG0eEi0BWY8hz%2B9qjs%2Fwhiy4zkotXM5c0wn1hXzRxgx5Dn97VHY%2FhClgzOTKPtctaT%2FTgON3D1ohfeIOHrRCAnhGb5Q5M5iZ5Yncwhlnh41iqNSy5xxnpkNBLKCApRUsgc1D443CrwdfFum5GU2q3dVJX6cBzW23eNsZI8NObHEDUHpHLnDhmGJM2nqlNLDElKX3Gt5W1%2FMLmM8Pg%2FeLaXl1FOTcy44dkhNSleff5cdHZ0YNzJTM4K4G%2BGxiYk5Sj4YareJX23zKoU64m6picmBuEElQt2qI5wGoKt4NLPBinzUxhPEOB8XT0k2XH6XSK0PG025hKVpCVHzaheOU67h%2Bq0GoTdIrVNmZGdkHlS01LTLRbel3U%2BUhaFbpI88dQyHBfxl5d4uNVwphSapVWpco5V5XEdLrbQllBqytpnUErUbbtODrC99jG1M98oMa8aGV2WPEjlhl%2F47jav0xdOxfKSzjUsl12XJQiZOsgHrJWjmTpUkckiA%2BeBa57%2FLEnR2PP5Y6YX4Pji33tktPbd1RlPyuRbq1wF8V1Co87Xqjk1Um5Onyy5uYWmclHFJaQnUpWlLhUbAE2AvAc8HYRIVb3j0ON2jzqTvARConCopjsgSYCsFAxVbVaPKlW8VNVu2AuDblxHvYcBRaLOyvePdKuEqtAZrQP7WOE%2FbRbpYFWN8NoHbV5Mcv%2B3RFxoRtSHfOoiPFSrnMPC6E81VqRA9PTogMfrTi%2FdJrK%2Fta5Oecfohz5IuuHwDmdThtdVUlOQ%2Fdoiz1r3vMSt%2FC%2FPic%2F%2B4XF4w0k%2B6xTEdnstKD%2BWiA%2FSNCEIBCEIBCEIBCEIBCEID88%2FFCnRnXmGnuxTVf%2FALt35400reUR%2FC%2BO8br4rUaM9sxkd2Kar8sy6Y0mf0IPNr%2BO8Bl2GU2pXpt%2BMxepGQn6pPStLpck9OT08%2B3KysswgrcfecUEobQkc1EkACLThkfnZ60%2Fijf3Bw3hd%2FOlljFNCpc2linzFTp9TqdS8UYo07LDpGpkjUkOkr0o0k7AkjlAYrlnkxXsYZiYcwpiaSqlApdXxE5hx%2Bov050tpn2UKcdkgQPsxSkpB8lJ3OwMXfPPKnC%2BBaBgvGGFqXiygy%2BLHKpLOUPFbSU1JlyUcF5i6Bo6FSVoSkc9QVzG8bsrEnnMjI3Mt%2Fiok6Pi2cpuitYUkHa23Kvsuua2nqnK9AUlbKNaChIBKrKF%2Bcch1qu13EM0mp4lxDUq1P8ARNsrmp%2BaW84pKEhKRdRNgABsIDyyVNdqD%2FQS5SFkX6xttFx9p1W7HGPjMeajVBmn1JqZf1dGkK1aRc2tGRnGFHGwL5HfpN4DG6tQZ2jIQ5NKaUhatIUg3sfPFsJ7iDGR4mr8jVZFhiUK7hzUu4t2bRjVx2QFS9o7syRdbl%2BDIvPlJbTTMQFZVytpc%2FEY4RB7DHdGTaUzXBe%2BysJCVUqutj0gOH5Y%2BbfCbOVxuv8ArR%2FJW62EfKV%2Bhx3gNv8A4KXm3NQ6PEjKut3mQVv6bGMyy2l3K%2Fjb2vPVGqMSApMzNKZp810CnHQpIQpSrHUE77RiuAk9JlLNTB5%2B2WXCh6ZAxdaJO1DD9ebr9FfXLTqJdxkPtpClJaI1KASdje3Ix9Es9VLmVznk277nCEJK%2FZrEQA%2BD48pRjB82qBJYexbS6LS5qdcTMshxT0y5qc67oFirt7T5ot8%2FxNzLIbQ%2Fi%2FEyekGoKXRZS%2FqsuMaXm1lvVsQS2IcXVrHFVcl3G1qbalZVrUlCtQQkqUQkEjfYxlhR4qhm3K4PqTrbOWlBmplLL7LEy7MTClNFYW2HAkq0lSQSoXFgqxttGq5vEKX5tbjMoWkq%2BCV6j6z2x68W1WVrFRXNSd%2Bit1Qq9xdSlW33NtVr9toxlbehy8Fl%2FZq4t1pcn0ER7RV23W1NrSpGsWuCLjzjzxjbavNFVLunsgiW3nc3pavzDMlM5aYbbemlttLmpV%2BbbWFEBPSJR0hQk9trWuTyi4zDfRrUj7RWmNO0aotyFXkZ99txxmXmWnXUNqCVLbSoFSUk7AkXsTsDG553MjJB11wyUvmElsuKLaX2pIlKCdgSle5A7drxVLwOd0SOTM3IMmakJp2VmWtJafaNltqvbUnuO8V3Mb5QLYWRJ44BIJSejk9IPZfrXt8sV5ukt9I7KzS1mVRcuqQgqWUAaiUp77RZSYzdJTWG5ibDTgbqmlTLZ%2FRj6k6tAuoaj8I7n07Ri%2BZ2DJGXwDUZl5meQ%2B080rpXppxXVUoC2hW23O%2FONMDOuhSaW0jEWN2UONhQF0EaTsCCly%2FZEqc4cvZ19o16vY5nZRDiVuy6W2E9IB2alrVb02iMiYzeOpZrs4RqD0kzgShTDrCClmccQ8tYJ2Dukr06hzG1r9kaum8RS6ptSpNt1aXAFKLwGrX28oq4qqrVbqLk5LI0IcPVBN9rm3zeqMYcBRMCE61oZRL11xbdvFkpj1%2ByZW1pUgjULAhVoxxhywj0pduPRDJDbKs3%2FZt9iXmcv8MsLcLcut2TadlyT1U6wAsgK7eVrk7RdH%2Bo4pv90U%2FEY07ITqJOek5xxsuIYfQ6tANitKVAlN%2BwkAgHvIjbk3mPku%2FNvuMUrHrcut0qabLkkVto%2B1J5KPn2iUwlci11WYmZKQenJSYdYeZF0ONqKVoNxuCOR35x7049ynW2oJpeNkr30EuyduW1%2FX3R7PEEPO%2BJPhRlnFe%2BBIBV0YGokA7E2giJdDOYQdqiZeYXJ1MkyrKVuCafUXVaR1jdXMxYsf4NprOX9Wbeps0mbbW0pD7s06SlGsApCVG1vPzjUEzndl3KJbZapWOUK0IUjpJqWto7DseZES%2B7flFOlCapQsfOtpUhTiGp%2BXQV6TfTck2B7TYwFhq2bbmE6g9T5LAGFHtLK0NPTEm44tGtJTq3XYrTe4JHPe0avXiFC5hXQNqCVfbKF4rYsqUtW6s9OyQIZVcpBO4BJNvVyjGwND4tETrM4llUvWSv4EVhUVuoKRdPnTsR6IsDbmiK7cxEjbjucDuJKtLpncvcIsvTjjMs47JSS5dW9kFYAXYKNrk25xVmEIbWtA%2BCop%2BWNYUKps06t06pTTBmGJOcZmHWQrSXW0rBUgHsJFwD2Xja8%2FmBkPMTMy7J4VzCaaceUthpdSkldG2SSEE6etblfblETrFuK97CFYedlaFMzMpMOszKAgtONLKVouoAkEbg2POKq8bZK2szhvH6VaCEqVUpJXW7yNHLzD449b9JtVF0p9a1sJUpKyEbqQlJWQBy1ED44RA6TmsIGtqYqLsgUqVKsNuKbmFpS4UtgBagXDdRtcntNz2xh%2BbGEqdTMup8Kpuid8aZW1MKfUV6CpIUhIKiLWN%2BV7xpGYzbwHIuJWuj4tSpaekT%2BbJYjT2fB5xQRm3ly7MsLnaTjB6XS6HH2UTcq0XkjcI1aTYE2v5olaYzUp3N2q4IqzzNNwfhNxTaHG2X3qcpbyAtJSVAlzSVgE2Vp2O9o1i1iF3XpQ2kAcgSdo9OKaq3WKg5OMoKELNwg%2FB80Y4z%2BiVXgqylqurUOshPqisKyhXlAj0GMeSrzRMFHugNsrzXn8UzaKbMYJwk09PrQy7My9PU2%2BRsNST0lgs9qrb77RK5724pHSK6iikee0a9w1VmKRXpCrTUuZhiUmEOushVi4gHrJB7CRcX7I2RN46yimZtx6Ww9jFppSiUtrnZYlI7tWkXi48uvzRMjnETi%2FLJfVTQ8WIBOy%2FHJY27ri24vz80V%2FF1tudGvrKT1fyxTLNaYXrG4twxyh78ylH%2FAPhgjsPgWdW7w8yGr9KTVWwe8dMD%2BW3qjkHHTKU8MUkNRsrMle3d%2BdgjsPgYP%2F6c6anRYoTVQT9t7%2Fe%2Fyx85%2BEXVcaI%2FzKfZLtYT%2BdV%2FDPthwdMJ0zrw%2FwC3eP8AnFR0HwM392mcv%2B1%2Bb%2FnIjnyZCkzzyV8w%2B8D98VHQnA5YZzztxf8Asem7eY6kR2tNJ%2FIFvP7u5qYdqvVPpT59noOKDEKCNJXlq%2BSvV2KYt%2BIWjTclOT0g0ZmnzypWaVNyLTb6La2wqYSlRTcEA2JF7RufP5oHilrwF%2Bvle6Tfv6E8vijSTiUFnQ7cthbbxSDa5bVqHyiNjRGM8Eu0%2FuR7GvfdVtV6W%2BalhObmqk%2FMIquJUNFzqJXOKWpA7r6Bf4oxPNfDMvRcGtzztSqs1M%2BMttlE68HEouu%2BpsWBSbbHfeLK9mpMyQKa1mnXpOZaDfStpkwtpClDUlKVqWCbAje1rxYqzjvDOKAhmuZqVSdaSQvQuUbtqHLbX2R6SNbWW16u4awpTmH61hZmrl5hp9x12cfbUelKrICWiAAAnne%2FOMDx5mFSMVVuYqspTkySpherxaWQpLLCAlKUIRqJUQAnmSSTvF6zNquEqiz0OF5%2BZflG5WSlWxNqb6dbjSVlxwpbulKSV7C5IAFzcxqOaQph8Enc9sWyRMMjbq0moD3xYMekTjSyPfFERi6XSkC5BMetp9W1yQIqltfCmYOFqNhyWotcwPTqpMSbzriJxc1MsurbWQoNqDagkhJvY2BsYus1NSk70U%2FIy%2Fi7M2ymYQxrKuiSrkm53IFuZjTHSdI2rrxuyiV7KGewzQzU8T1%2BRqsrTmpafZRJMOtF1BIu2ouJOkp0%2BUL3v5oSngwtjjljEEalutpB8pQHxxkCJnJ3bp8b14d%2FR0pk3%2BN2LTUhS25kTuHai9OU59BdYdfYDTmxKSFJBI5jmCbxGRk27glrEOIcC02aXi6tsq8Zm29EutpLCWW1hLTaUhu4IsSTc3uIv7GEp%2BZZfYn8dYpAEu4plLTrJQVgbBwLQbt2vcDfujWVGzFbwDRzQWcb1SmutPFbzLUi2tgOrSFqSkqVfkoX29Ee1zPSUqTCGKlmdVnWlGzjbVNl2wU9o1Fd%2BUMjJgc1iagYdkG3qzheWnxNFQS6qcfb0q3JTpb2tb1xhWL8dUbEVefq9PkkU9l8JKZKWQpLEsALBCNZKiLAbkkk3MXPNOZwvNysozhSfemJZgIQDMFHTLUlB1uLSglKdSlWABOwjVtih%2B0SrEZMmXWpBxvZx%2F7iKaazIJ%2FTH%2FuP9cWMLNt4lWu8I1JbcoWamDpXD1PolYwlJz0xJ6z44t6ZbecSpRVoXoVpUBewNgbRdHSy6pMzLsdA0%2BhLyWQoqDYVvpBO5A8%2B8aOBvHQbdSypmaRSnXsTVuVqIkmUT7QblnGA8lIB6IhQUEmw2ULg3gLVqT%2FuIoFXWGvlfui7uTmVoWFDF9bSntHibKvxLjwVBMk2BMUicVNSjjXStLeaCFncgggEi%2B3YYDatJbrT%2BHKMZTEVck1ty9ngzNXZeJWohQQUdSwITYG214lrEtWkUCpT05jHETjzAaLCFvoVLrTrHSJdSpFzcWAt23vFgYxvhfCci1T5zHeKZSfaSnp0y8uymVSspCihOtepQGoC9olns0MJVpjxWfzCxJMtgg9GZeU0kW5EahfeAx2cxfgrBYabrGCJWrPzJW4XX52aRayr6dLRCQLWHfGvMXY4pWJcS1Cuy0giQanXekRKyqVpYlk2sG2wslWkADckk7kxc84JzDFRdl14VmJp6SZASlU2W%2FGFL0JC1rDV0pClhWkXJAtfeNYQTDJU1qSRzee%2B5is3XpD9Wd%2B5jFSYIXaCI1N10jNPArWHqbR6vgKSqs5TkOIE%2BqZnJd15CllaUOJaXoJRcgKABIsDyiep%2BKmfWuSllSzDqEPNsFwudEFJvpCiLkDfc7xpuXc98R%2B%2BEdAPzWU9QlpJ6cxRXJOe8RZZm22JaWfYTMITpUWldIlSkKFj1gCDcQRLFlKIMQbUlb6EKUbKIEZME5LBY6THWIrWGpKaYwVA9v6bYxbK1I06Rnm3MOVJ2fpr7QflnphgMu2JIKHEXICgR2EiBDaUsuuu0emNsV2tsluWu4W3kltSys2KE6OqkJATa55XvvaKGIG621hucfexZXVPNOsKSl11tTDjesBaFpKN7g7WPOMbk8f0fD0o3TajmTXZCZSmy25aVSGkqvdQTqXuATztEJvMjC1SATN5n1adQiy0szMiytC1DcXTrAIv5%2ByCfzmK1DEOCcMmVYxDg9VRU814ytxM8%2ByVoKjdsBs2SNrX5xg2McZSWKcVVTEUrIokUVGZL7cqwFBqXb0hKWkBRKtKUpA3JJ5x7s3JjDc3U5NGEZ9%2BckGJUNJXM6Q%2BpQJ1KWlJKU3UVEAHlaNfI2iJ1phkzNaZ%2BE4qDtWklc1rjHA4EnnEFvRKG4KZmJl67S6fS6hhCYqVRYStrxtupTEst7UeolbYui6b6dQ5gbi8UZgNh5xSULQ2pV0IUsq0Duv2xq2jTCWKxIvOOBtKX0KUTySL9sbveeyonWpea9u081NFpPjLBkkrQh34WhYX1k91wD3wGPdXvV8UTItq5q%2BKL%2BG8qv8ArEqBv%2F3Pcn1BceKfkZWXmiKfNqm5NwFTDxa6NS03t1kG%2Bk%2Ba8BluA%2Fe8vs6XOv8A8nq2%2FMdVSlOfmjP%2FAAbyl%2BzGYVkXR4pSrqtyPjKrfljAcFIBy3zpJJA9oguR3ioSxA%2FHGf8Ag3SVTeYbffLUk%2F8AqVCPG6bxngt49HvpdXCo%2FtNP9ckrFxjm%2FEXisdyZMf5gRgWWBJzKwanur9P%2BPp0xn3GSsK4icUWQke9yRJB3VdntjA8pQDmfg7UL2r8hb78I2aZy0apmPI%2F8WKn9K8%2FCh094Q9IFAwC7vdOOm7WNti0n5o5xzGctnHizxn321fm9aFb398Vz7zyvHSXhC0n2pYEUNFhjZjUD5V%2Bi2t8t%2FVHNObF2s3cZqZVuivTZSr0LNjHN%2BDj9RUR%2B9V7U4pGV5qbmwbhyoYowJhyrTOLK2uampIKmEJU0GkkEhAbsjYBIG3eIv3ua0xVOqTNQqVffQuUeUlCn0FoqCCR0idN1J25CNLYSzhxFl%2FhaUlncUzcnTWEuNyTbFKTOKTospZUVKT1RqHeYlqvEzJ11h6SqOY%2BKQw%2BlSFdBQmWzYi23vm0e7c5hNIcpVMw5M4hqtAYrXiy22kyr8y6wg6m1KJ1t9a9wLdkWLEOaNHxRTKfSKXgCnYcZpnTOK8Umnn3JxxwpJU6t0k9UJASEgAAnvi74ixVlv7SXqFhOdxFNz780X3HJ%2BUaYZ6MMlCEJCVKUV6lElRNrCwF408hZbXAjUysVhkN9WXVft3gK6keTLqt6Yx1TxDdwN%2B3eKJm1A2A29MBsXCmYVPw4mptVDBNKxBL1JltstVB55oy6kL1pcaW0pKgrmCDcEHcRf14ipeLJJVXp2DpLDobmPFizJTTzzLvUCgr30lQVc72Nt%2BUaeQ6Vb3jZuXGLcsadhWdoOPJfFQnV1BE1ITNFal3G0t9GUuIdS6pJ1XAKVJNrXBhnmmHr0%2Fux8UEp98HXEXFzFmQ%2BtIRNZlWv17SMiNv3J6T8cSTM9gSrSpnMCzGJiJMpROIrkuw2pQWeq4gsqULdhBtAltXJqRmqjRq3JN1asSrTamuiTIzhYQlxVyVrSB75dIsBcWO%2FmjYNMwW%2BioMKmcU4rUgrSHUt1JSVFNxfe3dHP%2BHswBl6w9VpmtV6RM7dsClssuApRa5cDpG11C1t4vTPFBLWSZjHGMzp5hqmygv8avxwQtWP5mTwhiSvT83RGMRMSUyWEt1V5xSw2Vq0FSmyCpYAAuY19iXMuXxZJUuRkcHUjD0tSi8UNU%2FpFF9bpBU46txSipXVAHIAbWi742xngGt0KaYoT2J5yq1CaVMTk1Vww2jo%2FgNtoaJudRJUpR7rDnGqZRxWgbwGRCqqCtQHyxM5WFrFujv%2FAAosod2sYmDgHf8AHAbAwZmWnCEtVJN7CFBrstVEs6mqoytfi62iSlbKkqSUKNyDzuDF3XiWVxPLprUthanUQdMqW6Gn6w0dKQdRC1KOrfcg%2BqNU9Knz%2FHGw8DYxyzkcLv0PHNNxOZ1E%2BZqTm6M6xo6JSAlbbrbvM3SClST2kEcomZRMZvWXT54qNnULm8VVYyyOF9EhmKd9vfJEbQXVcG1ZvpcHy9fZDBHT%2BzCmFageWjoeVvPELRDaGV%2BG5GvYWnZqaqNYYmhOpQ0uUqDrDSWwDrC0IICibiyuYtGZU7LKivVBhqexBiZcstwBxLNXeQux7lFVhv5o1JhLNKSyspPjlSmcWoM884Uoo65RDAbSoJusTCFalk38nYCLw7xcU94Fv2Qx5bsURSrj1BqBkxnENZawQ9WK6cOUivuS80xJaayhbwSNK%2BsAlSbq2FybxgeKsyn8bmnrcw1QqG1TWVsNS9HlDLtrK1aluOXUoqWSLXvsABFxzGx9l%2FXsNO07CNLxO3OTM6ucnpqtTbLnSqsA2ltDSQEpHWJJJJJHK0a1lXCEC8EL2mpFHZExqmr4MWhTlx5UQDtvhQGfYTzOmsJUup0dOG8PVmRqrjDzrVXp4mC060SUrZWCFNkglKrHcRc5yvJxVIy%2BJFYeo9FccfflyzSmFMS60pIIVoKlWULkXB37o1f0w%2B2jYmC8dZaUzCrNBxthnEc%2FMy08%2FNNTNJqDcuC04gDolocQoEhY1BQI5kWgI38xiYcuRj2e6JkikpPtExssA7gV2WTcfeoru1PB2Iac5VsGUet0puTdRLvy1TnWZsu67lLiFtoTptaxBB5ixgNqZO0YVTDtRllyRmdUy3p1LWFtWHNFlAC97E23jYlNwFSpSfYmJzCweaQsFSHnXSgi%2FI2WNvXHOCMZ0fBNMlJuvU6tzqp8OOIVIzrcuhltKygIGpKiokgnew80Su58YUIUlik4uSFXuFVhk3Hcfe94jIS4yri8GTFRqdOpNJqN6s5KoFUYM4kMhHVA1KG4v5Rudh3RhOJMx6njBVPfqVLpMiilyniMrLUyUEsy23rKydIJupSlElRO8enHmOMKYioMpTMOUWoyJamHJqbdnplLyn3FWA06QAlKQOW9yYwPpNovkmF79nT%2Bt0%2FHEHKyVJ%2BxJHrMWXX5oa%2FNFUM7w5mfVsLU6YpdPplFm2JxxLq%2FZGQTMKaWkWCmlEgo22IGx7RGW0%2Btz2IpZNTqEpIS7zvNEjLBhq3ZZAJAMaX6SNnYPzKwbScPt0uu4SnJycac1%2BNMz3Q6mrC7RTpUOYuFbHc3iMjavkwHUp0na%2FIxQbQ6Fdp%2BOKb%2Ba%2BX7qjbAVV0k9tYFx6OpHtkMR0TEbSpiiUSbpzDBCFImJsTBVcXvqASfkiRn2QzP%2FDVgtZNrz7puTsPzK8d4wfgHS%2BriDpfi5vakVMuJuOs30R1fkjYOQLpRnRg%2FqJP5tmAUKFwQZN8H4hv6owDgE6nEBSFlCVaqTVBc8k3aPW9Vo4OkerDLfPxZ9kt3Do%2FtNE%2Bdurj%2BN8xsDjuwiB%2F6oxy9HUXH4L5kYKvzGERYf4zHLsa%2Bhn6ju8fuz7ZUvlX4%2Bv0pDEHG3HG1Nt%2BUtJSn0kWicjtgnnHpmpOp9Aq%2Fhqa4keC%2FCVMyxnZVM3TWKa3M091YbadfkUlt%2BScI2Qq9lo1dU9XvjjfNnJrMbJ6iy8zmLQJakGvszYkW25tt9xYZSnWV6CQny023337ot%2BBMzcwcsKg%2FVMvsWz9EmJpITMBhQU0%2BBy6RpQKFEW2JFx3xWzDzZzFzbclHMxsTrq4kEuplGyy222x0ltelKUi2qwv6IJdVcZC1M8OGTTqyEkOyfVPafYgcvR%2BWK%2FDHjDiIw5hLC2A8RZHrxVl5UGmk0iqIU2FydPfWV3dQvU28yglSgFBKgBYHlHJeJc08xca0ClYVxfi6eq1IoJSaZKTGjRK6WuhBTZIJPRgJ3J2EZJh%2FiYzzwlh%2BUwjh3MGelqVIsplpRpTTS1S7Sb6UIWUagBc2uTaA3BxC0fLPIXixy9xJh%2BRlKXSekkq9iCnyyT0EkoTKmg%2Bhs3LaFt2d0ch0aiAIz3jH4fcz8y8cULHGXMmxiWTboopnQInkILV3lOCYZCyELbdSpBK0m%2FVHZHE1YxJXcQ1SZrmIqtM1SpTqtUzOTjhdddNrdYnsA2A5AcozHA3EHnJlpSUYfwdjicl6QzsxIzCUzDMuCblLYcB0Jv8ABGw7AIDZXDXKqyK4tpLBuYiqfS5pLEzh9xaHUrYlp2al21sp6QbDUVBBPIKVaMw4kuETOXMPO3EeI8OU2TqNKxZMMON1Gam0tqpQ6NCOiebV1wlkoJSUXvcW3vHK2KcTV3HNcn8S4xqK6rU6msOTT7wSC4oAJGyQALAAC3KwjYFC4qOIHDtFTQKdmZUlyrTfRsKmkomH2Baw0OrSV7Dlcm0B0N4QqrU%2Bl4Ey5yxfnjP1%2BTe9lHZhabOGWalBKl5QO4LzguAdyEkxw8d4udbrtbxJUZitYirE5VKjNHU%2FNzbynXXD51H8Q2i1HnAS%2FCiZPOJU84mTzgJoGEDAIQhAIQhAIQhAQPPly7Yavl7Yh%2BXsiI58%2BXZAR5xIRaJxziRyAprVbyhe24iCVavJ7NoLUCLc%2FwAcShQUbjYQE9tuQidAFuQin67xOgHvEBXQWUMqU4uyUqHZe5vskDtJ5WHMxstOU%2BIcC41omEs18Xs5WtYvoD06KhOKLoTIO9XxeZZZJWgu6bdGq3YTFiygx5K5W5l4dzDnsJSWJZaiTYecps2BZwEEdI0Tsl5F9SCoFOob946vx3m7Rc0M3ZaTyRyTyrzXmcbUn2ZROVdpxmqyxQno5hif1qCUvN2FrEWSU274DS1b4dcJO5c4zzEy34g8L44GBpNifqkhJU%2BYl3Aw66GwQpfVvuSB26TGjo6mwtkrmlkvwz8QhzIwo7Q26xRqIxIB%2BcaecfDU%2BOkA0KUbJC7AnmO%2FeOVlqKG7oX1km9rXt5wO2w7IDfvDzwm4nz1otSxa%2FV2aBhxhEzKSE6qzjk3VG0jS0W%2BYYBUNbnMchcxpvHODMSZc4vqmCMXSiJasUZ8y06024HGw4ADdCxspJBBB7QRH0LyIzh4Wcusv5DLjA2arlV9jW3alOKcp007MFbgDkw84lDZ6NsK9SQOccwcZlcySxrjSn5h5R5gMYiqGIEODEMqyFFmXW0hCGXm1KSCOkTcKTuLpBFrmA54jMML4TzH9qVVzVwkmel8O0qY9ga7Vae8C5INTSAlfToSekEupC7KVaxvbnFmwfXmcK4ppmJZnD9NrrVNfD66ZUwoys2LEaHNO9rkHbtA5jaOuck%2BKrK3BmG8V48m8qsBYbqM4W6HJ4Tw248Z3ETzliBMNu%2B9CUHSKBcIJvqG19w1LP8MOHpjB%2BK8TYD4iMD4xewXQ1Vyfp1LYfSvxZK0p6q1DSPKHP0RomOrsvcj81coMreIev5j5fzGGZCr4CXLSHSOIcaCzPJUWUEKJ6qVgC%2FMJjlBS13gJPhCJz5MSb33ifshA37wvG0jipdr7yqLfwVn%2FAF%2BqMEwdgHD%2BOOJvETGI56rSsvI1V%2BabVTX0svdIgEp6ygbbgct7XjPOFvam4ov2OS57e1tcWbJ%2F%2FwCJHFribr0Tc2rle%2FvRt%2Fv5o83dv1tb%2FZ7n2DHqYnQW4R%2B9n1Wi1zMwqZfcfcS2FuLK1BsWSCT2eaJs7ZxpnKXKykzb7yJBcziCoqYQNSVzJdYb6VSfttACQewXiUtAuBCRzJHyx5uJtbMtl7lV0ZSbMVskAWJPjDV%2FxR6PJ8fiWq2JrDOnUqad6vfJm4iy4xm5GfTL%2BIvl1LaiCSgpPxGLU3UkI5ao80xNBxeuGS6n0YRC4MUlP6okLtjvEqKjiAsgW5xRcQtIBHaoCKqHkgg90SuuXAA7FAwGyZFVAFHkGHKmw24hizrZaUbHnYx5p2Xw6%2BhSET8np0lNnWTuPijDV1NC9XlR5lz%2BtpzyvJMB1Pi2v1jEOHMvZuuzip2bYwXTZQTKzqWtpsupbClcyQmw33iz5vzSpnLHLLD89PpZprLlfn%2FFXEqLK5hUwygvlIFisIASCeQ5dsemtq0ULAbSQBfB9MJFuRKVn8sWPPpa2MF5V6zdPsfWinSrvnk3vEwuwOTp%2BHEEKZn5BBG4KWynf7mLPjXxeYn2ES8w26htkJK2%2BSo8aKmyR13FpPouItr04hbiik6t%2B0RCiCWEpiYpRHnXNiJfGgYCdUsnUV2vcR5wwEOJCUaiTyismYCuZtBh1AmULUuwBgNjyEm4xJyr0tUWJdaUbFMyGltq5dUggiJ3qzi%2BjrE7S8c1CWm2RrZfarjra2ljdKknXYEERrxybl7q99HPtTHlfmG3Jd3r%2FBPwfNBaJzdd5y4vq2YGMKPjnEBlzWK5hSizVSWykJS9M%2BLBK3dvhL0gnzxjblMrNZwVjOnUKpS0pMuUJ1bqZhkrQ%2FLIcQt1sKH2NZCQUqItdNri4Me3HzbbVUw8w3ybwnRUn0%2BKgn5THsw1K68MY0nAsp6HDU6T3G%2BhNvl%2BSJlMNreD%2FJTlxMrvYCam7dW%2FJlR5euOLastK%2BnWNgp54gd11q2jtTgDGnLSaV3zM6f8AMkRxNVdkK%2Fvjn89UbueeHWf8UuTd4%2FKNt9jDXvKikrmIqu7ri5yVFlJijezczUWtLEz0EzKNH81IQpF0PJQdlovdJsbg8%2BYjRdNGgTM3TnkVaWeW1MtlbcuEbFd0kLB7CkAm4iecqDtSoshRG2GnWqU48pqdNw4UuaT0O5t0aSkqSOYKld8eN16W8XEkmozC5dpa3G0Fu1lKACiO64AvEqKktmRepjMw8ZR9xLzjKkDSXEghKu8EAkbd8BSfkJphvpVMgp1adSVAi9r227bR57fzo9LDjfRqZcU6hhxSVOJbRfdN7G3rPxmJH%2BjK1KbTYKXdNxa4t2j0wFI84miU84mgJTziQ84nPbEh5wCEIQCEIQE0eiTkJ6ouKakJN%2BZcQnUpDLZWoDvsI88XKjJqo8aeo1WMlMIbGoNzRYcdb31BJuNVrXIvAGqeqnzZlq6zM09amzpDssSoE8iUmxtz3hKuSsrTZ6XE30vTugNoS0bkoN0u6j5IIvtzijVJmqzTrblYqL84%2BEFIW%2B8XVpT2AqN9u4R40a4CY8oliY8jEsBfcJ%2Fo9X97MZeLrPWjDsKL0VEq7m1Rmd4CoEp07xIFFJ35ROCLb84lAJVc8oCom6k6r9vKBRcXAtvFVtsKHSXtY8oXK1d28BkOWnRDMnB3SJUT7Y6VpA5H81t3v6ov3EA90%2BfOZDtrasV1Pbu%2FNC4sOXgWjMTCC9O6cSUoi%2B23jbcXrPLR7umY3lafbVVdOnf%2B6V9sBg2pKuuhAAAsrfmYmLqkgEW1W33iVtu%2FX1iwPdziRZIN0EHfc2vAVNR0aybaja1%2BcQKwRYp2UO%2FkYlKQdwb3FuXKI7qRcC59HZAU%2Bv5onAPMiGje5ioAO0QEtz0ajfbTe1xHYeCVoThXD6i4Qr2Ll%2Bpbl1OccdzCkhpSU91o61wJ0qMPUN5WnanshP73T%2F8AmL2Py0eifcxXj5L7Y97bstiduiU9FckqRKTbtPYce6CdTqZdUU6NwLEWKgoWOxAjdWHsaoocjJSaWXilmWbbbFzcAJFt%2FwDe8c8yMg7Wqa9SmhdU0wpCSBug87m%2FZdMdRYdwfQ6hh6SVNNB9brCFlxJsbkDlG5XVwao4MOfZUTXFUTLW2fmNlYpwY7RRMuMqm9Wra6uVgrnbY72POOAqhh%2FH2XOLJHFMpV5ulT7jKn6dW6a7cTsuFdGpQtz0qBStpwbHsIIMfSHHOQtGxbKIlZeqzMgpJKSbagtJN7Ht5xxpxEU%2FCuWOP5DCMpX1Ygfk5BTtZcZsluSeUfe2jc89ABUOY2vHQs7SbeiKac44PN9rXmz7nr%2FCmJ4XP9iyZoNvVjBtBxvjfGr1dxtVJoUyWlnGGmZVqQDepTiUtpTpVrO%2B29zFqzXm5bLDKTCWVkhLzkvXsXSLGKMXz5fSpM22VLTJSTJbNvF20hSyk365Fze4GG4jouNarSpqdGE59Mgzadedbac1MtDyX9C%2BskEG10ixHxxuLJbIXFfELlkcCYkqMs1K4cl5qq4Xr8z1H6IySVOy0yo7OyLy7lKPLbVdSercRgtLamyqpmjz888vuhmosJmnKvw5zGWyI5N%2FhcuLxHMyj7b0o6tp5hxLzTqFWWhaVBSVJI5EEAg94EKPPz1ZnJ2cn5x6adU8p51bqypS3XCVLWSeZUq5J7TFR%2FDyujW5rT1b%2BSbhXoPcYjgmXSlM%2FMKRqQp1CEk8hpG%2F440bSKonKp0LPKY4VLJ6bWXKLLvuNr6rrC2%2FK2FxY27ja4%2BOMEnnPGPfIy6rIb9jJhxtxv7Geqn8fpjEej6unviszOWS0RG1rqtHRU3yewD8UVqy5eblx3SrKfiERxMyG63MtD7RJ%2BSI1hq1QaH%2FANO0fjEa7Ku1G8kfvY8%2BIfsCYr0f7Gk94ijiIWaSPNAY8OcTjkYkHOKggJYRP1fth8cLJPJQ%2BOA9mKRalUQX3DDm38K%2F5YqsC1Olgf1ERNji4kaCC1o%2FMHx9Y7xKk2kJW36kmApg3OmMkwJhStYvxBTsNYekVTdUqk23JyjKRcrecISkeje58wMWCXYU86EI8pRsI%2Bh3g9smKPgzDFZ4qMxkJkaZT5SZaozj3JqWQn81ToB%2BFt0bZ7ybQGzcxqHO5F5LYS4Qsl0MzWYWYTMxIB5p%2FoNKSi9RqLjvwAbFtCuwA25R7MJ4dqfERkRi%2FhVzemqc3mflyJKmvzrMwmYR4yloLpdSS4nmFJvLvee%2BrcxrPIjNP2z45zk47cxmw1SMKUoUPDUq8QEtrc%2BxS7d%2FhaOiSbblTqo52ybzozByizaHEjVqTXKjQqjUHJXFc4ZR0S09KzjhU630ltJcSffG973bAEBoTEmHath%2Brz1Fr1PVJVKQmXZScllixYfbWULbPoIMY86jSoiPoT4R%2FJCSmpyk8SOA%2Bjm6HidDEvWZqWA6NcwtsGTn9uSX2gEKP26B2mPn7OMKSTcWINj6YDwlVja0Er%2BDaIrAFj2wAAVeA3lwZYpwzgfiZy7xRjGtSdIpMjWEuTE7NuhtpkdGsAqUdgN7b98ebPjHkzP5045qmFsWT8xTJ3EE%2FMyb0tVJjonGVvKKFo0rAKSNxbsjP%2BATL%2Bg5l4zzCw%2FXcIy%2BJQMvas%2FJST0qH1CbCQGVtDmHNRSEkb3ItHP2KMH4twJUG8PY3w1VqDVWpdtxclVJNyWfSkjZRSsAlJsbHltAehvG2KlKs5imtAeaqTP9ZHbWW84OMnITC%2BXWHscGiZ75OqeeoDkxPrlna5TVAgFqYCtXSBNkqNzpUgauqu8cBdJHsp9WnaXNsT9PnZiUmZZYdYfl3VNOsrHJSFpIUkjvBEB1RhTIXjnoNdncIYbwhmLQXqw6fZINVBbMo8Sestx0LLe9z1k7mMzz0q2H%2BF3Iam8MeGcVoqONqtVvbJjKpUyYUlMu8B73LBxBCtXkg78knvjnx%2Fi54jp2kKoU5njjJ2SW2GloVP8AWUnlYrCQs%2Bm941PN1KZmnXHnnluOOKKlLWoqWsnmSTuTAZR7p%2BPraTjOv27vZib%2FAKyN88DGbaqHxRYOquYuZz9NoLSJ3xh6s1l3xUqMurQlXSLKblVrX7Y5UDytVjHZ%2FBtltk9mPw%2F5rSObFMkZcTdXpVEpVfeZu7Rp2cSpuVdSvmhHjBbC%2BwggHaA5ZzRmmJ%2FMDENQlX0PMzNUnHG3GyFJUkzDhCgRzBBB9cYnHTfH3lthzK7OWm4Xw%2FQafRlS2FaQJ%2BWkGQ0w5N9DZ10JGwKlC5PbtHMkBWlRqWU2vcEW747C8IagoquUDINyjLSj7dvJyOPpU6XL%2BYiOv%2FCIq%2Fsjymb%2B0y0o4%2F0kBxw9zERREHucRQbQHWHg5MYYTwXnVWpzF2I6dR2J3CFUYYdnplLDbjtk2bClEAqOxAvfY90aSms1czpZ95kZi4pFnDcCvTZF%2B4e%2BWsOyNw8OWUtFzH4V8%2BaoMCIxHiiimk%2BwDjUut6blnFuErDIRvcgG4sb2jnGsSE9R556mVKTmJSblllt6XmGlNOtLHNK0KAKT5iIDKGc280lLTbM3FjSwoFtaa3NdRYNwTde4BHKO2ce0zGvFvgKh8SPDpWJ1vMGk0JGFswsL0yo%2BLT7gQNnEJCgHmlDUoJPlJIKTqSRHzxQ5F%2FwljzFmX9cYxPgvEtToVVlwUNzlOmlMOhJIJQSNlpNh1VAjzQHSGX2UnG3jGWcyhoUnmJSMPTi%2Bjn2Ks%2B9LUuWbUTqW4XTqKRz0JNjGTcVebFMyvoeC%2BHXJjG9QTJ5cyJYqlWpU6uXE9UXLKcAU2oakJN%2B0i6vNGj8U8ZHEnjOjroGI85MSTUg6nS6yhxtnpB3KU2hKj8cafcnnHNlm8Bnfu55wjyM2cYj01qZP9OOpOCTOmsvyucMrmZmrNzCHMCTDVLl65WVKS6%2BoObMh1W6%2Byyd944dQ4DH0I4Z%2BG7IvOHh%2Bywmq7Q6e3jqpYump2TfeBPs3K0%2BYC5unuX6pQqW1EWsq6Lg84D5%2FVTSqYKkLKklKbKPb1RvFtNibxtzilwxhnBvEDj%2FDODqainUSn16bYkpRu%2FRy7QXshF7kJHdftMagUbHaAHaJSbxFR6sS80XgJkc4qRTRFSAqtG0e6U2Vcx4Guce9nqiAzmgpKqOsn7c%2FijzULScy8J3%2FAGdkP9OiPVh9QNBWe0rP4o8NHJTmNhRY%2FZ2Q%2FwBOiAxuq7ZgVe9%2F7cTfPn%2BiVxf8JAKzdpI76zJj%2FOIjwVinSrOOa0%2FPzKmwmqzl9CdZuJhfZePVl9MNT2a1CmJfUW3K1J6dSbG3SoHKA%2FSNCEIBCEIBCEIBCEIBCEID8%2BnF0nRxAZkIT%2B2mo%2FH4w5Gj1foEW5lKifjMb14xE6OInMxKezFVRt6fGHI0U6LSLduZbN%2FujAZhhr%2B1V%2F3v5Y9brTTyFNPNJWhXNKhcH0jtjyYa%2Ftb0f7kKi4pBUbJBJJAAHMkmwAHaSdgID2V3EFdxO%2FITOI6vNVN6lSDVLkXJpzpFS0o1fo2UE7hCbmw88WyMukctcQ1DAGKcx0uykrTsI1SRpE9LTSlNzSpmaCihKUEbaQnrBVjvsIxqep1Qpk05I1KRmJSZaIDjL7ZQ4gkXF0ncbEc4DzNMTEy50EsgqUb7J3Meo0KsJ8qnuj0oivh55MtWWnXFaEhCgTGcpqlMJSVzaNR6wuodlr3gNcTdPm5QDxuWcZvyKkWv8cZPlnk7mFnDVJmkZeYdcqTkg2l2dfUtLTEohRslTriiAnUbgDmbGw2iOOqhL1Bpro30r648lV%2ByMp4Y8Q16nZ24FwtTq7PSVJr2KaealKS7xQ3NlsOdGHQPKAuoWO28BrnF2Fa1gXFVVwXiNhDNUosyqUm20LC0pcABIChsRYg3Eds5JH%2F9Ga3EJB00quqJ7L2djl%2FiVbUjiFzGLibL9sUzdPaOqiOocjf%2FAIN16%2Fg06vX%2FAHVg7vHzT4UP1fdp8FtH8lbrYR8pX%2FDPucjZcMqcyXrK7CzWIpFRPbdUmR%2BSPdIp1O6e9twf5tURyqpdZRlHXqg%2FVcPM0F6ZklKkZh9Sao%2FOBo9G7LISCktJBsvWRyNuQv51zCZVh95V7Blwbc90KH5Y%2BkWcZ0uVO1pvFoSlmlgJ0kyYWRfcEqPPzxjIeUFWvGa5o4FrOWeNqpgHEU5JTdQopZbefknC4wvWyh1BQpQBI0rT2De8YKrquRaEPWiZvsYLUFG948oVEdR74kekOgC20A6D3R5rmFzAexKx3xVDiYt%2BpXfEekV2mAuKZhzo9IF97x0IdLS3F3trQvfuBb3%2FABxpbLHB6sw8eUTA%2Fs1L0lNZmgwuemELWiXbCSpThSgFSrJSbAC5Jjbzk7LFkzGouMaHEpUlJTrTpKQrSd032NjuL2gNJV4IApxSpJCpFBsDuOsoWPn2iyl06iIzXNzLqo5T5g1bLur1KTqE5SEy%2BqblAoNPJdl23kEawFX0uAG45gxgp5wHrS92Xim9ZTyTFDURfeHSXse6A94WByIicObc4toWftonCyPhQFyDtoj01ot%2FSkdsA6b84C5iYjoAFaXG3kjfogef7jeNL5YYPOYuYFAwEKu3SxXp1EoqecbU4mWSblSylO6rAHYc43M7MtS6VrukoaaW1cDZWlJTqseV7Xt2XtAaMxMEJclCkpNpJpJ094vFh6cXteM3zay5m8qcfVPL%2BfqUtUHaciWX41KoUlpxL0u28CkLAULBwA37QYwK%2B94D1pe0nnFEL1PXine8B1dxAe1Lhiql098W%2FpVQ6ZcBcg%2BRyibxg98W5LpPMmJw4k%2FCMB70TKlLSm%2FNST6rx0E5qXiJOtVipa9%2B4Fk2%2BSNMZYYOTmJmBQ8Brqqaa3XJnxZycUyp7xdASVKWG07rICTZI5m0bafqbBqjs5crZQhbYV0ekqT0RbCtG9jbfTfntAaTxUWiuW6NaFfmNGrRyBuraLI24e%2BM8zyy2eyfzKreWz9al6qui%2BLJE4wyppDqXZdt5J0K3SQHbEd4Ma91kbQXe1LvYYpJI6a8Uel88Aontgo93SfuodJ%2B6jxeuH8KA9yXNvKiolw6djFvSdvKMTpUexUBdJN7W60nXzWj5VARuOcsibWO24P8kRrfKvBbWYePqNgt%2BtJpLVSLvSzpYL3QobbU6ohsEFZsggC43IjYU883MPOOyxWUEnoy4nSoptYEjsO24gnNkWOk24X5A2vqzJcN%2B61LG35Y6%2B4HlBXDnSrHk3VQfN%2BaDHN1KyfxnnBkfiGq0jHOHqZh%2FBVYbqKqC9JupmH3nGEtmZL4SQpRSFJCb2AHIbR0pwTBaOHamNuJAKG6qNuR%2FNZF%2Fkj5p8JFUdx2cf5lPsqdvCNtU%2BafbDgqbFqhMDumHx%2FnFR0DwOW92id539r85%2FObjn2b%2FthMf%2BIf%2FwBIqOguBz%2Flonf%2FAN35z%2Bc3Hb00n8gW%2FwDDuamH%2FpNPpXLPCVMzxX1Rgc3ssXgPvKo0PP8A6EeQna7RIPqMdBZy0rE1a4yJGRwxPYap7ysGNtzkziSYUzT0yXQul7UtHWSsgWSQDv2RoOqolXJ2aFL1eKFaugCiSQgnbc7nzHtEbOhs54Fdv4YYb5H4%2Br0sZzHShftlca20OyCEDuJYQSI1Qlelwxt3OLBtZpNKpGYrs%2Bwuj46mJsyDDT5LzZkC0w4H27WTcrBQQTcX5Rp1Z0uGPTtR7fGFWHmjzTLiXnRfsimZkpOkxTKwpWqAmUTrFuyPUlfVEePzxUQvbnAevXZOwg28QdwYoBza2q0QK7Hy4C7tzqlEAnsMbLoadWEaQ6BbXLvkecF0gERqBqbQklS7kIuqw7duUb9r2CJjLkSOB5muyNXmpCSQ4%2FMSSXAy25MJD%2FQAuAEqQHACQLXO17XgnNhmaCAsVKYWB0rdYQwsgbbSqD6%2ByNctzFo2hnPgGqYbpuHceu1OWmKRjvx%2BcpjDbyi%2Bx4o8Jd0PoICUqKxdOm90kdsamuO%2BCYnN7kzagCm20eNa%2FfSq0SF5INokURe8FVfpBECsGKF%2FPE19oCqhW8ehKwOceJKiDFTpPPAXVudWrYqMbWoTa%2Fa5TG1fqS%2BztKrxplMylkB1XIR0LV8GzOXhksGT9alqrPU%2BWbcnJmWCw0HXkId6JJWAVaA4ElVrEg2uN4DX2bCCJyamAk9SqutX7Cnxdo7esxr9Dlo2pnjgasYbZoWOJqoyUxRseNzlUpjDLylOyxYdEs8h5JA0q1IBFrggjfsGptQgK5dOkiPKXLKJgp8cook3MBOt5SuyJmiTziloSfhRMEW5LgPUFEDsiq28Wt9MeVJ28uIhzV1dUBc25y%2FKNsyqCijU0H9bG3o1qEaZlFqTMNhKdRWsICb8yTa0b7xPhR%2FAk8nBM5iKWrVRokqiXqExLNuJZbmlXcWwhSwC50YWlJWBYm4HK8BrzNJkNzjXUsUTc4i%2FeLoP5YwlDlhGy86MAVzCzdAxhOVKVm6RjmTmKvSQ26ouMNtTBl3G3UKHUXrRewuCCN41b0loJh6jMnSRaPLrN%2BUQLo74lPPyoIT6rdhiVSz3GIWv2xDR5zAQS6Qu8e5iasY8BSAqJ0KsqAv0nOLW4hOrtA%2BWNpygKafKBQIIQoEH9%2BY1DS23ZqflpNlQS5MPNst35a1KATfzXMburGGZ3Bc87g6qVOUqE%2FRVrlJuYk3CthToWSoIUQCq17E23IgMnwWEe5VnhqPWGCWikf5Ql4z3wbCB7IZgrK7WlKQNPfeaVv6rfLGLZXZeZiZp0nFWWuVcph12pYmoC2amKvUhLPGXZmm3dMqkmxV1ElRN7AnlGc%2BD%2Bo85h7GOZGHqpKhE3KNUptwhwKCVpmVgp22PPn5o8Xp1OWCW%2FniP5qXWwn9Jp%2FrkYZxiA%2FVEYrUrmfFAPR0O0YTlQP8AhRwZ%2FwDvDIf6ZMZrxhf%2FABD4qv8Aayn%2BhjC8p21O5qYKQjma%2FIn4nkxs0z%2F61Tn5H%2FgwU%2Fpf%2B6Pa6f8ACGD%2Bw%2FBB%2B1xux%2FoY5uzfa6LNzGaO6uTR%2BNUdM%2BECkqjUcF4SkKQ0wudexww3Ll0dVLvQEoub7Jv5XmEc%2BZ30iapeYc8xXKlhudxCffKy7hycXM05c0o6joUsakrAIC0bgECx325nwbTngVP8VS%2BJx%2FaamBYqWFYBkkLdVoQ5VDpPIKIYtb0xpdt%2BN3YgwbV8WZYVmvUaZlUMZfNqqlWZecKHX2JuZZYb6AAELKVDUsG1gRa8aNdIaPKPfOdk9KJogmKJcuu5MeZUykGwIiHSX5EwQ9hf2tFMrvHnv54jqMB6kOWHOJ0zCgdlx49ZiBXY3gLmH9oz7LcKXRa%2B6FJAS5KoIPb1zGr%2FABgxu7BmEZWg5YyONTiRiYmcWTEzKilJlnAuWblHgOmU6eorWSRpG42vAW7HDF8Lyy9SbFM4qx57OND%2FAH9Eaw6SNzYnwG7inKit5hSdUlmBl89LonpR5K9c01UJoNoU0QNN0KSNQURsra9jGkFuW5wHqE44OqTsImYJSiPB4wiIF1R8lxQ9EBc%2BlibpQYtQcN%2FLVE3Sn7dUBci7blaHjJA7ItvTfujEqnyPPAXEzar842FlwA5T6me5TA%2BImNXNOlagPPG6sGYYlMPZeUnFq60qYnMXF9YkRKrSJNmVfLYUp09VanFEkJHIJ3gPNmihKMJ0kXF0pfCfOfGN41QHiO2N34%2BwOjFOUczmVKVdplzA03K0udp7jCgqYbn33FNPNuDYlKmyCk22ta8aJ5bwTmqPPqUg7xWYmAGgCY8pWkgiKPSEEAQQufjKe%2BHjCItvSGHSGAunTAi4IikuZWDYGPB0p74j0o7TAezxqNmZdBCsKVJ1RTqE5Lpt27hX4o1OlYKgO8xvCgYPksJ5fUCutVt2cncay3so%2FK%2BJ9G1JNNPuspSl0n3xZKbkWASO%2BAs%2BaSEJw3SApSUnxMKACt1fmpfMfljWHSKjdOYOBJet5RO5sNVhCHsOVSSws9TXGDdxMyH5hMwh0HaxRpKSPPfsjSGvzwHoL6gm14p9OQecUCs6rQJ9PxwHrQ8TziqHCe744t1%2FTEbjvV8cB7Fum%2FK8Q8YIHMiPGT%2B6V8cS67dpMB7kzij2xtTLoJXR3HkKSrpCi9uw7gg%2FJGn0OWJMdCUnBNNwNhihOylamqhM4pocjXpkOyyWUS3SlxKWUWUSsJ0C6ja9%2BUBsjh6CTnng4%2FDTNTKk91xJvxgXAK443n5Sg2UkOUWpoWrTeyS2bkd3p88ZZlDSqriDHtFw7hvGbmEK7U6giWka43TfHlSwW04gpS32FRXbVvYX9Me7hey2msp%2BLuoYBdq8tPuUaj1WV8bZCm0vANAFSUqF7m3I8t44Ok05YXbT%2B7Psb%2BHZd0UR52W8foPul4NVfb2ooH%2FqFRzAR2iOnuPsE5m4RUBYDCLYt3Hp1XjmKMGhs%2FkO7%2Bif5pYr5rvFfplTVEEgxExMlIO0elaqER0HvMdBnIPBQ4XcF5yJnqp7PYgxTJUaZb6VHiwZdnlsL0i2oLCE3Bva%2FwAUZ9m9klwYZJY09o%2BYWNcfyc%2B5KioN%2BLIS8gSxeW2DqSm2q6Dtz5GA5ACILFov1RpMjUMaTFAwImanpKfrJkKCZoBD8wy49ply4BslRSpOru3jppXCRkczjmX4fapnXWWM2n6WKhdNPSaUl0oLgaHwldVKjp1ailJI32gORInsY3NgPKfK2jt4wqHEfmc3hBWDqi5SXMP03Q7VKg%2B2E63mkq3LN1p0EC6t%2BVov%2BanDDTML17LNeCcedNhjNNVqfOYhaRJPU0BpDxW%2FyBQWXNQJAOoFJFyDAc9RAjtEde07hIyMxvWcRZa5XZ21Kr48w3TUz7ilyra6W8V7ISFoJ6uohJ0qJSVC4NjGA4AyPy1lMlJTPrP%2FABVXaBQa3UPY2lU%2BjyyHponpFtl9ZNwUXadUAkeSi%2FaBAc%2FRTcT2iNu8SmRMzw%2F44l8ON1v2do1Yp6arRan0QaW8xq0rbdSLgOJJTuDZQWki24GoSQoXBgJIQhATwhCAjYd8LDviWx74WPfARhC474QA8oDlA8oDlAQVEE84iqIJ5wE0UnIqxTcgKNj3RBI7LRUA2iAAvAInREp5xMiAnQu3U16kxUQ4HSSVKChuFIWpCvugQY88TDqmA9C33ynovHJlTX2jky4tPxKJEUriIa%2FN1Yp3PSW7IDMMus0sf5UT9VqmX2I10l6uUxyj1IBlDiZiTWblHWB0KBNwpNiN4xFGhttKG%2FJbSEJT3AbRCEBPcwuYkuYXMB7XaxWH5YyUzXKo9Lq2Uy7PvLQoXvYpKiDuBzjxrXeIRJAThUVAoGKIG8VByhA6D4XbexeKlJvqSpnke5pZH441tgKqVuS4sJ6Wo9cRS5ddSm36g85KCaSZZplanU9ESNRIFhuLEg3jZXCuUGl4qKuanGr%2FAHtVo1DhyqyVD4pKg7VFvNszk5Uab0jbRc0OPMltBUBvp1qSCewEnsjzVznPF7f7Pc%2BwaQfg6DXD%2BKPZWzJlspfR1NItcJJvYHcCLXxPsdNlplRPJWrSBXpcp7LomGlX%2FlRe2wrpR0idKgLEdxG0WniYV0WVOVUsE%2BUrELxPmMwyB8dvkj0r49DmbpREOkEea5hcwSrKcimpZPbEhV3xLzgKnS27Ym6UmPOpVjC574Cqpy%2FbFWUR07b%2FAEjmlKU%2Fa3jxEk849UrqLTxTyKDeA6wxnKqkJjDNNWrUqVwrR06uV7ywVf5YxviJk1sZcZR1HpLtPyFeQnzqRPJ1fzx8UZdmOwr2x0l4m4OG6OB5h4m3%2BW8WDiWaSzlHkw0m%2BoUzELir8rGooAt6xAc4pfA7YldfBjyFRG0SlR74Csp%2BJC6YpkiJS4BAehLpEFOXjzFwDsgHQRAVVuXidhqYmJZ51CkgNoOoFXZHlKyYuchtKP8A7pJT8kEw6pzDR0WI6ZLK%2BysYcozbu3whKI%2FJaIPYhVhbKPGVWYo5qjj0oinPpEwG%2FE2ZlYR4woHdaQpCU2HIuAnaPdm4gIzCmUJ5Jp9NA%2FBGosFeek5TJTMBx6YaacmJORl0BawlS1GbQdKAdybC5A7BfsgiG9%2BAQg5WzZF%2Bq7Pk2%2FvJMcSVYpU0pTYsklZT5xrVHbfAWkIygnXVEi66gbjmCGTHEdQ%2BwncHde47euY3pjLDrP8AilyrCfyjbeiGGKVBKoKTBKY0XVTBOqIhsje0ZLh3B1YxI4pmlSbswpATqDTZWQVbJACQSSTsAASTyjpTJzgkncZUWZm8xKzM4TqU8lHtbp82yEJmlgkq8bv12EK8lBte9yRtYhyUgXO28VgxrHnjpWawmnLqfqWCp7BtLkZiQeXLzLE5IoemUdwLqrk7EEKHMEER0jlJw0ZH5y4HZreIsGMys7NulCpqlumWU2UNBtIAF0lOwWRbdRvAfNQsWNrGJVN27I7P4h%2FB742ylo0xmDg6cXinB7G8zMBnRO09Nrlcw0m6ejvt0iTbvA5xyVVqS5KOKS4nT2wGPLBESR6HUARQsICEIQgEIRBXKAXHfHpk5d6cm2ZSWKQ6%2BsNN6lWGo7AX852jxXMVUHvMB76nTpylzJl5xlTaxcEKFrEbEekG4ieiU56r1aWp8tJPzjjqtpaX%2ByvWFylPebAxkuF3JPG8zK4Wrk7Ly06%2BoMys7NPdG26bdVDjh2Qu%2BwWdjyUeRjE20TUnNhTK3mJiXeISpKihba0HncHYg90Be6q7SazRV1Wk4Nco7ci%2B3LuzTTq3mHFKCilDhV5DpCSRbYhKttox6LlW6lWJ5emqvO63SH13ASHSdwtQFgo87Ei%2B574tUBfsKJvPrP7iMwDZTtFy4X8pXc5MxV4VNXRTJZmRdnJqYKdS%2BjQUjShPaolQtHYkzwO5YSyrPY5xChXPdxhJ9NiIDiuIgG4jtWncEGUUysXx3iPRfclyX3PpEXxvgSydUlKVY%2Fr6iTt75Lgj4hvAcLN3DfriKRzNu2O%2BpTgFydmB0ace4mUpXkhJYOg9%2FLeLovwfeSr5unGmLEiwulHQEX7bC0Bw3lK0mZzcwGy%2FqLa8U0kK02vbxpHfHsznV43nLmDO3v0mKaqb25%2FmpwR3DQ%2BA7KPDOIaPiemY4xcJyiVKWqculxMupta2XQ4lCwEg6SRY2N7RJX%2BBHKCv1%2BsYifxzixt6sVGYqS2tLKkMrecU4tCdt0hSja%2B9oD53obXaJVN2v3x36fB75RabpzFxcFA6r9DL209oItyiQeD6yiAVfMTFaSfJIaYNvjG8BwEltSz1TFQAtjc%2FLHfqPB85U2%2F5RsUuemXl03i3zfg%2BMsVq0S%2BZWKWTfcFiWXtAcIE37YlU4Ux3mPB85WLTpTmRinVbmJaXMcsZ%2FwCRVcyIxXL0Oo1Buq02py5m6TVGmy2JlsK0rbcbN%2BjdQq1xcghQINjAapmHS4y5q7B2R11hKcWjDNF6tkpkJdFz%2Fex%2BWOQX%2FsS%2FQY6xws637AUfX%2BspfqlVyD0YG3mjJYx%2BMifNPuYrx8l9se9tnC1UTKT0o64pOggpWm2yr%2BeN%2FwCU2MnHCvCVSWkqlQTT3Rt00v8ABSe9Sb29QjlaVn3WwwttHkJ0qT3RluFsbs06dbM5MOMusrC5V9N%2Fe1DkFebsjbn8LW59nPBl2I5MRzxVeC7Kuu5jnF9SW8mgvP8Aj01Q2h73Ov8Aa24snUEKV1lG5Jtp5GNkYNzIp%2BIkGSfmJdudbSNQQ4Clzzp7fVGWmbShsOrNkcr9kKuFVTNnnqna2KK4oqi05Yaz4ipTBkngOuYmqeD6TP1yalkyErOPsXeZSeqlLahYoSlN7Aco4srWd%2BZ4y5qeUjtbYTSqs82uoTzUqlqoTcs2gJRKOuosFN2SAVaQpQuCTc37C4k6xSzlxNMCdl1vCZaAQVgqub8hzjgCqsVquVBVHwpS5iq1BXSLDTQJCEJF1qUR8FI5neOhRTRd7vTVMZTm1oibza1Z641MKxNMLEomQkUDp5shloJHI%2FNFeRpyZCRZpzW6GwSpR21LPlGLhT6Iin3nKi8JicIuCB72336RFRxbfSRzbXOqc29TVERwYWyo38QmNCPIbOrl1trfJGKNnqjqXjNpssKkZxve6W1G9ue0YUyglI3jFK8MFxIpn2yTy3GwoIKBYns0gxccbSDdPxC3Kod6QKk5Z3V%2B%2FbSq3qixYmUTiCpj%2FtLfEBGRZgL6TEMu7%2F3dJI%2B5ZAjBLLDN8kmsIIxjSTjLDSsR0oKV4zTEzhlC%2BChQFnkgqSUqsrlva214t2YErQ0VOafw%2FSXKfKPPKU3KPPiYLKCo2RrKQVWFhcjsjzZbOaMQU8%2Fu7fIYhjRw%2BMK%2Ffn8ZiBjKXLAIUxLJSBayWE3PrtHmmnGWykIabPf1BEXndI5xbpiYgLlL1GXC0Jmukbav1jLttlVv4Qj2rqGE0NoMqzXw8AdSy7LhJPZZIRt8cYx0ioh0kBkM3UaJNLCpiluzzoGlD04%2BSUJtYJCUaUxb3nG1qs0AlACQEjkLRb%2BkMV2XE2BPwdzAbW4e8naznbmdRMvaOpbJqTuucmgNpOSR1n3yeQskWH7pQjsrwgObtFwNhih8LmWwbkqbTJSXXV2mrWYlkJ%2FM0kbcyd3nPOU35xsvgNyPmcqckHM1WaVKVTGGPpAT0i2uYS20iSTcyrBcIsgLWNaz3AAjaOecX8A%2FFrjbEtTxXiWWwnO1Krzj09NPe2NsFbjirnmNgNgB3AQFk4bM7M3MQUKjcMOU2EsvkTU09O1NqfxBJqmzNTSQXtam1%2B9JdShOlCiD5I5GM58JLmrjBzEOHMmn2JuToFEkWZ9SlJSy3V5tbYSuYDSLBLaDcIBHNSiOwxSyh4KeLPJ7Mih5m4foGCJieoDrjzMtNYiQWnitpbZSrSAbde9vMIs%2BM%2BBDjEzAxJUMX4uThmpVeqPqmJqZexI0SpSjySLWSkCwSkbAACA2TwG5k4bzlyixLwkZoqTMMy9MeNKCzdb1HWq7jaCdy5KPFLqLbhB7hHCucuV%2BIMo8d1zL7FKAalRJtcu46gWRMt82phH7hxspWD5yOyOocCcD3GHljjWg5h4RpOFmazhydbn5VftiZsvTstlQ2uhxBW2odyjG4PCMZKoxvljTs%2BqfRPYyuYXZl5OuSqnAsqp75shGsbOKl31FKVdra9uUB8tHUkKimeceiZAC4oAb3gLxhvHOK8CT4rODsRVah1AILXjdNnXJV7QfKRqbIJSdrg7bCPTinH2K8xJ5Fcxjiis12oNMplzM1WdcmnggXISFrJOnc2HfeMXebUTcnaKsojynDpT8HT2mA9IVflBJOoxKAb90X3B%2BFatjTFFJwhQWG36nW5xmQk23F6EredUEpBUdki55mAtMSLuT6I3XTeE%2FOSq1CvUmVoMg3N4XxPL4Qq6Hqi0hMtUX1lDQ1XsppSk26QGwuI1NW6LPUCqTtEqzAZnadMOSsw2HErSlxtZQoBSbpULg2UDYwFrHOLlJ42rtJpVQw7T6tPs0qrBoVGRamlol5zolami62NlFCt0nmDyjwI%2BybiLe%2BwttxcBleJMb4lxzNiu4qxJU65OhpEt41UplUw%2FoQLJSVq3sBsIsZcudooSnvcur91E45wHsk917R2B4RgacYZYJ%2B1y3pA%2F0kcgSF9Yt3%2FljsDwj6wccZcJTyTl3R7eg9LAccL5wUbbwXziVwXTAZRgnOjMnKxycGXeOa9hxFQ0eOClTypfxgpvpKwLgkXNjz3MeDE2MMQ42qz2KMV1qdrNUnCFPTs650j71gEgrV8IgJA9AEYspsuO6CLR7m2i3KhPM3gK3SEmJr3iinsjNMrcq8aZx4rZwPl5RxU62%2FLvzLUsXktam2UFbnWWQLhI2BO52gMRiW5jbOGeGrN7GeFKbjTDOF0zlJq7NTek3TOMtqc9jxeaTpWoEKSLkA%2BVY2vGqX29BgJUvJa6yztGQ0jOrH1AlKRTKFi6tyMjh6fXVKOyzNFIp82u%2Bt5gAdRSrqvzB1EEbxjLiOkbUi0WzxdfeIDLcU4mrmMKvOYrxBVpiq1KquqmZucfILrzqvKUsiw1eqLDe6o9DbK2ZFvUrZKTceeKI5wESkkREJ2tE45RAnsgJeUTxJE8BUbFjePc1ciPI2No90snvgM2w%2FwD2kA71R56DpOY%2BEwRe9ckBbzl9EemhjTRT5lfNHjw6q%2BZOEx%2F37If6dMBbcd0qpUPGOIKVV5VcvNNVKbWUKNwpCnllKknkpJB2I2MRyjKVZlYYT31qSH%2BfTGwao%2FQMQzFTwfjNbctItz84KRWSCXqMtT6zpWRu5KKUesk7oJKk7XEYngLCtdwfnRhigYikFy8y3XZAJXsW3kl5BS42sXC0KBBCgSCCDAfo3hCEAhCEAhCEAhCEAhCEB%2Bf7jTTo4k80E92Jp%2F8A0640G8bSTQPNTZP8qN%2FcaybcSWaB%2B2xTUP8ATORoJ5OmnNX5hs29Sv8AXAZdhi4lBc%2FpQ%2FHG8%2BEWSpk%2FxFYVlajJSs3MJaqEzR2poAtLq7Uo4uSCknZXvoBA%2B2AjRuHNpMH%2FALNH5YvclOTtNnpaqUydfk56ReRMysywvQ6w6g3StChyUDygM4XmcBktmZgDH79UmMbYpxlTa7OTDzZ0pdlul8bU8s%2BS70irBNt%2ByMv4qZuq1ZzKzEmMG1N47rOX8hNYr6QaH3nwtaZd59O2l1bAQTte1o8r3FBWajOMYmxNlBl3iHGMrZbeI5%2BQUl5bwtpfeYQQ084LA3UOe8arxTirEuOsSVLGGMa1MVat1d4zE9OPm6nV2sAByShIACUiwAAAgLKoOKWQm5vEpZf7Wl%2FFF5wxYVxm58kE%2FJGf6gvmr5B6oDUxaUk3II9Ii%2F4HpmN6hiiROXElV5rEUisT0maS0pyZl1oOzo0g6bHtO0XfG6L02VWCnUh%2F4PPcRnXDhO54YiNayayYq0vQJXEym5nEWIW5cpmaXKJsNZmgQW02BCWxupSjbtIDVGKmcUS%2BIZ842aqaK888p6f9kgoTK3Vblbmrck98drZFgO8Ha0nZXsdX0%2BmwdjSHF%2FmRg3MPHdIouDp96tDBVLFCnsQvIAXVZhBGpZI8sJ0nrciVKttG8sjEKPB4AyNalU6vbep6%2FwCWPm3wm67hdo%2FzY%2FkrdbCYzrr%2FAIZci5d1%2Bjz%2BW%2FtR9kUprLb8tPMShSq7rLbKtZCraQRvsTfYwfYcm5Z%2BWZAK1trtflYJJPyAx6spqi9I5C4r8VUllc%2FXKVLPPJbT0hZDCl9FrI1BBVuQCL7XvaPKy4daiCRqbcGxI%2BAruj6PZ7HKnawviNxjhvH%2Bc2JsX4PqLlQo1QXJ%2BKTK2FsqdS3KMtqOhYCk9ZChuOy8anc8uMnxHKy8uZNUs2UJek2nSnVexN9h5oxlwdeJhCkVb84avPApF4hpESJ9Xphq9MSaRDSICpr80NfmilYwsYDPslcUUfBuaeGsUYhmnJam0%2BbK5l5touKbQptadQSNzYqHKNluyr0y2uTlk%2B%2BKQsNJOwPvZI9Vt456RdSgg8iQI6XIWxUHEsLspu6dXobIP5YDAOJDGmHcxc6sR4zwnU3qjSZ5unol5p6WVLqdLciy0s9GrdIC21AX5jftjVLhN7xkuIJdhkyqpcEB2VQtV1X61yPyCMad2O8BT1w1xLCAnDkTa4pQgK%2BoQCt4pX88Rue%2BAzjJ%2FFNEwfmlhjE%2BI3HkUynT4dmlst61pRpUCQntteNtvS79QPi0uQVzAVoJ5EaSq9vQL2jm1Bu4hJ7VAfLaOoUKZbmEp1dG22gpGncgdEoAene0BrXiNxzh3MjN%2BuYzwk%2FMO0meZp7Uut9ksrV0MkyyolB3A1tqt5rHtjVKzYxf69KNyjkuhlvQlcq04E3va4O1%2FVGPuc4CGvzw1%2BeJdJhpMBOHO8xHXFPSYWMBW1jvh0nnilDlAbAyOxfQ8C5t4Wxdid99ml0ydLk06w2XFtoU2pGoJG5sVA2EbHl5Kanp005ACnXA6StA6pAQpZUP4IvaOfWOu%2B0PtnE%2FjEdMuMMe2J9HR%2B9dI4hSf3JaIgNfcTePMO5oZ2Yox7hF2Zdo1UclUybkywWXHEMybLJWUEkpuptRtfkRGpHNoyTEEozKNSYaB98lEKNzffcfkEYwvnBdEKiYLikBaJgIKKmuGuJdJhpMBV1%2BaAcIilYwsYDPMmMZUXA2ZtGxPiMzIpkoJluZVLIC3EpdYcbCgDzsVgkd14zz7Br179EnSrTvtbsjSNLbbfn5Rp0XQ5MNIV6CsAxviZQgT00kDq9IoeoQG5cCZ6ZX5Q5MZiZdYnnapN4kxT4j4qzT6etbDDiUFZQt5RCSQlaCdN%2B6N%2FcFbvjHDnSX97Klqpa%2FP9Fq%2FLeOQMyVuI4XaEwD%2FwDMJxz1mnAerYD4o684JSpXDZSVKttK1FIt3eNq%2BePmnwkRHcVlOW20pjqqdvCdXD9HvhwK7%2BinP787%2FpFR0TwMp1Z0T%2Fmw%2FNfKtu0c7O%2Fopz%2B%2FO%2F6RUdFcC9xnROH4KqBMA%2BnWi0dzTP8AUNvH7se2Grh%2F6TT6Vxz4xFh3C%2FFqiexHWWKZLTeCpeTS88lRQh9xLiUA6QSBbtt2xomc%2FMTz6XVC7NypSTdJG5uD3WtHQ2b6TK8YExURLsOOSuWTs5KKdaS70T6GVaXEpUCAtKhdJI2IBjnJ196cemX5uYemXXlrW668rUt1aiSpSj2kkkn0xm0LiIwO7ZeLDBfZ%2FHVT55Vc%2Bq9QTlvlrgNifK8RYbdrz1ZktCwZITTzC5dKiQAVKQkqsm9u2OfHlHpFRtjMhpL81iKefKn5sVKXa6daipekMJuCe3%2FUI1I8TrVHqWqplzfeIdJEpBvEICoHInS5vFCJgbdsB6NdyRflEhWCCb8op67Em8S6jYjvgKqz1FD9zHT%2BZmLKFjDGMxibDc%2BJ2mz7Mstl%2FQpAPRyrSFpIULgpWkpPojl3stG66SwJXCdAQ2kJQ5Si5YfbqcJUfXAXziAxZhmrZdZWYKpdQcermEpCtorksphxBknJmodIy2SoBKiWxq6txvHPy1ERs3MptEw%2FVaw6FKm3qsWHHFKJuhLCCE%2Bok%2FHGrlkd8Ewa4a4pWhYwQr3ENXnincwue%2BAq6vPDV54pajDUYCo4Spopv2GOn8f4uw9jbF1UxhhucXM0upBgy7ym1NmzUu22oFKtxZSVD1Ry30kb1pTctK0OlSrDIQ2ZFKtN7jUoXUfWYC5cReK8P1HBmW2B5KfL1XwdTapLVpnoVoEq%2FMz5eba1KAC1dHYnTcC9r3jQBdvteNlZqtodfmqiVqXMO1J9t51ayoq0staQb90auuYCcqJMNXmilq80NXmgK4X54mC7R5tUTajAV%2BkEOkijc90LnugPXLvllxp0n7E6lw%2BgEGOkszcQ0TFuYNexThqppn6RWpoTkjMJSUlbRQlJ1JUAQoLSsEEcxHMXSRvoykpIsU6WkWAyymWuEA3AJcJPy7wFfiCxfhms4PyywtS59UxV8IYen6bXGOjWkSk05UnHUN6lABatBBOm4F7XjQnSeiNhZvMspqr9QZv0s1UJrpVkkldiixPoBtGuIJhPrERDlop%2BuHrghWDsTBwR54mF4CqpdzeJNagb3MSk2iUmAu1CqDEhWqdPTbhSzLzrDzirE2QlxJJsOewMdF5g1WlYgxzX8Q0GpMVCmVaovzsnNMk6XWluKINjuk94O4jmenBC6jKIcRqQuYbSoX5grFxG%2BW5ViSl2WJVoNMpC%2BjQDska1bCA31wl4%2By9ynx7MY6zNxvSsPU12g1GRlzMLUqYdcWEoBbbSCSLgi%2B3IiL5wOVGUr%2BZOa1apV3pF5VK6J09XZU06oGx7wI07SJKQqGRWcjs9S5Wacp%2BHpFySddYStyTX7JMkqaUd0E3IJB3BIN42B4NZDnstjtWk9GWqQm%2FZq6Z3aPF6fU54HbTy%2Fg%2Fz0uvhH6RH9cjEuLsn6oXF6TvZ2WN73%2FSE7RiGUes5tYHKdW%2BIZAbf30RlfFt%2F8RGMd%2F0yV2%2FwAjG8lxqzcwQi1wrEEkD9389o2NmjNOfkf%2BDBT%2Bl%2F7o9rqnjtrknQ8OYInKgro5VOPGpl52x6jTUuoqO2%2FJXZ3RytmFNSNTxhVq5SKmxUadVZx2alJthRKXEXsR1gCCCLEER0v4QxH9hOBmJhAKZvGsuqxOy0dBZQI8940Jn1UX6lnFilTgDbMtUHZaXlkIS21LtpVshtCAEpFyTYDmSY5vwcU8DA6ZnbwqvatidczeKoWSWxBQcNZOZpSFdnxJzeM6NJ0ygsqbWoz0xL1Fh19KSkEJ0N73UQDyjmqed1r2jdGOmG38Fy3jAVrk1zTzHXICSotBW3LcRpBy%2FbHvmgkiKTaKcIKKwcibXFEAxEAmAqlyJS5EhFolPOAqa79sdAYUxJh%2BtZO4Xw7Izuus4YcqYqMsppSClExMpW04lRGlYIBBANxYRz1G2MsGm0YSqM2lkdK7OtNLcN76QRYei5MBsWexLh7DuQuYGEapNONVfHDtJRRGG2FKS%2BiTni5NKWsDSgJBTa562rblHNkw4T5O0bizAaS5hKmvuJKlSzc%2BWzq8i7zQO3n%2FJGl1qJgIA9sVErtFCI3MBX6QbQ6QbxQuYiDuYCr0hiVTnbEsSkQFZt0ggiN64dxZR67ldhXDck%2B97I4WZnmJ5txrSi0xOKdZKFfC6pNx2GNBg2jbmWMs17UZmbS0kOKmEBxdt1ALIFz3C3ywGe4ixVRMP5D4twhUXJr2UxnPUp%2BkoQxdssU994zLi3Ser1lhKUi5JHZtHObj%2Bk2Bv642rmew0cNUyaLYLjbT4C7%2BUC%2FbcdnKNQQFXpzDpjFKIX8xgK3SCHSCKUICdS4gHCBEsSq5wFZDqgoHzxvqj4ro%2BKst8I06nrmUT2E5F2mVBp1uyCXJl11tbarm40qAINiD3845%2Bjc2XjTScBJU2yhC3JhJcWB1lm7lrn1QGXY7xnRqFkFUctX5acVWsWV%2Bm4jlHUNgy6JGUbmWXNa731l1dgkDsuTyjnRbsbZzRZZcw5Ivqa99lJbogf3Kn1Ej1neNQQFQOkdph0x74pwgJ%2BlXDpVxJdULqgJy4qJS4q3OJOtEpCu2ArocjoSl4wpeNKDh009E2y9h%2BgSNBnGX2wAtxkuHpm1JJughSedlXHLkY51vaN54BQw3hqU6BtCSqWaU4UpsVKJVcnv2tAbWyexJS8A46o2YlclqzOSOHqmw8uUpMn41NPqAWsJSgqTpTZtRKybC1u2Mg4esw6Pmjxp1DGWHZKaYp1SpVYfZanFJLqEqRffTtffsjycNrz7GdmHHpV1TTl5tClpWU2SqUeSbkdm8YT4PNNs9h1b6cM1Xf7XqJ3jzmlk5YPbz%2B7V7G9cMovNFXgltzj8GnNLCqf%2FwBk2h8TyuXxxzGeUdNcfS9WbmHG9%2BphFj5XlRzKuKaHfqO7fw%2B%2BVL7qt6%2FSp3uYrNbuRQsRE6FlLgj0zUdnNtPv8AWVRQlSgvMGkgrCdik1d4fjt8Ubl4iqvxAyGaYZyq4ecNY6paZcOqn6tR0zDrM6p9wFkKJHVCQkhPYSY%2BdjGJ8YT9LksGs12szFNbmW1SFKZmHFNImNZWgtNDYL1kqBAve5EZ9iCtcTeDJFNaxVWsyaLJuOBpM3PTEy22XDyGtWwUew3veAwcpxDhTHTK0NsUjEtGr4WlucAQ1I1JuauG3QdktpcOg3Ngnt2j6IYZl5jEvEXS8TY54X6%2FhXHZoKxUsTPVRiZo0pJpQoa2XWiULdJUW0k2UGzv3x85pWmV7GVZckpSSqFdqtUU464022qZmJpR3WpQ3KyeZO%2FnjPaKviQxBTqllbQZ7HlRlKGgS1RoLT7yvE2%2FJDbqCdQTyTpJ80BsZig5pYqx1j%2Fiyydwhh3G0hIYnqsu3SJxpM888hQSylZkgNSurpcQb3sbgG0Zjxc4AxHmFP5LNCmuSWY%2BP2vYebwvMTZXIyjgZQ6XENnZkIcJQuw6wT3pjnxFBz3yVmHcUtUbGWB1OISw7PNNuyzS0jyUrI6h82r1RaZCvZk41xrKVaUq%2BIq7jBbuuTmWn3HZ0KSk3U2U7psCb6bDvgOz5zKjHfDvlA9l7w6Zd1XFuN8VS626%2FiuXl0oblEaCFdCFEEWSVhpsct1q3sI1djfDlazk8H5lLIZX0ecr87h%2BeTRZ6VkW9b0tMaZmXPSo5psVtqJPILvyN41Czj%2FiPmsRKwfIY0zAerodLKqUzMvGaQ4BYpKPKTsRf0x6Rg%2FicyBkprEkvRsa4Dp8%2BlCZ2bllKbl3L7J6a2pIVvbUoA7gX7IDaPhCKrLM4jy6wChxt2oYfwx0lR0qCiytfRNoQbcr9CtVu6xjke1oulWqdSq1SmqlV56YnZ6ccL0zMzDpcdeWfhKUdzFvUkQFCETWHdCwgIwhCAlKjEuoxPpEQ0wEIRNsO2IwCER0%2BeGnzwEpIEQBtExES6TACbxAi8IiBeAp22tENO0Vbb2hbe0BTtDlExTvzhp88BCETWHdCw7oCA5GJRzMTDkYlHOAjCJrCFhASwhCAimIRMjkYWEBLE0LCJgLQgdA8K6QaPid3kTMNI%2BJs%2FPFvyKnZiXzrx%2FOyJSJluYnwF2BIHRrGxO4i68LTixQMRBVtAmUhN%2BWotG%2F5IxvIyo0lvOLMCUfqcszOzK6mZRhxwJVNKSlZ0N38pR3sOZjzFzj8rW8%2Bj3PsuPzloTcI%2FrZVveaV8hH72Mc4p3HBhHKixIQaNVFAemeIJ%2BMfJGQyod03WLXSDbuJ5xcuJLK%2BuYkyGyvzQw2hVUkKYuqYZrLEugrXT5ozBeZUsDcJcQVb8gQPthHp3xmHHUQMZB7RMWqF2sOVFY70SqyPxQGBMZLWkDC1UHVN7ybm%2FyQSxsje8QjJRl7jIocUcNVMaQo%2FoRfzRfsV4InZldJXQcP1G6ZFCJxPia7JdA33A7bmA14ReEbAouAak3Tay1VsNVRMw7LBVPUZNwguA7iwF7mLD7QMYWv7Wqp%2BCLv8AigMbA80V23FobXo6vVMXk4Ixajnhiq%2FgjnzRdsLZV44xfXJLC9Hw5PLqVWmmZGTZWwpHSvOuBCRcgAC6rknYCA6MxiD4%2FQgo3V7WKKVnvV4mi%2F4hGGcUMw6xQMqKYmZDrCcLTcwmxuEl2oPFQ9N0CNoZz4WmMDZkzWBpuclpuZwzTafR5l6Wc1srfZlWwsoPO1zyO4NxGHcUuXeI3MuMm80ZeW8ZoVTw3MUNT0ugqErPS068tbLttkqUhYUm%2FlaV%2FamA5Zha4Me72EqxWS3S5xSRuSGVEWiApc%2FqIEk%2BAdhdtQsYC3G94li5t0uZ97DzDoT0idZ0Hyb7%2FJF7xlh2nSNfDOG1uTFPdYQ6FgE6Fm90k94%2FLAYirlEtrRlUnh6SewpVpyZ1pqku%2B14uwpJClN3Gqw9ZPqixGnzKPsjCh6oDxWPOPWzOvyzCm2wjS53pubxAyzgP2NXxRdsMYUreMK9T8LYepz89VarMtSUjKso1OPzDiwlCEjzk%2FEDBMOpszSVY3eUvyzTqdq9PijUW2ao9MreWOMmatIsTCJKSYnJdaxZcvMB0JS4hQ5bKUCORBjJM8KNOYdzZr9AqLaUTVLWxIvpSoEBxqXbQoAjYgEHeLElxTeW%2BNUi9lyUsD9%2FEEQ3XwPFDWSc8oJ1pUaiu17agGj80cPzitcuF%2FbBR%2BUx2%2FwADHvmR05%2B5bqnxlpVjHD031ZJPmQfxmN6qfydZemXKu0Z4hb%2FYxBw2UQPPE8vcuJOjX%2B574pObuGPVTf0Y0j90I0Z1Oo%2Bm3g3WKW3Xqil6UkZ3DuEpZmcanXKelp%2BarLxPRrUpQ1EMtl1KDe1l3IuARsjiAxMH80l4UVMMTL9QYeqdHmVHS90iR0kxJFXJYHWdaVzHXT3Ro7gwfrFGypm6vTQSKjWXGHCpVwA02kW8w3iy5z1TG1SzcoLeHGp53FEjUZaZo6GWulW06hwK1FNtOgEde%2BxSVXsIJU8dYny2zuxKzP03EKKBiRqm%2BIms1NH5y1lTarJl5tQuWjp%2BxvjYK2V1TcZ5lNnKxkjQTQMcy2HJtUogJl04arCJqYXqc8p9lF2%2Bon4YWlShbYxozG1YRU6%2FVFyVBpdGlajUJicVIU9oJlQtbhK%2BjG4CCrUU22sRba0eKls0KYxBS6fWZWoNUajS7lSqxoqW252altJ95aKgUDSpIUSocgodsB9hsosa4Zx1hByYlHpacpz6QjSpOpLza07hSVCxSQbW3B3j5BcemStLyUzyq%2BHKLKdBQ6jLorNITawTLPKVqaHmacC0J%2FchPdHV%2FCjnZUabgOkZeuopzb9OqLjUtOs6g%2FOSpbLiuqOqpKSpN1eoRpbwo1QTVcW5f1BVvGF0SebUssKSpaEzQtqWSQ4BqNgLabkHnAcETTdo8auceuZcBjyKgJNJhpMRhAQI29ESHnFUjlEhAgJIXtCEBPF3YnGJShKdX0a5p99xCN7rttcnbqj8ceOnU5yoOOfmhplhhJdfec2S2i9r%2BcnsA3MeiWw%2B%2FPUKYr0k8283Jr0zUuFWeZQbaHSntQSbFQ5HY2uLhblKLp6Um6u1Rh1Qi%2FPzRKQEDa6knkIIUUqset3CA6h8H1PU%2Bm521maqCgEownOqbB7XA43Yfj%2BKKM0qi4xczFzUzMxXixxmkYgcpzEtTZpRUUqc0MNoTqSlI6qrqOwAAsSYxbhEfLGZs%2B5%2F3O6n43EW%2BWLohOvJvNRggan8XU9YCttzPP8A0TAW1NSyMQpwjFOarYUoFssBKVAHmF3dNyOwiPU1WchUuJ14zzaCAnrXKblQB2Fndgdt%2ByNUmVdU10zSRYzokU9a13b8opLkZxDbzqykBidFPXvyePZ6PPAb2wpJZLYwreHsNYezXzIlK5XJlqRbYmW3ujMy5ZKG9aHe1ZABjxTk3k3TqhNSExnjmKw6w8thxpclOBTbiFaVJ2d5hQIse6NS0aoYhwXX5bFtDnEyFXwrU5WalpjSlZl5xDgU0oJUCFWUAbEER5ayiov1Gr1GrzSHJpqZMxPuafKdeUVE2HeVE7d8BvBiqZDLl0maz4zNDwulQErO6TY7KHvnIjs7DEzdRyFU24hzP3MpCvgnxKeKVb9o6TbaNFTcnOSS5tD60JVJtIeXuTdKu0d8SOtTjDr7DxSlUux4wsE%2FAPaIDdk5W8jOj%2FOvOXM3UooSETKJkayRYp6rn2x2v2RUxhJ5b4KxTUMKV3OPMBqp0WZXKTzHQTK0B1HYlYe8%2FdGiil3X0QUUqMv42Ck8kg3BB7wRHurtfr%2BNsQTWJsT1V6pVmtlU%2FNzj1tcws2BWqwAvsOQ7IDbaMYZCoSjXmTmy8rfUEqW2PNYl4xGoYoyTnTKewuaGYdNSlvTN%2ByaZmZKl3NlNll4WFrXBBNxsY0fN0qbk2HJ5ZQUDrW1dkTNsL74Drjhzq8sxmHJVXAmcOIqmilzEq1VZOeYmW2n5OYX0RUA84oagsoAFgbXIPMRtPwhswy5SsuHGnQVPCoqdCTfrAtg37jyjnjhAR%2FZpVVgAq6OkDfu8fTeNtcdSnBUMHILhKCioK0k7A9IiA5Tf%2BxL9BjrClM9DQqQ2ppKVok5YEjuKAR8kcouqSGlXHYY6to2sUKnTS3Eq%2FMkv8HknQm%2Fr5Rlsfz%2Fs98KW0Z2eX9crL0rTKtodZGt%2FR121cimFPptTxRXJWiYclelqE0SQNVm5dAHWccVyCEjck8rRUuwFpff09VkW53HafQCI9uH6gvDWXVSqNPmSzVcaPuU59AHWRSUBKjZXKzjmlJtY2BjZqmdlO2WhERGuUMTYjo1IQcNYCdW%2FLMKQZivLTZ%2BemUE6nGe1tkHZIO6gLnY2izYizyzTlsKzWHfZ0u0xV3iytsW6QDywRuD6DbzR4mA004EoNy2m4uLxZMXKb9iJ2clwAVNlOnV2kDcRkpr%2BLj8BTgRaT%2BMjNZ6%2FWfZKSlHpxBJmJNpaytSlFLh3URcmMNnPHaa%2BxUqDUH6fNML1sPyjhQtsjuIjZuaFA8XZw%2B9T0t6jh2RdUlItclKib%2BfzxrEvuaFtOIitVdVcRNU5y2dVMzFMZQv1WqrGYtCm68pDMtiujthVYlmmwhupS5%2FuxCU2CXUkgOgdUghYsbxg%2FwBkHSR7qRWHMLYqpuJWWUvBh0MzLKh1XpZwFLiCO26FEem3dFSoyMrTatO02WFpeVeU2zc3u3zTv6CIpnmvTEU7Fkn0hMvMqTz6Bd97dkYnLI6ojM6w2humzLn2zakxikkgKSm4itca2ajXDVmJf%2BMdSH%2Fbn8UXTEz5eqTRUvcSrA0%2FwOcW3Eab4mqo7n1R6cQkCsN6eXi7NvRpEas7V2ZZbJC8T01CiAlTyQbmw598VMwktoqTyW7W6VfI7c48uAlFNakFJNiHRY3j0Y%2FJVPFR5lxRPxxAwmZO0W1zyouMxyi3OeVASHaJCbRMTFJRMBVSbxVaUAY86OUTpNjAbfwTxOZ85fYcl8I4MzbxLSKNKFRlpKXmx0TGo3UEBSSUpuSdINrk2G8X0cZHE9qv7u%2BL7%2F8Aim%2F6uNFAm3OKiHSnZW4gN7jjJ4oP%2BvfF34S3%2FVxP9WXxRAaU57YsAvfeYaP%2FALcaJD6B2mIl9J7YDfH1a3FOk6hnrib0a2P6qMax5xPZ9ZmUT2tY7zTrdZpPSB5Um%2B4hLa1jySoISNVjuL8o1UXvN8sUi4rvgD5ubxTAvESdV7xBPMQG4eFfI2jZ%2FZv0rL7EGL5CgSU0sF0vzSWZmaSduilAoEOP9uj7UKPZGMZt5dJysx3VsFoxFR8QNyDyktVOkzaZiXmE6iBunyXBay0HyVAxmfCLlzTc2eITBuX1Xq1UpcpVJ0qVO0qY6CcYU22paVsu2PRrBSOsB3xhmZOF2cM44xJh6TmXppil1qekm3nQOkdS0%2B42Frt8IgAnvNzAYchuNh5JYjpWB81sHY1ryH1Uyg16RqM6JdGt0MNuguFCdtRCbm3baMNlaY87sAY7DynyqyiyLyVkOJHP%2FD4xPO4heU3gzChe6Nia0XvMzJPwL3IBuLdhgNlU7j4y%2BrGI8TP4zfK6YMxqViCgGToCWn5iiS7xUvxgoF3HQCLBd1bRwrmnWJDEeYGKMRUlJ8Qqlanp2VJa6O7Tr61o6nweqobdnKOp1celMq7vsZjjhkygqeFnCG10uXk0y82GuVm3yny7ctk%2BkRhnE7w%2F4Cw9hXDGfOQNRmZ%2FK7HWtqXlptRVM0OoJuVyTqjclPVWElW4KSkk7KIcsKSoG4SfijP8qMmqpm69UWKdjfBVAep3R60YjrTVPL%2BvVYs6%2FsgGk6rcri%2FMRhzshNNneXd%2BIxuzhDyKwrn7nPKZa43m6jJU%2BYps9PdNIpb6cKYb1JCekSU2JIvtuBAafx5hCdwFiifwfUahSp%2BYpzgQZulTiJuTfBSFBTTyOqoWNj2ggg7iMf5Rda7IpptWnae3p6OWfcaQUpCdQBtqsNhfnFtO0B66bvMI7ibfLHXXhHNsxMAtdjWXdFHyORyLSt5hsd6vyx114R%2F%2FAJUsGs%2Fa5f0UD7lyA49ULmIKFxFRQuYgYDffCvwvv8SCsTsLxtSKCxh%2BkTc20qYm2g%2BJpCEqbU4yohfipJst4bJjTeLMNVDCeIKlheqLk1zdNfUw6uTmUTDDhHw23UEpWg8woHeN%2BcFeUSc3MQ47ZbxrW8LzNAwbPVFqbpKkhT6SkpXLPBWy2Vi%2BpB2Mc%2BOSTpQkobCU6QrSgWG4vsOweaA8KGRG%2FwDgyzNwnkznhT8fY6qL1PpEtS6jLF9qUVMWedYKWgUJBJGq3m740lL059wApYUtRWLJ%2B2J5CO4JHAuSPBll5h3EecuBpXHmauK5NNQk6FOuhNPpTB3QXQdirvuDvsBteAyHBfGhlRXcu8PN5jppdNxHJyOK5Go0%2Bj4dLUj0s41ok3A02FIusAalAnrXvaPn1VGUpmCRyISnfvCbE%2BjaO0ZLjCyYzBmm8PcQPDDgIYYmfeXKnhFJl6hS0qNg8kAJUvRcklKr2BOk8jqHir4dnciceN0ql1f2cwvXpFFZwzWAQTO09ZsNdtulbJCVEABQKFbXsA596PujbGVfDjjjN7DruIsK17BMs21MLlTK1XEktJTRWkA%2FYnCFAG%2FVJ2Ma1XJupNkpJEbtyE4eMPZy4EzYxLXqxMUyby%2Fw6KxIhiWbdE051%2Bo5q3CbpSLpIIuTvygNF1enzdIqczSZ5CETEk%2B5LvJQ4lxAWhRSrStJKVpuDZQNiLER47GPXOMBg6Or1fe%2Bry22280ULWEBShETzgmAmsYWPdEw5RGAqtx75cWIjwNc7RcGBygM1o%2F9ph%2B%2BP44tlIWpvH2HHUeU3VZZz7lYP5IudF3o4v8AbGLC270OKKc7v73MBe3PlAXt%2Bc6SpTjn20y8r7pwk%2FHeM4y9xTQGazhqj42dLVHpVVlZmn1AIK10vQ8lZbI5lg2O3NBJttcDVbcw50i1%2FbKKvlj3iaSRp1G3faA%2FRhRq1SsQ0uWrdDn2J6QnGkvMTDCwpDiDyIIj3R8eeCbjfqWRFWlcC48nHp%2FAU86GyvdblJUeTiRzU39skb23FyLH69UirUyvUyVrNFn2J2QnmUTEtMMLC23W1C6VJUNiCDzhnmPZCEIBCEIBCEIBCEID4H8c3iR4jsxvFW3UrGJ53pdZ2Kitdyn1gxzq9vT2b%2FaW%2BXeOgON91Z4mMyUlRKUYnngnzXcVcfHHPz5%2FMDSe5u%2FymAzHDoHsYe%2FQ1b4zFzT5Qjw4bSBS%2BktyQ0PxmN08NOTVNzozEVR8QOPt0CiyvslVgwrS5Mo1hLUslXwekXso%2FapV2wGn0vMnWQ6g2523ibo77iPpzjOfyRydws0qt4UoEhKzikyNNolOpLb07VHz1US8uzYrcUokAqJsL3JjlDiuySkMu28MY4o2G04bZxN0kvVKCiY6dFLqKUdKEIWNtKkXBA2C0m20BqfBmS2amYFIVibBWBqrVqeh9coqZlUjSl1NtSbkjkFC%2Fpi%2Fo4Z%2BItbnRjLHEIPeSkD49Vo3RlDXsRYT4IsRYiwxWJimVKWxWppiaYtrbC32ErtcEbjaMKPEFnSo3OZ1Xv5g39GAwlzhj4ikBTjuVlfWhCFOLKgkpSlIuSet3An1R5cquILMDJym1aj4LTRlydbmG5ubRPyXTFTiEFCbHUOrYnqm%2B5jqzhVzEzBx5XMaS2MMVztVap%2BHlTMsl%2FRZpZUoEjSkcxtvHBdhtt3%2FAI4DNsys2cRZsztKnsSUugyK6NLOSbCKPTUSTa0LWFkrSjZSrjY9gjrXIffg%2FwD3tNr2n4nbRwpy5R3fkMgHhFaHZ7F1wH06Hrx82%2BE79X3f%2FVj%2BWp18I%2BUq9EuO8uNQySxA2nyU4jphP4KoQl3AF23HVUOduaSPyxLlkou5HYlUOXtgpm%2F%2BLqinH0ajY5M7WCz2CMaVRiRcbwvNgMyqGSrUjrEX35%2BeLd7kOPX9TicPvJ%2FfKR9KNmdTzREdGDewi6Gr1ZQY7T5VHI%2FwqPniLWUmL1LAep6kJ7SFJP5Y2lqbt5CYk1J%2F3EBrJWUmKU85VY9Q%2BeINZVV12yEodLvakNbfHeNnak%2F7iGpH%2B4gNYvZTYoaOlUsoHuOn6UUU5W4oWbCVI85sPyxtUFMVbJX1NlQGqk5S4t8YaQmWRdS0glbiUhO%2FMkmNvqmG1VQqbdRoU8oFy907JIvftF48Tov54gG7iA11P4QxRUZeWW3SXSWmQhWpaU33J7%2FPFsOWOLnTqMiEA9hWk%2FljbqGtoj0cBqZjJ7GDx%2BwMAed9H0oqIybxevlLsja%2B77Y%2FGqNqBtAN7RFXKA1a5kzi5tGstSqhe3VmGyfi1QTk5ipQSeiZGrld1v542ffzD4hEynbJ5D4hAakdyrxQ2dPioJ8ykn5QbRKnK3FpXoMkAfOtPzxtvpImL6gLXgNUsZR4temGkJalkkuJF3H0ISN%2BZJOwEbjmAluYeQHUKCSpIWk3SqwsCPMbbemPC24SeuiKql7bCA1XUMHYtqCmVewTyFNNBohS0X2J8%2Fnjxe5ZixzcyjbXpdEbfSo3ic8oDT4yoxV%2BotffE%2FPEE5WYlLoa6JFz26xb8cbdKF84ouAwGsPckxJbfovvqfnin7leIwT72nb92n542hCA1d7luJL%2BSi3pF%2FxxFeVOIrXT0Sj3FaR%2BWNnFdolLt9rwGtJLKzEZmWQsyjILrYK3JhASm6hdRN9gOZjcXslJqxC7NlwKlhMODWOSwAUgjzHa3mMWNwExBAIRpgMLq%2BCMV1BqVb9j2VKZl0tEiZRzBJva%2Fn%2BSLT7lWKlWLkvLt%2Bl9J%2FEY2TohotBdroZTYl7DLn%2FDI%2FLEwyoxD8JLPqeR88bFt%2B5T8ULfuU%2FFBWWvvcorRbcSFNhZILay%2B3pA7QRe9%2B60TOZWz4EvoS7e1pgl1o3Ormjrfa9h7Yz%2FAPgp%2BKH8FPxQQwBeV84ZiYLQe8XUlYlgtaA4FfA172t32jxLy0ryEadKVL%2B2DibRs3X5oipVhcQGs5DL6vtT0qpSGkhLza7qcSAAFAm5vtG0ZxwGbmtG6ekPKKF9rxLrINhAZPmH%2FwDDBRf%2FAPIKv%2F5cY7A4JFlXDXStXwWagPV42qOQcw0W4XaGv7bMJX%2F8tMdg8FobRwz0UIvfxKfUr98Zxd4%2BZ%2FCTquVj%2FqU%2Byp2MKnXV6PfDgNz9Euf397%2FSKjovgY3zjnvNh%2BaP8tEc6PC02%2BPtX3f9IqOi%2BBX%2FAJZZ4f8AcEwP84iO7ptlOA22Xix7Ya%2BHz%2FaafSvWdJUniyqenmnKp8j7yoxzox8KOjc41LPF1PJUbj3LXUpHmLKvykmOcmO2M%2BhtPBwS7fwwxX6Px8ws%2BLKXWKjNV0S1OfmETM20%2BhxpN0KsykH1jt9EYCvLbGK3DejvI%2Ff2H5Y250ixEpcMeoauTU6MrsXLCiaepJSCogjsETnKjGKUhaqaoJPIkc42kXFd5%2F39cUiq57fjghrFOVmKlc5Ep9KYnOVeJAm%2FQp1d2kxsjVbv%2BOJStfwSfjgNbLytxKPIYSfVaKT2WOKG06vFAfQY2Stb1%2BZ%2BOKep3vPxwGtk5bYsJIMiAANV9Q5RtSYpi6JQ6NSZh9l%2BYlqW2pZYcS4LLClBNwbarEXTzB2MeZPSfbxLZKNhp%2B2%2BOAt2M6XP1MVGWprInA9U%2FG2nGVAoW2phAvc25KBBHeIwJeAcUfCpik%2BlQjaF78omQbGCYaxTl1iI82W0%2Bsn8QioMtMSfaNfdRssqVe4cIiBWu27ioGTXCMscSLOkJaB8%2B0ToysxKXEtLDKVL8ne942Elz%2FtFROl8BXlqgZNcO5YYja5hs7kesRS9zfEitPRNIVq5b2jZ%2FjCidlm3niJc2gZNWOZcYoZOl2WaSe7WD%2BKNpGXVTabISzzjbjjEkgHolar7cj3HblFNXXv5ooq2NoGS243olTq%2FjsnIS5mFmqOvNqaIKFNrZb6wV6QR6Qe6MHRl5ipZt4gEjvLgjZMToRcQMmuxlhiopuiWaUT2awIj7lWMCvR4gNX74RshG0VQ5blAya39yLGO4MkAR3qAHx3iHuVYmShJdQ0kk6SNV7GNk9O52LiYLUrcm5ghrT3LcSdgb%2BWKCstcTp5stj0rEbT6Vz7b5YpPqcUPKgNXoy1xIpxIUGEAkAqLnk%2BeNtzLYlUyiFuIeLcshd2lBXVKiQNuSrc08xcXi3emJ%2B7T%2B%2B6vb6YCwZi0aoVWffap7XjKUTsy6hxvdCm1qSpBB77bW7LRhntDxKvf2OWn07Rs8LPdFRHSKNypVvTBMNZDLnEvwpdKN7bq7YqDLXEausENlI5m52jZe94n68FmtRlliJSAUlkqPZc7RTOW2IU%2BUpselKo2dpP25iax%2B3V%2Fv64KNWry8riXNJLZ2%2B1VFJeAK8D1Uo%2BIxtjSftzE%2FwDDMBrCl5f11uqSL0z0aGEzLSnHLE6EhQJNu2wvG0%2Bv0DTaz1kpOrt2KyR6NrfHEoWoCwWbRJe0BnFGOjILOxwK0%2FnDTkHzg1KX2%2BSNl%2BDTebPt8lRMWcM1SXCzp5pCnRqv6TaNZ0waeHzOlz%2FuWnJ%2F%2FiTEbD8Gekpq%2BPXyleyaSgG3V%2BzOEi%2FfsI8Xp7%2BpLX%2Fb%2FNS6uET%2BPz%2FrlYZxagjiHxjdQILkqRb%2B8JjG8lf%2BV%2FA21%2F7IZH%2FSRkPFgdXEHjI%2FazEuj4mExYsj1aM4sCq%2F%2FaCT%2Fnxnmf8A1imf8n%2FgxWH4V8iP3o9rpfwgkw1LYOwGVtJWfbsyLqANkhkFVu4naOfc62ynOLGSVI0%2Fnw%2Ft5rxvnwiN%2FaXgDu9urf8A9um8aHzrN84MXn%2FvV38caPwefqSif3qvajE%2F0mpgGM2XZrDLcrJyzsw6vp2tDSSpQUS0UkgdhsRfzRqp3AOKVuKCaJN%2BtNo3Drhr80e7abTyMusXqPWpLqB3qt88elGWGJlC%2FiTpPmbv%2BWNsa%2FNENd4DVQyzxEb3lHxbn7wdvlib3L8QJ%2ByNvJ%2Fxcn8sbT37z8cUnFkG1z8cFGr1ZaVxPlIcH%2BCt%2BWKRy5r9r9Ht6N%2FxxtBRvEsBq85eVodiz6ERnWBqRO0LDdQkZ1JHjE4ypsFQCttyQkG9trXi7QCLHUkJB79oDyYyYmanh2VlZNCnnF%2BMy620DrNqKm1pWruSoagD3pMa3VgLEANjJqA7yR88bW8tzpF9b7aJNHngNYoy2xAu56NPxw9zHEyj70ylX8ID8sbO0eeGi0BrI5Y4oSjUZdHoCkk%2FjiojLKvqFi2lKu4lP47xsuEBrJzLWvI5Fs%2BkgfliX3N8Qfqbf3YjZ5So8jEujzwGs28tq4r7JZPoWg%2FljO8G0uYoeHnqfOOtBxTos3qGoi5VrHZbs9MXMN23ETnVa20BbMaSExXaDT6dSAH3kpfS8i%2Bkte%2FpUgkq2UFJ1WtysQeyNenL3ERXpWwlJ860n8sbOWN94BAgNajLevfatfdj54qjLatrFg43cd6h88bHhAa39zKufqjP3Y%2BeJhljWTzmWR5tQ%2BeNkDlCA1uvLGsD%2B6Wvuh88UlZaVn9WaP8ADEbKWDeIWMBrQZZ1s8i199QI2FhanO0PCgpU2814yZpI6IL1HSlKiXbjbSSvSN73B7I9aEbXgdoDyYypUxiKiyMpTX0OOeLFuYQ4ro%2BhcS%2BpQsT5QUkg3HnEYD7mOItdvzN9%2FT88bF%2FTLxWgNeIyqryt%2BmlEnzviPQMpK2Eh1x%2BWKCbdV9BPxRn0Ttc4DBEZPVk3vMyh1eT%2BaUC3pioMnKgpoKM7LoWk2UPGEnV6I2COUIDXL%2BUFQSQhmaQu%2FL31OxjyLyjruvSh1j0lwWjZyfK7OR5fkioEgG4Q4k95O0Bq0ZO4iI1dNL27y6BGf4Uos3RKGmXnnmy8ghoIQbnSkeV3WJNh6IvAWv4bioprXvsTAbL4bwF5z4fSsXQozOvzDxZ4xh3g9GC7ny278FnD1TUre2xSkflEZjw1ArzloVrkjxo2Bte0q7tGGeD1CznkhQJAGHakVWF7iyPy2jzWl9UU4NeKv3Z9joYfGd4o9LbfHsB7r2H%2B%2FwBqcvf0dMqOZ3BvHS%2FHstXu0Uhk8m8KSvPnqL67%2FijmpYBMV0P%2FAFHdv4ffLHfPl6vSoQtc3iKx3QQO%2BPTtNmuUWaNVyZxk1j%2BhUej1GoybDjMsipyynkNqcsCtsJIKXbApSRc9Y25x2ArEmPsEcLuYWK%2BKDEbs8%2FmIlxFBw3O2W5KF5lQbbSg%2BR1ih3TzbDYJIJjlHILHeCctMzZHGeP8ADb9dptOYfcl5ZlCFqbnbDoHtKzpIQdR37SD2RuHOnPvhrzsp1ZqWIsB42msUvUaYkKLOPz4TL059SeotLSV6QNfWUbFSrWPZAbF4TsvpTImXwdWcayzrmYObk0il0mWbSQqk0pDKnnHVqt1VrCUqVyNlJT3xkeQSZ0cU%2FEv0yFNTL7ksphJunpCtS9DiSewqA37wY0Jl%2FwAb%2BbVExHh1OYNYTWsM01DcvUZOVp7CJmYbQz0aFIcO4WFBBO4uLiMhwfxlUWm5u5i5g4ro9an5DE1Hl6HQG5NllqYkJRhby20PWUAohTpOsEqPqgNn4GlM08rshsyWuLzG0pPU6fp7jchLzdUbnHzqlloWi6R1gp0tKQnchSb7RjfCRgmm5N0PBWN8dST%2FALes2ptqi4fkyghdOphRqemln4GsJCjex0qQBzMcTPF6clEMVaZfnVhsJUt%2BYcdIJ8ojWTa5jobLrjZzew5VaBLYuqcrWMNUstS05LNU1lM49JoRpCEOnkoAJ6219O8Bs7Deb2A8n%2BN7NmezJnvYqVxFaTlKvMIVoYcSllZ1qAKg24ApHSC4CkC%2B0X2by5zvw3g3FlXyL4gafmthmtyTpqNFxIE1B99goUXQwtK9Gst%2FA6urSCBqEaoY4vKZMZ34lx3i7A8riTBNfp7WHmqXNSTKpyRpjKlqaUlSrgu3de12IulQsbpEenBfEBw3ZAUrEMxw94KxaK7iCXEtrrUwDLS4TctG1%2BtoJvyubWJtAcqthoMshgqLYbSEFRudNtr33vbviRyK7jmq5JClrupagLXUoklXmubm3nigsXgKcIjYxCAgTaIXMTRDSIADeAJJiIHdEUp60BccPYfq%2BJ67TMM4fpzs9VKxNtSUnLNi6nXXFWAHx3PmBjNa1kDmVIY%2FxXlzQaC7iupYOdQ3Un8PIVOSydaEqFlgDrAqKSki4Uki0ZBwhYnw5g7iWwDXcVvtS9OTPOSnjThsmUffaU0y8SdhpcUnc7bx1rwl16m5eSWNMgsbTQpeZGF8Q1StVkurIXVZFwh5FQQ6PLQhtQuL3Skg23MBwzKZSYuqGWVfzVpzDb9LwpWE0WvSh1Inqc6pKdLrrCgClrUoIKuw32sCRiJlFlJUllZCfLKUqIHp7BHa%2BIcb4SxTNcTmelFWlWBMQYVkcEyc4tPRtYjrwSkF1rtWpIHlWuRuecY74P3HVcGPJrJl6nUaaw7WJWfrc2uYkUuTXTNSyW9AcNwW1AglJBsRtzMByOWrqCAVXI2CRcxBxkpKhdSVJAugpII89jHXPDpISWWeQrmclBwLTMU48xhjc4Iw%2FLVFSQzKnpi2hAKtkgkElXOwAuBGD8XC88ncV4Zaz3wrhaiTyJKYZpC6ClAYfZVMISsOuBRJUhekb2ABJ7TAaQwpg%2FEmOMQSeFcJ0p%2Bp1eoKUmVlGACt0pSVEC%2B2wST6ouWPsrcf5WVGUpWYWF52hzU%2FLeOSjcyke%2Fs30laSCQbHY9ojqLJXhSzvykzQw3mS2%2FgipMUmcDc3Lpr6NLsu%2B2pt1KHALdIEr1Ab3KbdsZrxU8PGaOemYErXsMTeE26Dh6lGnSL71ZAdmStzpVOPIsUskKJQN9wAbwHz%2FWLRLGR47wbVsvsX1XBNedkXahSHgw%2B5IzAmJdSihKrocTsoWUPQbjsjH4CiVHVaJ4gpPbBJ7ICMIQgJYQhABziaJQDE0BLY90LHuiaIgXgIAWhE9okgETiJbbXhcwJdDcLyVJw1iFZISDOI3I%2F7MCNT5SyFLm%2BI3E79Wp0tOGkS1an5dEwjWhEygFLblu0pKtSe5QB7I25wtkLwpiBKlm4qKQTe1rtp%2BeNO5b1GjYd4jMTyWK65L0hmqirUZufmyUsMvumzSnVfAbJG6zsOZ2EeauMxOKXiZ83ufYdKM%2BJuG0Rr2fyy2Q2iVY5N6ur8Lt9MXySxFWpOTcYoc1MSSnvswYdLYXYWBIGxNu%2BLr7TcLIUEPZz5VkqBt%2FZWxzHP1eeIyeEMPt7pzpyrIVqSAnFjFwRvzO0ei%2BMpnlfI%2Fia%2FBPMscjV8YlCm2cTVNrR1j7%2BQCe4jtiZvEGYTn2TFFX6v%2FbEARneXCMmqhiisYKxvnXhSl1anS7cy2ZWbEzLTDarH3uaSOiUsBQ1N3uPUY2ezhrhnSUpez4w0ogb2m2xq%2BWJ4UKcGWgma5jdQ6%2BLKt6pgx6UVvFQ6rmKajY8x0%2Bx9IAjYubLnDphun0in4ezvw6%2FV67NeKyrKntTKOQLjzyAUsNgm2pexPoMYs3hPDYGp%2FPXKdJ2uBipk%2Bns3ic4OBV4FubruMlm7eM6x3WD9tviip7I45uFDGdbSRyImOXyRcZap5WYCrlImMc51YEcos7Otykw%2FRqkKlMMFQJBLLQKg3t1nDsnbneN8zcrwoua2%2FdkwytCOrrFVbtvyNwdxDhR4TgVeBzA%2FirMmSWeixxWLBX6qDbuHkxY5%2FMbMpOpK8Y1FQOxVdIUPQoAEeqOm8UUHhTlqDPVZ3PTDcmzKS63ypM4l8kAXsltF1rJtYBIJJMc%2FyWXLeLacxXMPZk5cO0ydR0so5M4pl5Z5SCTstl0pW2ocilQBBBhwoRwavA1o6p%2BYdXMPuqddcUVrWs3UpR5kk7kxdqXi3GdEpUxQaPiWoSlLm30zL0ih0mXW8OTnRqunV5wLxnRyHxE4QWsdZcOJT2oxdJberXvFRnILGrW%2FthwS%2FwBW%2FUxZIn0fDhnEqVVU0TlVOSy0vHOPW29LeIZnSpOhaQy11knmD1YuIrWL5pZUKmlBOm%2F5kZO45HdHONkZOZfZZ1qdr%2BGMb5p4apmIcPOoE3TEz7bikoULhfSA9GvnuEKUQTY2jbcrlBkhLj%2FlQoi0JIJHjzFvT5USjh057XNyKlic6PGanLuaBZI9jZewH3EexrENZlEKYaFNQUiylKpksSR9xG1M1MH5c0mao9AwHjigVfE1XUtUnRTVWGnpllIJWtClKCDYJOylAmxteMMGUmY76Er9rssu56oRWZMm3n982gtnmxCZq1ZdUktKpYCQdnKTLq%2Fo7RZJ6t4gQoKXScMP6RbUuhMEk9523MbTw%2FlymnYppVFzVq9KwbK1p8ytOmKjUZfTOTG1mWylZGo6gLG3MDntG0KlwyYOmVluWzDpKSobJW6i4I9BgapcmP43n5TV0mE8HuBXPVQGrj0ERLJZo1KjzzFaoeE8IUmrSrgelqjIUkMzEu6PJcbVqISoXNjbtMb9xrwsyFBw3UsSIzKw2GKayX3TMzrcui3IDWs6QTyF40VMZK5uTVpqUysxO%2FLODW261IdIlaDuFpUg2UgjcKFwRyhnEbZMp5IYPVqlUq9Vput1mednJ6feXMTMw8oqW64o3UpRPMkmLPmGHk5RVubk6pNyjkrUpBDzTSrNzbK%2Bk97cHPqqCVDe3O47s%2FVk3m6hYQrK7FQvexFLcI%2BSMQzjw3ivCGUdXlMVYYqdG9kqnT0y5qMoqXLqkBwqCNXlaQbm3K4is1U8krZTG1v7gdQljJKaU4oJStmouKUewdAsXjiCoEGRQpPIpuI7a4LZkJyOnEi3Vlaiybf3gxxJO%2F2ua%2FeR0Ko%2FJ9l6Zcm6T%2Fb7efQw9zZwmPRIupZmmZg80rBI80eVw2XEULjRdV9QfBt4spNWwzjHLSaQ0ubk32sRSSF2PTSrqQ28Ug79RaU38yo6QzPwAavhGrqwc8qi14yLwZm5GTQ49NWTfxRwnrdC7YIXpIVY7doPyDyTzfr%2BVWMqLjHDs94tVKJMdLLKcJ6F5tQ0uyr4HlMupJSR2Gx7I%2BvmS%2BemXufOHvZrA070NRYSFVKgzDg8dp6%2B24%2FTWvtXUXSRa9jtAcUZiZCZz0GvsNO5b1Co4fZZamG5vD6fGmmkLbStbDaiAorbUSnSpIG1r2Memi5Y4vyjzMw9iqpLencNz8uH5Gel5JTa5uXeB1Sz0u91mn0qFltrG1jYkG8fQwuutnUlZEW%2BuYbpmMqe5R600t1Dx1JcHWcbX2LSe8XgLRlZgvL2j4XkE4Tw9T2GUNrQ10SNYQhStRS2TuEEm%2Bns5dgj5u%2BEczAp%2BLeIGaoVJUhUtgyms0NxaL28cuXJgdx0qUlNx9qe6N8ZtcTMrwoyGJcE4RrrFZxxNOuystIpPSylGHLx1xQOzikm6WUnytzYDf5r1aszVTmXJuamnn3nFqcdceUVLcWo3UpRPMkkkmAt7uyucUlG5g4u6rxId4CaES3PfC574CY7CJecQ1eeIwCEIQF9ouEqliGgVar0h%2BWddoamXpin9KBNPMLJSXmm%2BbiUGwXa5SFAna5EMJUd%2BpvVR9it06nGmUuYnlibmwwZxtOkLl2b7OOqCiQ38IJPdFmYfflZhE1LPuMvNG6HG1FKk%2BgiIa4CWHngd4QG7eFD%2FlEnf%2FK1f6RMe6oTipXJLMlSSQV4ipKwQd9pucVHi4Utsf1JX2tKJ%2FziYuWJqb0WUOK5ZtJJnK7h4bm1itM64T8ZgOfl1KYGpKXHAnpw8LHk5c9b0784leqk2sODplkPOB5dzzc%2B285i5ChTLqPGUtp6JyeTJCx5OEm3q25xFeHnlIfWW0pDU%2BmnrBPkrPJXoMBa3apNvF4OPuKD6gtwFV9Sh8I%2BfzxB6ozb5WuYmHHVPABwqUevblfvtt8UXGbw49LJnXlFBTKTaZVWlXae0eaJZrDsxKio9IttZp60IVoVfUV2tb44C3qqU0vpNb7h6VOhd1X1J7AfREy6lNuKW4t5awtvo1AqvdPdHrm6BMyi59CnEKMghta9JvqCuVvjiD1AmJYzKHSgiXYTMEhXMK5AeeA8QqMylWsOKv0fRX1E9T7X0RDx2a979%2BV70jQjrbpT3DzR7HKI82t1JWg9FLeNKIVtpva3piKKFMuPIYTpKlywmR1ttN7W9MBUknnVyM7qecV7wDYruOfnil0623Oj1q7PhR710edp1Nm3Xi2lDkuEghVyTrG0eUyTy3tZA0m0B0lwXqQvFdcK1ErLNK0edXjyb%2FJG1uOhwmpYST2aagR92kRqjgxZLWMKooclO0ZCvQZzf8UbQ459q1hMc9TM8r0e%2BpEBy4%2Bo9Er0GOspRzxeRkUrIKPEpcqty%2Bxp2Hnjk1wXZdT2gGOu6SwhctTFv2WrxJhVtPP3tIO3dGWx%2FPY7b8xks6pz2JmCBpsyoIIF%2Fg7R7JlL6cOYaSmXS42qUQtQdcKEKsSFC4BI5dgMeCWqCW20ScwgKbuOfLTa1j5oucgy5V8Ky7KwoO4anHG3kAXvLOHZf71KrX8xjaj86JaW2mfseOfVRENqWxTZZheoKSlM04SRY3uSm17xj1cm6HP0t%2BQXRmU9IypAUxMrUpCu8AjeMh6NcpN%2BMNTTgSlJb0BptYNze%2FX5R4%2FZSfbbdDEs270l9ww0Cmx3F7X7Ysjhed58S1yTdZpbU0KfMqkaczLjoZnWC0LlIUUjZYuQR2Rg9TfwxNOhcph5guAEqQZxwBZ7N7bdsZPNKq63Qy3TnluHcJZlmySLXNgLk7R5JjEdKmcOVSnTtKRNz0%2BmX9jJ5IQ2KepDmpxSkgXcK0XRa4te8DhZRnm1FidNPW025JUd6lqWkh5lb%2FTILgVspCiAQCOzsipX1KVWXFqBBWhtRB7D0YjOaLgh%2FHuL6JgyUeQ2JyZ6aaeULiVlUdZ1237lAUfVGJV%2BSdm8Q1SbkUuPSipt5UspQsfFwopaJ8%2BgJjBP505cjPTXHBjPlY9UVr9jJjW55Tald%2B%2Ff5oxSVcIUlKVW88ZTU2XGZGaU4SCW1DSewRjEhLuOdRH2sROtkolrqry3S1Wsvn9LmCCO3cRDEw01kAdkuyP5Aj21RHQVSuhwW0vEqHqBjz4sSRV21XuFyrC0nvBQN4152s8MkwKfz2kj9q4FeqKmM3Okmf4So8uCwlE%2FLqcXYahE%2BK%2F0SrR9sYgYnMKMeBXlGPW%2BuPGpW8BTVEsTKiWAinnE6ecSJ5xNAVRyhEtzC574CfXDXEljCxgJriFx3xLCAmuIXHfEsIDaXDrnC9kPm9hzNZmhtVk0J5bi5Fb5Z6dKkKQQFgHSoFQIuLbW7Y6HqXF7ws1yozlXq%2FAlQJmfn31zMy%2BrEKgp51aipa1WA3JN9h2xxOlaknYx6ETCxzMB2Qvie4R3mVAcBFH1aT1U4kcA%2BTnG5896lTK6rhbzfwV7UsPYCm6c9T5D20sGcoVHmtCiJacAPWFgttJJB1IueRj5stTihyJjorh04rDldhurZSZm4MlcwMqsRL6adw9NrCVycyTcvyi1bIJNlFNx1hqSUkm4dQDMeUmp2XZfxFwVOJm56bkJhxyjO6ZdLQVZxZPwHNICTy66dzFpwTWsFZQ8FCns68upDF%2BH8X5hT87RsPtTa5SXeZQpX5qllqsvoBoKkX8pK035xraVxr4NbDE2cT0fLfM7EM4kpcZoFXmUpkWlDcIKj5SQeQJVGmOIjiUxfxCYqarlbZZptMprPilGo8oAmWp0tfyUDtUQBc9tuwQG3lcR3BU2TbgWYItt%2FZK4Tf7qL7gTjX4WcrcQt4xy%2B4PnqBXpeXfl2JyXxBrKUOoKVJIWSCCD3RxC68pZuSTFPpD3%2FLAeyvzzdSqU5PstqbTMOqcAVz3N94tkTOOd8U9UBcKSm84wkfqiR8ojrrwlFkZ14YZHkt4Eoyf5CvnjkeiG1Qlge11P84D8sdceEvGjPikNfqOCqKn%2FADSoDj8kX5xC474kUbGIajAb%2FwCEfiOoPDji7EdYxHgl%2FE1OxJQnKK%2FLMTiZdaEqUCo3VsQU6kkbHe4jZLefvAwyhKGeCuaATyvia5%2BMuG8ccg%2BeKgc7oDseXz84GnpmWTM8HE3KMJmmFuTScSkmXAcB6SwXuE8yO21o3dntJz1O41KjV5tzLCbpeIsCSk%2FQ3sxg4KRNyzYSCiVWkFKZgW%2B4UT54%2BabD2k32O1iDyIjq7Kviry1xNlbT8g%2BLTAM3jLC9DV%2FY7XqcsJrFGb7Gkk2LiU2ABBPVACkqsCA2viyYo9ZwRW2F4T4QdE3hd6raadOvNzoKmz%2BZ2SEXE2k20i4GojeLrmHiTKXKjh8yIwPxG5OTWOq3KYU8clmBVBJzFLbcVshfWSVEpKRbs0co1nQMa%2BDyyemTizCOF8cZjYhlHvGaZLYjYTLysu6N0lY0IC9JANyCdo50zrzqxdnZjifxzjCdDs7Nq0IbRs3Lsp8hpsdiEjYD0ntgN7DPDgVQLHg6rAFrdXE5JP8AnIuMnxYcMGDMDY7wzlTw84jwvP44oi6NMTSqwiZbCbkoKkqWTZKj2b2JjjBx1SjubxDplQFWdcS86VAdXUT8ZjxnnFRa7xTgIW3vEwHbAc4mAvACLRMlJhFRA2gJm0EEbCLlLoJA2EW5POLlKHaAy%2BjbUb1mLG0hCsUU%2FWjUA8CU2vfzReqSvTSCP3RjyUGWVOY4o8qhGpbk6wlIHMnWIiqcomUxGc5NwZVcOjs3My9azKZnZemrQXUU%2BUKUzT6T5JKldVsec3PmjfchR8AUBoYfpGV9CTT0gqWZ5C5lV%2BxLiyoXJ25AbxkDsoKmuY8XxC2iWDAeenpmZQw3IEKDZU8tY0tjX1Qk877dpijS8vceTdaEgujzMtNOKDU1OaChlyVHN9K0ktugp5WJBNo6FnY2dnTnXrnzufaW9pXVNNOqPBHt8PWxOrZX5OYn6ROIMuV0ptwECbw1Mlh9i%2FwugcKm3Ld103747r4GqHQ8G5GyuBqLj2XxQ1SJ%2Ba6J5IU28wy44VobdZX1mVi5BTyvcgkERxbVZzAFVRMMyTVew%2FPyU0WkSFTWXfGkJJSXEKACmV%2FCLbg025Kj3ZS5qT%2BUuO5LFlCUqZZJDM8wkKHjUre6kX5FQ5pvyIi15unA%2BblPgRdr3FrrirONX9a31LhHmp1QlKtT5aqSDwdlpxlD7KxyUhSQUn1giPTHOdAhCEAhCEAhCEB8B%2BOYFHEzmXsdsSTahv23Pzxz48L09gb7IIG%2FZf8A%2FMdCcdAB4m8y7gW9sc0R6jvHPTw009jYX0C3qJv%2BSAzrD6wmnKQPJKWvjsY25kFnXNZG4sqdfRQfZmUrFNFPmpQP9CQpDmtp1KrEXSbgi24UY09h5V5ED%2Fs2zG28icG5XYvxkpWcOP6NhzDlMaRNLk6hOiVXWXC5YSzbh5IFruEG%2BkgDneA287xk5dVnF9FzDq%2BRkxM4gw8w7LUupeyyVKlErvq0IsE3upVlHcX2tGD5%2FcS7meNFomHJfCa6LKUqfcqDqnZkPLmHCjQjcAaQAVbdpIjKs0ct8vMx8eVPGMvxH5KYdkH0MytPplMm0oQxKso0N60g26QjyiOZjVOYWWWE8E0iSquHc8sFY1mZmcTLO06jvlcwygpJLxT2tiwBPeRAbXwhNOS%2FABjUteWjFWsfhLAjm%2F2w1bXbxj%2BTHSmCZRmc4EsYSj7hQhzFRaWRz2fYUPxRon2pUvpblyZV5wsW%2BK0B0BwEVyanMc5gSU84lbSsIly2mxuHiPyxyf3ev8cdgcDmG5GnYxx1NSq1FftV6M6lX2Lqj%2BSOP%2B71%2FjgIR3ZkLdXCEAL3NPrvLu0OxwnHdmQqgeEMJv0einV1JPfZLv44%2Bb%2FCbrw%2B7x%2Fmx%2FLU6%2BEfKV%2Bhx%2FlgjRkXiZP%2FAH%2FTD%2F6cx5dZj3ZaAnJLE7d9k1qmKt3kS5jxpRfnH0WjY5M7UmqJoqCXQUkqcQn0mKnii09o%2FwB%2BXxxdCiBcjaGmw9ERWtCL9dN7wQpC79ZO3KAQhqa%2FVUfvr7efeIgtXv0ggIgC%2B8V1t2CSna8Uullx%2Bnt%2FJFRMzLu6dLyF7X2N9oCCW7xUQjeIFbLeu7yP4JB27OUVWxvATWAHKJdogtaV6ih5AT278okStvtcBB2Ft4CJtEhBvFRK2vK6RF087c7RQcmGkLstwb9bTeAqaPPFJznaCJlgm%2FTJ52t54jdrV9kTv64CQRFaSOW0RPR32dRFRZlggEPC%2FpgKSEKVpIPM2j0lG14otvskhIdTsbc%2B2PUsdSAopAvFWKetlvy3h5Xnv54j4ywOcwkekQEx3ii4gRVL7IOkzCL91opLfl7q9%2FTdHlbcvTAUVoiWxifxmVOrU%2BgW88UzNSX65HxwEhHYYl0b3iXx2UuodOjaJi7LpTqU8ACL7jsgI2ES6REPGZcjaYQRyv2fHFRaUgJINyTaAlA23HyxKoHu39MTpKB2n4jEqlI5XPxGAglCu%2F8ALE4R2m8SpWyOax6wRFQOsDbUm48xgFmxzh73ENuzUr%2BCeXfyiazaE6tSwOy6O2AkLaVHa0SONkdu0VyoEXKFE%2BZBiiXkk23H8EwEh5cxEiBvFcoWoGyVEc%2FIMU27KNxvCBlOYgA4WsOgjf3QVG%2FmNOP%2B%2FwAcdf8ABmFDhooZKbapGfI848dXvHIOZmscMGHEnmnHqwr0%2Bx5%2FJHX3Bm4V8NNDB5NyE6geqcVHzL4Sv0Ox%2FwBSn2VO1hUa6vR74cCOfoyY%2FwDEvf6RUdHcCiAc4Kmfhe19%2B3qcbvHOB%2FRLv9%2Bd%2FwBIqOj%2BBf8A5Y6h%2FwDu%2FM%2F6REd3TX9QW3oj2w1MP%2FSafSvWcQWri9mgpCbHK10JI7uhXv8AHcRzgx2x0lm6NXFxNjWd8rnxpItp97VyPbfnHNrHbG3odrwS7z%2B7DHf%2FAJer0qhMSLB7IiXmkmyiIlW80Rs4kesR6VqJIliVyblD5U0ym2ygpQA%2BOJenl7lPjbVwQkWWm1%2BzaAiRC1uyJVPsKSSHm%2Brz64HKJRNSqlAGZaHmKwICZSL7xJaJula6nv6Osnq9cG%2FzxL0sta%2FjbH3Y%2BOAWPdEjo6h2idEzLFRT4y16QsRUt0mlbelRG2xuIDyoippMT2aQtSFlCVemIOOs8ukR91ygmEvVBtsb%2BeIOJ7OXbzvEuu5uHm7J7iIn1sp3W6BbbdUEJACYlHMxVLzB2DqD64i2lnUVXuOzeCFMDUbd0VU3O0QWptJuSIlDjI63SpglUSmxNwCPTEq7KuEpt6oih1kmwWm9%2BRMRQkOq5JPoMBRS3vFUaUjlALYQtSFPNgp5gmxgHGCAS8LWPM7QXTBJWbpN4m0KHMesc4mbUwRtMII9MFPMJ5uo9JO0FEmjeKg2iXxmW1%2FZEfJEVvMIHXcTvuDcQEqygm3yXiVTaTuFn0XiXp2SdnE%2BmJytBTspJ894CkpFoijlaIlxm%2F2ZPk98VENoDaXOqpKoCmlsXvb%2BVFVOw2iXWzbrOo1dwPL0jsiOtrsdR61QTCbkLxOTbSL8%2FNFNC2LX6Vr1KidTrIt76jfziCEdhfmbQTpty5RJ0jVjZ1G%2F7qCXm9P2dG%2B%2FlCAqX1dkR3HOJm9ITzHrIiZsIUTZQ%2BMQEg3PUPqhocWuwTtFQp6NQItcx6G203uvtgMtk29PDjnQ6oWKaZS0j11Jj5o2T4NOdeUccUoIa6HxulzZVp6%2Bu7iAL%2Fa2vt33jAEqA4as50gdY0%2Bk39Hsiz%2BURnPgzLip46JbVpU5Sk6rbX1Om1%2B%2B19o8Vp7qwS1nz0%2Fz0uphHy%2BX9crBeK6%2F1QWM7%2Frli33hMWLJS5zhwEkduIJTf0LvF84phr4gsZDumWEfEyiLTkmkozmwEG0g6MQydz%2FD5xmqnLReP9H%2FAIMVhqvcT%2B9Hth0P4RFBOFMvFjkMaJSr1sot%2BIxobOg2zexcEbpFUese8XjfPhEFqGEcvkAXBxsg277MIt%2BONEZ3NlvNrFBULFVRdUdrdpjS%2BDnXgVE%2FvVe0xL9Jq%2FrkYXEkRcKUKBW4EBQtvBJZO5mEajsATYmPeNNCIp5xIotnYzDYvsLrHP44ioJZTdxxKB3k8vP5oCeKahcxBuYZdHvcy0r0KvEXC00TrdSD2jz3sYMZ0XmiUt2PKKqSgjSp9KV7kpPaBv8AJEpflQnUZhNu%2FVBKTRaIaEwM3KBzolTKUrvbSSLxOgtuglt1CrdxvaAp6PPEbRFam2k3dIbA56jYekxTDrA64fQQfPtAVAIjFJU1LItd0b8rdsFPtDSpSyEqBUICrCKfTtbWWN%2BXPeHTtj4XyGAqRLqSOyCHgtKlautcDSBva3dziVTjajr6RIA5g7fHAT6x3RC5vE7aml%2FBP3JiLakuuWuLjstuRyvvAUVo66rRCxj0OIsCpOpQB65SkmwiRtrpN0BxWruSTv3QEiU3ifo4qplnyNKGJknv6JW3yRP4vMH%2B5Jg%2BboF%2FNAefR54WMenxWZuUJkJ0r0lekSyzdPeLCIGSn%2F2NnvwZz5oDzLR2xJccrR7RJTihqVTpzbbeXX3eiKS5Cd1WTTJ25vYeLOG%2Fo2gKSPtBFM849aZCoakp9jZ4lQuD4uvcd3KJH5WYl3QmblXpcrTdKXmlIUR2EBXZAea294mBj1MU2cmQsysq%2B%2F0fldE0pdr8uQip7CVUE%2FnVP6U81eKrsPkgPLFaXRqVfsj0ewta1dH7DT9xz%2FMy9vTtFaXodeClJTRp8kcx4ssfkgKWnzxDT54uTWG8TPKKWsPVJZHMJlVnn6oqowli1zZOF6pzt%2BhHOfxQFn0XP%2BqKlrI%2F1R7zhzEaVqQrD9UBRfV%2BZF9W3ftEU4fr60gpolSN%2BVpZe%2FyQFrJX3xLFzOHcRaiE4eqirG20m4d%2FijxPyM%2FKLDU7IzEq4eSH2lNqt32UBAbK4Z0g5xUdRF9KJq3m%2FMzsYd4PRIVnas33Thmom3fugfljMeGfSM46Vvb3ibudN%2F7nctt6Yw%2FweWkZ1Om11DDVR9Q97H5Y8tpl%2BpLzH7sujh36RT6W1uPpV86qX5sMyo%2Fzq45pWo3jpPj5srOqmJ7WcNyoPoLq45rXzjLohTlgl2jze%2BWC%2BT%2BPq9KWEIznL7JTNDM%2BWeqOCsJTE5T5ZzonZ1xaWWdQ5pQpZGtQ7QLx275fLvh9n8deq4op8NU5RzyxWVjaW9XBs4zlg0I3P9SLnvsPackE%2FwD17BHx6oqI4OeIVZUBgprq9vsgzv8ALHInSrA423uz6cNiMNvc7KJaZRE8bmHB5xCbXwQhFzbedZFvl5RAcIHEGLasCoVq5aagzt6d4RpXgc7L3Z9ON6e9l88nLTCucQjdieDvP8DUrBCCbG4TUmOfpvFH6kDP7V0ftF3%2FAPHM%2FSi3GnBJ%2Fa7PpRvO9t68SWl4kjdZ4O8%2FgbDA9%2F8AHmfpRBfB5xAhIWMCHfa3jrJI39MJ0owX63Z9KN53tvXiS0rC143KrhHz%2FTe2A1nlb80s9v8ACiZXCHxBC9sBE27pxjf%2BVE8Z8F%2BtWfShHe29eJLTHRiJFIAMboHCLxBC2vL9wE33E6yRsL%2FbRD6kbiBWFrRgN7Skm35pZJUO%2B2qK8asD%2Bt2fTjeiMPvU%2FRzzNL6BDQI3W7wiZ%2FN6Ve0OYsQCU%2BMskg23HlWiT6kXiDUpKU4Beuq9rzbA%2FpbQ41YH9bs%2BnG9bvbevJy0vpETBAHKNyr4RuIZGq2Xcyu3LTNsb%2FwAqIDhJ4gyE3y2mhqF%2F0Uzt6etDjTgk7L3Z9KN6O9t68nLUMmmRVPSqKuqYFNW%2B2idVLJCnky5UA4ptKtlLCbkAkAm28ddZEVrhAwpjaoV%2BXzZx1MVaaw5P05TuMJbxdtyWfQGnkIWkKK3%2BiACQTyAtyjUC%2BEjiBBTpy6nbr8kdO1t6ettE31JPEJpB9zqcsQDfp2drm1vKieNGCct7s%2BlG9Pe29%2BTlb8cUzhxkcIqlcqMyMyp%2Bdl51l2So9cpqGpAtg6FrKkmwWG90qtqNrHmYvPCdmnhDJ3OVvGWOJiYlqT7D1CUMwwwXih5aU9GlSU76VFJTcciR2R4%2FqUOIU2SvLubCvPMsEeohW8So4UuIFQP%2FAAdTqSBcAvsi%2FwDKieNGC5Z912fSjejvdeo22cshyXzbyxXljXcgs%2FJKpe1GpVV2u0esUsK8apc845q1WTuNJstKwDbUtJFiIn4qcycAY1Tl1h%2FLjEc9X5DBeH3KY%2FPTrK0uPLK0aFLUvdaylu6j3mMe%2BpP4gbXVl3Op3sSXmbW776oivhO4ggE6Mu5w3ulSfGGQoH0auXnisaV4F9cs%2BnTvIw69TsoluqjY2yBlOBz2iorlA9siaA5U1UgOLTOIxB0pKHEDmHUm2kg6beaIcIOLOHOiZJYkwpmbiDD0nVMTTU%2FLYhkanNLbdqEkhAMt28tyUlFjqG%2B8aUHCjxC%2FCy6nRpG132fi8qJXOFniCUAF5aT6urfdxo2819UJ0rwL65Z9Onet3svfk5agbQUNpb0aEIT1b87dlz2m0S2PdG4XOFDiB0dJ7mtR%2FgutH%2BlFIcKefqjYZaVYeno7fzojjXgcbb3Z9Onejvbeo20S1EUbRIUG%2B0bfXwqcQIX0acs6qv8AdJ0afj1RD6lTiCBscsKpe1%2FgfF5UTxrwOdl7s%2BnTvVnD71H0ctQ6TDSY26OFfP0lSTllVApKQq129%2FMOtziZXCln%2BkJJyyqnW87e38qHGrA%2Frdn043q9w3ryctP9GYBs3jb44Vc%2Fjzywq4sbHdr5OtEU8K2ffWDmWlUQQLi%2Bg3Pd5UONWB%2FW7PpxvO4b15OWow2Ijo88bZXwsZ9IUEjLiqHzgIsP5USDhaz%2FACTbLSqHu0lFz%2FK2hxqwT63Z9ON60XG9eJLVPRw0eeNrHhcz97MrayPU39KI%2FUu59aSfcwrdx2aG%2FpRPGnBPrdn06d53DevJzzNUQ0eeNsK4Wc%2BkaNeWVYGskeSg6fTZUBws5%2Fk29zGrAbbkI7f4UONOCZ5Te7PpxvTGH3qrVFnLU%2Bjzw0eeNrI4WuIFdwnK6r6htp6lz%2FKtEr3C%2Fn4yR%2FwYVdY7dAQf6UTxpwP65Z9OnemcNvcbbOVHJXMWjYG9kKNXnugkamtDomtJUG3h1euB8EjTuORHnja0ziPIesTi6hV6th5%2BafsXFuMtLUoja5JTe%2B0amPDbn0Lf8FFe3%2F7EfPGG4nwTirB1QTSMZYYqFFnXGumQxOsFtS0XsVJPJQvtsTzjn1WeE4tbzXdrxTNVW2KaonqfQcG0%2BxXArhTcrWwiuijZNUTnEeCeSdupvSoy%2FDq4SqXmsNFwdjiEpT8Yi2CmZCKJUHcKkj90r540H0fR%2FpcOr8JuNqMAs42WlXO6EfCza5fhXKzn7Pub59gsgnVkpdwspR5gukfJflE6aPw%2BtuJ2wog9gK1KB%2BMxoPQyrYtpPpETEhSdBQCnz2i0YBT5WrnYqvhWqq%2FYLLm%2B5vv2t8PWtCDN4XSVmws4T%2BWCKNw9JISiawupROkalkXPojQQShPJtIh1O20T3hp8rVzlPwqVR%2BbcbLmjc32aZkAQFIfwlv8AbOERVRR8hrhSXcJm9yOZuL2vzjQA0J5JT6xExcChpKU2vfZMT3ho8pVzrf8AlWv6jZc33Ogjh%2FIB5KWw9hVGvdJ12uPSYirD%2FD8whIXN4V1E2F3hb1xz4SyRZQJHdbaIXY7vkEO8FHlaudWPhUrpnPuGy%2Fr7HTOAsI8N1RxpSpTEKMJvUt5%2Fo5kuvaEJFiQVKJASLi179sbeRltwNDqNy2AFfvqh8644KDmvqL0qT9r2fEdomsyeqploju0pjuYZdrth1nVRaUzXnOecz9z5xpji1vpXfaL3TTTY8GnLKmNU65nPVMa9bvJeX3A81q%2FO%2FAA08%2FzWD%2FSgjAHBA%2BjaUy909%2FjaR%2FTjg8pZ%2FUE%2FJEdLKur0DfrSI6fdNy8j1%2Fc8lOG3qfp%2FVntO8xl1wRLCkJl8ujr61vG0kn0db8UUH8tOCFA6TxXLsi1v0bb%2BnHCIQwm1mGxbl1BtEvRS17%2BLsX79A%2BaL03u6Rssev7le9l48v1T2ndTWCeChtHRtU3L9aQCQFTiVWtztde0Tv4V4NXXNKzgVC736tS07%2BpyOE%2Bhlzv0LP3A%2BaI9GwkWEuwf4A%2BaJ7tuvkeuNyYwy9eX6p7TuxeCOESaliyZrBDrCz1mlVUqQSDtdJct8cVG8OcLzEuiWk8VUBhlrqNtS2KJhpCB2JSlLwCR3AAARwYtDP6g0PQkfNFMolu1lv7kfNExfbrH0PX9ys4VeJnXeJ5p7TvZL%2FDyws9DjqVQo%2FCRiyZ%2FrrRbsSNcNmJW5cYjrVCrKJAKEuKpWlzQY1W1aOkcVa9he3OwjhfoWeyXbt%2B9HzRDoGP1u39wPmiJv138l1%2FcmMItonP4%2FqntOxcTZw5TZX4OqNMwJM0Zx5yVfZp1NpVlI6ZxOnW5p5Jsdz5o4dqqQzLdCg6tCLfJF90IRuhCU%2FvRaLFV%2FJc%2Fexr3q9xeIpoop4NNPI3bhh%2FcfCqqq4VVW2fR5s59rCnTEqDBwxKgmNNvvU25ojIcOYzr%2BGahLVSg1udps7KKC2JiVfU062q9%2BqtJBHLlex7YxiPbTZB6oOltt5lpKE6luPOBCEJ7yTAdLULwgfE9RZYSxzAYqiQlSddUprMw4bm9yvSCSOwmLJjnjc4jsc012k1bMmakZOYSpDrNHZRIhxChYoUpsBRT640TUJKYpk0ZOaLZXpC0LbWFtuIPJSVDYgiPIT54CvN1BUwsqUpR1EklRJKieZJO5PnO8eIudkSuLtFLXvAVokhfa8XCjUV%2BuOraZnZKVCbDXNzCWklR5JBPMmAtxJBiGr0RGalpiUmXZWZT0brSihSSb7g27IpwE%2Br0REEGKcTA3gJ%2BUTXEUwbRNAR1GGow0mGkwE0RAvEImTAbt4Ukk48qquwUog%2Fdj5ovmYAdlslqrOJQq0xiShNJcSPJLcnNKKb9%2FWB9EWjhMt7fapq5exwv6NcXisYcr%2BMOG%2BnGjS6X3JnGDjiwp5LYV4vJOnQLkBSwkk2G9oDQYqQCdPTqI1a7E%2FC7%2FAE%2BeILqIXr1OX6RQWvrHrKHInz%2BeMj9xDMNNulpPR3t5TqfniHuI5gltLqaclSVHT1XASD57QFSm4LqFXprNSXV5VtE5dfRuElRF%2BZt6IhP4Jqssw%2B6avJujRrWmx69twIulNylzILbMql%2BaYI6vRqWEpT5rnaITuVWYjKltKmZ1ZGxT2H4tjAa8FRf6wW%2BolxOhfW5gG4B7xeI%2BPi19atWkpPWJuD2G%2FMRszAeUWK6LjfDlXruEvHaYxU5Z2cYmEBTDsuHB0gWAb6Sm9%2FNeLXWcisdNz00%2FKUXTJOTLnii2lamnGislJSruta14DAPHn%2F1dXklHldh7PR5op%2ByM63p0PudVNk9bs7vR5ozIZKY%2FUFFFFcVoKQTew35GItZI5huqsmiK9bibQGFOT86%2BkodmHClXNJVsfVFeWmnk2uskRmasjMxAtCRQwdfI9MLRFWS%2BYTCuj9h21qF7hD6Da3rgN28GN1Y3m2Fc1zNHWn%2BDNk%2FFGyuOcD2bwgO3xWdP%2BeTGI8HWFKxS8avPz7AQkGmBYSoKKFCaJAUB5INjYnnYxl%2FHKE%2B2XCW2%2FiM5b7%2BIDlxYOhyOwZJ51inSLLJKlJl2Lq097aeR7BHIy2itNk9pjspumsLkJDxdtRUmXZ6pNrWbTz74vZTlX9m5jtvzHilw5N7HVr%2BEntPpi7Yfn5miTbdUlW0OhsFqYYWeo%2BwoWW2odxG3mj0syDzSFuNyy1LULNI5XV3XjZlIyPrUzSGazPJabbm3PekLNr2B1JCh2%2BbmY2Jtaaaopqna0%2Fi5mM4a7xNIssSjE9hx1yYprySrolC78t%2B4cHcOQX2i0a7rDlYl1rmJWSZWvddiiyifPG2MaYcxnl9U2Omkw%2BlBD6Gio6bH9JCk9p2uL%2BaNWY3zSxTNFqZknxSHphClPNU2WS0004nZIW3uodgNzvzjas4pmnOZalrTXnEUwx6RzKxRQalLVOmuol5yTc6Rh5tsEoVYi9jseZizMV%2FpnGKXSZGZqNSmXNEvIsJK3nnVHkAO8xi2P6PjyYwy3mFNU5iSpNXmRLialWujS86BupIv3g3I2vGHYXxxjjAc07OUZ51tM4gsrmG0hLxSfKCHrakEja4IMYqrSJj8XLYosKqYzq5s3TbiWcsqXN0NVVam8cVtjoq1MSjt2qRLK5yAUNi6RYOW2A2vuYxHpG9HQIcSlWnTGGYdxJJ1KVbMqSkHZaF%2BWhXbq7z54yuX1uN9f4SdKorZRFFEU55%2BGfDJacLhZ1LdWaOVYfnJhQQXEBd033023jBqewG1IX8FMbSnktooFTY6ZatUoogkDcptt8R3jWDWgJT75EWkZTDNYzMw1FjN1bNWrSknZyYUPkAixYela5XanK0Ojyzs%2FOP%2B9y0skalrVuQhA7SewRfsYtdNP1hf2syr5D%2FriyYUquIMNV2VxThebflKlRXUT0tNMeXLuIUClY9BtGpVtbkbFyksVzVIcamJaXbcUzspDoKVJWDuDHsaxNO4omzLinyzThQ44PfSNRCSbb%2BiLPSaTXcZVj2Oo1OcnqlNqW70bY67qt1KsO08zaKDlKqNNm1ysy09KzLRstJFik25fEYqlRcrSVn3yVKf4Y%2BaKfso12ML%2B7HzR5X5ZTbikBJVp%2BFpMUuid%2FU1wHu9kG%2F1BX3UPZBv9QV91Hj6NX2ivih0avtFQHs8fl%2FhMK%2B6idNRkwLGWcP8MR4OjV9or4odGr7RXxQHt9kW%2FwBRV8cPZFv9RV8ceLoXf1NXxQ6F39SV8UB7PZM%2FqHyx6pd9EynqXSpO6knu7xFp6F39SV8UXGnSzjetxwWUsaUp7SID0mIEd0ehuXJiZUqR2QHkse6EexMoSNx8kDKemA8cVExVMuR3wDB7jAQSSN4qJfUNoplpQiUgjnAenxiJVPg9seY8olgK6nQYNkqMUFXiqwbdsAeFopgRWesYpJgLnQh%2BecqDyMy0n43Ex1z4TYlHEPJtnswnR0fEyb%2FjjkjD6dVUkU%2F%2FAFjH%2BlTHWvhOTq4lUt%2FqWGaUn45dJtAcduc4kJ74nc5xIReAazFRtUUtMVGxAehCrREuW7YlAFoprgKwfV3%2FACxKXD3xQiIFzATlxUS6ld8TBtRiYNKMBTGpXbDSe8xWSyvuicS6z2QFEJPdE6QYnDKhEwZXAU9JiYG20VAyoxHod%2BUBBF%2BcXCTO0eJKbbR7ZaAzClf2q9Z%2FHFwyolhNZx4ZSpVktTgeJtfyElX5It1LJ9i%2FWfxxfskJ1Elnfhtxx0tJcmFMlxPlI1oUnUPOLxWdkrU65dq4IxFgqaqwwpjEP072Xn25lFQKQ5IuPJQUoYnW%2FKDd90uJuEqvqBEZhMY%2Flsv5GdQ5RV0%2BXS8WVMSt1yilJ2JSAShKdr3AAMYHhSnUqpYkp8tWHES8qqaKA9MkIadcBOgKc5ISpQAJOwvHqzWxDiCvVxWGcQYInMIGTl7zVP6riXCDbWHBsppQHVKbg77x37KmiLWZqjVt%2FwDqP6yeevM1V0U007dn2Rltnw%2BDwsIkZpOOsS1Wal52Vdqkw6XJaXU9ZU8i%2B4bUqyS4lNj0d7kXtflFwQJmXYdpjkipL8qoKIUAg35ELHZ6R3bxRnMH4Ipsl4%2FQp6oMzqQD7EzzSXW3yf0yXfRbSRz0OJBsNjFyobFdr87TcMyEi9NVWqzAlGBsslSvhKNyQANyeztjDeLSJztZbF1ommmLONfJD6I8N83OTuR2D5ie%2By%2Bx4Ryt1ErUlH8kJjZMWfB%2BHZbCWFaThiU%2BxUuTalUn7bQkAn1m59cXiORHndfYQhCAQhCAQhCA%2BA3HWdPEvmVtbViOc%2FHvHPUwbyksnT8AEj0x0Hx1b8TOZdri2I5z8Y%2F%2FADHPEyQJVmwO6UwGc4d%2FQtv%2ByR%2BONh5a5lO5aVCpTyMBYSxUmpMts9BiKQEymWKFFQWyfgKN7HbcW7o19h9P5mPmbQI2NlLlJjDOXF8vhbCcqtLSVJXUqmtsqlqdL8y44RzJAISgdZarAQGy6TxJzddq9OoUvkbkpSVVSbZk%2FHp%2BjDxeV1qt0rpCQQhIuTFTinzVy3xNUGMvMrML4cEhQp4PVDEdNpzUsZyZQgoLEsUAEy4KiSo31EADleMeqmL%2BGHDVTew3J5M4rxNSpN0y81X6jXjI1B5SSUuONSqU9G2kEGyVm%2FfGP5l5TVvB2vFlEw%2FXxl%2FUHGvYSsVWS8WddbcQFJS63clB5hKiAFgXEBtzBM4iT4DsbTZR0hYxVdIvzPTS4t%2BOOel4vnW3F%2FmZryvtyY6DwVJrnOArG8o04lJdxYm6zySC%2BwbmOf3MFzHSL%2FPCX%2B5MB0rwF4hdqOOscSz8qhKPaopwrCuVnTt67%2FJHI3d6%2FwAcda8CuHXqXjXHcwubbdS5hXodKRbfpib%2FACGOSiLW9f44CCI7tyDSE8IqW%2FKJpld59%2Bh68cKJ5x3PkAtDnCSdfwZOu39SHY%2BbfCfOWHXf%2FVj%2BSt18I%2BUq9DkrK8JXklipXaisU4f5gxPRmiueaUlDalNnWkL3SSBcXHaLjlE%2BTzcu%2FkljSW1tma8dp0yy0FjpChDYDi9N76Rfc2ttvFOnfZxYX6i%2F5pj6NZ7HJnaxGp545j0wolnajJuqS0hVzTZVNrjkLN8o8COI%2FMdryZqT9clL%2FwBXGH4tqElUJxC5BwrQ0w20V6bAlI3jHIuhtJfEjmWt0veOygUQRtJS4AB5%2FpUTN8SmZzYAFQljbleSltv8zGq4QG2DxO5rKUVKq7JJtzk5Xs5fpMR%2BqazW2%2FPpAsb7S0qP%2FZjUcIDb31TmaXW%2FPpHWNyPE5X%2Bp88Sp4m80kW0VsptytLSot%2FmY1NY90LHugNqu8SOZ7zaml1hBSo3UPFZXrd9%2Feo2U2lSJkThbQpRT02ki41FOrl2i5jmC1o6rYbClgK6g8XNx2gdDzgNW1HO3Mqnsyq3MQuPF1oOp1MMjTe4sOptyi2jP3MQFSvZQlSgQSUt335%2FAjFq9OsTbEi20SVMSgbcuLdfUSfxiLDAbJHEHmQnZFV0jTpsEN2ta32kTDiGzLSq4rSh3gJb3%2FkRrM8okN77QG0xxHZo20%2BzzlrW8lr%2BriRPEPmWm2msrFiVbBvmefwI1dv3xMLkQGzVcQmZC%2FKqyyO4hv6EDxB5jqSEGqqsBYDqbfyI1npV9qYaVfan4oDZf1QOZTgDBrSwhRA06W7c%2F3kbZ6BDetbelS20lxOqxGoJuDbkbHeOXWkqDouDtY%2FLHVUqNT2kNld2VDQPhe9q%2F%2FPqgNa1fP7N6nGW6TGtQe8Yl0TAKksAAm45BrzRahxHZrJ8jE00n0dF%2FVxh%2BIJlid8RTKq1IlpNtkqtbURck%2FL8kWMpF94DZieI7NhFujxdOIsLC3Rf1cVfqlM4NZWMZzgUTckBkX%2FzUashAbUPElnAV9J7dJ8Kve46H%2BqgriTzgWDfGc%2Bb87hn%2BqjVe8N4Dah4lM4VbnGM0T3lti%2F8Ao4lPEhnAopJxnOkoN0khnY%2Fe41dv54b9t4DaSeInOKZdbQ9jWdWkqSmykMkWKhcEdHuI2G%2BBJ1Wael0JZVLrfeRYAhtYQpQIHLZW9vNHOMslTUy3qOkIWkm%2F74R085INzVWqCQdIW2%2BsX7PeFKgNb1rOvNqiCVYTjiqLDks3MgrU2T1tx8CLQeIXNoqClYxnioG9zov%2FADYxnEtQlqomQclVqUGKewwslNuslO%2F44x4bmA2T9UPmxtqxdOq08rlGx7%2FJiP1RObvTLmBjWohxwAKVrSb2N%2B1Ma3KD2RCxgNnDiUznBSTj2qkoN03dTt%2FJiT6o7OLUVe3ipb7n3xP0Y1nY90TdGojYQGyk8R2b6FBxOM5%2FWBbXrGr47RT%2BqHzd09H7bpvR3ah8141v0DkTdA53wGy2eIPOCZfaZXjaohpxaW1oDo0qQTYpII5EbRnNRaQzPvttJCUhZsAOV97fLGh6ewfG2taeqlxBWe4ahHQlTZ1T8wrUnyh%2BIQgXjM9J%2Bpcw8oeSMfuX9PsefyR1rwXo08NNHP28rPq%2BOcUY5IzgnqZI5AYYwdMVqnprhxYqpO0pMyhc03LqkrJdW2kkoSSbC9jvHXnBs4h3hsoimkFOmQnGzc3usTS7n8UfLvhMme5LCI8pT%2FLW7eExnNXo98OAlkKmXSnl0zoHn98VvHRvAoB7sNYX2jD7gHreQI5uBPSq%2Fvrv%2BkVHSPAqUpzdq1ydSsPvEegOtk%2Fkj0Om36gt%2FRHthp4f%2Bk0%2Bles1EKXxjVJDikhHuZOc%2B7oT%2BWOcV9RtwnbnHR%2BZ6JVvjSqCJ2cYbE1l2G0hbiUalqaAS2m5F1nsSNyeUc6zEs%2Bx00rNMraebWttxtaSFIUCQQQeRuI29D9WCXb%2BCFL98vV6VXFeb2McDzc7ScPtUBuRpkwzKNNu0WXfOnoErupa0lS1EqJKifRaMR%2BqWzG7ZHCx9NAlj%2FRilmxNyXstX5AOWfTVm1oQfKKBLJBJ9caxWLR6hptovcS%2BYrtryWFk23snD8sB%2FNgjifzHaGlFPwsB%2FwCQSp%2FoRqggX5RJYwG3TxTZmk38Xw2B3ChStvi0RBPFBmSk7SOFj%2B%2FoEor%2BhGo7G9on6FR7IrI22nihzKF7yuGFXN%2F7RSu3o6m0RPFHmMposmn4Y0E3sKJKjtv9pGo%2BgV3fJAsKCgLc4gbf%2BqjzOc%2FScNfxFKf1cX52szmK5KQxTPsSUvO1OXLkz4owllta9RGvQmyQSAL2AjRUizqdKVJje2F5fxjCGHngm6FSjqAe8pdWDAePE2a2L8Mrm5WSapHisrPKlWGV0thVm0oHNRTqUSdySYxk8QWOCrWZShX7xTWR%2FRiGa8zKeyNap%2FTJ8ZYrj6ujHwUFpPyXEa00%2BaA2ajiDxs0NpOiE2tdVPZJ%2FmxN9UjmBqBMtRTZQUPzuZ5jlzQY1aU27IlAvAbaTxNZjJWpwNUcFV72psv2m%2FwCpwPEtj4jeXpN7abinsXI9OiNT6IiGlHlAbV%2BqUx7%2Bt6T%2FABfL%2FwBXEv1SuYYGlDNHCe402XP%2FALcatMu6hCVlBUCYilhSlW0keaA2s3xJ5jW6rVEH%2BTJf6EZKqbma5LtV2eSyH59jpXAy0ltN76dkpsBy7BGjaa3rcjfOG2Eu4XpjtwpLsr72q1ttZSR6biAnxLn7mZgx1%2BmUubpCZKUmFykswqiyag002lKQNSmytR3NyokkmMXHFDmfr166Lf8A8plrfF0dotWakwwudnpH%2B6ZSrTiXgdiL9Hbb1GNdpRaC7bf1UWZwJUPYZNzc2pcqLn73FZfFlmqoaS5RwPNSpT%2BqjTjibxT6IHsgNyq4r81VpKTNU0g8702U3%2FzMSniozPUQpa6WogabmnSvL71GnOiHdFUo0pvaA279VLmZv1aVuLf2ulu%2B%2FwCpRI7xQZlu26tHFjcfnZLc%2FvcalDKlKAF94Fi3YYDb7fFBmgtSCpdEIA0kijSilW8124yWbml19MtVp1phMzUZdDkwphpLSFuEkawhNkpuALgAC940RT0IVsRHQFJlw5RcPvtgKC5FkoPO%2FvihAY3iLOPGGFHlU2TlqOZZDrzTLTlJYV0aW16QnUU6lHtJJO5izDiKxyk6hT8PX%2F8AKmPoxa81XGHK7MSqHgt6Vn6g28LeSrxg%2FjG8YUW0pTciA2MeInHF1fnZh%2B6jcn2KZ3%2FkxUHEjj1N9NMw4LjT%2FaeX5fcxq9YvyiHRmCuTag4mcxE7IkMOJG1gKNL2H8iKh4n8xVApNLwvYi39o5fl9zGqAwpXIw8WX9tAybTHEtj%2FAH10rDS7m%2B9GY2P3MTI4mcwEIWj2Jw0UrIJBozHZ%2FBjVXiyx8KIFu0DJuml8TeYaXkIErhlAUoXAw%2FLG2%2FnTGRGemKtoqs0hlL84gPOBlsNo1Em%2BlI2SNuQjRVNQhDrClKTuofjEb7pLKV0SlrStDgMokhaRsRqURY9vOCGUF23DZnK1oIvIUg6%2Bz%2B2LOx%2BKNkeDMdfUMbSqXSZfx2lPKb7A4OlAV9zceuNf1FtElwu5tPTT7THjiaW1LoWsJU%2BUz7RIQOarWJNuVjGeeDMSgTeNySoL6elAC2xTd25v33jw%2Bn85YJaemj%2Bel1MI%2FSIa%2FwCKJerP7GY26s0wn%2FMpP5YtORe%2BdOBEfb1%2BVH4z%2BSLjxQqJz8xr5p9kf5hEW%2FIsas5sBaVaSK%2FK%2Bvc7RtWtP%2Fqsf6H%2FAAY7H9Kj%2BKPa6E8IdpOEMAX8oY2at6Cwn8ojRmeYJzaxJ%2F41Ubs8IjMMNYZy8DkwGwMZJcIvYBCWUXV6riNQ58Mf8KdZn2yh2Wnl9PLzDagtt5F1DUlQ2ULg8o0vg5pywGj%2BKr2oxL9JqYTOY5xDl5hBNXww5JNvTE443NKmKezMqUgJTpSC4lWlIJJsBuTzjETxM5hqv0jVJ3JJApksBvz5Nx78x5tmTy%2FlZN0qDk9OzBa22IbS3c%2FGfxRpYpj3bTbXd4mcwkIshFJT%2B8psqP8A2opDidzOCy6JiT1K5nxKWN%2FT71GqltgxL0UBt1vipzZZGlmoyrY7kSEqP%2FZiJ4rM3lc6w16RKSwP%2BhjUQl7xMJXY7QVltj6qjN9RJVXrk8yZaW7rfqMTN8UmbbSNDNaaR6JWW%2FKzGpxK%2BaJQxpVyghtv6qXOPR0Xs%2Bkt%2FaGVlSP9DGRYYzKxTmXIzzeMJ9ubVT%2BjEqtMs0hTVybgFtCbg33BvyjRLCPPG1coAAzWwkm7aJe%2B3YpVufqgMoxPi%2FEuX2H5acw1PNy3jQeemSllClPFC0oAUVpNgm5sB3xgyuIrMgoKfZFO51boatf1Nxk2cM4zK4fpVOdU6pU9KzZZGgFKSmYRcX9Aub%2BaNGhs3gNko4icz279HVkJv3JR9CKv1SWa%2FwC2Fzlp%2BBsPN1I1ipvaKaGVazcm0BtT6pjODSEpxZNJAtaykdn8CJVcS%2BcavKxhOK3vutPP7mNbIlwREHZXqwGxlcR%2BbijdWKHie%2B6QfjCYo%2FVDZp3v7Y3799x9GNeiV27YkcY0tOLB8m3ywGzE8RObq1BwYumARyusbfyYyXDWNsU45p6nMTVfxsyqgGFOEEN3NiL2vvtty2jTVMB6ONm5XuNuMVFhF9bCm1L9Cjt%2BKAyzEeYePcusNyqcFYmnKSwrpJmZbliEJmHS7oCl7EqKRsN7CMId4l863r9JjyodYWNnbX%2BIRec3JxiWoFJp5adS%2FNS76780rSmZFiO63KNQlsDYwGwvqkM59ISMfVYWFhaaULRIOJDOpKShOYNaSkjSQmdWAR6o1041dUSdD19MBspPEnnWkaRmFXALk%2Fo9ztFoHiPznUSVZhVwk99Qd%2BeNcCXuk7ROZbyduyA2IOI3OUHUnMOuA31bTznO1r84gjiMznSnQjMWupT3CfdH5dvVGvBLXUodwvFFxhQRqEBsw8Qecak2GYldT501B0W%2BXaMvw1izFuP6A6%2FizEc%2FV1MzDTjSp%2BYU%2B40SFBQbUq5CSALp5bXtGmZOwRG28pFy01Rqs0khTkpNy6VC3LUlZ2PxwHqzBxfjDA9FpPtXxDUaYz4qjpG5SYU0hxxbqyXFBJ6yrJABPIC0YGrPTNRSQg42qpSOQM69b%2BdGS54T7LUvTqK4k9O5TmJpFiLdGHnE39N%2ByNTaNoDL1Z4Zpm98a1cX2P5vf3%2FlRROdmZ2kN%2B3asaRyHsg%2Ft%2FKjD3WLnYxT8W8reAzRvOvM9tQKMdVsEbA%2ByUx9OKnu05oklXt6rVyLK%2FPGZ3%2FlxhCZU2iu1Le%2BC5gMv92jM3QF%2B3GrG3YahME%2Fz4g3nZme2QWsY1VBSNIKZ6YFh93GG%2BLuaF7xL0CkpBJEBnbWdWZd0qcxrWbpNxoqEwLHv8uM9wvXq9iemiertXnqg62AW1Tcyt5SArewUskgbcrxpFtADdjG5MsJliZwzMpTs4w%2B2yr0hBJA%2FwBcBufhsl3HM4ae22jrNMzLno94d2jD%2FB3FoZvVLUn35WGJwNG%2ByR0jev1kAD1xmGSGJsKYBxo3jDG9dk6NTJND7Spp8m63HGFhLSQkEqUQCQAOyMR8HqypOdE5rFiMMzpt3Aqbt8keV00iO8l4n910sN%2FSKfS2Tx7m%2Bd0md%2F8Ai5LDn3OrjmxcdIceZSc72AOacPSoPrdcjm9e8bOiX6lu3o98ta%2BfL1elK5cSzrvJSEKI9Qj6QSlUl8ruGSnV6iSjQRh3B4qjLJ2Q48mWS6oqt2rWrc84%2BcD%2FAOg3usPsSh8kfQTMRt1fCFUm0WSRl24bHtCJZBPyR5H4RqYtbxcbGvXTNc5x0Y9kzzujhczTY21VO2Ihzy1xZ8W88tuoSmTXTyryUrSJelTCkEHlYgnv74uMlxWcXDkuXF5HMFKdi4uRmU2PnF9vRGiM4MRYjkcw6tK0nElakZIS9OdbYlak%2B00NchLkkISsAXNz6411J4gr0zL9JMYkrK9Sjq1VF86vP5ceostFMEtbOKqrtTnMckZe9zbS3tYrnKZj7Xck%2FnxxXIp0zUqDgmh1puUmGpdSZSnzQUpSxfqgnewBJA3FjFhRxMcaxFxkBMKFr3FImo5BFZqSVJWmv1UKQrWk%2BPv3SrvHX5%2BeKjeMcTLaL4xZiDmT%2FbWZ7OZ8uLcT8D5bvSjuq28Z2PI8TfGI9OMS09kZ4i26oBb79MnAhCSd1Gw7LfKI9Vb4j%2BK%2BltsO0%2FKyn1Vb3SdIJemTw6IItsbgbm%2Bw7Y4tp%2BLMWz7HSoxTWUJ%2B1VVZr49lxBGLMbPTDifbXWrpN7mrTXPze%2BRXibgeecXeOved1W3jOu2uLHjBT9kyCW5vYWps2m59Y7YudO4rOKyaUU1DJNmmtDUPGJmQnSnWBfR1U%2BUeyOMXMT43v%2FxurX8bzP04mOLsZadJxliG3Owq01z%2B%2BQnQ3A5%2FZ4553ndVt4zsqd4qeLCUcDDOSbE%2F1dRdlpGbCUn7U6h8sTM8UvFoGw7NZCONpVzBk5gK8wvaOK3MT4rcGl3FleUO5VVmD%2FTjz%2B2nEyqhKNO4mrSkLX1gak%2BQbch5cTGhuB%2FV4553ndVt4zuhzih4rFJAZyBdC7i92H7bjbsigOKfixl3EpneH5aQpOoDoXwSL2vuI5hzgxlimbwflc1OYgniqSwZLSyFtzDjalteOzagFlKuuRqI33A2jWIxHiC%2F%2FGCrfxg99KJ4m4F9Xp553p7qtvGd5u8TnFEtsvMZR0pdm9YZLM4XL28nybXi3L4sOLlBsrhwedF7EiUmvmjiI4hr7SA4rENWAHK1Qe%2BlHoqGI8SSMuJg4jrCgbWvU5gf0opxLwKf2eOed6Zvlvl%2Bc7bb4uOKpZSF8Nz6ArtLc19GPZPcU3E3JNdMzkfIz6iQA1LibCwD8LdFrRwt7PYvWx0pr9T02vY1V%2F6UeeTxDiRcuFt1ipBKxcAVF8W9WqHEnAuS7xz1b0xfbePnO3kcYvFKAQ5w2vL7jpmAR%2FJi40zjG4g5pn808PjrCnbdE6t19LY33J6hJFu6OEUVbECfLrlSP%2BUXvpRN7M1kbGt1Tnfafe%2BlEToTgXLd456t63d1v4zumd4xc%2BJbWVZHtTL32sq%2FMnQkfCILdzfzRBjjNz4m0ak8PsySnnZ9255Wt1OV44WRXKw1fo65VkX56ag8L%2Fyo9dBrFZm1z%2FSV2re9JSn9Hvct%2FwB1EToVgWeq7xzzvRN%2Bt5%2Bc7qd4wc%2BUMFxnh7qLpQCXF3cShNue%2BiPKONfO5Cx0vD3UClQukoddUFDzEI3jl%2BoY1xU1w2UmktVyfRKJzAqa2VCadDyPztlkrR0gVfQeqdN7XHnMa2bxRihq3RYorSNIsNNSfFh93FeJWAztu8c87zuy38Z3u7xiZ2rLSkZBoKVC%2Bhc48HB6uitFvmuNzPeWWtpvhtqroRYqI6cpA79m%2FljiJvF2L1uhlGMcQalJ1f21mPpxKvG%2BNm5vxQYvxCQpI2VWJgAfy4tGhWBx9BHPO8m%2FXidXCdtS3G7n9Mqu3wxVdxF%2BaRMcvT0cXn6rzPxGh1zhqqa0FAeUhp98r0HlzateOFJrHWYEnpR7c8QpSSLaa5M%2FTiRzGuP3EFJxhX0AixtWpk3%2BNcJ0LwL6v11byL9eI%2BdLugcY3ELMFXinCriYj4OpuYV8fvUe6Q4s%2BIydGtfDFVW7A2C0zCTf1tco4GTjfHabhWNsQ78%2Fz4mfpxTcxdip23TYsrzlhYaqpMH%2BnCNCsC8h11b098Lx40voCOKjicT0mvhnnuqLjo3nSQfQWvXFM8WPEyFtJmuF2uAKPvaktvKuPvcfPOYxHXgFFrENVSobgife2P3cXd3EWJJSiy0zL4orjZcCVLCKm%2BNR37NcW4k4FP0HXVvR3wvHjO9Zni74gmdCE8M9fU5YhxK2nE6Fdn6Wb3jyTvGrnjT0dHNcN9aQ6eXvrgSkXsb2b5jzRyVQsZYtTkRixCMR1RWjFdEIdXUZgPMkys5shQXsFb6huDpT2gGMI9t2K%2BXtur3Mn%2B20xzPM%2BXFJ0JwL6vHPVvO%2BF48Z3NN8bOdMuppJyDnx0gvZT7o%2BQt3jyzfHXnHKOFo8PdXKkGy9JcWPUejjiZrHWM3AX2sc4kJBKNQrMzfbs8uIyWYuYc2rTL43xPz%2BHXpkf04tGheBx%2Bzxz1bzu%2B8T852w3x8ZoBR6Th1rygOdg5cfyI9j%2FHNmm02h1HD9VCksCYPvqydJ7LdHz7CO%2BOHkZkZl%2BNqa9vOKUqDQ1J9n5nlfv19%2B8TTGP8zXyL47xXsLDViCZVYfdxPEzAuW7xz1bzu28eNLtZjjvzcfdDSOHTEFzySEuX%2BVEe2W4186pzV0HDZiM6QCbrUnY8juiOHvbrjuZv49jvEq789VamVX%2BNceZ6uVx8aX8SVh0adNl1J89Xu3XyieJmBfV4553qzfbx48u9HuL7Ppp9m%2BQDjLUyjpWg%2FVWgSg%2BkWivIcX%2Bf8AVpoy0lkVLvrISpLTNYlivSTYbW3j5v1Lrvy9utqV2kqv6bmKCJcLeb94TcK5pFomNDcCiMu5qevev3ZeJ%2BfL6dVTiyz2whTpuuY44asRU%2BmU1Cnp2ZQ62roWULQlx22ndCS4i6hsNQ3i%2FcW0pI4x4cZ3E0%2FLpW9R5mRqFOdWj3xnpinUlJ5gLbXuOVwO6PnvhN6psYRxyvp51LScOKYSsTDhASqaZ1IuTyIAukcxzBj6AcQM%2BuW4S5%2BnvjWZqSoNlX5rCWgB8UeBxrCrng2MYf3FRwZqtMpyz5Joy5Z8aYn2Opd7W1tLvazaTnlTHXn5o8D5%2FuRSIUTtFVR0nrRRUVE7R9kefnWjCEIBCEIBEw09sSxAhR8kwE4sSR8UNFwDblADlFQEbnugJG9I57en%2FfaJllMOqOX%2B4iU6fR6O6ALKygbAejtiYLuoFJO%2FI%2F6opkG4IBSQerEydR5kWt6xAVFLJ20iIJF%2FgCJCNr3iKTbtMBEnSlSkC5ES36qVHyj2RMmwvtzMXfBuFqrjjGFDwXQksmo12oM0%2BWLy9CA44rSCo9gHMwFGTolcqlMqFWptBnpuQpDImKhNsS61syrdwNTiwLJFyOcSuYdra8OLxe1Rp1dDamvEnakhhSpZt%2BwPRqcHVSdxsT2x23gyRxjwh0iUyDVP4ZxTi3NGsTU3TGpkus0iSkWpctTL08SnWtCghYCAD5J5Xix4Zx%2FT82cB1Pg%2FoE5l9R5zEdLD9CquFWps0dxxl8PvyU0y%2BkOpfUhvUlwakqHbtAcWREHvjOs5MqcR5M4%2BmcA4odk5icZlJeeRMyaiph5h5JUhSbgEHYgpIBBEYPo88BRc5Rj9YNm1%2BiMhcFhGO1r7EswGFwEemninmZK6q663LJBUSykKWT2AA7XMV6q3SRMNuUWYeclnWwsofSEutKvYoVbY99x2QFYYdqBpqql0sp1Wg%2BZczCen6Im2sIvciLYtfUiZz7Prv1%2F9XzbRTVAEu2Qm6yQkWAPZ6BF7mcNVGWpqqmp6TdQ2hDjrLMwlTzSFGyVKRe9r%2FF22iyJiZKlIUVoUUkgpJBtseYgJXEExSKSOyLrT00W7rlbVOFtKRobldOtRJ71bAARQqDEkzOut02aXMylwpl1aNClJPYodhHIwHoncOTtPkRPrmJJ1CVBDyGZhK1sKPILA5X3%2BKLUuI%2FY3IE3gIIDi3Et%2BUpVkp%2FIIutZw1UaJLom5hyUfZUvolKlphLvROWvoXbdJt3xaoh0nlfuvK89uUBCEXGkt4bW2v2am59pa%2Bq34u0lYRtspVyLi%2FYN7R5JthUrMOSxA1Nm1%2BwjsI8xG8BSBvsYvrVUwuhpDa8IKdWkWW4aioFR77adosMTQGQCrYTAscDqPnNUX9CKiKpgx4FiYwfMSqXLJ8ZZqCnFs%2FuggpAVbuuLxj1iTZKSpR5AczF4xBhxVCEu61VJSoy740l%2BW1aW3glJWyoKAIWnVY7WO9rwFGs0d2kPtWdTMSk0kuSky35D6O8dyhyKTuDHg5RdKRVpeWYcpNZZXMUuYOpSUHry7nY81%2B6HaOShsewxQq1JfpL6ELdQ%2Bw%2BnpJWab%2BxzDf2w7j2FJ3B2MBuXhQQpWPKn0fP2KV%2FOjY2W2ImMMZL4KxvhyWkvbDhzHVY98mGRMNlLkuUBt1lZKFdRxRSrTcHkdo1vwpkJxnWFKvYUy5tztqjaWTqKVjPKbCmBaolynUqVxFVxXK6mUW%2Bqk9MyZiUmA21dTjeptaFlXVTqG4gLqjiZzQQAHFUBZtZR9hZe6v5MTq4m8yVm5Zw8fMaKxb8UZO%2Fw%2FZFMWS7xVUxBIvdeHZoD8UUk5F5ELRccWmHEDXYF2jzKN%2FWIDHPqk8yhYolMLAAEWNCYI357WgniZzKTfVJ4TN7cqAyOXoEZJ7hGSCyA3xeYMBUbALp0wN4pJyMyROonjDwEEpUUHVKPg3HPa0Bj6eJfMMXtTMIpvz%2FOJqJmOJLHV9DkhhdCUpCkg0VBTt2WHKL57hOSqiot8YeXJSB5SmH9j80QXkFlA2E9JxhZYpJF7kPi8BYF8SWPrWcouDVbFN%2FYNu5B9EUVcRWMFgJXhrBikjsNBaMZEvIbKAIStzjByu0r8kqMwAfjiAyCyeUerxg5WcuYU%2Fa%2FxQGOucQeK3Bc4TwWdrdagNH8kedWfdfLZaOCcD7m%2B2HmrDv2jLRw%2B5SjoSeL7K49P5HXfGr0bRWb4dcp5q6WOLjLG6RYnpHrau7ydoDwZM4tl8b50UCpz1JpVMqEo0ZVr2OkBLIfa1lfvmjZSk6iBcHY%2BaHHIonEuEk32TIzn%2BnEZZlTg3D2VubsvS6XjGg48lK3ItyiazRHdTNLmlOlaWXW1jUFrSyopWOwkERhvHA4VYwwu32JpcwfjmDAc1o1XAv2%2FljtqUW6qWlktNFCuibvtsk6Bt6LxxOhJLiE2vdYFvXHccgroktvqXqSEJC23Lg2CRt6RF7P5T7GG8TlZxLMMDilM1EVzFqVopdNR0kwltJWp3kAhIAJKiTsO02Ed3ZcytDrlFla3KyikyaAUyLDzekoRtdakHyXCbg9w9cfPoVh2Qw5UnKes6wpkyjRvbxnWNJHcbx0hgvM00WVZoqpx11Ek0lpSiTY6QLnz73PrjJaWEWlcTHga9leZs4q8H3QyLiepmGhh6cdnXzKI0nSW5dK9ToGpBtcbJUB6ATHzXm6PRsS1Ss4kxbiaXoNHpbrLE1NS8q5NOThc2ShhpFiVkJUQpVhtY846t4sM3VvUWn0%2BmMGbOptxbKLrdUlS%2BsQBvfTeOapvAlfw3S5tdWYclKFi%2BpIS2%2FUGiy4tppRdZUllXvig2FFKlpGm6gLx16bOzizpsc889sQ0vja86rWfsefNGqU48MVOwjljWariTC2H66%2FNVacqlG8Um6ep1SUtIWApQSysr2IPlAgxgPDNmBg3CGNhI5o0Bmu4IqyTLVaQdTdTeojTMNquClaCdWxFxcd0ZVgusyuXT%2BMME5h%2BzdPw9iuWak0YgkpRc1KJAXqQXmBs%2By6OqtKSHEEAp3BjFMEZIUXMPMZOE8GZrUOSXVZ1yUpKpuSmtEyoIKkIJKAUhZSUo1b3sDuY1re7TFnwKafwad%2BftXut6oornhVa6p8Hmy9EaohfeJLKKjZK5guy2Eqx7IYar8oisYYqySFdJLr3DayPK0nqk2FxY84smD8QS2IZYsjSxOoSLoJ2Nu1PfGu04rqjstJ%2ByqXHFUtTjLUtMqKksoBUlTOknYBV9u8RPgty8v07DnWacKdSfN%2FqIjBaTTFWdP8AXhbVnRVVTlXt%2FrLqybgq7YaodRWtSAtcotoA7k3I2v6o1h0awjo%2FQqM1drrVSw9OImZoMzTTJVotsoAbW8%2FbGuJmoA9Qk2IuTe28K5iYzTZUzEzEsBqcwhyp1hvX9lmXUxdc15XC1NxlL%2B0KlexEmik04LSh1a1LmfFkdO6SskjpF3VpHVF9gBGJ1F8irVA35zKz8Zi54qdU9V9S%2FKDLCfibA%2FJGpLZiMl%2Fw2joXGHmSG3NuugaSCO24j01pBdUpxaytSt1FXMmGGmwtxlJtskGKtVTtygyMQn0EAxZX07xkdUbskm0WF1POKDyEWiWwJvaKhFolItAQHOJ4kHOJ4CaB80IQBOuPfIsCYcICU7C%2B8eCLlSgoOab7rBAgO68qvBtUfMHKvC2ZVTzvFDGJKY1UTLO0hKkS2skBBcLgB5c9owziE4AcY5HYZGPKNimSxphxDzLE49KMKYmZIvLCGnFNEkLaUtSU60KNiRcW3jsSnUbKOtcC%2BAKJnjiFdFwfNUKlh%2BeRMGXUl7WVMpCwlRF1C1rG8alzRz2yOkcj5DhS4YK9O4mqdaXL0alOrUtbMn0kyl0KVMPBIWvpLAIACQO4CAx3Dng0KFTqRTE5u57U3C1eq6UdDTUS7ailxVvegp1aelWCQCE9ptGucUcBWKsH8QWEslcR4nlUUnHDj6aPieWk1FDnQoUXW3JdR1IeRZJKNRBCwQdjbqXNfOLKGpytCwBx%2B5IzOFK%2FMy%2FjMpO6TPyCnNQbedlJyUUXZdRUhKltKB03Te%2Bxj0YkykrODeJPIDE8rmzifFeE5%2BszcpJU7EVQE49T5kyK3G3WXtKVONuNdUhY1gpBJNzAcG8Q%2FDQchc3pfK5vFiMQNTrMk%2BxPiV8XUBMK06Vt3Nik9t9wRyjPuJDgLrmSNUwfRMG4mmMf1LFzs3LtSEnS1MzKHWEpWdCdRDiSFHuItGacf1PqM5xV0VmWkZhxdRkKCmRCWyfGFB4pX0f2xSdiBy7Y3P4RrH2KctMRZTYywLiF2jYhpUxV3pObabQ4pCVttNKuhYKVJIJBuIDmLHXADibL3hymc7cV4tbptck%2BgW%2Fhd6SJW2l14NhKngqyXLHVaxG1rxyM%2B3Yx9VsxsaYkzD8GvL4%2BxjP%2ByFbrUrJPTsyWUtB5fsgpIUUJsBskcrR8r5vy4DwqiUX7YqORTgERSoiIQgJyrUII23iA5RFPMwF5w2Pz0kyOZmpf%2FTIjq7wnwtxSzo7sP0kH1S6fnjlPCgvXaag8lT8on430R1X4T4%2F%2FAKqaog9lGpif%2FTIgOPnOcQJBEQc2VEDygIxFJtFO574XPfAV%2BkiUrvFK574ngJriJ0RRBuYrN8oC94WobuJMQ0ygsupZXUp1iTS4oXCC64EBR8wKrx3C54KbHrK%2FFV5x4NEzfSGlsTCSo%2Bba5%2BKONsrEBePsNN99akP%2FALhEfU7jFy24c8cY4oNUzvzxnsA1CmSrop0vKPhpyaZ6cKU4DYkELTYEQHBGMeD%2FADhwTmzScm5%2FDiJms4hUVUWblHekkqgyk2ccQ7YWDfNxKgFJFttxG7R4MHEb7TtJk8%2BMCrxS1Ll9dDPSEgAX3Wm6kp%2Fd6NI58oz3MLiafzO4istPqZcKz2Ys5l2iemJlsJLQqUs80hmZQlS9wA2EqDhHl2NrRdJWtcH2e2dqalKTeOMos9ETJliu66fUBPNpCFNEK1yzy9ICCm6NaTa28Byzk7wRZkZs5gYxyynatScI1%2FA4QKkxVkuOILi1lKUoU1e6SLKC%2BRSoGMDykyGrWbGcMvk1K1mnUmpvOzjSpx%2FU5Lo8XCisjT1lA6Tawj6F8LGEsdYG4ss4aBmZjI4srz1Fo821XVNBpVSkFOEMOrbGzawLoUnsKeZFo5b4SWX18ccilTDnSsz1cU%2Bkp3ZAQ4Dr7tyOfmgMDb4PcyJrP2pcPtEmKVVatSdLs3U2XFpkWJYoSsvLKhqSAFgabXJ2EbFzR8HBjXBeB6jjXA%2BY1BxwaG0t6qU2RbW1NNpQNThbuSFlKQVFs6VWuRflGTZpV%2FPin8a2PKDw81ealK7iEy0rNoYl2nUOMNMtG7i1ghpKSb6rj1xmZqmA%2BBPKTFeFK3j2XxPmnmElyYm5aWfHQsPLbU3rIvsAFq3PWWfNAfORxvo12j0S3ZEZ5RXMKOgJT8FPaPNEWPIgMspn9qx5yY8uFpuZkcwKVNyJSJpiYDrGtGpOtIKhqHaNt%2FNePVTAfYseYmLVTlvs4qlJiVVZ1kqWk%2FwFX%2BSImIqjKTOYnOHcuE8T0fNCley%2BHpZiXeUgImqM2LusKI66mzezzRNyCBqF7EdsXYvOqp65OpvOLRJNeKtoUpatDd79GEE3SkHsG28cLYLx5jLANTlq3g7EU1TJ2WUlxp1uygFAdqVApO224jerHHVn5MttKrMrgasTbI6k5O4bbLw9aFJB%2BKN%2Bzvc5cGr3%2B6JadpdqZ1059U%2B2YbxksBztcdC6JTZmamVke8yjBASL7EHmAO25jrDhOySw3SVP5kuz0lUaih12SaTLu9MiRcSdLrerlqB2NuXLsjjPIaR4pON7ETlHrWNXsOZfyK0itzNDkkU9laefi6CganHFDs1WSNz2A%2FUjL7L7CWVuEKdgbA9HaptHpbXRsMt7kkm6lrUd1rUSVKUdySSYxXmuLWIias9fJs3zzQvdaa7OZmactXLOc7o55ZFCEI1myQhCAQhCAQhCA%2BA3HSB9U3mXewviOc%2FFHPM8LNSw72EK39MdCcdKv%2F1NZljffEk3y9No57nTdqVVttLp5d9zAZ3h%2FwDQ7l%2F1NEbiybzokctqbO4axJhP2ao09XKXXmlN1RdPVJ1CUUUtPOuoBK5cBfXRbYDUN409Q9mVfvURtrJrAOWOORURmHmGrDT7U9LSso14zLMI6BxC1Oza1PEFaUKQlGhHWu4DygL9mFw5Z%2F4uxvWKw1ghjEvtpqD9SFYoUy0qkzCphZcLiHdQDbY1fCtYC5i%2F5%2F5uSHsbUMtKGaZVMQ1uRo8tmFiSReW7Jzk1TkaGZOTQT0aUNAJC3UCylBVuZjJ2%2BHvhelJM0uT4rFSsjMXvKt1mWbaVfndCVhJv298a7zTyuyLwdhWdnMu84GsQT8kuSEuw3Nyrjc30q1peaQ02S4gtJSlZWRpOqwgMywHMy8pwIY8cdWQGsUtLA7fs0uLes2jRTmMZTplp6F7nbyY3ngtiYm%2BArH0tKo1PLxShCATYX6aXO%2FqBjnQ4TrynVq8Wa5k%2FZBAdTcCuIpSq46x1JtIeQ77VOlF7W0h4g%2BveORFiyj5ir8ZjqjgKotVp2ZGNVzEqltlWEtGq4vr8YuB6OccsOrU486tRuVOLJPf1jAQRzjuHIMK%2BpHd0JurxSu7fwHY4eRzjuDIMqHCK6vUCVSle027Oq6I%2Ba%2FCfEd7bvn5WP5K3UwvVVX%2FDLkzLOlYabyln6%2F7WZV6u%2BOybLdXded6aTYDKgpppAUEaXLnUVAnutHnmpxyQlJqYlyQpLSwkjmAQfyR7crpSpu5Q4im2naSKPIzUlLzAdUrx1yZXLlTZYAGnQnfWVHtAEeZuTlp9xUnOuLRLuJUHCgb20Hb1mwj6PRscydrFeJXBmF8C5z4hwzg2nKkqRKtU91hhT6nynppFh1fvitzda1HzXt2RqNznGbZn45ruZuNKljjEMrJy07UEsIUzJIUhlCGWUMtgBRJvobTck7m5jB3DYxdAN4mAtFPUYmC4D0tspUN4rIYQOwR4enUnlFZmZJ2MB7Ogbh0DcShQIvEbjvgM0yUoFCxLm3hChYgpqKhITtVbbmpRbikJfbAUooUpJBANhexjcC55Eu%2B68y2ENNlaEoSNkosU6QOwBJtHP%2BFMVVLBOJ6XjCiiXVP0WaROMJmW9bSlJ7FJuLg37434ltE4XFrSUCYQp4pQeRWkqsD3XNoDAeJ3C2FMH50YgoGDKKKVSWJWmOMSaHVuIbU5IsuLIUslR1KUVc%2BajaNOORnGZWOcSZmYunscYoEkmo1NqXbcRJsdCyhDDKGEJQkkkWS2Lm%2B5uYwVarqIgAAO14qJaSecUtxDpCmA9aWG%2BUVmpZq%2FKPCibMeliaPdAepEq3qJ%2B2gZRsJKQYlQ9uTfnygXbC14DOMiaPRKxnRg2l12ksVOSeqaTMykzqLUwhKVK0KSCCUkpFxfeNpzVScb8ZmmkJbXZxWlGyUgg3SO4WJHojQ2E8XVfAuKadjHD%2FQeyVJeExLdO3rb1WKesna4soxveUYlVzaXJsaZYJW45pudujJt3kXt8sBg%2FFVhvDeEs%2BsU0LCNDYo9JZ8RdlpFgqLTAdkmHFBJUSbFa1nc9sadVzMZnmfjnEeZuL6lmDixUqatWuiW%2BJSX6FhIbaQ0hKEdgCG0j1RhB5wE1h3RUbQk84pAxEulHKA9rbTZ2MVxKsjfaLYiYINzHsamNYgPSmWaF7fCgqWb2%2FcxKlfLflBS%2Be%2FOA2Nw7SFInM7MMMViiSNYlQqZfckZ5suSz6mpd1xCXUAgqRrSklN97Rni5%2BYfbdnFFPTTKC4dIskFSbFI7huRbujSGEMYVnAeK6fjDDxZ9kaYtSmA%2B30jataC2pKk9oKVKHrje6qZKImX5TodUshp4hu5NilpSki4sSAoD4oDAuKiiUDDufONKNheiy1IpUvOMmWkpZCkNMBUqytSUhRJA1KUbX7Y04OcZhmPjfEmY2LKjjfFrzDtWrKkTEythgMtkhtKAEoAskBKEj1XjD4Cskg7GKqUIMeXV3QLihteAuCGEEdkVUMARbmphQNt49zbxIEB6AwiJVsoHKIB0d8SrdEBsTh4ptJqOcuHZSr0qSqUmoTjjkpOtdIw6pEq8tGtNxqAUlJtfmBGb9I48svOkFTiQtVthewOwEaYwZjSuYGxXTsWYZWymqU5xRl%2BmZDraitJbUlSDsoFK1C3njdMxKOMOLYb6qdkhO9htyF%2BwcoDfmS%2BX%2BXuKsgc5KriDL%2Bh1Kq04SE5J1N9gmbYdWChRS7e6R1B1Rte%2FONqcGyAnhrpLSjYGXqRJ7rzi%2FmjlTFONc3MDZKP1TCeKKRRsI4trLeHJylyVPQJ2aSyx0yXZh9SST1tVrG%2FqjqTgrW%2Bvhqpq1udbxap6VembXb5bx8w%2BEynhXWwn%2FMp%2FlrdvCasuFHm98OCFHVMOK733T%2FLVHR%2FAogHN%2BrKPNOHX9P3xF45xQPfV%2F353%2BeY6Q4Fbe6%2FVesP%2BLsxt%2FhW47%2Bm%2FwCoLefNHthqYfH9qpjzrlm3SMHV7i7qycZ4TksSSdMwKw%2BzITrzrbCpjoDoWstKCzp1bWMaQqRcmZt96YcK3XFK1KNySfWbn1m8bczk9uU5xgVprBM5h1maYwQw7NezSXPFnJREuOkQNHW6U6k6SO2NSzbzMzPTTsr%2Bh1PLLPPyb7c97d197c42dDY%2FId2%2Fgp9kMV8j8dV6Xj4isIYYkMDZbY5plIdl67i1NdXW5kvKWiaVLzDKWFBJ2b0oUU2HO1455f2jdGe2O6pWxR8uVSMvL0fAInJSnON61PvmbWh51b6z1T1gAlKQAADz5xpV8kKIj1TVySExXZbQrnHmvcRMFqRyMUQujMowrnHtbkZa2wixNzTqbWMepFSdTzgLsqSlvJsrfuMSPSTBQkC4095i2mqk2JSdj3xK5U3dwlGxgPY8wlpQ8X2UopT6ybR1ZmVRsP4VxlPYVwpRJej0ilpZal5Fh5x1DaiygrWVOEqKlqJUd7XOwAjkPx5xV9fVVdJCu60dKO4tquYjctjysyEtKVKuNJdmW5VKksno7MpWlKrlOpKASLkXvaAtXEphfCtJw1lriej0bxWsYqoM%2FO114OLUmbmmqgttD1lbIPR9UhNhsNrxz3sOyNt5y45xDiJ2lYRn5WVRTMDtTtHpbzbaw6607MrmFqdUSQpWpdhawAAG%2FONRFUBA9Y2j0MyyDzIjy6x2REPLTyMBeZenMrF1HfsAj1ppUqnrJKhuL2%2FFFiRPOISOsY9CatMBIAWPWIC6qpbGlSUhdjumKExINtt9JZWr1R4vZl%2FvTEjlTdXzVAV5aXaTNspClXW%2B2g2VyuoDaOrc1JSh0TH1ZoOGqHJ0ak0yZMtJyMmVlllISnVp1qUq6l6lEk7knlyjkluassLKt0kK%2BLeOhDievZgKTjLEMsxLVGsnxmaSw2UN6r6dSUnlcJCrd5MB4%2BJ7C%2BGqU1lviei0MU6cxjhBVVrGl1a0Tc6memGvGQFE6CpCE3CbJ25c45%2F125RtfO%2FG9ZxhU6RRpuVl2qZgqnqw1RltNLQXZRt5x3pHdROp1S3VEkWHIAbRqTtvBdOCVHePU1LNLHWMePUeyKiHVAc4KLqzIyyrc%2FPYx6kUuVI2DlvTFlROuN%2BSRaPU3VXgNgLemAuRpUsR8O%2FmtFF%2BRl2htr89yIoGrOgeSgnzx5pipKdFth32MBc8MyjE5iWjyD6VLZmqlLS7iQqxUhbqUqAPZcE7x09iml0%2Bi40qtEolPYptJo9RdlqdJsFSkMMNunSm6yVKPaSeZJjk2Qq01TJ%2BUqciUpmJKYbmWVKFwHELCkkjt3AjqGnVmfxs6xi2tSKJGbrzvjk4w2TobW64dWkHcA87E7XgmGA8S%2BF8O0Cp4LquHqaqTXifCTVdqg6ZTgmJ5ycmUOPi%2Fka0obugbAp25xpZKtaNzGys68ZVfF1el5apScrLS%2BFpE4ZpSJZtaQqTYmHlpW4VE6nCpxVyLDkANo1glZBI7L7QM1ZLaTzXHoal2iN3I8ZcUO6CX3B2iCF6ZkZa1lKJvFZNNl%2FhBXmi0NT7qBzj1N1d1PwbwHudpsvcbK9ced2QYZSUlHUWer33jyO1aYUdiBHneqL7idJWfVBMTkyHB9Okp%2FFeH6XUUFyUnarKSswhKikqaW8hKwCNxdJIv2R0PiWmSFGr9VotHlBKU%2Bmz8zJycslxSwww28tLaNSt1WTYXO57Y5joVYnKTV6dWpAJVN0%2BbZm5cLTqSXW1haAQOYKgNo6QVW5jFilYsnKainzFdKp9%2BVbUooZdcWStKdXWA1XIB5XghtPhoyayszqx%2FU6LmphVValpPDM47KLTPPMKlXGjrSpAbIBJKiDquN%2BUZPwDU6nUrE%2BYlMprS20S1VpgbC1XIbCXha%2Ffff1RrHDeZeamS%2BE8RZo5XUTCxlaLIokq1PVcLfmfzc8GEpYZC0p0pIQSd%2FKN4zvwdNVm61Vsf1OcUFTU5OUt11SU2BVZ7s7N48F8IlM95q5jw0f%2FALKHUwj5eI%2FrY1ZxRJKc%2BsaXt%2FbFu1u7oUW%2BS0W7IOxzswHqO3tglvXuY9%2FE6AM%2Bcbaf2UR%2FoG48WQH%2FAC24D%2F8AP5f%2BlG%2FbT%2F6rn%2Fkf8GOx%2FS4j96Pa6T43qJT8QzGVdErEsX5OcxbMsTCErKS6gyjQKPNfcbb9Y2jnjMMUaVxfVaXhzC8phykyM%2FMNylIlX3XWJTrAK0F0lVllOsjldRsBG7%2FCDVWq0eUy0qFEWhFRbxNNGUK03SHTLspQVDuuRfzRozMiRxNTcYT9OxgKL7YGXnBUF0VThknFazpU3rJO45729HKNP4O5mMDoz8NX80q4jOd4r9Puh5ZvDWHMSZMZlVCt0xUxUMH0uUqlEmm3lIMm8%2FPsMv3SOqtK0WSQeVriOZHhp5Rv7GeNarg3LSq4apUrLOt5gNex1VceCi40xKvsvthm2wKljrE322Fucc%2FzDl4901EE7xVS0DHmS5aKqZjSd4KPa3Lo7or9CjujzMzQO1o9aXQRygJCyi0UHG2wY9K1C20W99zciAn6nmjpLB8nRZTIbBs5KUSQl6pVqjWHZ6ooQfGZttmYQhttar20I5gADeOYS5vG6crsZVSvYS9o083LeJYaccnKc422UvXmnAXkLVeyk3QCNgRvvvAZ%2Fiek0GtcPOYdSqtIlpmqYcmqE%2FRp9RUHpMzE4puYQixsUrSBcEHdIIjlx4aHNMb5zNxfXKFgGYwhRUMmmY06N%2BtBxjU4n2PmQpjol36gKnDq2ubCNCPLuq4gJ06Tsox6W2EWuCIt51EXBtE8rMrB0kwF3aZbtuIn8Xb7opS0wkjePV0ybXtAUVy7fdHhnm0tJUvotSCoXTqteLgp1J5xbag5dBR2QFOSfS0CkoO%2FIA3jpqnrp0jkllzLydCpbD81KVOZmag1LJTOzR8fUAiYdG7oTp6gPkjaOWELIjdWXeK8R4nwy3h%2Bruh%2BRw8laaUsspSpAfd6R5JUPLBUAR3QGwsV0%2BkVnhnxdWahSJR6o4exHQm6bPlFpiXamPGA%2B0FDfo12BKTcX32jmR8jpNuUbkzLxjX6HgQZe01baKLX5hFWq6ehBdemZVa25ezh3ShIWeqOZue2NKlZPOAiN17x7WZdtZBIEW8qIF49EtNHVa8Bc0yjVuyCpVA3im26e0xV6UQFNbLY61vKjyTCGEIUj7aPW4uLVNOlS1eaArNO25R1LKeJS2XeX0pJU2nMB%2FC7E8%2B5KyyW3ZmYU%2B%2BlTj6wLurtsCeQAEcmtuqSrc7RvLLDEuIcQYRaplaUh6Ww90crR3yyEOIllFxSmSofZEBRuNW6TfextAZrmlIUub4eqpOP0qTfqMji%2BlMy9QUyPGWGHJWZK2Euc%2BiUUglB2uL7GOZFkGNw5v4qxDLYck8CsTCm6JOoarM6z0CbPVBtTjbbvS%2BUbNLICLgC5Nje8aW6WA9CAg84qttNqjx69I3iqw9vzgPWJZHdFRMukbgRK24CIj0ouBAQW0kBXnjyOpRyEemYeSlIi1uzI1Gx5QFfURtHV1VYl04KwO1T6bLMKRhCkzL%2FAIuwlsPOlLgU64Uga1nYFRuTYDsjkZM1pOpXKOisr8Q4sq%2BFmGMRuqeYo7bEjTi6wlLiZIJKm29QAK2xdWm%2B433gNtZCsSc1mvhBE1TqdUZSdqrLD8tUJVuaaSVBSdRbcBSbBRF7dsXjIqmyFM4z8cSFLpsrT5dqjVMol5VoNNNp6RqyUoGwF7xiuVNDxZWcXKoOCMcu4KrDy3J2XrDckmZWlttlxwspSryNS9B1psRbui18CNermK8%2BKtiWvzs1UZ%2Bcw1OOTc2%2BvUsqU61uo9tzHlNNYjvJb5%2BLLo4b%2Bk0Mz491JVnm0Uu6lLw%2FKHRY%2B9pDrgG%2FI35%2Ba0c29u8dIcd51Z5sg%2FBw7Jp%2Fzrp%2FLHOShvt2RtaJa8Fu0%2Fu%2B%2BWve5zt6vSg8keJzHmZWfkj6CZlTLQ4VJlSypTbmBQyq3PS5LtI%2FKY%2BfM3qElMkfqDn4o%2BgmcoZleFioyyChKUYBI6%2FL9Dsgeu%2FLz2jyfwgxwr5cIjxp9tG90MN1Xe2nzR73CufrLUrmJPSbN9MvIUxsE8zaTaAJPabARqeVaelpYJdCU2vzMbBzzl%2FG8ZIcVVX2n3MNUEoCm79ITT2iSo9l%2B%2BNblbjckGn3gopuoqV3R9EuufxFGfgj2OXbfKT6XvYDBsp2ZaFtzdQ29USyjLIkVNuTjCV9I6qxWLWKjbeMZfmF9IreKfTufbxs5sTLaMpmmyimH5lgq30qS8kpO%2Ff2XEStPdDMvul1mzigRpeSSIxPpD%2B5%2BIRLAZi5PNk7vtffBHncnGb7PtffBGLQgMkL6FfDbP8ADETsyU07OS8wlKAhskqUVDYW5xjzC7G0ZZTHGy31%2FtT%2BKAz3OeQW9RsuJRlLKVN4KpriQCACC9ME37ySbkxq%2FwAWUl0pUttPpUI2fmtMeMS%2BXbyAOj9oNMQkg31aXpkH0biNU1dfvkUHrnZdIkill5tThIA64233j119DU3IdFLzMspwKSbFYFwOdoxMueeIdJAZU46n2NRLtqQp3o%2BWoc%2FTePPKKS3KJb1BOn90IxyH3EXGROPJ%2B3Sf4Q%2BeKKn0jtHxiLCdPaB6oh1b7QF9Ci6PeQpZ7k84veGJCck%2FHlzrJaDum1yDe178oxemOdGtDnwtUZwiYb6Py%2FLT8sBnuYVEVSuHDL%2BVaKSXcUVmadUkWK9bDOnUO0hItfutGn5SWWo63XEJHnVG28b1Z2qcPGCEzDSkLkcV1mUQon7IhMrLnUfureqNHzjqhcJPbAZA1Lo9l230uoDQlChR1C2vVyinUJcN1diZbcQpsJsVJWOV4xZb7n28Uy4s81GAy2tlUyUmWRr0qCtWobfLEjhP%2B6oxS57zEbjvMBkKyQq%2B3xxSWtXd8sWTUAL3MEuC%2FlfJAXgyszMp6NhgqUe0WjIPFNdNk5RzqrQ2NQ1cjFloMx7%2FANH9smL3NODQFa7aUmA2XUKGmj8Ks2tyVZ8cmccSTvjA%2ByKZMo8EoUe0ApUQOzUY1Kw2PNGy5nE0zVeG6uUh9tCW6PiyjhtZO7ynJeaJt3FIHxGNJzM45c6SQIRqGRU5tDdNV0y0tlMw5sVC9idjFCjESa3%2BnI8o6dwe3aMdM44ee8SlwmAybxhPsgp240KZ03894reyDQ5n5YxDWu8R6SAyhyqMnkReKBqAPIiMdKlA7KMTIeWO2AvzMjO1CZYUywtaUrC1EHkI9jslMSzza2kdIlBIWi4BV%2FveLVLTFSUlAkpgNG9r3EVVvVlLvSzVREwgKAUUq3IIgOu8S4cwhTeCukz2F2jUq7jBTlQnXmkuEsvJeLSpNtA2UpCEXcNjubjYRvzidUlHCynolakqaoYv5iGvyxzLwS19j3QKdR8S45Vh7C9FqMviNybdmeiTJFvWHktuK6rQfbu0tNjrBtztHTPFEuXd4ZJpyTa6OWXM0pTCPtWlOhSAPME2EfN9L7OznEsMqojLK1iMuWZmqmZnqjX58nZudUxd7amdecRPojXEQ4T584lIN4C5POJo%2BkS4yTlziYemCxvuIlRc8xARtvE0IlJN4CMTC0U4ngJrCFoE2gDeARJE8S2PdAQ0iAFom0%2BeGnzwAC43iA5xEiI91oBEyXSwDMJdW0Wuulba1IWgg%2BUFJ3SRzuNxaJRy39B9MTNnQu8B9AcVZT4klqtkXmRQcbs5l40wjS3m5uTTVGGqhiGnutrdExIKcOl1yXDyrahdaUJJuQYt%2BTGRtccz2puN8e4mr9GqFMw87L0OQxRU5FzELr60rZ8cabZOkSzIdKk67nVe%2B1o4qwTiurYAxlQsd4cUyirYdm0Tcg48jpEtlNxosT5BBUCkWG8ZDm5mfinOXGqsf4tZk5OoGVakmGqchTTcsyhJAS2okrGq5Kt97wFjx4isM42rspiDFpxTUZSozEq%2FWvGS%2BmfLaykPJWeaVAXA5C9uyMbWFX2iuUIR1EaU6bJSlKdhbsHdFIg9sB53oxuuH3lz0XjI3%2B7vEY3XPsTvmRAYvItyD4mETs4ZZQZUphXR60rdFrIVbkCL79htEsy1JNsyypCacfW7LhyYStrR0LupQKBudQsEnVtztbaPLE6IC6TMjRmni6xVnXWlySXWj4vZYmbC7KxfYA6hr3BFj27W1SVFBUEmybXNuUR0oOw5%2BYx7qdW56mStQp8rMJMtU2BLzbK2wpLiQoKTz3BCgCCLGAt5QpKNRSQUi9jF2q0hh%2BVmZtNMxA7PS4YacknFShbLrh0623Ek%2B9lN177g6R33jzVKr1CsOtTFTmVTDrEu1KNrUACGmk6W07AX0pAF%2BffHkgPdJytMfpVQefqSpeoy5aVJy6mromkk2cGu%2FUUnYi4soX7RvLPM0uVny3Izz03I6kHpiz0bhSQNfUJ5g3A3sbX7Y8moclbX74jAe6p0%2BiSsxPokq45OttOpEg4JYtiZaN9Slgm7SgNPVsbknfaLapAtqAVY8iREVKSDuoCPY3Vp5FIeoiXUqkn30TRbUgHS6lJSFpPMHSSDvYjmNhAeKUbllTjDc6%2BtmWW6hLzqG9am2ybKUE%2FCIFzbttCcZYYm3mpWY8YYQ4oNO6dPSIubK0ncXFjY8rweUXXFLUsFa%2B4RKkXGntEB61y1KVQm51qpr9kUzK2npNbRA6KwKHUL5HcqBTsRYHcHbxQ7bQgJYmiWJoCvT3peXnEPTjTrjKb3DSglYNtiCdtjaPR7JJ9jJinL6RwzDyHrqWNKSm%2B%2FfqINrxboQFXXePW1OzJp%2FsWp1SpVL3jDbZ36NdrEjuuOY8wjwxVZ5KgN68KSL4vrSzayaYLg8iNfKPfSalPUbh6q8%2FQqpP02cOKKK05MSkythwlcrNlxAUgg6SLAjkbco83COjVizEA06r0m3o6xN%2FkjzylVMrw51yfV10tY2ovV7DaTmwR5u%2BAxpOYOOm%2FJx%2FiI2O%2F56vK38%2FWiVWZeYo3bzBxARe3XqK1fjvGHyOLVU%2BWp7Lck0tUhUDNgnm9fV1D5t4kRitfRNS6pRromquqq6COd%2FwBLNvgwGyJTOnNGWl0S6sazrqUXGp97UVG%2Fabbx6Xc880UsrQjGr7QWkoJQpNwDzG4jVTuKnltTCEss3cqfsiPSbe9j9ztyiaZxY%2FMmeUuXl0CcnGptSQjYFB3SnuBtAbhwFnji2m48w5UccY7r03h2VqjC6vLshp5bkok9dKWykBRsdkn5osk1nNmk2%2B%2B2xmPWnGelXo6QtE6NR0agUGx02uO%2BNbTuJ1TkvV0Klm2%2FZF1p4W5tlJHk%2BmIT2K3p56qOKlZdHsg235N%2BoUgC6fOe2Az9%2FOvNhXWGYlWUbclKZ2%2FkbR45vP3OslLDeYVZU22kFv7Hbz2siMIexEp8ToUygeMyqGgQPI07gjzm0VPbXM%2BN%2BNdE3fxZLFuzbe%2FpgMsXn7nKG1BWYNaKVEKPXQPX5Me%2BjZ05sTU%2Bwy%2FmDWlI1adPTJHYb7aYw5%2BtuT1EnmXQ2lTYbCCNyoFQHOK0pVyirNI6FPld4%2B1MB1RwhYmxDifFbE%2FiKsTdTeRXaZKNuTKgpSGwxMuWBsLC%2FwCOL1xvJPtwwwdVx7FPqG3L80EW%2FL64xTgjcEzV5J7SlKk4ykU6yfK%2FMU0rT5xYcoyjjeKjjrDSSSLUVZA77zCjAc6IKUzCCRca0i3f1hHc7KAtBbfW2pVkAKt3Adg587RwqBqeaSRcF1AI7xqF47aaZSFpaQSiyBYpvcEJ2BPyRksddpPoYr1qs6Y%2FrkZFKONOIflXXpZtpuYam3CobEMONrCEfu1AqHqjqp%2FK6gTrSphgvNqdST0jfLSrfly5RyzhRMu6t6nzCEkTSFNlahYb7H4%2BUdZZd1J17B0jKTAWmZprfsfMoUblK29hv2gpsQe0GNiqmOFEtSmvKmYj0uauJnDmZOUtMaxTltiqqyya1pp1QXIMtmZAbuprSspUtHb5Nr73jj9M1i%2BsV52u4xm8SVJ%2BXSnxmeqDrr7suxfZRK76Wwo7gWEfXFbrD46J5ttQ1X0qSCLjt37Ys%2BKcAYFx5LysvivDkrN%2BJr6Rh1pIZdRfyk6kAakKGykKukjmI26LeujKKcsmrVY2dUTVP53s9D5nTmKKpjWep%2BT8rien0Cm1gMS8zNvLvLLmVKu044dw2gK0qKhGKUXEE3khj2Uq8t0OIsQYXqwfaHSpTTlvsLISoOJBLzSiAtKk2uI2hl5kjWZDiao9BbpUm%2BzhnFKJqeRZLcgumB8uKAKzp0BpWnQSbWKe6MFzlwrL0rNfGzdOTLuUmXxJOy8iuXsGhLlZU0lAHwQghItt1Yz29dcWlcTOfBiI82vNisLCiqimNnCzq9OWTUeIi7U5%2Bp12ZZl2X6pPTE%2B81LtlDLbjzhcUltJJISFKNgSbC0TYBknjQPGgbB591Q9F7fkj2YnlnHUM0%2BTbWp%2BYV0aEp53PMiMikKT7E0qWkEJA8XQE37D3n445tUzXOcurRlTGTxVJHRyD%2FwBt0JjFSwTpt2xl1QbPicwF%2BSGlJH5IxpgdI5y%2F3MVWanqY%2FPeoD%2F6hf4zF0xKgory2%2B5tr%2BYIt1Wt7NVMd0wv%2BdF%2Bxq2W8ZTjShYpSyD97TGvM62bkZZguVQ%2B%2BjU3ezR%2FEYkqqByi7ZcAJnEhWmxlnL6uXkGLbW0aHLRVZitTTds7RYHE2EZJPgFJiwPpsq0BbiIlj1rbigpvfaApwHOJw35omCBASRAm0TKFjEyW7wEkemUf6NYCvUYp9Cq%2B0TJQU7wHT2MuNet424c6Bw8zeBKbIs0FFOS1V5aecU46JQkpJaKdIKr72Vsfk0GxXJtuabmmpt5mYacS8082spW24kgpWk9igQCD3iMf6QgxP0sB3phzwn9ddw7K07NTJjDuMarJFJTUS6lkPuBIBeUy42tLbirdYoIBN9hyjUOd3GdmZnPiyg4n6ZGGU4Umkz9ClaYo2kppJBD5WrdxewSbi2kkWsY5rD6hayj8cTeML%2B2MB9BKN4VWsCkyqcXZHUKp1qUSdM7KT%2FQtFw%2BU4ltxClMlXaErI88cw8QHEtjXiCxgnFOLES0oiVaErI0%2BVv0MmwCToTfckqOpSjuTblYCNM9Oq3lGJOkJ7YDpud40Z%2Be4W6fwwv4EkG5WRbYYTWW55ZdWhqYLybslGkEk2NlWjmaaVdfOKXSRKteo374Cm5FOKi%2BUSWMBCEIiOcBOlO0RSneCDtaJkmxgL1hFOrEVJT31OSH%2BfRHU3hOjfitriftKTTE%2F%2BmRHMGB06sVUNPfVpIf8AqER054TFXScWWJ0%2FqdPpnxGWRAchOiy4kJid03X6Ik0kmAhCJwiBRaAkhAi0ICZI3isk2ikOcTg2gL%2FhOvTGG69TMQyjLTr1LnGJ1tt2%2BhxTSwsJVbcAlNiRvvG6uKHionuJzFlLxXO4NlsNu0ym%2BxxYl51Uyl330uFepSUkbki1o58aWQIrIUbQGwcqs18W5P46pWYeCJxqXq9JcWpAfQVsTDa0lLjDyQRqbWklJF78iNwI6xe8I5gKaqIxvN8KGGVY7CBetKm0LJcSnSFlZb6Q7bXPWtteOD%2BmKYeMGA6KoXGNmtQs9pziAQ%2FJzlaqTapOfp7yVJkpmRIAEtZJ1ICNKVIUCSlQvvciN5zfhLsJyZncQ4N4a6PR8XVNoJmas9MsrK1nmXFNtpW6PTa%2FbHAgmFdpiYTR7YDqDI7jMquUeNMcZgVrAchi6tY4caVMzkzPLlXZYJUpS0J0pUClV07bW0jnGbYt4%2FsG4opdYkqlwl4BmJisyrks%2FOzLqHnyVIKQsrUzqJTcEHUDcDcRxX0%2Bruh0vmEBWffS88XEIKE%2FBTz2G28eiXspMeEKubiPSw5ogMwp6tNLT5yY8mGpZU3jeSlkp1FYdAHeeiXHpp29LR649WXEr43mrRJfeynXdx2WZcP5IDF5YBTSVd6R%2BKM4ygwcxmHmjhHAs48%2BzKV6tyNMmXmQCtpp59DalJvtcBRIv2xh8nJuTTigkIQyynUty%2FVQPPGwuGqtJneJXK6Sp3UkUYxo2%2FJUwoTjXWPm7hAfePL3L7COV2EafgfA9HZplIpjYbZZbG6j8Ja1c1LUdyo7kxkcIQCEIQCEIQCEIQCEIQHwD46bDifzIA2%2FsinTc8tlCOeZokhoHkGkAR0Hx1f%2FABP5k73%2FALIp%2FwBXWEc%2BTHktfvW4DP6J9hV%2B9RG%2FOGtJWutJRkgrMAIn5Bx5aZeUdLKAl20n%2BaDZIeKgslHXPQ9140PRrCTGyb2Rc9sbPy%2BqueeA6W%2FiXANAqqKVNOt1FUyui%2BMy5cZStKJhClJISUpWtIWDyUqA6pVMSDJI%2Bt8zJ1G50yNPV%2BKNWZ%2FdCnA9ULHC8vAqXvY1IqCpKRaFOJfUel1tXdPTj3qxAR1dt4wM8WvEAtCULzDQjULjo5FgX%2BSI1TEPEZnVQH1TlJrOIaZUVMMPzcjQU%2FmjxVZW0yp9tOoobWpSgi9go3gNjZcLaZ4GsfzLirJRilK1K7E2XLi%2FxGNIJxBSdavzajyj2xuPATi18BmZ7YTdxrEQQlHbqDstcHz845lMnOBarSb%2FAJR%2FSzAdi8D1UkJzHWM2ZaabWs4aSvSDvYPEX9G4jjZwhS1qTyK12%2B6MdPcATc2zmli0uSziELwmsFSkkDaYRYfKY5jf5uH%2FALZz%2BeYCVHOO3uH8X4Q3AFXvK4h59nUc2jh9BjuHIFV%2BER0faSuIU%2FEhyPm3wnRM4fd4jysfy1OrhNM1Wlf8MuU8pf8AkLxj%2FwCe0v8A%2B3MSSDRU6E%2FCNx%2FJMMrF6cjcVp%2B2r9L%2FAPtjHtoMoqbqktItVGmy03NlXirU5MdGZhSRulAsSoi8fRrPY5c7WlMXdGp2TdZbQkOSLalhCbDXc%2FNzjEHRZRA7436vKKjP9A3PYskHlMIDHvdSaCbJvzuL33jzKyYwo9NSqX5qdEvNPJQZmXWh4aNYSpSQLarAkgdtrRdDQ0IyrGVApFHqb0tRXnXpRpS0tuvJ0rdSHFJSsp%2BASkAlNzY3FzGLrbPZAUiqJkKiUoiZCYD1tOEiK179sRocvKTdYp8nPl%2FxZ%2Baaae6C3SaFLAVpvtq03tfa%2FON4VrK%2FLP2dnvYCn4iapCZhzxJuem2VzCWdR6PpVIASV6bXttflAaHmSrQux%2BCfxR1LJaQmXe1DQqVTdVrG3Qi0YSMqsFqtdqpBN%2BsC4jcdvZGb9MwgFwuMy8sy2Qtby%2Bo20E2uo9yRzPmgOf8AEX6FpZ06byZPputW8YisWcUI6RfyjwG9LyqJvH1HV0MqhCPzWrrNnrJXcN7gg3EeR3I7AvRJdl8TU2oHUgqak58qfCCRqVoUgAhINzvAc8RKrnGYYuolIpc6uXpYcU2gK6yzuuyykHzXABtGIrBvygKR2idtyxiUgk8omQ3Aext28VNRMVMNSspPYipUjUEvKk5idYamEMqCXFNKcAWEE7BWkmxO143nUspsAJqU6qnSFQap7jrhk2n5kOOtN6joC1pAClBOnUQAL3tAaHFy80f3aR8ojqCYb0KmVfbNLP8AmzGKyGVGBWzqmpGbeUlQUjTMaBt2HY%2FJGX1GZlZWXmJidfSxKNtLQ84dw22U6SfUDAc84l%2FQkg30enVIMufGDGJx0TN5YYLeblUTWKVuKTJMhnUw8gLZ09RW7e9xCn5KYLmn2UNThmEh1szIaSoLDAWOk0a0gFejUUi%2B5AB2gOd9J5xIfPGYYyotHptTmmqMHfEw%2B4JdT4AWWgshGoDYK02uBsCTbaMRWDeAkJAio27aKRF4ilJMB7mnSRFXVfti4YDptNq2M6FTKyzMPU%2BZqDDc41LuBt1xjWOkShRBCVFNwCQQCQY3hV8j8EipzUzT5WdlpR99xcrLuzHSuMMlai22pYAC1JTpBVYXIvYQHPssnXPS%2B%2F8AdDf84R1bOMt%2ByNSUU7dDOEW5mzCyLRhstk7gth1Ew8xNudGoKCQ6U7g99oy%2BfnWJdtybnZpiVkktLbfedBIaQtJQo2AJJsrsF4DnrG60TD8rMeTqkJX%2FAEQjDtBjpZ%2FJ7AzzDDc3jUOfmdJbS5JTLZcaA6igejtuImo2QmAqjNMiVqvjjRUStKGnm1LSgp6RKFOICSpKTe1%2FVAcy2iRZtGWY4o0jSqzNStKbWmXbWpKNRuQATsT2%2BeMTWLmAghW8elD1hHl0xG5EB70PE9sRKzbePfgOnyNXxpQ6XVmHHpKZnmW5hptehbjRUNSUq30ki4CrGxIMbsmsscv%2FAByYbRSX22S6ospExqUhvUbAqI6xtbewvAaNoAvXJAf%2FAFTZ%2BWOj6i3eoujTpsv8QG0Y63llgmXmGZlmVfJYdSsBT5BUAeRIG1%2B8Rkjy1POrddF1OOE7bgeb0DYeqA9mbyT9THhVRR%2F03cSD3gSSjb4yfjjqvgr6NPDRStPNcnUVn8LVeOXc4Ej6lvDJtbTj5Y5f93qvHUPBS4tXDVTUq%2BBJVRI9HjKz%2BWPmHwlTwrrYT4LWn%2BWt28Jj870e%2BHBSPL9Ljv8APVHSXAgArN2uE%2FBw84R63kRzajmn985%2FPMdJcCNzm7W0jl7XHifU6mPQacx%2F6%2Fb%2Bin2w1sP%2FAEun0vVjdvXxkYxcv9iy71bdnvLO%2FqjScs2AwmN2YyB%2BrAzFWnUCcvQLns1MMCw828adpUoZ1xLKpqVlEXCS%2FNOhtpJJsLqO25ja0O1YHdY%2Fcp9kNe%2BT%2BOqYTmq5%2BeeJWPgqrDKfUGAR%2BMxp2YbjpzEmVLlZxLWJ%2BoV%2Bks%2BPTaX1SKaigpbWlAABJF%2BQJ9cW17JOltoU901MnECwWZWYS6UX5XANwDyj1DWzc3xFxITpKTckXMbhzbwDhnB0wKfRHRNqEvJOvPFgtFp55jpHWLEnUEHYLGyr3jTrl4LJdRhqMSWWeRMNK%2FPFFFQGJ%2BYilHTcxkrgR6hYcqVKkZtoVCh06ZmvGVIWVTa2dT62tO4ZKiNAV1tjfsgOZygnnHUOD5fpMAYTf%2BEunhtPqeVb1Wi1O5M4YAIS05faxCQfTGdUSkP06kU6hyiHHxIAS8sgJF1FS9hblzMBpnNXpPH8QS%2FwEYjmU%2FE1Go1t2jq%2Bp5IYaxHP1KszGdmEmUzs%2B5OuypniSy8TpcT5G5FrWBiVHDXgqYQkS%2BbeBJlxRCUNJnF6lrUbJSDptcmw3I5wHJ%2BiKS9o3Fm9l7SsCz0zQ2G0rmJRxtLzgRpOpTKVKTa5tYkj1RqBxuAphUTBXdEoTaJtO0AuInimlMdRTeRuCnkyszRpV5iVmJSVWETaUrdS8plJe3TtoLhVoBuQm1zeA5iT2%2BgmOnqIhC6BRVE6lCQa6U9x1WHyRa3MlMNpQrUhP3u35Yzmn0ZbFNlaXLN6zJNNoBIAuq3LzCA0jmq2tybn5e%2FWl61UGVeYpWkWjV5YjoSuYAotdqM1XGce0BEtUZp6oIlTOKUW1ukFaQdH2yT2xRYygoM66iXpuI8NOzb6g1LsGcVqddOyU3KQBc2Fz3wWc%2BlpXdA7RtfPDBVCwTiM0Oglx5mSYaL7rzfRu%2BMLZaW62pIJFkOKWlJB6yQCbE2jVSwTyEEqWqxiYLAiBREpBEFFXXftiBRfmYmlEa5hpvq%2BUPLvbn227I6nrPD9g6beTOUNh2SkHJeWebl6ghKplKlMIL2pTfV0l3WUDmEFOreA5YaQVOpT3rSPlEddUSWJplImVk6ZltpYVe5t0mm%2F44xN3IOnNEqbmWUFvtDR9UbMpNMcpshIyEspbi5FttKFOWBWpJ1XPYAST6oDm7NhHSVKY%2Fcz8%2BlPo8ZVGt9EdJT%2BV%2BG67NPzk1mdhu78y%2FMhnxhSujLrilqQDosQCSPVEsvkThOYmWJGVxphyZm5xxLEsymZUFPOq8lAJSACfOYDnEtmxiidjGz868F0rA%2BKpjD1HeceakwlJeWkIUslKSSUjYG5I2PIAxrHozzgGuGsxKRbaEBFSrxGLjhuTZnK7JS8yyl5txyym1KKQrY2BI3te0b3ncmcHIeQulF16VcZZWjxhAS6lRaSpwKCTbZZUE96Qkne8BovDA%2FsjpZ7pxo%2FyhHSMmR7DSDurV0jF%2FR1jGMM5WUOSmmpyUCWnmVBxpYQTZSTsbExlLzctKy8tKSqV6WWw3ddrqt27bcyYDIK24F8LubyejB0GipCu0XqDZ%2FJGd%2BDRLfR44Ac9%2BM9TOr3JCH7H7o2jXta%2FwDhczXXf9PoibemeRGwfBotWONZm24nqY1fzEPG3x7x4j4QI4WCWkeej%2Bel1cJ%2BXiWt%2BJ%2Byc%2BsbI%2F7ySr42W48vDwAc88BBSrD2caPK9zoXYfHaPTxRG%2Bf2M%2BuVfngnstb3pvaPNw8hK89MAIN7KrzA2%2Feqi81TxSpmfIf%2FAM2Kw%2FS4nzx7W8fCHqUhOVYQoavbWspHnCZf%2FVGrc80qTnBiVCgkFMyAQOQO5%2FLGzvCFkCp5TJsCTidZtfnvL9ka0zxC3M3cSqPlrnP9UU%2BDyn8hWfpq%2FmlXEYyvNfp9zW%2BY0u25gKVUoAq6Z8puNxu3yjQb8vHT9ewU9iGhStMXijDLCGHXXFEVIdIsLCOooabApKOzvMYmrIumqBSjEVNfdPktsVBC1uHuAta%2Frj28tLNoYNEdsUnCQuN24uynwxh3AE1iIVOdNZangwzJ9ADLrli2VKcLt7hwLCRotYpJNwRGknAdfKCFZh4gx6w%2BSOcWsa0m8TB5Y7YC5iYtzMed1es3jy9OvvjcmV%2BW%2BDcZZfztUqDdVTXGax0LLyZhsSSpMS5Km1N21l3pLKCgdOkEHeA024FXNo3FkWpQoWIEXFvGGDawudrc4uj%2BTOFUcg%2F93GQYXwxTcJSE7IyLCiZxxtanFL2CUg7W7723gLPmirpKJKp63vknNcvO%2Bj8oMaJ6MnaOrZzA2H8YU6Vbr%2BNaNh4MpeCEzRdU6604sbhLaFBKQpNrm199os1P4f8AKt2Y6FWb2H1OOdUJCZsqJ9TP4oDmpSNo852O0b4zJytwJhbCy6hSKyqqzTjv5lm5NRVJPM9HckFQSvWF3SQQLWjRMB6mXrAAGPWmZ6tri8WdRUk7KiW7nPXAXgzG%2FMR4plalqvePLqc%2FVI3fljl%2FgvFOXqJ%2BpUh9VWM%2B6FTgmLtqlghIS10VtlhYUrXfcbW7YDSPLnG8clUNnDqukKQoiyL8zd43%2BQCLj7kmCtGoSri%2Bt2qtF4otCpmHZFynU6QTd1SVF4rJUixvpSOVrkwGO5vlfsE0xdOnoOr6enJMaUKCOcdM1nCVFxNTW2azVjIqkUKW70dOmH7NuudQurbSUo66SEg77mLAzkvgl9aWJbEbr7yzZKGKTOOqJ8yQm5gNCKSdMUW1lK%2B3443dmNlzgvCuAZCZpa35iszU4qYTPtTAVJTVOW0nowlsgLbeS4HNWrYggbERpNbdt4D0ImSntip4554tqypMSBxfaYC5OzStOxMeUlaopHpFDa8dCYNwHgDEWXVIW9hYNVlqZdVNVFEyq04wppAbZU1yQpCtSisG6r25QHPpaUe%2BOgMo0tu4OSrfS222m57D75tFf3JsGpvop61fbWcItF8pNIl8PSJp9Nl0ttFYWpRJKlAJISg9lhcnvuYDFM67e16nNhzV7y33fqixt8UaRU0AbWjpur4ZwvielygxLWZyWXKjxZKZakuvp0lRcAW4khOrdVrchcRa5fKPK97rs1yrPFsFxz84ZhVkJFz1Qfl7IDnV1tWm8UW3LGN25yZf4NwjhShzeHD4zNT0xOKdnUuK0TMt70pizZHvSkArSoXN7jlaNIuNkE6RaA9iJiw5xEzF%2B2LerpB2wSXD2wHpeeKto8x3vESF9sdEYWy7wDVsHUuYmqChFQa6VL8yl9ZM0F6CjUg9VBbsoAp5hW%2FIQHOZQTzjpHLicWmguypspLjEkkG5NtDf%2B4iZOVuAnho9i3lK%2B1LlhF9pdHpFFkRL02UWjSbOqUsknsHq2gNlcOy1e6vJMOIuFSM46e%2B6ZdY2jXfg7SyM16mHEXX7WX%2BjPd763f5I2Vw8oadzSkl9IsPMyM%2F1EjygZdYMa58HwA3nFMoSkEOYYeUrzDW3HlNNYzwO8fwulhn6TSzrjtAGfBIIN8PyHpHXdjnVHbeOiOPABOfZFueH6eb2%2FdOxzwOe8bein6lu38Pvlq3r5er0pXxeRmR%2F2Sx8kd954laeFuetpLjuAUMpChzUoS6QB5%2BttHAcyU%2BKTKVKsno1G47rR3vn2lxXCtMtob1uPYPk5ZtFr6nHFyqUj448xpzOWIXH01e2hvXHPua2y83vcE8SMhP07M1qnTYAmJXD9DZmQP1VEihK%2FlTGrap%2Bg%2FufxxuXiR6NeakwuZGlbdHo6LHstKI%2FLeNSVdDTkslts%2FCEfQbD5GiPNHsc21nOufTLHSFKOqJSLRdJeVbDzPjCdTXTNhwd6NYBHxRWqMtSWpOpLl0OqdRUdMoq%2FVEuOk2P7q4T6rxlY1lse4xPF%2BqVPosvM1luVS6WmmmVSZWryFKWjVq79iq0TCRoiS4fzQkIoiX0p1C%2FjehJJN%2Fg3KokY%2FCMglJCjqm6Wh9D3Rrk1qmutzeHS6Sk92ze3p74kp8lSnE0IzLbylTM08md0qFlNhaAnSOw2KoCxt3Cx%2B%2BEZXJpWmRmEt6ukLCw0QPhW2jGej98%2FhFXqBi8y8y6lslJcICbgi4AFriA2rmlIPSdAyrbfS2lTmX8k8NBv1VTk2Rfz2I%2BSNPV0lDibdt43LnTPh%2BlZUJbZW2Gct6Y0SoEalCYmbkX9IjTNU9%2BcRfzxQWobwi6yElJjxkzwWUiTfWzo5h0JugnzX5x7ZKRork3QRNpfKH23TPhP2wW5p0%2BawTf0GAsESkDsi8yErTX2KSH0uF16fWicKeRYBbsE9x6yvkiR6Tphkpl1pDnTpqfRNm9h0GlRI9Owi4tEQIvuIv9Sp9IaNe8XS8DLPoTTzruCguKBC%2B86besRCbkqGmZqSGPGEstyKFy2o9YPkNFV%2B9PWXb1QFqpdjNttrvYmMsqcu%2BGJJbWsATSEOaL7A3Fz67Ri0q2ph9LqOaFRfBU55ehLy1kFxJANhc9hgNsYnkJuS4ZsKuzBAbmcwa%2BWbp6y0pkpUage6%2B3pjQ84TrO8b%2BxtOqmuF%2FLIKaPXxTiR4ub2JKJcW7uz5Y0O%2BxrUTeA8Bv2xCLouVk0Up19WszSJhtKBfqFsoUVX8%2BoJt6THrqVOo7LlfTLqmEmVLapEG3IuAKC%2FQk7QFghGQLp9F8YfQFuhtNKbfaJPKZKEEg%2FublXyRTap1GLlP8AGFTAbmKa%2B68pJTcTCel02H2vVRtzsTAWOJRF%2FkKfRn%2FYQTPTIE0%2B4mdKSLhAWkJ0X7bE8%2FNHhcYkfYhLzanfHPG1ottp6EIBH8K94CtQEqXMrseSfyxdmmlzVc8UW4sI6C4HebxY6ct6XdU42TuI9CKi%2BJ5MwlwhxKQB8fKA2q3TX5Lh9x06tnSyvGlAbbcINlKTKTpUlJ5XGtJI84jSrlzG%2BUzyp3hQxNNE2EzmHTAW7nqqRT3QpXrMaO8Wc7oDxxNF5ZkaR43INvdOlt2UcW%2BUnfpgHLWv2bI%2BWIyclR1%2BwS3w4C%2FMLTP2PwAtNin1EwFliBF9xF3l5GmGnS00%2Bp7pjUCw8lPIsaUnbz31fGITklTW5aruyqnSqXnUtypUbXZJc3UO%2FqpgLPEtzGQTtPo4fqyJQPhLTbfimog9fUgLCtu4qtHgqcpKNOt%2BI9Jo6Bkr1nfpFIBX6tV7ea0BPJrc6C6TuSSbdsSMLmCs6iSnVexirJocVLpQlNiFEbRVQpMq6hei5QsKIPbAbIwlQ6p7jmYVbLQTJzMnIS7JUoe%2Bqbnm1OWHckdvp88d9cUzaGuGV1IAA6SiJHdslEcI4bmlTHDvjRp1y6ZByTZbAvdJcnQvT6CPxx3pxahCeG5XRC6fGKMfVpRfaPl%2Bl8Z47hcR5Sr%2Baxdy6ZRdbafNT%2FycDgRKoEcomTEyhH1CXDUd%2FPCx7onhAQHKJYniSAmHKJ4kGwieAgqCecFQTzgJucNJgnnFVKYCS3k%2Be%2FqiGkWiupCNIJJ22O%2B94goJSyHnFoQ3puF3uD57wHnI7IAbRVKBfb0xTUbG14CU3idIvEsVUCAtVZqi6a8httYSgjVeJaLi5yam1SU690suUda4F0WNgr0xcqrIylZkEyEwhPSNqLjDvItX8oedJsNuwiPbgmcm8DyGJKbSm6VMMYqpZpM85NyKX32mSsKK5dxX2Fza2sA7efeApufwbfBUO2KKwe6K7i%2BkiQ6bdfqjv5wHieHVPVvGNV1PvLm%2FwFRk0x5HOMcrw%2FM7htfqKgMHj3UmUYmpkmdf6GVZSXX3ALkIHYPOdgPOY8bce6XlZmak5tEqwt0MoS%2B8Ei%2BltKhdSv3IJFz2bQF5bxnVJQhGEpFmlyrd0IUiXS88sfu3FpNz6LR5q9VavVkSr9dk2Q8kLSmYRKIZU8Odl6AAq3YbXEeykUer4gwyulUKcDzspOOTcxTumSgkaQlMwgHyxbqkA7d294tVYolUobjDNUbbSt4EpSH0uFPffSTp9cB6X8XTM1ILpb9MpPQLQlF0SCEuoKeSkrG9%2FP2xTpNYk6NLCYTTJeeqK72M23rZZR%2B85LUfPsIszZ98Hr%2FFGY4cp8lXcOqptQpL7RZmtUpWZdsuFlRHXZfQN1t8iFDdBJ5g7BTGJcX1GmpXUmpGYpj3SsIU7IMhpKtPWCSlIKVAcjeLNSJalNsLqVaLi5RnZDCFaVzDp5Iv8FI5qPdHpYq8%2Fhp%2BZpbMxLVGnuLtMyurXLTI709qT3KFiDHgqUk6llUxLsvGTbmFMoUoXCVEBQSo%2FbEfHaAvgxzW0ttytNo1GkWSAUMopjbhWOabqcBKz577xb3dddqqHJtmVp2tsOTKmWejQ2hI6y9APOw5DmT2RcVYfrmI5WnTdKnEVJpqVblQlb6Urkyi92lBRFkgklJ5WMWmYpdUlZl6RUEvOpYUtYl3A6FNJ6yrFN7gWufRAXRGLJ2lptg%2BhS0lLlPVmJiVS%2FMODlrK1gpTfuA288V5irJrL4omOaVLyM44lJYqUvKiVdZWsAoU6lICXGjtvYEA3BPKPLQJWo1zDz9Bp1VutudE37GreS2h1IQQHUEkAqTuCL8jePHiX2RdVJ0ycqBnn5JgMJQhfSCXQVkhpKhzAKibDYajaAskxLTElNvSc2nS8wtTbgveygbfFtEsV6mp12ccW%2BT0wsly%2FwBsAB%2BSPNAImiWEBdaPhus11SE02UDgccDSVKcSgFZ5JBJ5mKErSZycmHJVpizjRIWFqCNJBsb3tbeL7LSbLNPo7FWwvMTPS%2B%2Fyk1JLsp9tSt0r84IO43EWepyryZ%2Bd8XafcZbmFJBcGtabnYKI7YCNVoFUorMrM1GXShqdC%2BgWhxKwooICgbHYi4594jwNmKsxLTkuw307bjbayVISq4HcSB%2BWPOiA6D4RU%2F2UYiV2ClpB9HWvFmZZUvhirbNiSvHFIT%2F6Oa3%2BWL%2FwgIJr2LFDmmkot8ao8dPmG5PhhmaglGpQx3TrBRsCUSUze%2FqMBoTxJ0t6wDu5pTt5USeKvFJWEqsFaL6dtXd6YyWUrnijUi0202VSMy5MMrP2yhuD3iJfZYsNtsNoSlLU57IJT9q52j0X7IDHDKP9yvK0cvhd3pgqRmEgqUhQSlQQTbkT2emMiXWC4HNSG7vTyZ%2Fq%2FqoHZ5ohNVpTpmveUpM4%2Bmac08g4LEWHdcX9cBjjkupHSpKT1CAYj4o4gqSpKgW%2FKBT5Ppi%2FzFWVNCoLKUpNSU2pxKR5JQbix89opTk%2BZt%2BcddQlJnkhLgCjYFI2tAWVcu4gr1A3QBqHcDyiTojysfJBi%2BPVFTzkw4pNzMS6GVfweRiRFdDE30%2FiSFL6IM%2BUOSeRt3wFGXH53ToIN9DZH3QH5YryrZXVW0pG5cNvuIlncQKnpNcv4ro6QJ6wI2AIPIeiPXTamXJ9tQYa0rXc%2BpJHOA6f4HE6p6TT1b%2B3GRVuewU%2BZ5fJGU8ba%2F8AhDw%2ByCCE0dxZ7wTML%2FIIsnA10jk4x1ElDWL5RzzgmnTO%2Fo3i78byv%2BEihDvol%2F8APrgOeGP0ZLjsL6AfMCsXMduMOPSEwlkpbdb0pKXLEKBHb%2FqjiWSBVPyoFrl9sC%2FK%2BsR224S8klSEo0Cy0pNxcDv9UZbD5SfQxXjXZwuEnPql3UdAnUVXICN9PabmNt5YZlNUYolZhLjjallDyFLvqb7LfukHkTzG0aXlVMy6S4lxVykgA%2BbfeAm1Je6Rp7SVHY957o3fS5su2ZWpSVQlkzkhMJeaXuFJP44riYWpISi49EcnYWx9XKClLcpOuoUl3UpAPVcH2pvtaMvTxIzFOFqvQQtSdrsPDl32MZaYpmNqJrmJyiM2%2FVyci80pmapss8herWFsIOu%2FO%2B294%2BePEJgT2m45rdOYl%2Bjk2VomZQJ7WHPJA845eqOhK3xUqTJuv0SgoDibdEqbdITz3uB%2BKNE47xvWMdVNVZxG8y%2FNOI6JPRtBIba7EDzDzxmimizonOdvgRTaWldpE8HVG3NpqhUZtpa63Nt%2FmtxOmTQrbokfb%2BdR5RVm9HRrQ436NPfF%2Bn2PfOk6RKv3PcBytFhfccXqbWUq1RoS3onNZKppNOmgFX0pJG1iDcbfjjHpJrrpv9sIy6rEuUx7pW0p6p06duUYvLtrOnT3iKVbWWnXDTVZTpr1WHdNOD%2BVGTZi290aq6fJ1s6fvSIs9ek%2BjrlWcdXLhLj6136S17m%2Fxxc8Wl6axpPPLT1lLbN77HqJ3Eas7WXbDYuV7CHKgttZsEyT5uewhs2%2BW0WWudZ0emMqyll3U1QhCNanZN5ABFxcoNox%2FEjDjboLzZSruAiEsRnE3HkiLRMMEnkIv7zSV%2BSq%2FqigunuK3CR8UBjy5ckbCKBZWk8jGS%2Bx7g2U38kQXTL%2FAKWfigMa6M9oiUptyjInqOdNwgj1RZZtgsKI7RAeQpBVFaXStLg0xTQCTeLzh%2BlTVWqDElJS65iZfdS0yygXU64TZKAO0kkAemA2bkHwz5i8RNZnqLgRqnNGlywmp2cqL5YlmEqJDaSsAnUsg2AHYSbARr7HGBcTZe4oquDsW0h6m1iiTa5KelXbamnUnsI2UkiykqGykqBHOPp6mo0PwffDNSkzNKarOMq5NNTM9JhzQZybISp9Gob6GGjoT3rNu2MA8IFlTQc0Mv8ADnFplqfZGRep0rL1h5lO71McP5lnFgfDZWSw72gEX5QHzdWi24iS5EXGdlegdKSLb2i3uItASoO8VNJVFHlFRCyICk5PnVoYYTpTsCon1xWZfbfT1UhC0eWn8ojzOSi0OdGOv9qpPyfJHplpcMoK1KutexHcICO%2F%2B6Ybnt%2FkxU0xs%2FJXI2sZ0S%2BNn6NWqfT1YIwzMYnmETgXaaZZ2U02pIOlZ7CrbvgNWFvzRIRba0bIwjkXm1mFQJ7FGBst6%2FXKVS0lU5NSMqp1DNk6iNvKUE7kJubCNfvMEAKG4UNV7Wv80B5NG9483j5%2FS0J0%2Fuuce%2FQQQ2oWC%2BZ7o8k3TXWH7BJIULhadx8cB6W%2FzRLom0I0JVdPrHOIIFonYR0Eolj90VKT3GFj2CAyHAn%2FABsoP%2Fm8j%2F8AcNx0p4S2x4uMUHukaen%2FANK2fyxzfl%2BlRxfQNHlCsSBH4S3HRXhJV6uLfFY7peR%2F%2B1bgOT3EHUfPEvkILh%2BDFdzyok0a0Fv7aAkS866ApRTYdgFrxNueyJRLPJcCENLUPMLxXDW0BSDYPMRMGU90VQi0bIw1kniLFOT%2BK85KXPSApWDqlI0yflXXFJmXFzXkKaFtKgDa4JBtuL2gNZdHbtiXT5xGdHKDM1WB3MyW8A15eFWl9GusinuGTQQbXLgFgm%2B2rl54w1yWWhelSbH0QFHpG22%2BkWfJ7I8bddmW3AVNMLbJsUBNjbzHvj2Ot9Ijo%2BceNFMXrvoVvAXSYCG9C23elbcQFoI7j2HzxSid9OkNtnfQm1xyvFIkwFTpB3w6TzxSiI5wFZK7RPrudooDnFRIgPQ2TFdJPdFFoR6AkWvAZlTP7VNegxecpmk%2B6lSppZASwH3FE8gAyu%2FyRZaafzqa%2FemMhyobQ5j1oOLCUGVnNSj2ASzhJgMAn6miekV0%2BTcU3KtS9ysb9MvRcX7h3RmnCR%2F8SOV%2F%2FwC91G%2F%2B8ajXzkqGJc%2BLvlQ6EDyCbXTyNo2BwlahxI5XhQsr230a47j441AfodhCEAhCEAhCEAhCEAhCEB%2Bf7jpN%2BKLMpJJuMRTv84Rz68dRZuBbQ38d46B469uJ%2FMoi5%2Fshnd%2FPrEc%2BOW1skWPvSQR%2BWA2DSvsW32ifxx2hLZ04fycwBktiusVnHkxUpbAS3pDDFNWPYWqJS6%2B2BOBRsLrUb2B6oEcXUfyf4Ii8z1arNVl5CUqtWm5yXpMqmRp7T7hUiTlgpSgy0Pgo1KUbd5gOmMNYblcNz%2BUGXlH4faVjah5j06nVXENceYdXMzD82tRmWpR9B0yjcok2sftN49mI2ncM8PWGKNgjFeYfj1Kr2LJDDzuF1OGWnmUVBSNc%2Bps%2BQW0nSU3%2BFtHO1EzNzEwzh1%2FCWHcc1um0aYCwuRlZxbbVl%2BUEgHqg9um149WFM5c2cCUNrDWC8xa5RKUyVluUk5jQ2jXfVYEG17m%2FpMBvbKJlZ4JMdsyMm6847ixCQyyhS1qVrYuQBvsOcaxRRsR9b%2Bx%2BreUf7hd%2BaPRk9xL43yVw3MYWwpRaPOy03UHKm%2BueSsuF1baUGxBtbq3NxzMb%2FwArOL%2FMbGOCM08S1uk4fTNYHw61WKc1LoWEurU7oUHgTfTyNwRAeTg0plQksc4uRP0ydldWHAEKfYWgKPTcgVDc232ji18DW6n%2FALZz%2BeY6cmvCB5ulOhvCuE9YChrSh4jcEctXnv6o5g56v3xV8ZuYCSO4cg2w7whzSDyMtiK%2FxORxASI7k4YjL1PhraoiXQlb8xWJFwncIU5dP9MGPmvwoTFGGWFdWyLWP5K3VwifxtUeGmXJ%2BVzY9w%2Bup%2BG7Xaef31pbf4rxbC49J46w%2FPtOOMCVYmT4w2FamlEpAIKdwefKNq5bZKZ3ZdS1VoddydpuNqVNlnoWBiQSbbT7N09Mko3VqTYWNrWjL28H45SVW4MaUANwDjpZsbW9cejp0uwPL8G9Wc%2F76Y97DOG3vP5Kr7IajcqGGUkpcxXJ3O5HRuH%2BjHonqvJzZp7svOqmww2EBwoKQUpV1QL72tG004Txupdl8GVEHSb3dxq5b44oe1bHNtP1G1F37fbk7cHzb7RPHDBZ%2FarP%2FwCSnenvXe%2FJV9FzZUct53ElRaTKVGnS4mlr0CZdLYbutR65tZPpPmjWeIaD7DzaGEzAeS40lwK0lJBI3SR3gx3CrCOPXJdxlvg6oqXFIWlKxjdYUgqSRqso2Nr33vGr5zhlzImpjpJrImYdCEBCdWLWhYDtJCdzFZ0xwaP2mz%2F%2BSjtLU4Ve6vo6o9MS5WMuL%2BV8kVW5RKgpdj1UkgfbHujqVrhZxu6NRyBSj99jJIP82DvCpj0AJRkMxco16k4wSfVy5%2BaKcdMFjbeKP%2Fks%2B0mcIvcfMnmnc1kMlJOh4gl1S%2BYFKqbEq%2FLveMyLDy2VnQlxQSVJSeqolskgdZJtcbxn7zgdcUu466tUbZ9pWZCGktnhIwsopQhGr21vXNhYk9fmYq%2B0bMhXlcJmFB%2F%2FALa9%2BRcZI0wwaf2mz6dO9Heu8%2BSq5vvaiuO2PHihp2YwxVmGEFbi5J5KUDmrqHYRuhzBGaTnRkcKmExvbUrFby7j75tF1Tl9mEro2n%2BGnBBUu3LE0zt6SFRWdMsGjZeKJ9FdO9NOFXqrPOzqj7Pvack6pSXaTTnZ%2FFDEstEmy30L7bhU0AgAI5W27or%2BztGS0qSpddTUC4oKUhplaUelRUAB3eeNjzGAM0W5lxljhYwa82FWStOJn7EelTm%2FxCKQwPmwhehHCtg3SOdsTu79vMOw444Py3iz6dO9WcMvMfRVc33ucp7LGaxFPBaazTpMOuFsdMpQS2nUSCtVrAW%2FJGqq7RPYyf8AFUvFxPRpXqItzF47lRgXNdSVpTwrYPaDgUm%2Ftqd1AqBFwekNrXuL7XjXx4U8xakQZnJymFTSQ030uLwCUp2sLAb%2BcxMaY4N9Yo%2ByujetThN6qjPgVR6Yn73Jglh2i8VEyqTsU33AsnmY6ua4S8edIllWQ9LJUAdSsYiw9JG0JXhUx84FNjISkMOFJQlbuLjsfthva%2FdCdMsEj9po6dHaJwm9Rtpnmnc1ojJSi0bEEjMUvF4n5eTdZdL6JRxAcKdKjpSrcAk6d%2B1JPKM76UOazcJ59Xu3jbwwLm8ykSf1KeBHOhCWyo4kdXrskDXs7ve19u0mHtLzcWoD6kvAYSRZYRiRwfGeluImNMcFn9ps%2BnTvR3qvXkq%2Bi1GwodJzEWzGLTs7g2sS0uy4uYdlVpbaSkkqV3C0bvXg%2FN9pBU1wm4EUW0hQ04jeUTc2sPfdzF1RgPMvxKXXN8MOCxMPoCy2nEEwro9%2BSj0lgfNDjhg07LzZz%2Fvp3p703rb8VVzNPs1mjpkpE1OvLlnDLNAtrlXnSkhIuAUgiwj2UrEFEdfLVOmpmc0AuqJllNoT3XKrd8bHfwxnezMJZlOFfBLzKLpaIxE55Pdu6LH1RSFDzySkhXCjgdSAkpI9n17%2Bvpd4Tpfg8ftVl06d6ney9%2BRr6P3uZZ%2FKmo4grLbNQq9OpUq%2B84FzU0tQaYHWUFuFIJCTYC4B3IjUNao5ptSekQ6VhogBSha%2B147yNEzmMs7LnhIwT760por9sLuoBSSLi7pFxfbaNXDhczNn3%2BlfyFktW%2B8xiwG1uQvfeHHHBfrNn9lpRvO9d8mM4squZyeZbvidqVKiW0pBXewubAnujrZjhEzMUoKdyOoNu0O4oO%2FxGK54UMyUFKGch8OtKBFle2pRvvfa6opx0wWNt4o6dO9k7z3zLP4urma5kMmqdhTHTE3RMT%2By8hSptp2Xn%2FFFs%2BNAJSokNK6yLKKk789N%2B2No7T%2FNenrFXPvMbHVSuIFNul4YMstrCwqTlja29um80QFP4iwoKHDbloCOX55LsP8APRbjlgf1uy6cInCb35Krmje1x4qGbpCblXfvf0RZMdU6aewVV25GXLs04yOjZQnrLspJ29QMbqDPEgj%2FAPpxyz%2FjJfW9Hv0eqSYz%2FccT45w9ZepBSTdqfcI1Gx3982iKtM8DpjPuuz6cLRhF65bOrm%2B9pNWIsPJZaM9UayhaWUJLYprjgTYcgb8hHsomM6S%2FUZaTpDlUm22EvTCw%2B0ppCSpISLJJtckbnuja83K8RTK0hXDjlq%2BlQUklFRc1AE8ieljxFjP1N0jhXy9NxYkVV0Aj79e8RGmeCzsvVn06d6s4VeY%2Bjq5vvcyTeTlTxNWHXZitScky%2BXXFOupUUoA1qBOkE9gHLtEaarVINMqL0gTcskC9rXuAfyx9AOgz9XKvyZ4X8u2UPMOS5KKo4lQStJSdJ6U2Nu3nGpJjhdzQn5gvzOSdKWrqpBcxMomwFgL3hxzwWI13ij7K6N6Jwq8%2BTqj0w5LLAG3bFeXlA4ttJudS0psnzm0daDhJzJ%2F6jsO9U3P9lC9x3eXFSX4Us0mJhqZkMkMNsPMnUFLxMpQN%2FMV2%2BOK8d8D%2BsUdOjtHeu8%2BLPM1jScoqXhvFspVpTEipmVpswh9DniqkqcsPtCbp622%2FdeM0DnSOK1xuxWGs%2BNOp3hcy2ULAG1XcHK2%2Bz23KKKsP53J0oHCxlqQBsfZd3bzfZufyRPHPBp2Xiz6dO9Peq9cllXzfe04EMn4QiC2SDqB6npEbcmcI53P9ZHCll%2BFH7StO7%2Bf7NFeSwvnoy8HEcLmXqHB8JVYcKTbzF0iM0aY4Hl%2Bl2cT%2FAB071Zwq%2B8ljVzNW5xqCuFzDKUG4RjxSVWG1%2FY9R%2FEofHHUfBjMS7%2FDPTBLEnoJCpIdJ5lYmHCv0jcD1Rz5m1khxAZlv0alyeWmFsMyFHDivE6XV1Ll3XXCFdIsOLPXSBpuOwkR07w44BquUWS%2FtRxJNyj05LSM%2B%2FMLllFTSelKnCm5AvYXv2R4LTnGcPxO7WNndbamurh0zlE56sqterzzDpXG7Wt2oqm2py1T7nzqZVq0K79R%2FlGOleBBQTmxiFV9xht0j78iOZ2PIT3WVb0XMdI8C7qEZr19snruYZet6A83f8Yj2Wm%2F%2FAOP28z4Kf5oc3D5%2FtNM%2BefY9uLHSOMDNH4Rl8ENt28%2FRy%2B3yxo2sTAkJKTm%2BjKm5aqyy3rC9k9aOn8wsls0GOI2fzowVR6TiGkVmlJkqlR5yqCQW6CwG1p12OwUhK0qG%2B0eF7BOMmFgs8IuF12Frox07b02I5xytG9K8HuuFXewrvFEVU0UxMTVETExERMTn52zeMOvFtaTXTRMx5tfvaWcxTgNxfTO4kmlLI1EmmuqVfuv3x76HW6DV1T8nR5%2BYebQ0yErdZU2Ee%2B6iN%2F8Ae0bTVhDG4NxwdUBtX26cdr%2BYxE4VxqwvqcIdJXq8pTeO12%2BIixjvccsG%2Bs2fTp3sHeq8eTq5vvc9Zg0Cp4qrK5htAeaEsxqWhW4LLOgpA7TtGpMx8CjBFafoTz7T81KudE%2BpmYS81r0hXUWnZQsobjkbjsjuBGFcVpcC1cHVINjewx24AfNsI17ivhtxvizEMxV3cifEm5p1b%2FiftxQW2So7oQro7lIsLX3iOOeC%2FWKJ9FdO8pwy81fMmPTH%2FwBuMSyE7aYiiXK1WAjsJjhBxWtVzkfIJKtkh7Gm4PfcNiK8vwf4vbWSclaGVA3urGC%2FyJiOO2CRtt6elTvZIwe9Tsp9rRFHyWlavg2jYnkq9KTLtXl3npiUbKg5T1ImHGktu3FipSUBwaSQErT2xv2mzKW6VS5Bx5LhpdPlZHUPJJbTp%2FJvGwcKZbZm4Nw3IUBnhpy7qSKaFoafnMRvLeIWsrOrSpIVYk22va0XJqiZotElPCXlxc%2FCGIpkX%2BJcU48YJyXmjp07ycIvUfR1c0b2u%2BhDnvd9f21ouVIp96lJ6krQ30qSVnbtjOUyubTRCm%2BFLLoaftcRvg%2FKu8e%2BTns3mEXc4XcDIdB6hRiF7SfSCT%2BOL06a4JV%2B1WfTjerOFXnls6uaN7k6g4toUpICn1uen5Ocl3n0uNmTWogdKreLkrF%2BGyhtEhN1GacfcbQlPiK0BR1jt5R1BVKnnRPrUn6mDAbwIBLiq%2BoEqtuOV4tjshm0%2BW1zPCzgdQRchIxU4mxPPlDjlg%2F1qy6cMc4XeI%2Bjq5o3ucc2sJVvGmM6rPy7CFSkw%2B24khYChZtKCkg8rFPyxpLMrBSMF4jfojc03MrllrZecadDjSlpO5QsAak7jf0x30ijZj69TnCbggnUFX9uDwv6bRq%2FFHDbmBi3Es%2FiOfyRpTS6g%2BuYVLIxeRLslR8ltOi4TbaxJiJ03wOnbebPp070xhd4n5lUemHFXQHuh0B7o7Jb4PcXlKVe4nh%2FUAb68Yr37uSeyJ0cHOL06ArJnDSiD1j7bnbW7vJjHOnWA%2FWaOlTvT3pvPizzS0NTMk5aqYVotfp9WRNO1eRM040m48VdDq0dCq4FyQgKuNrLA5gx0AxNtty8qyp0EsS7MuknYHSkC%2FyRsPCuWOZ2FMMyGHU8M2XlRapzamW35rFD5eUkrUrraVAG2ogbcgIuTeGMz2wlA4UctdKbmwxRMbnznXCNN8Cn9qs%2BnBGE3rLXZ1c0b2swhb%2Bpz7ePdT5TUFhG5N0aR2nsjZCKNm2gJSjhby5ATy%2Fspe2%2FlRcZSUzVQhJmOGTALbgNk9HiV4keve0WjTXAp%2FarPpwnvTefJ1c0b3JWEqjSZXDsjS6vPTFOnZQOMuy7kk4dKws7AgWi9M1mipfl2ZeqvTTi5pj3hEosA2cSbkkAWFr%2BqOnZgZ0OzSlI4bMvVNkgpKsQuagR3m2%2FxRQXQ80pgHpuGLL5VuY9tbyQfVpis6bYLH7TZ9OCcJvEbaKuaN7lfNfBtWx7jio1mSlQmSfcSSvXdwq0pC7J7hbnGlMxMItYMxXUsNtTjM4mnTK5bxhhwOMvFJtrbUPKQew9sfQ9vDeYrakFPC5l%2FZBGxxhMb2N7HaNTYg4Usb4krtQrU3k9QG%2FH5pc0JZrGC9DBUokoQejvoF7AXNgO2I484H9Zo6Ub0xhV4n5kx6Y3ZuIjL3idqUClWjthPBTidbWlOU2G0uKNwtWNHDb1dEIgeCbFW%2FR5W4bSSbg%2B3J07d32OLcd8CjbeKeeExhF55acvslolrI%2BnuUShVSj1OWqblWpbNReLDix7HvLKgqWeCkj3xIRqOm4ssbx0AKsqalWkKFlNyzTSj%2B6baCPxJBjZVGy4zGwvhql4cb4csAT6KYwJdD7%2BLphbzoBuCspABO9tgB5o9CcMZlt6izwzZetKURfTiqZsB2gAg2vEceMD5bzR0oW70XnydXNG9rNtvpP33wvni6KpDymOkCFKSUrsACSq6TytzjYKKRm22FBvhyy6TtsVYmmFfk3i7y7%2BcqEgP5B4BJRYtaK%2FMEC38DaInTnAo23mjpQjvRevJz1b3IVOrFLVIywnqs%2FJvNNBtxgybpKFDmLAWEe72epLk3TJGRqE3NKFUlHFI8WcQhOhwHVc%2Bbtjq2fczqmtb73D%2Fl48VHUfz%2BdSsnv%2Bxc4sD9KzRmD0kzwwYOWoix6PFq0X%2BJuLRprgtWy82fSVqwq25aaub73K2a%2BBq5mFmJVKlKtMdBOuIKFreCOxKeR7Bz%2BONIYvwuvDGJalh4zLUwadMuSxfaXqbd0KKdaFdqTa4PaLR9FpekZitOpeXwnYPcUhaFJvjFfwTe32ONM1%2FhQxniKvzdZmcn1Nmefcfdb9uLagFKUVGxLfk3Jt22ieO2CfWaJ9FdO9TvXbzspnmcZLl0g22MQblgXAm0djngvxMFdInJyXKPtTjVF%2F9FFN7gvxOo6ZfKUMpJuScZNEjzD3qKzpxgnl6elT2icLvEfNnmnc01KZQt0l6l1in1ZqdS7LMzuptd0tKWDdld7aXEW6w3AuNzeNpOTHRo6NtxtXRJCer8PSkC4jdVFyrxjSaJTKHUeGqmVV6QlGpVU%2BrHqG1zOi%2FXcAZslRuAbbbROvLPEDrRbd4WZMXOq6MwEhQ82ror2jJGmeDTri8WeX8dO9Xvdb%2BJVzNGuTaHHN9P2wSE8vNHkmFBauVo3wvK%2BrrcUpXCiyQre%2Fuj7j0e82if3KaujS43wvyqiCbh3H4ULH%2FAxWNNcFmcpvFHTp3p72XjxKuZp%2BruKTwqZqIKrJXOUUAd5E6nn5rRnng03D4zjdq5t4zTHLW2Bu6L%2FLHrzHyUzTxlgNzAmDMrafg2Wn6gzOVVxeJxOCcaaB6NnR0YsA4UrvfmkRsDg7yGxZkgiuP4tqFPdfrkzKFuXlHCsNJZ1lSlKIA31AADujymmGlGEYhh1pd7teKa65mnVE57KqZ5PNEy6NwuNvYVxaWlOUR4XN3FQb8QGND3TyB%2FmUR5%2BG5AXn1l6pXwa40f5C4hxMTDE1n3jx2XVqSKsUE%2FuktICh6iCIk4dHQznzl8pS0pBrzCTqNgbpUAL9lzaPR1xMaIxTlssP%2BDmWE%2F2yn0x7m5vCEOE4nyhl%2B32ddX6%2Bmlkxr7OporzVxCFarmYJue3dW4jfHF7kRjLO8YWn8FVCRk57Dr8ysibeLVy50akLSbEEpW2CQRyi0VfCOPKlN%2BP17hXwpVqm622man%2Fb08kzDqUBKndASANagVW7NVo8%2FofpThVwwqzu9vbU01xNWcTMRl%2BFMxt8zdvuHW9tbVVUUzMTPJzNE0Sq0SYosmqpYhZknGEFKmnWlnTc94Fo9fs%2FRGG3JSQxC3OPPqbBlW2VhLllXuSRYabX3jb6MHYvS22TwcYTO1ikY3fFviESO4MxelzUODjCq%2BkAV%2Fx4fsi3ZyEeo47YNH7TZ9One1Iwq8Z66Kub72gcbNOVvCU1SJFoB52oImUFxWwRoUhQv2c0xqLEuU0%2Fh7DMpiqZq0k8mdmnZUSjK9T7BRoJU4nmlCtY0K3CtKu6O2ThXGqnC4vg0wgokWucavf%2FAI%2BSMax9lLmNjWnScjJcNNDoTUsXQ54jjRZLwWoE6gtJ6w0gBQtteHHXBPrNn06d6%2Feq8eJVzbnCrsghJtsYpGSR9rHYctwoYymEdI7kDSNQJ1F3Gqk3HZsAIqHhIxidJTkJh5AG6gcZuEnzX7IidOMDj9oo6dO9MYPep1RTPNO5zbgHLOTxdSq5UJjEMpIzVKEmZWnOtrL1RDzhQ50SgNCehSOkVqIunlcxtrL6gHCdCmKSuYK1OzqXrEW0p0W7I29l5kXmZl%2FMTzspwyYOq7c%2BgIUioYsccQ2Um4KQFA39N%2BcZQuh5p69R4OstrdwxE%2F8AkciOO%2BCz%2BbebPp07096LzG2zqn0Rq65hphxCFrIJBtEipdSthcjsKd7emN1N0PNcABHB9logA7asQTHLt%2FTY99Po2bLIcbc4U8sZZAR1LVh9wkg7D7J3dsROm2DR%2B0WfTp3kYReZ%2Bjq5o3tCMTshJ1F9iqz7slLzMq0A8hhTgKkrXsQncc%2Fli5S2IMI0l9ioSmM3mpiVUlxpxqQe1JWDcKHV53jeE%2FR80Ura8R4UsrH7j3xT9UfRv326T5bx4hQc4Ta%2FCTlMLnSfz8f6o7%2Fsv4ocdsGn9ps%2BnCveq8Z5fF1c0b3OmK5ZzFmG2JOXeDa%2FGXXmy4CNTbpUST287%2FHGpcY5XqwtRqXV1VqTml1B6ZaclWgrpJTolhKSu4sQ4CVJtfZJvaO41YezYacCjwh5QPFA0pV7MvcvW7GHZg5O5t5guyBmOHXA1HTIoWhKKZiNxttwKN7rSVquocgdrDaJjTbBuW82fTgnCrzyWVfNG9wu%2FIoQq20UvFEHYWjsdjhKzCUkBWSeDVK0ndzEz3PvPW%2F1RWb4S8xyA6nI3AoUtekoViN46QO09e1j5orx6wTy9HTp3rRhFvPzZ5nOWAstKDi3DdSqU3UlS0%2FTnWWkS5ST4wlwqupKuQKQkbHc6tuRjamEaSxhqiexctMghCybEc0kRujAOSueOXDdUNIyMyqmW57ogpmpVNyY1FskhbXvg0Hexvz2jIV0LiFupSuGrJK7g6xDit%2B69nt7Qp03wWrZebOPTXHuzTGEXidUWdU%2FZG9ovU11W9Q7Ep7%2FAFQcYN%2BRA74301h3iJ06jw7ZGIV9qvpCfkdi4ydD4gwFeNZEZIISAChKG3tjffk4ey%2FriJ04wWnberPpfcnvNefJ1c0b3O0jPSsvPzias%2FOS0vMtNNNrlWVOhZSolQUB2ciIu8liDDNHm0T8niKroeZOtBbkHGzcfuuyN51CjcQbYaNIyKyZVcnpA606Ld1vfBHibonEk8NLuQGRjYPYtDv9bExpxgk%2FtVn0vuRGD3ifmVc0b3NeMqcrFGG5GipU009K6HFG48ldyQe49YRrHHeWEnhKj0GpsVtqdeq7cyqblktqSqnuNOFCULURpXrTZxJSTYXB3EdxpoXEba5yByKUVC4CkOmxvy%2ByxiGYGTOe2P3pKYq2TmVEo5JNqZaTTpt9hvSpWolSOkIUq99%2BdtomdOMEp%2FarOfRVviEVYReI%2Bjq5o3uDH5BOrYiKHiSE7EiO3pLhJzSW2p1eWGViDbSETFQmln0iy7CIr4Rs2%2Bk0IywynKd%2Bv43M2%2Fn3jHx8wTPL4%2BnpQvGC28xnlPM5pwHlrhvEuDZqtTdcmWavLVBEuiT6D8zuyqm1lTvTX6riFpSkNkdYKJBFo2jhRhihUSXojc1q6ArWtRtYk6Qm3bayd79sbuwXktxHZeszUph7LLJaYZnFNrcRPMuzIQUX06NSxp5m%2FOL2vDHFYVKT7kWQjaSd7UglJ9QcvDj3gmWc3mzj%2Fd9ys4PeOSmere0YHmCCpLqR6%2BcQWtvtjeasKcVYToGV2QJ8%2FsMu%2FwDPi6UzC3FAoKXUcuMiQdggN0ZwkenrHaJnTvA4jPuqzn0TO5TvTevJz1b3O8vM09Kn2pwToSpaVNqZa1oI02IO43iq5XKJJoc8UVV3HFIUlIMqEXJTbnqjoafwdxNuLT4hl7kWlHwg7Q3jc%2BgKsBHgm8IcUzSlpTl1kK%2Bhv7G4aK4i%2FoGvb0mKxp7geWc3miPTM7lu895iNdE9W9zDi2hHGOHKTR3nVSjtJdcIWG9aHUraQNJtulQUlW%2FKNZY9y8kMMexTtPrCZ1ufkVTD6eiLZlX0urQWiTsu6UoWFD7e1to7mcw5xaMFCmcuMiVlQsSilqGnzHUuMLxxklxHZgTkvVMR5eZSqmWGPFx4olbCAgElIKErsSLnfnF%2BPWB5Z91WfS3wr3pvHiVdW9wu5JNA8x8d4omVTfqkR2e3wm50OS6nFZdZThwKsG1re1Ed99dvyxBXChni6hxPuZZSt2AFwpd1X7vfIpGnuCTnleKOlC0YPePFnmc%2BYLymoeKsMorDtbmmKimYU27LdBdgS4RcLDl7lZXtoty3v2RtKiyjdFkJWRZmiUtbFSwDdXLa3mtG4cI5OcUmXlKnKXhrBuT65WcdTMutTLfTHpEApGgrXcDT2DYx7XMP8X6lhSsrskVEC21Mat6bdJzjJTp1gVUfpVn0lasJvNOqLOqebe1JKKLrD7ss42pxKDoT2r3sqw8w39EeVy5l2pxsJS06ryr3G3ON0N4e4u2AHW8s8kOk5XTSkBQv59cU00jjEQnoUZYZMpbvqsKc2AD3gdJGSnTXA6v2qz6Sveq9zssquresvD3LTDOZ1OnFtlTD8jPoCwANNpdzc%2FjjWng%2B7jOaY%2FdYYfT6tbdrDs743BVcNcYuIsPVbD0xgbKmlM1SReknJiTl0MzCEOJKVFpaFkocsdlW2ipwscNWYGVGOKji3FrtMZl3KOZBhqXf6Z1TqlDuAsLC5Mef0q0rwe%2BYXbXewvFFVdUZRETnm3bhcLxY20V2tM0xHhY3x5gjPdI%2BD7ASBH%2Bcv8sc4nmY6K465hMxn1dKknRh2nJNjyPX2PnjnePW6KRlgt2z8X3y496121XpSzdvY%2Ba0c%2Bgc%2Fmx3fxOOmX4SX31XunDVKII5hZXLBJHoIvHB83vTpxP2zDieV%2BaTH0KzuwXV81uHFnBmDUSztRncPUsyyJh4NoWlHQOKSFHYKKEK0k7A2748hp%2Fb2V2xDD7S2nKmKpzmdkRwrPPP2%2FY6eGUzVY20R5nz54j6PNLzNmUEaegpFGY6199NOYudvOoxrBmjzbLYVdKk322j6HZi8OmB8R1ybxHN4azNnXZnoWm2qbTZMlplqXaabQOkmADYN3JtuSeyMXmuHjLKZTvklnhLql0pQOhbpdnFb3WdTxAPm5eaPU3fSjCYs6Ym8WeeUfSUdpq1XC3qmZopmfsnc4gaknQWVKFx0zd997axEkzTZl2nTbLDDiyuoqCCATqA17XHdcR1lmPhLJ7LGTptVxFw55mMB11mVlRVa3JycvOKbcS4%2BFloKVrU0FpBTyKgRyjWmH8xcF0yWqFLewZi%2BSkU1SbmaYzRcSMMlMm6u7bUz0rKw68hICelTpChzF9z3rveLG9WcW13riqmdkxMTE%2FbDStLOuyq4NcZT52o5umVGZmasWaa%2B4p3oi2lKTchKklQHn2ioKJUVLcR7GTBS5TUoQejVYL0jblG9FZn5WpQdGEc0yo2G%2BMJJIHedpaKgzcy2SAkYWzSAtuBjGS5%2Fg0Z1GhGpCcTN04PSL5Bk1BRS2RZVnfnTHjp6OrR1W8h90n7tNo35Us4cBsSDicP4OzCE2llYlhP4tlVy6XSghKlpRLhSk3O6QRcbXEY3hRzK%2BsKoNFXlfiucrzzbbC2KfPsONzFQU6oksII1pQpAbsgkkEK3taK1102dM11TlEa5TTTNdUUxtlpXoz1TFyYl5r7IhxKG3WA2pspvyHMdxvHR0zknhcoM5O5M5syi7rKpVima0NnsSFX3vcxWp%2BVGCJxozb2TmalNaaISvpKa46F3G2yL6fMY5dOOYdVstqelG9tzcLzG2ieaWr82JmsVWhZYF11tIYwHKyragjcoTNTNjt272%2FgxreYk%2FsWsdYNpSv0gbn1x1FiWg0XEMrQ6c9k%2FmazLYboqKNKOtUPrvpS864Fukr7ndOwv1YtcvlphmqMyUlOZP5kUoSTKkuzoo63nJ1al367YVZOkGwKbctwbxknFbh5anpRvYu5bfxJ5pc5NNKQmZATcCTfJ82wiq0gMPUh5TS1NMtkPFPMKUXCBflvG9sS4WwDhqmyzlUytx9Jsy7apWaqjtNLDcytzVoWQ6oBKgSlIAtcA9pjy4Zx9ldhbEtXYolCx7L4WmJSTbkFpdppqZdQgF8THSoW0pPSqcLakBKgnSFE9m3Y21leKeHZVRVHhic2Kuiqzng1xlLSMjKzDSaYhyXILM2VP9YeQVN2PyGILkZoSak%2BLqK%2FHwsjc3TpIP446TXm7lMCjoafmwkAnVeaolyOyx6D5IkazYyh6RYdpmbZSVEhSKhR0m3YLdBaM6rnWcp08U1UolHCh2bSpvqndIcVc%2FLFCbYs9UgRYty6APModECI6P8AdXypbU24ij5tPFC9Skrq9ITqF72BEudJ89jGI4Sr%2BSdUen5%2FNnL7Fj8%2FUpubU4qhT8v0aGFJQqXIQ4UlTiXA50nJKgUkWO0RM5DS3i6%2ByJxJ1NSGG1PoPRq1JWUkq53EdTqy54c5iyahlpnxQ3EMJb0CjsOdJts4bqNiYoSmCuGqbaLU1gPPWTVYAPN0eXUOzcAL58%2BztjSjErrOy0p6VO9s9yWmWc0z0atzWVVnKrM8O2CpCcUkyUjjSvBkBIBQXJaVUpN%2BZFwT%2FCjVfikdeVJeRE3hejZfDAOca6ZRajNVGWeTQmTMTT77KGlIWSsdUBu4tvdRi0M4L4fZ7VTXMsM62SyvUX0URlTjd1XCVDpNxYW5dsTOI3WIz%2BMp543qU3e1qnKKZ5p3OW3JR40x5IbuozLZB83RritPtLcdrriWVFK9Gi3MXdTz9UdJV7C3DzRJFSKnl9nS1LgF5c8qkyzWlF9wrW4EgAG17dsYecRZJyeLZKcwxRcf0ykuyE0irTq%2FEnZ9ybU6S0W2VLDXQhsNpUFHVcqIOwvsWNvZ29PCs6omPNOfsVrsqrOcq4ylpsy7q6lMSjLKy4ac00lJ7V6W9h39sU2dQMkFIICZF0K25KPSj8ZEdA%2B3LJ5H2PEmZ6FefD1MVb0Hpop%2B3TKwr6%2BMsxCgbDpcJ01fxgPfiMZVMmgJVpQ9iroI0rd19YbDWDeKIbIpjaiCD404Lf4NMdBPYtyldSbYvx3c2uV4Lpqth2fZosrFYyPrmIqxP4%2Fw7jZ2TSmURSH6UZNl58toKHnJtoqCEKWnQUhskJtY35wMmkUS8weuwfJVqip4vNuTa3ClpKtPJPL1R00xgDh%2BqsvLzEnlznpJy77CVNPJpsu94wFbh0EKIsfNsRBrAnDuXAlWXud6ei6QOPqprBS4fggJBuO%2FsjSnEbpEzHxlOcfvRvZfiK4jPgz0Z3NcYcdmXeG%2FHlJceu3LYroM%2FwBHp8kuImmisK7b6bW80ay8TX3x1o1JZESGD6nhD3NM310%2BpuSTj06ukN9My5LuOrQlrraRqLxSrUDsNrGLBT8D5IFh2kuZTZzPrmnEOtz6qU100ulANw2kL0qSrmdSb7C0O%2BN0jbaU9KN6KLC1tNlM807nNzEosvyiXOaZV71Ks4RE0hLKW7RkNtdIoOuKWlBv1QQo%2FEI6cm8G5D0qlOSnuV5x1B9J6VqfFJbZXL3J1NEKVYp3vy9cYVPVvJGlOUCYwFhHGyn5GquTFSfqc%2FKS7ypItpQluVU0FBtwK1q1LBBFge2M1jebK8ZzZVROXgmJ9iLSzqs%2Fzoy%2ByY9rTMpS55UlLMiQfW8md6RYCFHqWTv8kTzlDqbkpUCmmzYSub97IYUQpN3De%2FrjoT3Ssq%2BjSFUrNxSua7YnpyQT3j3i4iRnNHK9tpxp2l5vEKASm2K5AADzjoN4zsbQ01Rak5M1Qpp04rpEpLSiwqyt0X7PMYtlUps1KvpYmZZ1hamGHNLiCk2087HsveOjRm3lUndygZuPGwFlYykkgDuFpfaMUqOOsuq3jJmpYpy8r9bw5IU5ctKyk3iJJqKpguBwOPTKWwlbQstAbSkEBVwbwGl26XMOi6X9PrMehigTLmsqn0pIGwuSDG%2F8D4Wy5xB4rUxkjmLNUNt9xS3qW340Hxc%2B867AEC4Gob7bxNOZSSCkt0%2BTyPzTdU2VBE0KfpW4k%2FbJvp2jn2mK3GxrmzrtqYmPDVEe9sU3W2qjOKJ5pYBhHppXJnNaUmXUBSkUF0IPlEpnSnb1G%2Frjv%2Fi6UXuGx16wF6jSNhyHVjmVnKLFc%2Fl7jfB%2BGsg8eyVRxX7EtST88wgS8r4vNdI4p5alahqRsCkbduxuOleL8mW4c5iRKgVN1aktEjkSkEH5RHzTSK%2FXe%2FY%2Fh0WFpTVlaTnwaonbNllnlOrZPM613s67O621NcTGqnbq8O9wegWteC1cxEurlA7x9blwSIEG8QFwYmgEImsO6Fh3QCETWECBaApjnE0QtvtEYCdI5RXSk3FiI8%2FLsishQ1Wtz2gOpeFnKbE%2BXeIKHxLZmYZkpDLGQpc9U36xUltLDLYQUsvtsG61rU5pDdk3JIsNwY27g3HWROCs1Hc58V8OlYwbSccLk2VVmpvyUxIyyZz%2B6HKclRXKtzQKekVpIGoEhIJMYNldhfPniJ4K8eYBVVJWfkpEycrgdpxKUTcwuQcDszIOOCwUyElKW9YB1WBJTvGIZm4EqnEPO0XCOXGF6ecSTEjRaTPMzeFZ%2BnVuk%2BLSbcvNmdnHAJZTaFJVt5SkhASdoDX2eXD5mflDP1HEuL8CM0Cg1SuzktTDKTbT8slJWtxltvQolKS1YpBtsLdkaise6OuuP2t5lUnFFByrrE7K%2B0VmlSNQoKWGkhybel2RLPPTJPWLiFpUANgErHO8ck2HdAUtNt4XtE8S6YDIMuqbJVfMDC9GqjXSyNTrUjJTSLkamXH0pWLjvSTGXcSeCsOZcZ947wRg2VXK0Oj1Yy8lLuOKcUwjom1FGtV1EBRVa5JAIF9osuTehGbuAlOJulOKKYSO%2FwDNCLfLaMu4vnQ9xR5qKSq%2BnEbyPQQhAtAafKrRKV98RKdheJSmAoPAqSbRjNcVZh0fuFRk6tiQYxvEKLyzu1uofxQGDtm0XjDWJ6rhSsM1yivIRNMhaClxAW0%2B0tJS4y4g7LbWklKknmDFkvaJkqIMBeK45h6dmUTlFln5JDibuSizrTLrvultfNSO7V1hyN%2BZ8ahINyjSJcOmYDilOnYIKdtGntB53vtyt2x5dZEOkgPW5L0sLeLczMqToJYSUAHVtYLN7d%2FLuiZMw2zLNKlZuaamAVpeSlWlCkHydJG%2FfcH1Rb%2BkMRC4C94crjmGqzKV2WkpCdek3OkQxPyyZiXWbEWcaV1Vjfke0A9kVsO4omsOonJQy7c9TKm2lmfkX90TCEm6DfmhaTcpWNxcjcEg4%2F0hibX5oD2VBNNXNrcpaXvFl7oRM2Ljf7lRGyvSLX7hHpka3NUGqyNaw%2FMOSs1IFDrazY%2B%2BAda45FJBIKTsQSDzi06zELnvgL3X57D9acFSp8gaXNOkmZk0gqltRPlMnmhJ%2B0N7cgSIqYTxfXsB4gkcWYUnhI1WmLU5KTHRIc6JZSUkhKwUnZR5gxj8Rv3mAK6O20Sq5i3KInRaIK5i3KAhCEID2ylarEjLqlJKqTTDKr3bbcITvzIHYfREJOq1OnIU3I1GZYCzqUG3CkKPee%2BPHCA9E1NTk%2B7084%2B4%2B5y1uLKjbu37Ipt%2BXEgJvFQdkB0pwYShmK3jNwI1FujN2HpUr8gMYo6VK4TpptKgSvMdgJGr4Psc8fxxtTwfUq1N1nHbcwSGVyEiy5bnZTix%2BWNg4V4Osy8OUKsZfzNFwbjXCdRnkVGTM5Un5Cal5hAWlt5K0JOlQQ4tJTuki3dAcBrafSb2%2BWIjphzSfiMd9q4HsUNlK2cm8GFKR5KsZzRv8bcRd4KcTvtpSMj8F6hfUr27TW4PYAGhYQHF2WWW1VzMxazhGm1qkUubmZaZmZd2qzBYYdWy0pwMhdiA4sJKUg2BVYXEYl0Uw575oV14%2BimGOEnM7CU3NT2Hsq8B06ZnqfM0p55zEz0z%2BZphGh0JS42QlenZK02Ukm4i0L4HcZgJCcqcCq6MANn22zOxAtc3a3gOAEszAX5CoqeLvq%2BCr44%2BiMvwYzzaUKf4esMLeLaUurazBcQlSgLFQSZclNzva5iq5wZ1EhDslkDhmWmW0ktqXjtx5tLgFkKUgy41i%2B5SSL27IDgbL7Cb%2BNccULBSKnKU1zEFSl6Y3OTeroJZTqwgOOaQToBIJsDtFnq1NeplWm6c88y85KzDsup1lWptZQooKkntSSkkHuj6D0DhBzRwtWqXiShZYYDkqtRpxufk5lOJ3SETCFBSVBBaIsFC%2Bk7W2ihM8FmMKnUJ6p1TJfBMxMz80ubcW3jJ9pIWslS9KQzYAkk27Oy0B89PF3IudIaWkuOHkwkuH0R3wvgvxO0lIVkTgZSgnSCrGb5BA5XBa5gXF4gngoxWG3rZIYRaW6nQNONpjSAedwGfywGHcA8uvxlx9OwXiWWB84Eg8bfHaPXxwI0ZlUVJSRahDn2%2B%2FrjfGR2QuM8usRS03WaFhjDlEp6Xn2ZGlVB2oTE5NrQGw4864lOlKEXAAG%2BoxozjmfaczSpUuhd1y9DbC09xU8tQ%2BS0BzpI%2F2wk%2F%2FEtfzxHcCggBxBOrUFJsFXJ80cQSf9sJT%2FxLP%2BkTHc7jYeddDLSgdQ1WtpJ7xGWx%2BUn0KW%2F5kR55eIKFgEMgi2m3yWiCVNlPQhFlNqsTfnftj2LZSHShxCkqZcsTfnccxHn0I6f7H1v9%2B3tjbc%2BaXpl2Q6ndRNje4PKKFRkZd4lEw2lQV8ICxB7xHqlNAUo9Gobbq7xHrcZbcZ6RDm4HVKu%2FzxOas05NbV2nzEopJA6hN0m1wfmixPoUgddA1KFtjGyp%2BVL5KHFpKUjrpPfGHV2huSi0Kl29aFG5R3Ht9UM1qZYbMNhBWtG9xfzDvi2OMMha0uGyT1hYi0XeYIuoC6Ekk2KeUWacZUpajbZQIJtt6ooyvBiJq0g4u1ve%2BXfGLNhKQnUrTvGTVZavYl1txfkNCx7rEbfLGNNjpLN26lx%2FqitW1monU1LiF0JrE%2BlSUkJn2lG%2FphXwE4lmmgNI6dSdyb%2Bj4o8uKyRWaue6Ybj04nKfbVMBPLptviEak7WeNjYWDKjTaMpupzFCFVUwyUKlZmfmGmXLjmS0tKgR2WMY3XsWtpeU5IM1ZpCyVFhdXW623y2SVJ1W9JvHvpiiKa6vttaMRrqQFnTtEJToxWVOlT7E7oI8lE8Qb999PyRKvEa3gpJNRQFcgJ0m3xpixNhSl2j2NpSBvAXFdeVp066iTa288rn9zEZfEBlz0jqaoux5IqRAI7iCneLQ%2Bq55RBDkBkuNsQVWg1FmWotUmFS8zKNvFEwUPadYvYK0gxa5sF%2Fr81KTqVFHG6iubpiuw05o%2BvcfkEevoxf%2BCPxQHiYYKjaO7PB0cP8AKVvEcxnrjBltrD%2BENaacqYT709PhOpb5vsUMIBUTy1Ed0cn5U5bV%2FNLHNHwNhdjpKnV5gSzF%2BSL7rcV%2B5QgKUfRHfXGTjzD3Dtkfh7hfy2cCHZ6QQifWk2WKdclSln9UmXQVHt0JPfAWfDlKw14QniGxhO4tr1Zp%2BC8FUxlmgylPcQh%2BZQ6%2BWy%2BpSwQm6h0p23ukdkXrg8xXRsLY9zH4G8cVEYioTM9U2cNuzCAjx9gXTPyWnkFLQemSBsFpXp7I114LWpE5%2BYjpTiz0U5hR1zR9sWZppRPq1RzRizHtdl836lmHh2oGQrUpiV6sU%2BbbuOhmETK1oV5wRsodoJEBS4iMmalkbmlW8t59Tz7EgpL9LnHB%2Bjqc71pZ8HtOnqK7lIUI1O4g%2BsR9QeJfDdH4x%2BFnD%2FERgOlBWJ8NSj01MyTB1OdCk%2FnnT7DcqZWOnbHam9ucfMmfYCVFTZulW4I7QeRgLWsEHlE7aAecRUgg79kTtgCA6D4P8scl8zsez9CzhxcaWymjzr0hIdE6lU8tMs4ouNPINg6xpDgbO7guADyjS2KKZRKViCep2GMRt4ho7DxTI1ZEq5LCda7HCy4AtsntSrtEb54GcrMv85c3JnB%2BZlCNWozOHqjPpYEw4yUzDTWptYWgggje3ZfmDGgXEsDYz6HPOpQv6%2FPAeRtsHnG9OGDOGiZL1jFSMTYPqeI6VjbDEzhmZlqVOJl5xDbrgUtTZUCD1QRtuCQReNMNplEMrddmGSEC%2BkKuo%2BYAc47smZygcC2BMMSOEcHyOKM7MaUxNYm5%2BekjNJoUotIKEtNJBOrfblyJJgLXgPihy%2FyToNDoklkpmpSKBhWtu4mws5PVREup6fdYLbrE%2BvQlD8sSdSdN1AbHlvxtjGpv17E9Tr81LNMP1ObenXW2U6UJW64pagkdguo2EdV07j24mKdOOO5iNy%2BOsPTYV7J4cruG9MrMs%2FDQlzo%2FezpJsVBSb8xGJ8W%2BTeXmF2MGZ25MuOM5a5pSK56mSj5N6POIsXZPUSTpuTpBPV0qTcgAwHMa2rHnGw8r8C5RYppM1NZg58SWA51qZ6FmSmqBOTomGSkHpUuMApG90lJsRbziMILUur%2B62Pux88dC8H2UOXGbS81ZTHdPVUPa5geYrFJXLzi2TLzqNXvgKT1rADZVxvuIDnCry0nJVSbk6dU2KjKsPuNMzjCFobmWwohLqUrAUAoWVZQBF7HlHlAFuUVltxT0iAyLLwIVjfDqF%2BSqtU4H8KaMdA%2BEcVfi5xiD8FuUT8Us3Gg8s0g5gYXTqAvXqaLq5fopuN8eEdVfi4xmfPLj4pduA5eXEADExiKQIDpHhzyNyUzPyqzIxNj7NhjDdaw5Tm5iWZXKvk00dOhKZpwIBEyy5ctlKLqRqCiI55nJMSk29LJmGphLbikpdZuUOJB2Wm%2B9iLEA7i%2B8dFcOuUuAcd5GZ3Y3xXJTa61gOjS85RJqXnFMeLrcJC9QGywbJuFbWB7458WlB%2FTm%2FuhAedtq8dF5C5t5aYZypxxkpmlgjGVdpuN6nT6kHMLzDLU20ZZNkpAdve6t7gHujSWGcPTWJq9S8N0paHJ%2BszjMhKoG93HVhIPoF7nzCO4cw8x8McD003ktkThukVDHkpLNqxTjCoSJnH0zBAPRNJtZISDfcgeYmAsp4v8ABmDMBjCMtl3mDKVqnYRncAUeVq8y23SZumTDhUibm5bbVNoSSklKSFG9jY7cSz7HRuLbR5KfJT5hyjsTDPHbXcTzzWDuK6h4ezIy%2FrT6JOpOTVJErP05txQT07LqQB1L3IGldh1VXEak4qsipLIHNicwZJVn2Roc3Ls1WgTzyx0j1PfBLYWdtS02KSq3WsDzMBoco80bUwvldlLiHBTVdqXEfhfDtdcYcW5QqpSZ7pWHklQS2p5tBQoKASQpNxZQjXKpdsrv4w1p%2FfiOgsrMoMAYy4Qs2M1qvLTRxNhGuSMlSJlmaUhtDbiWytC2%2FJWFEqG%2B4vsdoDmlzpP0zqq%2BFvfftF%2B2IRUcBEU4CSx7oWMTwsYAOcVUiJQBeKqUwFVrsj1ge9iPM2I9drIEBlFNVemNj9yYyHK1WnFE04SQEUypKURzAEo5GPUgaqegfuTGQ5U%2F8YKu5f7HQaqv%2FwBK5AawwTOTkpUJZclNOS7im0o1oNjYpsY2nwxj%2FwDVRl6PtccUoeTb%2B7Go1NhI6J%2BVXa%2BkINu%2BNucMn%2FxU5f8A%2FwC%2B9KP%2FAK1qA%2FQdCEIBCEIBCEIBCEIBCEID8%2F8Ax2rJ4ncyUEjq4ineX7%2BOe1eU2vziN%2FcchB4nczSP2yz4Pp6SNAH4HqgNgUfyf4KY9hjw0tSm0rUlou6EpJQOagFbgee3LzxtvNvKCn4Po1MzFy8xCrFmAK4ENydXaYKXWJogBUpMtC%2FRvBVwB29kBrDUb2iYHvjNsX5I5sYFqtDw9iXAlSZq%2BJVBukSTOl5c29cAsp0EgOJuCpJsUjc8jGRz%2BTeG6dmdgfJpvGLdcxTVagzJYrTT7KkKS6p1J8TaeH2Z5KAvpFDqg7CA2Tw4cIysxqFL5iZkzc1TMNzY6SmyDBDczUGwd3VrIPRNEiwsNStyLDeN4v4w4PsnZaoYPYlsOyKKpL%2BI1RlhCphc21cHQ%2Bu5K033sY8XHNmdN5V5Zy2H8IuGQeqbhp8spnq%2BLyzaQLI7urZIj51UyanZ9pazPltSlfBbSST3kne8B3xX%2BGnILPCgP13JSq0%2BkVJIu0ZF7XKLXbZDrRJLd%2B8cu6OKsTYcrOEMQVHDGIZFySqdKmFS0ywsbpUO0d4IsQe0GLtkxmjiHKTNCg1iQqC1y01UGJKpsaAlMxLurCCDbYlJUCDa%2B3njpPwhuEZKXreDMwpRhttyuyszTZpSRYuuS9lIUrzhKikeYCA4%2Bub2vGyspM9sVZPJmpKmycrVaPPO%2BMPyE0pSdDtrFxpad0KIABG4NhGt4Rp3%2FD7rilhVdr5RFdE7YleztKrKrhUTlLqdvjtqSEhPuby9u3833%2FGiH1eNX19bLSTKf3M4L%2FKmOWIR53iJgHkPWq7TZ7uvMRrrnq3OplceVa%2FS8spH%2BFOA%2FwBGK6ePCq6d8sZMnvE2n6McpRPDiJgPJYetVvR3dePHnq3Oqk8dtUAF8spEW7PGh9GIHjtqoPUyykwL9k0mx%2FkxytFaSk5upT8pS6fLOTE3PTDcrLMti6nXXFBKEjzlRAiJ0EwDlu%2FrVbzu68ePPVudTfV41T%2Fqzl%2FwxP0YlPHhVb9bLCXI%2FwDGJ%2BjFkHBRitqpuYLdzNwecdtyJqCsNIeWp8NA28sC3Pa9rEkdm8c9z0rMSUzMSE02W35V1bDqDzStKilQ9RBhxF0f%2Brx0qu0d3Xjx56tzqAcedU%2F6tpdPom0H8aIh9XlVEEacuGV2F7rmkAk%2BgItaOVtB74heJjQXAPIetV2ju68ePPVudWfV5VLSLZasBXaTOJ%2FFoiRHHpWwbKy4lj%2FjSfoRyuD3xG474idBcAj6D1q%2B0t3defHnqdWnjyrJG2WsoPTNI%2BhEw48anbrZbsg9wmkfQjlCFx3xMaC4B9X9avtK933jx56nVSePOqBV15bs2tyE2nn9zyic8etS19XLZnT55tF%2F5kcpQHVSXe6HEXAPq%2FrV9pMX%2B8%2BPPVudX%2FV51T%2Fq1b%2FDUfQiKOPOrAdbLVgHuE4m3yoi2VThQy4w5WKLhHFXEhSKTiWuybE1KU%2Bapy0dIHkjotJvyUq4FyCY0tiTKzGmHMy6plM7R5moYjpT6mVS9PZU90yQkKDqAAeoUkG%2FqhGguAclh61faJv945a56tzfv1eNVP8A8tZb1zifoRD6vCqj%2FwCWksf8cR9COa8RYMxfg6ZakcYYYqlDmnwFNtz8uprWD2pJFleqN%2FYo4XsnMAVhvDePuJ2l0SrKlGJ12UfpDpUll0XQpNibgi%2Fn25RHEXAvIetVvV7tvE%2FPnq3Lorj0rCwUqy0l7Hn%2BbUn%2BhEiePGqjyss5M%2F48PoRzlRsJ1rF2JHsNYGp83X5krmlyaJZk9JMyzOol4I5pBbTrIO4BtFjBujpBqKYvOguA5fIetX2kxfrx489W51aePGpkp05XydvhEzgP9CJ1ceFRLdkZYSaV95nRb%2BbGPYZ4RpBw4foGPc68N0DGGLJVU5SaCygzay2E30LcQrT0ljulPnAvYxi%2BDuF3GmKMz8WZcVGsU6jt4ER0tfqzwUuXZQU6mwgc1KWghQG1hcnlEcRsBnV8R61W8m%2F3iPnz1bmyBx4VEc8r5Q%2BifH0Yl%2Br1qF7e5XKfxgPoxhNd4badTKHgzH%2BFcx5LFGBMUV2VoM3XJWTU2aa6%2B70SHFtE3KNfVO4sbX5iPRiPhXm6DxLULIFrE3TStalE1JNZXJ6VNSqW3FPqLV%2BaFN6ee5UIjiHgMa%2FiPWq3o7vvHjz1bmXfV5VH%2Fqslf4xP0Imc48qjazWWMtfvVPC382MKxXwvv4Y4gcE5Mt4jdmpHGaGphqpmV0uMMALMwot3sS30fK%2B%2Boco1znHgmnZa5mV7ANKrq6wzQ5hMqucUyGit3o0qWnSCQNJVp59kRxGwHyHrVb093Xjx56tzfQ49KsE2VljJ6u8Tu38yIDj5qvJWWMl%2BGD6EcmknXzgom%2FOJ4i4D5D1qt53dePHnq3Oszx81XV1MspBKfPO7%2FIiIL4%2Fat8DLKWHpqA%2BhHJeo98CrbnEcRcB8h61XaO7rx489W51qnj%2Bq1iDlnLA22Pj4O%2F3EE8flX6S6stZMoty8bF%2F5kcjEm8RBNocRMA8h61faO7rx489W51y5x%2BVMoHRZXygV265wW%2BRMS%2FV%2BVf4GWUnfzz1h%2FNjkm5i5YfolSxJWqfh2jSvjNSq00zIybOoJDj7qglCSTyFzuewRPEXAfIetV2ju68ePPVudTtcfeIgLu5aU7%2BDPfOiIDj%2BroXvlpJFJN%2F0eAQO7yIsx4KHn8T1TLekZ6YTqWP6RTfZGYw03LTCFpQQkgdMRosdSbH92m9rxzMT19BQppSVFLiDzQpJKVJ%2BMGIjQfAY%2Bg9artHd148eerc60HH7WSbjLGVA7lVAG%2FwASNoj9XzWFc8rJE%2F5SH5URyVrHcqHSDzxfiTgPkPWq3p7vvHjz1bnW31fFU039y2Tv3ePj6ESfV%2BVYK%2F5L5DT%2FAOO3%2FmRyZ0g88QKxfkqHEfAZ%2Bg9arerN%2BvGf589W51dMcfVSW4Fs5YS6VjsXPix9FkRiOZfGVjbHmGJ3CtJw9JYcl6myqWnJpmYU7MrZVspts2AbuNirc2Jjn1RiF79sZ7PQ%2FBbG0ptYsIzp2ZzM7PNM5Im920xlVVOUn7zqpT5PmHdF%2BwbjTEGAsRSWLcLTvitTkFHQojUhxs7LacTyU2sbEeg8xFgVEI9BbWFneLObK1piaZjKYnZMMFNU0znDq6U49sQtS6EPZayXT2GtbVSUlBPbZJSbD1x6jx%2BV5SrqyzlCP%2FHf7MclJMTR5aNBcAzzi7xH%2B6rtNmL9eI%2BfPVudZnj7rJP%2FACYSlv8Axw%2FIiJXOPqsHZrLOUT%2B%2Bn%2F8AYjk6EOI2A%2BQ9artJ7vvHjz1bnWSuPirnUU5ZyKexP5vJ27%2FIiDfHzVwqyss5QDvTPf7EcoDlGWZXZc4lzaxpKYCwmiV9kJpp2aU5NzAZZYYaTrddWs8glIvDiNgPkPWq3nd948eerc6GRx9YhSon3OZPT2Wn1A%2FzYnVx%2FV47Jy5lEnvVP%2FMi8agz2yNn8hZ%2BhyNTxPI1%2FwBnpFc6wuRYWjSEuBsIsrdRUSNJHMGM9Z4LMROVCVwdM5nYUlcwJ%2Bjity2EHulTNrZIPVLltAUCFJO%2FNJ7BeL8RsBj9njpVb1e7bfx56tzIT4QCvEXOWsoVdxqG38yJUcfVeH2TLqSV%2B9nrfjRHLE9KTNPmX5GelXJaZlXVsPMuCym3EKKVoI7wQRHnuIjiLgFW27%2BtV2ju238eerc6uPH7W%2BzLWX%2FjAf1cR%2Br8rX%2FVrL%2FxgPoRydrhriOIuARssPWr7R3bb%2BPPVudY%2FV%2BVrsy1l%2F4wH0ImVx91xX2PLZlP76fB%2FEiOTAveKoXDiNgP1f1q%2B0d23jkrnq3OrHOPXEIPUy8kyO8Txv6PIgOPivX%2FAOTlr8P%2FANmOU9cNd4mNBsA%2Br%2BtVvO7bz489W51enj5xB25dyx7vzwI%2FoQPHxiNPWGXEofTUyP6EYDl7kFget5QSucuY%2BcUpgylTlXmaOwH5BTqOlaNgCsHyldYgAckneLBnfkkvKQ4ZrFJxdJ4rwtjKTVNUSsyTRSJlaSNbWi5uqyklJTfUL8iLRSdBMA8h61XaO7bx489W5t%2F6vzEOnfLmVv8A%2BZH6MSnj7xD%2FANXEp%2FGR%2BjHPlcyozMwvRG8S4ly7xHS6S6hLgnJuQW22Eq8kqJHVv57Rs7BHD7gCsZMUPOHMHOaWwbI12pTlOl0v08ut9IwpSQjUDcrUEKVa1rCJjQfAY2Xf1qt53bePHnq3M2c4%2FK6kNhnLZhRsekK6kQL9lrJgjj6rejr5ctavNUtv5kc8ZmYdwfhTFRo2X2PWsa0oSzC%2FZNmVUwC%2Bu%2BpkJJ3KeqLjYkxbcWYVxJgTEc3hDGNGmKVWZEIMzJTCdLjWtAWm486VA%2BuJnQbAZ%2Bg9areib7eI%2BfPVudLDj7xIk3Tl5LhPcKkb%2FwAyJ%2Fq%2FcQrQUqy8Zv2E1I7fyI1hlVkZQMYZf1HNjH2a1FwNheQmlSCFzSemmJh1JSkqDQOpKNSgkGxJN9rC8XHMnhexjgrMTBmAMPVSQxH7oKVKoU80OibXpAUvpOekJbIcKhcFPLfaEaD4DH0HrVdpMX28T872bmwG%2BPrESR%2FyeS485qZ%2FFoiK%2BPivHTpy9aT9sPZNR%2BI6Yslc4P5F2SxlSsvM3qRinGeBJTxqsYfTKLYWkdHr0oWfhEAgXFrixsTaMLzLyFk8G5HYBzqwpiSZxAxjZUsyqWclAz4s9MNqLTYUCb%2B%2BoW2Se0Xi8aEYF5D1qt53bePG9m5s76vyvczl0j0mqkD5ERBPH5Wv0zLxs%2Bipq%2BjGI8R%2FCo5kJlzTsdy%2BKJiurVUWqdVZYynRIlXHGVKSUKBOodKlTe%2FeD5ox3iEyHp%2BRftRkTil2qVXEVOdqM3LGW6NEohHRgBJuSq6nCne3kkxjq0EwDb8R61W87uvHJXPVubNXx%2BV3VZGW7Wm%2FM1ZV7fcRMOPusaFasu0avg2qZt%2FNjlEpA7YlinETAJ%2Bg9artHd158pPVudWL4%2BK0Ui2XaCrt%2FPVQH82CuPmtXARlui1hcmrK9fwY5RJtBDm8TGgmAeQ9artJm%2B3nyk9W51cjj1rnNeXSfVVFfRiJ4%2Bq6Fq05dthPwb1RRPr6scp9JEIvxGwD6v61W9Tuy8ROfDnq3Orjx%2FYhKrJy6YCe9VUVf%2BbEyuPmt8xl20fRVT9COT4z%2FJvJrE%2Bd2IpugYXXJSqabK%2BP1Cdnnw0zKy%2BsICjfdRKiAEgXieI2AfV%2FWq7S0X68%2BPPVub3HH1iHQEt4AaRpI8upkgj7iIp4%2FK8FXcy7SU2%2BDUt%2FlRGlc4slK9lHj2nZbOz0tXqlUJWVmJUyLax0q5hxTaGQlW%2BoKTbu3jPaxwiqoi38Mz2eOAmMeSMi3OzWF5qc8XWnWm4aD6yEldiLbcyL2BBikaDYDnqsPWq7R3defHnq3MoPH%2FXuRy1T%2FGn%2BzEx4%2BaspR05daQRtqqm9%2FueUcm7tuLbWFJWlRSoHmCNiIli1WguA8th61W9WL7efKT1bnWX1fNbH%2FwAu2z%2FlM%2FQiP1ftcH%2Fy4Qf8pn6EcmA2iYKHeYidBsBq%2Bg9arev3defHnq3OsHOPqtpQHF5coAPYKqdXxaYtlc48MZT1MelsPYLkqbPOJUlubmZozCWCRssN2AUodgJtHMKzqMQue%2BLUaDYBZ1RX3PE5eGqqff1K1X68TE0zXOv0e6HoqE3NVKefnp6bdmpiZdW8%2B86bqdcUSVKJ7ySTEJKZmpGbZm5KZclpiXcS8w82qy23EkKSoHvBAMeeJgoiPVVUUVU8CY1bMmvE5TnDqKicdWKZSVQ3iHAUnUJ1P2WalJxTAe23UUWIBJuTY23i5Hj8rR3GWjY%2Fymb%2FAMyOTekMOkMeVr0GwCrX3PEZ%2BCao9ktju28x8%2BXWP1f1ettlq1%2FGZ%2BhEfq%2Fa3o3y0aKrdtTJF%2FuI5L1mI6zE8SMBpj5D1qu0nu68%2BPPVudZjj%2BrhV1ssZfT5qhv%2FADIgrj8rWrq5ZNW%2F8xt%2FQjk3WY9VJkpysVWSotOZ6adqUy1JyreoDW84sIQm55XUQPXFZ0HwCdth61XaO7rz489W51Ynj7rIBtlq3e2355DY%2FcQT4QCvA75bM281T%2F2I1zm5wq4wybwAxjbFGKaJNPqqjVKmKdT1qeDDikr1EveSrSpBSbdsejCPDG1UMEYXxrmFmvQMCt44mxK4dk5%2BWdfdngogNqujySsnYHkLEncRXiNgH1f1qu0nu28xtr9m5n54%2FwCuKO%2BWbBHcakPoRBfH9WvgZZsj01AfQjn3NjLHEeTmPapl7ioMmoU5LTyH5dWpqZl3U6m3UnnYi4sdwQRGIXHfFo0IwLksPWq3o7tt%2FGnq3OrleEBrgFvc1YJ7%2FZIfQiX64BX%2FAPq1l%2F4xH0Y5MV5cIniPgXkPWq3ndtv409W51oOP6vnnlzLDe29TP0Iivj%2Brp02y5lT9t%2BeJH9COSge2JtcOI%2BBeQ9ared23jkrnmjc62%2BuA1UNn%2Fg2Z19n547fzIlT4QGu%2F9W0uP3tT3%2BVEcmBd%2ByJVC5hxIwLyHrVb0923jlrnq3OuV%2BEAxAbdBls2Nt%2BkqYN%2FiRFVHH%2FWutry4b%2Fc2qX4%2BrGpsjMj6BmjhnGuLMV5gN4TpeCkya5maclOmR0T4US4rcaUp0gdvlRXzc4f6ZgbL6SzXy%2BzOpmO8HvVA0eenZVHRLkZzfSCL2UkkaewgkXFiDEcScC8h61W9WL5b%2BNPVubP%2BuAYjF%2F%2BDmXPd%2BeZH9CKQ8IBijV1suZYC3ZVDz%2B4jnxnKbNCYwycaS2WmKXqElBdVPoprhbSgblR2vptve1ozPJLJHDGZ2CcX5h4zzMawhQcITEpLzE2Zbp0e%2FpJC1m%2FVF9KRzuTDiPgc%2FQetVvJvtv409W5tH6vzEahvlwj%2BNdv5kTfV%2FYk%2FwCrlH8bK%2BjGk83cE5VYNNHVlrnDL46E4l81FDEmpjxEIt0aio7ELuRbmLeeMRrmFcR4ZapT%2BIsPztParsgiqUxx9uyZuUUSEvNnkU3B847RuIcRsC5bD1qt6Yvtv409W50seP8AxOT1cuGCPPVV%2FRionj8r1vfMtW794q6voRpjJfJp7N%2BYrE1M4zo2E6Bh1pDtTqlScHVKgpQbabuFOK0oUo22AHnjIc2%2BHVGBcB4fzTwDjqTxzhPEc%2BzTpWak5dTbwdeKks9Q%2BUFuIUjbcKABG94cR8Cj6D1q%2B0nu238b2bmxRx%2B4gTsMu2B6Kor6MTL4%2Fa7oT0eXCdXwr1M29XUvHglOCuT9nqflzV86aDTsxqnSjVpfDrko4pPRAG6VOja9wQbcglRsQIw1HD0FcPOJs4pqvvSuIcGVWapVcw6phKkybstMpafu8DvZC0uAgWIMTxHwGdth61XaR3deI2Vezcz9HH5X%2Fh5dI9VVV9CJzx%2BV6%2Br3PEX7%2FZVV%2FwCbGLzfCe%2FLcNXu6qxLNCrN0VvED1G8VBbTJl4BQC76tYaIc5W5jzxiWI8jZDDvDhhnPGfxQ6aliicaYlKR4sNBaWp33zpb9iGwq1vhCK8SMB8h61XaO7LxPz%2BqNzaqvCBVw88vBf8A81I%2FoxSHH%2FX%2BRy8Sf8rKH9GOUIk5Q4j4F5D1q%2B0juu3n53VG51kePzEShYZdhJ7zVln%2BjEyOPqufDy7Xy7Kurn9zHJ3SQhxIwLyPrV9o7rt%2FHnq3OsU8feICbDLgW89ZXf8AmxUXx9VpAsnLtSV%2F%2BcKKf5scmXA7Yj0htfsiY0GwGdtjPSr7RF8t5%2Bd1RudX%2FV%2FV2%2F8Ayc3%2FAMsK%2BhEfq%2FK9r%2F5OFaf%2FADff%2BZHKPV037YzDKbKvFGc%2BNJXAeD5dpU%2B%2BlUw688rS1KyyCOkdWR2C425kkCE6CYB5D1q%2B0mb7eJ%2Bf1Rub%2B%2Br%2FAMQ%2FpeXnq9lv9iKieP8AxF8LLsH%2FACp%2FsRr7H3C%2B5hjAVczDwJmfh7HlOwnPKkcRN0rUhynLSQFGyvK0kjUOdjcX3i15B8N2LM%2FXKw7Sq1LUOmUlbMuKjNy63Wn5pZuWEhO90o6xPZsO2JjQfAo%2Bg9areim%2FXiPn%2Bzc2qOP6vg3OXNh3Cq3%2FABoiRfhBMQAe95ai97daqA7d%2Fkc45WnGVyk0%2FKLUFKl33WFFJ2JQspJHrEeZSiDEcScD8h61W8m%2B3ifnex1r9cErdlD3OF3PI%2Byg2%2FkbxKfCCVwW6PLxPcdVSB%2FoRyVEpA74mNB8Bj6D1qu0mL5ePG6o3OvFeEBnylH%2FAAZm%2B%2BvTUE%2FJdEW%2Brcf%2BI3JdxNMy7ZbmVCzTkxUNSEecpSkFXZ298cqRBW9iYtToTgVE8L4j1qt53beeWvqjcvGKMT17GVcncT4mqCp2qVF0vTLx8m%2FYlA%2BChI2AizRN0%2FwLRTWY9RRRTZ0xTTGUQ1dqa%2FnjoPKbi7qmAsLSeEcX4dmsRNUpvoKdPSswhqZRLjyWXteywjcJUN7bHleOeLnvi6URouPOKDIcCGypV%2BQFx88c3F8DuGO2UWN%2Bs%2BFETnG2JifNMZSzWNvaWEzNnOWbrR%2Fjrwg%2B0UTOXGI7KNxpnpW9%2FTEMNcYOH8RYoouG5XAFbYXWKixTkzD9Ql9DJdWEpUQBvYnl2xzQiWlinWZVkpV%2B4vYxQrqGJWnU56RU5L1FqeXM%2BMIAToKQlTSk23ulQv8AFHlbz8HOCzZVRY0TFWU5TNVWqeSdutvWeKW9MxFVWr7HXvF1lXiLM%2FAlN9qzKpuoYeqSpzxBOy5tlbRbcDd9taTZWntF7Rw3M5d4zkH1S09hOuS7qSQUuU9wbjn2R15hnjRwrOUplWNqDWGKyEJTNinspelnnAAFOpKiCnUbq09hJi9fVnZW6iBRMVEWvcSiOfd5ceRwW86WaN3ebjTcuHTEzl9u3KYziYz1x6fsjfvE3C91%2FG1V5S4kVgfFKbg4aq5PcJJy%2FwCKKC8D4sSd8L1oX5fmB3f%2BTHcY42cpUlKVUfEqnD2CTbv8i49SON%2FJ1sWmcNYnK%2FtvFwL%2FAMuO1TpTpXl%2Bro553Naq74d5Sepwd7TcVHlhisn0SLp%2Foxt%2FhdyXx3Vs26Diebw7U6ZScNTaarNTk5LLZbUW0q0NIKralqUoWA88dLJ44Mml7jC%2BJrHlaWSfxLinMcbWT6mtSaFixxSfJZ8USL%2FwiuwjXxHG9KsRudpdJuHB4cTTnGc5ROqeSI2L3anD7tbU20VzOWvLz%2FYu2dXEBJ5OVOjSFRolSqblXlnZpKpWZQ30SULCLKCt9ydrd0a5TxyUJHk4FxGf8fZEaJzjzRqOb2NH8VT1PFPl0IEnT5IL1GXlUklIUobFaiVKURtc%2BaMOp0qhyeaR5STcKjawn4M8K7ispxKyztsvwsqpjXty1TlqjU17fFLeq0mbOqYh1Snjjw6Qn%2BwLEYJ5%2Fm5iwiZ3jow0yFOe59iZ3T8BE8xuPNHOhkJXbSyk6ee0W6syjLEuXG0pTpUlJ285jpT8G%2Bj2WUWM9KrepTit6pnPhz1bndOcdEqmeHD0%2FTqASZqvUyUrElLPvDruBSH22So7BRGpIPK%2Fpj561PAOL6DOu0%2Br4VrEjMsq0ONPyTiVJPdsLfEY6ayP4qKRgnBkrgjMCl1Kbbo4LVMnpJKXVGWvdLLqFEeQSoJUDyIuNo2T9WZk2U9elYr0p2A9j0n4hr5R5LB6dJdEK7a5Xe6fG2U1TMTH2RnExntiI1TGeeboXi0uV94NpXVlOTgtVBqwUdVNnk%2BmWWPyRFWG66kajTJ8Dv8AFl%2FNHd31aWRyRpeoWI0ACyQaa3y%2B62j2jjVyJQgdNQMTrv8A93Db%2BVHf416TRH6tnnnstTubD9vxs80b3AqMM4gdUEtUapuk8giTcP4hGV5b5L4%2Fx%2Fium0ak4bqjSFzTK5mcmJRxqXlmA4krcWtQAsE325nsjtJnjWyGVcsULE6UggFQkR2%2BhURXxrZJEKSJLE6Ufu5EkX77ao1r1pLpXb2NVnZ4fwZmMs%2Fwpy%2Bzgx7V7Oxw6mqKqbSZy%2Frws%2BzbzWOVeEZnG1QZqE%2FKy03LySGJWZDbq%2BkVoSRqNtgLkRpQcdGENR6TBOKFW%2BEH2d%2FjMax4jOIqUziZp%2BGcM0p%2Bn4dp7pm1LmgA%2FOzNrBZQCQhCRfSOZJJNo0pJsS65trX10qV1kxq6NfBpcrTD6a8Ysp%2BNmZnLOYmI5InLl5ftXveM2vxmdhVq%2Frwuuvq5sIKNhgnFSR3iYlz%2BWJlcdeE2QVNYHxY6oC1%2FG5dJt6dUczexkn8CVb%2B5jyVGRl2pZwplUJNuaU7x3%2F8AxlgHJZz0qt7V78Xyfnz1bnf9Qmvd3yDmWpCYck2ccYedEumbdK%2FF1PJIQHSPtVpAJEfNzEOXONsJVN2jYkwnVadOy56N1DsqspJGxKFgaVpPMKBsQRHSnDzxPUTLnDhwNmBJT6qbJKW7SahIth1xtC1a1y7rd90hRUUKHK5BHIxtw8ZuRC0lDrdfcSBYBVJURbzXVtHk8GsNINC7xeLtdrpNrZVVTNOWeWXJOcROuYyzifBycvQt7S6X6imq1ryqy%2F8AuHz7VS55vrOSUym3eyofkiQ02cPXMrM6fMyr5o%2BgKuMTh2VvMSNaTb4S6OCBHpa4xOHDowHqfWy2rkoUlIB9UeinS7SLL9WVZ%2Bmew0Zu9xj6aeaN756Kps4pPVlpv7wr5ouFEy%2FxfiyeRRcP4bqs%2FOzY6NlpuVXYqOwuoiyR3k7CPoB9WBw0E6WJSr37B7Djf0WiZjjK4fNOll2vsdIOt%2Bda0i3cbGMVppVpPXRMU4blPhzqnqiiPbC1F3uGec2sz9kR72W1vFD%2BSeUMrUKqqbnEYUpEhIPsyLw1OOICGiGySAQFE%2BoG0am%2BrlwJr3wti5Q%2B2s18vWjXvEhxLUbNOgS2BsDSdQlaMJxE5UJmcaDS5xTYPQtpRclKEm6iTuo27BHOvmjm6NfB3d73c5vGN2cxa1VTMa8py1bYjlmc59DNe8XtYtZiwr1Oz08cWXykArw1i1Kr3I0tc%2Fu4lRxx5fk6nMLYwBTyIUyb%2FwAvaOZhRqclpAcl2gQkE7eYR5n6bT0oV0cs35J%2BDHe%2F8Z6P%2BTnpSw04zfKdtT6IZVZq07NPBjeMaCqqyknNPuywROqs%2B0plely4ST3x818wsrMZ5f4pqtEr1An2wxOPFmaRLqUxNNKcUUPNrAspKgQY3Pw08RlJyjlJ7CmNpWcdoM7M%2ByErOSTXSvSMyoBLgUj4bSwEk23BF%2B0xv1PGLw%2FEaXJqsKSk7J9iHQn025R5TDrljehWJ3izuF0m1sap1ZZzqiZmnXETriJynOM9Wfp27a3uuIWVPx9eUx1eGMnzzcpVQaQlbklNJSu%2BlRYUAq3OxtvFJVNqABUJKbI8zKj%2BSPocOLLhlbbQhZm0NtklCV0ZVkkm5sLbb7x6mOLzhpSCVPz6QRpOmkKG3dyj0MaW6RTtwyrnq7DU7lw%2BPpp5o3vnGKXU1%2BRTptX71lR%2FJFZrC9fmnky8rQqq%2B%2BshIaalHFKJ7rWj6ODi44YwSG%2FH1FIubUlX0YmRxjcOW62KjVmCOWmlupJ%2BIRSvS3SX5uGzz1z%2FAMFoutw5LWZ%2ByN6vk1TcSZT8OdGlsUSM6xM4doszUpqnsrPTIbup3ogLga9O5HeYwdHHNlyE6k0HGHWANlS6bjzHrmMfz84uMJ4swPPYDyvl6i4a0gy9RqM4wqXCJU21ttJJ1KUuwBVsAL98coRztHNAoxaLa%2FaQWcxaWlczERq1cucenZnryZL3i1VNcU3adURk7RPHPl0Rc4fxSfMZRv6UaVz94j1ZvU%2BVwtQ6HOUuhSkyJxzxtaS9OPpBCFEJ2SlIJsnc3N40rEFR7TDtCMGwm8U3qws5mqnZnOeU%2BFz7e%2F3i3p4NdWpJpT2Q0mIad4AKHbHrWkiEmJgLwAvE0AiSJ4kgJ4gQTBO8Rse6AhpgExGEAN%2B6IggG5VaAuTziBA03tAZDS8eY1ouHqnhOhY1rtKo1ZWh2ekZCcUy0%2B6kWDhtuFWABIIvYXvYRvfNrjTxJmnkvh7LNNOrVJrUi9JKrlXRUyBUESjZS30ZQQtKlq0LXq7U9t40BRJdl%2BVcU6lCj0gA83m9cXM0%2BXTzYSPQDAebFmMsW46qaK1jPEtSrk%2BzKtSLMzPPdI43Lt30Ng2Gw1He1zfe8Y%2BecXKrNBmotyjKEXmOjQmw5KWoJv8t%2FRG%2B18EWOktJdRm3lK8pRsUoxKkaT6SneA5yhHRI4JcdFSkKzXynC0mykjFCLj5IlHBFj8atWaGVJ0nSrTitGx7t0wGqsnEJdzgwA0q1lYqpg35fohB%2FJGVcV9zxO5q6uftpm%2FwASY2hl9wgYxwxmBhXEtRzGyvfl6VW5KoPtMYlQpx1pp1K1BIsOtYG2%2B5jUvE5U5CtcR%2BZ1Xpc03MSk3iabWy80oKQ4kWTdJGxFwdxAatiSKi%2FNDRt1tMB53BflFum5Rt9CkL%2BF1VevaLsW4oONQGrZ6jz8lMKYdl1m3JSUkgiKHij%2FAOpOfcGNsIY3uIpPtv8A2%2B0BqvxZ0fAV9zEpacv5CvijZbjZTstIPpAMeKbCUeUhsfwRAYB0Tnd8kTNy77ytLTK3COxKTGTTk0w39p8Ueek1L88FNoXp6VpxtWnbsuPlEBYPFn%2BfRK9cNDo5ojIuk19Ra1aY801LtoI0wFnCFn4J%2BKBbXzKSPjjqvhHmctZjD%2BIqNjj2BTPs1BiYpy6mpKFltbZSsNqPcpKSfTHRJwzlYpsLJw2pAFx%2BbmCgd%2B0B8yikjmbfHEyUXF%2Bz1x9HqtJZDUxBmqscGgjmp15tw%2FEnt80a%2BxXndkHSKPN0ij0ykzhcZdZQmUoyCkFSbatZF7i9wQecBxA42UdkSBJPIGLpN9G2%2BtDYUpGo6SdyRc2JPfaKaFrQ4lxs6VQHiLLwTrLC9PfbaJdKvtT8UZYip1RyTMlNTzzkopSVqZJGgqB2NrRWYdb%2B0T8Q%2BaAw3Sr7U%2FFEQy8ryWln0JjYcuAtPVQ38Q%2BaL5RGULnEIfQlSVJPV0jnAalRKzJ6yZdZSOZCTYemKzUpMLNksLPoSY3qinSdygSoAPMA2CvT3iPNUKdKyMuhbbASrV%2BMQEuQuYOM8lp2brlATJqXVm0MzslOtdIy8yk3TuLKQsHcKHedo3%2FK8dmZEoUhGDMMlKNgC49HN0SQHUP1fOY69zgjDafP0z34oDj1zECf%2BJWGirvK3%2FnjmGGuA6hTx85iDysDYaVv2PPCCuPrMAm6cB4dA7une%2FH%2FAKo5e1%2BaKkv746E2gO0Mp%2BMjGOYmYlKwRPYEo0m3UWZ1an2Zt0qQpmVdeTsraxLdvXGJy%2FhAMfvy7T5y5w8nUnV%2Bin%2BZEc7syLReQUOKaWOS0LKFD0EEERJNyLDcpML6P7EnUn4xAdMU3jfzgqwW7RspKRUUy4SH%2FFhNuhBPaooB038%2FdHsXxrZ4tt2VkhJNL%2B26Cet8WmMR4U3c3USFRXlnNYZZl1V9hKk1YTOvx7xRehV2OTXRa0%2B%2BdUqItvHR6hxiLbuKtliD%2B6VNn8cBouo8budlNbTM1vKelybFwlLkzLzbSLnkLq7TFNjwhOZMs2ekwBhd0XvdUxMJiTiidzxGDak3mNMYRmZJM%2FSm55VKE10pUUuqk1ILvvSkDrhZRdSSQFRp7KDGGHsMTNRlfcn9vWMKqhMnh2XmVBclLOq5qcZ5uEkjlyAgNs1bj3zDqTK%2FEsB4Yk1rHVcS%2B87oV32Nrxzli7FddxpXpvEmJqgudqM6vW%2B8rYE9gA5AAbARuTi2w7hbDuJMLJpdDpVAxLM0RK8U0mkn8xsThKSkti50nyrgcwBeNDL3gJ5FTaanIlYVpE0yVW521pjuWcl3lPuIQSjr6rJ7f%2FzHC8unVPSqe%2BYaH8tMd7ltxm7JbKXGwkKtubefvi9lP4c%2BiFLfXZxPnn3PB0SkBVwpZO6tok0EqSA0sX3NxyEe8TXSJ03TYbG3KIBCb6mirbygo7WjaaSi2w%2BlZWR7ysDUDsdv994rPNvFqzSQra6QeV%2ByPc1LqW2CtQ0WHM9sSvtXaHRX6o2Pmi2ZUsszK65RSFsjUBZYG3xRahIBSXHF6lKVurVvuO6L%2Bph9TOlZNwCLk21f798UXJZwjrjZYNz54ZqxDA6th1pRceliUm%2Bogp2MYdVpNxDaumYAKe0dpEbcmZBSkhItZV7pP44xaq0gLaKnUFJCVaQRzhlmtE5bWn64s%2Bw80vo9WlPNPcVAH8YjHJJKisBI3tcekRsDF1JPsbMuNt%2FA63mNxGK02UGv3zUnfUnT6YrVTrZqJ1NCYuSRXqylXMzLJPywxFf23TX9%2BH81MVsdJKMTVzTzQ82R6Yhik6sXzKu9xB%2FkCNOra2Y2MsphvTX%2FAERiVdSdXxxllK3p74%2FcxjVdQLiISsLJsdVto96FNFrUE7x5Ukg6dMexooLWkJ3gPE%2BE32jzDUVbR65oAHaPM2Fa9oC542%2F5nO29Ma5G%2FwAJQ%2FJFxbb1rTfbqj8UWzHC9b1IG3VpjQ29KouygQlOkgHSLEi4vbtHaID6K8EmXNAyFydrvFBmU2JRdQpy1U5t4BLjNNQdyi%2FJyZXpSnt02744gzazMrObePq1j3ENQbXO1maVMdEV7MotZtlA7EoQEpAHcT2x2nRvCYZbPYbp1KxVkTPqelZNmVmJWWmZR6RKm0BILSHhcI6oIChcX9cRT4Qrh5WdTnDe7fv8TpZ%2FoQHN%2FCHQ8pqvmJOjNPPKq5ZCSpqpimVGl1UU5195awhaDMKBASlNlFoj3wbdkadrzNOla7UZSn12Xq8rLTsw0zUG09GJtpLqgh7T8ErSAojsKjHeLnhAOGl8aZjhmU4kHYKp9JI%2BVMehPH7wwFFzw3KCu406mfNAam8HvxDS2V2ZzmWmIKxLIw5j59tpvxhxPRSdZSkpYcUDsEPouwu%2B1yi8YDxt8PwyGzamZWjybiMKYn6Sq0AkfYEFXv0mT9sy4SB%2B4UiOjn%2BPXhdfA6bhnWdCgtJ9j6XdKhuCDbYg7g9kaj4xeMfBnEXgijYNw7gCo0tVKqS6n4%2FUX21upWWuj6NsN3skp3Vc7kDaA45UmCdrRUWIpwGzcg89sa8PWN1Y7wMxSZmcckXqe%2FL1OXLrDrDunULJIUFdUWIPeN7xvNfhE8xXnOkXlHk8r7bVhcE39JVHIaDaKqVbQHW6vCG5hrQrRkzk86QNRQMLi5SDcgWPOwNvPaN2Z8YkZw%2Fn3gHimpuaddwPgLHOCGJSQxZQ6QiqmTnEN2VIutLQpICgQdxe6CPgm3zkZWE2UDYiN65FcV2NsmKLUcCTFGo2MsBVlalz%2BFK%2B30snrV5TjCrEsqO5IsUkkkAHeA3%2B7xVzFaprFGnuOPMCYcq9GmWJySXlrLOJcn1AIRKgBrVodBUBa9rDcX2u%2BLc0qzwccOmUmT0%2FhbClfxY5IzNYrFJxFIicapjb69SEpTfqOXUR6AqNVSHGLkpl%2B%2BuvZI8IeGMMYlWVqRU6hUFzwlVKHNpBvax3ttHNuP8AMTFeY2Jqhi3GNbmKrVam6XZmZfVdSj2ADklIGwA2AAgOj1eEHxczfosiMmt%2BdsNgXjyzfhCscuUurUqQycywpKa1TZilzcxSqUuVfLDyChQCkEdhvvcXjk0rWVHn8cQUVX7fjgC1aeqjdPLzjzRSieIFJ5wGVZUNJfzLwiyrkvENMH%2FqW43T4RN7peLrHaf1N9pP%2BZRGgMK12YwtiSkYmlJdt9%2BjVCWqLbTpIQ4plxK9CiNwDa1%2By8ZlxCZtHPTNzEOapohpHtgeD%2FiJeDpYshKdOsAavJve3bAa1iINoaYAW7YDenDrxSYu4d5LE9Pw%2FhPC2IZLFrcsifYrrDjqCGArSnSk2UlWo3CgeQjZI8IHiInq8O%2BSrfmGHyR8UcjAkcorIUYDtTLzj1KsfYddxdkXlJTaT7KyqZ2o02iliakmVOBKn21nZJQFar9wMZ1mxX65kFxN5v1Op561DLNGLm5OuYemG8KN1yTxSxoVZIUoHo1tlRR1ed7nkI%2BfDbnlIXpUlWykq5EdxjpPLjjEmpDL6Tyezzy3oubOCaXZNKl6o8WalS0WsEMTQBJSBYAEpUBYaiAAA2RmRm1UM48JYiyjwrxdzWYdSr7UlJ0fDz2WLMkKwt5adaC%2BhILCmiCrV2aR37bA4n%2BJ5rI%2FFFHyfkctsvscO4Yw%2FT6fPTuIpLxp5qZDQC2UKANkpsLgnmY00jjUy%2Fy4pU6xw2cOVGwJV59ksqrU7OmfnGAb7tKVfSRfbe0csVqu1Suz0zVqrOuzk5NOqdffdVqW44o3KiTzJJgOn%2Fq95oAIc4YMknAk22oUWTMDjfrGNsssQZXSeTWA8KUzEbzL845QGFy6luNLCkqKB1Sra1yL2jmbpD2mJFKvARWEr5RRKQmJrmJSL9sBLE1hEQLRMBAQSLmKyU%2BaJEjeKyRAVGUAmPQoWTtFJsWtHoQnXAZTR2tFMQtXakxf8qx%2Bb66rtTQaqfV4qv8A1RZpIBFLbT%2B5VF4yxYemJnETMv8AZV4dqoR6fFlWgNT4XN5yXPmQPxRt%2FhhTfiowD5sa0r%2F71qNdYdw1PyK2ZuoKlWQgIWoLmUhQt2gXjYnC4%2BiZ4pcAzDataXMa0pSVJ8kgzze8B%2Bg2EIQCEIQCEIQCEIQCEIQH5%2BeOA6uJ%2FMtP%2FwC01Q%2F0pjQ6WdVjblpjf3G5Lk8UWY%2F7rEtQV6ulMaTaDSZdKphQShsh0ki5PZYAQGSSCnAlTbKwha0pAWRcI3HWt22527SAI2%2FmPmnQEYbk8nskZWepGAKXMs1KYnpxARUsR1VBC%2FHprn0aEuC7bI5Wue6NP0B2n1F11qkza5mYSx03QqYLbmlJ61r3vYb7dke6%2Fn5c4Da2LeKDOfF%2BJMK4wmK9JU%2Bq4LddmqSqRlA2jxl0BLzzibnWpxAKFC4Gkm1r3j31jNjLQZnYBzowdh2aw%2FVZWqNVTGVJQgGTbmUujpH5RfNSHG1OKIIuki0aYgL3uOfaO%2BA%2BiPG9lRM5tZXS1awYTPTVEWarLBj3zxyRdb5oA8ojqqFr7R8yGKm5SFKlHGdakmykm6VJPcQdwfNHYfDfxhvZX0uVy%2BzAp0zU8LyoKafOSo1zdLQbnoijm6zflbrJvbcRu%2Bp13gazAJxBVKnhBbryg46ZtgNOhXbqTYKv384DizhtyqrueWZtHW1T32sO0KcZqFaqAQehaQyoLQyF8i44tKUgDe1z2R0T4Q3F8u9iHBWWsu8hU1QadM1eqISblh6cUOhbV3KLaCu3YFJ74zPFnGJkrlRh04dyKo0riCoSxPijbUp4rRJFdt3nNgp9XclI3PNQEcO4hxBW8UVuoYjxHVX6lVqtNOTs%2FOPG6331m6leYDYBI2CQANhAWxRtAKJ7YKG8AIBcwuYjpENIgIXMNRiOkQ0iAjHplEzAmGUyjUw5MKcQGES9%2BlU6VAISixvqKiAPORHmG5j0ysxMSczLTsm8pmYlHm5lh1HlIdbUFIUPOFJB9UB2Ng%2FAGJOE7CrmYMzg6q41zixTLGSlJaVZdnGKC15RS%2B8m5UU2TrtcqKQhOwJjjifmJyYm35mffW7NzDzj0y4oWKnVKKlkjsOonbsjZbXFLxEy0y5NsZuVtLzqy4tYLYJVzvskAbxrCZedmpl2cmFlb0w4t51Z5qWpRUpR85UST6YCUEkc4jEBtEYCSI3MT9HECgCAgeW0Q35xNEQICERc2l3B%2B5iMRU2l5BbKCUnmRziM8kO5OIjMfJnAWZOGpzGuTb%2BL8TSOHaZUpGfM4GWGk6LstqTfrFKkkg2NowugZnY2rORub%2BfeE3vFsxK9jWVkK7PSCC7M0ehdGlTLUsCCUoPIrt3nnHO2PcycXZnVqXr%2BNZ1ubn5Sny9LZW20ltKZZgENJ0ja9ibntifL3MnGuVleXiXAtbXTp15gy0wnSHGJpq99DzauqsA8r7jsMSluySxTjPMTg5zUnc2qrO1Wl0Cdpr%2BEa3VE%2Fms1BUwkOSzbhALibEj%2BERfaMv41qxl37bZvCCsratP47XQaW9L4nYfUZeTYt1WlNC%2BshCVA7fC80c85l56ZmZuyspTMdV1qYp0ivppenScsmVlEO8w50aNiodhPKM%2Bl%2BN%2FiHlW2fFq5QQ6whCUvOUVpa1FIsCok9Y2Av3wGTcF2MMspDHdNoM7ghUnjASFYfXi5%2BrhEuJYNFSpfoFEBN2xoue0k98aRzIxJlvimuylTyuy%2BewZTiwlqalXqh42JmZKz7%2BlXwEkKSNPpMYdOrNSmX5udQ267MvrmXboFi4tRUogchuTsOUSA69SH0a0K6qk%2BaLjqLh2pcrkTm5hvAebGQk%2BvGWIqmp%2Bh15663qcy43pGhsXQpIUFKK73Tqja2CMO1eSqvFhgCoYjdxLiR1xmdXUChKH5hmYprhZSUp2Gm3R2HLbvjm7DvF9n%2FhihSuH5LFspMMSTQYln56QbmJptsJCUp6VW5AAFr9wveMJwlm9mNgnG8zmLh7FU2ivz6lGoTT5DvjwUbkPJVssXOw7NrWiIjJExm3jhdxct4NfFs8%2Bh5hVTxCXKR8AqmUz0sWlNg9y2XPuTHStaqVGrcpIcWl2PF6dlJU9CL9czM3pWCD2aVBaPXHBOZWfWZebSJGTxpWpZVOpq%2BllabIyiJWVQ7a3S9GjYrsTueVza0UkZ6ZnIyuOS%2Fs837UC14sZMS6A70HS9L0XTeVo1729XKJMnceRMixmLhfInPqu1EuzuD8JVmm1XpR74%2B8pIbcUpR5KQWVKP7%2BPnpijEL2LsR1fF0wVF2u1GaqatRuQHXVKSPudMZVhvP7NjBeCZ%2FLrDGJWpKgVJc2t9nxNC3R4ykJfCHTulKgL2HIkntjXfkNpbR1UJTpT6IolDSdeoq2iV1xI2BhY253iUpv2QENd%2B2FzEOjMNJHbAR1w1xLYwsYCpGXZS0aYxLmjg%2FDslXjQ5qoV6Rbl6mACZNwOpUl0X2KgU7A7EkA84w8BW28V2V9GpLocWhTa0rQtCilSFA3SoEbgg2II7RAfUmXrNPxXxD5gZXSOXNXwpXnsLsMqzLlZZCHX21JbFgSNKVJUsBNrlRbWDbSmPl1UZNNNnXqa26h0ST70r0zZJS90bhR0gJ56tOq%2FnjZFW4oeIau4cewjU84K%2B9TH2yw4kOpS6tsiykl1KQvcbE3vz3jVoATZCBoCNkjuERMZiKiQbXVbzRDUqxsn44K1FW4v57xT629yYkRLi7xN0irCJOjVE%2FRqsICRTqidA5QCiOZETlB3A5HnEOunYjbe20BMglXOJlXHKJEoWrcRNoWIAlaoipSrxLYxMEkwENcR1xKUkQ0mArN781xNMTs3KU2pqkZyYlVv0%2BYlnFsOFtSmloIW2SNylQABHIjYxQiZfXQptfWS6kpUnvBFiPigOuuM5TNOxbkLOOoQiXlMMU511I8ltLcxKrUfQEgxtXEeGMTTXhIsNYqZpU0ujzGGEzaKihoqZ6ES7yFjpBsOutva%2Fwx3xwrirMXHePG6Q1jXE03V0UGS9j6d4yEXl5bazYsBcdUc7nYRkUtxB51yWDTgGUzMrbNE0dCmXS%2BNSGrEdGly2sJsbWCuVhFpjMeDOOrU%2Bu5uY2rFIcQ5Izdfn3JdxHkrT0pGoeYkE%2BuMLue%2BJ0dHo0I6qUeSmJSLwiMhCETWHdDbzRUSg2iJX54aREqkwE4VftidF4pRW6RfR9mnUPkiM8idbrTAeIMAYd4IcPVXM%2FLhzGVGGPagw3INzXQFmZKlBuYvcXtYpI%2FdReMlc26VnTxE4WpNMwVTaDQ8vMH1heAMPPuBxKquG0lDjnwSrTfSkXta9ybxyk%2FmJi57LtjKhyppOFpWsuV%2BXk0tAKTOLRpUSvmpHNQT2KJPmi1UirVOh1aTr9Hn35KoyDyZiWmWHChxpxPJSSOX5QSImdaHV%2FCbmlxBY84gmMIZi1utV6j1FM2nH1LrcqfFJKXDSiolKgAyUr0pSL2UCefOLphmvZTYU4OMDDHuXM7mBh0Y5xBK0qRknClxlTc1MdFM60kEJ6Pq3%2FdCNI4w4s8%2BcdYemsMV%2FGgRJ1BvoZ5UjJtyr0039o44gaiCOcSZZ8U2bWU2D2sDYQmaIikSbjrso1NUxDq2C4rUtKVE%2BSTvYiIiMkrRlXiHLjB2Jp97NLLScxBJzLkv7HMqnjKrpbwmkqDjl7dIkIKd%2F3F%2B2Nu8cGLMsanmPiTDdOwa3MY1k5ynuzOMGKl0jMyx4uCqXDSSUkhKkJ35WJ80aGzLzMxXm5il3GmM5yWfqbsqxI3lpdLDSWWgQhIQnt3Nybk%2BoRiujo20I%2B0iUTGbaWXeEJvA0pJZ7Y3yOXj3L96Vfkmh0vvS5hxzo0LGm51ocSpGhQ5q37I7Mr0s2zxX5GY5mqvMt0zE%2BF6vSKTQpuXS0aPMCTQ7ZCeYK0HQb7haNPK0cV5WcRubWTNMfomB69LCkvvrml02elkvsdKq2paQd0FRAJsbEi8WjGucmZGY2K5PHGLMTPuVymlBp8zLe8iR0LC09ABsjri5Paed4iYzIjJ15wyyVRkuMXPetVaVXLyMiZoz762yltaHJtDyLqOx96SV%2BiI8NVIpmdXDDScCB5KVYMzGanW9gR4s1UPHmUJHYFNPLSBHOmMeLLPHHmFZrBtdxLJtU%2BoN9FUFSEkiWfnEHml1xO5BGxAtcbcox%2FLHPXMzJpqpsZc1iUkGas40%2FNNvyiHwXWklLa06vJISSNue3dFoS7CYrLPExKcQ2Wz08hZkMwKbO0rpVFTTMmw80DptySXJV6%2FncMc%2BcdWL28TcR9dlJWyZTDklLUlpF90LKS86PunR8Uazy9zgx5lJV6jiDA1Tl5ScrDQani9LpeQ%2BnpelOpKtr9ISq%2FnMYtiXEtbxhX6pivEk4ZurVqbXPTz5SE9K8vyjYbDkBbuAhI8Ou%2B9%2BfZEpKlcolCFK3vtE4BG0QIKCuUSpKuZiZZJFgYlBPOAnhC474XHfAIvGG5mcaq9PRLTkwymYqEmy82y6pHTI8YbIQoA9ZOoA2O20WeKzL7su83MMOFDrLiHW1pNilaVBSSPQQDAds8QlQkqV4QbLScqykNSbKaP0ilkBKFqdmUtk35dcojYPiMjmRxJZi5O5i5E4fdwXJUdM87iWYpVp5c2WmtT6ppQt1gtwICSCgS9zcXjgDG2O8W5lVt7EuO69NVmqzDLTDk3MEBwttkltN0gW0kki29zeMqrPEfntiHCXtGreZ9Ym6OppMu42paUuvMgWDbjoAWpNtiCd%2B2IiMhr6aal2JmYlpWZMyww%2B6y0%2BTcvNoWUoXftukA388UIibBNk2AFrAchEtx3xIHlEtj3RNcd8TADvgJLkRKTFQpB7YgUQFO5iaJggeaJtAgJLmFzE2iGkeaAkJMToueYiBT3EREBQ7oCaK0i9MSk4xNSj7jLzLiXG3WzpW2sG4Uk8wQdwRFMIUReIosF2uEwzzHT2NXlS%2Fg8sCTLylOKXit9x5alFSnff5tRJJ3KiQbxuOiTrOWWTmQlCxdl9N5rLqs9KCQnZeVQsUFKwl1lTagDq6LpAAo2uEKueqI4fmsd4znMEyeXM3iWcfwxTpgzkpS1FPQMvkqVrSLXvdazz%2BEYyPA%2FEBnRllQU4bwVmJU6dSE6uikiUutMatz0YWDoBJvYbX7ILTGbMuNPD83h7iBrYn8UvV16qyctUkOvBIVKsrCkolQEgAJRpOntKVAncxoe5i5VqvVrEtTma3iKrTNSqM650szNzK9Tjq%2BVyfxDkItikm%2BxEREZIySKN4lBsd9oqBN%2BcSlNjEoSnntyiZI7%2BUFt7jTyip0dk9blASXCYi2dTo7hziGi67X2idTZTZQPp88RKHVXCTUMPUnJLPet4sw8qvUKSkqa5VaWl0JM7LpQ6ShJJFiSR2jlElHzlyvzExRltkZhnLKSwRlnM41k6pXWX3wtc%2FNBRLSHDcgNlzRck72SOUaCwxmVjHCmDsWYBoFTbl6NjVphqsMllKluhonToWd0bEg25iMcv73ocR%2BTluCLcjeGREZOqsaZr8VcrxaqozFXxLLVOXxKinyVBZlymmqpanwlIW1bQtss3JdJ2332tG0Ojy1wTL8WSxghOIMGU%2FFtMMxh%2BniyZgqlGy%2By3p2Gl5SjtysY5oluMXiLk8OtYaYzDX0LLHiqJ1cq2ufDfYPGCNVwNgecWXKriBzOyYFYGAarJspr8y3O1AT0oJouzCQodLdRvrUFnUre8WickvI%2FiXLiXzamsVVfKCfGCHJh59OD3ZtbDhZLWlCA%2BednOvse2143zxLY7yVncscAUSVy4cqMzU8CqOGZxmuEe1YLcRZpYST0q0qTcg87WtvcaEzXzyzMzofpYzCrUlNtUUvKkGJSRRLoZLunX5O6r6RzO3ZGBlGhCtCUJStV1JTtc9588WGbZeYKr1YW7mQjKV%2FG%2BFsGTSX6%2Bwi%2FQKbSjWplwpOoXQdXVBIAv3x1VmDUKBjDI7IrN7C8rNYOwVR8dUbp8IvNIRLpQubU2l4GwUotq1KBvpUlZVzF45NyyzazBydrLuIMva%2BqnvzKA1NMOIDstMpBukOtK2JFzZWxFyL2MXHNPPXMjOlMpLZgVaWmJKQK1S0hKS6ZeWbWoaSvQnYq07AnkCbWiJjMdZ47o9ad8JXhVSZSbU2mkszaHg0roSy3KzKHuty2WtIPnUO%2BJsDz9IzTxpxYZJyc2y3L4kmFTctMp8lCnWfEZlYHbpdbbUfVHO1P4xeIORwyjDCMYyzwaZ8WZn3pJtU622AAAHe8AAAkX27TGA5fZn4zywxG9i3BVXEnVX5d%2BTfedbS8H2XlhbgWFXCiVpCr877xGQ7raxVKVLiGxPw6dOn2NXk%2FLUKXb%2BCidbYJdJHLUWn0G3cmNGcZ6pfBeF8ncjpJaFJwnhhD0wW1XSXAhEslR%2FfBp1QJ%2B2MaTl84MwZbNFzOZiuJRi52YdmXJzoUltS3GuiWC0erpKLC3ZYRbMwsx8X5p4kcxfjeotzlTdlmpMuNspaSGWrhCQlOwtc%2FHETCYYssK1G3KJVcu28VkqTyCbxI4pSfgiCFNCL3JVFRSLqABvESE6dyLmDaeZTtASqZIOxhbbQPXqibo19JfpIFpaUlXSavNExOSYnJKFHlGXZWYExjmfjiQwRgSYdlqrONuvKmUTK2USss0NTr7ikEEtoGkkdpKRGIBJMXzCWLcVYErAxDg3EE5R6j0DkqZiVUAtTK7a2zcHqnSm48wiZjNZ1Fn%2FACruQWSM%2FkLlJhGuzMpOlqcxzjF6nrEsekcaCh0ltPW971WNm2wBe6jHQuVMjhXClWwbgjK3G2F6jg7DVDnVztNps6l%2BpViouqbCpxSU3HRpOq6ib6lpFrRwLiHiHzzxbh%2BbwniXM%2BsVGj1Bky05JvFBbfZKtRQoBPIkAm28YvgbHGLctcQDFGXtdfoNWTLrlfGpRCAotLIKk2Uki10pPLYgWiMlclfMfDreEcd17DCK3Ta2KdUX0Co0t7pZWYC1dJdCu0p16FDsUlQ7Ixde0VyuxUdKQVrU4rSLXUpRUo%2Bskn1xTWgr5RXIyUwSo6T2f784gs6dgCo8rxOptdrCwHaOwxKGSvYBV%2B0RKEiQ4ny7WiJIPI7RHoSnybkROhtw8yAICVKU3uYlWATziv0IES9FvcQFHTbsj0SlQnJJSzJvrZLiShZT2p22%2BSIdEpWwtEnQG%2Bom1ouPairVJXlTTh0%2BiKM5OzM0EofeU6lFwkn5YpdfkLWiVaLbiInWJ2iADbtj0yAlPHJdVQRMrk0vtKmkypSl5bGsdIlsq6oWUagknYG0eNFwdzHskEyblQkmqlMuy0i5NMNzj7SdTjMupxIdWkDmoIKiPPaInUmXduQuLMD53V6pYapnD1hzD%2BTVFohYqM%2FVZZBnW521z%2BaRsbNgqKgbpI1E8gbBw74bpctw0zlewNSsvajVJnHNRkqVUscBroE08TCWmg44bHpFICClPwiokR7sYZxcJWJcCyuUFCzarmD8Ey35nmJSkUN1Ls8xq%2FTnVpudVtS9rrPPbaOfMIYc4WMb5dTWE8w8b1vBOKpWsOLbrrjLkzJ1ilh1XRaZYHo2XujKQeSkqTcXBsJic1YhR4maLj6gZoOyOZWBMMYWqgpsumXRhdot02flklYTMt%2FbLJ1JWTY9QXAjUi%2Bcbr4rs6cN5z43o85g5M0aBhqkJpUk9NNFt2ZUV6nHClW4TdKQm%2B53PbGk%2FLgZIE98QYecZWl9hehW%2BlUFNq7IlQN7JimeSXq9k6g2kpRNLI9Vt%2BcU5ipTr7KmpiYW42o3KCLi8U9G0QKL7aVfFEiTUFKB5W25x6EBOkC%2Bq3n5xQLRRY87G3LlFWWBVYHayu7lvAdQ8PmYuFFIwLlHlhkdT6zi2oT6VYwrGI5dt9pyUVdUy40Uk6EJFgkKA2SBuVRtHCXD%2FlP9Upm3WsL4Tk61TsESVOTS8PuOaZFmvTLK3Xm7nZKEaUbKJCC6ofBtGJZFZm8N%2BV%2BURpUpmg%2FhjG%2BJpPXX6ymmLenZN9f6SwSkoSltIGi1wSdR3jGsqMzMmMosYZj5XSOY1bq%2BXmYdGZa9uj0svxiVrC2HEPOOaeuUkO7rtspO%2FfAScU1CxknAOGMVYqymy6lXn5wM%2B3XAlU6aVcvq%2FMsywEgDUfJXc2U2QDvaOW3F9kdGZl46yuwXw24d4Z8qcbKxkmXqiqrU6y3LqYYRZ1TnRoQobFbigQBySCb7gRzmtveLQmFIntiLa3G19I31VJ39HniJQQoDviboj3RVD0rrFS1%2Fo5fxj5opu1Gdc3W%2FrBPLtikWQNiNzEOjtASarmKjabxS02MVW1WgOisk8xsuMPYaw%2FgfA2QoxxmnWqi0xUJityiHZNTC3PfSwQSUoQ2ALqSLXUpRNgIyHiAm8rOHPiSrBwnlXhTEVKqeHZSYnaJUlL8UpU8paipyX030FaUpVoIsNW1gbRdeGTMDh4yuyump85r0%2FDeZuIJZ3x2pTFOcmXqQjWQ000gp0qASAsi9lEi%2BwjTVdw7koc76FS387nMVYJq0wzVcU4pnJVxDheK1uOy60i5Kl6EI1DYdJ3CLQNz8Qz%2BB5Thdw9iGrZNYXwljPMScYmqfK0hkBySk21dL0yl2BBU1oCk2sS4BHHrjnSRuDirzhk85s2p2t0J%2FXhmiMIo%2BHkISUo8WSAXHUiw2Wvlt5KUiNNwgQJI2gCYhpMNJiouSa7UUoSgOeSAkEgXsBYRTXVag55b6viEePQe%2BJyjzwXU7DsJisAdG14oqBHfE%2FTBKO2Cjc2TWNsm8BYZqlRr2W85jzMubm0y%2BH6TNyhVSw2SkI98Ct3FEkkFJ8kAcyY6Dx3klkE3xHZN03FOG6fhRnFtInprEGG2HyJRVRbaQZZB3ukqWpxBAIC%2BjG3ONf8GVa4e8DyFQzDzJxvR6bjZM0qVpUvU0qLclLJRcTDYAIUpZJBVzSE2Fr3i7UjMTKXL7inw1nPizO%2BXzSarsjUJGsVJulFtjDsypTYlHAyL6WAnWgEXUm5UecWgZTm%2FlrQJTJPM2sZr5L4Wy9qlAnlS2CKhRXFB6obp8WKgFEK6U9QhQFwo7DTeOHT5ZjtLEOZGWWDcls2MNVvP2VzbXj6ZnJmg0oBxxdM6fUUJKl%2FYg2opXdNgC0NIBJjip9fcpSlK8pXK57TaKzCYSKBHbFMqI5mIage2GkHtgg1X7YREIicIFoCUDvgReJiLQAvAQhE2iI6DAUjuYiU3G0VQwSLxAN72gKaOcVAL9sFI09kEns0wEizY7QtteJ1p3G0RCdoCDdu1AV64jpB7UjzRFISDuLm%2FZEQD8E9%2B1oD0S9RnZOWMmw630C1a1IKATfvvzit7OVJZ98mG%2FWgRblhcSC%2Fw4CvNTTk250kx5WkJ8m2w9EeVNNpg8mnSo9DSYriy%2BouJigJISICgabSufsdL37%2BiTEUSNPvtJM%2FcCKxbMSbiAmVT5BYOuTllXBFy2kn47QRoQhKEISlLQ0pSlIsAOweaIo%2F31QP8AvaAk%2FwB%2F9URCO3QYj6PiVEUa7wEyLKGkgae0mILZT5PMHke6KmknrD4jEi0lNzc6TzB7ICQIKDYAGKTiNRsRHo6PRrbXq6vxD1iKTnU3gLe8hLYJI7Y1jNOVSpzLxbW4pCHDfSo2QL7CNlTi1k7dxjD6OwWKPNLQ8pC3pxSHE6tiEgFNx6SYDHVU6o9rTh8%2B5j10mVnWapLJUNGpenrecWi%2B63IoLeWiZl3gTcPI5WHMwFwXRJj9TVFBdHnRbU2q3btF7XV19bQy6P3KhEvszMqT0apdah33t64DxUyQcaWrp0dT90nzxdPF5XsZQfSmKUtMPvrVrbskCPQeUB5n0IQ3shKf4IizTi%2Bv5EXic8iLM%2F8AZPfOrAQfoE4XL9AqKLlEmkKF2FD1RljGJXmm0JVIE6UhNyLkgcooO1x1xADkq4spvub2sYDF52Wmm6c%2FdC0hKCb27oxttE%2F%2Blqd%2B6MZ9Uap0so%2B0uVASplYGx7osrD7nQIHV8kfigLKzM15hQUy8%2Bm3nv%2BONj0Kam25eXmXFq6XTqVqFiTyvGMJcWVJAULdlhzjK6YXHpVD7x1qXqJIFr7%2FJAXxuszn2qYlmahMzrYQ90YCVX5WPdHlShXYLROGTuUarnvG0BAnzRKfREwQ52iJg0s8xAUwbRKrnFZTducShHfASdeJ5dbjDnSfamETEXFoD1GuTrOyOj095REF1aYmWHGXCgJdTZVhYR4igkxMBaA2tklM5HS8jPDNmp1mTnF1BFjIT83LBUgGDYo6AFK3Q9a4XYaeRvG11v8CS3LnGOOb%2FAPnNQ%2FHaOUoQG6M53eHpWFlN5S4lrc5Ppn5YyzE7Upx8dAUqEz0jTydAsoIKVpN%2BdxHl4dM5sEZKTlbruIcFTtZrc%2BhqXkZyVebQqSYAPSBOvkpRINx2CNQwsD2QGb5s4nyyxbV2qzl3hfEVHmJovO1hdZqgnlzby1ApcSq3UsLgjlytyjA4n084hAVZFAM%2FJ%2F8AiWf9ImO9lXdm1pQbqUfjjg%2BlKl2qnJTM4pSZaXmWXn1JTqIbQ4FKIHabA7R1G%2FxUZKuzfjDE9VVJV1rmQKbeaxO8ZrGnhVTPmj3sV5q4NER6eTPwNmNoQdWgpT8HZN7GJuijVaOJ7J5skszlUSVne8irn8cTp4oMpSTrqNSAB2tIuXt542uD%2FWbS4XmnmltllvbeK%2FRptzMakRxPZMauvWKqkf8Al64rjigyVSerWKiR56eu8WinUrNXmnmlsx9nkQbd%2BqIFlLiSlKt%2BwA7eqNaDijyUULKrNTBB7Kcs2imOKDJUrUFVepJT2KFOcJ%2BKLxQcLzTzS2L7G7%2B%2BR5KnQ0uJTZF9uX5YwdXFHkgfslbqh%2Fya5Ex4qciy30iq5VDtaxpzl7eiKcHJHCjz80rBjynzcnTJxxCblKFd1iO38sa9pksVqTfsTGxcUZ5ZB4ios5TJPE9Sl5t1s9EtdKd0FQ3AJ7OVr%2BeNRtZtYOkTrNPqTqfthLjcd%2FOK1bWSymeSJ5mkMxkdHiiv8vszfP0xLihNsYPj922f5Aj3Y2lXcQ1KsVuRlXkykytEwjUg6ggna4i2TswajW3KglNkuaVW7hYD8YjQq2uhGxmdDQTLugjmIx7EcsUK6vbGR0RzS2oHlaMexXODxgISOyISx9LJUrckx725ZQTsgx5pF0LcAWk84v7baCgabiAx6al1DsjyBtQc5RkM1LhXZHkEmC5ygLfjI%2B%2FU7zSKR8SlRfn06UJ%2FepirVsC13E7ErUaRJrdaZZ6BZCkAagSbbqHfGZKy0qa2mwqdaTdlBAUgk8uVxzgNeuLUk7GKXTr74ztzKmrHbx%2BX%2BIxS9yStE7VGW%2B5V80BhPTr74dOvvjNxlBWD%2FwA6yvxKif3Hqz%2Bysp9yYDBenX3w6TV5RjOvcerPZVpT7kxEZPVy1%2FZeVv3dGqA1%2BuxMUo2MMna2f%2BcpX7lUTDJqsnc1OUHqMBrlMVEdkbA9xytA%2FwBspT7lUT%2B5BWgP7YSv3JgMERCM59yWs7j2RltufVO0PcjrfbUpf7hUBgp5RTIMZ%2F7kdX7anL%2Fe1RKrKepJGpVWlgO%2FQqA1%2FZXfCy%2B%2BM%2FGU1VPOosD%2FAASoe5LVP2VlvvSoDXwBvE9toz%2F3I6qeVUl%2FvSoj7kVW%2FZOX%2B9KgNfpb3iC0kGNiIygqxH9tGfvCjEVZQVQcqoyfRLrgNbqSecS2jZHuP1C9zVUfg64m9x%2BoWv7Lo%2FBlQGtxziuhO0bB9x%2Bf%2FZlr8HVEDlJUk3tVmiPMwqAwHSImjOvcoqXL2Ubv3dCbxP7k1TP%2FADin8HVAYFFNeq%2BxjYasn6mB%2FbEn0MmKZyfqnP2RR62jAa8sYWMbC9yGo%2Fsk3yv9iVEwygqF%2FwC2jR%2FwKoDXFuyJ9EbG9yKp9k%2B196VA5RVT9kG%2FvJgNc6PPE2jzxsH3I6v%2Bvm%2FvRiojKCrEfo1v70YDXYTaKqY2AcoKmOc8gehoxMMpKgBvPj70YDA20qtHrYT384zRGVrydnJ9w%2BhqJ15cuMgETMwVdlk2gPEwfzuT%2B8MXrLVbbb%2BIFulQQMP1G%2Bnn9hVyixVGnz9MZLCG1uDfSSIyDBMuMO4axDizFra6dJzNKmKbT1vJI8Zm3khISkfCCUkqXbYbDmYDXvvbkov7bof6MZ%2FwjpH1ROWqk%2Fttoh%2F9a1GvZydpb0qWqf4zdaCF9IgICTYjbc3%2BSNncIUmXOIHLpSb%2B94sop5DsnGjAfoHhCEAhCEAhCEAhCEAhCEB8y%2BMjwdua%2BYedlTzGytlZGqUnELhnJlhyabYflJpVukBDhAWlSgVAg3GogjYE8UcR3DDmTw%2FViSw9jGlIQ7NyLc7LqYcS6hxBUUqAUnYqSpJuOYuDyIv%2BguNf5zZGZdZ8YaRhrMKjGabl1l2Tm2V9HNSbhsCppyx03AAIIKTYXBsLB%2BcdhU9ITbU7Iuvyk1LLC2nU3SttQ7QY2vKTaKlKtzVSoNOdfeaStTrQUxrJF9SkpNrm8fRWveCbo8xUnF0PMVwSRV72mcbBcCfPpRYmL9QfBdYXkJJiXqeNH33GklClNiySm%2B1gUwHzQ8Upn7Xmfwlz54eKUwf9Hmvwlz54%2BpP1sjLU88S1EehafoRL9bGy1%2FbPU%2Fu0%2FQgPluGKSk%2F8XUK9M06In6Ol9uFmj6Z1w%2Fkj6gK8GLl98DFU%2BPSofQiZPgxcu%2FhYpqPqUn6EB8v1ppavJwuhP%2BPO%2FNEnQUztw6z%2BGu%2FNH1GT4MbLYeViep%2BpafoRU%2BtjZWnniesD0Op%2BhAfLgMUX4WHkH0TjkR8WoP7X%2FwD1rnzR9Rx4MTKq%2FWxRW7f31H0In%2Bti5R9uJa79%2BR%2FVwHy18WovwaAfwxz5oj4tRe2gH8Lc%2BaPqaPBjZPj%2FAKTYg%2B%2FN%2FQiqnwZOTA8rEWIj%2Fh2%2F6uA%2BV%2Fi9G5%2BwZPpm1%2FNEegon7X7f46v5o%2BqifBl5Ijyq%2FiM%2F4dv6ETjwZuRgG9dxL6n2voQHynEtRLkqoKiOwCcXt8kTeL0L9r6%2FwxfzR9WPrZuRP7OYn%2FCGv6uI%2FWzshv2bxR%2BEtf1cB8pTL0Lsw%2Bv8MX80Q6CinY4eJ%2Fxtz5o%2BrZ8GdkP2VvE%2F4S1%2FVw%2BtnZDXv7N4p%2FCmf6uA%2BUnilBP%2FAEfV%2BFufNAyVG304fUe682vb5I%2Brw8GnkOP%2BesUfhLX9XE%2F1tXIP9lcU%2FhbX9VAfJ9MnR%2FhUA%2FhbnzROmSoduthxZPO4nV8%2Fij6wJ8GvkAPKqWKD%2FjjX9VE58G3w%2FnnP4o%2FDWv6qA%2BTqZCip5UFXrmln8kVFSlBVzw8v8MX9GPrEjwcHD2kdaYxKr0zzf9XE31uHh6%2FVsS%2Fhzf8AVwHyY8RoV9sPL%2FDV%2FNEW6dS%2Byhr9U0sfkj60J8HHw7jmrEp%2Fx9H9XE31uXh17sS%2Fxgj%2BrgPkwaZRk7qoqzt2Tiuf3MU%2FE6PyNDWf8bWP6MfW1Hg6OHRPNvEavTUEf1cTfW6uHT9SxH%2FGCP6uA%2BSKJKjDnQl%2Fhiz%2FAEYiZSj2%2FtCr8MV9GPraPB08On6jiI%2F5QQP%2FAG4j9bp4dP1DEX8Yp%2Fq4D5HiWoyTth5y%2Ff46s%2F0YGUoh8rD8x%2BGLH9GPrl9br4c%2F1piD%2BME%2F1cQPg6%2BHLtlcQfxgn%2BrgPkaZSjcvYF3T3eOLv8dopeKUNPOgPn0zyvox9dleDq4cFc5TEHqqKfoRL9bo4b%2F1piH%2BMR9CA%2BRCmKL2UJwemcWfyQEnRlj%2B0zo9E2v5o%2BvH1ujhv%2FWeIP4xT9CJvrdnDd%2Bx9d%2FjAfQgPkGafR7Eew7u%2Fb40vaJkUykW%2FtM%2Bf8aV80fXr63Zw3fsfXv4wH0IqfW8%2BHH9jq3%2BHj6EB8f10ykX%2FtQ%2BP8YPzQ9jaV8GjEel9Zj6%2Bq8Hdw4K%2FuGvD0VAD%2BhD63dw4frGvfxgn6EB8gvYyl%2FsIv78uJfY2lfsOv78qPr99bt4cf1nX%2F4wT%2FVw%2Bt2cOP6zr%2F8AGCf6uA%2BQPsbSv2HX9%2BVETIU4ixpCtP8AflR9f%2Frd%2FDh%2BsK7%2FABgPoQ%2Bt38ORN1SdfVsB%2FbBI%2FEiA%2BP8A7G0r9h1%2FflRUTTaUka%2FYNYCtgemXzj68%2FW6uG%2F8AWeIP4wH0ImPg7uHI85XEJ9NRH0ID4%2F8AiNMv1aMr78s%2FkifxGmW%2FtMfvqo%2Bvzfg8OHJryJOveufSf%2Fbip9b24c%2F2Prn4ePoQHx7MhTj%2FAMyJ%2B%2BriBpsgeVFT99XH2F%2Bt68OX7H1z8PH0IfW9eHH9jq5%2FGA%2BhAfH9umU%2B29FT99X88RNOkf2GR99XH2C%2Bt98Ol7%2BxtZ%2FDU%2FQiCvB88OatV6bWhq52nxv%2FACID4%2FGnSP7DI%2B%2BLimmnSd%2BtR2x6HFx9gx4PbhzF7SFdF%2B6oD1fAiP1vjh2%2FWlf%2FAIxH0ID4%2FinyR29h2%2Fu1RN7F0%2B1zSE%2Fdrj6%2B%2FW9uHO1vY%2Buenx8fQiJ8Hvw5q50%2BufxgPoQHyB9jqX%2Bw7f3a4lTJU4LsKK192v54%2BwKfB88OiPJp9cH%2BPj6ERX4Prh1cFl06tn%2FHh9CA%2BQokKeRtRWvu1%2FPA0yR5%2BwTX3xXzx9d0%2BD24c0iwkK7bu9kB9CJvrfPDp%2Bx1b%2FjD%2FYgPkIKXIH%2FmZof4RcTex1P2%2FORnb90v54%2BvSPB98OzagtEjXAR%2F9eD%2BNEFeD84elc5av%2BqoJ%2BhAfIbxGnjnRGT6XHB%2BWHilL5ewTP31z54%2BuqvB7cOq%2FKlK%2Bf8AKA%2BhEv1vHhy%2FWVf%2FAIxH0InMfIvxCl%2FsKz99X88PEqby9h2bfvl%2FPH11Pg8uHI%2F3DXv4wH0Ih9bx4c%2ByUr4%2Fx9P9XDMfIrxCl%2FsM398X88REjT%2Fg0Rk%2BlSz%2BWPrn9bx4dP1tiD%2BME%2FQh9bw4dP1tiD%2BME%2F1cQPkd4nI%2FsGx90r54nEtT0j%2B0ct69Z%2FLH1t%2Bt3cOfZK4gHoqIH9CA8Hfw6jkziP8AjIfQgPkkWJL9hZX4lfPEvi8j%2Bwst9yr54%2BuA8Hhw6DnLYhPpqI%2BhA%2BDx4dDylcQD0VEfQgPkf0VOTyw7L37yXPxXiPQyROpVAlrHmAV%2FJvH1t%2Bt3cOh%2FScR%2FxkPoQ%2Bt3cOn6jiP%2BMh9CA%2BR%2Fi9P%2BFQZZXpK%2Fnh0FMtb2uynp98%2BlH1vHg7eHa1inEp%2Fyin%2Brh9bs4dO1rEh%2Fykn%2BrgPkf4vTeygS38v54m8Xkjv7By9z3qXb4rx9bvrdvDp%2BoYj%2FAIyH0IifB2cOSuctiL1VEfQgPkmliQFtWHpM9%2B6x%2BWIBiQJ%2F4uyqf4a%2Fnj61%2FW6uHL9QxJ%2FGY%2BhEw8Hbw5p3EviK%2Ff7JD6EB8legkf2Bk%2Ful%2FPE4RI20rw9IqHZ1nBb5Y%2BtB8Hdw6H%2B58RD%2FACiPoRD63bw6fqOI%2FwCMU%2F1cTE5D5M9DTej0e12T1fba3L%2FjiCmKaR1cPyqT361%2FPH1q%2Bt5cOv62xB%2FGI%2BhA%2BDy4dT%2Fc2If4xH0ITOY%2BSRYlikhNGkQT22WbfyorIbkk8sOSJ9PSfSj6y%2FW7%2BHTn4viL%2BMR9CI%2FW8OHX9QxF%2FGQ%2BhED5LrYk1KKk4dkE37LObfyodBJ3B9rsjt2WXv8Ayo%2BtH1vDh1%2FUMRfxkPoQ%2Bt4cOv63xF%2FGQ%2BhAfJdTMoUEDD0iCrmQF%2FJvtDoJGx%2FsckrkWv19vlj60%2FW8eHT9a4g%2FjEfQiVXg7%2BHNXlS2IT%2FlEfQgPkuGZZI0ihyJT29Vdx8sEtSABScPyJB70r%2BePrMPB2cOYNwziMeipD6ERT4O7h1T%2Bk4jPpqQ%2BhAfJrxen%2FsDI%2FGv54lXLyJ8mhSSfWs%2F0o%2BtP1vHh1%2FW%2BIf4xH0InHg9OHQf3HXz6aiPoQHyTTLyXbQZI%2Fd%2FSiboJD9r8n8a%2Fnj61%2FW9uHT9ZV7%2BMf8AYiP1vjh15eJ17%2BMR9CA%2BSfQSH7X5P41%2FPDxeQP8A0fk%2FjX88fWr63tw6%2FrTEH8Yj6EPre3Dr%2BtMQfxj%2FALEB8lfE6eRb2vyfpu588Q8RkP2BlPjc%2BePrX9b14c738Sr%2FAPGX%2BxEw8Hvw6D%2B4K7%2FGH%2BxAfJVMpTRzw9KH%2BE588R8Wp37XZP7tz54%2Btg8H5w6D%2Fm2tn%2FKH%2BzEw8H%2Fw6jlTKz%2FGH%2BzAfJHxanftdk%2FunPniHQSP7W5D7pz54%2BuP1AHDr%2BxVY%2FD%2FAPZiQ%2BD94dT%2FAM21of4%2BPowHySDEjf8A4t0%2F43fnioGJG3%2FFun%2FG788fWkeD94dRv7GVn8PH0Im%2BoA4drW9i6x%2BHj6EB8lCxI2%2F4t0%2F43fnimWJG%2FwDxbp%2FxufPH1u%2Bt%2FcO37G1n8PH0YDgA4dh%2FzbWfw8fQgPkmG5H9rkh%2FnPniOiQ%2Fa3If5z54%2Btn1APDv%2BxtZ%2FDx9CJT4P7h2P%2FNta%2FDx9CCc3yV0SH7W5D%2FOfPDo5D9rch%2FnPpR9avrf3Dt%2Bxta%2FDx9CH1v7h2%2FY2tfh4%2BhAzfJfoJH9rcl8Tn0oiGKd24YkSf8ACfSj6z%2FW%2FuHb9ja1%2BHj6EPrf3Dr%2Bxta%2FDx9CCHyYDMgP%2BjUkfT0n0odDIftZkfic%2BlH1p%2BoA4c%2F2IrH8YH6MPqAOHP8AYisfxgfowHyV6GR%2Fa5JfEv54dDI%2FtckviX88fWr6gDhz%2FYisfxgfow%2BoA4c%2F2IrH8YH6MB8legkP2tSN%2B%2Bzn0om6CT2%2Fsep%2Bwt5Lm%2F8AKj60fUAcOf7EVj%2BMD9GJhwB8OX7CVY%2F5QV80B8khLSiSkjD8jtzBC7H%2BVEympInbDFPHoDn0o%2Btn1AfDj%2BwdV%2FjBXzRN9QNw4ftfqf8AGC%2FmgPkf4vJXv7XKf6LLt%2FOiHRSY%2FwCjlO5W%2BH9KPrp9QVw3D%2FozP%2Fh64m%2BoO4cQdsNT%2Fo8eXAfIoJkvh4ckFffB%2BIxHoZFXk4YkPunfpR9d%2FqEuHD9qs5%2BHuRH6hThw%2FapN%2FhzkB8iPF5T9rcj%2FAJz6UPF5T9rUj%2FnPpR9efqFuG%2B1vajNfh7nzxMOBnhuH%2FQ6Y%2FD3fngPkN0Mj%2B1iQ%2BNz6UQMvJHlhiQ%2BNz6UfXv6hrhu%2Faa%2F%2BHO%2FPERwO8N4%2F6GPH0zzvzwHyC8XlR%2F0Zp%2FxOfSiPi8p%2B1mR%2BNz6UfX%2F6iDhv%2FaQv8Md%2BeJ%2FqJOG79op%2FDHfpQHx%2FEvIFX%2FFaSt%2B%2Bc%2BeIpkpMbjDckPQXPpR9gPqJuG79oh%2FDXvpRMngp4b08sBD1zj30oD4%2F%2BKS37XZT43PpRDxOV%2Fa3J%2FdOfPH2C%2Bor4cP2hD8Me%2BlE31FvDh%2B0BH4W99KA%2BPfsdKK39rcl92588Q9jpQf9G5T74588fYYcGHDgP%2Fl83%2BFvfSiH1F3Dfv8A8Hze5v8Aot76UB8ezT5IjfDUt9%2BdH5YkEjTgo3wxLEdg6d7aPsT9Rhw3f9XbX4Y%2F9OJ%2FqNuHEHUMu2Qf%2FFv%2FAE4D46Jk5JPLDMp63nvnicSVMHl4Xll%2F4w6n8sfYr6jnh0F%2F%2BD1rc3%2FRb%2F04mVwecOar6su5c3%2F%2Bqf8ApwHx18SoxP8AxWl%2Fv7vzxFUjRSjSnC0uFd%2FTO%2FPH2I%2Bo54cLEe5vLbi36Kf%2BnE44PuHMf%2FLiW%2FCn%2FpwHxzXIUNWnThNlNuf5qd3in7G05XkYdlx6XnD%2BWPsj9SDw6f8AVxLfhUx9OJ1cIvDmryss5M%2F41Mf1kB8a%2FYuSJ99oLKx%2FfnBAUumi18PMmxubPOcu6PssnhG4dE3tllJHULG81M8vvm0QTwicOieWWEl65uZP%2FuQHxpNOkNwnDzQ7vfVn8sQEhJA7UJoehxfzx9mTwj8OpIPuYSII5FM3Mg%2FGHIkPCHw5EWOWEnb%2FAMbNf1sB8aE0yQ%2BFhxn1OuGBptOsR7W2732PSuco%2BzKeEXh0R5OWMmP8cmv6yIfUi8Ol9XuYyd%2B%2Fxya%2FrID4yGmSXNOH2h%2FhHIeISYO1Da%2B%2BrEfZk8IPDib3ywlLHmPHZqx%2FzsS%2FUe8N3%2FVbJfhk1%2FWwWzfGsyMkkWVQUj%2FGHIlVJU0nq0MAeeZcMfZf6j7hu7crJA%2BmbmT%2FAO5E31IXDf8A9VVN%2FCJj%2BsgZvjGafT%2F2GT9%2FXEyJGmjyqChW%2FwCuXB%2BSPs19SFw3%2FwDVVTfwiY%2FrIgeEDhuPPKmm%2FhEx%2FWQM3xl9jqX%2Bwn%2FqV%2FNEfY%2BkfsETtb9FLG%2Ffyj7M%2FUf8Nv8A1UU38ImP6yH1H%2FDb%2FwBVFN%2FCJj%2BsgZvjL7G0m9%2FYIW%2F8SuCqdSiUn2DuBzHjCxf5I%2Bzf1IPDd%2F1U038ImP6yJPqPOGv%2FAKqad%2BEzP9ZBGb4zqkpBRB9r6bDn%2Bal3%2FFFMydN%2FYEfhK%2Fmj7OfUecNf%2FVTTvwmZ%2FrIDg84bByyqkPwuZ%2FrIGb4yeL079r1%2F3s2sfktEUy1LHKguD0Tq%2Fox9mfqOeGu%2Br3K5C5%2F%2Brmf6yCeDzhvSbpyvkh%2Fjkz%2FWQTm%2BM3ilKCSn2DXuLXM0okfJEBJ0cc6Dq9Mwv5o%2Byv1GfDb%2FANWcsfOZyZv%2FAKSJfqMOGz%2Fq1l%2Fw6Z%2FrIGb42GQpKudCH4UofkiJptKSkD2EO3aJlR%2FJH2QTwXcNqeWXDPrnZj6cS%2FUV8NhGn3OW7Xv%2Bjpn6cDN8b%2FEaZ%2BwA%2FCHPmiHsfSNNjh5d%2FtvGlfRj7HfUS8Ne98u0b8%2FzfMfTiRXBDw1KFjl6Pw%2BY%2BnAzfHT2Oo%2F7AOfhavmiQ0%2BiAm2Hlpv3Tix%2BSPsX9Q5w0H%2F5fn%2BMJj6cSfUL8NH7QV%2Fxg%2F8ASgZvjv4hRv2Bf%2FDlfRiCJKhtqJNAmvVPK%2BjH2HPApw0n%2FoM8P8ov%2FSiX6hPhs06faXMW%2FwDMXvpQM3x6NOoq%2FKoT5H%2FjT9GIil4e7cPTPqnlfNH2E%2BoU4bf2mTH4e788PqE%2BG%2BwHtPmdv%2Fr3N%2FlgZvj4aXhxXPDs96p239GHsVhz4NBnR6Z4H%2BjH1%2B%2BoM4bv2pzv8YORD6gvhw%2FatPfxguBm%2BQYpGH9yaFPnutPD6MTIpWH086FPfhgP9GPrv9QRw4%2FtbqH8YL%2BaH1A%2FDl%2B12pfxiv5oGb5Dew%2BHbdehVBX%2BOgf0YpexeHkiyqJUCe8TgH9GPr39QJw5%2FsDVf4xV80DwB8OJFva%2FUwe8VBV%2FxQVfIQSVAQAlNHqIHaPHR9GAlcOjlRqiPRPJ%2BjH12%2Bt%2BcOf7D1j%2BMT9GH1vzhz%2FYesfxifowHyJMph1QKRSKkASL2nEX%2BPTEFUzDyv8Amie9U2Pox9c%2Fre%2FDna3sVWfT7Ib%2FAMyJfrevDp%2Bx1c%2FjEfQgmJyfIw0rD52TSJ8f40D%2FAEYj7D0Mj%2B1c9%2BED6MfXL63pw6fsdXP4xH0IifB7cOpUVGn12x%2BD7IgAfyIJzfIsUWh%2FsbUPwkfRioaXh7a1LqA23vMpO%2F3MfXAeD24dRyp9dHoqX%2BxEfrfHDt%2BsK9%2FGX%2BzAzfIz2Hoh%2FuOc%2B%2FD5oiKTRk8pKZP75%2F8A1R9cvre%2FDr2U6uD0VG39CIHwe%2FDsTfxCuj0VH%2FYgZvkd7F0jtp8x9%2FHzQ9iaJ2yE3%2BED5o%2BuQ8Hxw7gJT4hXCE8r1EbfyIK8Hzw7k3EhXE%2BYVAfQgZvkcKZRgCBJToB%2F7cfNFP2Kpeq4lpv74Pmj64nwefDud%2FFcQA9%2FskPoQ%2Bt5cO97%2BLYg9Hsgn%2BrgZvkeaZTf1rN%2FfR80S%2BxNNII8Um7nl79%2Fqj65%2FW8%2BHf8AWde%2FjBP0IDwenDyEhHi%2BIDbkfZBN%2FwDRwM3yMNEpp3ElM%2FfT80QNFp4%2FuOY%2B%2FH5o%2Buf1vPh5%2FW%2BIP4wT%2FVxH63nw8dsrXz%2Fj6f6uBm%2BRzdLpaQUuU%2BZVtt79ax%2BKIKpFK5iUmU%2F4YfNH1s%2Bt28Pe4tiOx7PH2tv81D63Xw9d2JPw9v8AqoGb5J%2BxNK%2FWs19%2BHzQNHpR3TIzf30H8kfW363dw992I%2FwAPb%2FqoiPB4cPgNwMR7m5%2FN7e%2F%2BagZvkkKVSk7qkpq%2F98HzRN7F0f8AWM399HzR9bPrePD39piL8Pb%2FAKqIHwd3DyQR0WIt%2FwD69H9VAzfJE0ukfrKb%2B%2Bj5ok9jaMD%2BgZz7%2BPmj62K8HRw9H9sg9E%2B3%2FVRA%2BDm4eT%2B2X%2BMG%2FwCqgZvkr7H0b9YTv34fNEvsfSDykZ378n5o%2BtR8HJw%2BdjmJfw9v%2BriX63Fw%2Bfq2Jvw9v%2BqgZvkt7F0nWF%2BKTW3Z043%2BSJjTKMOcjOH0PA%2Fkj6z%2FAFuHh6tbXiS%2Ff483%2FVRL9bf4fv1zib8Na%2FqoGb5NCQpI2TJzI9Lv%2BqHiNL%2FWr%2F37%2FVH1kPg3%2BH4i3jOJvw1r%2BqiT621w%2FwB7%2BOYn%2FDWv6qBm%2BT5k6URbxOYHnDsUzR6O5uqWnN%2B50fNH1kV4NvIE8p7E4%2Fxxn%2BqiQeDYyEHKqYo%2FC2f6qBm%2BSk5S6LISMxUnKW88qTbU%2BEOTJCF6d9KgBex5bGNbSapKcoKnRJOy1Reqb776QfeDLrQkoShJ3SpCwq5JsUqHaI%2B0lc8GRkbV6TN0puvYnY8ab0dKJlkqRvfb3oRgDfgmcEyi3UyeOZ9TalXQXtJUB3bItAzfJXolfqS4rU6TUut0hKmzpNQlzv8A3wc4%2BtX1qnC%2F7eH%2FAL2n6MB4KrDSXG3W8cvBTS0uJu2nmDcfBgZvn85T2ta%2FzIjyj%2BljvMSexyP1sn72I%2BkCvBvtncZglJ7%2FABZH0IgfBv6gArMUne5PijfPzdSCJfNqeokrNtht1hTNjqCm7JN4tftVpnfOn1j5o%2Bnjng2qa4lxLmOVOat06pdHVPqRyimPBqUlPLHLg2v9iHPv8mCHzCcwdSHPKNQ9RTFrq2A5VtlxyVXNEt30Kctta1jH1YHg2aGFH%2BzV3Tfb3lNwPuYg74NTDj7ZaexxOFClajZtFx6DogPnCikAobUZRu62xq6gNjbne0TihM%2FrUR9KR4Omhp8nG0wTa11MNn%2BhE7fg6sPX99xo%2BbG%2B0u3uO7yYD5eY0pMrJ4QrE34k2NEorSdPWCibAiNJNNpQNAvfzgx9qK34M3L%2FABDJtU6oY2rTcsl5LriJfokdIEm4SboO0UT4LPJxZJViWujuCVM2%2FwBHAfGZtHK6gLeaNrUOh0p2hSK3ZZ3plN6i4HdlAnuttH1KR4LLIcbLr%2BJCDzs4x%2FVxdpfwaeSss02w3iXFBQ0gISC7L7AC36lAfK80OjlfUbmwnzrF%2FkiY0WlEJCm5s%2FbWUn5I%2BqZ8G5kv2YhxKP8ACMf1cSK8GxkweWJcTj0Oy%2F8AVQHytcoNHvdpE7a52UU8uyJfYGlfC8eH70pj6rJ8G1kuOeIsTH%2FCsf1cQ%2BtuZPb%2FANkuIt%2FOx%2FVwHyq9gaMQd6hfsOpERGH6JZPXqV%2B37HaPqp9bcye2%2FsnxJsnTbWxb0%2FY%2BcQPg2snVc8TYi9Rl%2FwCrgPlf7X6H%2FwB4fG3EgodHHlInD%2FDRH1PV4NjKP4OKcQevoPoRRV4NXKgHq4sr4H%2BA%2FKiA%2BW4olGJ2anzq8rrI29EQNEpJ3Jn%2FAORH1GV4NXKwnbFNbV%2B%2BDP0IpOeDSy0VYIxdWkJHYnoRcd3kQHy6NFpXwUzh9JTAUSlHm3O%2BpSfmj6h%2FW0st739tlW9FmvoRIfBr4FSB0OLZ9BCbGyGxfznqwHy%2BXQ6epWr83k95UiJhQ6d8Lx0%2Fwkx9OV%2BDWwiq%2FwDZnPG42uhG38mPOrwaGF%2FgY0mvWhH0YD5oLodHPkInuXatHP4opih0oc5eZPpdHzR9LVeDQovwMbuetpP0Yl%2BtoUkcsbX9LKfowHzOnaOzMsiWZSZdv4QSSSr0nti3DCEsf0xP3uPqEPBoUj4WNf8AMp%2BjE%2F1tKjftyH3lP0YD5fjB7A3S8R6AYe1GWPlOOH1R9PvraFG%2FbofvSfoxA%2BDPpGtS%2Fbuq6uZ6FP0YJiZjY%2BYPtRleYW59zEfamz%2BqL%2B5j6fDwaNJFtONjsLbtJO33POIfW0KRb%2Fjuu9v1NP0YJ4VXhfMA4QZJv0iviiYYRZA8r5I%2Bng8GbR73ONlW%2FvQ%2BjER4M%2BkDljhX3lJ%2FowOFPhfML2qNhWzpI%2BKJvao39uqPp39bOo9%2F%2BO67f3pP0Yj9bOon7dnPvafowOFPhfMNWFWPtlje%2B14l9q0te%2FSEH97H0%2B%2BtnUT9urn3tP0Yl%2BtoUtP2PG%2F3TKT%2FAEYIzzfNeSYrVPDaWK8%2BG2hpQ2UJWkJvfTYjlfsizvYCoT80qdLUy04tanFpac6pUeZAVy3j6gq8GjSyOrjex%2FvKfowHg0KT244V6mk%2FRgh815TDmGWG9HilTV%2FjCD%2BSPPMYOwbNLW47LVQqUNOkOo028%2B0fTM%2BDRo1tsbrv%2Fek%2FQiCfBo0axSrG7hB%2F7JP0ID5epyzwe2dTKqwk%2Fv2z8sekYIoSRYPVTb903H07%2BtpUT9urn3tP0YfW0qJ%2B3Vz72n6MB8xfaZRf1ep%2F5uJVYNoF%2Bsupn1tx9PPraNAt%2FwAcnL%2FvB9GIDwaFA%2BFjJfqbH0YD5gzGD6UpAT0CnUdgeSCfkjL8L4wxHhSmpo0szTZ6SauWG56VDqmSTchKr30%2FuTsI%2Bhx8GZh0%2FwDTJ37hP0YkHgycParqxk5p8yBf%2BbAcEDMzExN10jDSvMad%2FtROvM7EdwWKNhtoW3HscTv91Hev1snDX7cXfuR9GH1snDX7cXfuR9GA4KGaGJgd6Rhw%2Bmn%2FAO1EFZmYqWsqNMw1bsHsYL%2FHqvHfH1snDH7cX%2FuU%2FRiZvwZ2Gmzf23uq%2FfJH0YDgf3ScT%2FsTh3%2BLv9qJ%2FdMxRfUKZh3lbanBP5Y78%2Btr4Z%2FbSfuB9GJk%2BDZwwOeKD9wPowHAXum4o%2FYzD%2F4B%2FriZGZ2KUkH2Iw5fttTrX%2BWO%2FfrbWF%2F20K%2B4H0YDwbWF%2FhYoV9z%2FALMBwH7qeK%2F2Hw3%2FABefniRWaOLVK6tKw4kf%2BWg%2F0o7%2B%2BtsYV%2FbSv7kfRiH1tnDN%2FwDjSbfvB9GA4B90jEvM0ugfxf8A64qpzSxUnlTMP%2BunA%2Fljvs%2BDawvtbFCvPdP%2BzA%2BDawt2YnV9z%2FswHAJzQxYXel9i8PX%2FAPLAP6UPdNxJ%2BwGG%2FwCL%2FwDajv3621hj9s5%2B5%2F2Yh9bZwz%2B2hX3P%2BqA4HczRr6zdGGsON7ckySrfzomGa%2BJBzw5hk%2BmQP0o70X4NjDatk4qUkd%2BgX%2FmxH62xhm%2F%2FABpVb94PowHBIzXr6fJwxhkeiUV9KJ%2FdbxF%2B1fDP4Ir6Ud6Hwa%2BFuzE6vuB9GJfrbGGb%2FwDGlVv3o%2BjAcHHN%2FEwFhhzDKf8AElH%2BlFP3X8XJ%2BxULC49Mgr6Ud6q8Gvho%2BTitY%2Fgj6MQ%2Btp4ZPl4scP8ABH0YDgpzNzGCzqFGwuk%2BanH6USLzdxopOg0zDIT3Cl%2F6473Pg08MHb22OAfvR9GJPraGGSeti5wj96PowHBBzYxmr%2B4sPI%2Fe00flMQ91XGX63oP8WJ%2BeO9h4MzDN98YvW8yR9GJD4MnDRH%2FHSYvfuH0YDgheZuNHDcNUIf5MT88U%2FdGxvp0fnJbv9jRf8cd9HwY2F%2F26zXyfRiA8GJhntxvNeq30YDgX3Q8ZW8qkfxcn54kVmDjFXN%2BkD0U9I%2FLHfJ8GBhk%2F9Op3%2BT9GIHwYGHezHc38SfoQHAqcfYxT%2FdVK9UgkfliC8fYxUf0VTPwFMd9fWv8AD37e5v5Pow%2BtfYd%2Fb5O%2FyfoQHAAxzi4EK6emEg33kh88Pb3jLXr6Wj8rW8QFvxx399a%2Bw9f%2FAI%2Bzn8n6ER%2BtfYct%2FwAfZ3%2BT9CA%2Bf4xxjICwnKWO4iQG29%2B%2BHt4xp%2Bv6b%2FFyfnjv7617h79v87%2FJ%2BhD617h79v8AO%2FyfoQHAQxzjIAAzlLIBvvTh9KKSMZ41T5VVpyv8nI%2BePoF9a9w9%2B3%2Bd%2Fk%2FQh9a9w9%2B3%2Bd%2Fk%2FQgPn4rGWNTcCq08A9hpqDb8sRTjLGKb%2Fm2kk%2FBKqU2bfGd4%2BgP1rzD%2FAO36c%2BJP0Ih9a7w%2F%2B36c%2BJP0IDgB%2FHeO2pd12XrVPlVpGrVL0iWBNv3yFRpPE1fxhi6fTP4srNRqrzadLSpm6g0n7VCQAlI8wAj6zzHguKG6ytpGP5ka02uQPoRYqJ4KdctPg1bMNhUnfcS6CHLfwkWgOFeF3hhxfxIY79ptFMtIsoknZ2cnJsL6OXaRZIJCRe6lqSkeknkDHc3Dj4MrGeWeadLxvjTGFHFOodSl6lLy9PLjjr62Va20kqSkJTrSkk8yNrdo7HyN4ect%2BH2iTVJwHT3unqCkLn6hNrDkzNKQLJClAABIubJAAFz2m8bNgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgEIQgP%2FZ%22%20vertex%3D%221%22%20parent%3D%229%22%3E%3CmxGeometry%20width%3D%22175%22%20height%3D%2227%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2211%22%3E%3CmxCell%20style%3D%22vsdxID%3D9%3BedgeStyle%3Dnone%3Bdashed%3D1%3BdashPattern%3D12.00%206.00%3BstartArrow%3Dnone%3BendArrow%3Dnone%3BstartSize%3D5%3BendSize%3D5%3BstrokeColor%3D%236F0000%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3BverticalAlign%3Dmiddle%3Bhtml%3D1%3BlabelBackgroundColor%3D%23ffffff%3Brounded%3D1%3BfillColor%3D%23a20025%3BfontColor%3D%23FF0000%3B%22%20edge%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20relative%3D%221%22%20as%3D%22geometry%22%3E%3CArray%20as%3D%22points%22%3E%3CmxPoint%20x%3D%22211.91%22%20y%3D%22125.76%22%2F%3E%3CmxPoint%20x%3D%22502.35%22%20y%3D%22125.76%22%2F%3E%3C%2FArray%3E%3CmxPoint%20x%3D%22211.91%22%20y%3D%22101%22%20as%3D%22sourcePoint%22%2F%3E%3CmxPoint%20x%3D%22502.9100000000001%22%20y%3D%22106%22%20as%3D%22targetPoint%22%2F%3E%3C%2FmxGeometry%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%2212%22%20value%3D%22Blocked%22%20style%3D%22edgeLabel%3Bhtml%3D1%3Balign%3Dcenter%3BverticalAlign%3Dmiddle%3Bresizable%3D0%3Bpoints%3D%5B%5D%3BfontColor%3D%23990000%3B%22%20vertex%3D%221%22%20connectable%3D%220%22%20parent%3D%2211%22%3E%3CmxGeometry%20x%3D%22-0.0192%22%20y%3D%221%22%20relative%3D%221%22%20as%3D%22geometry%22%3E%3CmxPoint%20x%3D%229%22%20as%3D%22offset%22%2F%3E%3C%2FmxGeometry%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2213%22%3E%3CmxCell%20style%3D%22vsdxID%3D10%3BedgeStyle%3Dnone%3BstartArrow%3Dnone%3BendArrow%3Dnone%3BstrokeColor%3D%23009900%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3BverticalAlign%3Dmiddle%3Bhtml%3D1%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3BflowAnimation%3D1%3Bcurved%3D0%3Bcomic%3D0%3Bdashed%3D1%3BdashPattern%3D12%2012%3B%22%20edge%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20relative%3D%221%22%20as%3D%22geometry%22%3E%3CmxPoint%20x%3D%2297%22%20y%3D%22-26%22%20as%3D%22offset%22%2F%3E%3CArray%20as%3D%22points%22%3E%3CmxPoint%20x%3D%22206.91%22%20y%3D%22126.4%22%2F%3E%3CmxPoint%20x%3D%22110%22%20y%3D%22126.4%22%2F%3E%3CmxPoint%20x%3D%22110%22%20y%3D%22226.03%22%2F%3E%3CmxPoint%20x%3D%22206.91%22%20y%3D%22226.03%22%2F%3E%3C%2FArray%3E%3CmxPoint%20x%3D%22206.91%22%20y%3D%22101%22%20as%3D%22sourcePoint%22%2F%3E%3CmxPoint%20x%3D%22206.91%22%20y%3D%22200%22%20as%3D%22targetPoint%22%2F%3E%3C%2FmxGeometry%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2214%22%3E%3CmxCell%20style%3D%22vsdxID%3D11%3BedgeStyle%3Dnone%3BstartArrow%3Dnone%3BendArrow%3Dnone%3BstartSize%3D5%3BendSize%3D5%3BstrokeColor%3D%2300CC00%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3BverticalAlign%3Dmiddle%3Bhtml%3D1%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3BflowAnimation%3D1%3B%22%20edge%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20relative%3D%221%22%20as%3D%22geometry%22%3E%3CmxPoint%20x%3D%22-94%22%20y%3D%22-26%22%20as%3D%22offset%22%2F%3E%3CArray%20as%3D%22points%22%3E%3CmxPoint%20x%3D%22508.9100000000001%22%20y%3D%22126.4%22%2F%3E%3CmxPoint%20x%3D%22602.8299999999999%22%20y%3D%22126.4%22%2F%3E%3CmxPoint%20x%3D%22602.8299999999999%22%20y%3D%22226.04%22%2F%3E%3CmxPoint%20x%3D%22508.98%22%20y%3D%22226.04%22%2F%3E%3C%2FArray%3E%3CmxPoint%20x%3D%22508.9100000000001%22%20y%3D%22101%22%20as%3D%22sourcePoint%22%2F%3E%3CmxPoint%20x%3D%22508.9100000000001%22%20y%3D%22200%22%20as%3D%22targetPoint%22%2F%3E%3C%2FmxGeometry%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2215%22%3E%3CmxCell%20style%3D%22vsdxID%3D12%3BedgeStyle%3Dnone%3BstartArrow%3Dnone%3BendArrow%3Dnone%3BstartSize%3D5%3BendSize%3D5%3BstrokeColor%3D%23009900%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3BverticalAlign%3Dmiddle%3Bhtml%3D1%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3BflowAnimation%3D1%3B%22%20edge%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20relative%3D%221%22%20as%3D%22geometry%22%3E%3CmxPoint%20x%3D%22-1%22%20y%3D%22-26%22%20as%3D%22offset%22%2F%3E%3CArray%20as%3D%22points%22%3E%3CmxPoint%20x%3D%22209.91%22%20y%3D%22225.58%22%2F%3E%3CmxPoint%20x%3D%22502.5200000000001%22%20y%3D%22225.58%22%2F%3E%3C%2FArray%3E%3CmxPoint%20x%3D%22209.91%22%20y%3D%22200%22%20as%3D%22sourcePoint%22%2F%3E%3CmxPoint%20x%3D%22502.9100000000001%22%20y%3D%22200%22%20as%3D%22targetPoint%22%2F%3E%3C%2FmxGeometry%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2216%22%3E%3CmxCell%20style%3D%22vsdxID%3D13%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3Bglass%3D0%3Bshadow%3D0%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22171.91%22%20y%3D%2262%22%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%2217%22%20style%3D%22vsdxID%3D14%3BfillColor%3D%23ffffff%3BgradientColor%3Dnone%3Bshape%3Dstencil(vZTdcoMgEIWfhksZ%2FmLwOk1eIE%2FAVKJMrThIG9On7%2BqajiSxvWq8gt3Dnv0YViJ3fW06SwTrY%2FBv9uzKWBP5QoRwbW2Di7Aick%2Fk7uSDrYL%2FaEvcdwaUgk0RW%2BIZPqoFM%2BH16L4sxiTVrFh%2BOYqwyrv%2FHN0H1DJMXXAnONViihxQDHVHx1ms6GaL%2BjAf4JoKjaFZs6EqT2rODkNmBtdnwUcTnW%2BTXGNCZTPwyk6NqZJUf7a2W4T5srvGtQuUAtp7ZP0QBdrUKQqwFzxB4Wztdp5AA%2BaU8cR%2FqynXvyKJO6S8SJDGO1JJ0R%2FI%2F0e6expX75XHxtTNY8spVwkOW7mfJ8D8MTiwmMb1urmdZQjhf0DuvwE%3D)%3BstrokeColor%3D%233a414a%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%2216%22%3E%3CmxGeometry%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CmxCell%20id%3D%2218%22%20value%3D%22%26lt%3Bdiv%20style%3D%26quot%3Bfont-size%3A%201px%26quot%3B%26gt%3B%26lt%3Bp%20style%3D%26quot%3Btext-align%3Acenter%3Bmargin-left%3A0%3Bmargin-right%3A0%3Bmargin-top%3A0px%3Bmargin-bottom%3A0px%3Btext-indent%3A0%3Bvertical-align%3Amiddle%3Bdirection%3Altr%3B%26quot%3B%26gt%3B%26lt%3Bfont%20style%3D%26quot%3Bfont-size%3A14.11px%3Bfont-family%3AArial%3Bcolor%3A%23008a0e%3Bdirection%3Altr%3Bletter-spacing%3A0px%3Bline-height%3A100%25%3Bopacity%3A1%26quot%3B%26gt%3BMRM%26lt%3B%2Ffont%26gt%3B%26lt%3B%2Fp%26gt%3B%26lt%3B%2Fdiv%26gt%3B%22%20style%3D%22text%3BvsdxID%3D13%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3BverticalAlign%3Dmiddle%3Balign%3Dcenter%3Boverflow%3Dwidth%3B%3Bhtml%3D1%3B%22%20vertex%3D%221%22%20parent%3D%2216%22%3E%3CmxGeometry%20y%3D%22-0.47%22%20width%3D%2269.85%22%20height%3D%2217.78%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2219%22%3E%3CmxCell%20style%3D%22vsdxID%3D15%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22471.91%22%20y%3D%2262%22%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%2220%22%20style%3D%22vsdxID%3D16%3BfillColor%3D%23ffffff%3BgradientColor%3Dnone%3Bshape%3Dstencil(vZTdcoMgEIWfhksZ%2FmLwOk1eIE%2FAVKJMrThIG9On7%2BqajiSxvWq8gt3Dnv0YViJ3fW06SwTrY%2FBv9uzKWBP5QoRwbW2Di7Aick%2Fk7uSDrYL%2FaEvcdwaUgk0RW%2BIZPqoFM%2BH16L4sxiTVrFh%2BOYqwyrv%2FHN0H1DJMXXAnONViihxQDHVHx1ms6GaL%2BjAf4JoKjaFZs6EqT2rODkNmBtdnwUcTnW%2BTXGNCZTPwyk6NqZJUf7a2W4T5srvGtQuUAtp7ZP0QBdrUKQqwFzxB4Wztdp5AA%2BaU8cR%2FqynXvyKJO6S8SJDGO1JJ0R%2FI%2F0e6expX75XHxtTNY8spVwkOW7mfJ8D8MTiwmMb1urmdZQjhf0DuvwE%3D)%3BstrokeColor%3D%233a414a%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%2219%22%3E%3CmxGeometry%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CmxCell%20id%3D%2221%22%20value%3D%22%26lt%3Bdiv%20style%3D%26quot%3Bfont-size%3A%201px%26quot%3B%26gt%3B%26lt%3Bp%20style%3D%26quot%3Btext-align%3Acenter%3Bmargin-left%3A0%3Bmargin-right%3A0%3Bmargin-top%3A0px%3Bmargin-bottom%3A0px%3Btext-indent%3A0%3Bvertical-align%3Amiddle%3Bdirection%3Altr%3B%26quot%3B%26gt%3B%26lt%3Bfont%20style%3D%26quot%3Bfont-size%3A14.11px%3Bfont-family%3AArial%3Bcolor%3A%231071e5%3Bdirection%3Altr%3Bletter-spacing%3A0px%3Bline-height%3A100%25%3Bopacity%3A1%26quot%3B%26gt%3BMRC%26lt%3B%2Ffont%26gt%3B%26lt%3B%2Fp%26gt%3B%26lt%3B%2Fdiv%26gt%3B%22%20style%3D%22text%3BvsdxID%3D15%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3BverticalAlign%3Dmiddle%3Balign%3Dcenter%3Boverflow%3Dwidth%3B%3Bhtml%3D1%3B%22%20vertex%3D%221%22%20parent%3D%2219%22%3E%3CmxGeometry%20y%3D%22-0.47%22%20width%3D%2269.85%22%20height%3D%2217.78%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2222%22%3E%3CmxCell%20style%3D%22vsdxID%3D17%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22171.91%22%20y%3D%22162%22%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%2223%22%20style%3D%22vsdxID%3D18%3BfillColor%3D%23ffffff%3BgradientColor%3Dnone%3Bshape%3Dstencil(vZTdcoMgEIWfhksZ%2FmLwOk1eIE%2FAVKJMrThIG9On7%2BqajiSxvWq8gt3Dnv0YViJ3fW06SwTrY%2FBv9uzKWBP5QoRwbW2Di7Aick%2Fk7uSDrYL%2FaEvcdwaUgk0RW%2BIZPqoFM%2BH16L4sxiTVrFh%2BOYqwyrv%2FHN0H1DJMXXAnONViihxQDHVHx1ms6GaL%2BjAf4JoKjaFZs6EqT2rODkNmBtdnwUcTnW%2BTXGNCZTPwyk6NqZJUf7a2W4T5srvGtQuUAtp7ZP0QBdrUKQqwFzxB4Wztdp5AA%2BaU8cR%2FqynXvyKJO6S8SJDGO1JJ0R%2FI%2F0e6expX75XHxtTNY8spVwkOW7mfJ8D8MTiwmMb1urmdZQjhf0DuvwE%3D)%3BstrokeColor%3D%233a414a%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%2222%22%3E%3CmxGeometry%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CmxCell%20id%3D%2224%22%20value%3D%22%26lt%3Bdiv%20style%3D%26quot%3Bfont-size%3A%201px%26quot%3B%26gt%3B%26lt%3Bp%20style%3D%26quot%3Btext-align%3Acenter%3Bmargin-left%3A0%3Bmargin-right%3A0%3Bmargin-top%3A0px%3Bmargin-bottom%3A0px%3Btext-indent%3A0%3Bvertical-align%3Amiddle%3Bdirection%3Altr%3B%26quot%3B%26gt%3B%26lt%3Bfont%20style%3D%26quot%3Bfont-size%3A14.11px%3Bfont-family%3AArial%3Bcolor%3A%231071e5%3Bdirection%3Altr%3Bletter-spacing%3A0px%3Bline-height%3A100%25%3Bopacity%3A1%26quot%3B%26gt%3BMRC%26lt%3B%2Ffont%26gt%3B%26lt%3B%2Fp%26gt%3B%26lt%3B%2Fdiv%26gt%3B%22%20style%3D%22text%3BvsdxID%3D17%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3BverticalAlign%3Dmiddle%3Balign%3Dcenter%3Boverflow%3Dwidth%3B%3Bhtml%3D1%3B%22%20vertex%3D%221%22%20parent%3D%2222%22%3E%3CmxGeometry%20y%3D%22-0.47%22%20width%3D%2269.85%22%20height%3D%2217.78%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CUserObject%20label%3D%22%22%20tags%3D%22Baggrund%22%20id%3D%2225%22%3E%3CmxCell%20style%3D%22vsdxID%3D19%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22471.91%22%20y%3D%22162%22%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2FUserObject%3E%3CmxCell%20id%3D%2226%22%20style%3D%22vsdxID%3D20%3BfillColor%3D%23ffffff%3BgradientColor%3Dnone%3Bshape%3Dstencil(vZTdcoMgEIWfhksZ%2FmLwOk1eIE%2FAVKJMrThIG9On7%2BqajiSxvWq8gt3Dnv0YViJ3fW06SwTrY%2FBv9uzKWBP5QoRwbW2Di7Aick%2Fk7uSDrYL%2FaEvcdwaUgk0RW%2BIZPqoFM%2BH16L4sxiTVrFh%2BOYqwyrv%2FHN0H1DJMXXAnONViihxQDHVHx1ms6GaL%2BjAf4JoKjaFZs6EqT2rODkNmBtdnwUcTnW%2BTXGNCZTPwyk6NqZJUf7a2W4T5srvGtQuUAtp7ZP0QBdrUKQqwFzxB4Wztdp5AA%2BaU8cR%2FqynXvyKJO6S8SJDGO1JJ0R%2FI%2F0e6expX75XHxtTNY8spVwkOW7mfJ8D8MTiwmMb1urmdZQjhf0DuvwE%3D)%3BstrokeColor%3D%233a414a%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3B%22%20vertex%3D%221%22%20parent%3D%2225%22%3E%3CmxGeometry%20width%3D%2269%22%20height%3D%2217%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3CmxCell%20id%3D%2227%22%20value%3D%22%26lt%3Bdiv%20style%3D%26quot%3Bfont-size%3A%201px%26quot%3B%26gt%3B%26lt%3Bp%20style%3D%26quot%3Btext-align%3Acenter%3Bmargin-left%3A0%3Bmargin-right%3A0%3Bmargin-top%3A0px%3Bmargin-bottom%3A0px%3Btext-indent%3A0%3Bvertical-align%3Amiddle%3Bdirection%3Altr%3B%26quot%3B%26gt%3B%26lt%3Bfont%20style%3D%26quot%3Bfont-size%3A14.11px%3Bfont-family%3AArial%3Bcolor%3A%231071e5%3Bdirection%3Altr%3Bletter-spacing%3A0px%3Bline-height%3A100%25%3Bopacity%3A1%26quot%3B%26gt%3BMRC%26lt%3B%2Ffont%26gt%3B%26lt%3B%2Fp%26gt%3B%26lt%3B%2Fdiv%26gt%3B%22%20style%3D%22text%3BvsdxID%3D19%3BfillColor%3Dnone%3BgradientColor%3Dnone%3BstrokeColor%3Dnone%3BstrokeWidth%3D0%3BspacingTop%3D-3%3BspacingBottom%3D-3%3BspacingLeft%3D-3%3BspacingRight%3D-3%3Bpoints%3D%5B%5B0%2C0.5%2C0%5D%2C%5B1%2C0.5%2C0%5D%2C%5B0.5%2C1%2C0%5D%2C%5B0.5%2C0%2C0%5D%5D%3BlabelBackgroundColor%3Dnone%3Brounded%3D1%3Bhtml%3D1%3BwhiteSpace%3Dwrap%3BverticalAlign%3Dmiddle%3Balign%3Dcenter%3Boverflow%3Dwidth%3B%3Bhtml%3D1%3B%22%20vertex%3D%221%22%20parent%3D%2225%22%3E%3CmxGeometry%20y%3D%22-0.47%22%20width%3D%2269.85%22%20height%3D%2217.78%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2Froot%3E%3C%2FmxGraphModel%3E
Cisco Resilient Ethernet Protocol
A group of ports becomes part of a segment. The segment is either closed in a ring, or open towards the rest of the infrastructure with 2 edge ports. A single port in the segment is in ALT (blocked) state to prevent loops. Instead of using control frames just like MRP, it checks the state of the local neighbor and agrees on which port will be blocked. In regard to spanning-tree, the logic is the same as with MRP, it is recommended to enable the protocol on those ports that don't belong to the segment, to prevent loops. The convergence time is not deterministic as in the case of MRP, but it is better than spanning-tree as it is running on a physical link base.
Parallel Redundancy Protocol
While both MRP and REP have better convergence than spanning-tree, they still introduce a short outage in case of a failure. In order to provide seamless convergence, PRP was introduced. Parallel paths are built which send duplicated packets to the destination. The source and destination are connected to both paths. Duplicated packets are discarded, while arrival of a single one signals a broken path. Nodes that don't support redundant paths are put behind a redundancy box that does. Spanning-tree is also disabled in this case, on those ports that run the protocol.
High-availability Seamless Redundancy (HSR)
Enabling 2 redundant independent paths might not always be easy. However, we still can achieve seamless redundancy on a single ring. While protocols like MRP send only control packets in both directions, with data being sent in one direction only, HSR sends both control and data in both directions. Duplicate packets are then handled by the nodes which support HSR. Nodes that don't run HSR are put behind a redundancy box, just like with PRP. Similar considerations to the ones before are done in relation to spanning-tree.
Protocol Comparison
Conclusion
Industrial redundancy protocols are designed to address the unique challenges of industrial environments, where fast convergence, seamless failover, and high availability are amongst the most important factors to consider. Traditional spanning-tree protocols are not capable of meeting these requirements, while redundancy protocols like MRP, REP, PRP, and HSR are designed to with OT in mind.
Each protocol offers specific advantages, from deterministic convergence times with MRP to the zero recovery time of PRP and HSR. As industries continue to evolve, adopting these advanced protocols will be key to meeting the demands of real-time operations and ensuring a future-proof network. For more details on implementing these protocols, check out Cisco's documentation in the reference section.
References
What redundancy procedures are based on Layer 2? - ID: 109479676 - Industry Support Siemens
Redundancy for industrial communication networks | Industrial Ethernet Book




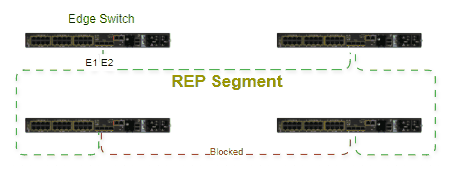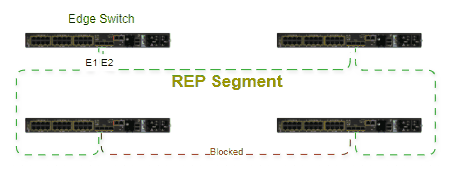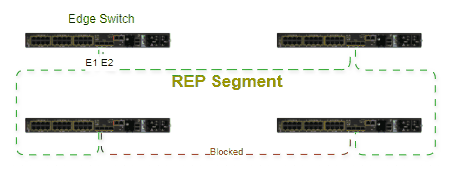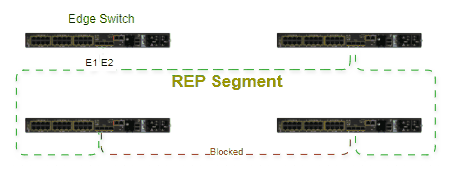



.jpg)




