The evolution of switches: #cissp insight
Did you know that switches were already introduced in the 19th century? Voice switches, also known as circuit switches, were the backbone of communication networks. Invented in the late 19th century, these switches established a dedicated circuit between two points for the duration of a call. While effective, this method was resource-intensive, limiting the number of simultaneous calls that could be handled. Early switches required also significant human intervention for line establishment, posing security and reliability challenges. In the next sections, we will deep dive into the most important elements of switches and the security concerns we have today.
When did it all start?
The 1970s and 1980s marked the beginning of a new era with the introduction of packet switching, a concept which initially began with the invention of ARPANET, the predecessor of the modern internet. Unlike circuit switching, packet switching sends data in smaller packets through various routes before reassembling at the destination. This approach optimizes network efficiency and resource utilization.
Our office museum has a telephone switchboard, which you can see at the following picture:
Why packet switching?
- Improvement of efficiency: Packet switching allows multiple communications to share the same network bandwidth, significantly enhancing network efficiency compared to the dedicated paths of voice switching. If you were to compare it to a transition that is happening today, it would be the switch over from dark fiber to MPLS and later on to SD-WAN.
- Scalability: As the demand for data services grew, packet-switched networks proved to be highly scalable, accommodating more users and diverse data types without the need for expansion of the underlying infrastructure.
- Cost Optimization: The shared network approach of packet switching reduces operational costs. It eliminates the need for dedicated circuits for each communication, lowering both capital and maintenance expenses. This is also similar to the transition to SD-WAN.
- Additional capabilities: The switchover meant that the traditional circuits would also open up for other kinds of traffic than voice, which is basically what happened in the next few years.
- Resilience and Flexibility: Together with opening for other kinds of traffic, new capabilities were also introduces, like the ability of packet-switched networks to reroute data through multiple pathways, which enhances network resilience against failures and congestion.
What has changed?
Since then a lot of things have changed. Today we have an unthinkable transmission speed, from a few bps to gigabit or terabitps speeds. The initial packet switches didn't have any modern protocols supported, like MPLS, QoS etc. Their main purpose was to do basic data routing. Today we can see switches that also do dynamic routing, switching, have firewall capabilities and even VPN or IDS features. With the recent developments of AI we expect more machine learning and predictive analytics functionality, as well as possibility to automate troubleshooting and optimize networks. It will also help with securing that these systems are configured in alignment with the organization security policies.
What are some of the most common attacks against switches?
As this is a CISSP focused post, it's normal to discuss the security aspect. Historically the focus was in external threats to the company, but now we need to implement zero-trust principles as internal threats are equally important.
Some of the security concerns we face today are:
- MAC flooding, which basically is going to fill the MAC address table of the switch, causing it to become a hub and broadcasting packets to all ports. A hacker could sit on one of the ports and mirror the traffic to his PC.
- ARP poisoning. In this case, the hacker would send a fake ARP response over a local area network to behave as if they were one of the legitimate hosts. Years ago I experimented with an old rooted android phone. By using an app to poison ARP, I was able to hijack sessions and change all pictures on all websites that my colleagues visited at the office. Fun times...
- VLAN hopping. The hacker would add some extra VLAN tag to the packet, so that when the actual vlan tag was removed, the switch would see this hacker tag and send the traffic to a different VLAN than the original one.
- STP manipulation. Knowing how Spanning Tree does the root bridge election, the hacker would install a switch in the network and make it the root bridge, which would then send all traffic through it. This can be a devastating attack and can happen also due to a mistake. I've experienced shortage on multiple cities many years ago, because some misconfigured switch was connected by some end customer to the ISP network. Then the traffic for all those cities would tend to go through this single location and get black holed. This would come handy to a potential attacker, as all traffic would go through their switch, and they would have the possibility to perform Man in the Middle attacks.
- DoS and Vulnerabilities. The attacker could either overload the switch with traffic, or exploit some vulnerability. Vulnerabilities have more and more focus nowadays, considering the increasing threat landscape.
How do we mitigate them?
- Port Security. This is one of the first things that should be implemented in a modern network. Unauthorized devices should be prevented to connect to a network and the amount of MAC addresses learned through the ports should be limited, to avoid MAC flooding.
- Dynamic ARP inspection. To prevent poisoning of ARP and the possibility to hijack sessions like explained on point 2 above, ARP packets should be inspected, and the invalid ones should be blocked.
- Secure VLANs. There are several things to consider, but default and native VLANs should not be used, and access lists should be implemented to isolate traffic between networks.
- STP Root Guard and BPDU Guard. These mechanisms would prevent an unknown switch from connecting to our network and making devastating changes, like the ones explained on point 4 above.
- Regular updates. The only way to protect from vulnerabilities is to keep the software updated and reduce our exposure. Back in the old days, it was normal to brag about how many years a Cisco device had been on for. This is no longer an option today, and in the best case it should be mentioned as something to avoid. We still face gaps in this area when we analyze customer networks. The best option would be to implement switches that can be updated automatically.
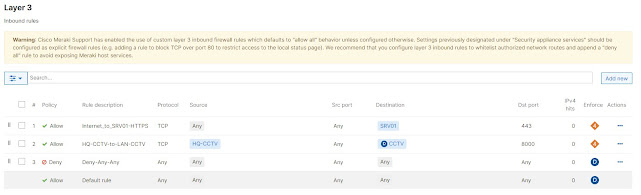
- Network Segmentation. The network should be divided to smaller subsets, like VLAN's and private VLANs. Furthermore, the traffic between these subsets should be limited by access lists. Ideally, the network should filter by TCP/UDP port and IP.
Conclusion
The modern day switches come from an invention that started back in the 19th century. Since then a lot has happened, which testifies the human effort and desire to improve. It also reflects an adaptation to the growing demands of a digitally connected world, offering improved efficiency, scalability, and expansion of communication capabilities. The introduction of AI is going to push further into the simplification and increase of capabilities towards a more digitized world, as well as simplify the secure implementation of them in accordance to the company policies. It will also pose new security risks, which we need to address. It's important to implement security with zero trust principles and take extra steps to secure the internal domain.
References
(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide: CISSP Domain 4: Communication and Network Security
General MS Best Practices - Cisco Meraki
Image courtesy: DALL-E












.png)


.jpg)




